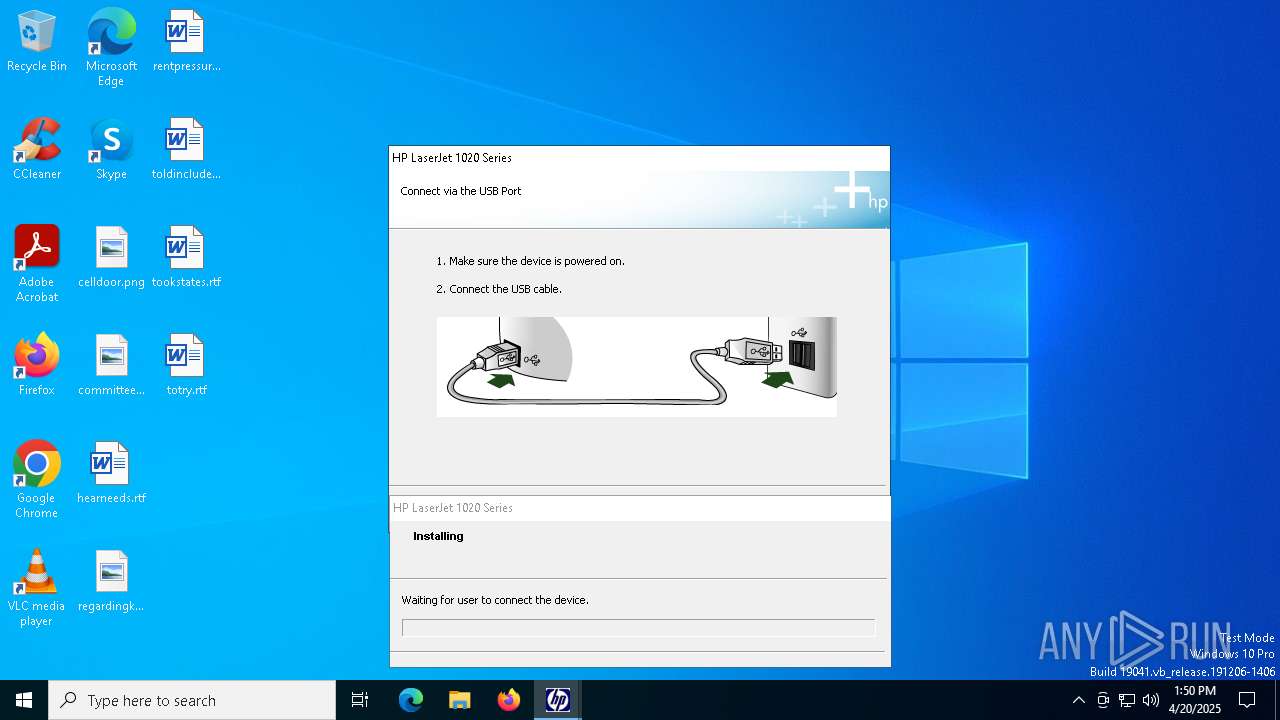
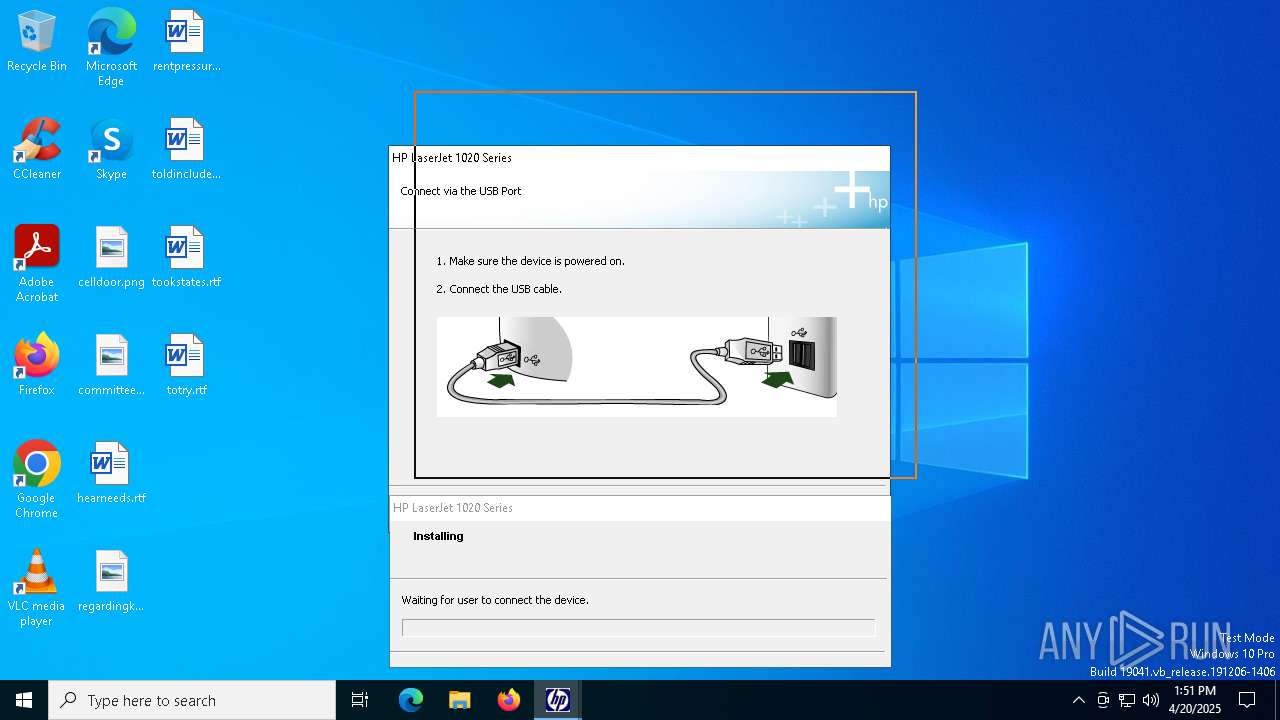
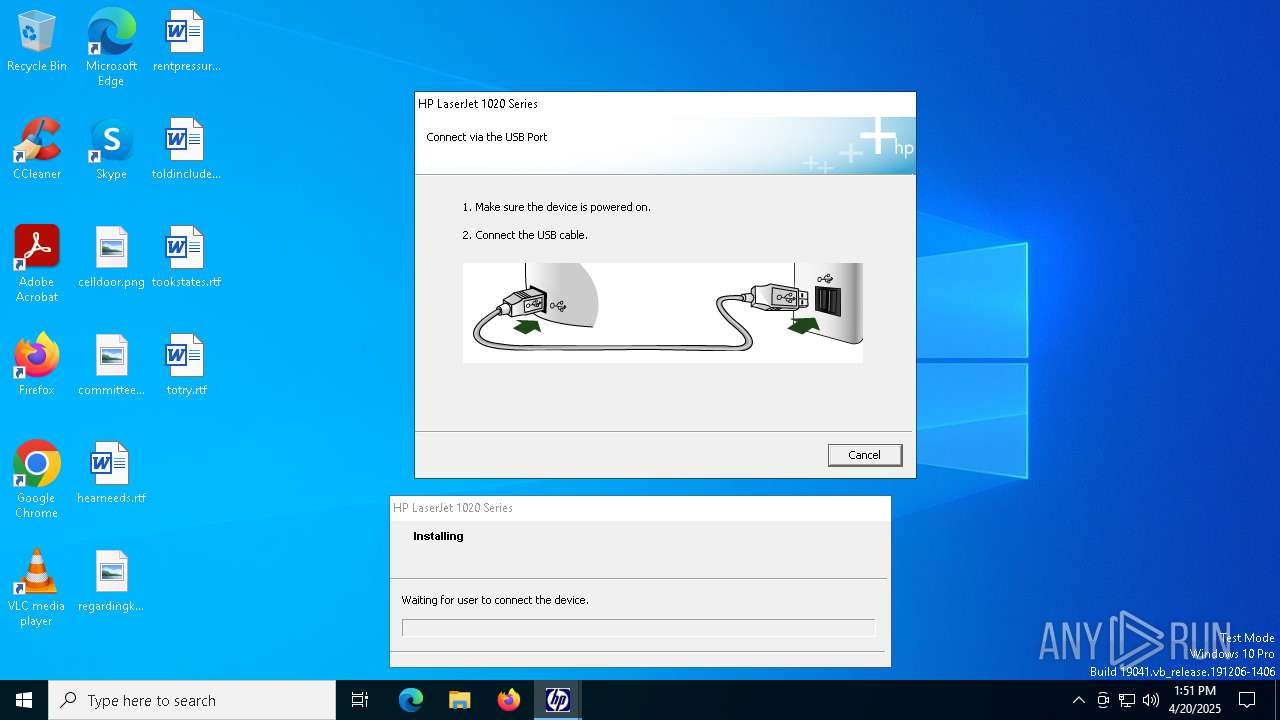
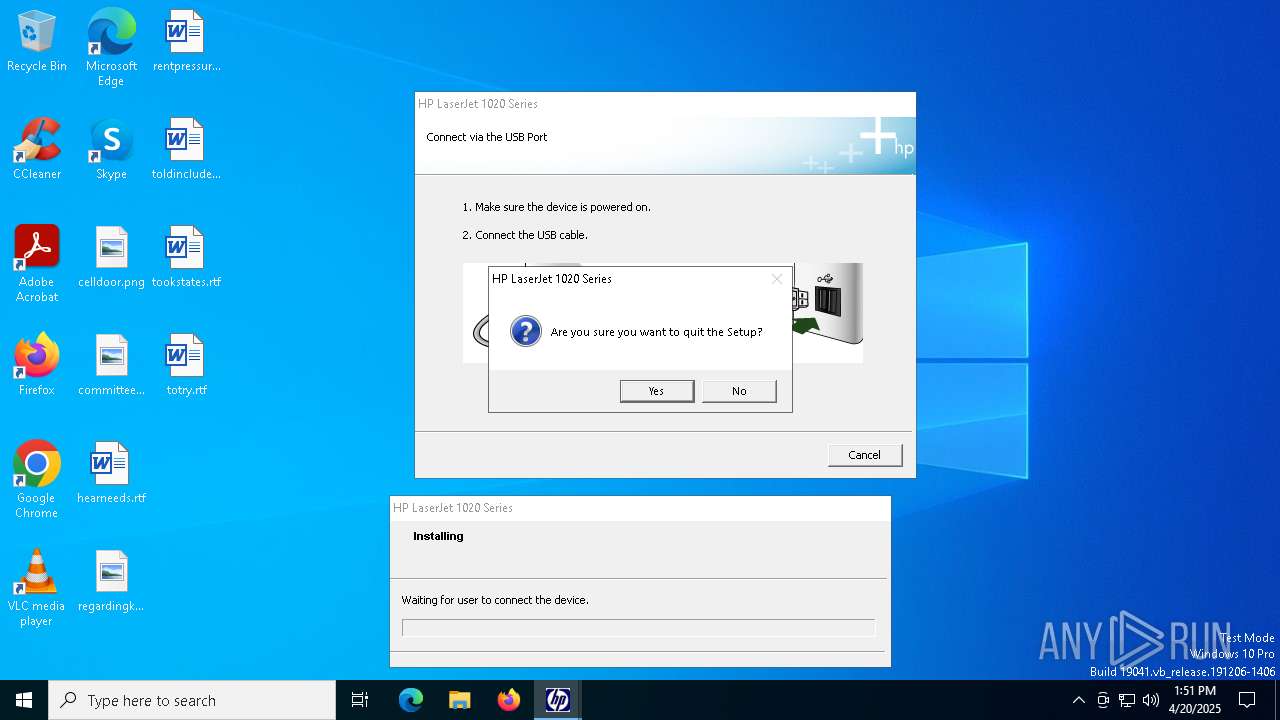
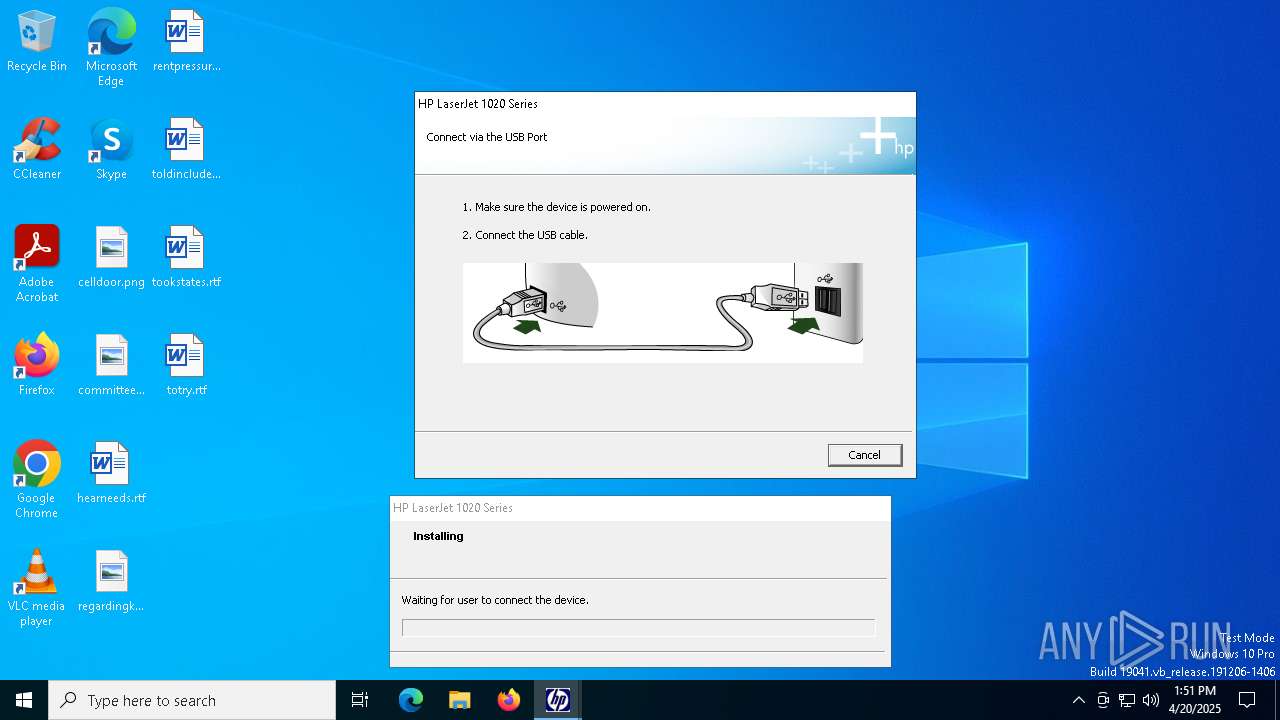
| File name: | lj1018_1020_1022-HB-pnp-win64-en.exe |
| Full analysis: | https://app.any.run/tasks/70fbb0c3-6b43-4ee1-93d8-396aea63aee0 |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2025, 13:50:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | D946E3984D48C18812169CB3D31063B2 |
| SHA1: | 3A77D33E606440E6DB4A19B61FCF491F24B0B75C |
| SHA256: | D6D4393576030F1B253316F4C6C9B7AF3B122244B0A4FCE98E3B11B11A19172D |
| SSDEEP: | 98304:Im2xwZtHAbjBJ2f3vbfZbSJbVXD4n6XFbUrULobe1hFHJ8AotQCE3DsxOw2KpCK2:/uKgkjR |
MALICIOUS
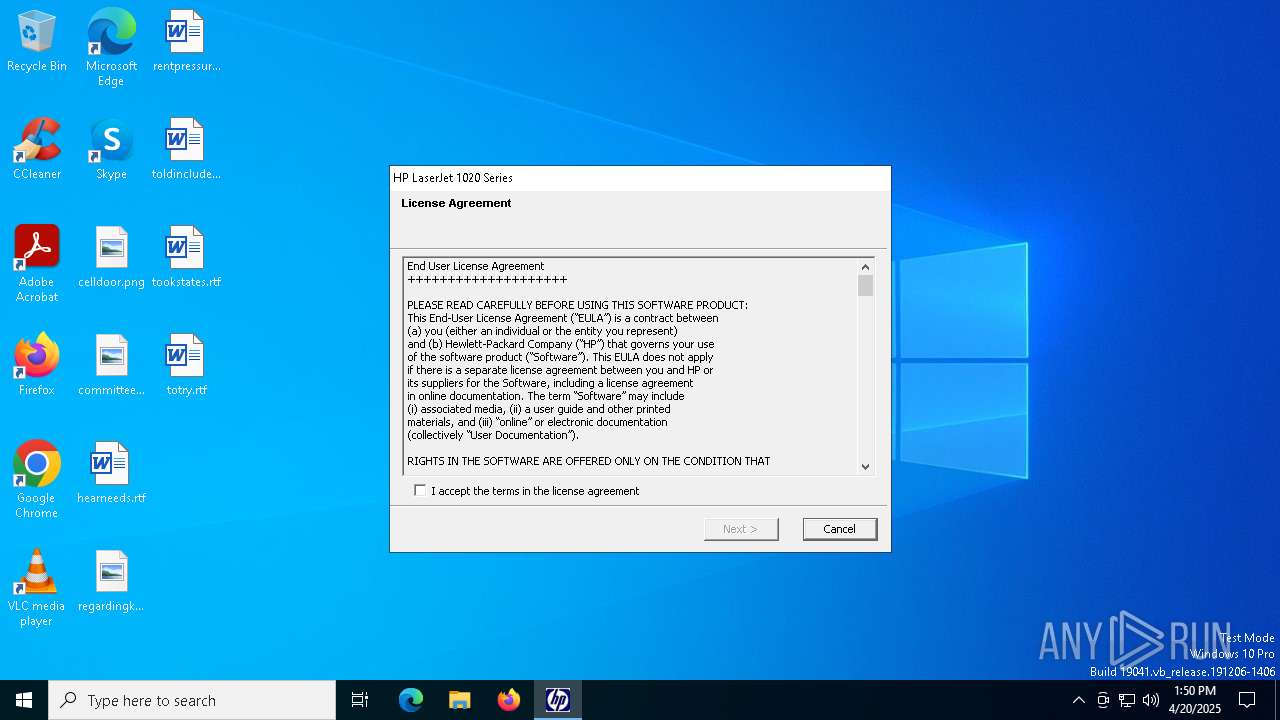
Executing a file with an untrusted certificate
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 1532)
SUSPICIOUS
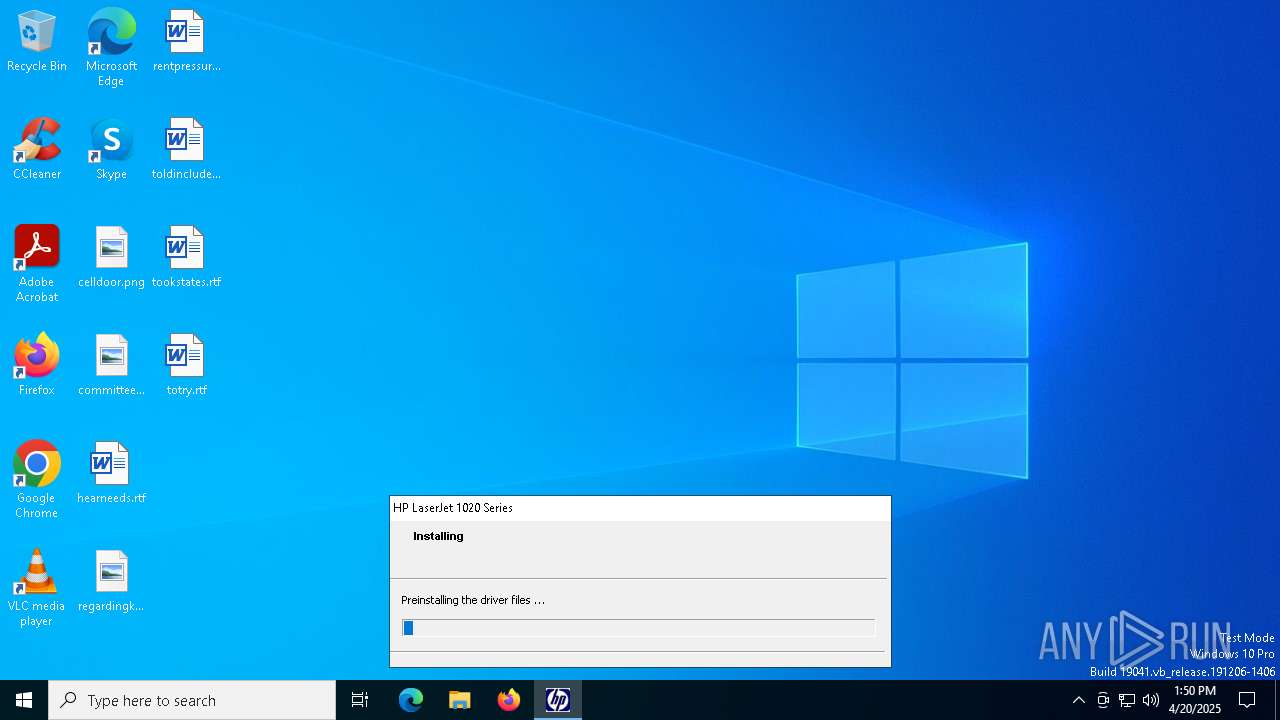
Process drops legitimate windows executable
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 7184)
- ProductInst.exe (PID: 7268)
Executable content was dropped or overwritten
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 7184)
- ProductInst.exe (PID: 7268)
- drvinst.exe (PID: 7880)
Creates file in the systems drive root
- ProductInst.exe (PID: 7268)
Creates files in the driver directory
- drvinst.exe (PID: 7880)
There is functionality for taking screenshot (YARA)
- ProductInst.exe (PID: 7268)
INFO
Checks supported languages
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 7184)
- ProductInst.exe (PID: 7268)
- Setup.exe (PID: 7252)
- msiexec.exe (PID: 7744)
- drvinst.exe (PID: 7880)
The sample compiled with english language support
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 7184)
- ProductInst.exe (PID: 7268)
- drvinst.exe (PID: 7880)
Reads the computer name
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 7184)
- ProductInst.exe (PID: 7268)
- msiexec.exe (PID: 7744)
- drvinst.exe (PID: 7880)
Create files in a temporary directory
- lj1018_1020_1022-HB-pnp-win64-en.exe (PID: 7184)
- ProductInst.exe (PID: 7268)
Creates files in the program directory
- ProductInst.exe (PID: 7268)
Reads the machine GUID from the registry
- drvinst.exe (PID: 7880)
Reads the software policy settings
- drvinst.exe (PID: 7880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:04:14 01:03:15+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 269312 |
| InitializedDataSize: | 94208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x242e5 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Hewlett-Packard Company |
| FileDescription: | HP Webpack |
| FileVersion: | 1 |
| InternalName: | 7zS.sfx |
| LegalCopyright: | Hewlett-Packard Company |
| OriginalFileName: | 7zS.sfx |
| ProductName: | HP Webpack |
| ProductVersion: | 1 |
Total processes
138
Monitored processes
8
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1532 | "C:\Users\admin\AppData\Local\Temp\lj1018_1020_1022-HB-pnp-win64-en.exe" | C:\Users\admin\AppData\Local\Temp\lj1018_1020_1022-HB-pnp-win64-en.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7184 | "C:\Users\admin\AppData\Local\Temp\lj1018_1020_1022-HB-pnp-win64-en.exe" | C:\Users\admin\AppData\Local\Temp\lj1018_1020_1022-HB-pnp-win64-en.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7252 | .\Setup.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\Setup.exe | — | lj1018_1020_1022-HB-pnp-win64-en.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7268 | "C:\Users\admin\AppData\Local\Temp\7zS19F7\ProductInst.exe" PRODUCTI | C:\Users\admin\AppData\Local\Temp\7zS19F7\ProductInst.exe | Setup.exe | ||||||||||||
User: admin Company: Marvell Integrity Level: HIGH Description: Printer Software Installer Exit code: 0 Version: 1.0.5.3 Modules
| |||||||||||||||
| 7304 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7744 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7880 | DrvInst.exe "4" "20" "C:\Users\admin\AppData\Local\Temp\{96fbbe02-05f1-b840-9276-78b5bf11fbb6}\HPLJ1020.INF" "9" "4431a86d7" "00000000000001C8" "WinSta0\Default" "00000000000001CC" "208" "C:\Users\admin\AppData\Local\Temp\7zS19F7" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 414
Read events
3 397
Write events
17
Delete events
0
Modification events
| (PID) Process: | (7252) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Hewlett-Packard\PRODUCTSetup |
| Operation: | write | Name: | PPN |
Value: lj1018_1020_1022-HB-pnp-win64-en.exe | |||
| (PID) Process: | (7252) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Hewlett-Packard\PRODUCTSetup |
| Operation: | write | Name: | SetupIP |
Value: 1020.1022 | |||
| (PID) Process: | (7268) ProductInst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Descriptors\USBPRINT\Hewlett-Packardhp_La26DD |
| Operation: | write | Name: | Configuration |
Value: LJ1020.NTamd64 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Configurations\LJ1020.NTamd64 |
| Operation: | write | Name: | DriverDate |
Value: 0040CC8B3095CD01 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Configurations\LJ1020.NTamd64 |
| Operation: | write | Name: | DriverVersion |
Value: 7CE201009603DC07 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Descriptors\Hewlett-Packardhp_La26DD |
| Operation: | write | Name: | Configuration |
Value: LJ1020.NTamd64 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Descriptors\USBPRINT\Hewlett-Packardhp_LaE75C |
| Operation: | write | Name: | Configuration |
Value: LJ1020.NTamd64 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Descriptors\Hewlett-Packardhp_LaE75C |
| Operation: | write | Name: | Configuration |
Value: LJ1020.NTamd64 | |||
| (PID) Process: | (7880) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\hplj1020.inf_amd64_5ffa82d4dfa98331\Descriptors\USBPRINT\Hewlett-Packardhp_LaD566 |
| Operation: | write | Name: | Configuration |
Value: LJ1020.NTamd64 | |||
Executable files
62
Suspicious files
87
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\hp1018.img | binary | |
MD5:92AD60ED96583F868736DE7BD3C2C157 | SHA256:9D10D8E84A9577F268AAC6336ED18CF9235E6F732C1F68E8913C787DB60106CE | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\hp1020.img | binary | |
MD5:4175DD1F8B1DEAF28C3079067DDA1FBD | SHA256:375721050EA60DE50CD56A2C7B80C34F913C7AF336372C93B98ED42D30CB20D9 | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\properties.ini | text | |
MD5:69C38FFDD841DE462C820EEEEAB1392A | SHA256:D09F837F43190FD197BB5C53866A55BB521B57533017D6482F04FF35734536DA | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\English\SDhp1020.chm | binary | |
MD5:EC5CA899B688D5BAAE797E2405C9DC91 | SHA256:3594E3BDAAA541825D2AD0193C97FA9BD970948DC7EB38616337B2AA638BF9CA | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\License7z.txt | text | |
MD5:1AFF779C3F376C276E0C382BEB803851 | SHA256:264BE4477E3A7589CE4114DAFA3AEF8EE91C9CC862AC2AA397C70875136C778A | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\English\ZShp1018.chm | binary | |
MD5:295BE7B1F6CB4998189233F289FB01F5 | SHA256:274E851A691BD50C0CC039C01E79A515CF4451B4312B17DDE5F46C4302D2A081 | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\hp102032.cat | binary | |
MD5:C249F42DC693893F1C89F740424AD1C0 | SHA256:575F27645BAEC48C7BC109ED65B2A6EF5BD21B9937F22778D9BD62185DDBE72A | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\hp1022n.img | binary | |
MD5:2999FF547F0B8D90F7D5C7EA5038AF63 | SHA256:4B0443460508914E1C0287821E768913A77DCA15D38FA82A8DA2E36EC7E08DDB | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\license.txt | binary | |
MD5:54972C3C1C50C5BDD69B34A35E84E1EC | SHA256:4DF8CA259FC14160A0CA9AAF2C6278F352BB460F4A04785866FFAA349C6F5F86 | |||
| 7184 | lj1018_1020_1022-HB-pnp-win64-en.exe | C:\Users\admin\AppData\Local\Temp\7zS19F7\English\SUhp1020.ent | xml | |
MD5:0E0C1D80FDB397C16E272AAFB9F9434B | SHA256:4FBFD5284D25FE64601F3822E44AFA6A544C8C1FACD43236E7B6529BF9E5C96C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8060 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8060 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8060 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |