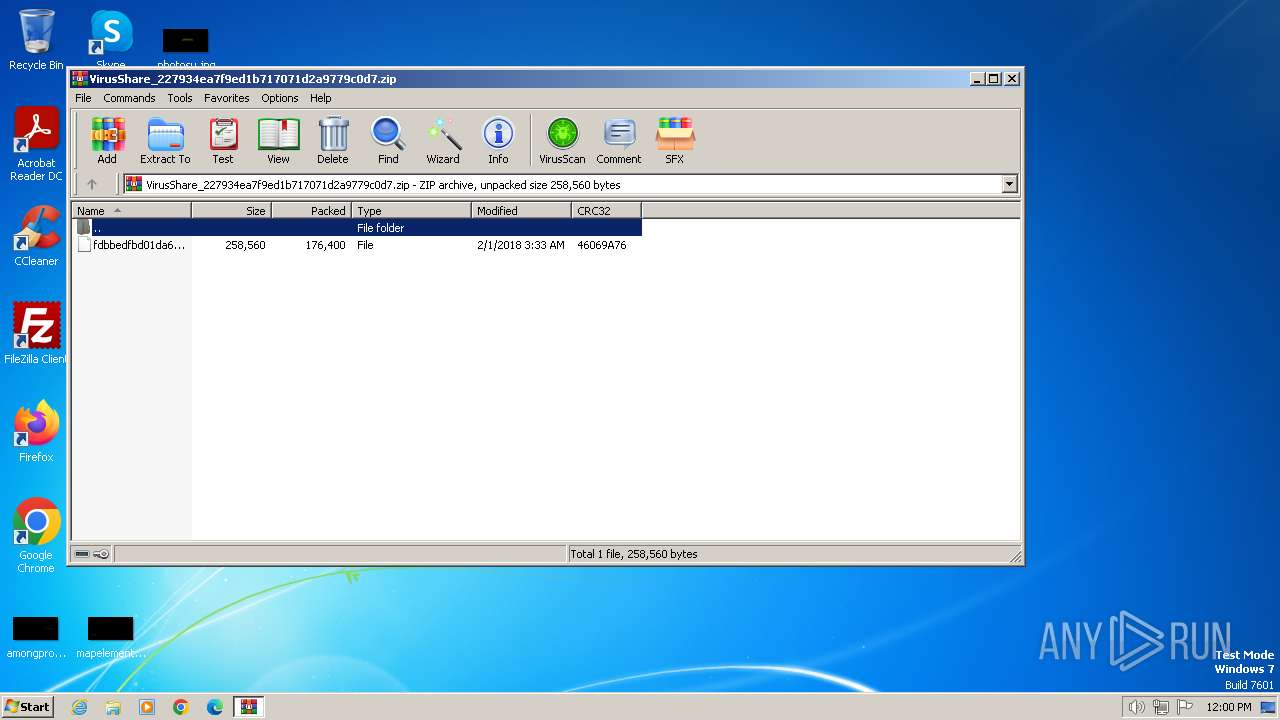
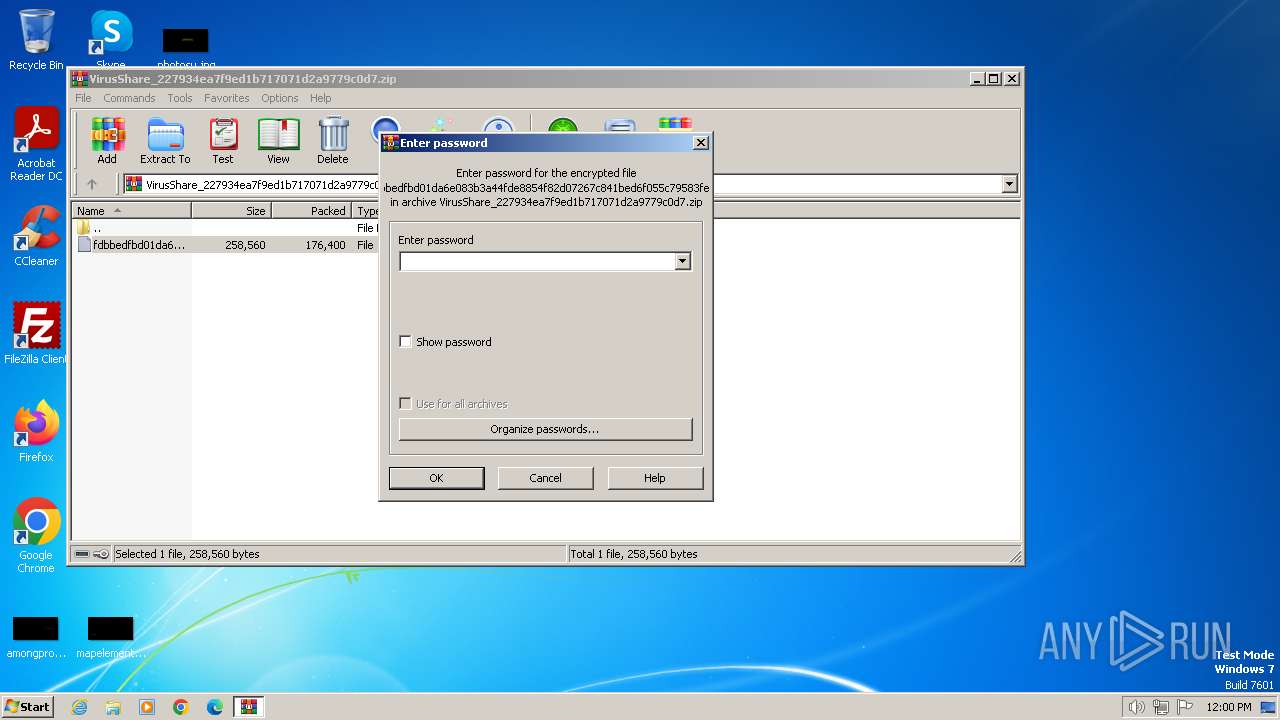
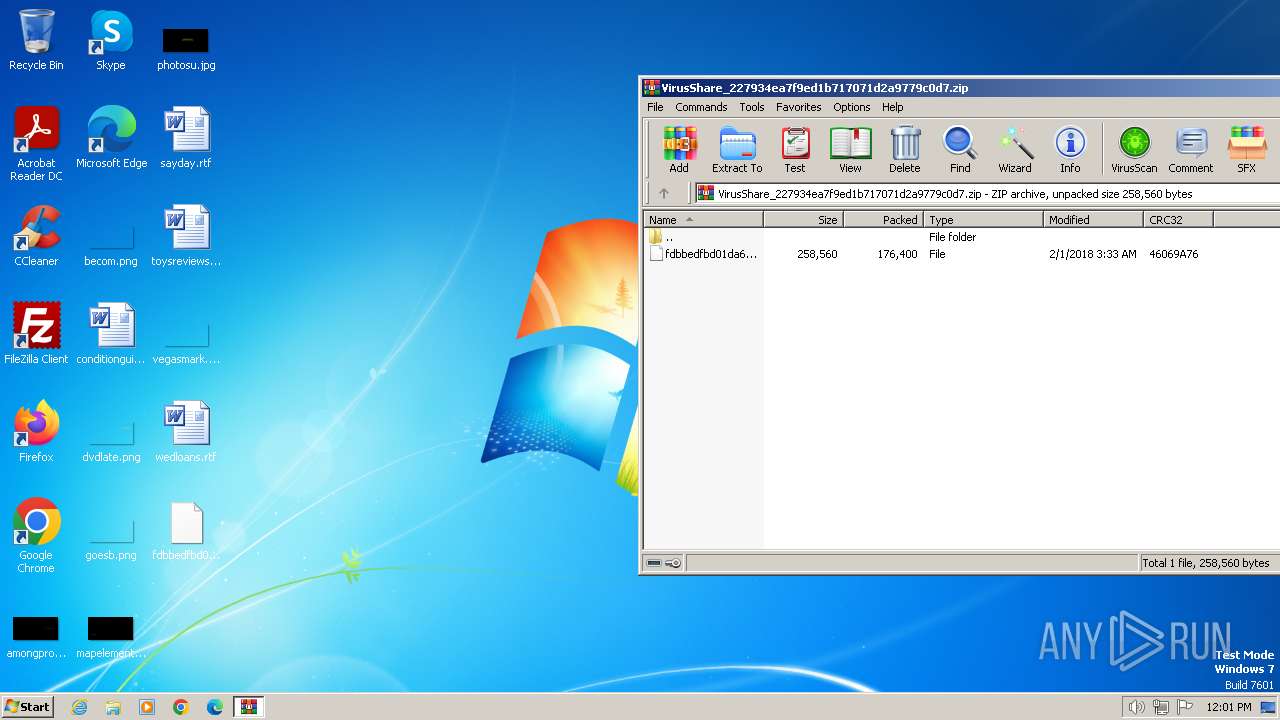
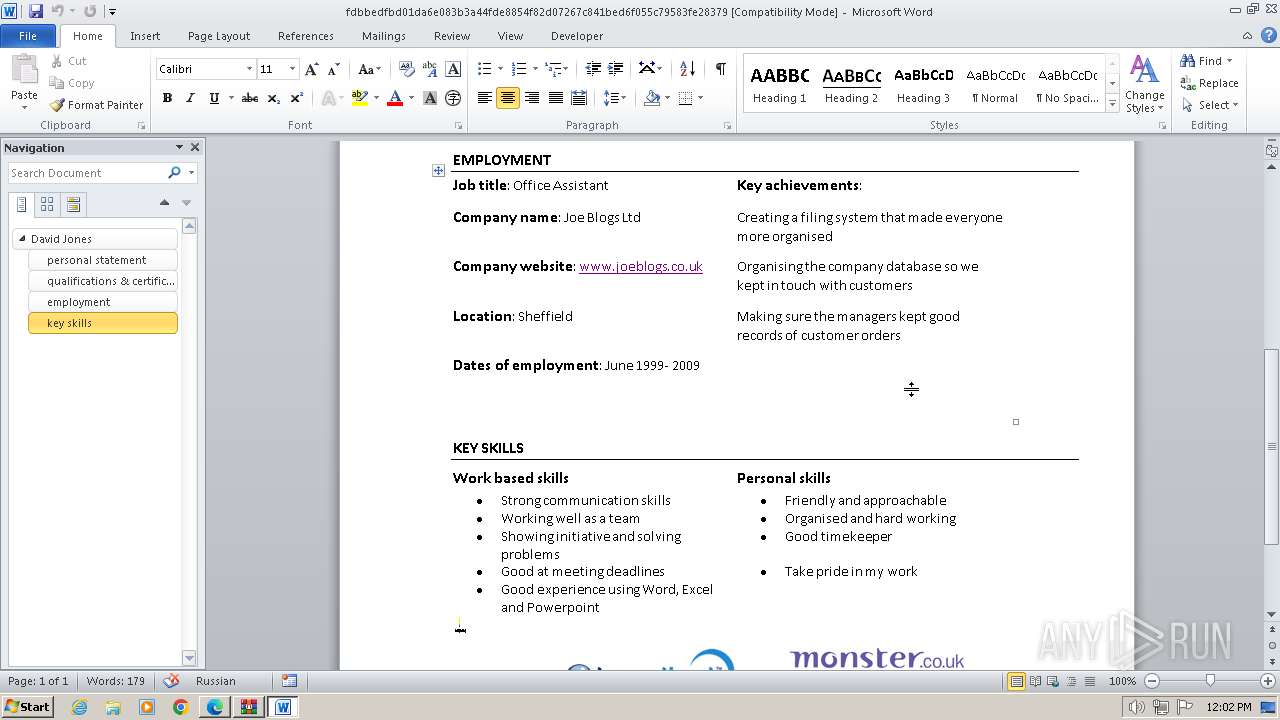
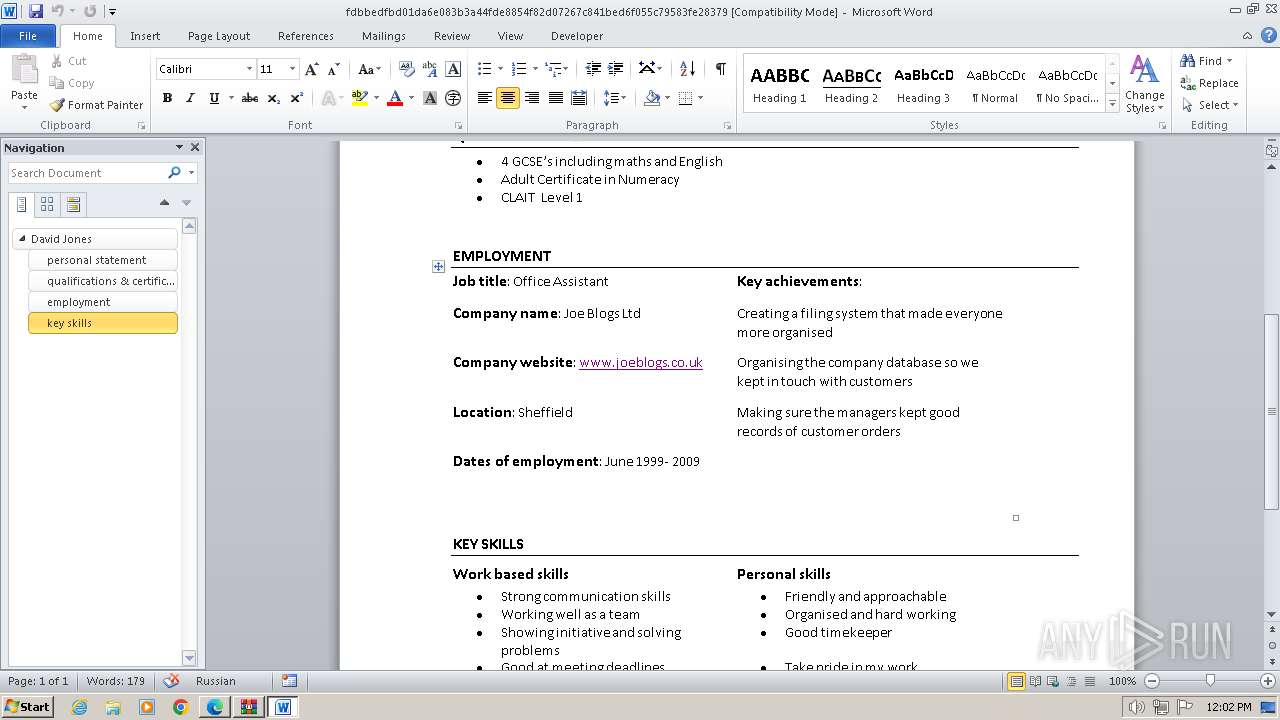
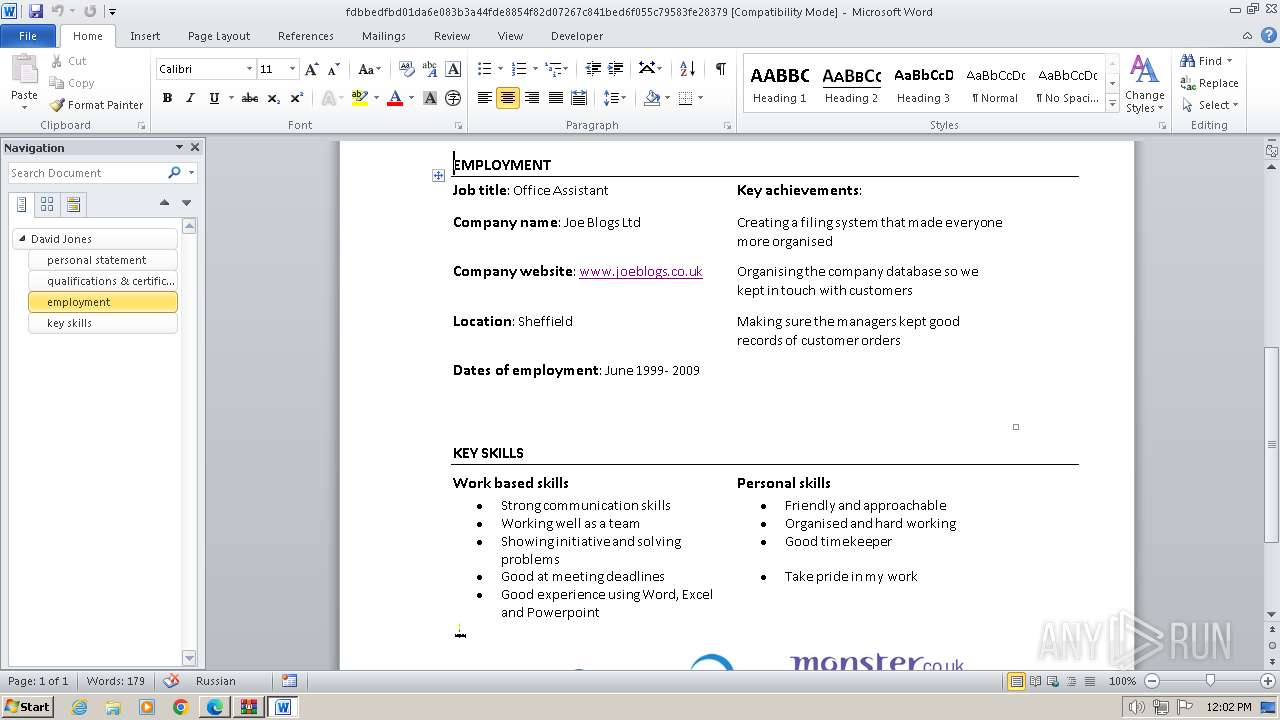
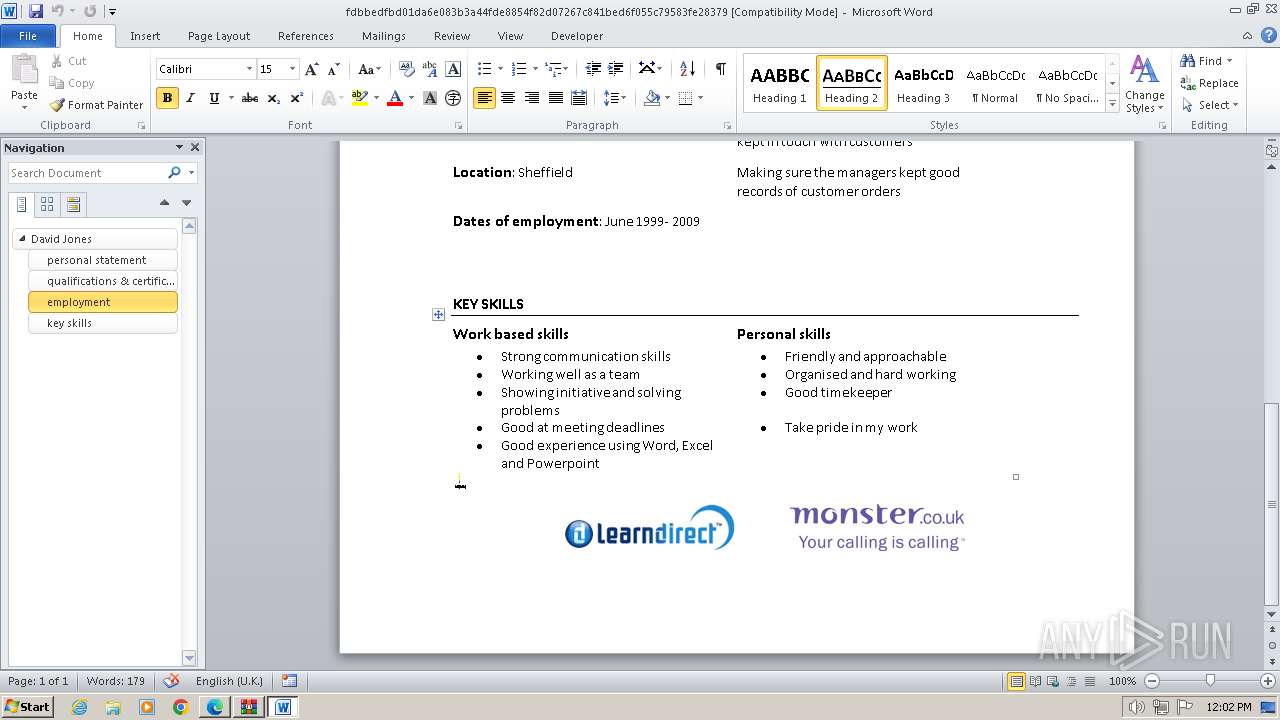
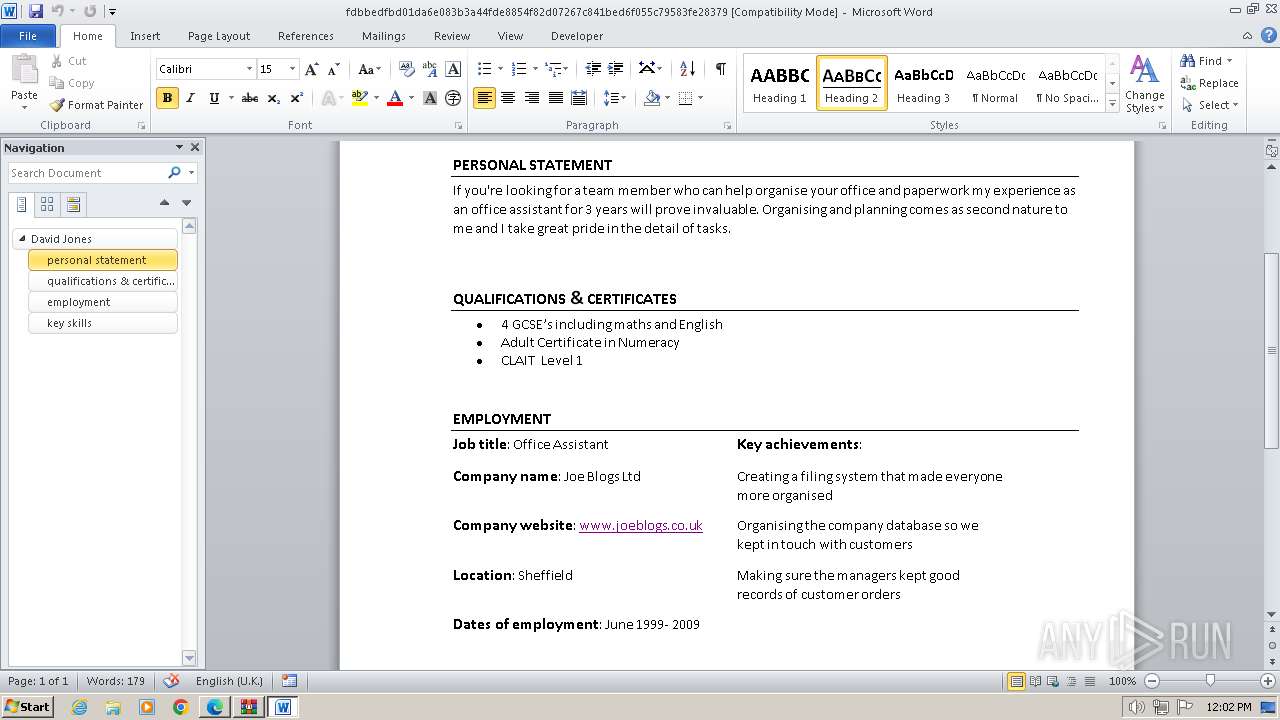
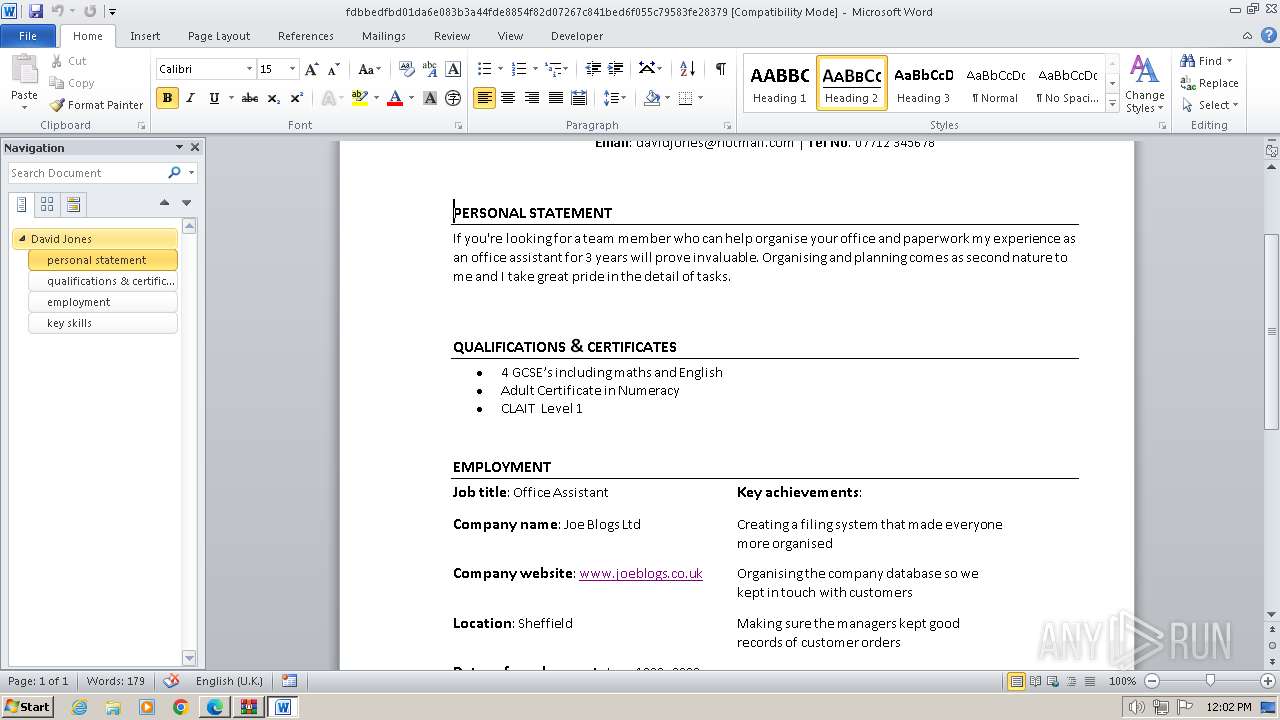
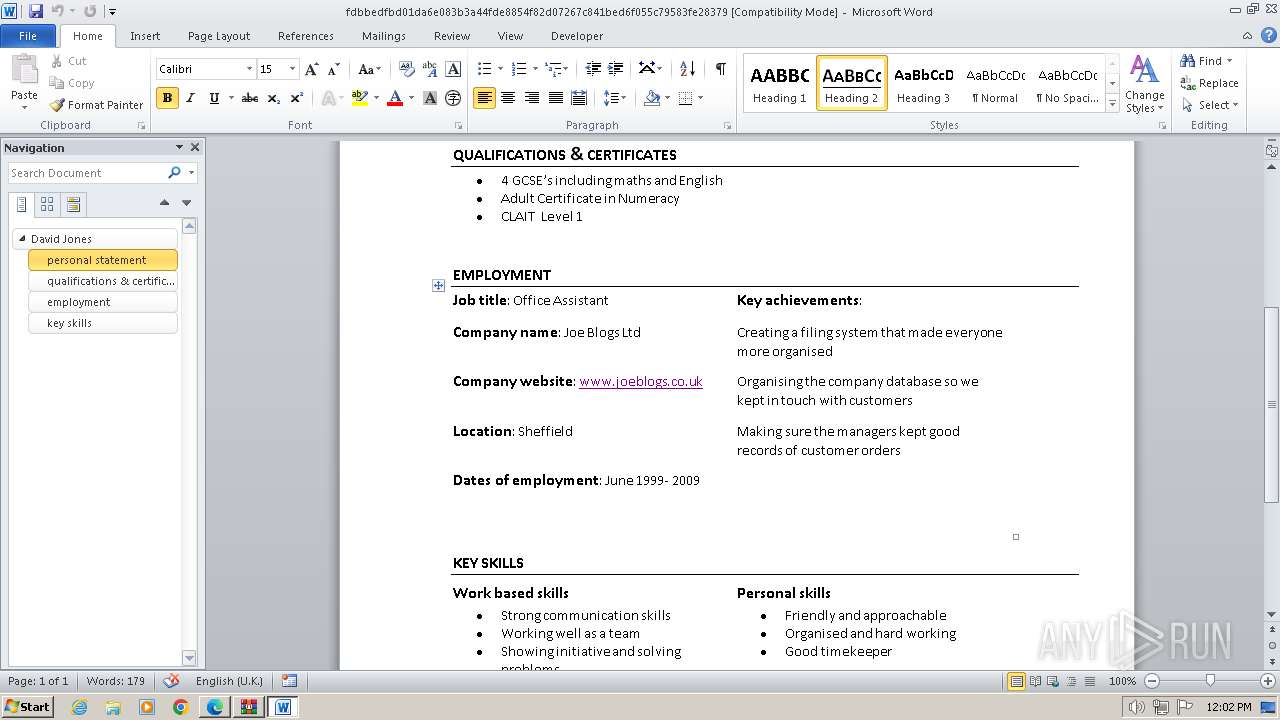
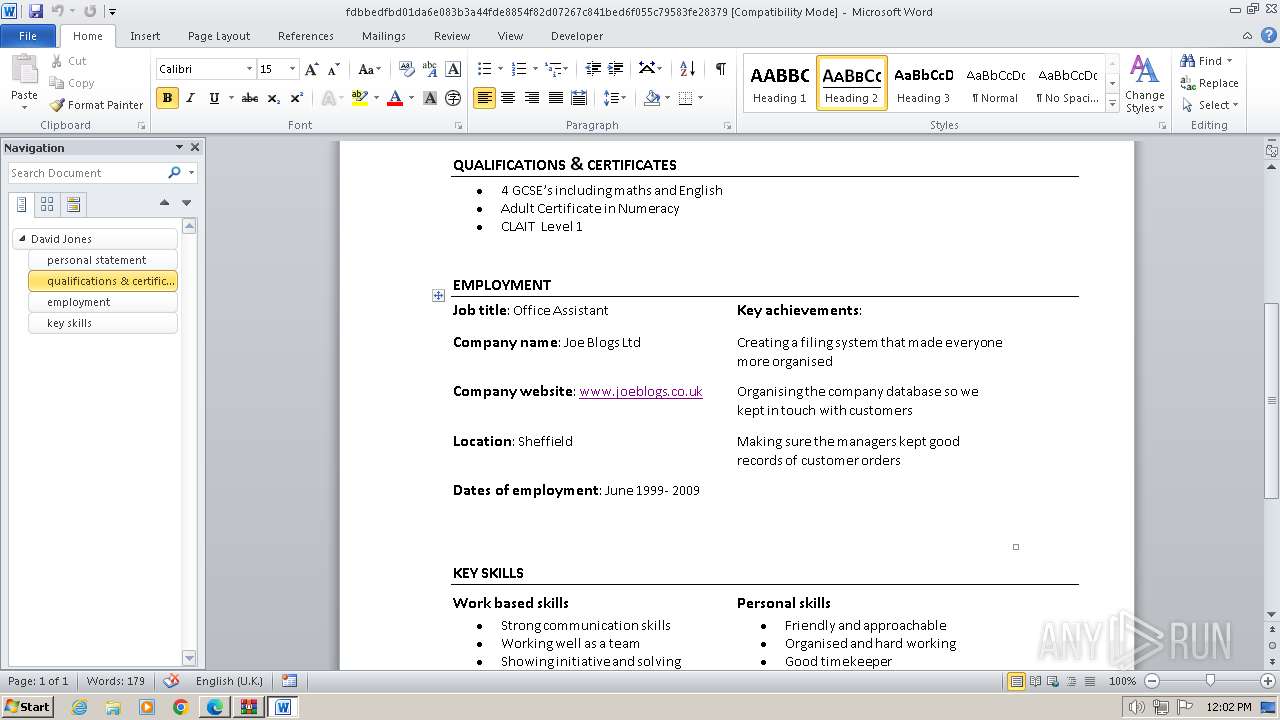
| File name: | VirusShare_227934ea7f9ed1b717071d2a9779c0d7.zip |
| Full analysis: | https://app.any.run/tasks/46614b4b-d842-461a-bebd-bc99ff5045a1 |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2024, 12:00:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 583593998AF2869F0563804A2E52AD2F |
| SHA1: | 9B98E6813B83ADC4E202359CB04EBE77380F59E7 |
| SHA256: | D6DCB0ABEB322E5F4579738B14630730FC87E3DED993A922B7DDFFC99FA22EF8 |
