| URL: | https://www.01net.com/telecharger/windows/Utilitaire/compression_et_decompression/fiches/telecharger-2257.html |
| Full analysis: | https://app.any.run/tasks/ecc25f28-fcda-4270-a575-58bef2e20b87 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2021, 21:15:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1E12B70D6EBC83F39E932EE71D1B9305 |
| SHA1: | 84CAB55B504B170D45AF24450EE396AE902F047A |
| SHA256: | D6F3D10688162E56A829ECF6FCDED384871F1B41995D47322662125EF4DA297E |
| SSDEEP: | 3:N8DSL+BTb4SyKSKBg4Iy0FGiW0tcpWSyI5Gn:2OL+BTb47KSKBNr0rW0td7I5G |
MALICIOUS
Application was dropped or rewritten from another process
- wrar591fr_QnI2-B1.exe (PID: 2556)
- wrar591fr_QnI2-B1.exe (PID: 3336)
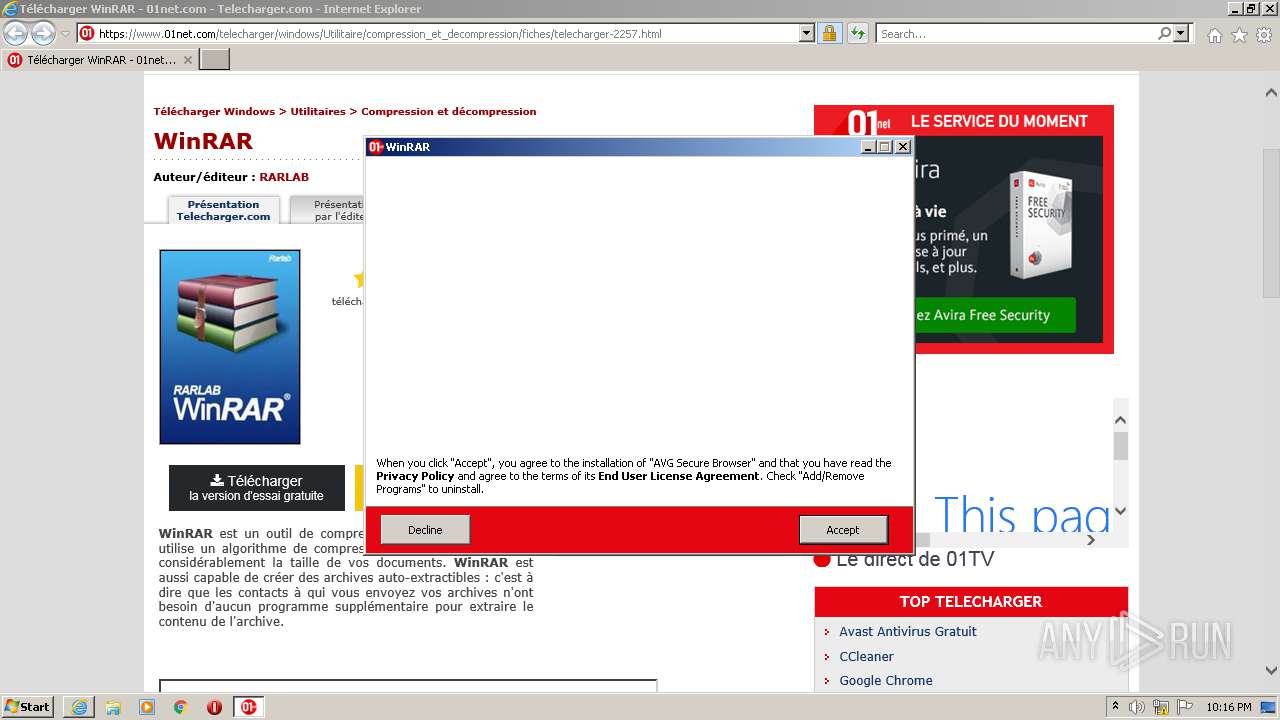
- avg_secure_browser_setup.exe (PID: 2628)
Drops executable file immediately after starts
- wrar591fr_QnI2-B1.exe (PID: 2556)
- wrar591fr_QnI2-B1.exe (PID: 3336)
- avg_secure_browser_setup.exe (PID: 2628)
Changes settings of System certificates
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Steals credentials from Web Browsers
- avg_secure_browser_setup.exe (PID: 2628)
Loads dropped or rewritten executable
- avg_secure_browser_setup.exe (PID: 2628)
Actions looks like stealing of personal data
- avg_secure_browser_setup.exe (PID: 2628)
SUSPICIOUS
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3984)
Reads the computer name
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3984)
- wrar591fr_QnI2-B1.tmp (PID: 2968)
- wrar591fr_QnI2-B1.tmp (PID: 3776)
- avg_secure_browser_setup.exe (PID: 2628)
Checks supported languages
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3984)
- wrar591fr_QnI2-B1.exe (PID: 3336)
- wrar591fr_QnI2-B1.tmp (PID: 2968)
- wrar591fr_QnI2-B1.tmp (PID: 3776)
- wrar591fr_QnI2-B1.exe (PID: 2556)
- avg_secure_browser_setup.exe (PID: 2628)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3984)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 460)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1376)
- wrar591fr_QnI2-B1.exe (PID: 2556)
- iexplore.exe (PID: 460)
- wrar591fr_QnI2-B1.exe (PID: 3336)
- wrar591fr_QnI2-B1.tmp (PID: 3776)
- avg_secure_browser_setup.exe (PID: 2628)
Reads Windows owner or organization settings
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Reads the Windows organization settings
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Drops a file with too old compile date
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Drops a file that was compiled in debug mode
- wrar591fr_QnI2-B1.tmp (PID: 3776)
- avg_secure_browser_setup.exe (PID: 2628)
Adds / modifies Windows certificates
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Reads Environment values
- avg_secure_browser_setup.exe (PID: 2628)
INFO
Checks supported languages
- iexplore.exe (PID: 1376)
- iexplore.exe (PID: 460)
Application launched itself
- iexplore.exe (PID: 1376)
Changes internet zones settings
- iexplore.exe (PID: 1376)
Reads the computer name
- iexplore.exe (PID: 1376)
- iexplore.exe (PID: 460)
Checks Windows Trust Settings
- iexplore.exe (PID: 460)
- iexplore.exe (PID: 1376)
Reads settings of System Certificates
- iexplore.exe (PID: 460)
- iexplore.exe (PID: 1376)
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Reads internet explorer settings
- iexplore.exe (PID: 460)
Creates files in the user directory
- iexplore.exe (PID: 460)
Changes settings of System certificates
- iexplore.exe (PID: 1376)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1376)
Reads CPU info
- iexplore.exe (PID: 460)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1376)
Application was dropped or rewritten from another process
- wrar591fr_QnI2-B1.tmp (PID: 2968)
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Loads dropped or rewritten executable
- wrar591fr_QnI2-B1.tmp (PID: 3776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1376 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1376 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.01net.com/telecharger/windows/Utilitaire/compression_et_decompression/fiches/telecharger-2257.html" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2556 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\wrar591fr_QnI2-B1.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\wrar591fr_QnI2-B1.exe | iexplore.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Lakon Software Download Manager Exit code: 0 Version: 1.5.3 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\Temp\is-6EDIU.tmp\prod0_extract\avg_secure_browser_setup.exe" /s /run_source=avg_ads_is /is_pixel_psh=BjYV4fPKGhitKtpRyilnSWNJmJ8KKvhtFmgUIBALV9u4BW3da3jHGUBoqZip1djtrVeROiwpOuZBHbE | C:\Users\admin\AppData\Local\Temp\is-6EDIU.tmp\prod0_extract\avg_secure_browser_setup.exe | wrar591fr_QnI2-B1.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: AVG Secure Browser Setup Exit code: 0 Version: 6.9.0.3251 Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\nsp81D1.tmp\AVGBrowserUpdateSetup.exe" /silent /install "bundlename=AVG Secure Browser&appguid={48F69C39-1356-4A7B-A899-70E3539D4982}&appname=AVG Secure Browser&needsadmin=true&lang=en-US&brand=9145&ap=mv:91.1.10666.126&installargs=--make-chrome-default --force-default-win10 --reset-default-win10 --auto-import-data%3Diexplore --import-cookies --auto-launch-chrome --private-browsing" | C:\Users\admin\AppData\Local\Temp\nsp81D1.tmp\AVGBrowserUpdateSetup.exe | — | avg_secure_browser_setup.exe | |||||||||||
User: admin Company: AVG Technologies Integrity Level: HIGH Description: AVG Browser Setup Exit code: 0 Version: 1.8.1066.0 | |||||||||||||||
| 2968 | "C:\Users\admin\AppData\Local\Temp\is-2920M.tmp\wrar591fr_QnI2-B1.tmp" /SL5="$401E6,1887685,1098752,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\wrar591fr_QnI2-B1.exe" | C:\Users\admin\AppData\Local\Temp\is-2920M.tmp\wrar591fr_QnI2-B1.tmp | — | wrar591fr_QnI2-B1.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\wrar591fr_QnI2-B1.exe" /SPAWNWND=$10210 /NOTIFYWND=$401E6 | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\wrar591fr_QnI2-B1.exe | wrar591fr_QnI2-B1.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Lakon Software Download Manager Exit code: 0 Version: 1.5.3 Modules
| |||||||||||||||
| 3776 | "C:\Users\admin\AppData\Local\Temp\is-IG8U9.tmp\wrar591fr_QnI2-B1.tmp" /SL5="$20212,1887685,1098752,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\wrar591fr_QnI2-B1.exe" /SPAWNWND=$10210 /NOTIFYWND=$401E6 | C:\Users\admin\AppData\Local\Temp\is-IG8U9.tmp\wrar591fr_QnI2-B1.tmp | wrar591fr_QnI2-B1.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3984 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe� Flash� Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
Total events
29 717
Read events
29 459
Write events
251
Delete events
7
Modification events
