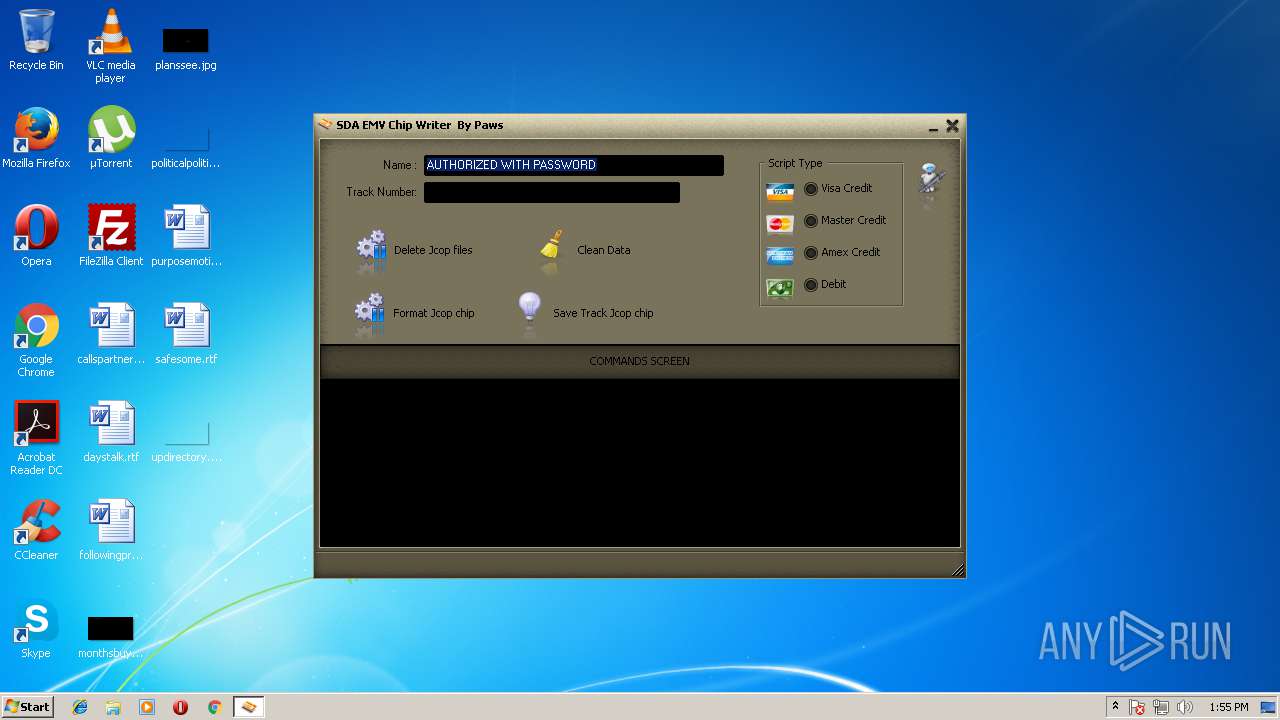
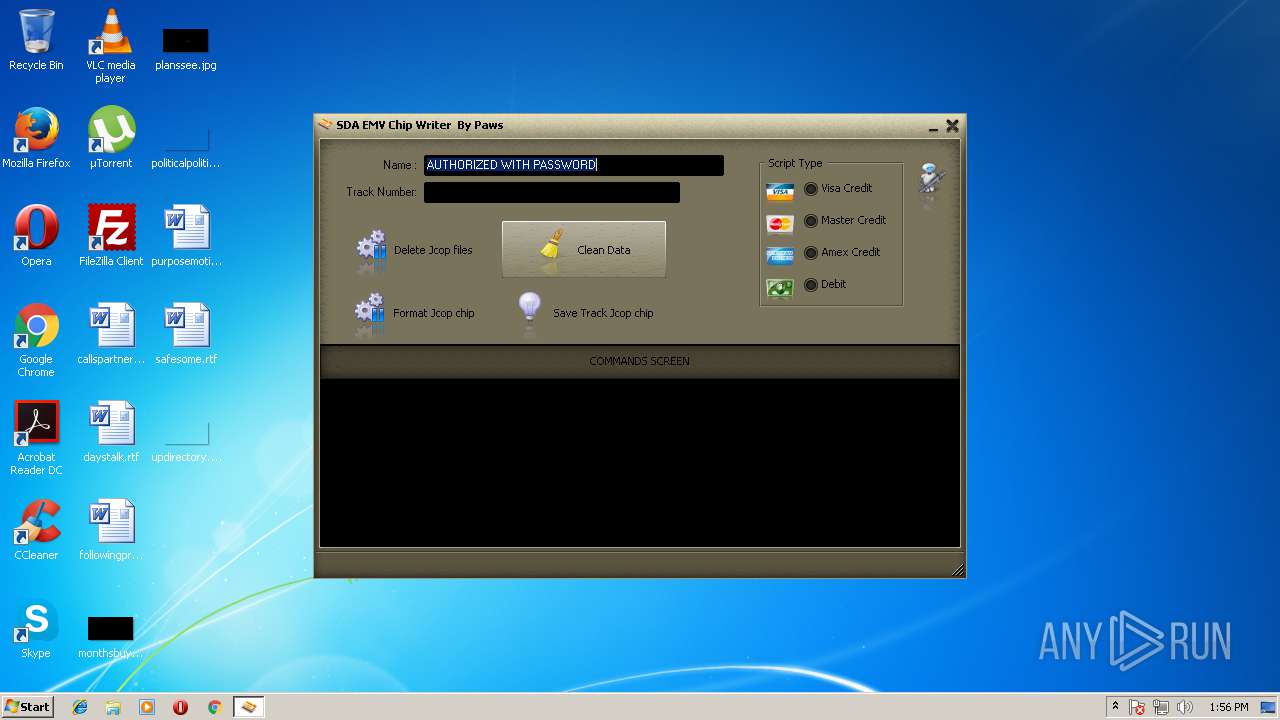
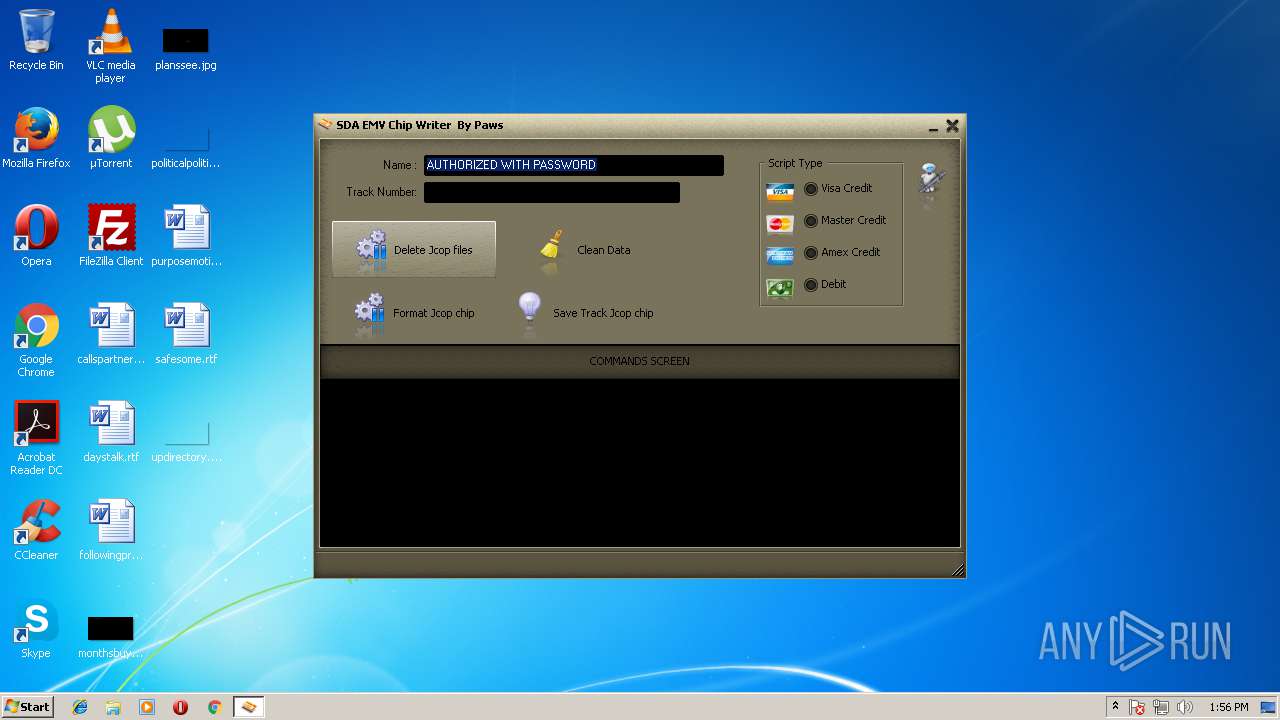
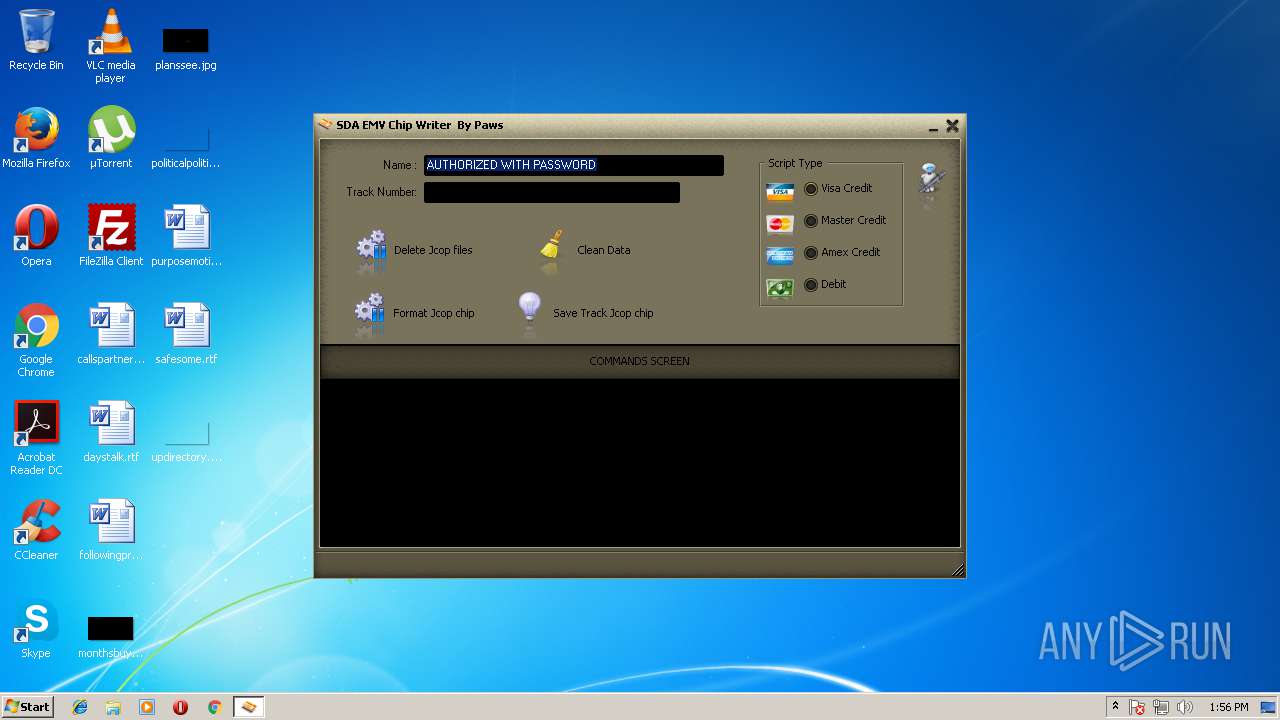
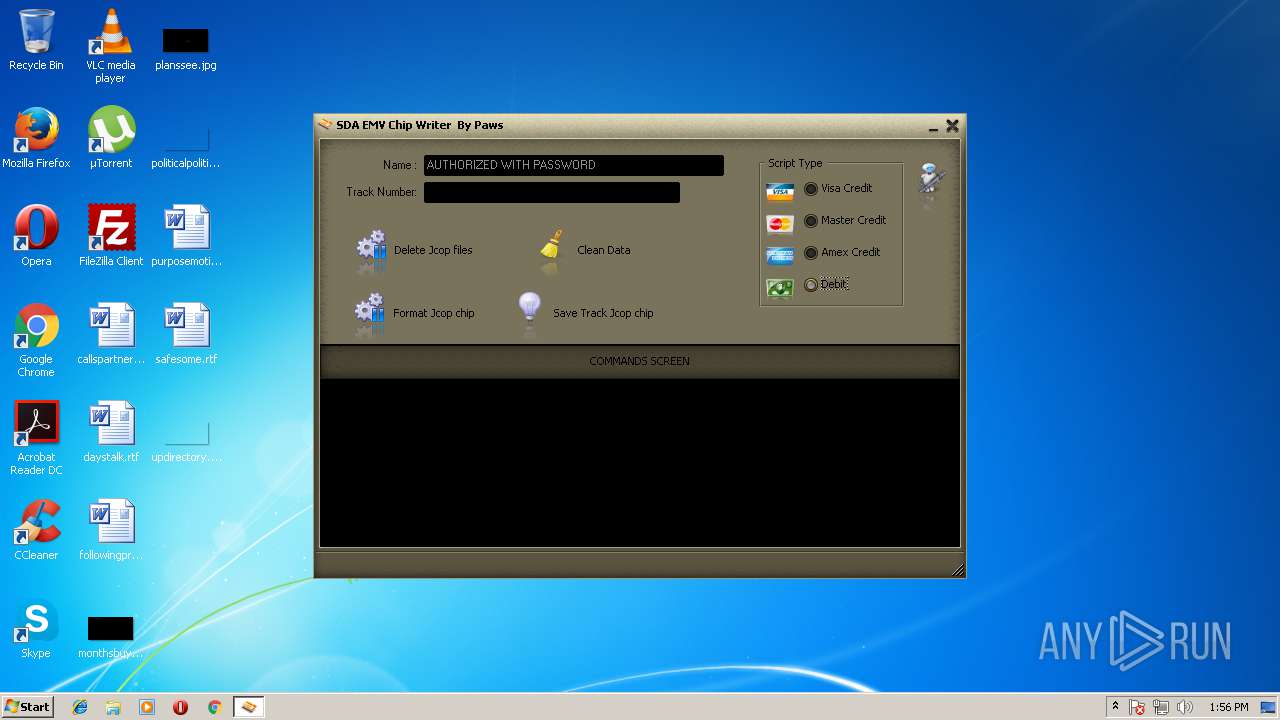
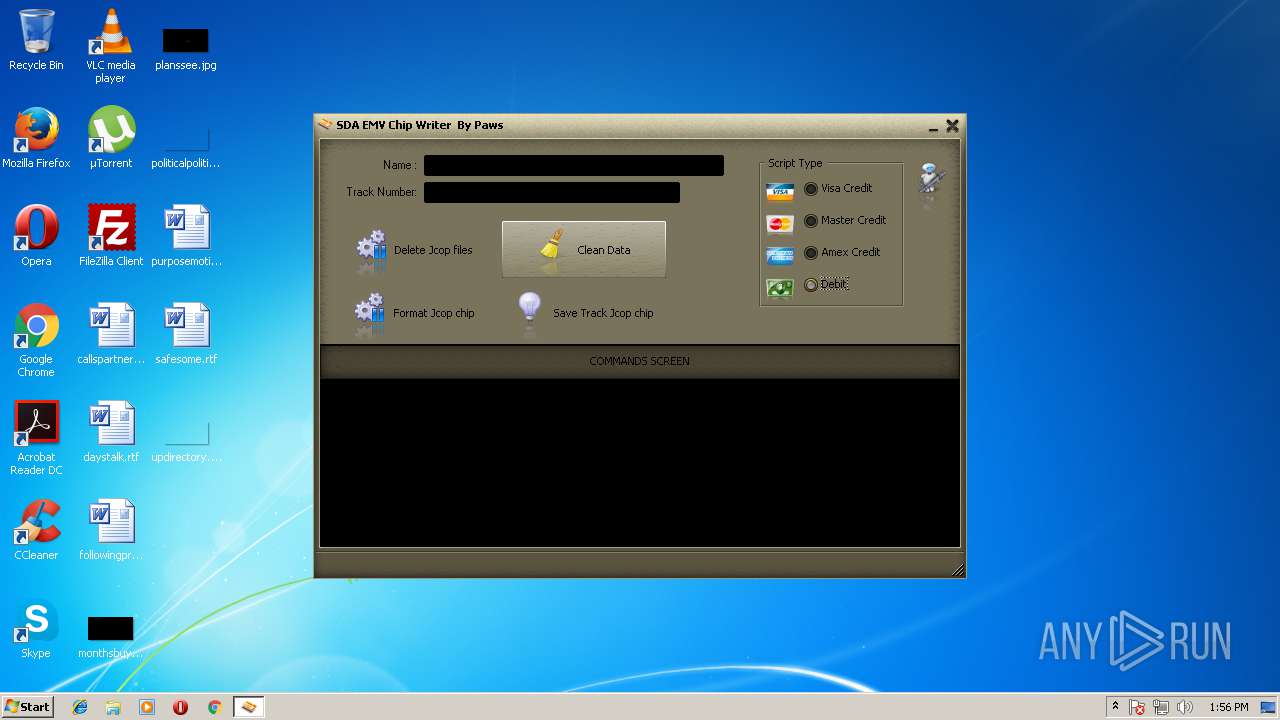
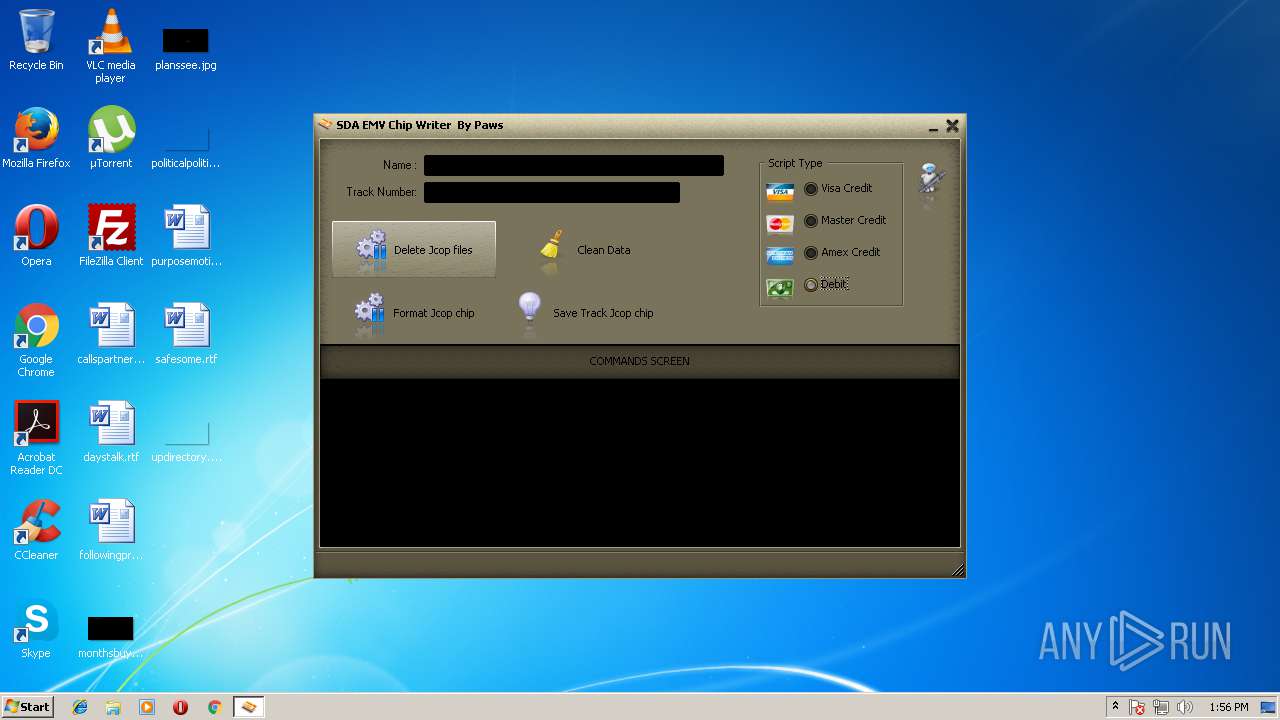
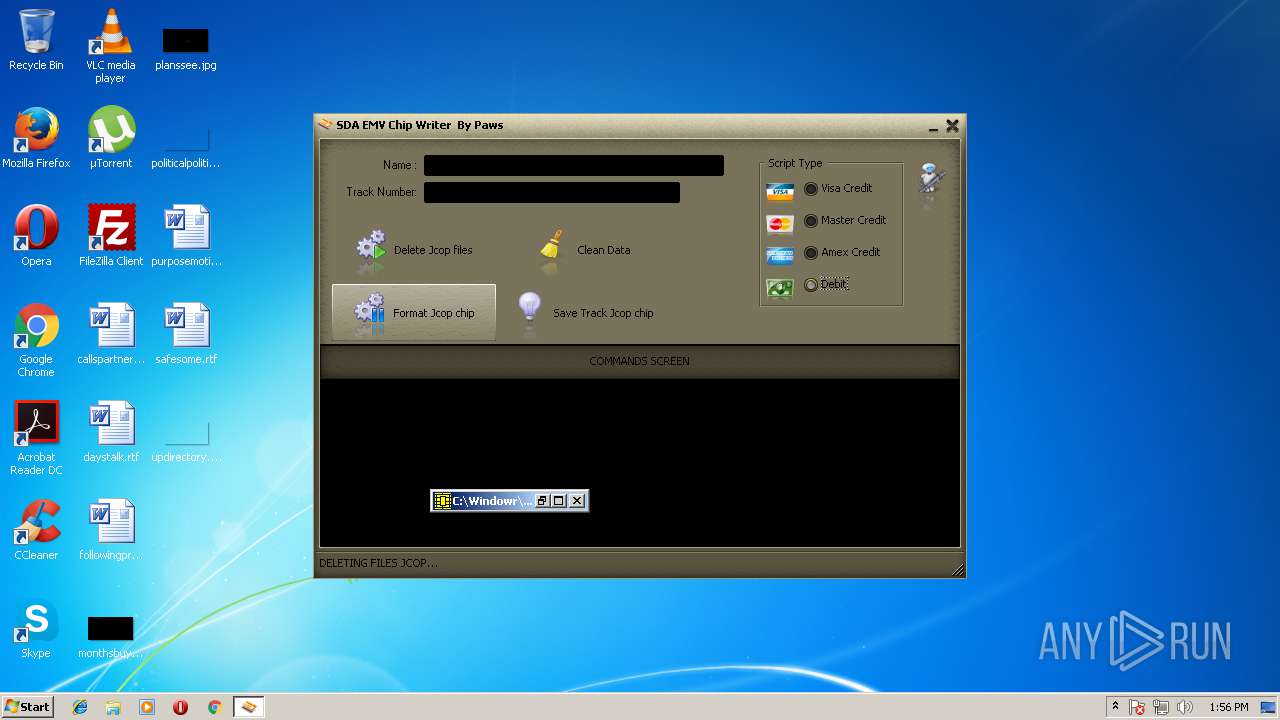
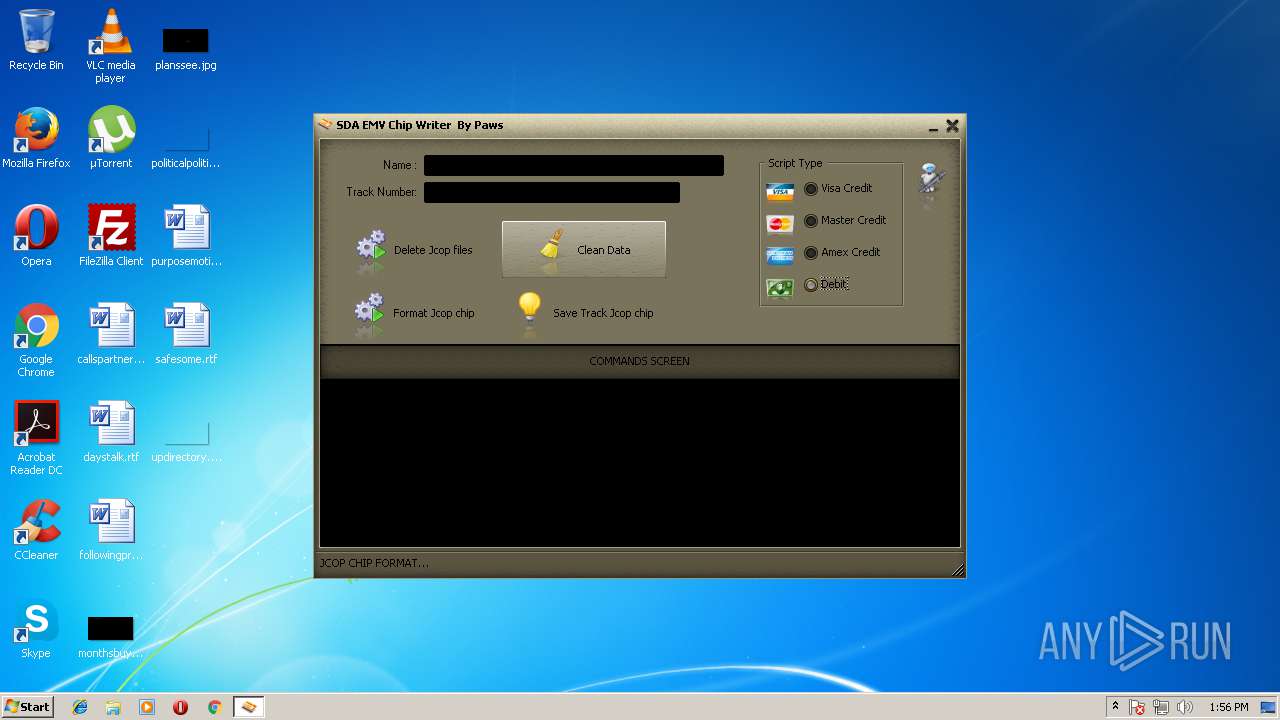
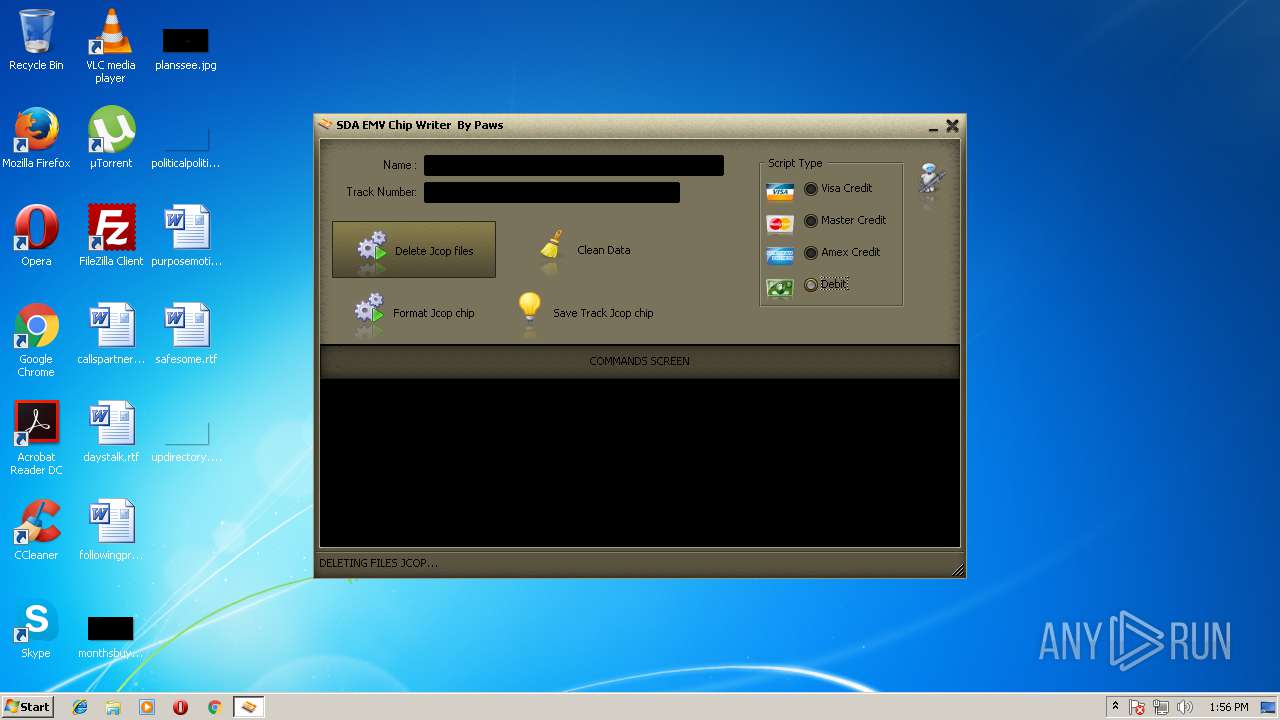
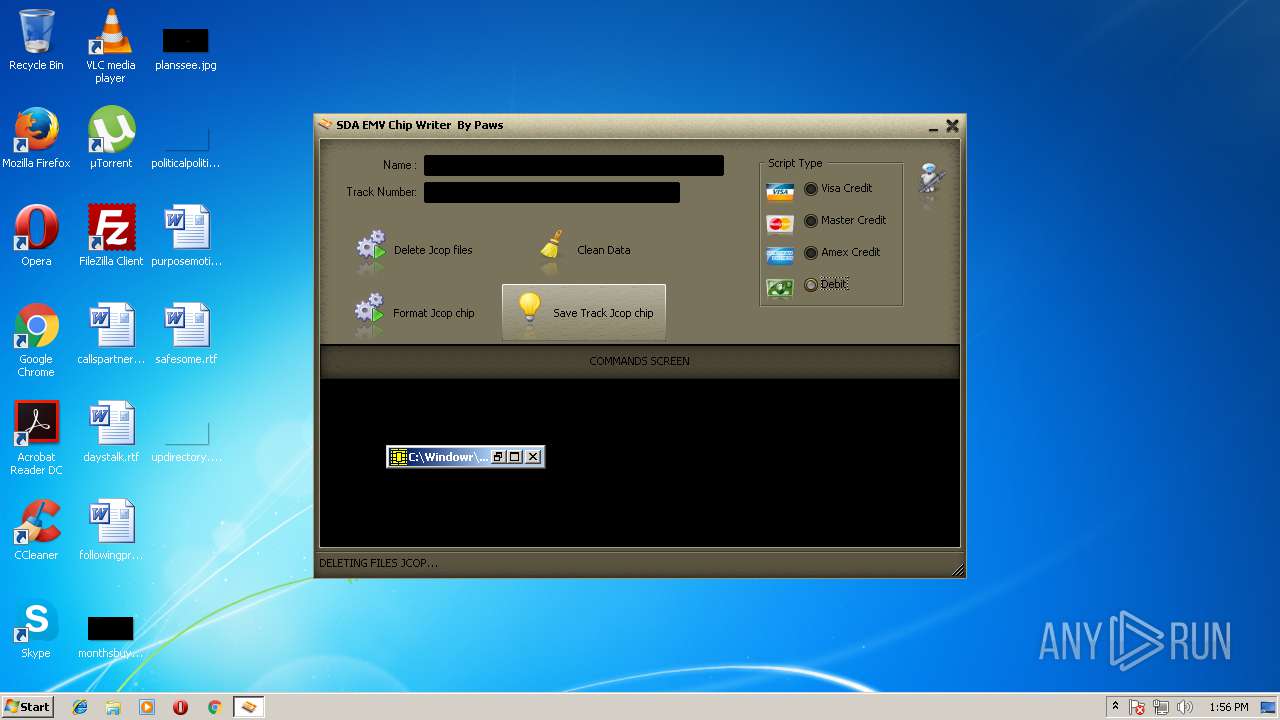
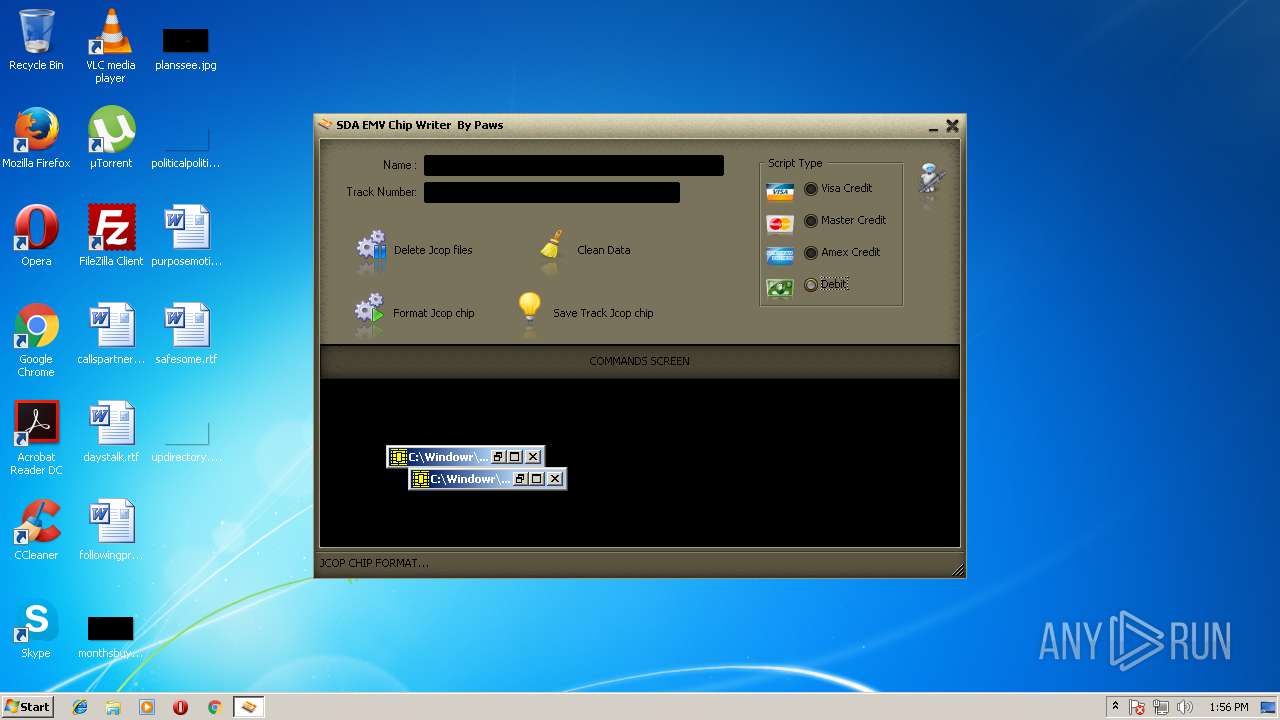
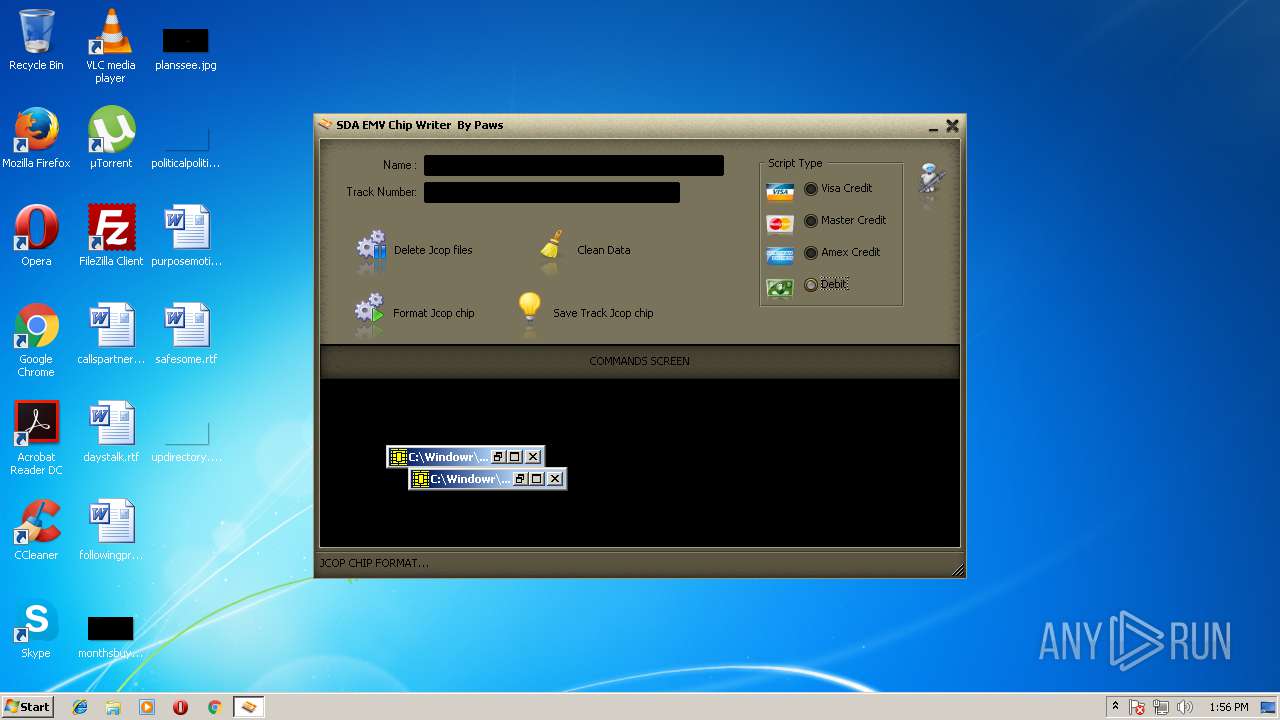
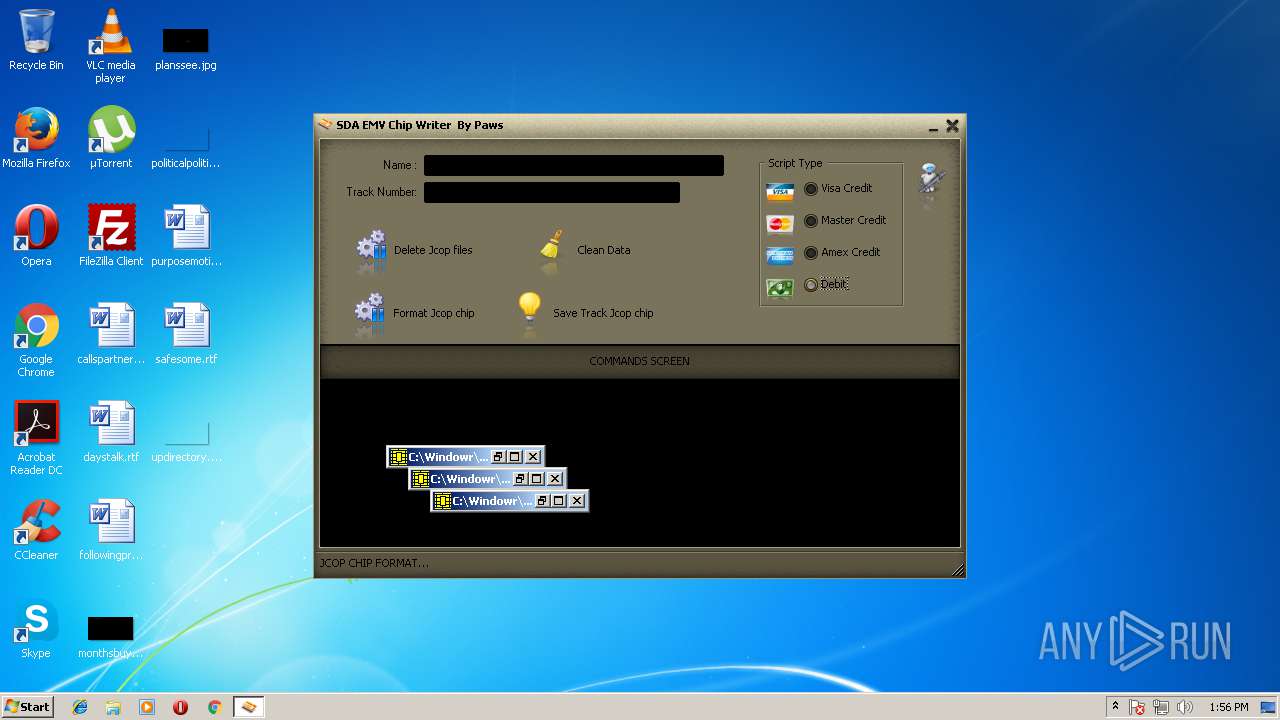
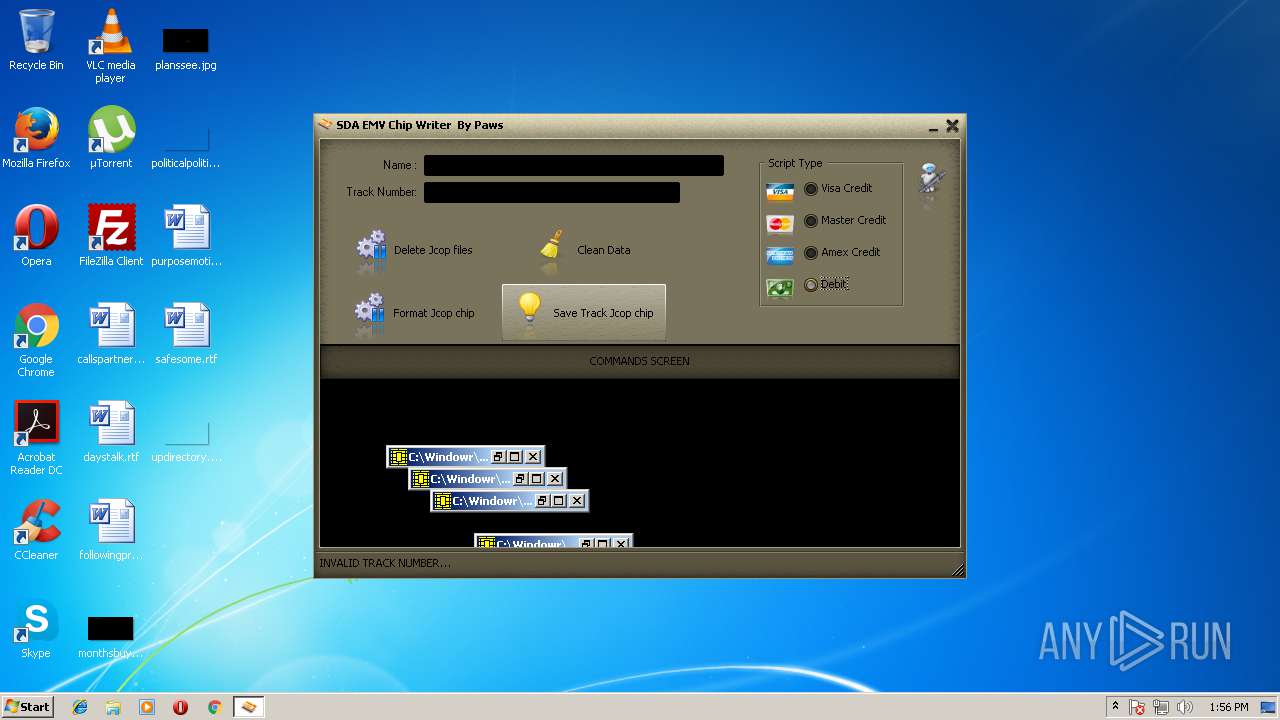
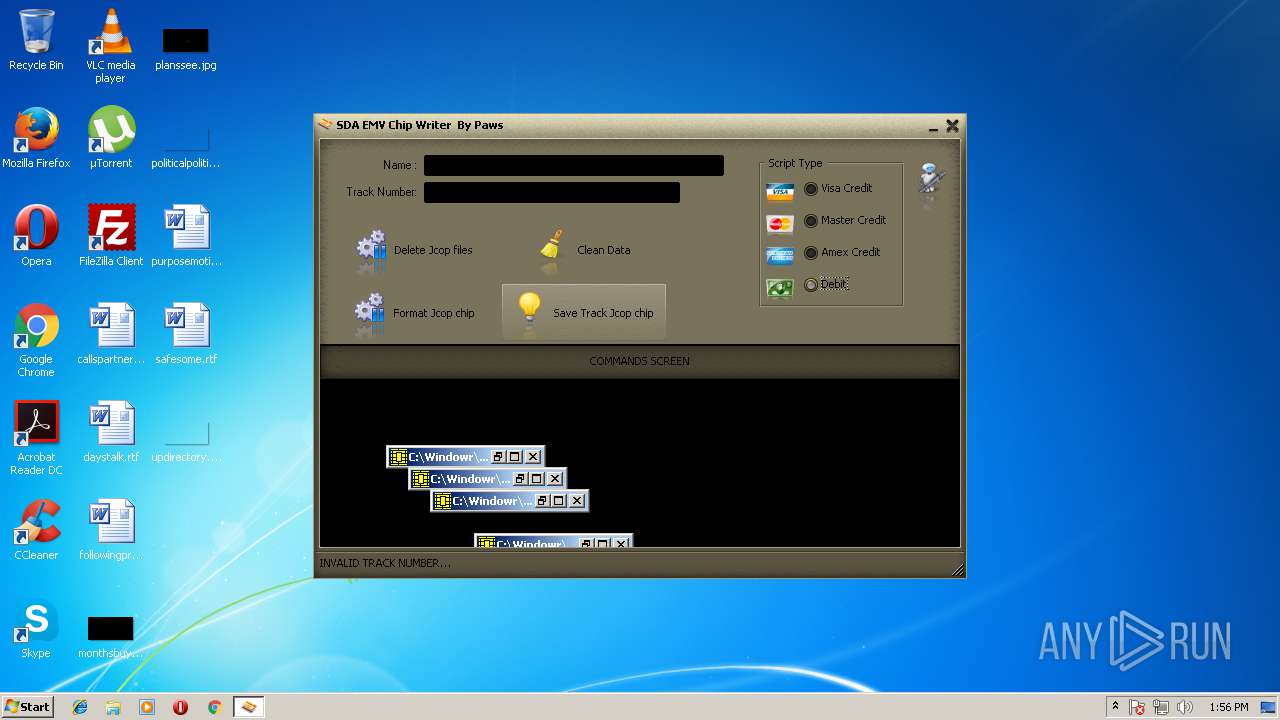
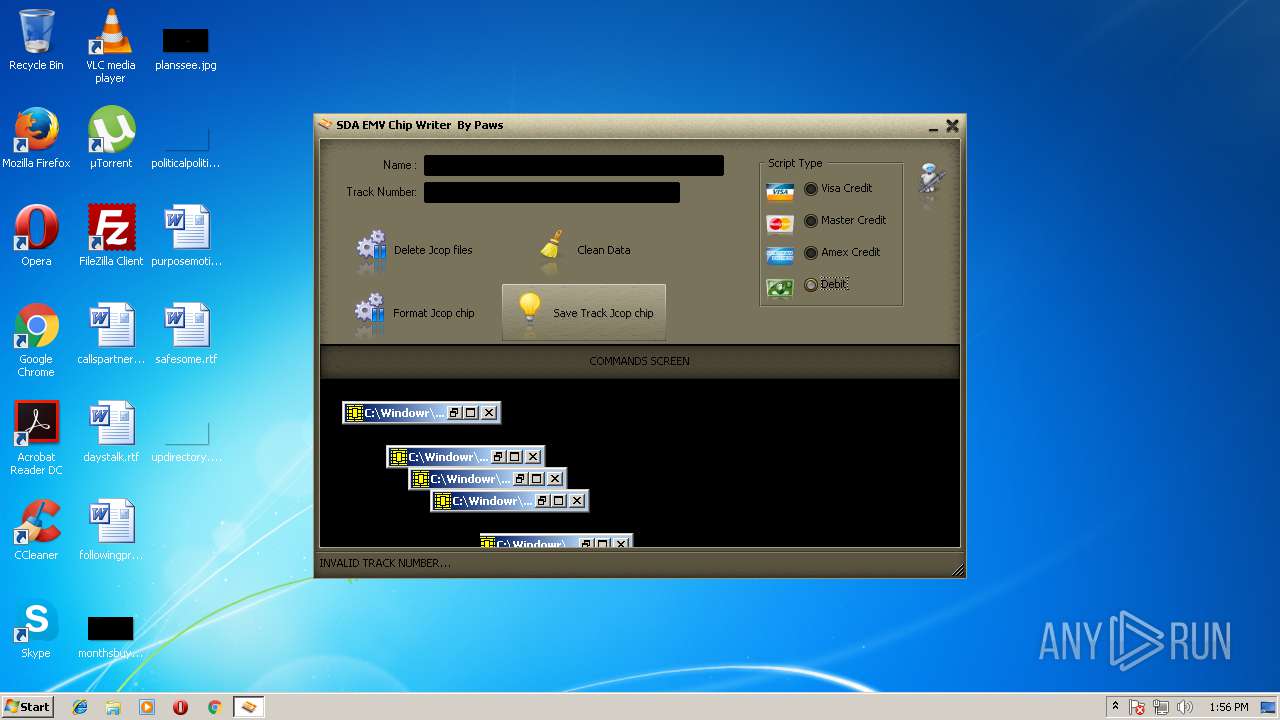
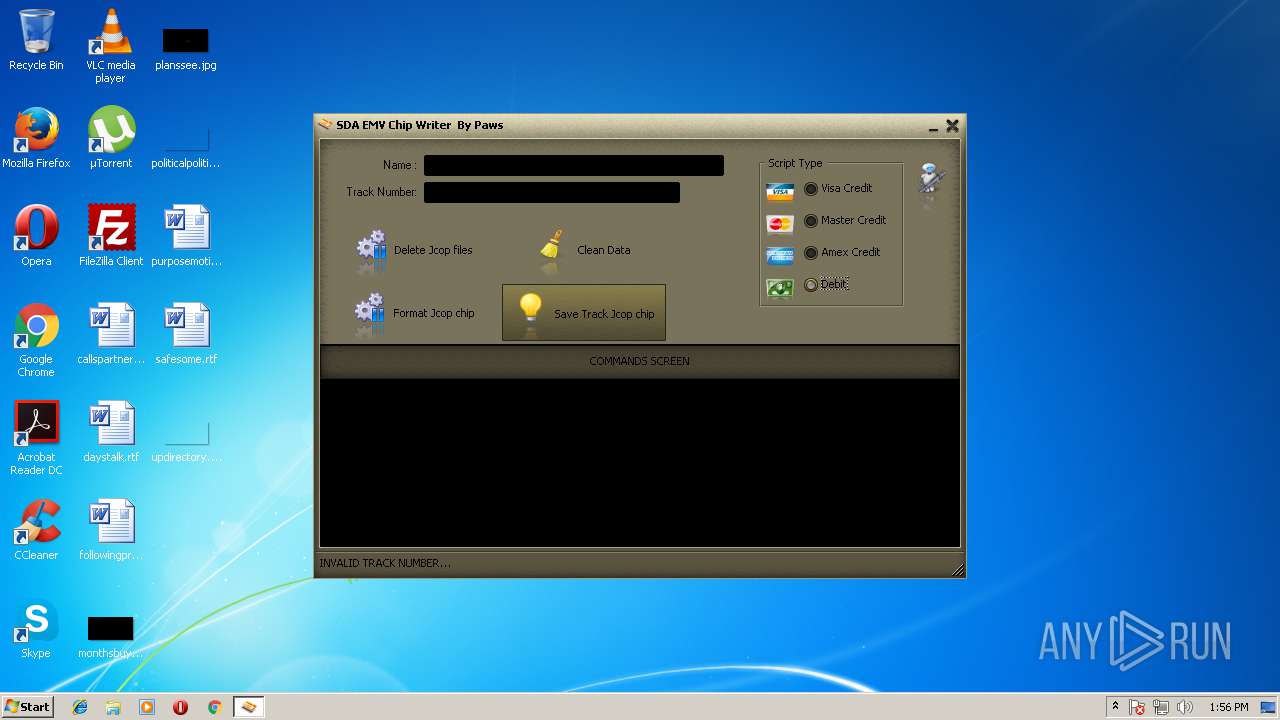
| File name: | jcopenglish[PremiumFile].exe |
| Full analysis: | https://app.any.run/tasks/b8df887b-f6c3-4f6f-b515-c7d0923c5b2e |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2018, 12:55:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | B1808E9A3F9E2E565CD0D2DDD19F14E7 |
| SHA1: | 643A6CE9DA18F82B53E95B21FC98D6D618C8B769 |
| SHA256: | D6A070B8B9F4C23AF80A5410E179892523CDFBBEFB9E65FBA2FC4AD3028E27C4 |
| SSDEEP: | 98304:/8lWoDM0MhiB3h7IUwuVN/LKN2y5VEQx/l:zoDOiB3hscDSDZj |
MALICIOUS
Application was dropped or rewritten from another process
- SynTPHelper.exe (PID: 1084)
- tmp1.jpg (PID: 4040)
- tmp2.exe (PID: 3036)
- emv.exe (PID: 3800)
- jcopenglish.exe (PID: 2228)
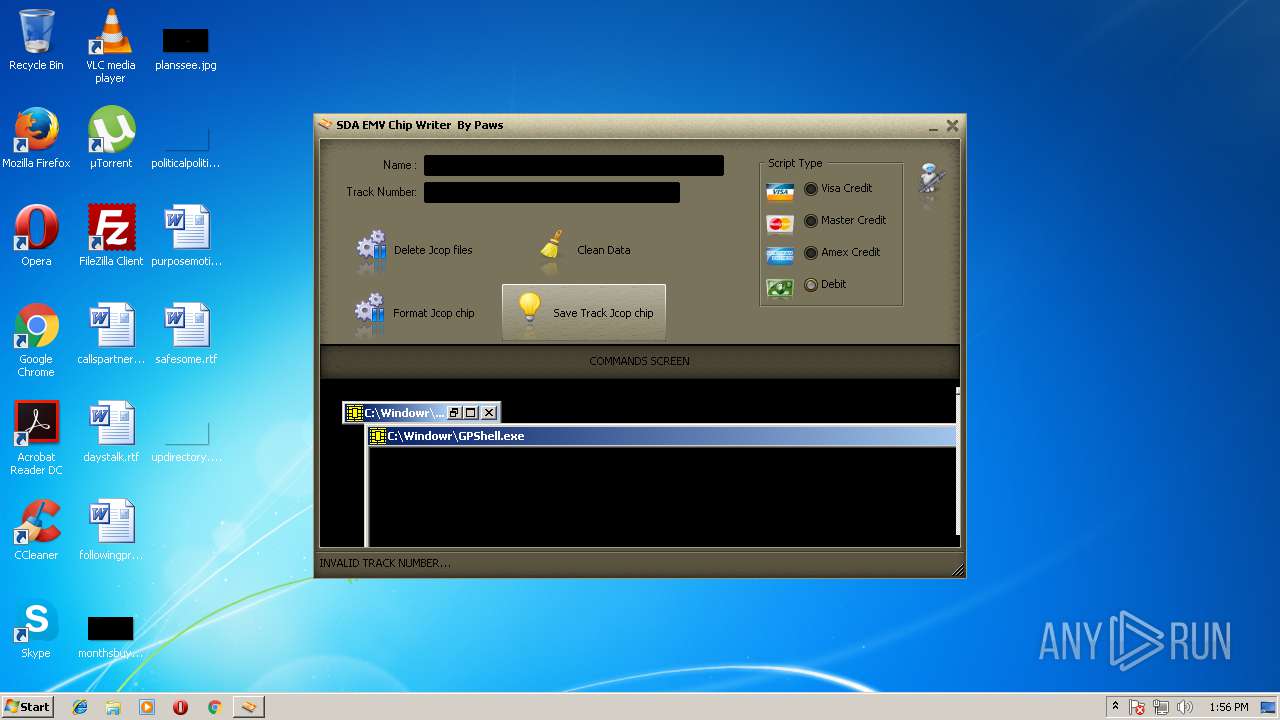
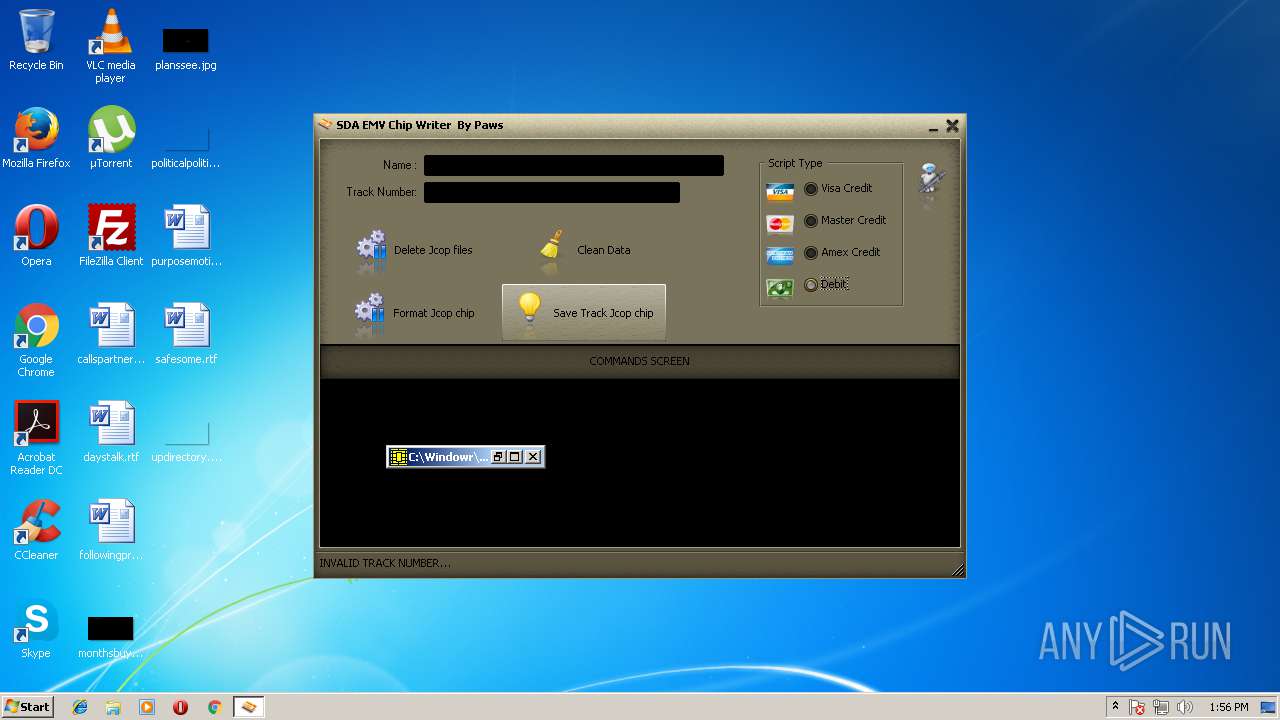
- GPShell.exe (PID: 2800)
- GPShell.exe (PID: 3768)
- GPShell.exe (PID: 2052)
- GPShell.exe (PID: 2724)
- GPShell.exe (PID: 2128)
- GPShell.exe (PID: 3164)
- GPShell.exe (PID: 3876)
- GPShell.exe (PID: 3456)
- SynTPHelper.exe (PID: 2156)
- GPShell.exe (PID: 1832)
- GPShell.exe (PID: 2676)
- GPShell.exe (PID: 2888)
- GPShell.exe (PID: 3828)
- GPShell.exe (PID: 2220)
- GPShell.exe (PID: 3748)
- GPShell.exe (PID: 1388)
- GPShell.exe (PID: 2992)
- GPShell.exe (PID: 3020)
- GPShell.exe (PID: 2208)
- GPShell.exe (PID: 4024)
- GPShell.exe (PID: 2716)
- GPShell.exe (PID: 3888)
Changes the autorun value in the registry
- tmp2.exe (PID: 3036)
Loads dropped or rewritten executable
- GPShell.exe (PID: 2800)
- GPShell.exe (PID: 3768)
- GPShell.exe (PID: 2052)
- GPShell.exe (PID: 2724)
- GPShell.exe (PID: 3164)
- GPShell.exe (PID: 3876)
- GPShell.exe (PID: 3456)
- GPShell.exe (PID: 2128)
- GPShell.exe (PID: 2220)