| SSDEEP: | 6144:zZ5vmO7YVFX13tc3ES6F/uxtNKz3l3LNrOL:zzX7uV13tCESrDET3iL |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1392)
Connection from MS Office application
- WINWORD.EXE (PID: 3768)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 2628)
INFO
Application launched itself
- msedge.exe (PID: 3560)
- msedge.exe (PID: 3964)
Manual execution by a user
- rundll32.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:02:01 03:33:36 |
| ZipCRC: | 0x46069a76 |
| ZipCompressedSize: | 176400 |
| ZipUncompressedSize: | 258560 |
| ZipFileName: | fdbbedfbd01da6e083b3a44fde8854f82d07267c841bed6f055c79583fe28379 |
Total processes
66
Monitored processes
28
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2216 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 376 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3968 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 492 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4980 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4992 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=4376 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4904 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --mojo-platform-channel-handle=3960 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4964 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=4480 --field-trial-handle=1240,i,17872037866227515270,45280658172616169,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\VirusShare_227934ea7f9ed1b717071d2a9779c0d7.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
13 588
Read events
12 992
Write events
459
Delete events
137
Modification events
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2628) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
7
Suspicious files
205
Text files
69
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
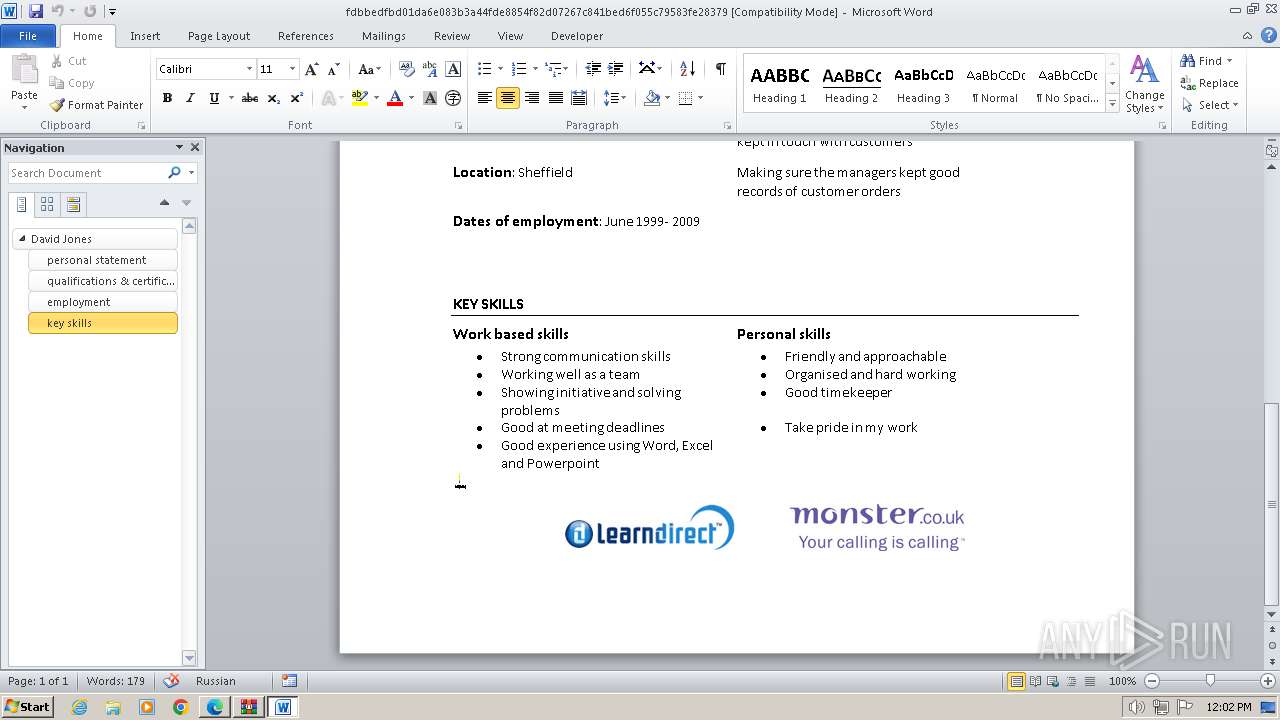
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD0A3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E33B2F48C17BF2B612B5EC0FA5E47429 | SHA256:171397CBA927DBDC279FF3279FA7B211ECFFD39F7EFAF38694C8A5ACF6C5444B | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\fdbbedfbd01da6e083b3a44fde8854f82d07267c841bed6f055c79583fe28379.LNK | binary | |
MD5:ECC223F3613397B02BA93FEF242931EE | SHA256:E9629CDCCEB157F45D60922069AACBED04B5D066DCD09020346AC9150E73CE2F | |||
| 3768 | WINWORD.EXE | C:\Users\admin\Desktop\~$bbedfbd01da6e083b3a44fde8854f82d07267c841bed6f055c79583fe28379 | pgc | |