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30899024 | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 88538600 | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30899025 | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
12
Suspicious files
49
Text files
125
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_ACB084F1532E23E916946A083A45F6BF | binary | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\parameters[1].js | text | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\telecharger-2257[1].htm | html | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\smoothbox[1].js | html | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\scripts.min[1].js | text | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\smoothbox[1].css | text | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\styles[1].css | text | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\app[1].css | text | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\bdd[1].js | text | |
MD5:— | SHA256:— | |||
| 460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bootstrap[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
149
DNS requests
68
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
460 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGCDPAjbzpoUYuu%2B39wE%3D | US | der | 1.40 Kb | whitelisted |
460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
460 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | US | der | 1.41 Kb | whitelisted |
460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEArLKLpGXuU5CHZ0cPPNxhI%3D | US | der | 471 b | whitelisted |
460 | iexplore.exe | GET | 200 | 13.32.23.69:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
460 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | US | der | 727 b | whitelisted |
460 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
460 | iexplore.exe | GET | 200 | 13.32.23.16:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
460 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
460 | iexplore.exe | 151.101.2.207:443 | www.01net.com | Fastly | US | unknown |
460 | iexplore.exe | 104.18.20.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
460 | iexplore.exe | 104.19.183.2:443 | cdn.hubvisor.io | Cloudflare Inc | US | shared |
460 | iexplore.exe | 205.185.216.10:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
460 | iexplore.exe | 143.204.205.27:443 | static.bfmtv.com | — | US | unknown |
460 | iexplore.exe | 69.16.175.10:443 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
460 | iexplore.exe | 104.18.11.207:443 | maxcdn.bootstrapcdn.com | Cloudflare Inc | US | suspicious |
460 | iexplore.exe | 142.250.186.34:443 | pagead2.googlesyndication.com | Google Inc. | US | suspicious |
460 | iexplore.exe | 2.16.186.104:443 | ced-ns.sascdn.com | Akamai International B.V. | — | whitelisted |
460 | iexplore.exe | 104.20.20.31:443 | st3.igstatic.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.01net.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
cdn.hubvisor.io |
| malicious |
static.bfmtv.com |
| whitelisted |
ced-ns.sascdn.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
code.jquery.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
cdn.static.nexway.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
460 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
460 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |
460 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
460 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |