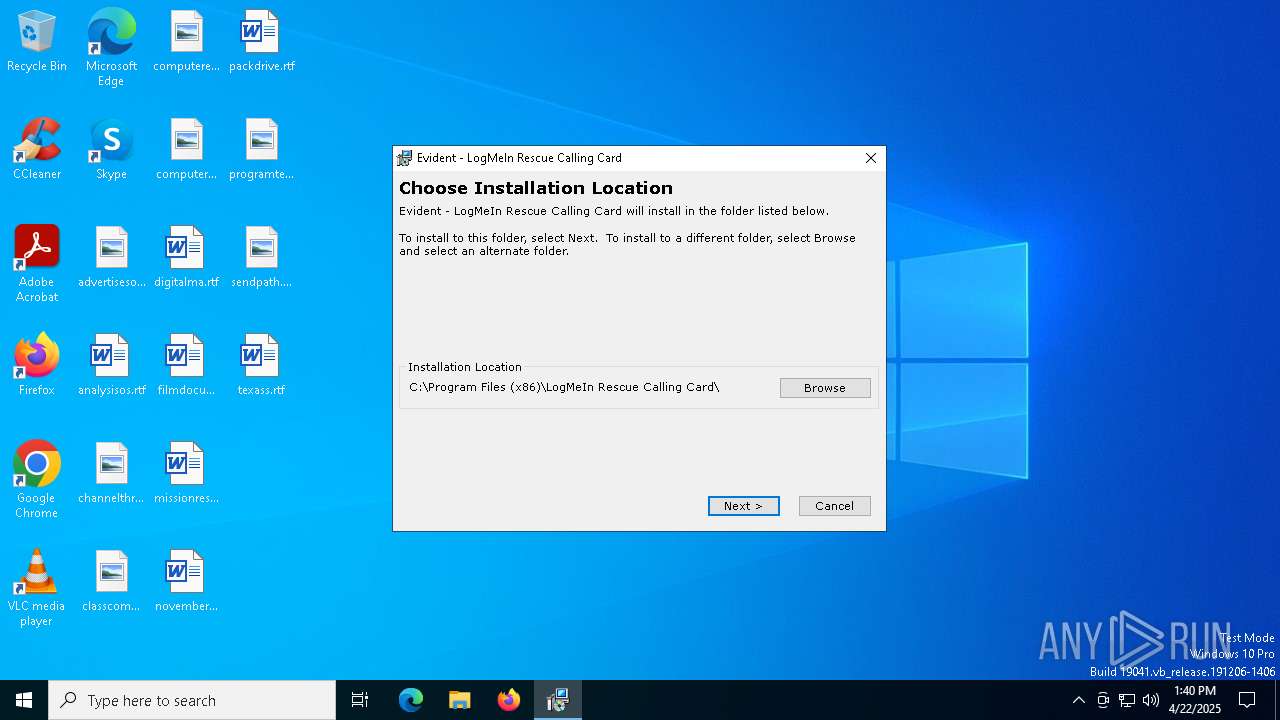
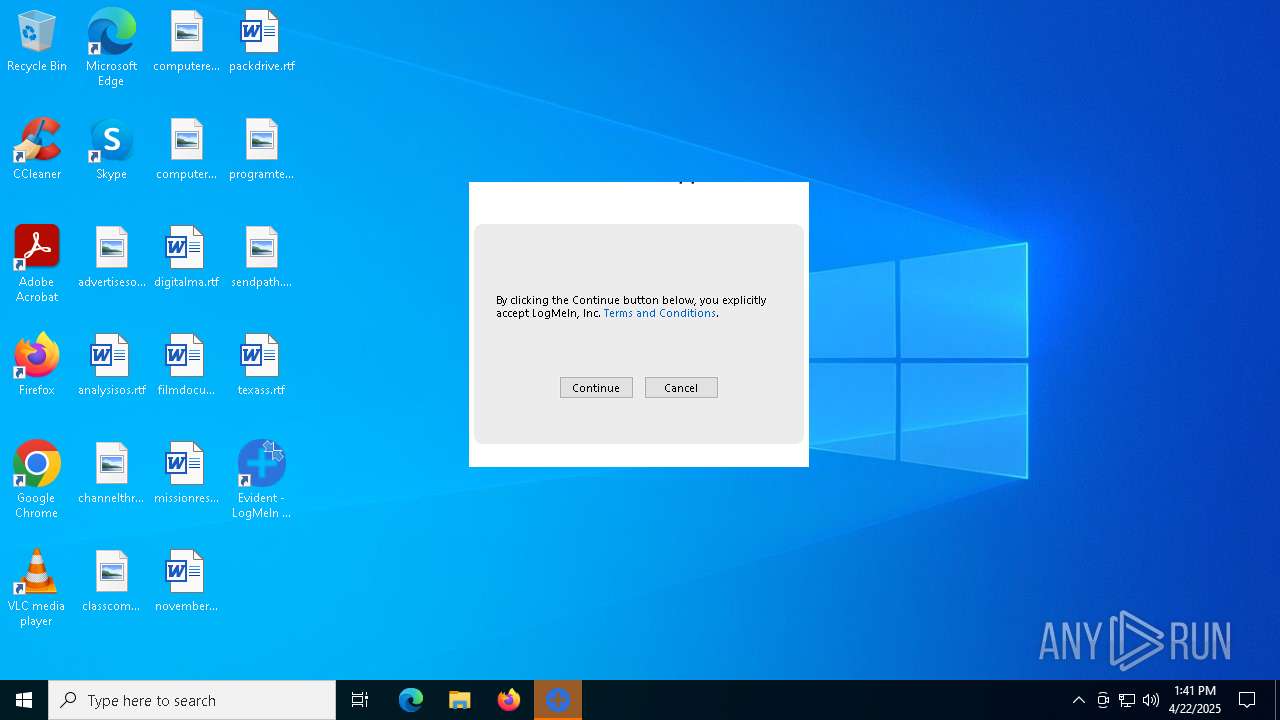
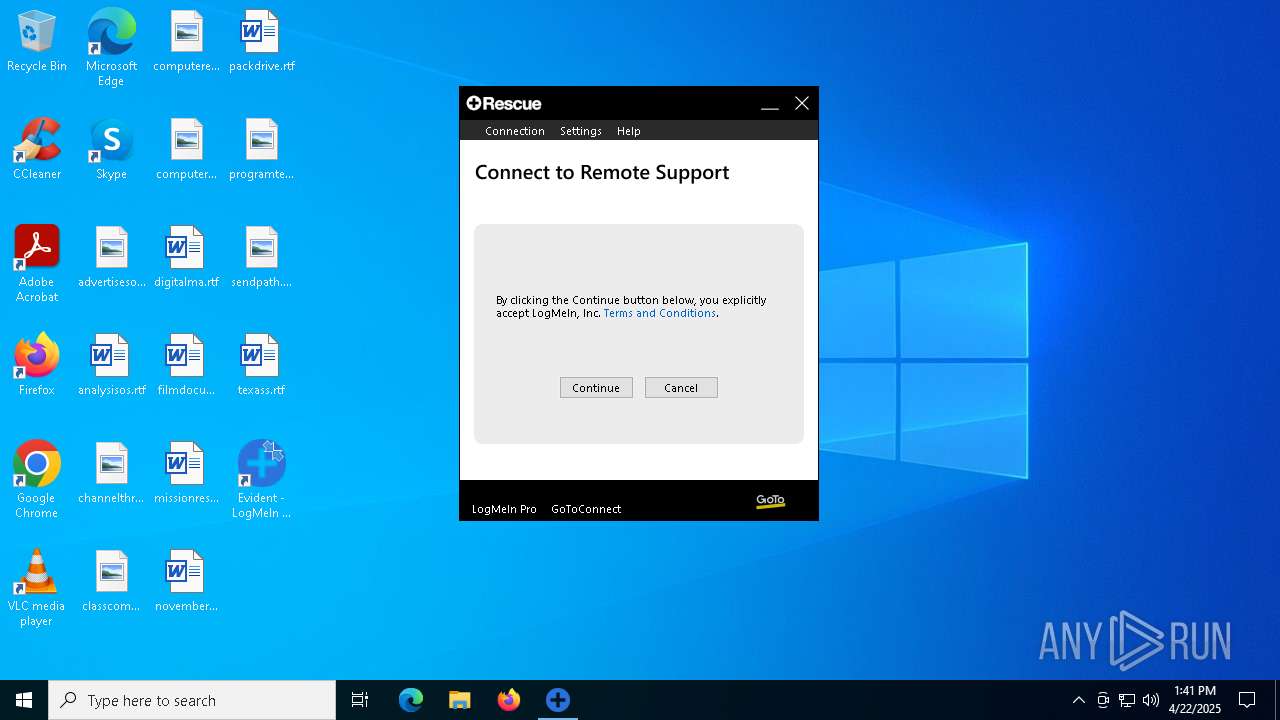
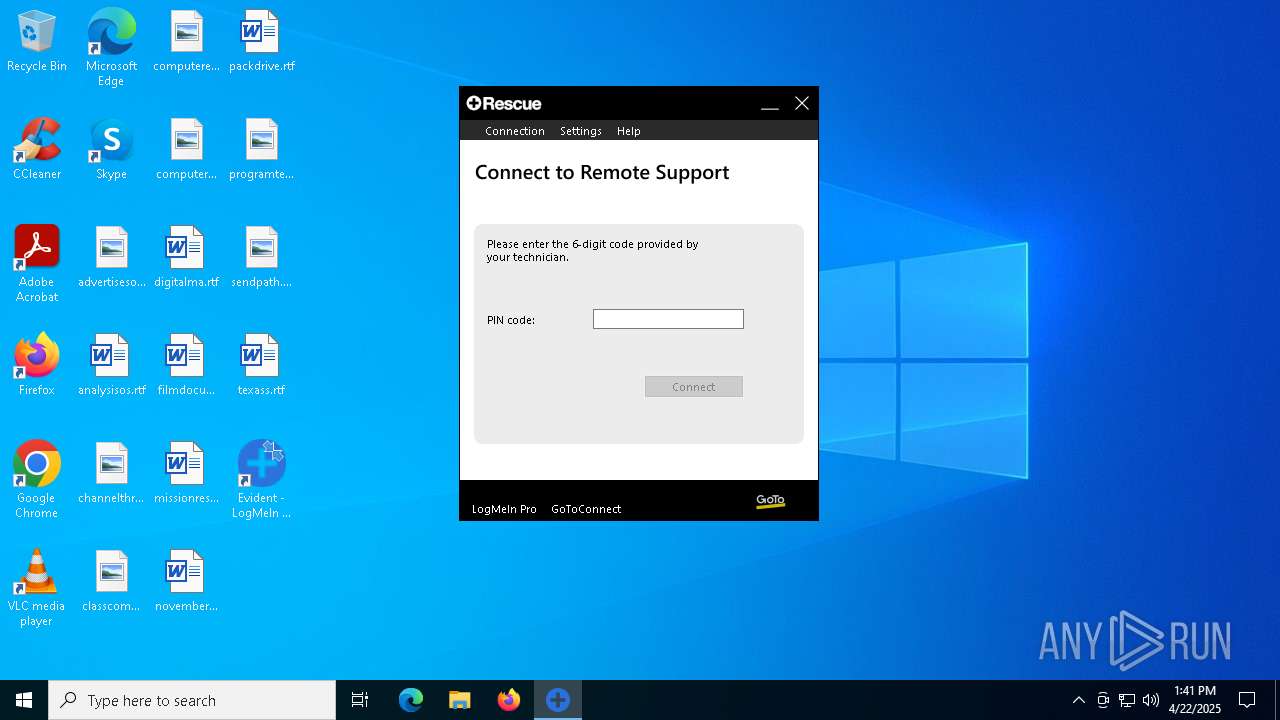
| File name: | LogMeIn Rescue Calling Card.msi |
| Full analysis: | https://app.any.run/tasks/0e13eb60-726f-4abd-9185-2c49f12b2237 |
| Verdict: | Malicious activity |
| Analysis date: | April 22, 2025, 13:40:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Number of Pages: 300, Template: Intel;0, Number of Words: 0, Security: 0, Name of Creating Application: Windows Installer, Author: LogMeIn, Inc., Comments: Calling Card x86 v7.51.1054, Revision Number: {FFAACEEE-198E-74B3-0083-22C575FDFB57}, Title: GoTo Calling Card, Subject: Evident - LogMeIn Rescue Calling Card |
| MD5: | 9C511FD31C70945BEA9D679D8F6E2FD9 |
| SHA1: | 11826A3EC0E42B0C7B3544F0194DC1157B3A7F04 |
| SHA256: | D6FD77171377AA1D61D5AA793659C7031D9E573063F17FD0CB925FE92C6BFC1C |
| SSDEEP: | 98304:BvI+cz07bLlbe3kRJmg6S3labWQCnE1Cpz7Iug3AOJjXeP/Q1guuy4dbgSgZnvLT:pW+9P4IM48CFzNwW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5116)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5868)
LOGMEINRESCUE mutex has been found
- CallingCard.exe (PID: 1128)
- CallingCard_srv.exe (PID: 3304)
Reads security settings of Internet Explorer
- CallingCard.exe (PID: 1128)
- CallingCard_srv.exe (PID: 3304)
Detected use of alternative data streams (AltDS)
- CallingCard.exe (PID: 1128)
There is functionality for taking screenshot (YARA)
- CallingCard.exe (PID: 1128)
- CallingCard_srv.exe (PID: 3304)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 4164)