MD5:CAA8B494632D84B75D4E320804DE079F | SHA256:C04FE054332E59125BE94EA3B9D40F9F597B967C46950C9D20C9433013E1A060 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\0L9I4TZQ.htm | html | |
MD5:F5D40B7259645010F9A248858AD14178 | SHA256:7F5007068D2B56EA9735E2490D60CFF2E72CAE312024AC1F6C91158EBA47D05D | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\FRXHSIDN | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:811320DC8DDDBAD2DA7CD40DE754294C | SHA256:91CA2597DCE94E6CF25B515B5E9B9F9806E0D1CB0F6D9E2FD5CFBF87C6E344D5 | |||
| 3768 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:0D7D0AB6F624783FEDCB66664C42A313 | SHA256:3329A24FE72938DE56BE82C4C2A9528141644741A0415D36B2818A0AE2B119C0 | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF173393.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
124
DNS requests
157
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3768 | WINWORD.EXE | GET | 304 | 23.32.238.210:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?084499ee290b4ca7 | unknown | — | — | unknown |
3768 | WINWORD.EXE | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
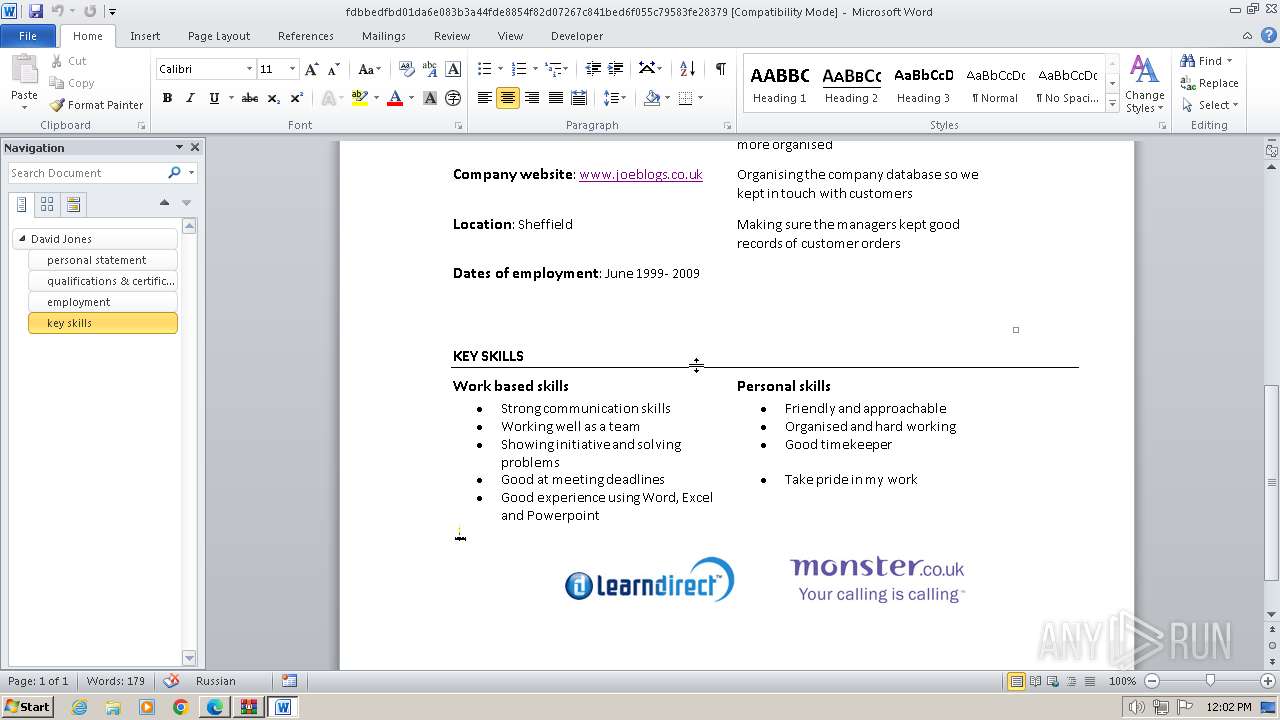
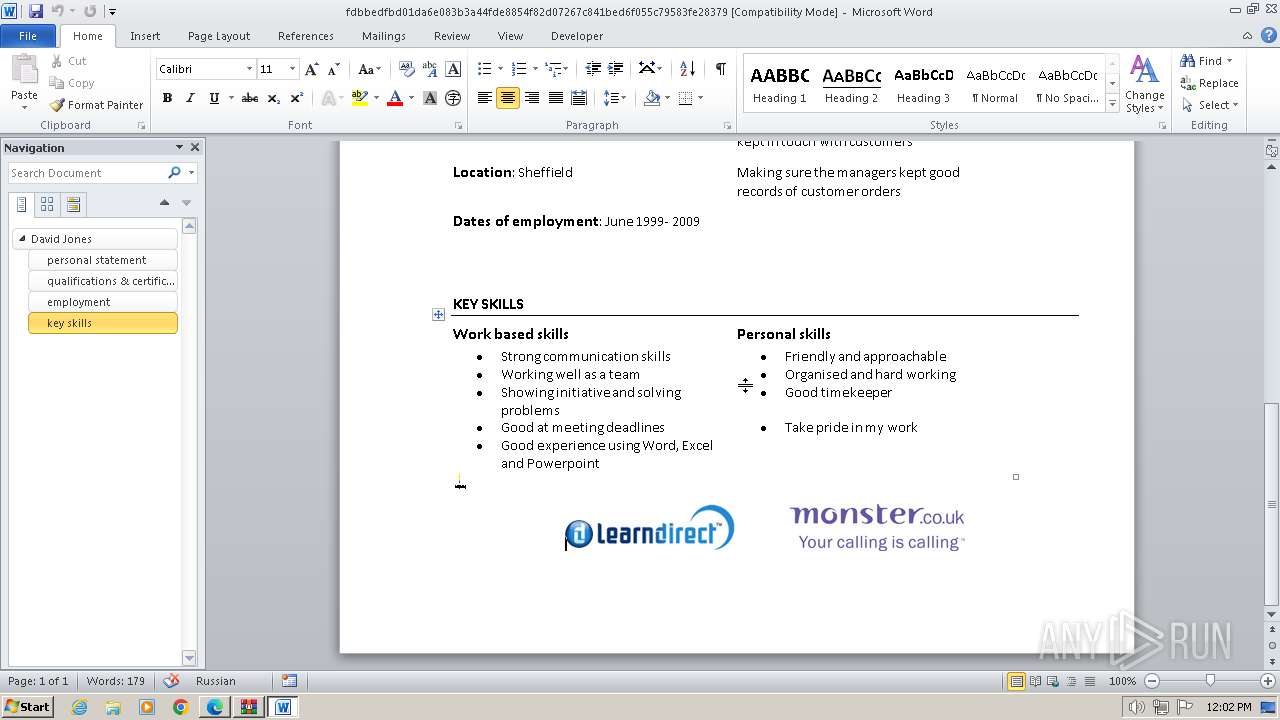
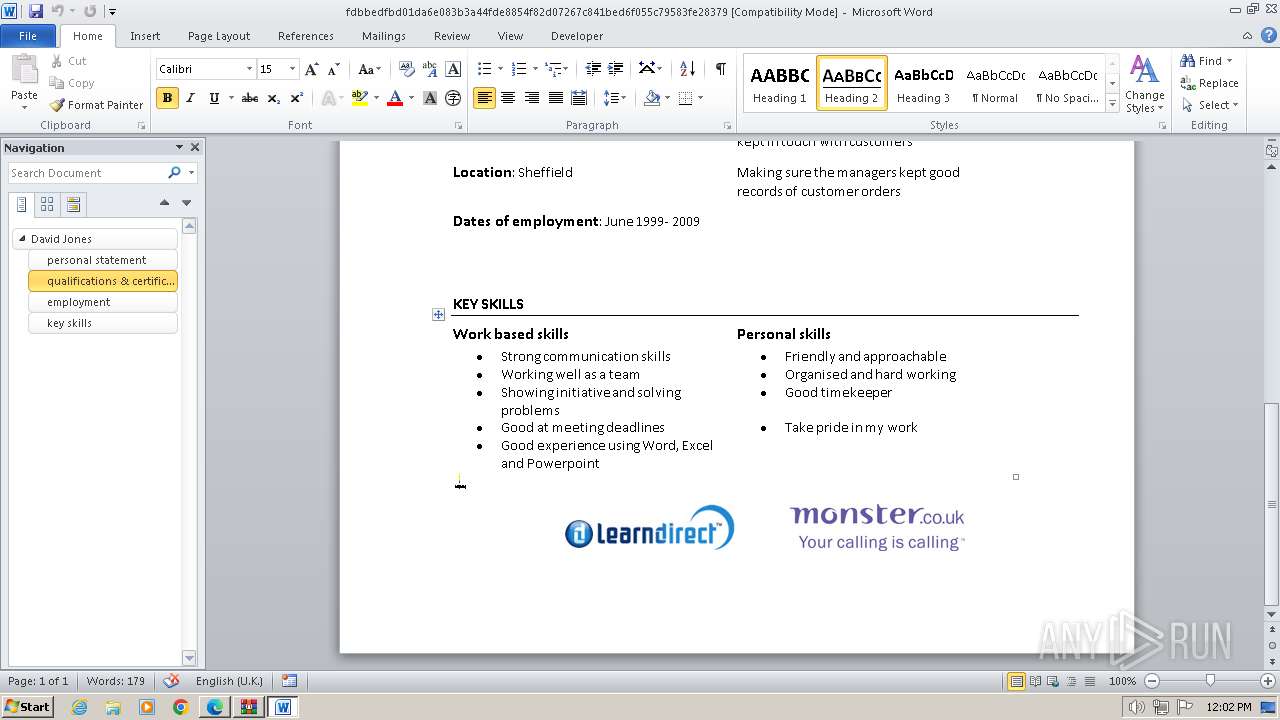
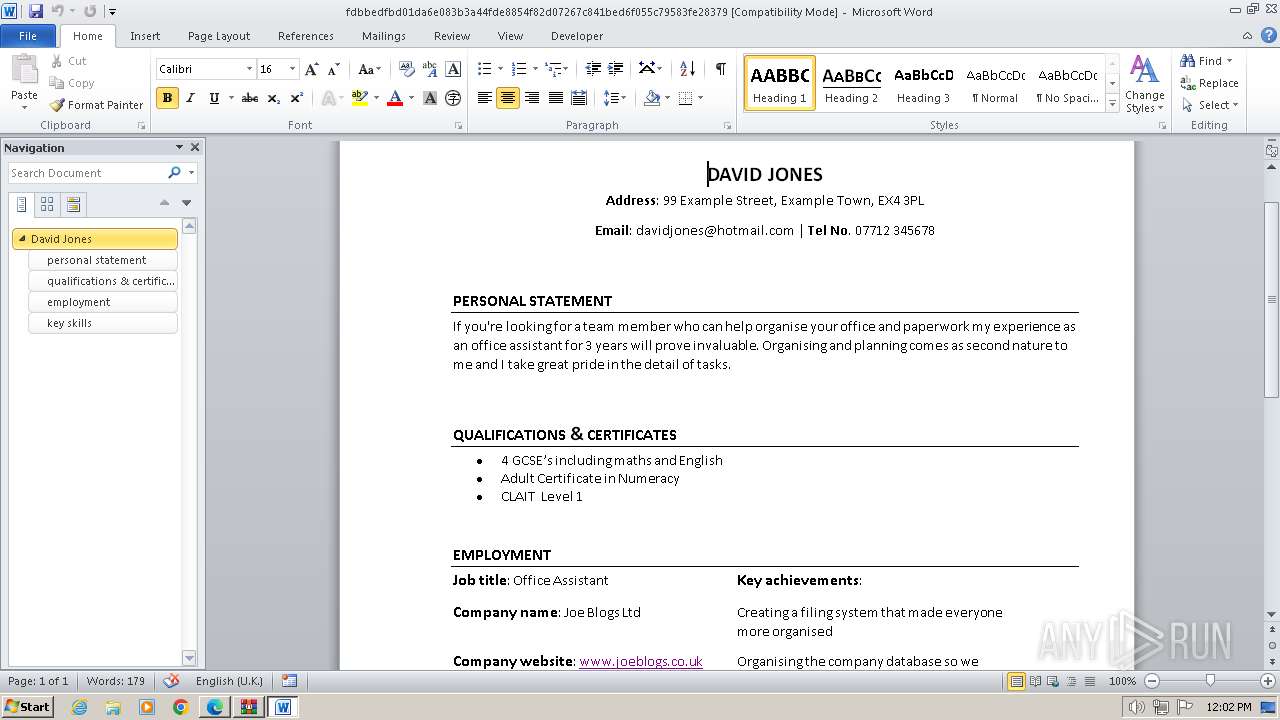
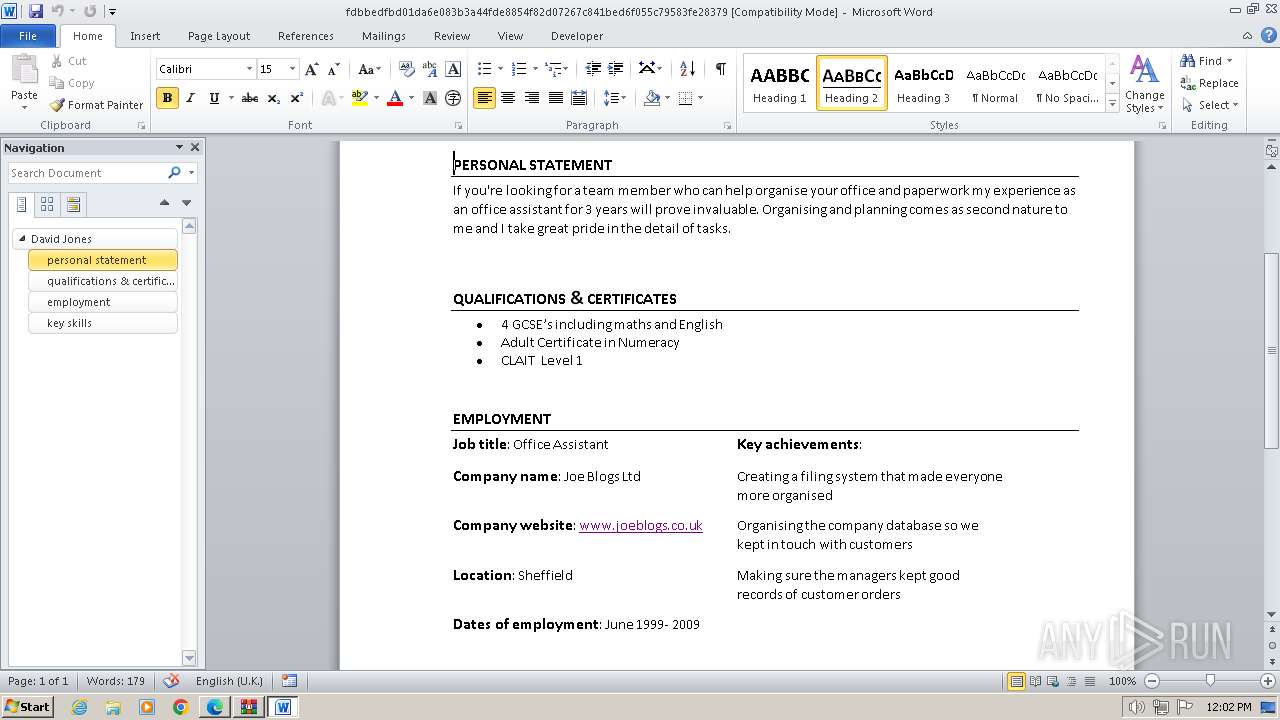
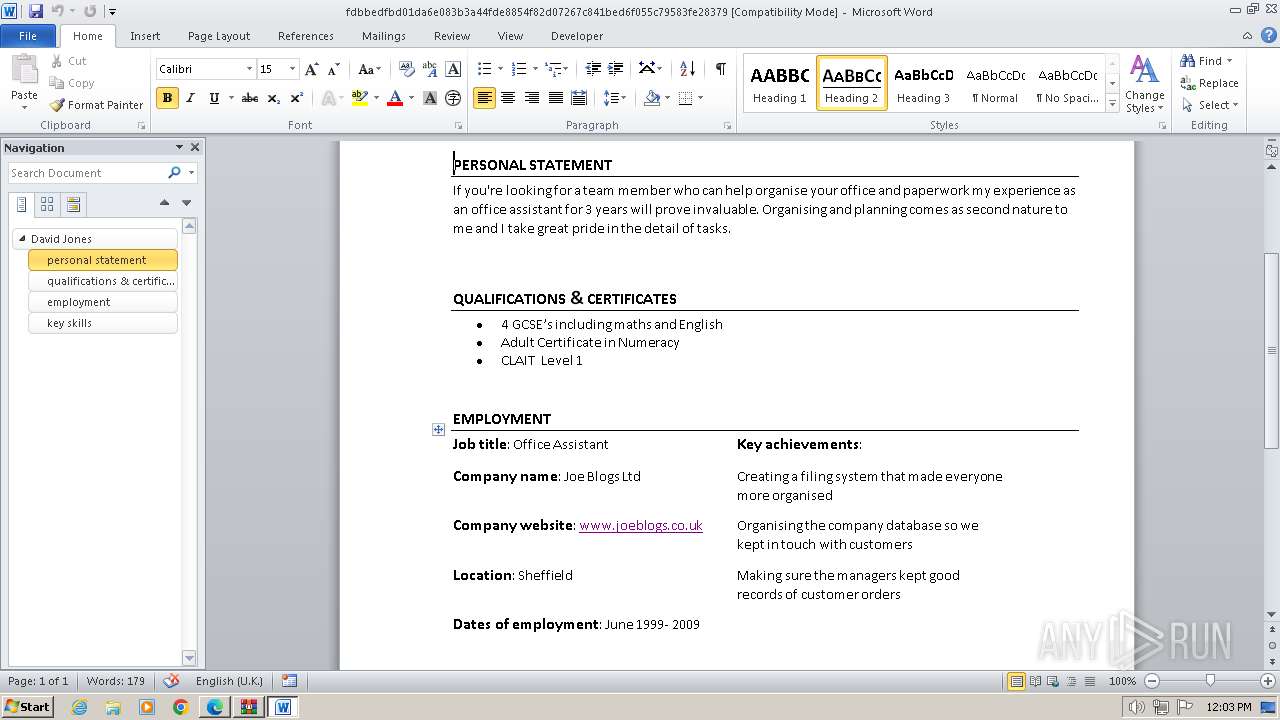
3768 | WINWORD.EXE | GET | 301 | 34.36.185.118:80 | http://www.learndirect.co.uk/ | unknown | — | — | unknown |
3768 | WINWORD.EXE | GET | 200 | 108.138.2.10:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
3768 | WINWORD.EXE | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
3768 | WINWORD.EXE | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | binary | 1.37 Kb | unknown |
3768 | WINWORD.EXE | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/s/gts1d4/t8UwLaA-ND8/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEE1YyQAEMLTBCbr2Eq3JBcM%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?624d1ab720bef5f8 | unknown | compressed | 65.2 Kb | unknown |
— | — | GET | 304 | 23.32.238.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1dd404ff67a3d8ee | unknown | compressed | 65.2 Kb | unknown |
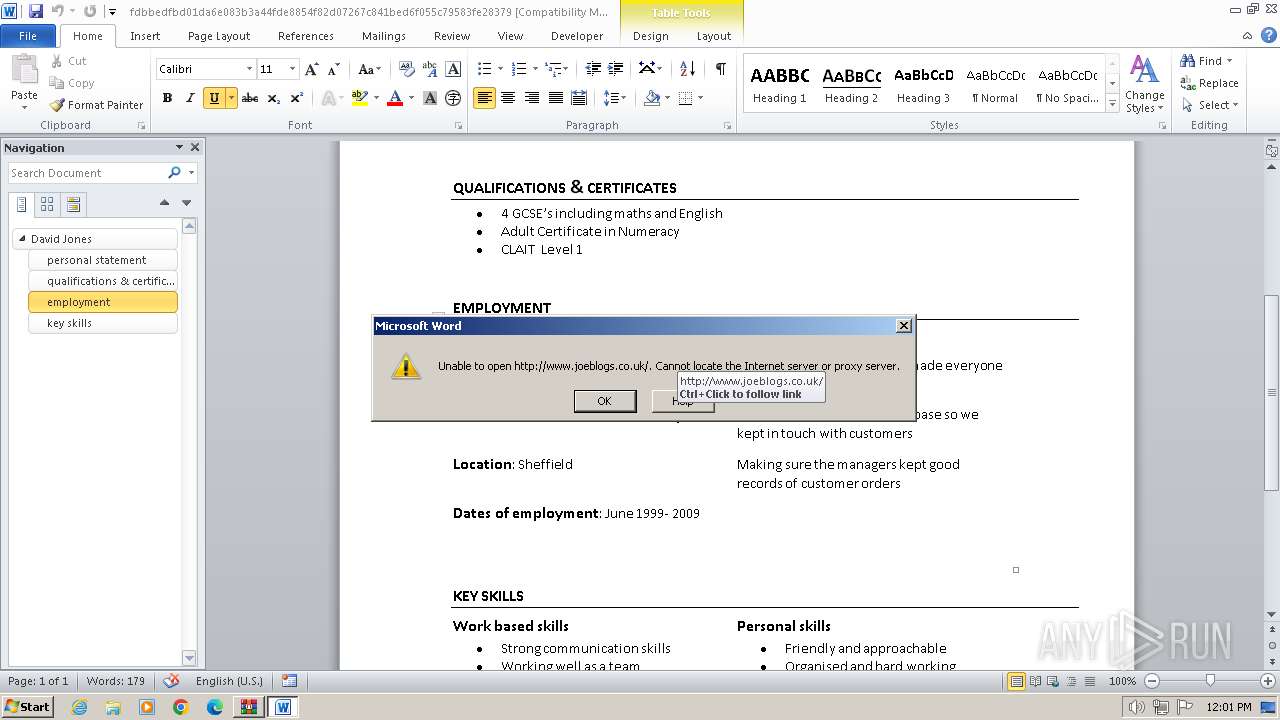
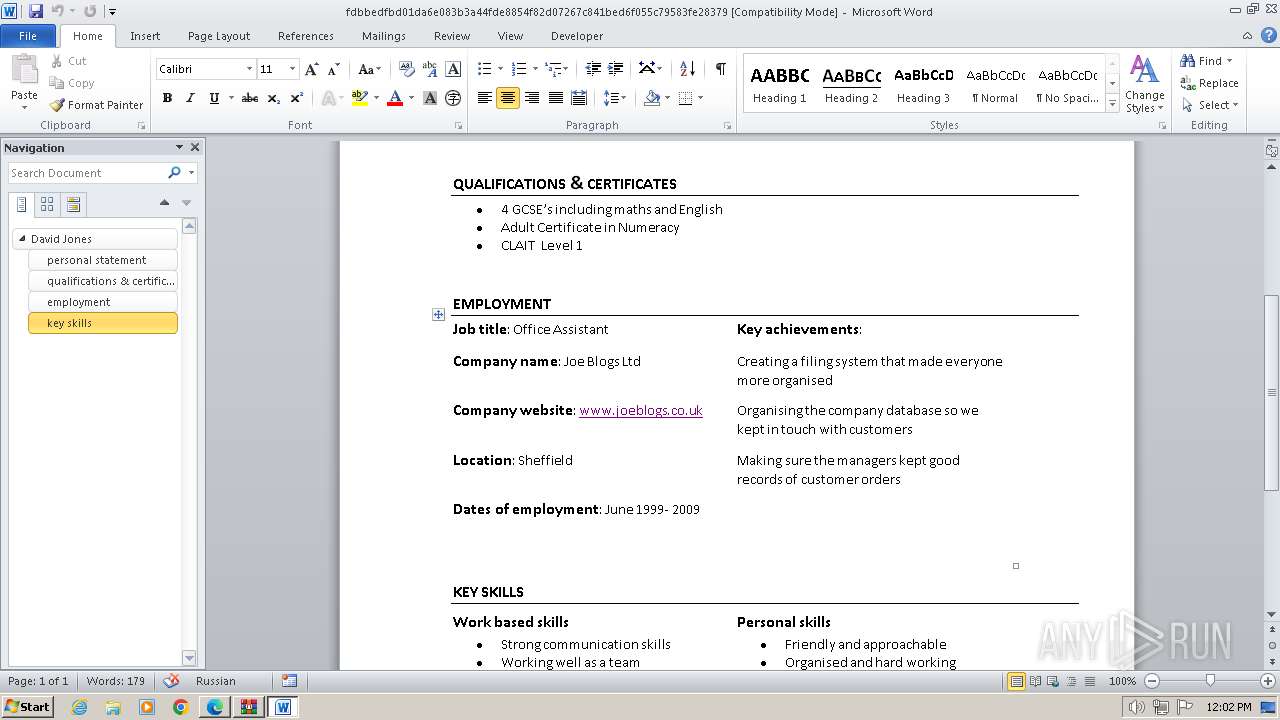
3768 | WINWORD.EXE | GET | 301 | 88.208.252.9:80 | http://www.joeblogs.co.uk/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3768 | WINWORD.EXE | 88.208.252.9:80 | www.joeblogs.co.uk | IONOS SE | GB | unknown |
3768 | WINWORD.EXE | 104.26.3.176:443 | joelblogs.co.uk | CLOUDFLARENET | US | unknown |
3768 | WINWORD.EXE | 13.32.99.128:80 | www.monster.co.uk | AMAZON-02 | US | unknown |
3768 | WINWORD.EXE | 13.32.99.128:443 | www.monster.co.uk | AMAZON-02 | US | unknown |
3768 | WINWORD.EXE | 23.32.238.210:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3768 | WINWORD.EXE | 108.138.2.10:80 | o.ss2.us | AMAZON-02 | US | unknown |
3768 | WINWORD.EXE | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.joeblogs.co.uk |
| unknown |
joelblogs.co.uk |
| unknown |
www.monster.co.uk |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
securemedia.newjobs.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2136 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
2136 | msedge.exe | Potential Corporate Privacy Violation | AV POLICY Observed TikTok Domain in TLS SNI (tiktok.com) |
Process | Message |
|---|---|
msedge.exe | [0206/120158.164:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|