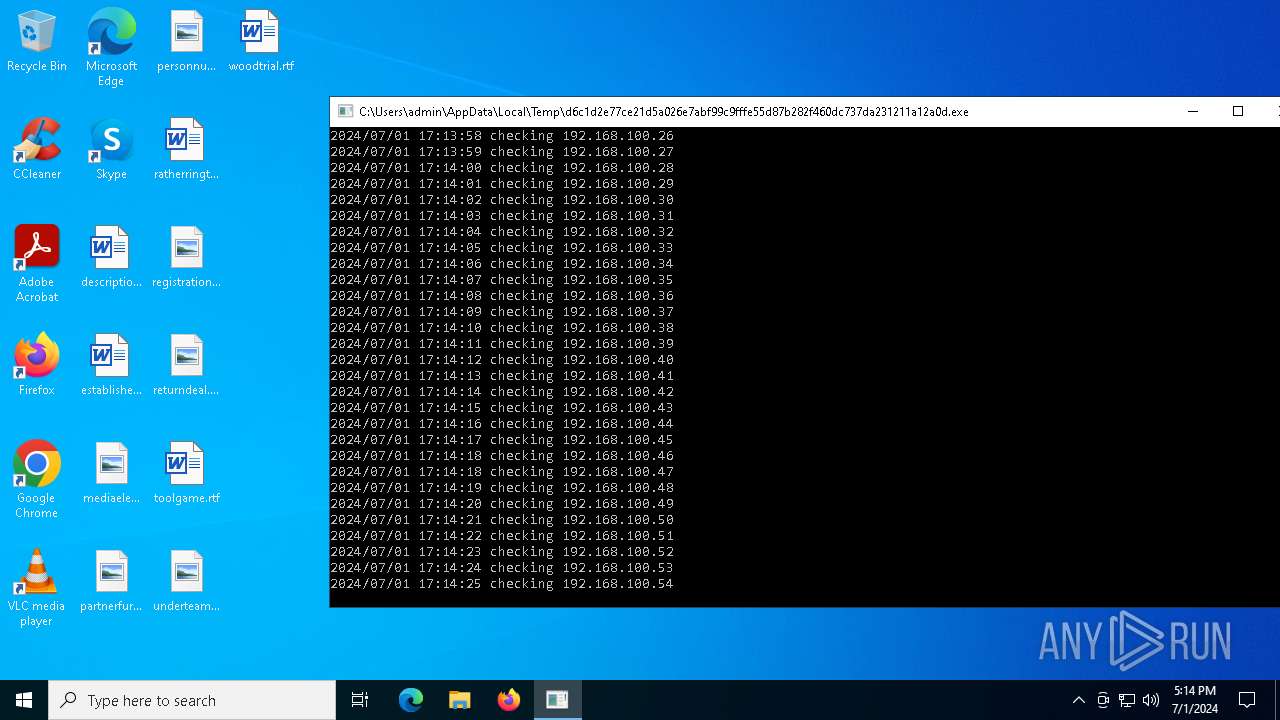
| File name: | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe |
| Full analysis: | https://app.any.run/tasks/73c34793-dcd6-4ac3-8d7a-2463bfa98d74 |
| Verdict: | Malicious activity |
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | July 01, 2024, 17:13:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 193964C937493B979B1E9649A83FF000 |
| SHA1: | D85A46B51B7CF9FE24783508E0739CCEE3CF5874 |
| SHA256: | D6C1D2E77CE21D5A026E7ABF99C9FFFE55D87B282F460DC737DA231211A12A0D |
| SSDEEP: | 49152:yE3R8uH1HeAFWCk23y/pkx9rN7Su89t9H6paP6sYqXlCPhzYuDA5juRIOmmmAig4:yE3R8u80k2imx9rN7Suer6p |
MALICIOUS
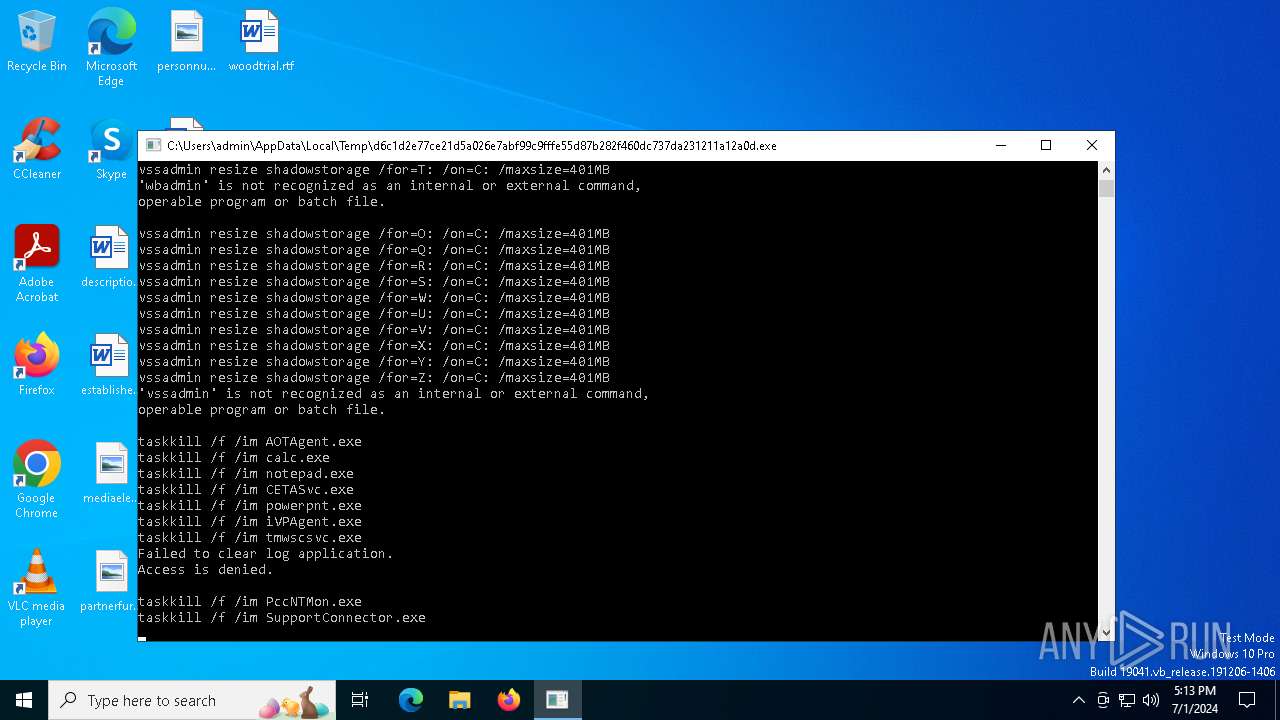
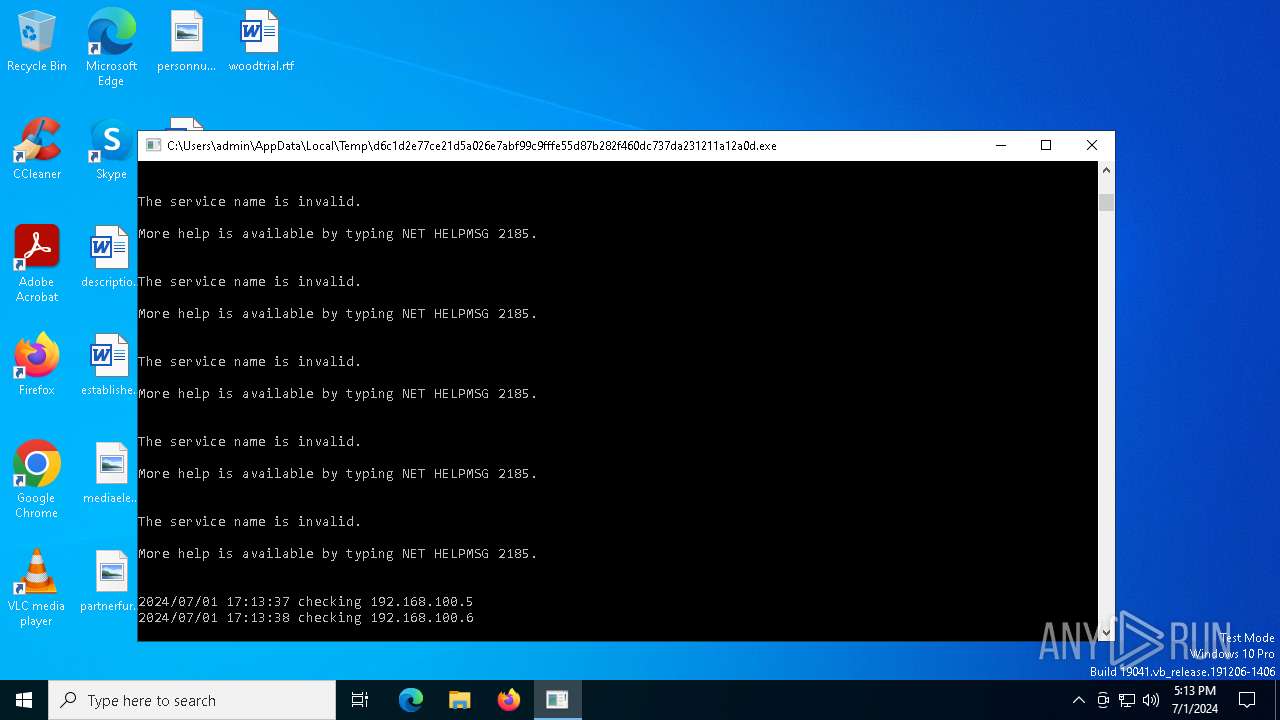
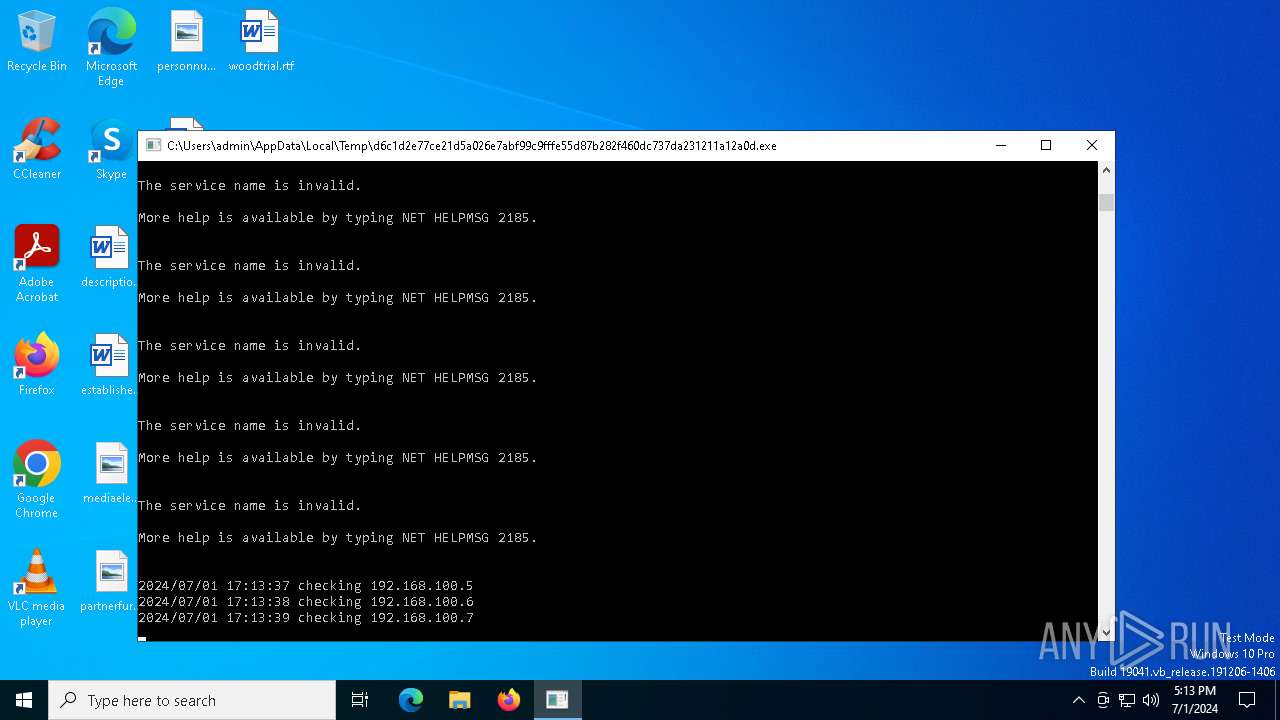
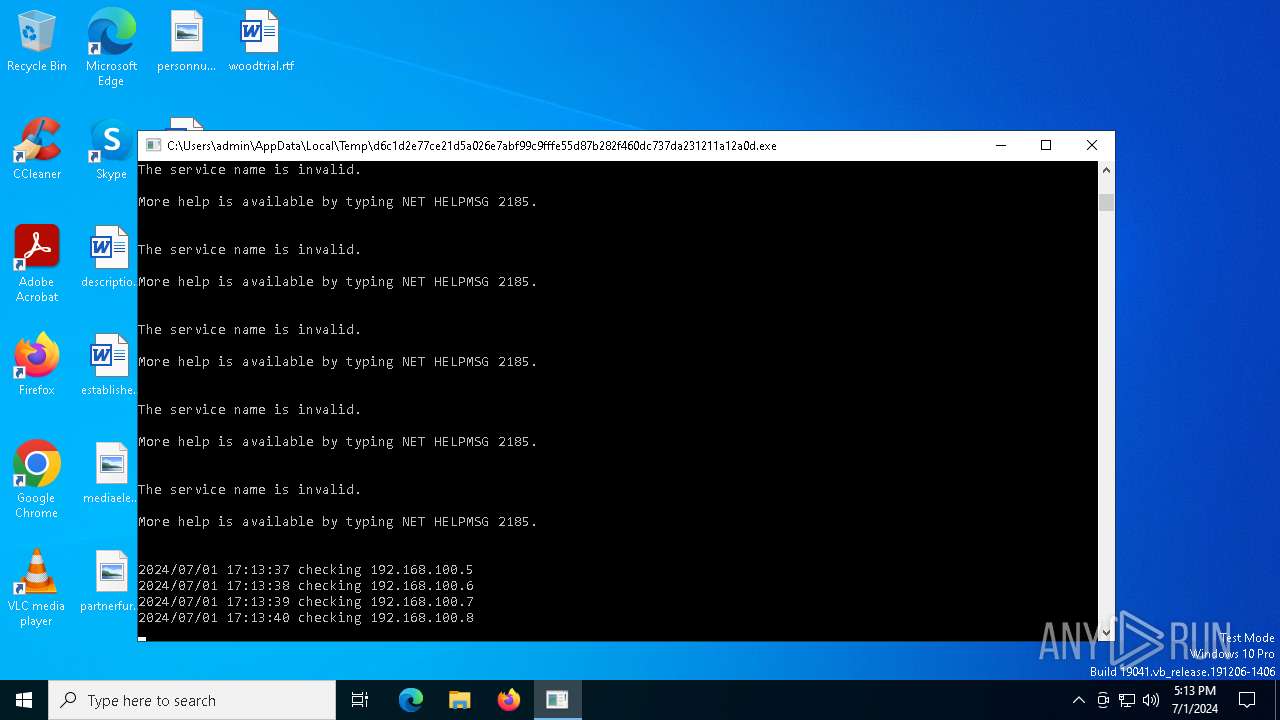
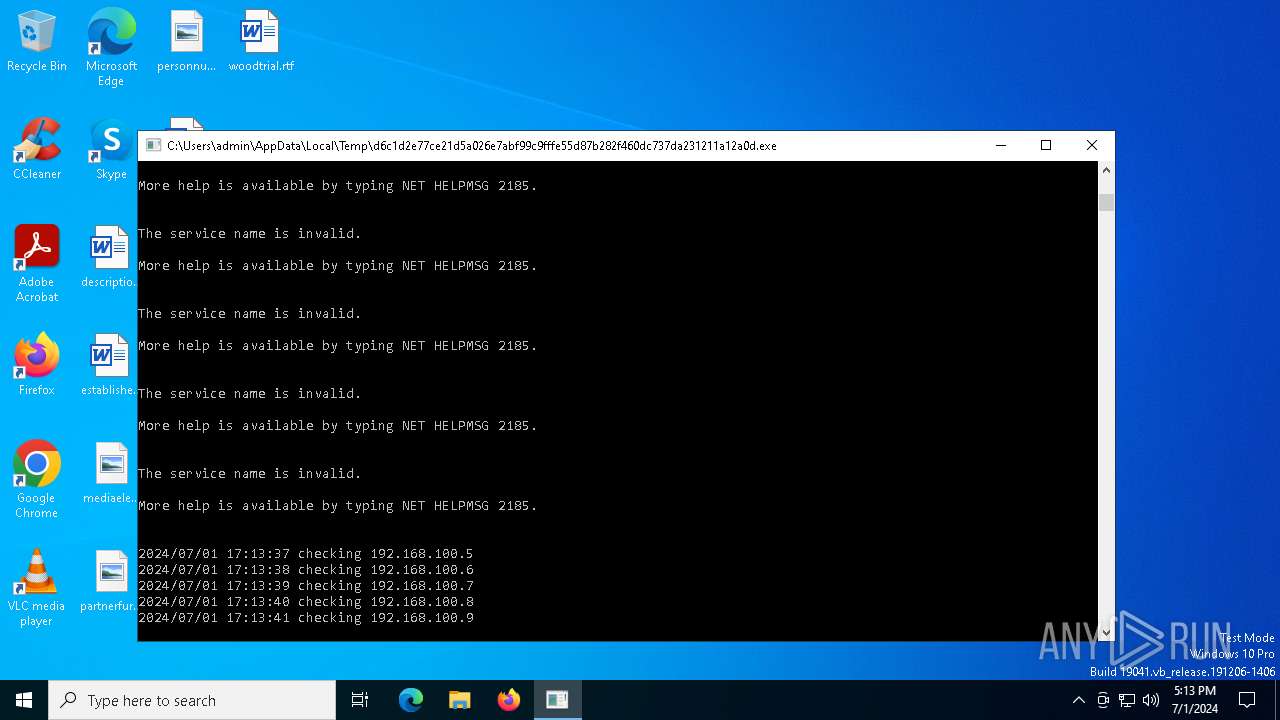
