| File name: | index.html |
| Full analysis: | https://app.any.run/tasks/85e5957b-050b-48e7-b139-97bf941be060 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2019, 22:56:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | 4F0AFDEE5D76B09288FCFD8168329487 |
| SHA1: | 0379AAD65FF379F981B498AE12083C2D5C6CC459 |
| SHA256: | D682B05C19D96C99EB442D32B4686E8CEB6C88052C89F1ECC72B6822D9600CB8 |
| SSDEEP: | 1536:xph1P+y/n9L4ulrrb8UbCBqb8OqXGqXhqXrqXqqXpqXob8bqXBqXSqX3qXKb80Ad:Hh1P+Wnl4ulAjr3XPXsXuXzX0XXeXMXO |
MALICIOUS
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 1844)
- CCleaner.exe (PID: 848)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 2768)
- CCleaner.exe (PID: 848)
Changes the autorun value in the registry
- CCleaner.exe (PID: 848)
SUSPICIOUS
Executed via Task Scheduler
- CCleaner.exe (PID: 2768)
Reads internet explorer settings
- CCleaner.exe (PID: 2768)
- CCleaner.exe (PID: 848)
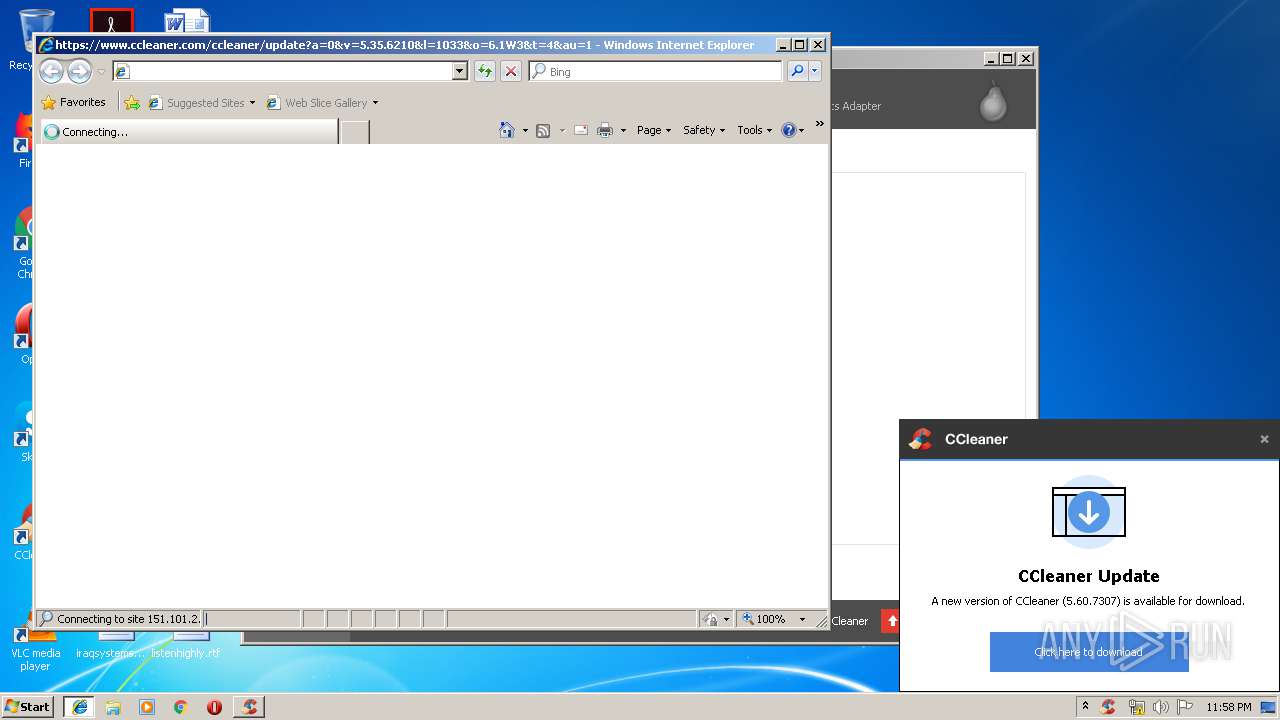
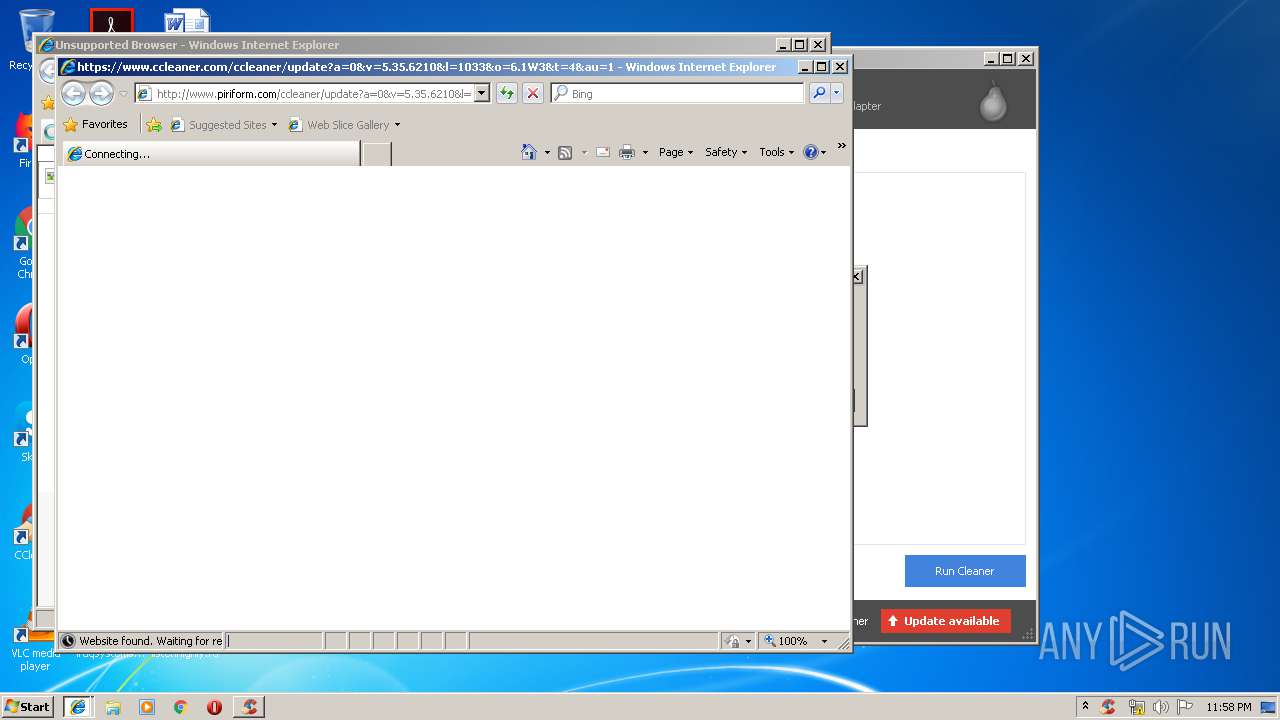
Starts Internet Explorer
- CCleaner.exe (PID: 2768)
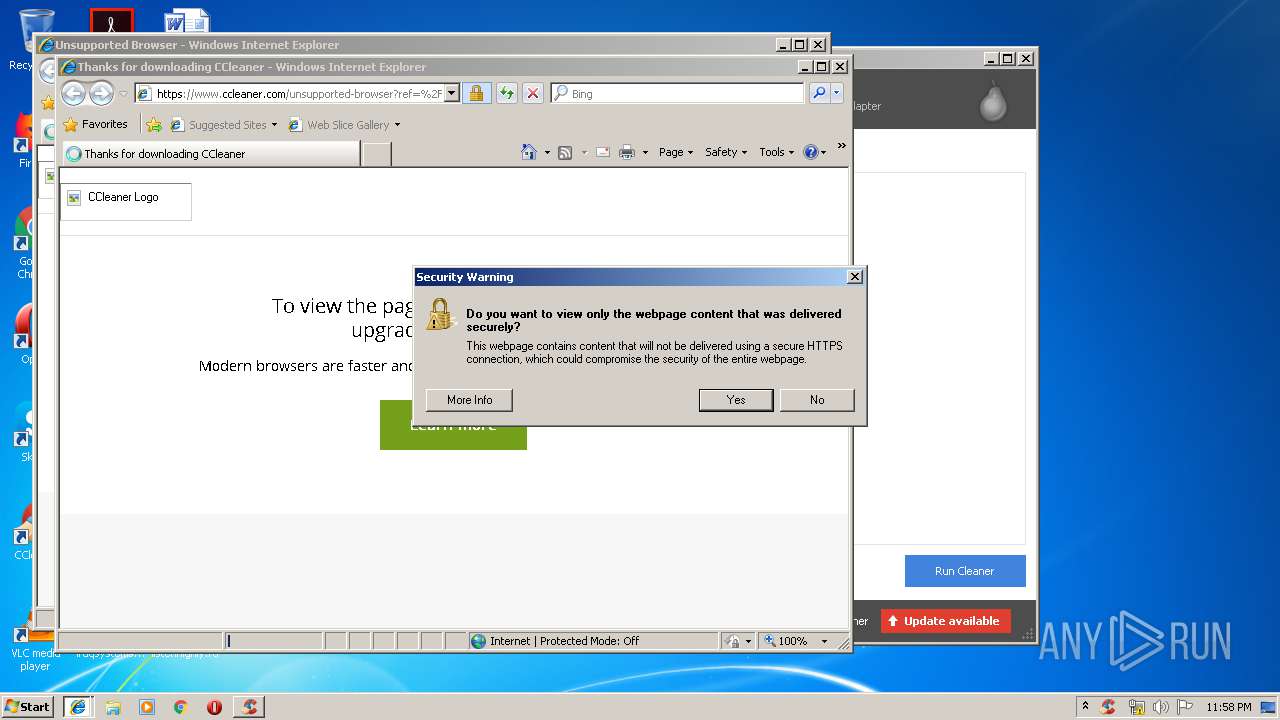
Creates files in the user directory
- CCleaner.exe (PID: 2768)
Application launched itself
- CCleaner.exe (PID: 2768)
Reads the cookies of Google Chrome
- CCleaner.exe (PID: 2768)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 2768)
Reads the cookies of Mozilla Firefox
- CCleaner.exe (PID: 2768)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 3480)
- iexplore.exe (PID: 2052)
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 3948)
- iexplore.exe (PID: 2948)
Changes internet zones settings
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 3672)
Reads settings of System Certificates
- iexplore.exe (PID: 3480)
- iexplore.exe (PID: 2812)
- CCleaner.exe (PID: 2768)
Reads Internet Cache Settings
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 2052)
- iexplore.exe (PID: 3480)
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 2948)
- iexplore.exe (PID: 3672)
Application launched itself
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 3672)
Creates files in the user directory
- iexplore.exe (PID: 2052)
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 3948)
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 2948)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2052)
Manual execution by user
- CCleaner.exe (PID: 1844)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2396)
Changes settings of System certificates
- iexplore.exe (PID: 2396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| Title: | Home - Spybot Anti-Malware and Antivirus : Spybot Anti-Malware and Antivirus |
|---|---|
| HTTPEquivXUACompatible: | IE=edge,chrome=1 |
| viewport: | width=device-width, initial-scale=1.0 |
| Description: | Spybot offers a unique technology for your security. Far beyond antivirus Spybot searches and destroys unwanted software and protects your privacy. |
| twitterCard: | summary_large_image |
| twitterDescription: | Spybot offers a unique technology for your security. Far beyond antivirus Spybot searches and destroys unwanted software and protects your privacy. |
| twitterTitle: | Home - Spybot Anti-Malware and Antivirus |
| twitterSite: | @SpybotSD |
| twitterImage: | https://www.safer-networking.org/wp-content/uploads/2018/08/SpybotHome01.jpg |
| twitterCreator: | @SpybotSD |
| msvalidate01: | 11AA582CA73B81677B7BC2E7500B72DF |
| yandexVerification: | 94b93249c2b2d365 |
| HTTPEquivXClacksOverhead: | GNU Terry Pratchett |
| Generator: | EDD DP v1.4.8 |
Total processes
46
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Program Files\CCleaner\CCleaner.exe" /monitor | C:\Program Files\CCleaner\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 1844 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2756 CREDAT:268545 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:79874 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2768 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2756 CREDAT:14339 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2948 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:145409 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3480 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2756 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3672 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | — | CCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 275
Read events
1 761
Write events
510
Delete events
4
Modification events
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070800060011001600380028007201 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2756) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {4588E015-C142-11E9-B86F-5254004A04AF} |
Value: 0 | |||
Executable files
0
Suspicious files
12
Text files
117
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2756 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2756 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\style.1553000490[1].css | — | |
MD5:— | SHA256:— | |||
| 3480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\style.1553000490[1].css | text | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\work-sans-v3-latin-ext_latin-600[1].eot | eot | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\work-sans-v3-latin-ext_latin-300[1].eot | eot | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\work-sans-v3-latin-ext_latin-regular[1].eot | eot | |
MD5:— | SHA256:— | |||
| 2756 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 3480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\cookie-law-info-public.1562225018[1].css | text | |
MD5:BFE76D662A875D5559147021E126A0B5 | SHA256:81E82457FB12EF9A7B3981ECEBA4363763A703FD04BBE4DA183903FD74E2CBCD | |||
| 3480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\frontend.1529135204[1].css | text | |
MD5:0E161E16D789BF14DDA632172D231FDD | SHA256:7E57269BDD2CE18D1CFF1A6D1B8F64411DE43D165B66FE33BB3C1E72C350D0BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
102
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=176FFA7675534AFCB58660D126A9861B&CID=3B45C4823B83621F3EBBC9393AAB63E5&Type=Event.CPT&DATA={"pp":{"S":"L","FC":47,"BC":125,"SE":-1,"TC":-1,"H":156,"BP":219,"CT":234,"IL":3},"ad":[-1,-1,772,444,1089,498,0]}&P=SERP&DA=DUB02 | US | image | 5.73 Kb | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/6n/53/cj,nj/dd882357/b8881a70.js | US | text | 1.77 Kb | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=176FFA7675534AFCB58660D126A9861B&CID=3B45C4823B83621F3EBBC9393AAB63E5&Type=Event.ClientInst&DATA=[{"T":"CI.GetError","FID":"CI","Name":"JSGetError","Text":"%27SVGElement%27%20is%20undefined","Meta":"http%3A//www.bing.com/search%3Fq%3Dnon-necessary++%26src%3DIE-SearchBox%26FORM%3DIE8SRC","Line":9668927,"Char":%20undefined}] | US | compressed | 773 b | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/30/2R/cj,nj/3f1e2270/f8c6dd44.js | US | text | 773 b | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=non-necessary++&src=IE-SearchBox&FORM=IE8SRC | US | html | 32.2 Kb | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/30/1V/cj,nj/4c7364c5/40e1b425.js | US | text | 816 b | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/5k/cj,nj/c44ec255/9a358300.js?bu=EqsfzB_vHvoe3QSGH4gf5B-KH5Ufmx-_H7kfxR-fHrYdvB2qHg | US | text | 4.95 Kb | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/SharedSpriteDesktopRewards_022118.png | US | image | 5.73 Kb | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5b/2r/cj,nj/08abbb2f/e177b199.js | US | text | 2.86 Kb | whitelisted |
2052 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/Passport.aspx?popup=1 | US | html | 230 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2052 | iexplore.exe | 40.90.23.208:443 | login.live.com | Microsoft Corporation | US | unknown |
2052 | iexplore.exe | 13.107.3.254:80 | 06f5f949bcf61466d3c4974e31958e39.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
2052 | iexplore.exe | 104.211.224.23:80 | 890c8bb8358b6ebe48b6dfb9d4d24b6f.clo.footprintdns.com | Microsoft Corporation | IN | whitelisted |
2052 | iexplore.exe | 52.231.32.10:80 | 100413694e62feb2b2d01d8332d14faf.clo.footprintdns.com | Microsoft Corporation | KR | whitelisted |
2768 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
2768 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
2052 | iexplore.exe | 204.79.197.222:80 | fp.msedge.net | Microsoft Corporation | US | whitelisted |
2756 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3480 | iexplore.exe | 167.114.117.64:443 | www.safer-networking.org | OVH SAS | CA | unknown |
2812 | iexplore.exe | 167.114.117.64:443 | www.safer-networking.org | OVH SAS | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.safer-networking.org |
| whitelisted |
www.paypalobjects.com |
| whitelisted |
s.w.org |
| whitelisted |
login.live.com |
| whitelisted |
890c8bb8358b6ebe48b6dfb9d4d24b6f.clo.footprintdns.com |
| unknown |
06f5f949bcf61466d3c4974e31958e39.clo.footprintdns.com |
| suspicious |
100413694e62feb2b2d01d8332d14faf.clo.footprintdns.com |
| unknown |
fp.msedge.net |
| whitelisted |
www.piriform.com |
| whitelisted |