- GPShell.exe (PID: 2208)
- GPShell.exe (PID: 2888)
- GPShell.exe (PID: 1832)
- GPShell.exe (PID: 2676)
- GPShell.exe (PID: 3828)
- GPShell.exe (PID: 3748)
- GPShell.exe (PID: 2992)
- GPShell.exe (PID: 3020)
- GPShell.exe (PID: 3888)
- GPShell.exe (PID: 4024)
- GPShell.exe (PID: 2716)
- GPShell.exe (PID: 1388)
SUSPICIOUS
Executable content was dropped or overwritten
- jcopenglish[PremiumFile].exe (PID: 2720)
- tmp2.exe (PID: 3036)
- jcopenglish.exe (PID: 2228)
- tmp1.jpg (PID: 4040)
- SynTPHelper.exe (PID: 1084)
Starts CMD.EXE for commands execution
- jcopenglish.exe (PID: 2228)
Creates files in the user directory
- tmp2.exe (PID: 3036)
Starts application with an unusual extension
- cmd.exe (PID: 3420)
Starts itself from another location
- tmp2.exe (PID: 3036)
- SynTPHelper.exe (PID: 1084)
Creates files in the Windows directory
- SynTPHelper.exe (PID: 1084)
INFO
Dropped object may contain Bitcoin addresses
- jcopenglish.exe (PID: 2228)
- tmp2.exe (PID: 3036)
Dropped object may contain URL's
- tmp1.jpg (PID: 4040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:27 06:38:55+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24576 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x310d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Dec-2015 05:38:55 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 27-Dec-2015 05:38:55 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005E3C | 0x00006000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4323 |
.rdata | 0x00007000 | 0x0000126A | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.00589 |
.data | 0x00009000 | 0x00025D38 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.29176 |
.ndata | 0x0002F000 | 0x00008000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00037000 | 0x00007F78 | 0x00008000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.45709 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.19265 | 727 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.09944 | 9832 | UNKNOWN | English - United States | RT_ICON |
3 | 4.26454 | 4392 | UNKNOWN | English - United States | RT_ICON |
4 | 4.07509 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.49052 | 62 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
89
Monitored processes
31
Malicious processes
14
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1084 | "C:\Users\admin\AppData\Local\Temp\SynTPHelper.exe" | C:\Users\admin\AppData\Local\Temp\SynTPHelper.exe | jcopenglish[PremiumFile].exe | ||||||||||||
User: admin Company: Synaptics Incorporated Integrity Level: HIGH Description: Synaptics Pointing Device Helper Exit code: 0 Version: 19.2.17.59 26Apr17 Modules
| |||||||||||||||
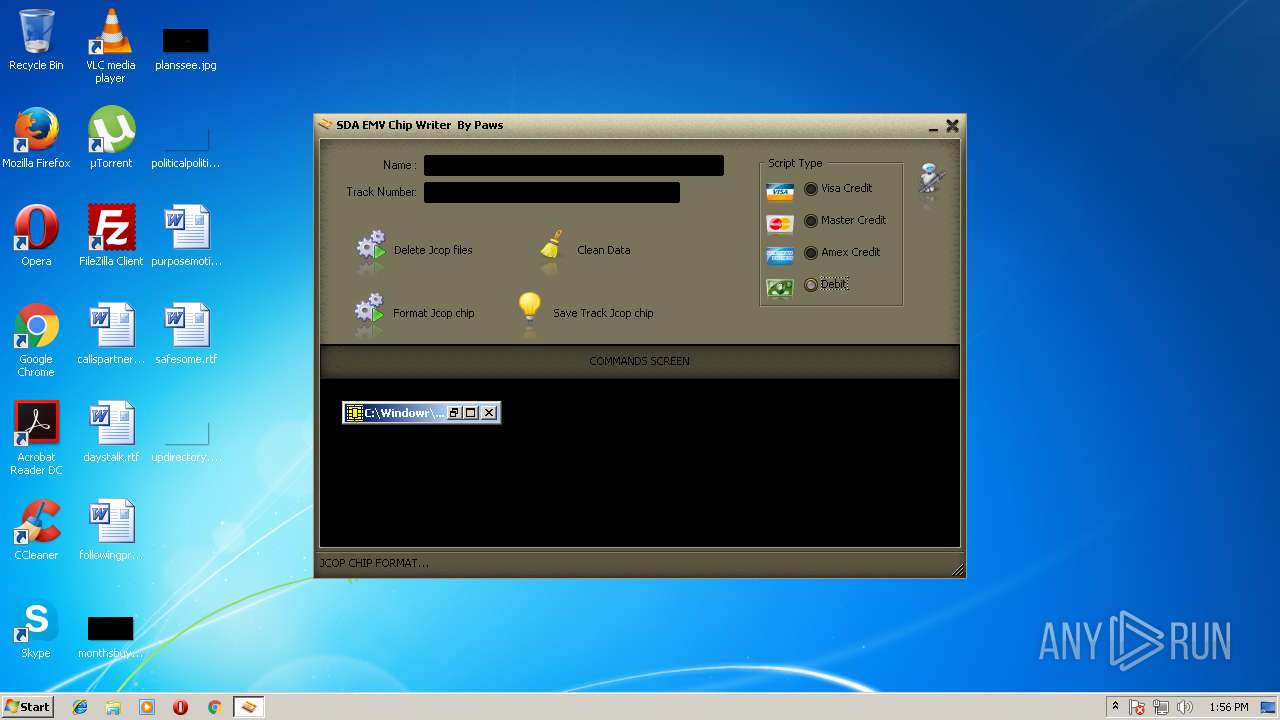
| 1388 | "C:\Windowr\GPShell.exe" apdu.dll | C:\Windowr\GPShell.exe | — | tmp1.jpg | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1, 4, 4, 0 Modules
| |||||||||||||||
| 1612 | C:\Windows\system32\cmd.exe /c start %temp%\tmp2.exe | C:\Windows\system32\cmd.exe | — | jcopenglish.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1832 | "C:\Windowr\GPShell.exe" apdu.dll | C:\Windowr\GPShell.exe | — | tmp1.jpg | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1, 4, 4, 0 Modules
| |||||||||||||||
| 2052 | "C:\Windowr\GPShell.exe" form.dll | C:\Windowr\GPShell.exe | — | tmp1.jpg | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1, 4, 4, 0 Modules
| |||||||||||||||
| 2128 | "C:\Windowr\GPShell.exe" del.dll | C:\Windowr\GPShell.exe | — | tmp1.jpg | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1, 4, 4, 0 Modules
| |||||||||||||||
| 2156 | "C:\Windows\SynTPHelper.exe" | C:\Windows\SynTPHelper.exe | — | SynTPHelper.exe | |||||||||||
User: admin Company: Synaptics Incorporated Integrity Level: HIGH Description: Synaptics Pointing Device Helper Exit code: 0 Version: 19.2.17.59 26Apr17 Modules
| |||||||||||||||
| 2208 | "C:\Windowr\GPShell.exe" apdu.dll | C:\Windowr\GPShell.exe | — | tmp1.jpg | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1, 4, 4, 0 Modules
| |||||||||||||||
| 2220 | "C:\Windowr\GPShell.exe" apdu.dll | C:\Windowr\GPShell.exe | — | tmp1.jpg | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1, 4, 4, 0 Modules
| |||||||||||||||
| 2228 | "C:\Users\admin\AppData\Local\Temp\jcopenglish.exe" | C:\Users\admin\AppData\Local\Temp\jcopenglish.exe | jcopenglish[PremiumFile].exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 123
Read events
1 105
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2720) jcopenglish[PremiumFile].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2720) jcopenglish[PremiumFile].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3036) tmp2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | emv.exe |
Value: C:\Users\admin\AppData\Roaming\Frfx\emv.exe | |||
| (PID) Process: | (3036) tmp2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3036) tmp2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4040) tmp1.jpg | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4040) tmp1.jpg | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1084) SynTPHelper.exe | Key: | HKEY_CURRENT_USER |
| Operation: | write | Name: | di |
Value: ! | |||
| (PID) Process: | (1084) SynTPHelper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1084) SynTPHelper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
13
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2720 | jcopenglish[PremiumFile].exe | C:\Users\admin\AppData\Local\Temp\SynTPHelper.exe | executable | |
MD5:00291C15181BAA184B62938CB519BA4C | SHA256:C4820B44454F5072937047AF8FA53CABE7E21D3FDF0464581A70594B9F2A7F73 | |||
| 4040 | tmp1.jpg | C:\Windowr\del.dll | text | |
MD5:39F489355AC6CCC48A810E2C867475FD | SHA256:71E16A8C9540CBEB6AFC80045A21F7C5954F9E54B5EC731C93AFCA6D67A61646 | |||
| 4040 | tmp1.jpg | C:\Windowr\ssleay32.dll | executable | |
MD5:63D26ECAFCF3B2CEBD5E2F05BCAD553D | SHA256:4F1BAD1A6B9E00473D885BF4E7F3D9D0EC3D91CBDCE05B46F6C6CB2D1FCA8C2B | |||
| 4040 | tmp1.jpg | C:\Windowr\libeay32.dll | executable | |
MD5:A7EFD09E5B963AF88CE2FC5B8EB7127C | SHA256:FA4FB4F5A28BDE9C9CBC4BAA9E737C282799294C65E31D39CDF8E2C758969A70 | |||
| 4040 | tmp1.jpg | C:\Windowr\GPShell.exe | executable | |
MD5:50FCDD91AEE3EC8D7C54FEB63E324C03 | SHA256:BA5E9041668257393AE28413F5099DB5D12D7F48C239E8D19E9BEDA2036B31BE | |||
| 4040 | tmp1.jpg | C:\Windowr\MacGyver.cap | compressed | |
MD5:3709E18B229E3DB113BF5C7863C59DB4 | SHA256:9DC70002E82C78EE34C813597925C6CF8AA8D68B7E9CE5BCC70EA9BCAB9DBF4A | |||
| 4040 | tmp1.jpg | C:\Windowr\zlib1.dll | executable | |
MD5:C7D4D685A0AF2A09CBC21CB474358595 | SHA256:E96B397B499D9EAA3F52EAF496CA8941E80C0AD1544879CCADF02BF2C6A1ECFC | |||
| 4040 | tmp1.jpg | C:\Windowr\form.dll | text | |
MD5:20640673B59B3E298D00899F8EE77079 | SHA256:58C92AE2DE19A77BEA6F8A934FC317310E33030C93A01205BB375CBAE3E5706D | |||
| 1084 | SynTPHelper.exe | C:\Windows\SynTPHelper.exe | executable | |
MD5:00291C15181BAA184B62938CB519BA4C | SHA256:C4820B44454F5072937047AF8FA53CABE7E21D3FDF0464581A70594B9F2A7F73 | |||
| 2228 | jcopenglish.exe | C:\Users\admin\AppData\Local\Temp\tmp2.exe | executable | |
MD5:913157F29B94106F5B6DB18D04EB3C41 | SHA256:CC4CD74A7DB7EDD8A16DA7FF6FCCF491BF61CC19AC73AAE5843C56821D09272F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report