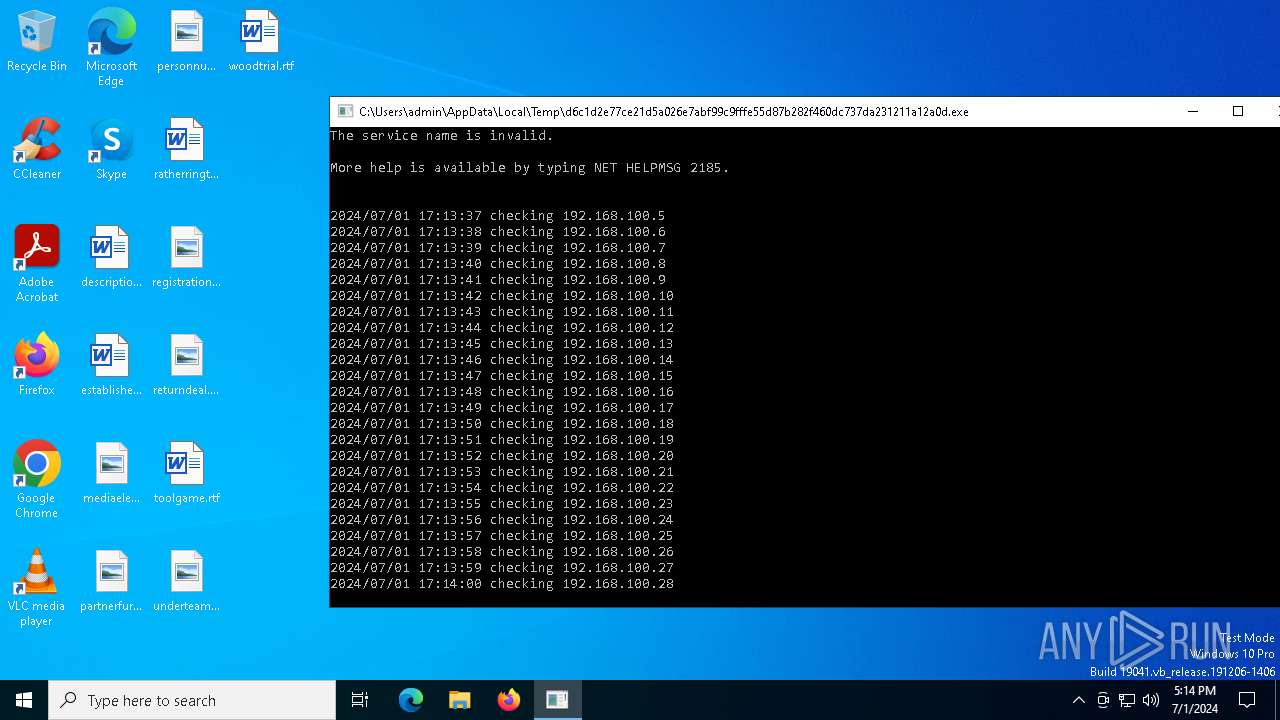
Drops the executable file immediately after the start
- d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe (PID: 900)
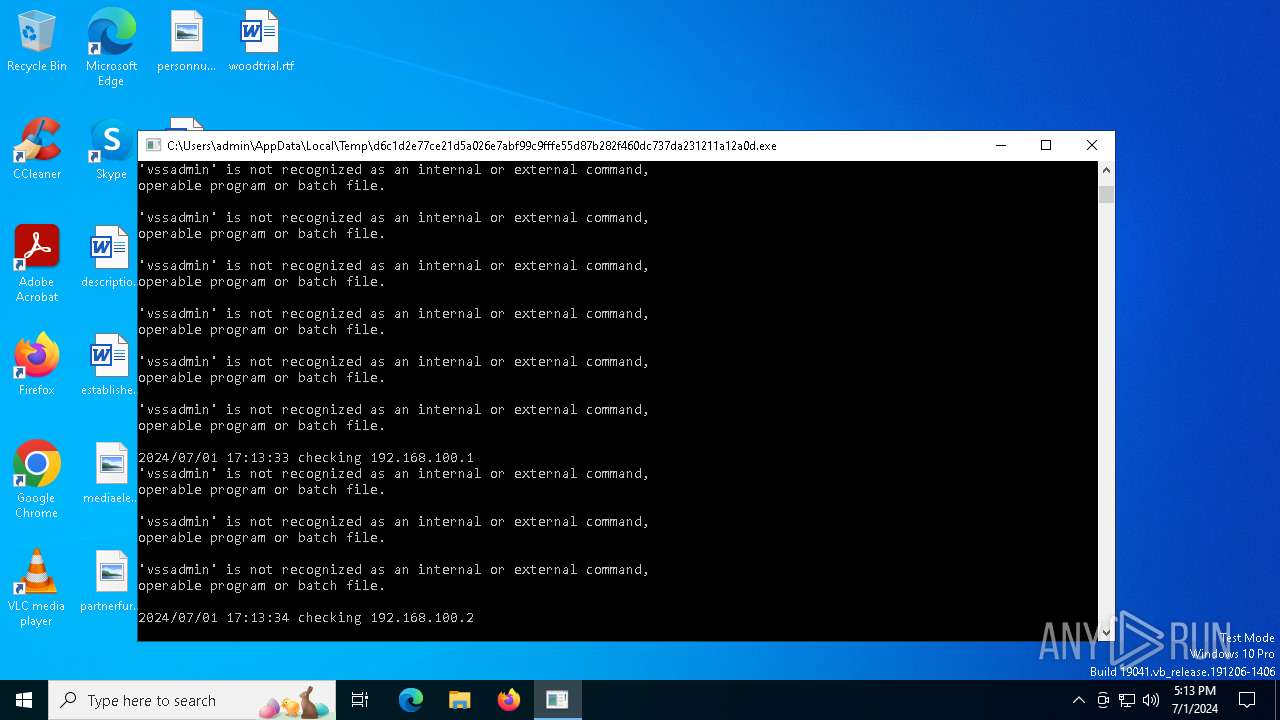
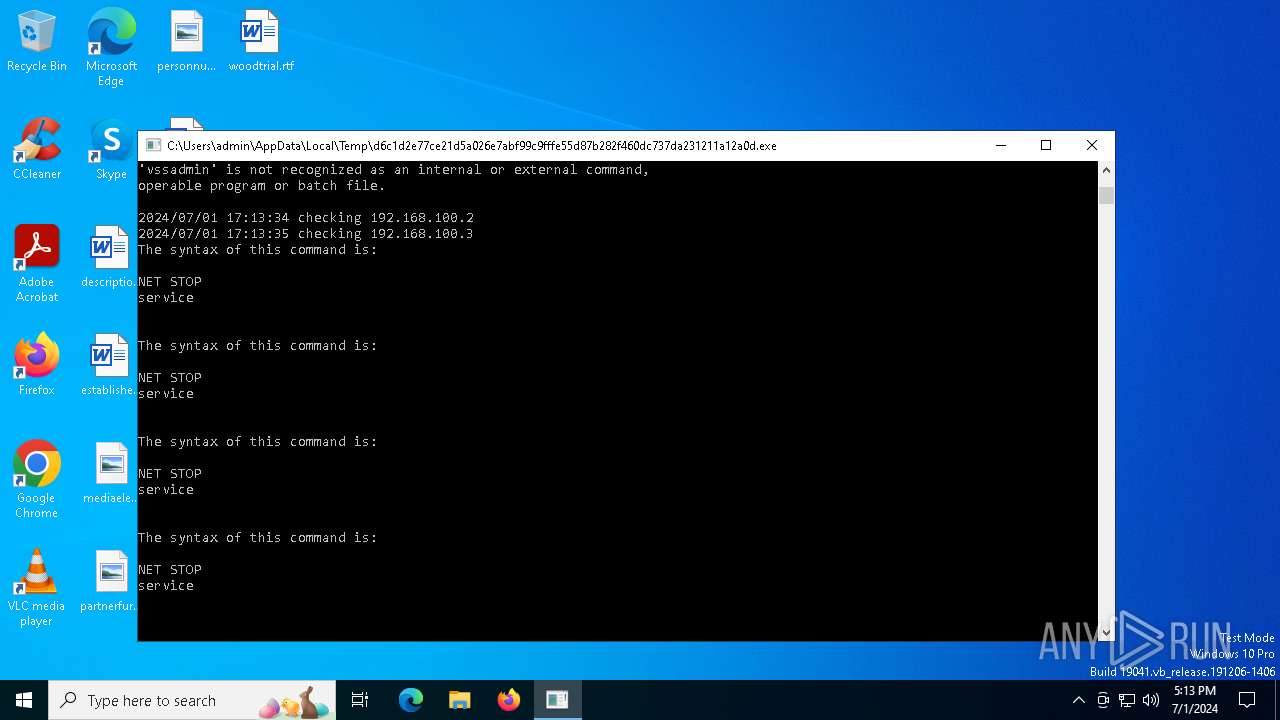
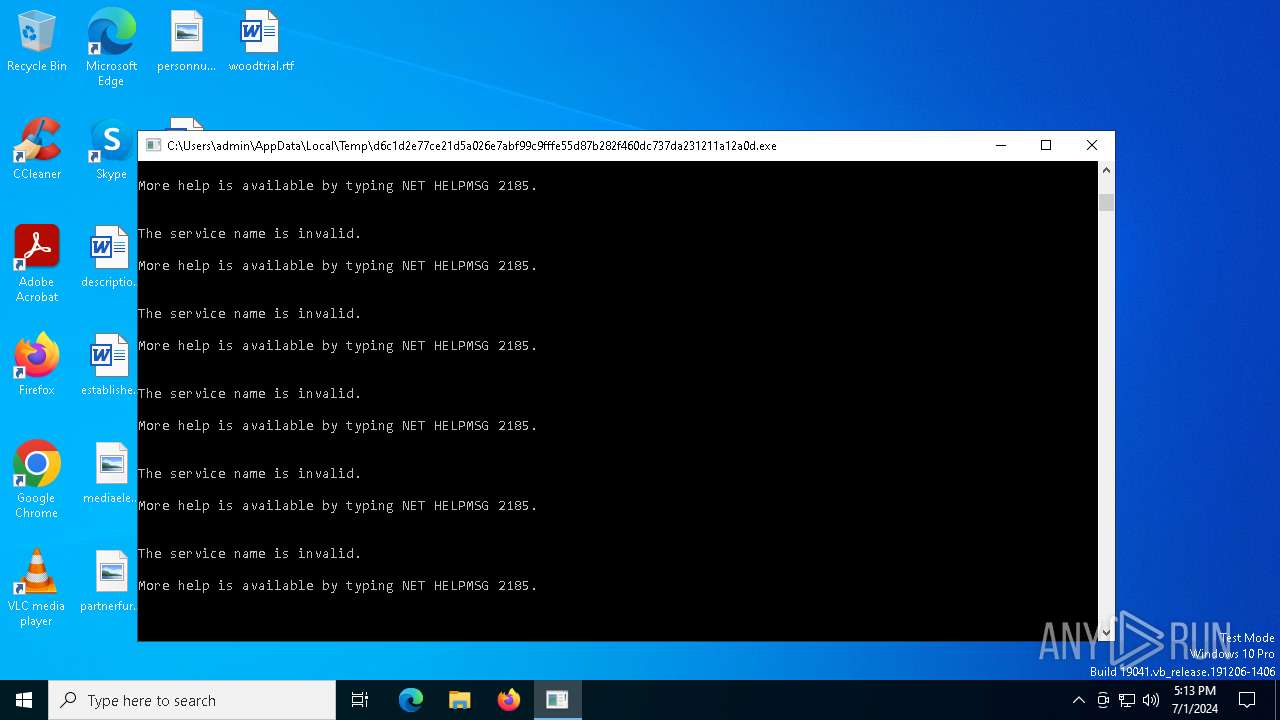
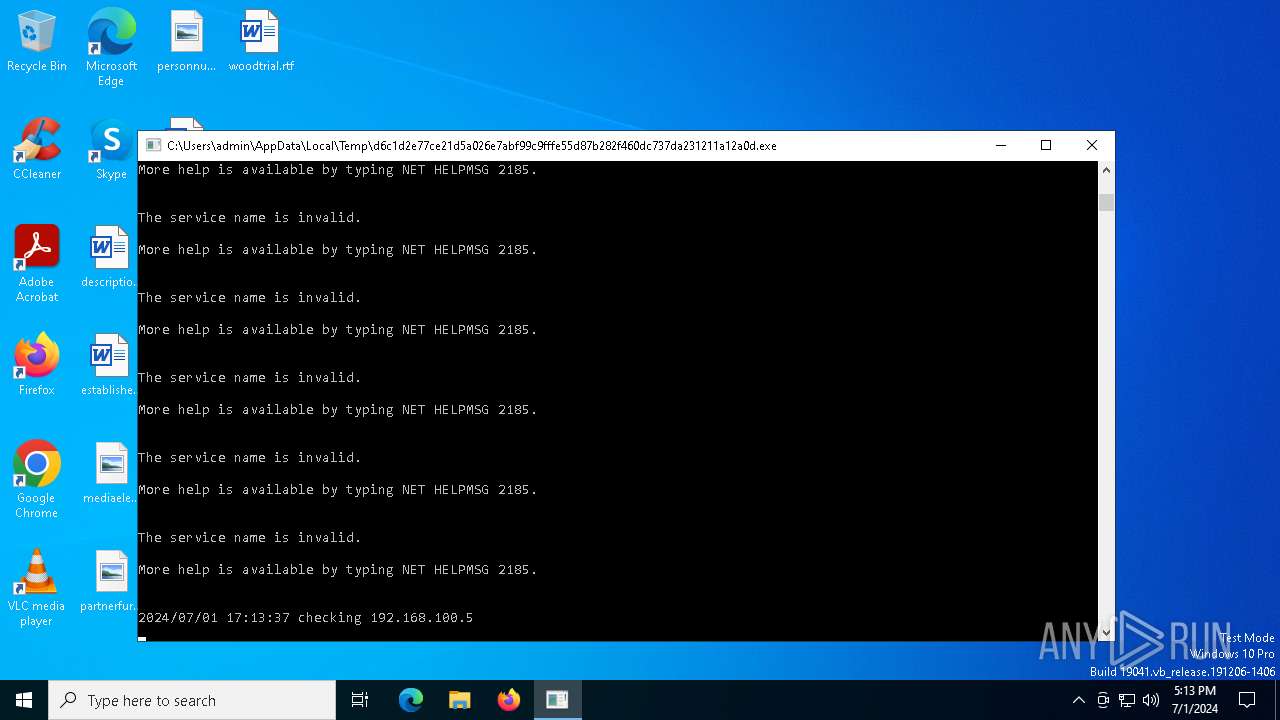
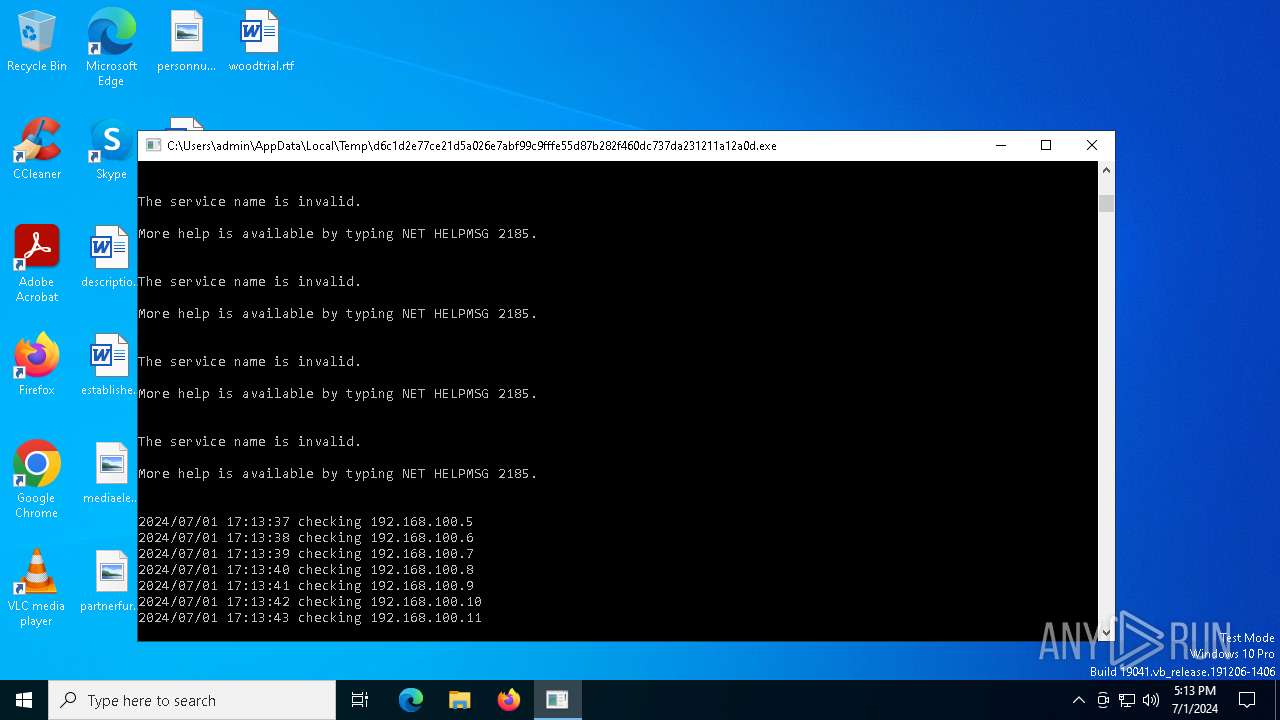
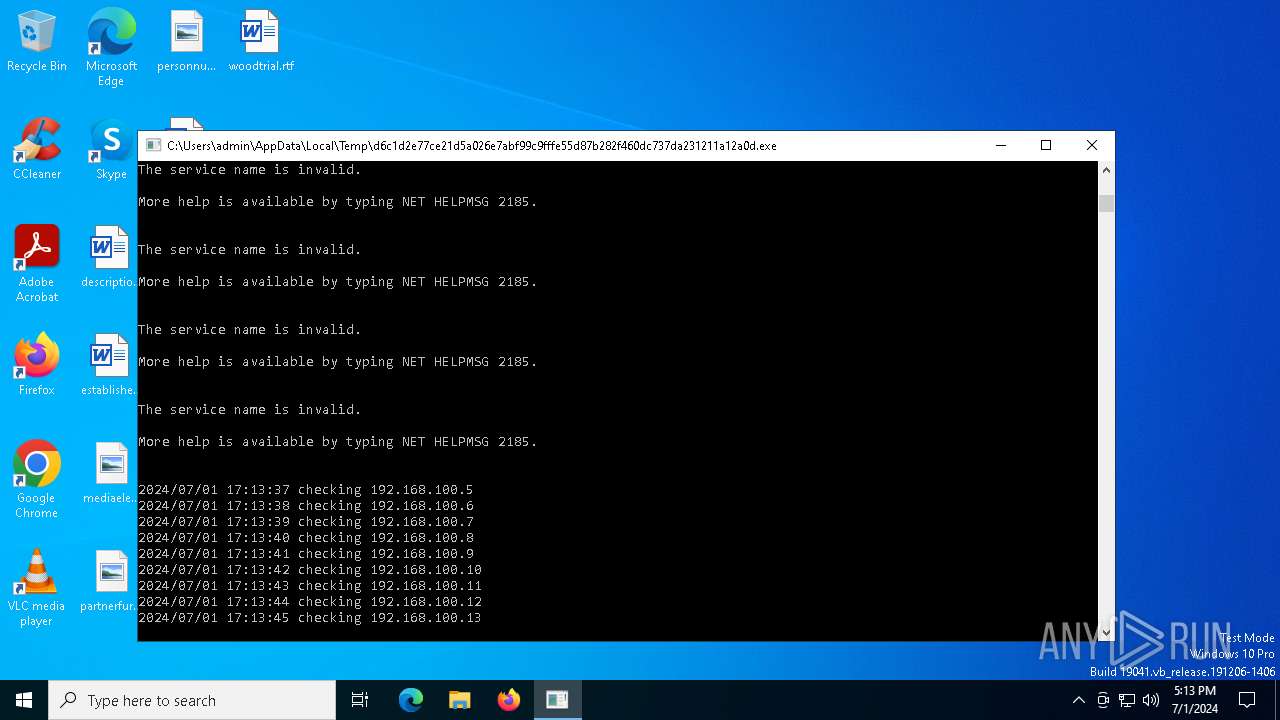
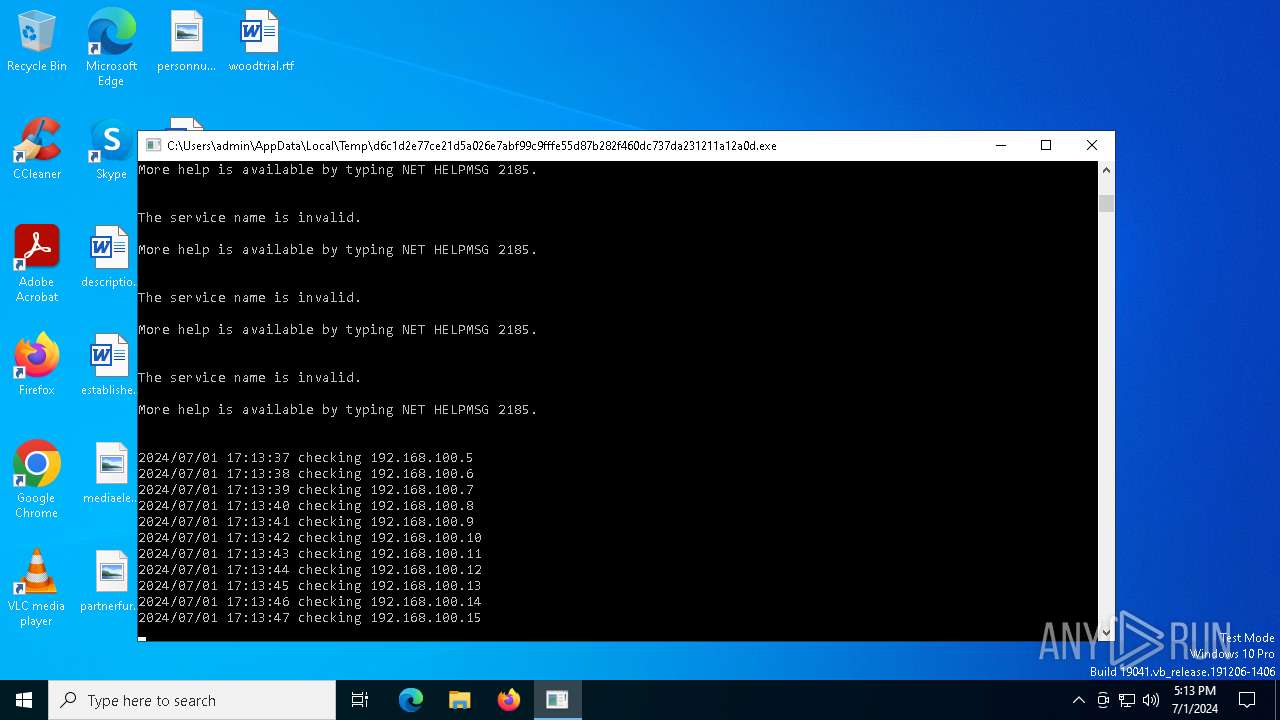
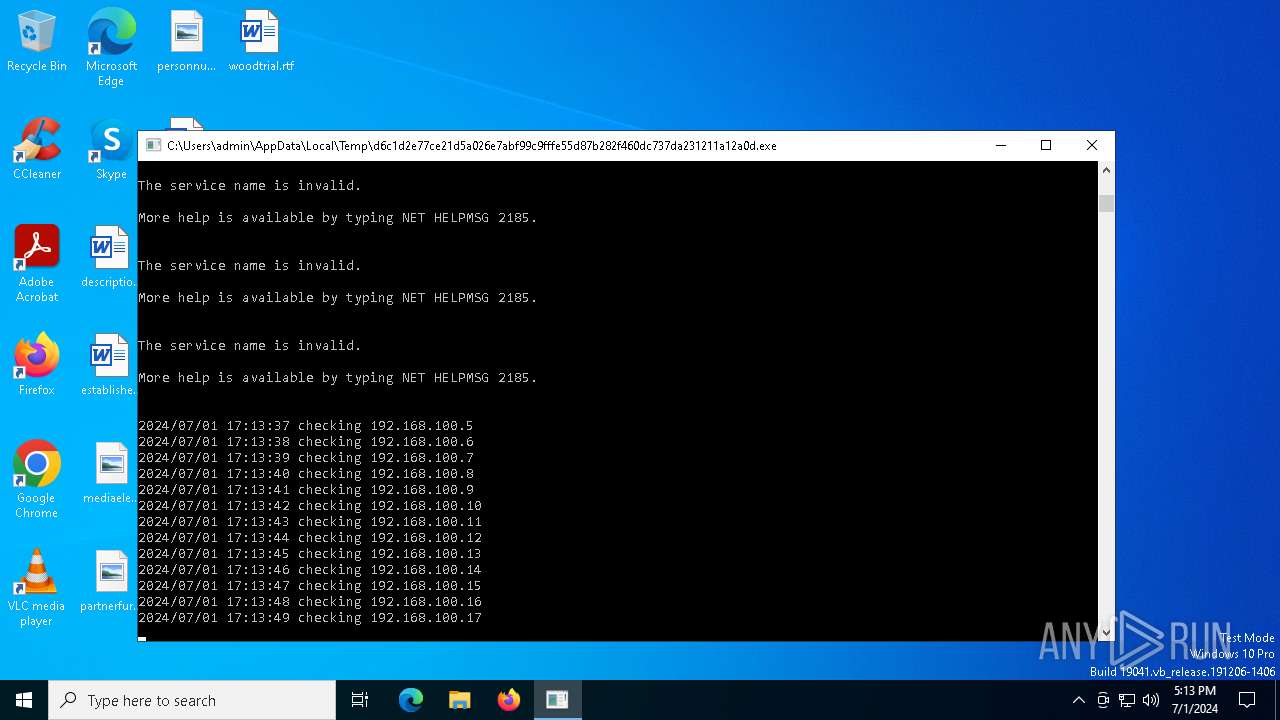
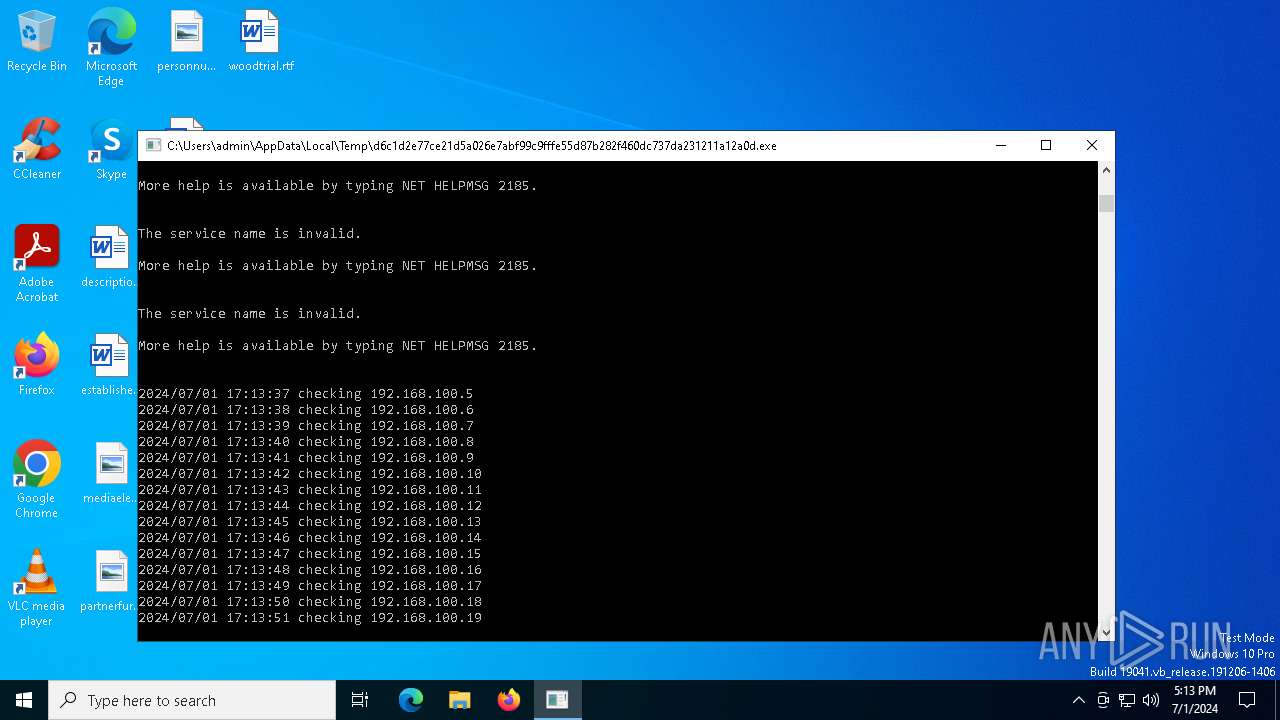
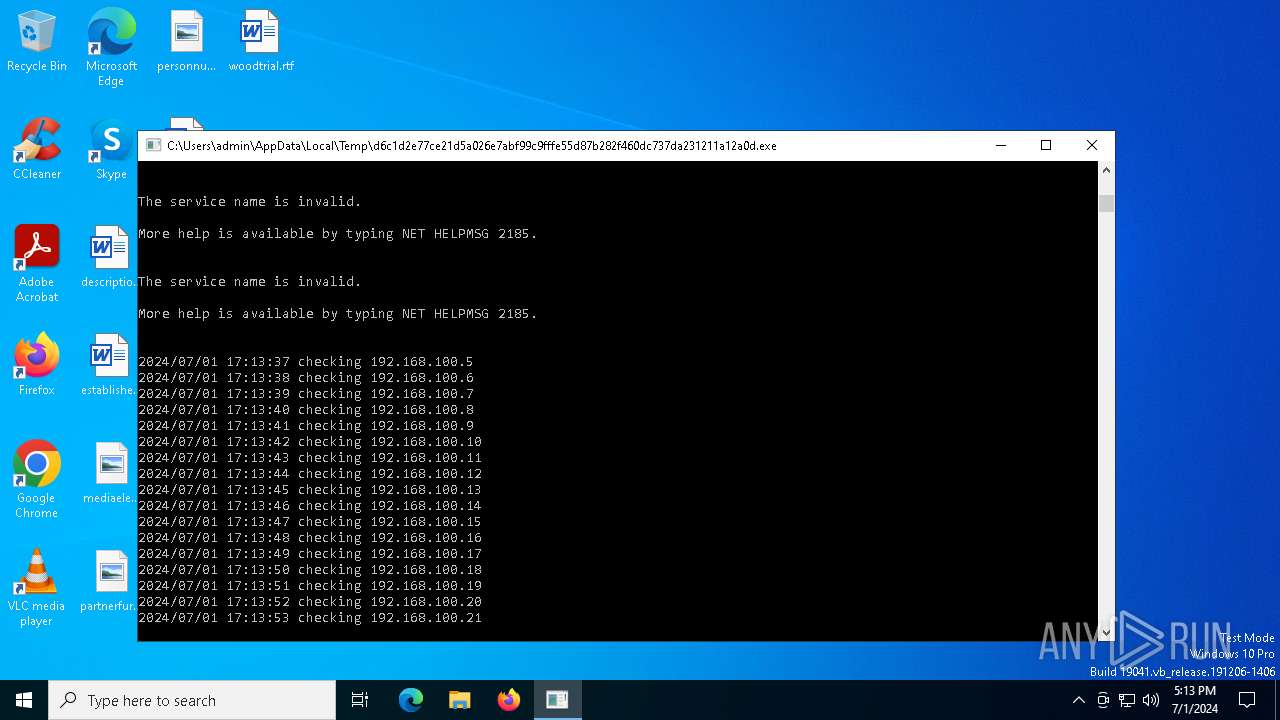
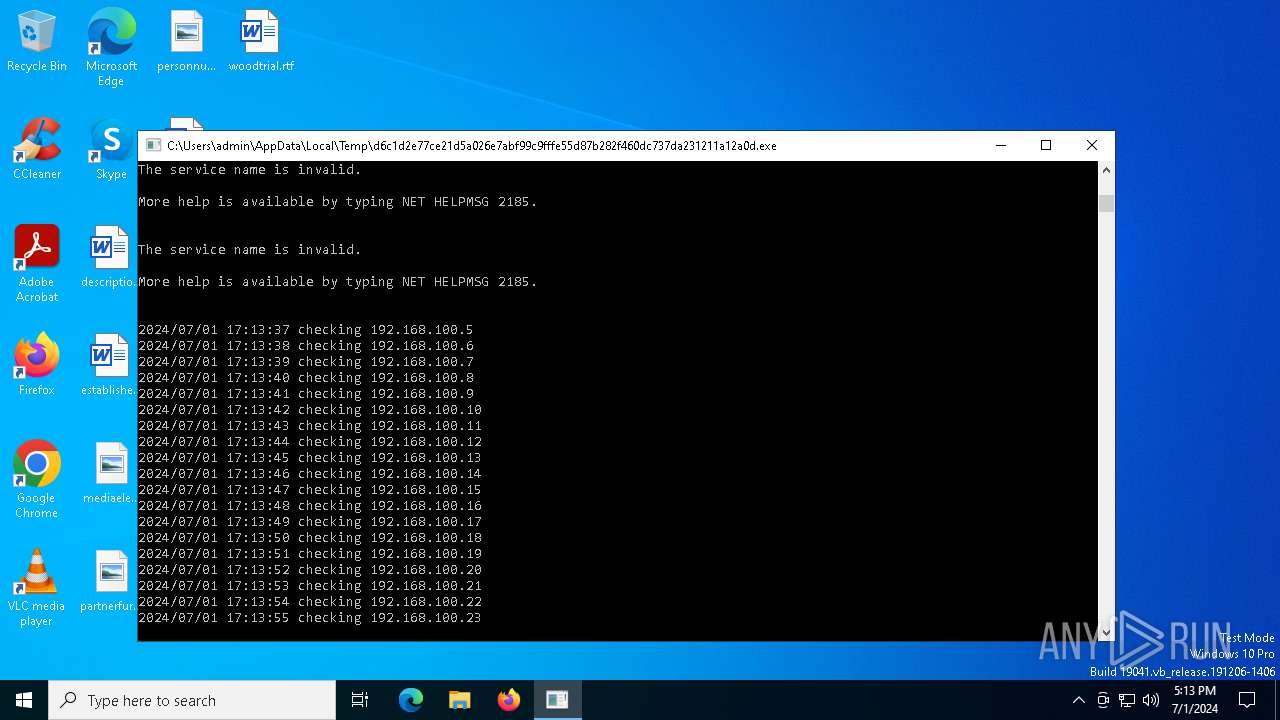
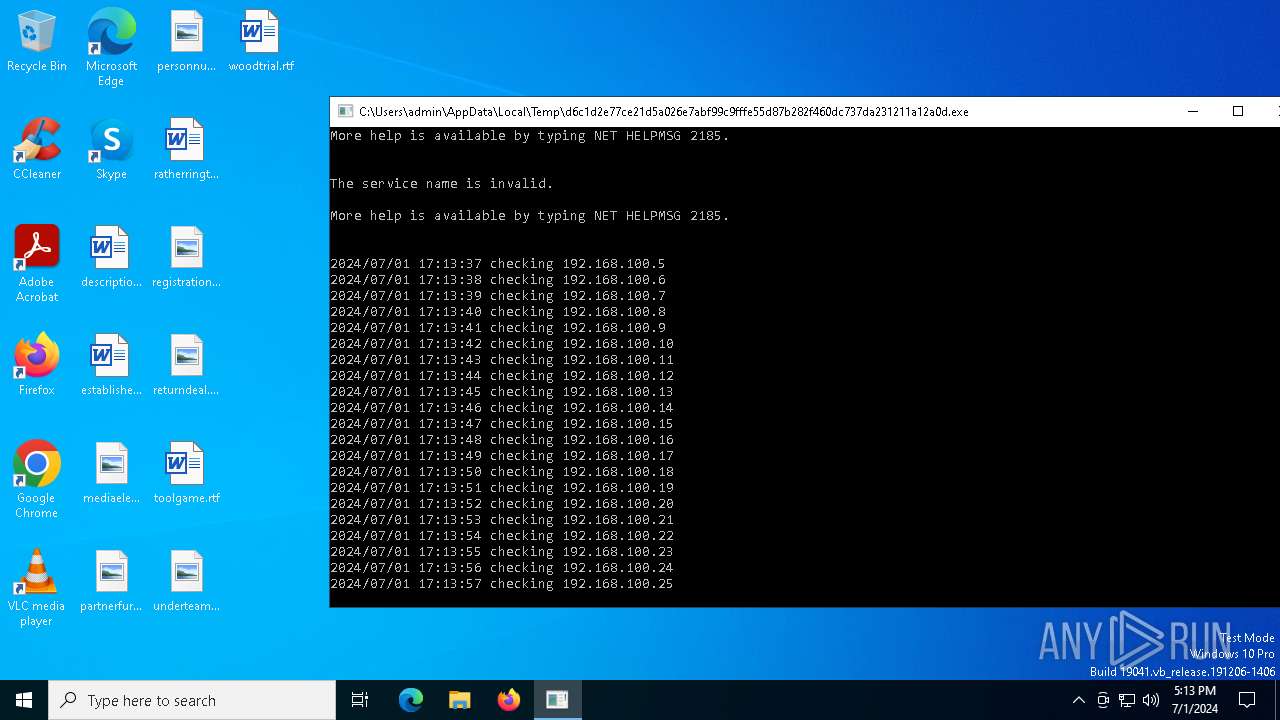
Starts NET.EXE for service management
- cmd.exe (PID: 6328)
- net.exe (PID: 3780)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 7096)
- net.exe (PID: 7480)
- net.exe (PID: 7540)
- net.exe (PID: 7608)
- net.exe (PID: 7740)
- cmd.exe (PID: 7316)
- cmd.exe (PID: 7256)
- cmd.exe (PID: 7280)
- cmd.exe (PID: 7344)
- net.exe (PID: 7732)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 7224)
- cmd.exe (PID: 7528)
- cmd.exe (PID: 7392)
- net.exe (PID: 7796)
- cmd.exe (PID: 7440)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7412)
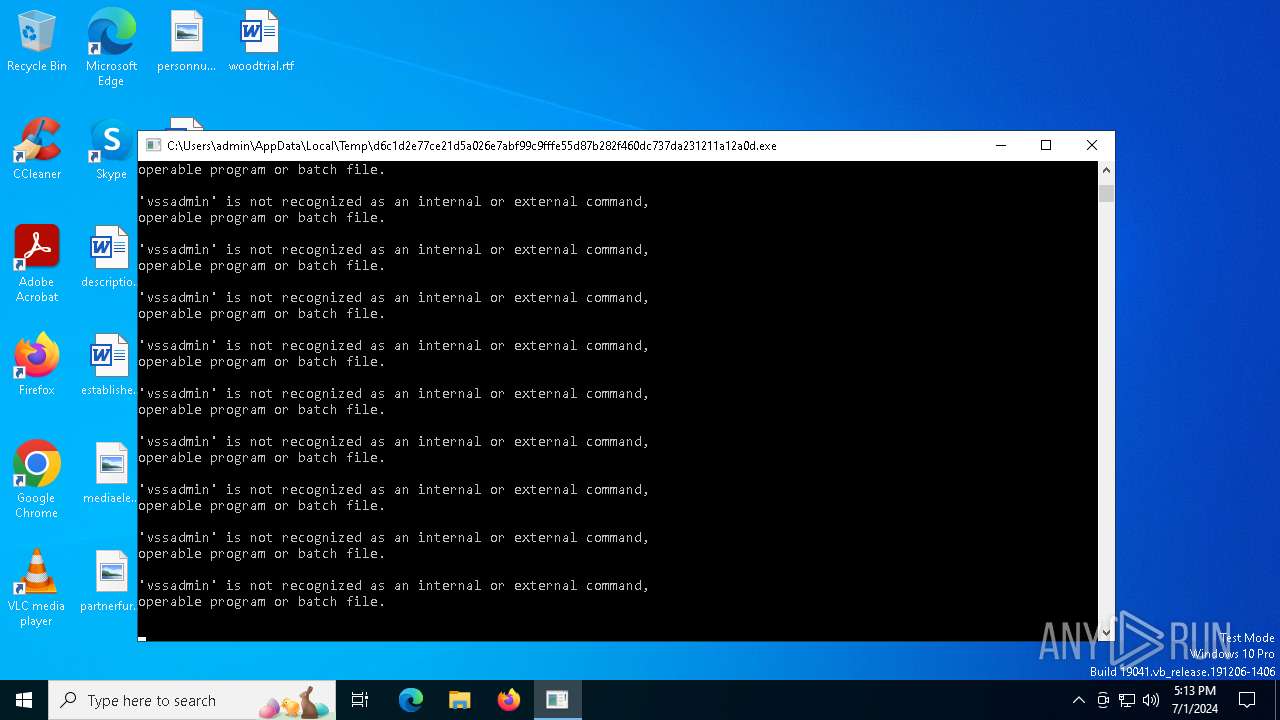
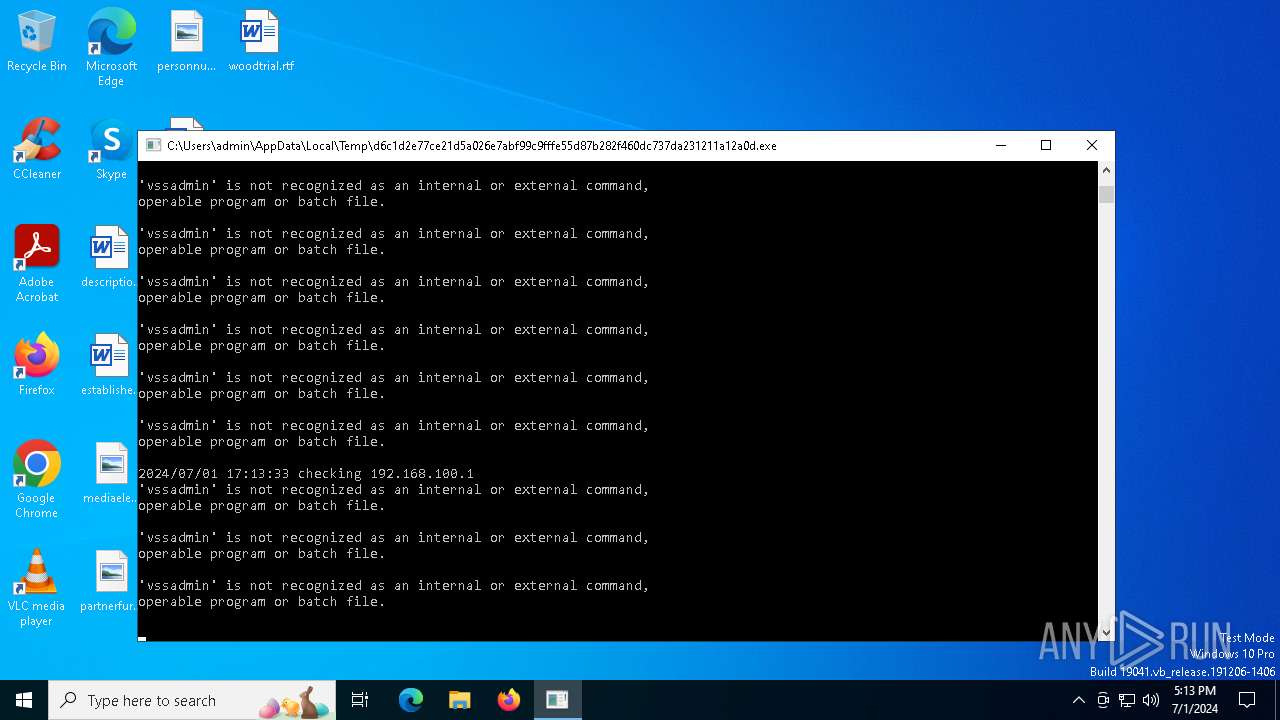
Uses NET.EXE to stop Windows Security Center service
- cmd.exe (PID: 7332)
[YARA] LockBit is detected
- d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe (PID: 900)
SUSPICIOUS
Uses WEVTUTIL.EXE to cleanup log
- cmd.exe (PID: 2440)
- cmd.exe (PID: 1828)
- cmd.exe (PID: 1220)
Starts CMD.EXE for commands execution
- d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe (PID: 900)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6212)
- cmd.exe (PID: 4820)
- cmd.exe (PID: 6180)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6280)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 1436)
- cmd.exe (PID: 6288)
- cmd.exe (PID: 6312)
- cmd.exe (PID: 6304)
- cmd.exe (PID: 6172)
- cmd.exe (PID: 6220)
- cmd.exe (PID: 5036)
- cmd.exe (PID: 6320)
- cmd.exe (PID: 6228)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 6348)
- cmd.exe (PID: 6696)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 7820)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 2828)
- cmd.exe (PID: 7048)
INFO
Checks supported languages
- d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe (PID: 900)
Reads the computer name
- d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe (PID: 900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 3 |
| CodeSize: | 1378816 |
| InitializedDataSize: | 112128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x61420 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
266
Monitored processes
137
Malicious processes
1
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | cmd.exe /c "vssadmin resize shadowstorage /for=E: /on=C: /maxsize=401MB" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Temp\d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe" | C:\Users\admin\AppData\Local\Temp\d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1112 | cmd.exe /c "vssadmin resize shadowstorage /for=F: /on=C: /maxsize=401MB" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | cmd.exe /c "vssadmin resize shadowstorage /for=B: /on=C: /maxsize=401MB" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | taskkill /f /im Dbnmp.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | cmd.exe /c "wevtutil cl securit" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 15007 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | taskkill /f /im Sql.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | cmd.exe /c "wbadmin DELETE SYSTEMSTATEBACKUP" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | cmd.exe /c "taskkill /f /im calc.exe" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | cmd.exe /c "vssadmin resize shadowstorage /for=C: /on=C: /maxsize=401MB" | C:\Windows\SysWOW64\cmd.exe | — | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 284
Read events
10 038
Write events
246
Delete events
0
Modification events
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-462 |
Value: Afghanistan Standard Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-461 |
Value: Afghanistan Daylight Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-222 |
Value: Alaskan Standard Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-221 |
Value: Alaskan Daylight Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2392 |
Value: Aleutian Standard Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2391 |
Value: Aleutian Daylight Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2162 |
Value: Altai Standard Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-2161 |
Value: Altai Daylight Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-392 |
Value: Arab Standard Time | |||
| (PID) Process: | (900) d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | C:\WINDOWS\system32\,@tzres.dll,-391 |
Value: Arab Daylight Time | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
57
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
9144 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
9076 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
7156 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
7156 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
900 | d6c1d2e77ce21d5a026e7abf99c9fffe55d87b282f460dc737da231211a12a0d.exe | 192.168.100.1:445 | — | — | — | unknown |
— | — | 192.168.100.2:445 | — | — | — | unknown |
— | — | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 192.229.221.95:80 | — | EDGECAST | US | unknown |
— | — | 2.19.246.123:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
— | — | 184.86.251.9:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 184.86.251.21:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |