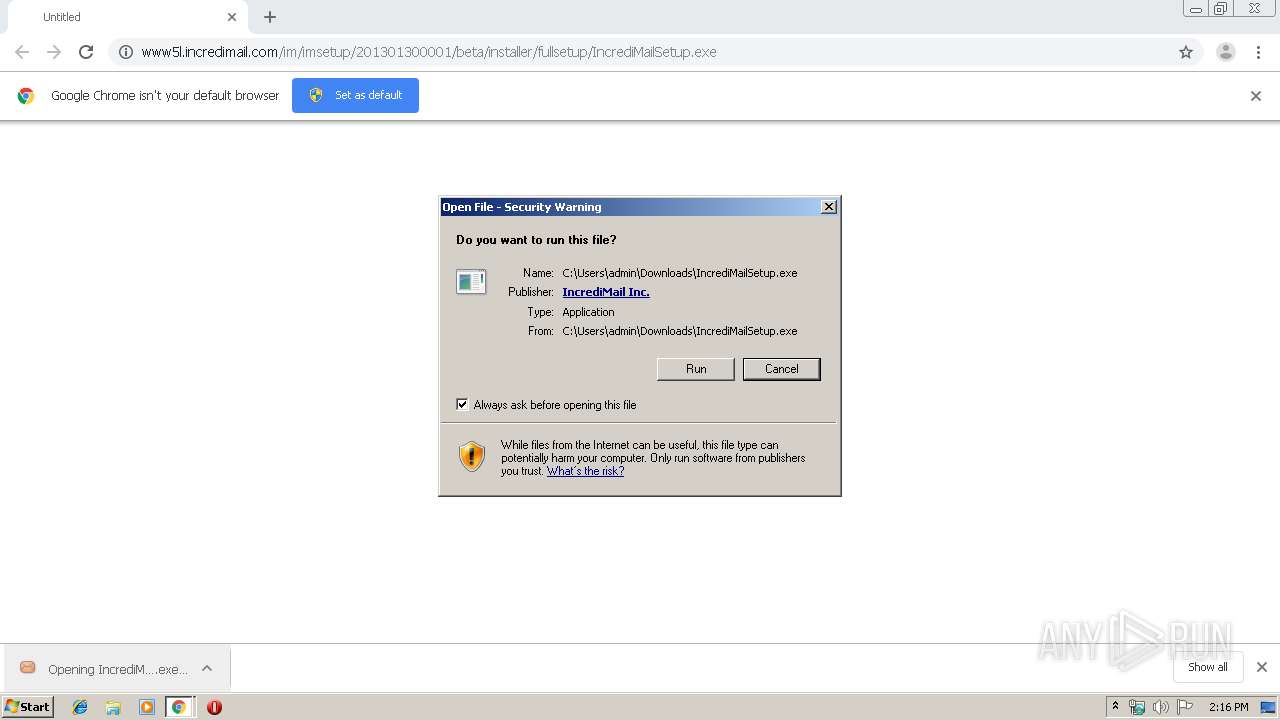
| URL: | http://www5l.incredimail.com/im/imsetup/201301300001/beta/installer/fullsetup/IncrediMailSetup.exe |
| Full analysis: | https://app.any.run/tasks/f6107f5d-ba3e-43ef-9c8d-33958de03e6a |
| Verdict: | Malicious activity |
| Analysis date: | January 12, 2020, 14:15:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3037BC09ACD268D69F97B863D883B9A8 |
| SHA1: | 917A0D5ECA47C6293F3C2FC872B534059C1FFC52 |
| SHA256: | D6BD1FDDDFA59746A0CF529D18AA1F2905B7AB30C7130136131B19B67075CDEF |
| SSDEEP: | 3:N1KJSjJGl6IHKKM3YAZX+2L0EyqOXKDQLXAB34pVkA:Cc1G6PKML+2LnOX9LUopaA |
MALICIOUS
Application was dropped or rewritten from another process
- IncrediMailSetup.exe (PID: 2520)
- IncrediMailSetup_en.exe (PID: 3392)
- IncrediMailSetup_en.exe (PID: 2144)
- IncMail.exe (PID: 3748)
- ImApp.exe (PID: 3084)
- ImpCnt.exe (PID: 2848)
- ImpCnt.exe (PID: 2096)
- ImpCnt.exe (PID: 1016)
- ImpCnt.exe (PID: 2548)
- ImpCnt.exe (PID: 2676)
- ImpCnt.exe (PID: 1296)
- ImpCnt.exe (PID: 1768)
- ImpCnt.exe (PID: 2440)
- ImpCnt.exe (PID: 1244)
- IncMail.exe (PID: 1600)
- IncMail.exe (PID: 3940)
- ImApp.exe (PID: 252)
- ImLpp.exe (PID: 2444)
- ImLpp.exe (PID: 2712)
- ImLpp.exe (PID: 3940)
- ImLpp.exe (PID: 1596)
- ImLpp.exe (PID: 3284)
- ImLpp.exe (PID: 3588)
- ImLpp.exe (PID: 3892)
- ImLpp.exe (PID: 4012)
- ImNotfy.exe (PID: 2952)
- ImLpp.exe (PID: 3324)
- ImLpp.exe (PID: 2700)
- ImLpp.exe (PID: 3612)
- ImLpp.exe (PID: 2004)
- ImLpp.exe (PID: 4068)
- ImLpp.exe (PID: 1900)
- ImLpp.exe (PID: 3916)
- ImLpp.exe (PID: 388)
- ImLpp.exe (PID: 2844)
- ImLpp.exe (PID: 3256)
- ImLpp.exe (PID: 1556)
- ImLpp.exe (PID: 3224)
- ImLpp.exe (PID: 3608)
- ImLpp.exe (PID: 2236)
- ImLpp.exe (PID: 2612)
- aeldr.exe (PID: 4088)
- ImLpp.exe (PID: 1796)
- ImLpp.exe (PID: 3092)
- ImLpp.exe (PID: 3248)
- ImLpp.exe (PID: 1704)
- ImLpp.exe (PID: 1952)
- ImLpp.exe (PID: 720)
- ImLpp.exe (PID: 1484)
- ImLpp.exe (PID: 2200)
- ImLpp.exe (PID: 2968)
- ImLpp.exe (PID: 3568)
- ImLpp.exe (PID: 324)
- ImLpp.exe (PID: 3352)
- ImLpp.exe (PID: 2108)
- ImLpp.exe (PID: 2648)
- ImLpp.exe (PID: 2132)
- ImLpp.exe (PID: 3124)
- ImLpp.exe (PID: 1036)
- ImLpp.exe (PID: 4036)
- ImLpp.exe (PID: 1104)
- ImLpp.exe (PID: 3920)
- ImLpp.exe (PID: 2684)
- ImLpp.exe (PID: 2176)
- ImLpp.exe (PID: 2556)
- ImLpp.exe (PID: 3708)
Loads dropped or rewritten executable
- ImApp.exe (PID: 3084)
- IncMail.exe (PID: 3748)
- ImNotfy.exe (PID: 2952)
- ImpCnt.exe (PID: 2848)
- ImpCnt.exe (PID: 1244)
- ImpCnt.exe (PID: 2096)
- ImpCnt.exe (PID: 2676)
- ImpCnt.exe (PID: 1768)
- ImpCnt.exe (PID: 1296)
- ImpCnt.exe (PID: 1016)
- ImpCnt.exe (PID: 2548)
- ImpCnt.exe (PID: 2440)
- IncMail.exe (PID: 1600)
- ImApp.exe (PID: 252)
- IncMail.exe (PID: 3940)
- ImLpp.exe (PID: 2444)
- ImLpp.exe (PID: 2712)
- ImLpp.exe (PID: 3284)
- ImLpp.exe (PID: 3940)
- ImLpp.exe (PID: 1596)
- ImLpp.exe (PID: 3588)
- ImLpp.exe (PID: 3892)
- ImLpp.exe (PID: 4012)
- ImLpp.exe (PID: 2700)
- ImLpp.exe (PID: 3612)
- ImLpp.exe (PID: 3324)
- ImLpp.exe (PID: 2004)
- ImLpp.exe (PID: 1900)
- ImLpp.exe (PID: 4068)
- ImLpp.exe (PID: 3916)
- ImLpp.exe (PID: 3256)
- ImLpp.exe (PID: 388)
- ImLpp.exe (PID: 2844)
- ImLpp.exe (PID: 3224)
- ImLpp.exe (PID: 2236)
- ImLpp.exe (PID: 1556)
- aeldr.exe (PID: 4088)
- ImLpp.exe (PID: 2612)
- ImLpp.exe (PID: 3608)
- ImLpp.exe (PID: 1952)
- ImLpp.exe (PID: 1704)
- ImLpp.exe (PID: 720)
- ImLpp.exe (PID: 1484)
- ImLpp.exe (PID: 1796)
- ImLpp.exe (PID: 3092)
- ImLpp.exe (PID: 2200)
- ImLpp.exe (PID: 324)
- ImLpp.exe (PID: 3124)
- ImLpp.exe (PID: 2968)
- ImLpp.exe (PID: 3248)
- ImLpp.exe (PID: 2556)
- ImLpp.exe (PID: 2108)
- ImLpp.exe (PID: 2648)
- ImLpp.exe (PID: 2132)
- ImLpp.exe (PID: 3352)
- ImLpp.exe (PID: 1036)
- ImLpp.exe (PID: 3708)
- ImLpp.exe (PID: 1104)
- ImLpp.exe (PID: 4036)
- ImLpp.exe (PID: 2176)
- ImLpp.exe (PID: 3568)
- ImLpp.exe (PID: 3920)
- ImLpp.exe (PID: 2684)
Changes the autorun value in the registry
- IncMail.exe (PID: 1600)
Scans artifacts that could help determine the target
- IncMail.exe (PID: 1600)
SUSPICIOUS
Executable content was dropped or overwritten
- IncrediMailSetup.exe (PID: 2520)
- chrome.exe (PID: 1328)
- chrome.exe (PID: 2148)
- msiexec.exe (PID: 2696)
Starts Microsoft Installer
- IncrediMailSetup_en.exe (PID: 3392)
Executed as Windows Service
- vssvc.exe (PID: 2496)
Reads internet explorer settings
- IncrediMailSetup.exe (PID: 2520)
- ImApp.exe (PID: 252)
- IncMail.exe (PID: 1600)
Creates files in the program directory
- IncrediMailSetup.exe (PID: 2520)
- ImApp.exe (PID: 252)
Creates files in the user directory
- MsiExec.exe (PID: 2212)
- msiexec.exe (PID: 2696)
- IncMail.exe (PID: 1600)
- ImLpp.exe (PID: 2004)
- ImLpp.exe (PID: 1900)
- ImLpp.exe (PID: 4068)
- ImLpp.exe (PID: 3256)
- ImLpp.exe (PID: 3916)
- ImLpp.exe (PID: 388)
- ImLpp.exe (PID: 2844)
- ImLpp.exe (PID: 2236)
- ImLpp.exe (PID: 3224)
- ImLpp.exe (PID: 2612)
- ImLpp.exe (PID: 3608)
- ImLpp.exe (PID: 1556)
- ImApp.exe (PID: 252)
- aeldr.exe (PID: 4088)
- ImLpp.exe (PID: 1704)
- ImLpp.exe (PID: 720)
- ImLpp.exe (PID: 1796)
- ImLpp.exe (PID: 1484)
- ImLpp.exe (PID: 3092)
- ImLpp.exe (PID: 1952)
Modifies the open verb of a shell class
- msiexec.exe (PID: 2696)
Changes IE settings (feature browser emulation)
- msiexec.exe (PID: 2696)
- IncMail.exe (PID: 1600)
Creates COM task schedule object
- MsiExec.exe (PID: 856)
- msiexec.exe (PID: 2696)
Reads Internet Cache Settings
- IncMail.exe (PID: 1600)
- ImApp.exe (PID: 252)
- ImLpp.exe (PID: 2444)
- ImLpp.exe (PID: 2712)
- ImLpp.exe (PID: 3284)
- ImLpp.exe (PID: 3940)
- ImLpp.exe (PID: 1596)
- ImLpp.exe (PID: 3892)
- ImLpp.exe (PID: 3588)
- ImLpp.exe (PID: 4012)
- ImLpp.exe (PID: 2700)
- ImLpp.exe (PID: 3612)
- ImLpp.exe (PID: 3324)
- ImLpp.exe (PID: 1900)
- ImLpp.exe (PID: 4068)
- ImLpp.exe (PID: 2004)
- ImLpp.exe (PID: 388)
- ImLpp.exe (PID: 2844)
- ImLpp.exe (PID: 3256)
- ImLpp.exe (PID: 3916)
- ImLpp.exe (PID: 3224)
- ImLpp.exe (PID: 2236)
- ImLpp.exe (PID: 2612)
- ImLpp.exe (PID: 3608)
- ImLpp.exe (PID: 1556)
- ImLpp.exe (PID: 1704)
- aeldr.exe (PID: 4088)
- ImLpp.exe (PID: 720)
- ImLpp.exe (PID: 1952)
- ImLpp.exe (PID: 3092)
- ImLpp.exe (PID: 1796)
- ImLpp.exe (PID: 1484)
- ImLpp.exe (PID: 2200)
- ImLpp.exe (PID: 3248)
- ImLpp.exe (PID: 3568)
- ImLpp.exe (PID: 2108)
- ImLpp.exe (PID: 2648)
- ImLpp.exe (PID: 2132)
- ImLpp.exe (PID: 2556)
- ImLpp.exe (PID: 1036)
- ImLpp.exe (PID: 3708)
- ImLpp.exe (PID: 2684)
- ImLpp.exe (PID: 4036)
- ImLpp.exe (PID: 3920)
- ImLpp.exe (PID: 2176)
- ImLpp.exe (PID: 324)
- ImLpp.exe (PID: 2968)
- ImLpp.exe (PID: 3124)
- ImLpp.exe (PID: 3352)
- ImLpp.exe (PID: 1104)
Executed via COM
- ImApp.exe (PID: 252)
Reads the cookies of Google Chrome
- ImApp.exe (PID: 252)
Reads the cookies of Mozilla Firefox
- ImApp.exe (PID: 252)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2148)
INFO
Reads the hosts file
- chrome.exe (PID: 2148)
- chrome.exe (PID: 1328)
Searches for installed software
- msiexec.exe (PID: 2696)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2212)
- MsiExec.exe (PID: 856)
Reads Internet Cache Settings
- chrome.exe (PID: 2148)
Application launched itself
- chrome.exe (PID: 2148)
- msiexec.exe (PID: 2696)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2496)
Dropped object may contain Bitcoin addresses
- IncrediMailSetup.exe (PID: 2520)
- msiexec.exe (PID: 2696)
- IncMail.exe (PID: 1600)
Creates a software uninstall entry
- msiexec.exe (PID: 2696)
Creates files in the program directory
- msiexec.exe (PID: 2696)
- MsiExec.exe (PID: 2212)
Manual execution by user
- IncMail.exe (PID: 3940)
Reads Microsoft Office registry keys
- IncMail.exe (PID: 1600)
Reads settings of System Certificates
- IncMail.exe (PID: 1600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
141
Monitored processes
98
Malicious processes
68
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Program Files\IncrediMail\Bin\ImApp.exe" -Embedding | C:\Program Files\IncrediMail\Bin\ImApp.exe | svchost.exe | ||||||||||||
User: admin Company: IncrediMail Ltd. Integrity Level: MEDIUM Description: IncrediMail Tray Application Exit code: 0 Version: 6, 6, 0, 5344 Modules
| |||||||||||||||
| 324 | ImLpp.exe "/SetCookie:C:\Users\admin\AppData\Local\Temp\Low\IM\im3645.tmp" "/Domain:http://www.incredimail.com" | C:\Program Files\IncrediMail\Bin\ImLpp.exe | — | ImApp.exe | |||||||||||
User: admin Company: IncrediMail Ltd. Integrity Level: LOW Description: ImLpp MFC Application Exit code: 0 Version: 6, 6, 0, 5344 Modules
| |||||||||||||||
| 388 | ImLpp.exe "/SetCookie:C:\Users\admin\AppData\Local\Temp\Low\IM\im2BC3.tmp" "/Domain:http://incredimail.com" | C:\Program Files\IncrediMail\Bin\ImLpp.exe | — | ImApp.exe | |||||||||||
User: admin Company: IncrediMail Ltd. Integrity Level: LOW Description: ImLpp MFC Application Exit code: 0 Version: 6, 6, 0, 5344 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1036,15717240026979722871,15473170587917080511,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=14206427817265862060 --mojo-platform-channel-handle=1048 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,15717240026979722871,15473170587917080511,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9693256191823163731 --mojo-platform-channel-handle=4968 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,15717240026979722871,15473170587917080511,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16049764769388841934 --mojo-platform-channel-handle=4464 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 720 | ImLpp.exe "/SetCookie:C:\Users\admin\AppData\Local\Temp\Low\IM\im34A7.tmp" "/Domain:http://incredimail.com" | C:\Program Files\IncrediMail\Bin\ImLpp.exe | — | ImApp.exe | |||||||||||
User: admin Company: IncrediMail Ltd. Integrity Level: LOW Description: ImLpp MFC Application Exit code: 0 Version: 6, 6, 0, 5344 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,15717240026979722871,15473170587917080511,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12852000590749855 --mojo-platform-channel-handle=2780 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 856 | C:\Windows\system32\MsiExec.exe -Embedding D0F8E8719FA87B3491F15C3C4686F40E M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | "C:\Program Files\IncrediMail\Bin\ImpCnt.exe" /silent /nothumb /common /path:"C:\Users\admin\AppData\Local\Temp\IM_F1BD.tmp\CommonAppData\IncrediMail\Data\SetupData\Emoticon" | C:\Program Files\IncrediMail\Bin\ImpCnt.exe | — | MsiExec.exe | |||||||||||
User: admin Company: IncrediMail Ltd. Integrity Level: HIGH Description: IncrediMail Content Importer Exit code: 0 Version: 6, 6, 0, 5344 Modules
| |||||||||||||||
Total events
17 321
Read events
4 275
Write events
12 517
Delete events
529
Modification events
| (PID) Process: | (2168) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2148-13223312144584000 |
Value: 259 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (2148) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
141
Suspicious files
469
Text files
1 848
Unknown types
191
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\005fd373-8b89-4936-999c-c406c838b848.tmp | — | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF39a969.TMP | text | |
MD5:— | SHA256:— | |||
| 2148 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF39a94a.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
27
DNS requests
19
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
252 | ImApp.exe | POST | 500 | 82.80.204.5:80 | http://cen.incredimail.com/app/ | IL | html | 4.61 Kb | malicious |
252 | ImApp.exe | POST | 500 | 82.80.204.5:80 | http://cen.incredimail.com/app/ | IL | html | 4.61 Kb | malicious |
1328 | chrome.exe | GET | 302 | 172.217.16.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 515 b | whitelisted |
1328 | chrome.exe | GET | 302 | 172.217.16.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 510 b | whitelisted |
1328 | chrome.exe | GET | 200 | 173.194.163.91:80 | http://r5---sn-5go7ynez.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mip=82.103.130.125&mm=28&mn=sn-5go7ynez&ms=nvh&mt=1578838256&mv=u&mvi=4&pl=26&shardbypass=yes | US | crx | 293 Kb | whitelisted |
1328 | chrome.exe | GET | 200 | 173.194.150.168:80 | http://r2---sn-5goeen76.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=82.103.130.125&mm=28&mn=sn-5goeen76&ms=nvh&mt=1578838256&mv=u&mvi=1&pl=26&shardbypass=yes | US | crx | 862 Kb | whitelisted |
252 | ImApp.exe | GET | 200 | 52.48.188.30:80 | http://www.incredimail.com/h/upn/?r=79e80d9e-f028-4a0d-bfaa-fc01d7021986 | IE | text | 19 b | whitelisted |
252 | ImApp.exe | POST | 500 | 82.80.204.5:80 | http://cen.incredimail.com/app/ | IL | html | 4.61 Kb | malicious |
252 | ImApp.exe | POST | 500 | 82.80.204.5:80 | http://cen.incredimail.com/app/ | IL | html | 4.61 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1328 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1328 | chrome.exe | 172.217.22.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
252 | ImApp.exe | 82.80.204.5:80 | cen.incredimail.com | Bezeq International | IL | malicious |
1328 | chrome.exe | 172.217.16.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1600 | IncMail.exe | 172.217.16.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1600 | IncMail.exe | 216.58.207.78:443 | accounts.youtube.com | Google Inc. | US | whitelisted |
252 | ImApp.exe | 52.48.188.30:80 | www.incredimail.com | Amazon.com, Inc. | IE | malicious |
1328 | chrome.exe | 173.194.163.91:80 | r5---sn-5go7ynez.gvt1.com | Google Inc. | US | whitelisted |
1600 | IncMail.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
1328 | chrome.exe | 172.217.16.142:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www5l.incredimail.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.incredimail.com |
| whitelisted |
cen.incredimail.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1328 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1328 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
1328 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
252 | ImApp.exe | A Network Trojan was detected | ET MALWARE Misspelled Mozilla User-Agent (Mozila) |
252 | ImApp.exe | A Network Trojan was detected | MALWARE [PTsecurity] W32/IncrediMail.A.gen!Eldorado |
252 | ImApp.exe | A Network Trojan was detected | ET MALWARE Misspelled Mozilla User-Agent (Mozila) |
252 | ImApp.exe | A Network Trojan was detected | ET MALWARE Misspelled Mozilla User-Agent (Mozila) |
252 | ImApp.exe | A Network Trojan was detected | MALWARE [PTsecurity] W32/IncrediMail.A.gen!Eldorado |
252 | ImApp.exe | A Network Trojan was detected | ET MALWARE Misspelled Mozilla User-Agent (Mozila) |
252 | ImApp.exe | A Network Trojan was detected | MALWARE [PTsecurity] W32/IncrediMail.A.gen!Eldorado |