- msiexec.exe (PID: 5868)
Creates files or folders in the user directory
- msiexec.exe (PID: 4164)
Checks proxy server information
- msiexec.exe (PID: 4164)
- CallingCard_srv.exe (PID: 3304)
- CallingCard.exe (PID: 1128)
- slui.exe (PID: 5956)
Reads the computer name
- msiexec.exe (PID: 3300)
- msiexec.exe (PID: 5868)
- msiexec.exe (PID: 6436)
- CallingCard.exe (PID: 1128)
- CallingCard_srv.exe (PID: 3304)
- msiexec.exe (PID: 5756)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4164)
Checks supported languages
- msiexec.exe (PID: 5868)
- msiexec.exe (PID: 3300)
- msiexec.exe (PID: 6436)
- CallingCard.exe (PID: 1128)
- CallingCard_srv.exe (PID: 3304)
- msiexec.exe (PID: 5756)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4164)
- msiexec.exe (PID: 5868)
Manages system restore points
- SrTasks.exe (PID: 2644)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5868)
- CallingCard.exe (PID: 1128)
- CallingCard_srv.exe (PID: 3304)
Reads the software policy settings
- msiexec.exe (PID: 4164)
- msiexec.exe (PID: 5868)
- CallingCard.exe (PID: 1128)
- slui.exe (PID: 5956)
- slui.exe (PID: 5892)
Creates a software uninstall entry
- msiexec.exe (PID: 5868)
Creates files in the program directory
- CallingCard.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Pages: | 300 |
| Template: | Intel;0 |
| Words: | - |
| Security: | None |
| Software: | Windows Installer |
| Author: | LogMeIn, Inc. |
| Comments: | Calling Card x86 v7.51.1054 |
| RevisionNumber: | {FFAACEEE-198E-74B3-0083-22C575FDFB57} |
| Title: | GoTo Calling Card |
| Subject: | Evident - LogMeIn Rescue Calling Card |
Total processes
152
Monitored processes
13
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Program Files (x86)\LogMeIn Rescue Calling Card\qpul5d\CallingCard.exe" | C:\Program Files (x86)\LogMeIn Rescue Calling Card\qpul5d\CallingCard.exe | msiexec.exe | ||||||||||||
User: admin Company: LogMeIn, Inc. Integrity Level: MEDIUM Description: LogMeIn Rescue Version: 7.51.435 Modules
| |||||||||||||||
| 2644 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3300 | C:\Windows\syswow64\MsiExec.exe -Embedding 72486E48A772266EAC5169975292BBE7 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3304 | "C:\Program Files (x86)\LogMeIn Rescue Calling Card\qpul5d\CallingCard_srv.exe" -wd "C:\ProgramData\LogMeIn Rescue Calling Card\qpul5d" | C:\Program Files (x86)\LogMeIn Rescue Calling Card\qpul5d\CallingCard_srv.exe | — | CallingCard.exe | |||||||||||
User: admin Company: LogMeIn, Inc. Integrity Level: MEDIUM Description: LogMeIn Rescue Version: 7.51.435 Modules
| |||||||||||||||
| 4164 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\LogMeIn Rescue Calling Card.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5756 | C:\Windows\syswow64\MsiExec.exe -Embedding 83E45989EB5E21568E5E2D4B7BC484DA E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5868 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 740
Read events
15 443
Write events
278
Delete events
19
Modification events
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000002866D3308CB3DB01EC16000004150000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000002866D3308CB3DB01EC16000004150000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000027DD42318CB3DB01EC16000004150000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000027DD42318CB3DB01EC16000004150000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000003D074A318CB3DB01EC16000004150000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000FFA347318CB3DB01EC16000004150000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5116) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F9B808328CB3DB01FC13000008160000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5116) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F9B808328CB3DB01FC130000EC080000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5116) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F9B808328CB3DB01FC130000501A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5116) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F9B808328CB3DB01FC130000A0170000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
19
Suspicious files
33
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5868 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 5868 | msiexec.exe | C:\Windows\Installer\115a04.msi | — | |
MD5:— | SHA256:— | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:EF666BF967D236A6CE187FAACFB9A078 | SHA256:023FF32C4670B64E9B9C873A7F4213A158F179EBFDA4A8F708524ED0788A7EFB | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:DAF220C59011E8B4C2209785A3CD0DAC | SHA256:09864A87707660A5920570D6C4B941859C557579AC377DA8FB016AB822D18772 | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:F8E9132B5EE09CF7865187CCABC101F7 | SHA256:932F8D8C1848F81D9504DA1913EDE3AAC21F6B09C4439BC1C46E63B73245D7E6 | |||
| 5868 | msiexec.exe | C:\Windows\Installer\MSI5EF5.tmp | executable | |
MD5:4FA6CD6685A323B67BE3C7B9813848F2 | SHA256:5DF4009BC5930606BDA011BF90360ECA2CC2A4E9F27BFEE67EC77B553D86B538 | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_6808B279563A59FEB199FAF60E053D02 | binary | |
MD5:244D563FA56601FCCB87397BF23B03A6 | SHA256:3E3CB0E41D242E5BFFABDC299EB748F9D961CFDCF754EA8235F3D4C485C1D93C | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE4D5.tmp | executable | |
MD5:4FA6CD6685A323B67BE3C7B9813848F2 | SHA256:5DF4009BC5930606BDA011BF90360ECA2CC2A4E9F27BFEE67EC77B553D86B538 | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE2C1.tmp | executable | |
MD5:4FA6CD6685A323B67BE3C7B9813848F2 | SHA256:5DF4009BC5930606BDA011BF90360ECA2CC2A4E9F27BFEE67EC77B553D86B538 | |||
| 4164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIF4A5.tmp | executable | |
MD5:4FA6CD6685A323B67BE3C7B9813848F2 | SHA256:5DF4009BC5930606BDA011BF90360ECA2CC2A4E9F27BFEE67EC77B553D86B538 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
34
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4164 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
4164 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4164 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAwL03T7HdoO9xcWGmUZKdE%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4164 | msiexec.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4244 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |