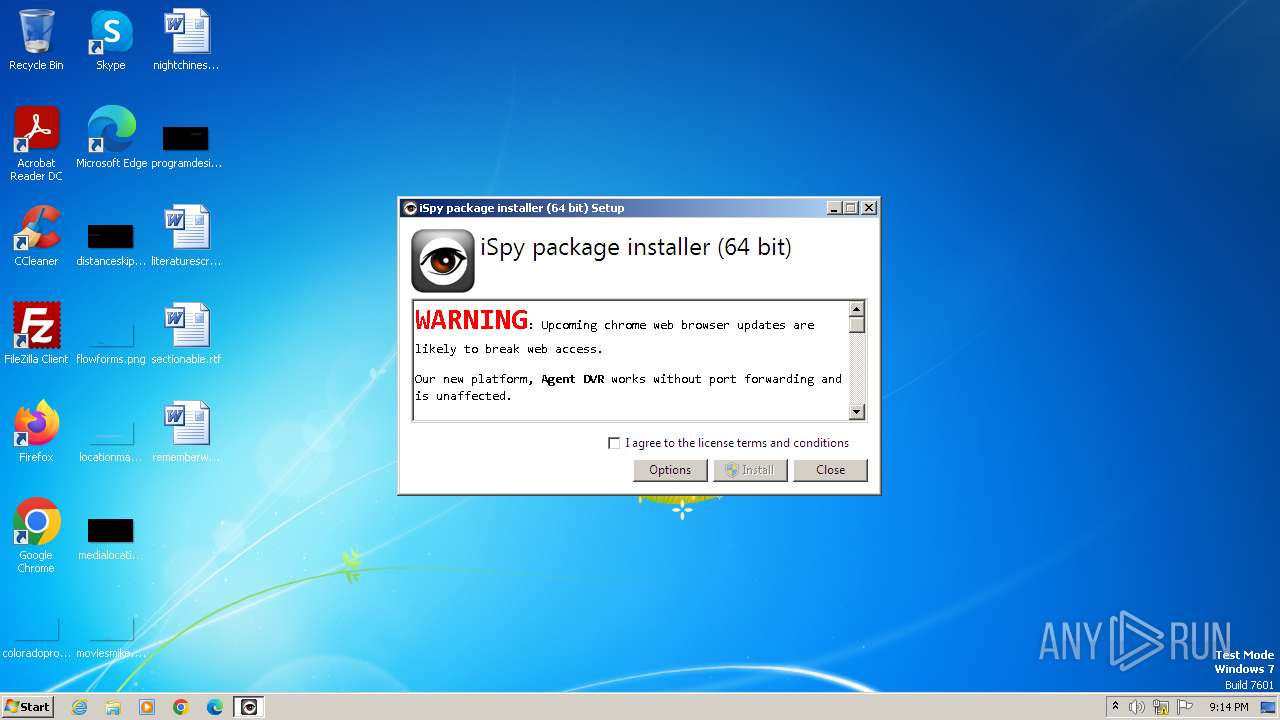
| File name: | engine.exe |
| Full analysis: | https://app.any.run/tasks/3ec949fc-2c1d-479f-bb9d-85c789b0c1c2 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2023, 21:14:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E7E548D0217FF8F35648F824DB9F0204 |
| SHA1: | 10503909D592C3131700CCC913CD8F862FAFDD34 |
| SHA256: | D6C85BC3403DC805A29E5A71A69A03B308A55F98A78C0830D8EDE4D57CD2117B |
| SSDEEP: | 24576:eLN9pggkHLWqnivnuhHqaEVYS8vpBMOIdHL3:eLN9SgkHLWqnivnuhHqvVYS8xBMOIdHT |
MALICIOUS
Drops the executable file immediately after the start
- engine.exe (PID: 2168)
- engine.exe (PID: 3024)
- iSpySetup.exe (PID: 1448)
SUSPICIOUS
Searches for installed software
- engine.exe (PID: 3024)
- iSpySetup.exe (PID: 1448)
Starts itself from another location
- engine.exe (PID: 2168)
- engine.exe (PID: 3024)
Reads the Internet Settings
- engine.exe (PID: 3024)
Executes as Windows Service
- VSSVC.exe (PID: 2776)
INFO
Checks supported languages
- engine.exe (PID: 2168)
- engine.exe (PID: 3024)
- iSpySetup.exe (PID: 1448)
Create files in a temporary directory
- engine.exe (PID: 2168)
- engine.exe (PID: 3024)
Reads the computer name
- engine.exe (PID: 3024)
- iSpySetup.exe (PID: 1448)
Reads the machine GUID from the registry
- engine.exe (PID: 3024)
- iSpySetup.exe (PID: 1448)
Creates files in the program directory
- iSpySetup.exe (PID: 1448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:09:17 07:33:38+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 299008 |
| InitializedDataSize: | 189952 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2df71 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.2.6.0 |
| ProductVersionNumber: | 7.2.6.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | DeveloperInABox |
| FileDescription: | iSpy package installer (64 bit) |
| FileVersion: | 7.2.6.0 |
| InternalName: | setup |
| LegalCopyright: | Copyright© 2020, DeveloperInABox |
| OriginalFileName: | iSpySetup.exe |
| ProductName: | iSpy package installer (64 bit) |
| ProductVersion: | 7.2.6.0 |
Total processes
43
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | "C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.be\iSpySetup.exe" -q -burn.elevated BurnPipe.{03499AB4-9692-4151-A30A-6E23E595CFC3} {CD013AA0-9F11-4C7D-8068-A0D1DC854ED8} 3024 | C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.be\iSpySetup.exe | engine.exe | ||||||||||||
User: admin Company: DeveloperInABox Integrity Level: HIGH Description: iSpy package installer (64 bit) Exit code: 1 Version: 7.2.6.0 Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\AppData\Local\Temp\engine.exe" | C:\Users\admin\AppData\Local\Temp\engine.exe | — | explorer.exe | |||||||||||
User: admin Company: DeveloperInABox Integrity Level: MEDIUM Description: iSpy package installer (64 bit) Exit code: 1 Version: 7.2.6.0 Modules
| |||||||||||||||
| 2776 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3024 | "C:\Users\admin\AppData\Local\Temp\{110AAB55-6073-4002-B6D0-548E10003097}\.cr\engine.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\engine.exe" -burn.filehandle.attached=152 -burn.filehandle.self=160 | C:\Users\admin\AppData\Local\Temp\{110AAB55-6073-4002-B6D0-548E10003097}\.cr\engine.exe | — | engine.exe | |||||||||||
User: admin Company: DeveloperInABox Integrity Level: MEDIUM Description: iSpy package installer (64 bit) Exit code: 1 Version: 7.2.6.0 Modules
| |||||||||||||||
Total events
1 700
Read events
1 676
Write events
19
Delete events
5
Modification events
| (PID) Process: | (3024) engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3024) engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3024) engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3024) engine.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1448) iSpySetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1448) iSpySetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1448) iSpySetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (1448) iSpySetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1448) iSpySetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1448) iSpySetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
5
Suspicious files
3
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1448 | iSpySetup.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1448 | iSpySetup.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{e9ba5903-554b-46e0-a2e5-fe3b1136a606}_OnDiskSnapshotProp | binary | |
MD5:494717FD4FAFF49E3F8BD8FEE5B3DEBF | SHA256:2FB1F03D45621C2BF87FB1CDF2CBF6733A2564E2E5A9BA9457FEBE3524FD2CE9 | |||
| 3024 | engine.exe | C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.be\iSpySetup.exe | executable | |
MD5:E7E548D0217FF8F35648F824DB9F0204 | SHA256:D6C85BC3403DC805A29E5A71A69A03B308A55F98A78C0830D8EDE4D57CD2117B | |||
| 3024 | engine.exe | C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.ba\thm.wxl | xml | |
MD5:5D492AF2E8C9B2AB58CA1A10248C726F | SHA256:ACCF0D8BFCEF21F5F80730D90705446FC0253174A484FD73B6523A092224322D | |||
| 3024 | engine.exe | C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.ba\license.rtf | text | |
MD5:CA72F690340350A22801DB23BFDE6254 | SHA256:69CB6A8F567BE4779915D279A571A634D6044A255FAB796A0B0C47AA4004A57C | |||
| 3024 | engine.exe | C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.ba\wixstdba.dll | executable | |
MD5:FE7E0BD53F52E6630473C31299A49FDD | SHA256:2BEA14D70943A42D344E09B7C9DE5562FA7E109946E1C615DD584DA30D06CC80 | |||
| 1448 | iSpySetup.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:494717FD4FAFF49E3F8BD8FEE5B3DEBF | SHA256:2FB1F03D45621C2BF87FB1CDF2CBF6733A2564E2E5A9BA9457FEBE3524FD2CE9 | |||
| 2168 | engine.exe | C:\Users\admin\AppData\Local\Temp\{110AAB55-6073-4002-B6D0-548E10003097}\.cr\engine.exe | executable | |
MD5:E7E548D0217FF8F35648F824DB9F0204 | SHA256:D6C85BC3403DC805A29E5A71A69A03B308A55F98A78C0830D8EDE4D57CD2117B | |||
| 3024 | engine.exe | C:\Users\admin\AppData\Local\Temp\{B81E068F-C920-415B-BCC6-BA3DB7718602}\.ba\BootstrapperApplicationData.xml | xml | |
MD5:40313902F9E562EC9D5E77064F991DF8 | SHA256:7BEE444D019445487690F59D24324DE33374F72C6DFCF356F2BA2221A87263FF | |||
| 1448 | iSpySetup.exe | C:\ProgramData\Package Cache\{61b26316-2f5e-4661-842c-8d0d44f8aee1}\state.rsm | smt | |
MD5:EE926E3E237FAFA04ED87CD4CAC149F6 | SHA256:283F7A51C7924E9FAF6C679E7EBC6EDB7EDBC82F6EEFC6006EBE36709E321EFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |