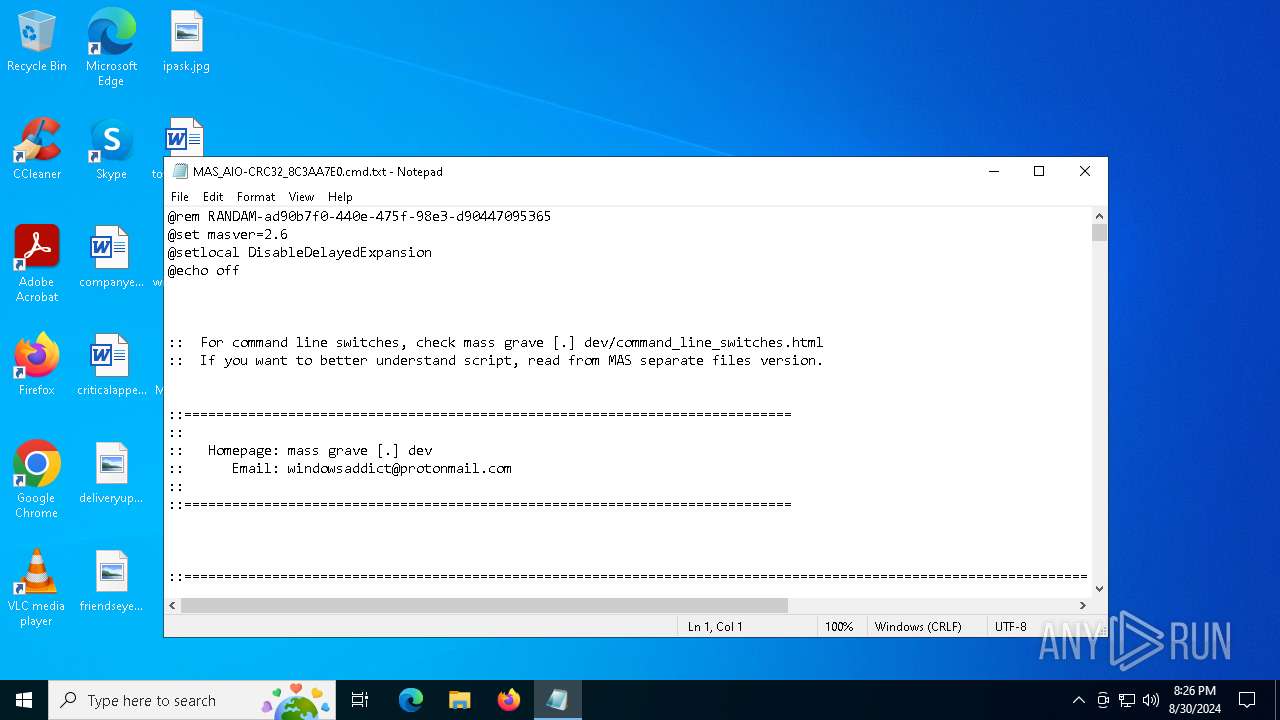
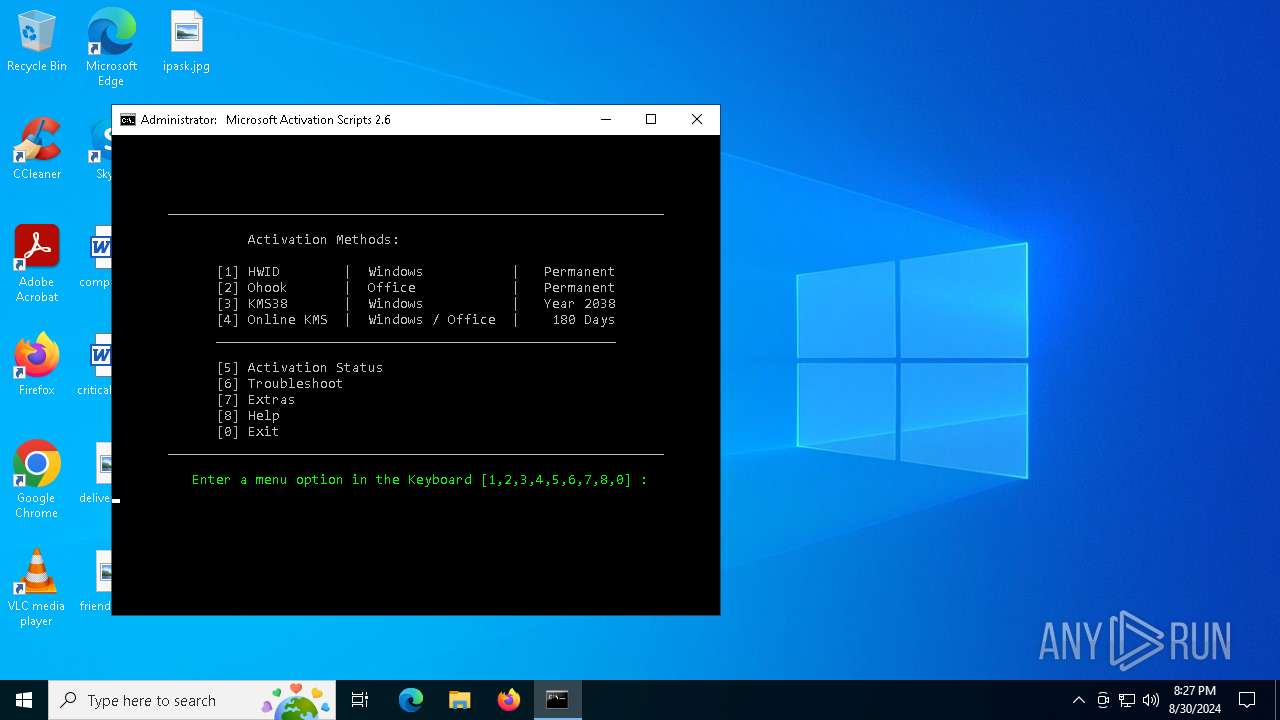
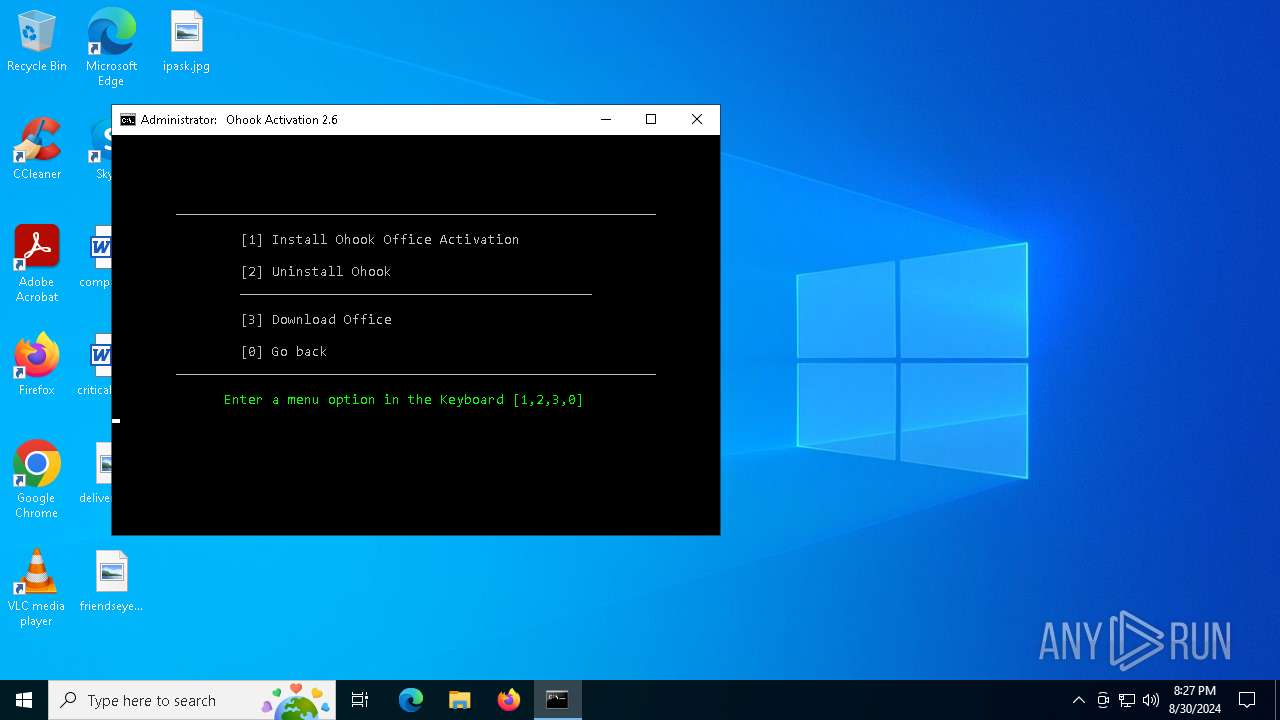
| File name: | MAS_AIO-CRC32_8C3AA7E0.cmd |
| Full analysis: | https://app.any.run/tasks/aa7c7431-0758-4ba4-961d-6821d62b33cd |
| Verdict: | Malicious activity |
| Analysis date: | August 30, 2024, 20:26:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (311), with CRLF line terminators |
| MD5: | 92CC8F1F67A875563D1299E7DD7B5723 |
| SHA1: | BEE4ADFE87603F91067B9F868F7F42B34B2FBDEB |
| SHA256: | D666A4C7810B9D3FE9749F2D4E15C5A65D4AC0D7F0B14A144D6631CE61CC5DF3 |
| SSDEEP: | 3072:O/dR3S9mF2TJRMP0u+RciNiYFRd8nVFR3mP5sLtV7bJuAMTVFp6zGDNSCE2K0xOn:UAnHu+R7VLo97bJu9p6zGDNS0KgOuCV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4540)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 5988)
- powershell.exe (PID: 368)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 964)
- cmd.exe (PID: 3728)
- cmd.exe (PID: 6708)
Application launched itself
- cmd.exe (PID: 4540)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 964)
- cmd.exe (PID: 6708)
- cmd.exe (PID: 3728)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4540)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 3672)
Starts SC.EXE for service management
- cmd.exe (PID: 4540)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 4080)
Executing commands from ".cmd" file
- cmd.exe (PID: 4540)
- cmd.exe (PID: 4080)
- powershell.exe (PID: 368)
- cmd.exe (PID: 5988)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4540)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 4008)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4080)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 3672)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4008)
- cmd.exe (PID: 5988)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 5988)
Hides command output
- cmd.exe (PID: 4008)
- cmd.exe (PID: 2476)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 788)
- cmd.exe (PID: 6556)
- cmd.exe (PID: 568)
- cmd.exe (PID: 6380)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 6140)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 3972)
- cmd.exe (PID: 4708)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 5476)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 3672)
- cmd.exe (PID: 368)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4008)
- cmd.exe (PID: 5988)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6984)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6984)
The process creates files with name similar to system file names
- Dism.exe (PID: 6800)
Process drops legitimate windows executable
- Dism.exe (PID: 6800)
Executable content was dropped or overwritten
- Dism.exe (PID: 6800)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 32)
The process executes VB scripts
- cmd.exe (PID: 5988)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4060)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 4060)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 4060)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 5212)
- cmd.exe (PID: 6556)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 5988)
INFO
Checks operating system version
- cmd.exe (PID: 4540)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 4080)
Manual execution by a user
- cmd.exe (PID: 4540)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2816)
- WMIC.exe (PID: 6724)
- cscript.exe (PID: 4060)
- WMIC.exe (PID: 6500)
- WMIC.exe (PID: 4088)
- WMIC.exe (PID: 3672)
- WMIC.exe (PID: 6984)
- WMIC.exe (PID: 5096)
- WMIC.exe (PID: 6504)
- WMIC.exe (PID: 6452)
The process uses the downloaded file
- powershell.exe (PID: 368)
Checks supported languages
- mode.com (PID: 2056)
- mode.com (PID: 6852)
- mode.com (PID: 5164)
- DismHost.exe (PID: 32)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6984)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6984)
Reads the computer name
- DismHost.exe (PID: 32)
Reads Environment values
- DismHost.exe (PID: 32)
Create files in a temporary directory
- Dism.exe (PID: 6800)
Reads Microsoft Office registry keys
- reg.exe (PID: 3832)
- reg.exe (PID: 1700)
- reg.exe (PID: 6780)
- reg.exe (PID: 888)
- reg.exe (PID: 7040)
- reg.exe (PID: 6196)
Creates files in the program directory
- cmd.exe (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
346
Monitored processes
216
Malicious processes
6
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | C:\Users\admin\AppData\Local\Temp\6421217B-3C08-4393-A613-9135440696B9\dismhost.exe {C6D017A7-BAF7-4BA7-A076-C4E5416A4109} | C:\Users\admin\AppData\Local\Temp\6421217B-3C08-4393-A613-9135440696B9\DismHost.exe | Dism.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | fltmc | C:\Windows\System32\fltMC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Filter Manager Control Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | cmd /c exit /b 0 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | powershell.exe "start cmd.exe -arg '/c \""""C:\Users\admin\Desktop\MAS_AIO-CRC32_8C3AA7E0.cmd.cmd""" -el \"' -verb runas" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\ClickToRun /v InstallPath" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "127.69.2.6" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\ClickToRun /v InstallPath" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | powershell.exe "$acl = Get-Acl '"C:\WINDOWS\System32\spp\store\2.0"'; if ($acl.Access.Where{ $_.IdentityReference -eq 'NT SERVICE\sppsvc' -and $_.AccessControlType -eq 'Deny' -or $acl.Access.IdentityReference -notcontains 'NT SERVICE\sppsvc'}) {Exit 2}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
53 144
Read events
53 131
Write events
13
Delete events
0
Modification events
| (PID) Process: | (368) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (368) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (368) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (368) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2768) reg.exe | Key: | HKEY_CURRENT_USER\Console |
| Operation: | write | Name: | QuickEdit |
Value: 0 | |||
| (PID) Process: | (6552) reg.exe | Key: | HKEY_CURRENT_USER\Console |
| Operation: | write | Name: | QuickEdit |
Value: 1 | |||
| (PID) Process: | (1496) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SideBySide |
| Operation: | write | Name: | LastScavengingStarvationReport |
Value: 3314B4101BFBDA01 | |||
| (PID) Process: | (1496) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31128347 | |||
| (PID) Process: | (1496) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 280237107 | |||
Executable files
50
Suspicious files
1
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_o3neudbt.zbk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qlpaiso1.rlj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_32nmvmo0.prf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6660 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nglsskod.nfj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2rtq1m1m.0da.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6800 | Dism.exe | C:\Users\admin\AppData\Local\Temp\6421217B-3C08-4393-A613-9135440696B9\AssocProvider.dll | executable | |
MD5:B7DB592706D3EEFBCF0D5A166D462E56 | SHA256:DE21321272862E7C332E1724DC315F06F3ABE7A0340E61D351CAB208D6BBF059 | |||
| 6800 | Dism.exe | C:\Users\admin\AppData\Local\Temp\6421217B-3C08-4393-A613-9135440696B9\DmiProvider.dll | executable | |
MD5:0C2E5696F987350B0AE36E692D10FFB2 | SHA256:52FD26A88D386B906CD1034DF69618195E98A3A2743FE4AA185C461B24D5EBA3 | |||
| 6800 | Dism.exe | C:\Users\admin\AppData\Local\Temp\6421217B-3C08-4393-A613-9135440696B9\CbsProvider.dll | executable | |
MD5:14932441A96E254B3D29D452CE1263A0 | SHA256:8FFF21CB7C88A0DD8C8E7B386604001F2974E75D229369A87BEE0BA18DA575F3 | |||
| 6268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_b5ubfpkc.2ow.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6800 | Dism.exe | C:\Users\admin\AppData\Local\Temp\6421217B-3C08-4393-A613-9135440696B9\DismCore.dll | executable | |
MD5:681186B5696BA7D46B6681C027A659AD | SHA256:FBB5135DE4F6A5C9422A0B218D676930DB9BC9A2AEA0F7219077862912455914 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
27
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6308 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6308 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1280 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6880 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6552 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6880 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1280 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6308 | SIHClient.exe | 40.68.123.157:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
updatecheck.massgrave.dev |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=6800 TID=3832 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=6800 TID=3832 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6800 TID=3832 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6800 TID=3832 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6800 TID=3832 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6800 TID=3832 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=32 TID=2400 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=32 TID=2400 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=32 TID=2400 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=6800 TID=3832 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |