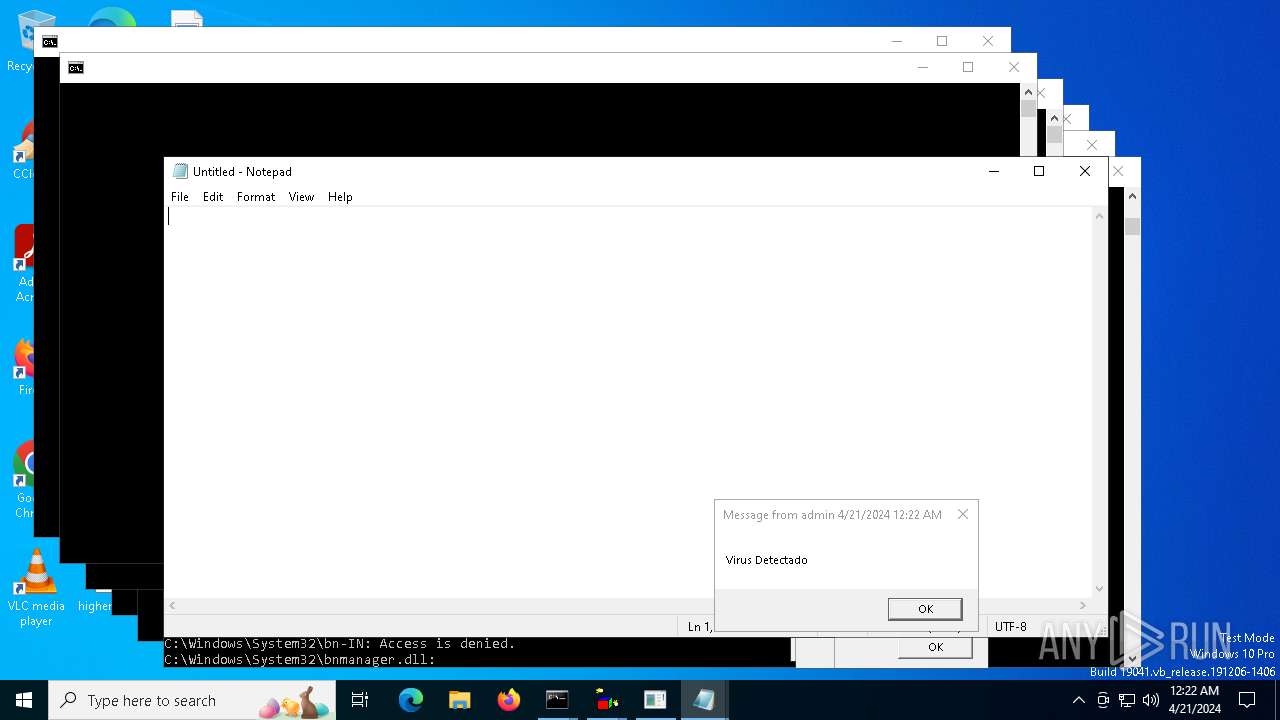
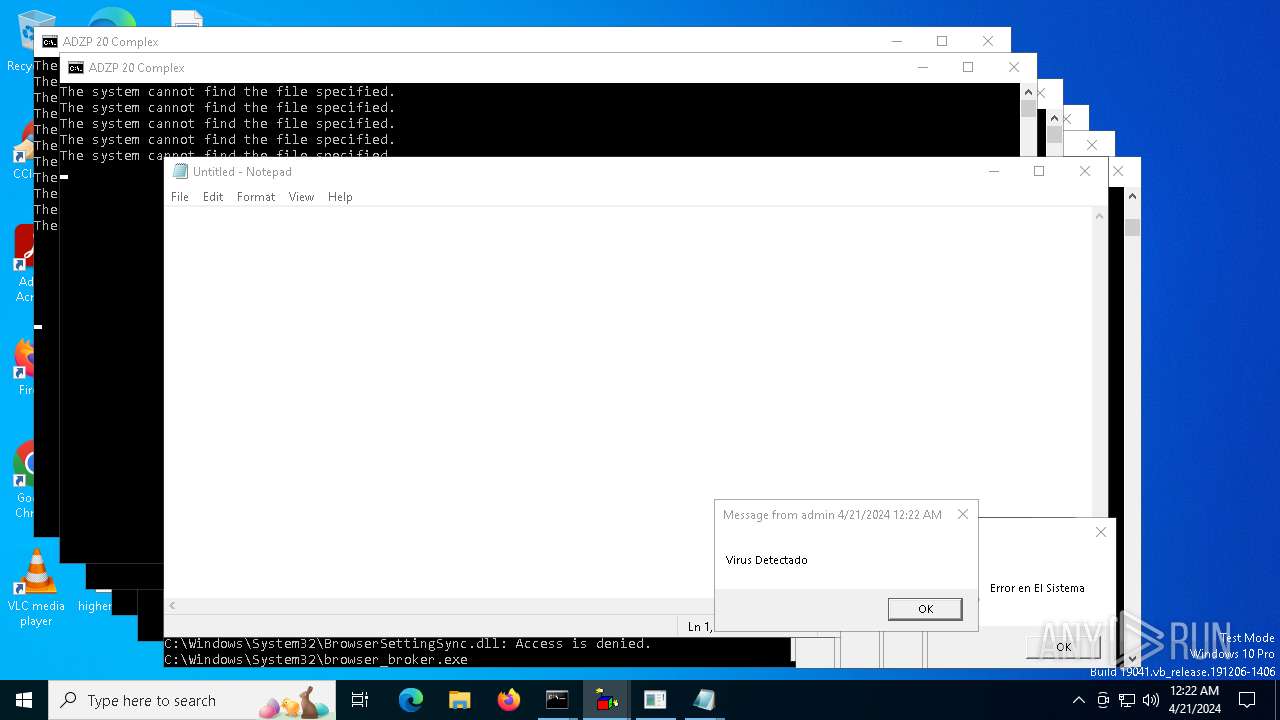
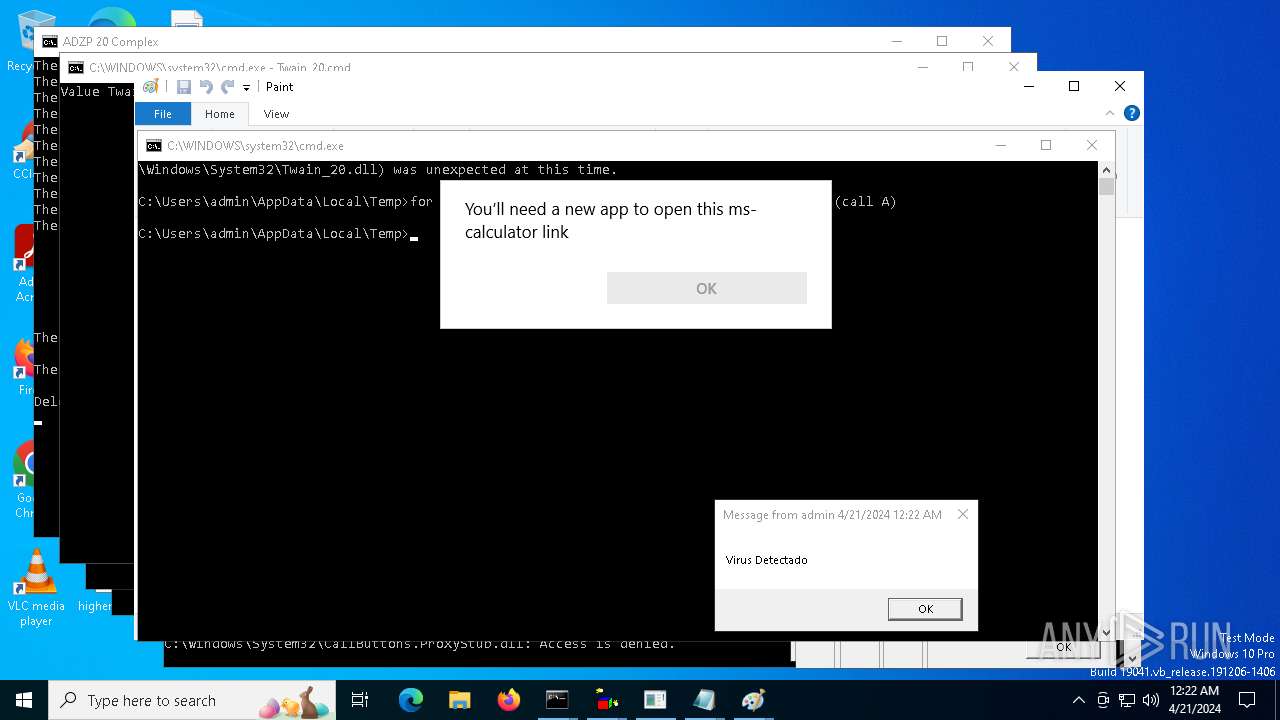
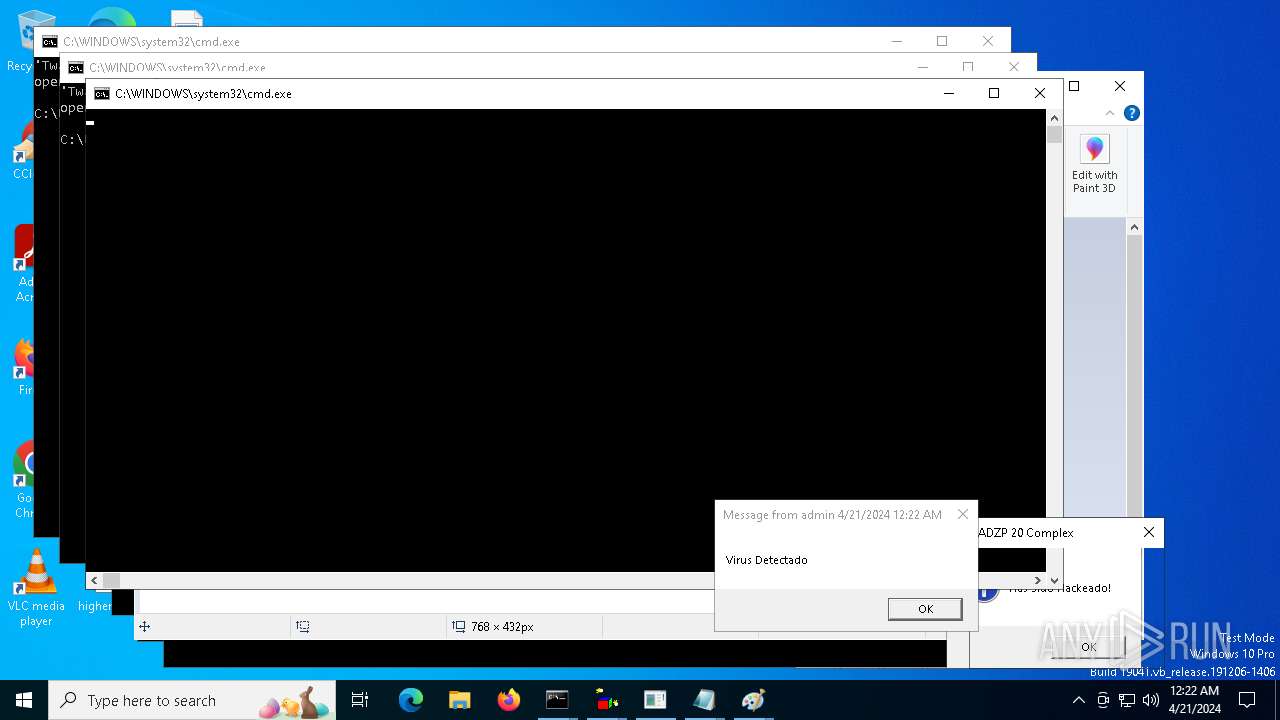
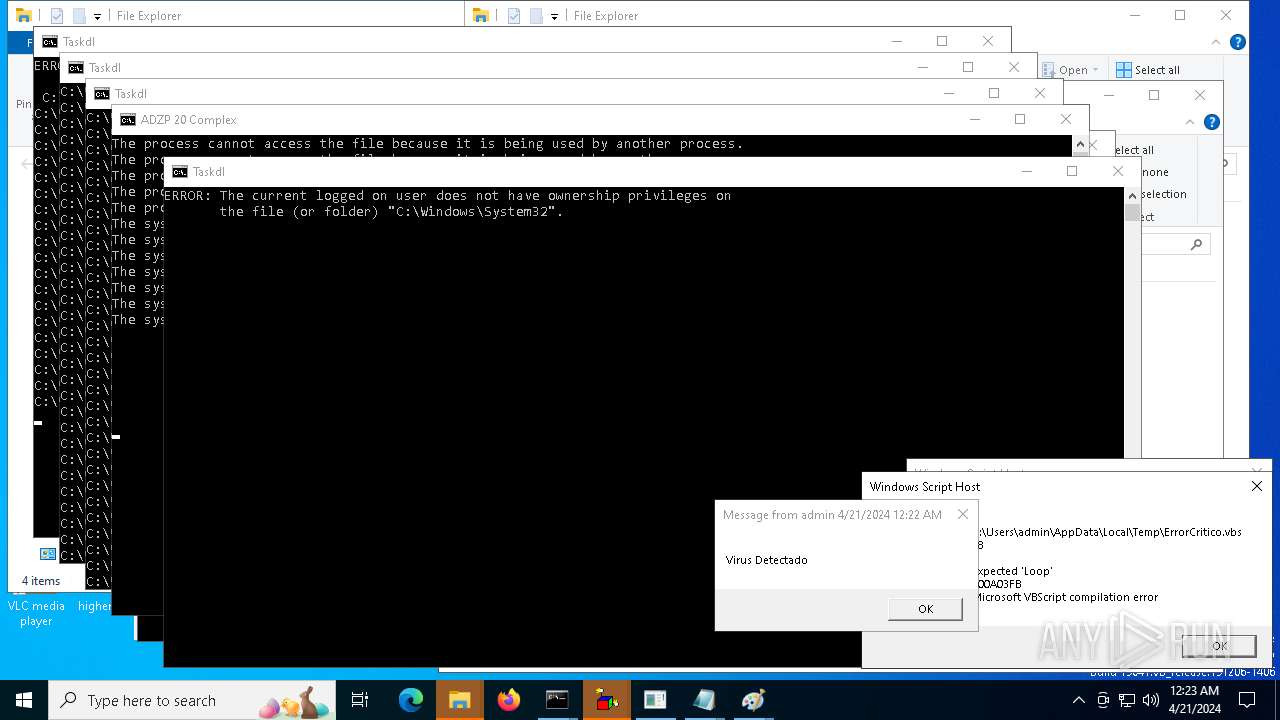
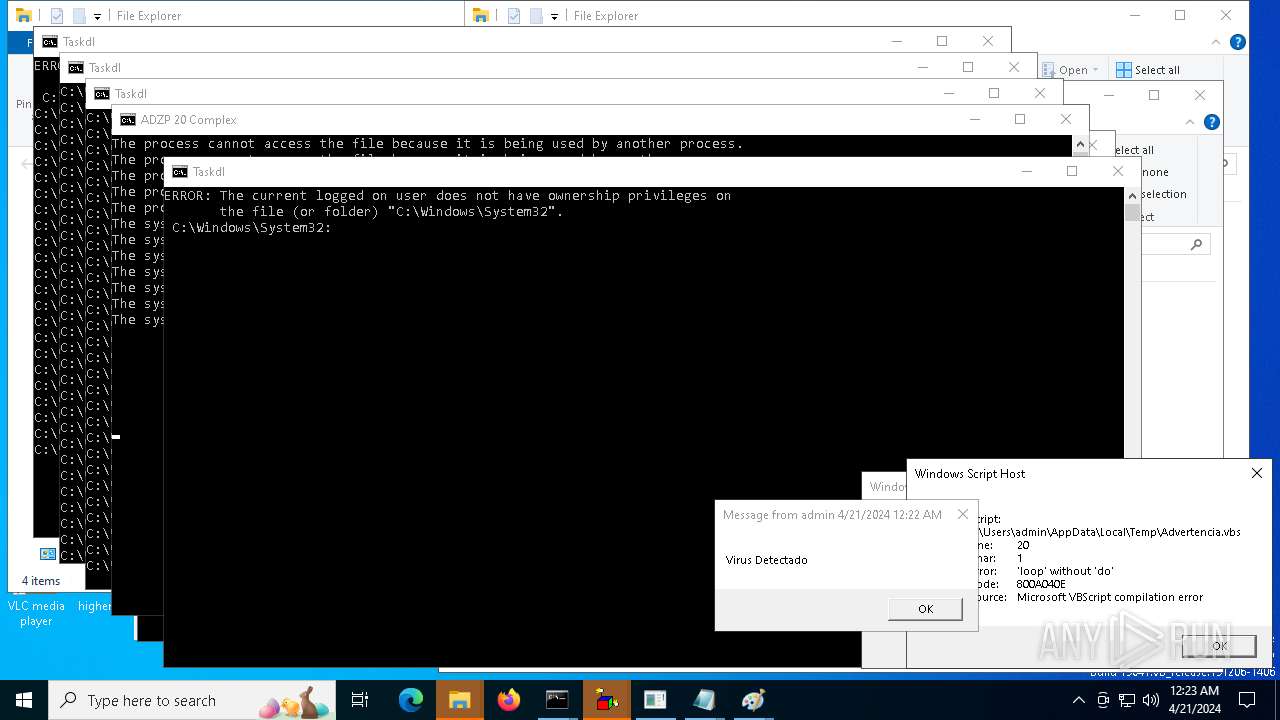
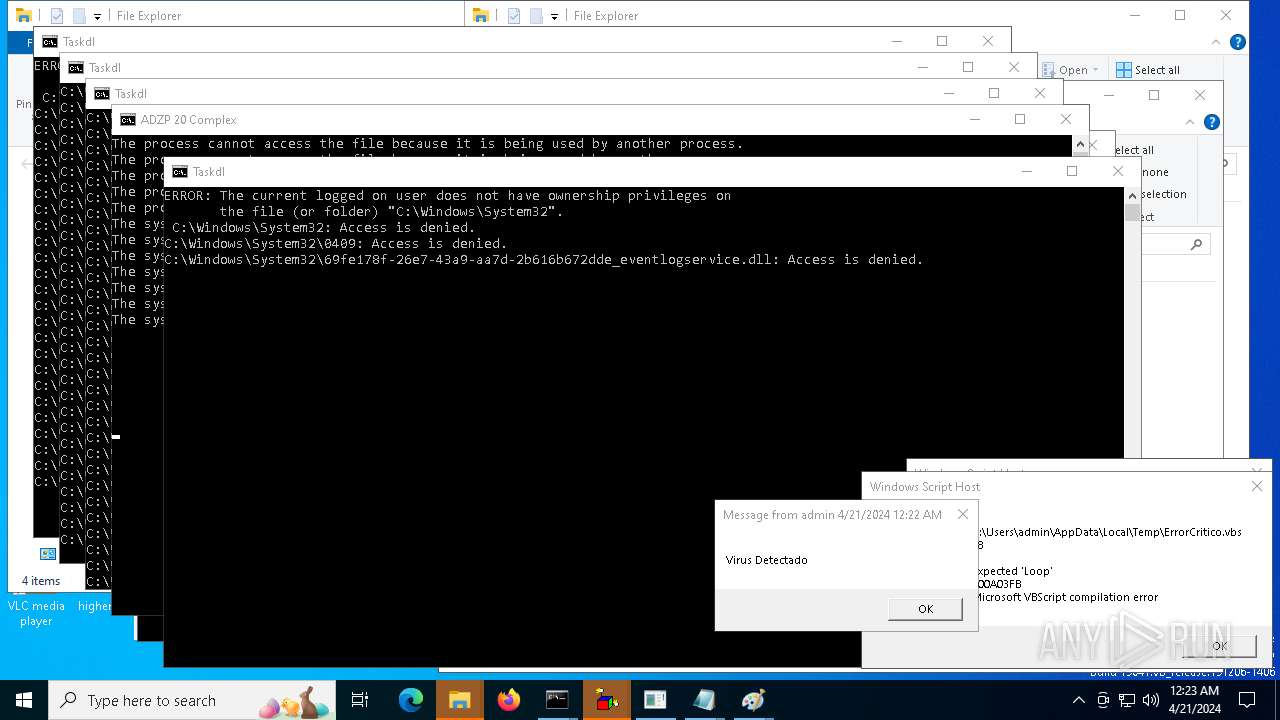
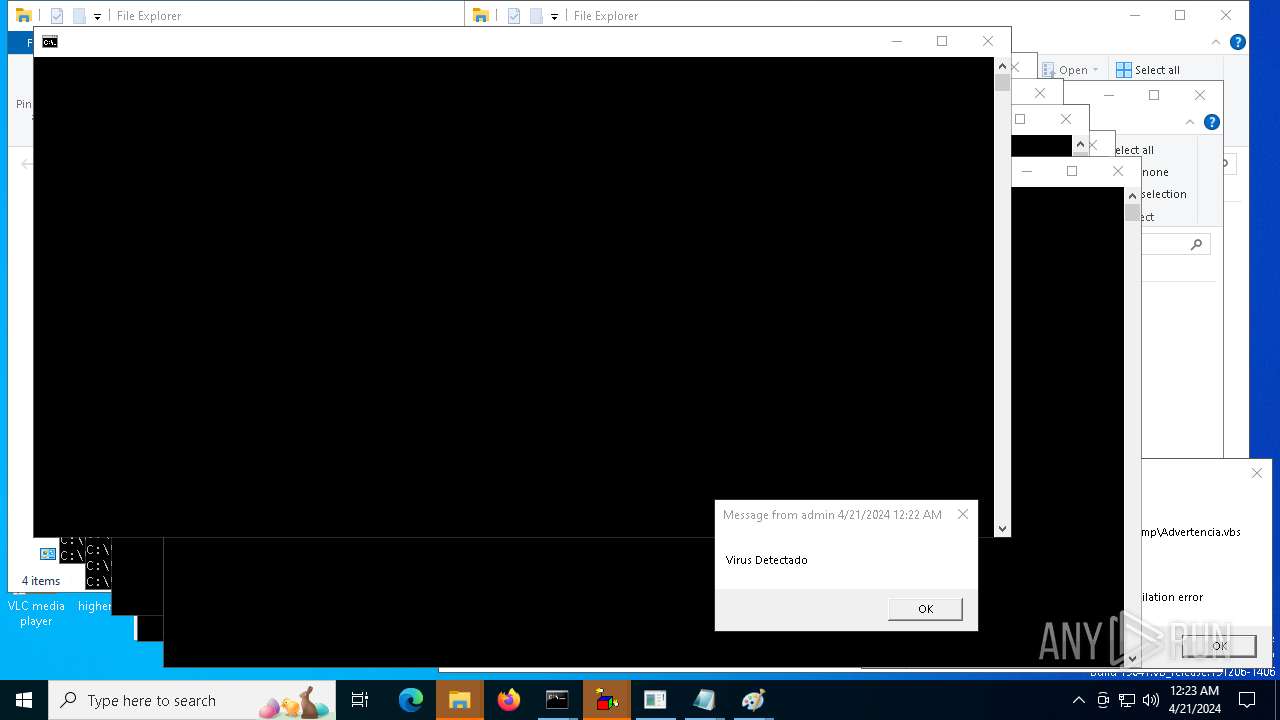
| File name: | d6607a9ec5fc0698f50382ffe61a4ad1f36a8b26c0834c305f40e41647980668.vbs |
| Full analysis: | https://app.any.run/tasks/ad8fdeef-b368-4048-a16f-c906fcab987c |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2024, 00:22:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 36DECA5BD53F31D062D07C1D3FA0CC8D |
| SHA1: | 1D245DE03D3725B180F572B15036CBB168445EDF |
| SHA256: | D6607A9EC5FC0698F50382FFE61A4AD1F36A8B26C0834C305F40E41647980668 |
| SSDEEP: | 384:WO9h4Bbs9odeP93e6xj6BT2xg2mP+CMdNLjl9NQJW:lZ+kPxe6x+BT22FGCMdtZoW |
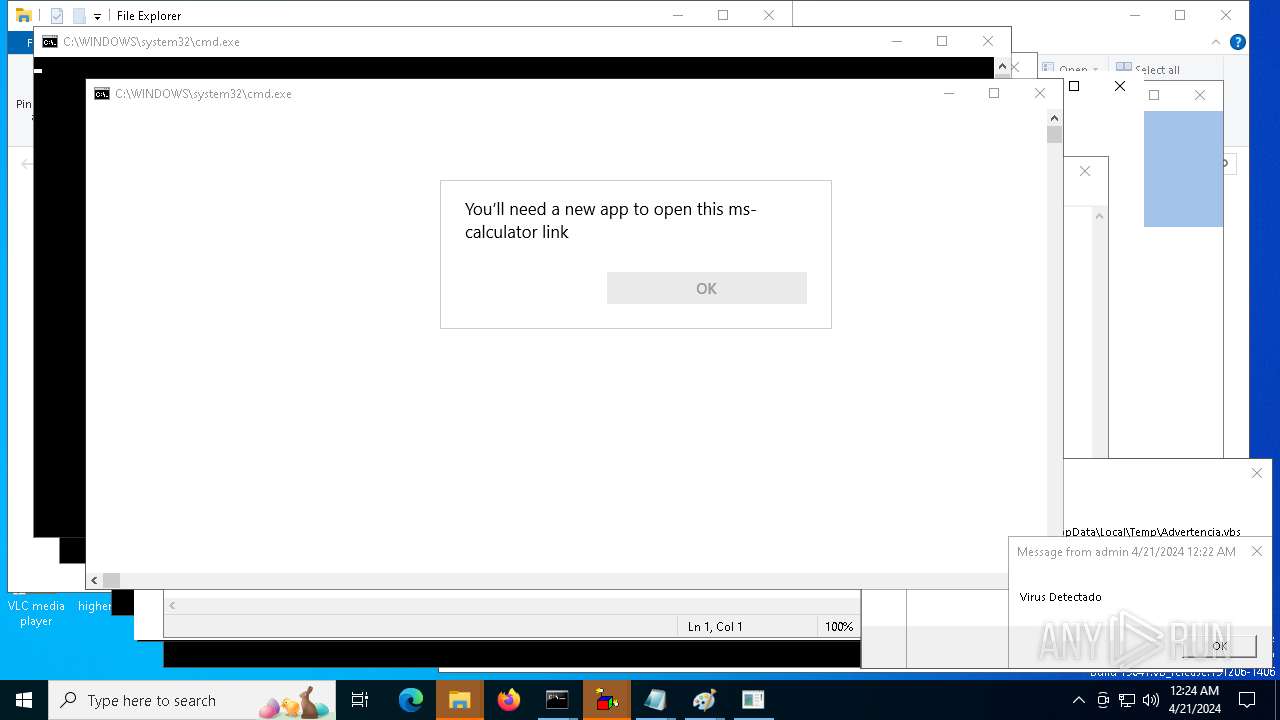
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 980)
Actions looks like stealing of personal data
- cmd.exe (PID: 2212)
- cmd.exe (PID: 2304)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 4000)
Executing commands from a ".bat" file
- wscript.exe (PID: 4000)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 16808)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 14424)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4000)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 16808)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 14424)
- cmd.exe (PID: 14152)
- cmd.exe (PID: 17452)
- cmd.exe (PID: 13520)
- cmd.exe (PID: 13784)
- cmd.exe (PID: 15184)
- cmd.exe (PID: 15620)
Application launched itself
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 16808)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 14424)
- cmd.exe (PID: 14152)
- cmd.exe (PID: 17452)
- cmd.exe (PID: 13520)
- cmd.exe (PID: 13784)
- cmd.exe (PID: 15620)
- cmd.exe (PID: 15184)
Executing commands from ".cmd" file
- cmd.exe (PID: 2304)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 16808)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 14152)
- cmd.exe (PID: 14424)
- cmd.exe (PID: 17452)
- cmd.exe (PID: 13520)
- cmd.exe (PID: 13784)
- cmd.exe (PID: 15184)
- cmd.exe (PID: 15620)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 4000)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6788)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 7420)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 10088)
- cmd.exe (PID: 11316)
- cmd.exe (PID: 11340)
- cmd.exe (PID: 11460)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 11308)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 13288)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 16820)
- cmd.exe (PID: 16916)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 15028)
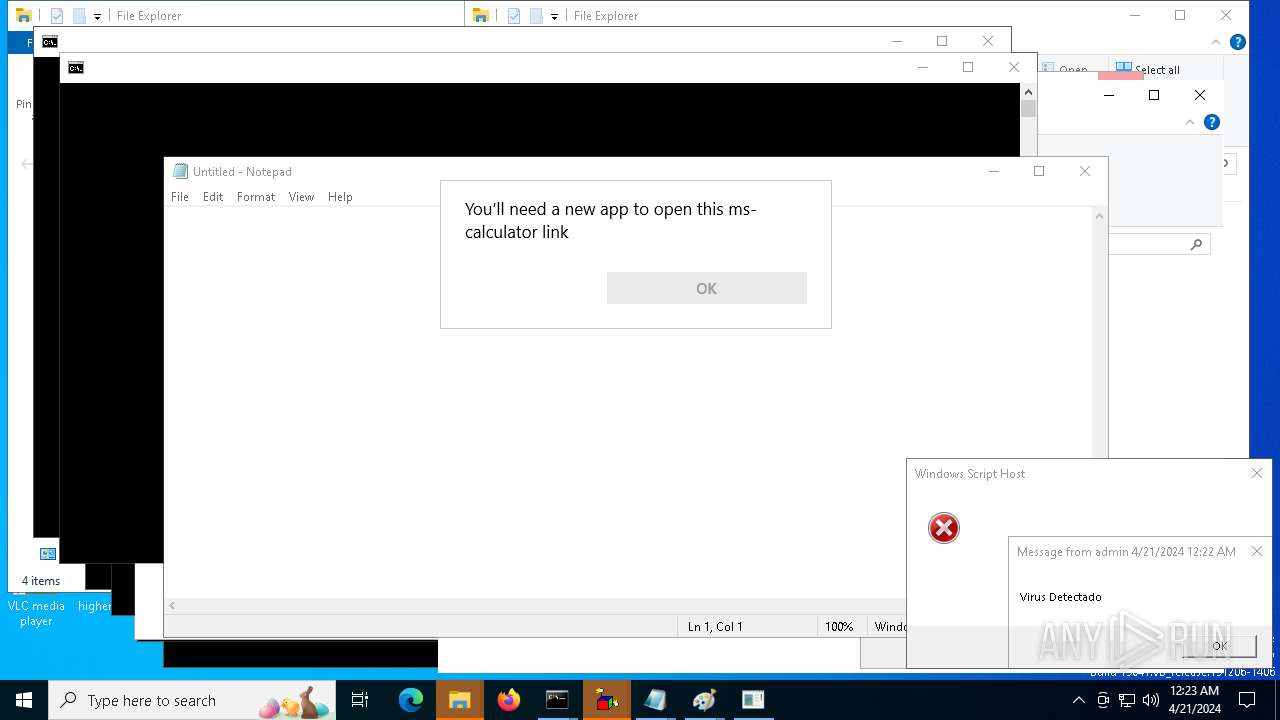
The process executes VB scripts
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 16808)
- cmd.exe (PID: 14424)
- cmd.exe (PID: 11300)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 16808)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 14152)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 14424)
- cmd.exe (PID: 13784)
- cmd.exe (PID: 13520)
- cmd.exe (PID: 17452)
- cmd.exe (PID: 15620)
- cmd.exe (PID: 15184)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 2304)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 14724)
- cmd.exe (PID: 15028)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2304)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 6268)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9316)
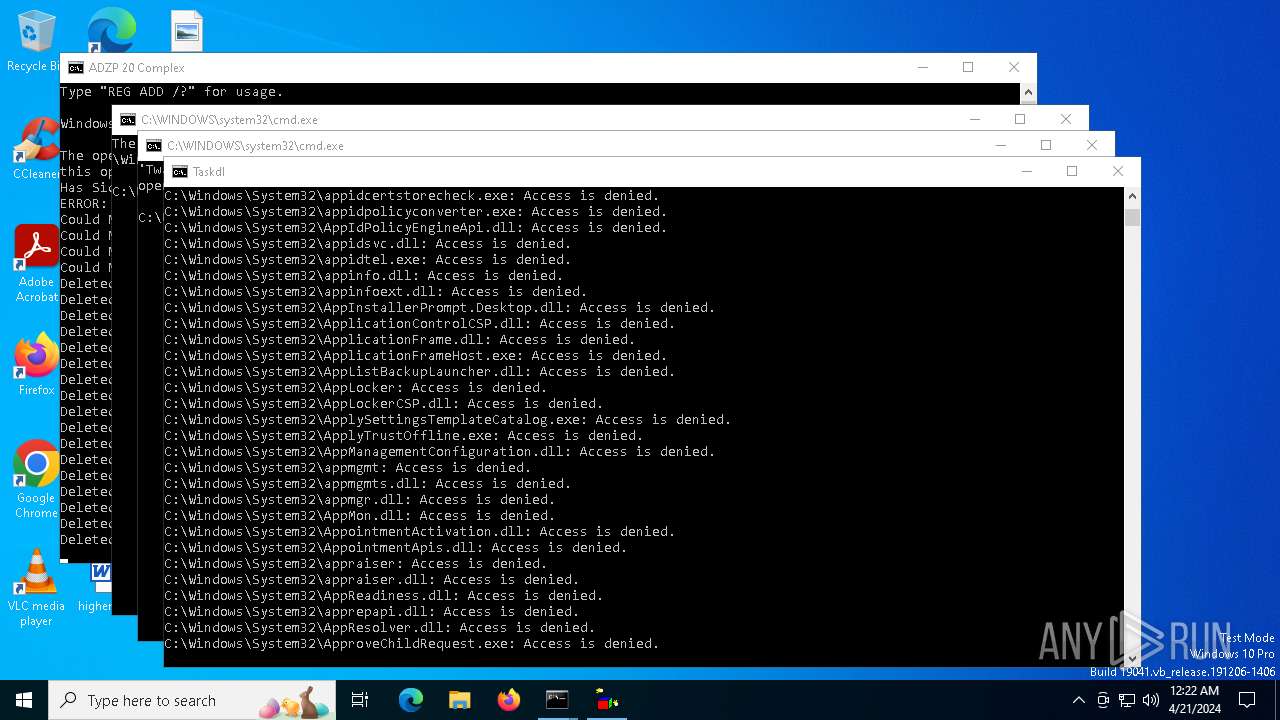
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 8020)
- cmd.exe (PID: 1592)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 8256)
- cmd.exe (PID: 11184)
- cmd.exe (PID: 10156)
- cmd.exe (PID: 12424)
- cmd.exe (PID: 12384)
- cmd.exe (PID: 13604)
- cmd.exe (PID: 12300)
- cmd.exe (PID: 12392)
- cmd.exe (PID: 19176)
- cmd.exe (PID: 19108)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 8020)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 1592)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 11184)
- cmd.exe (PID: 8256)
- cmd.exe (PID: 10156)
- cmd.exe (PID: 12424)
- cmd.exe (PID: 12384)
- cmd.exe (PID: 12300)
- cmd.exe (PID: 12392)
- cmd.exe (PID: 13604)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6268)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 9876)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9316)
INFO
Create files in a temporary directory
- certutil.exe (PID: 1296)
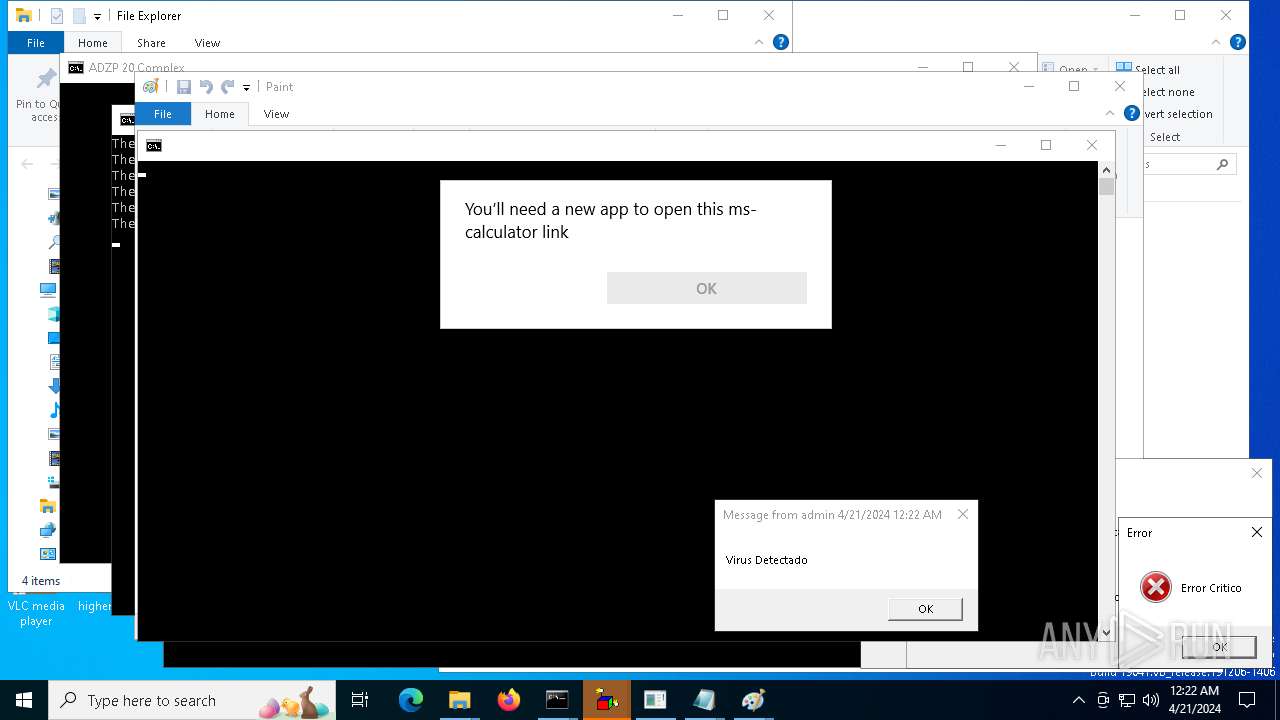
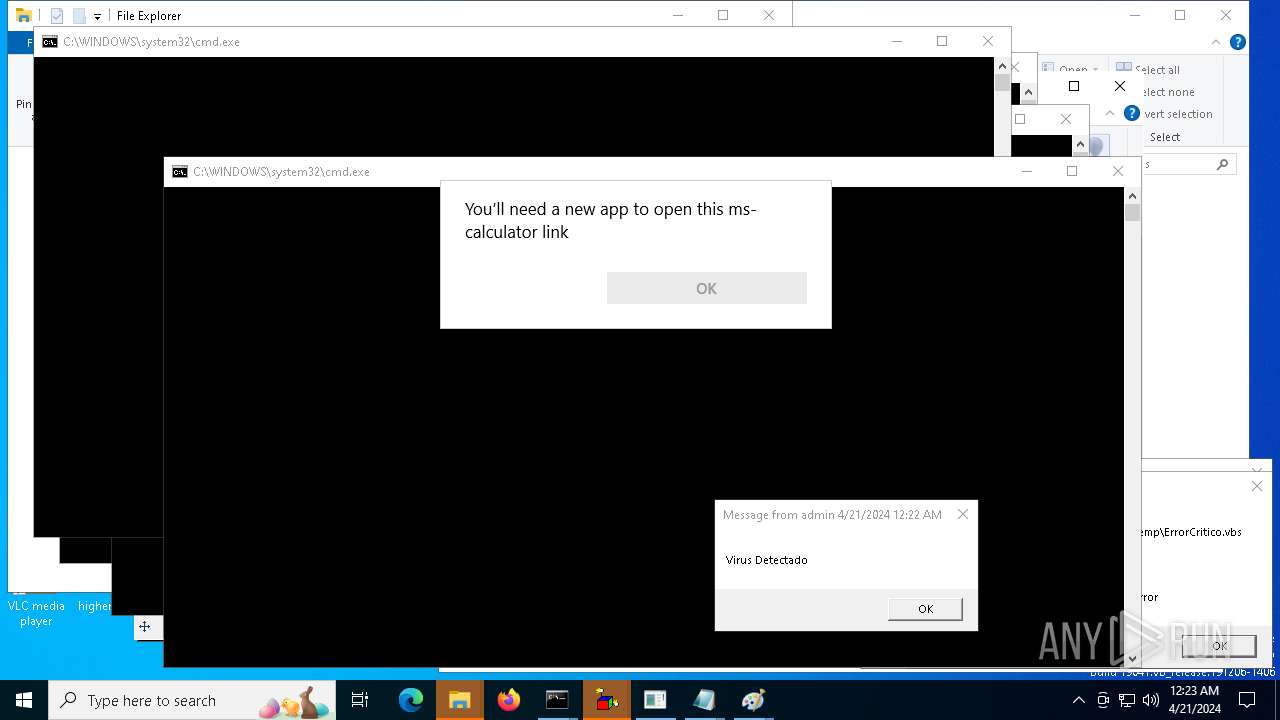
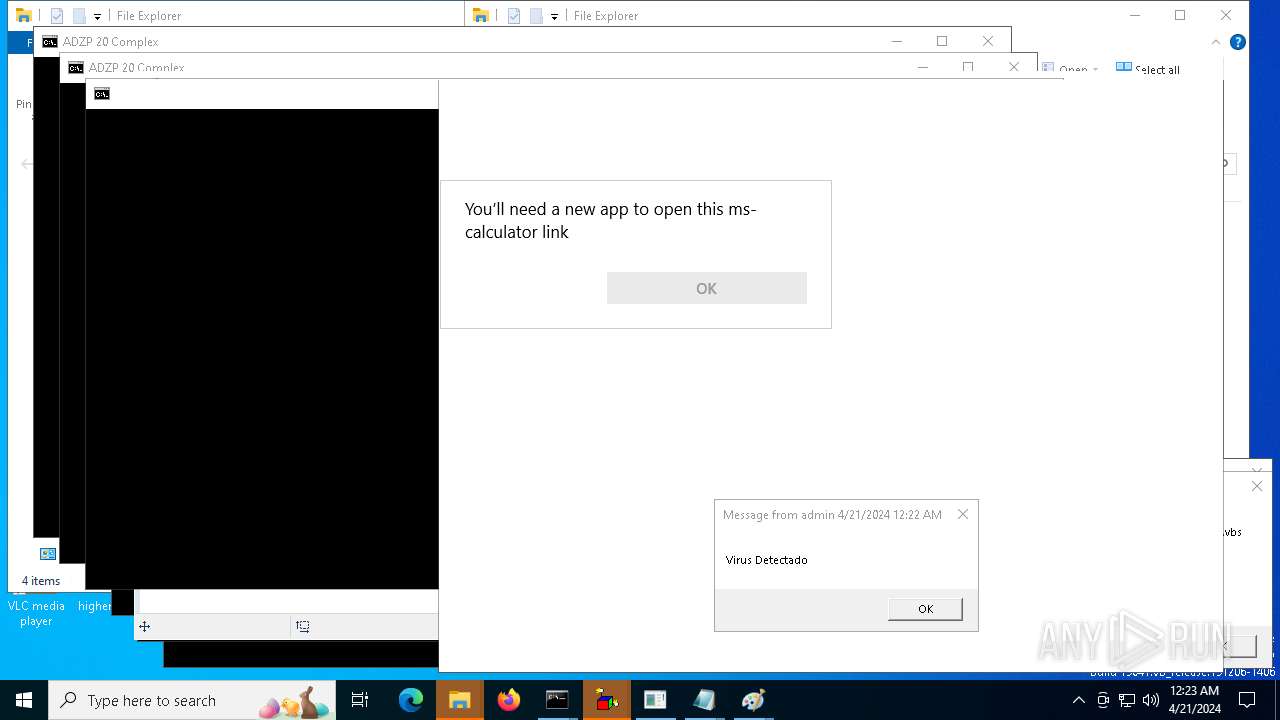
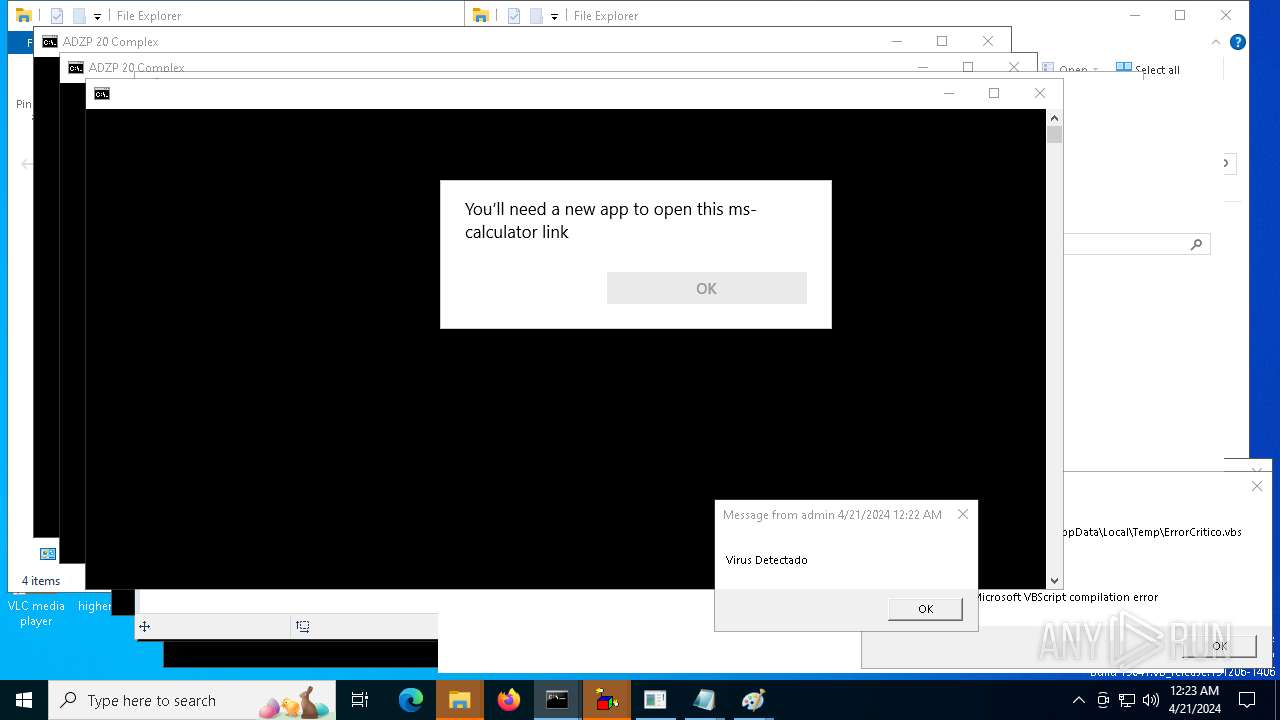
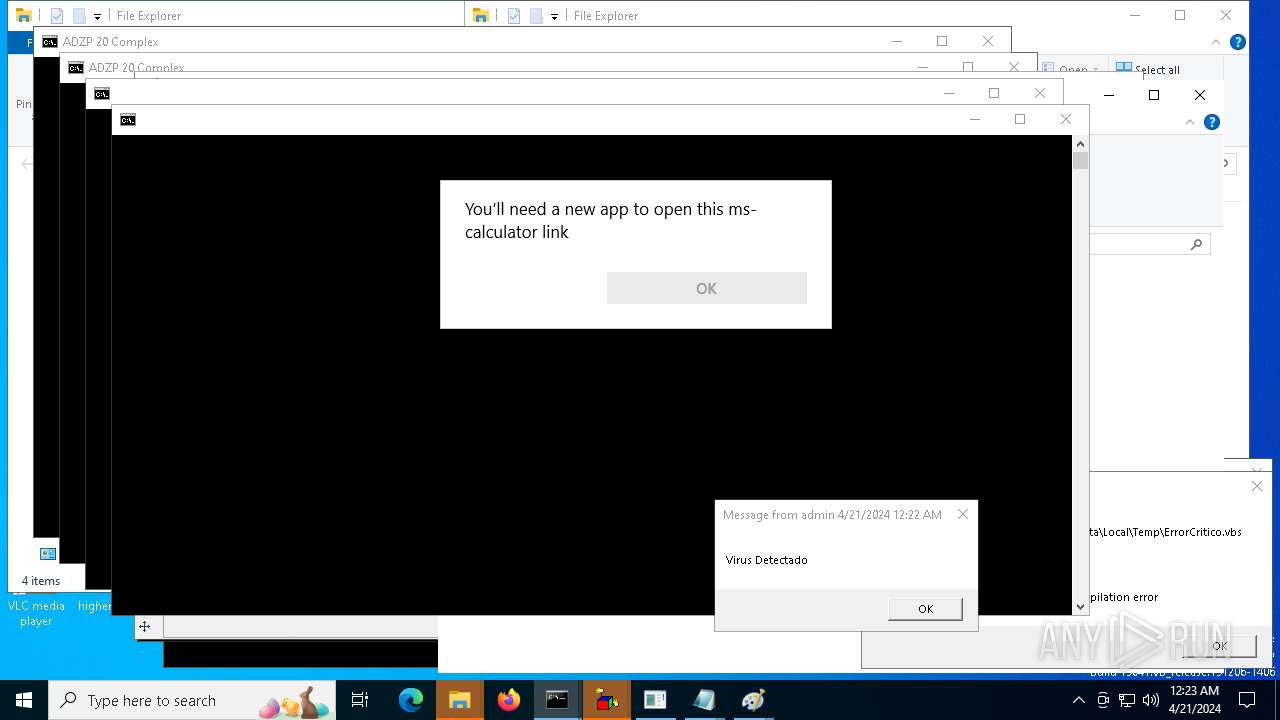
Reads security settings of Internet Explorer
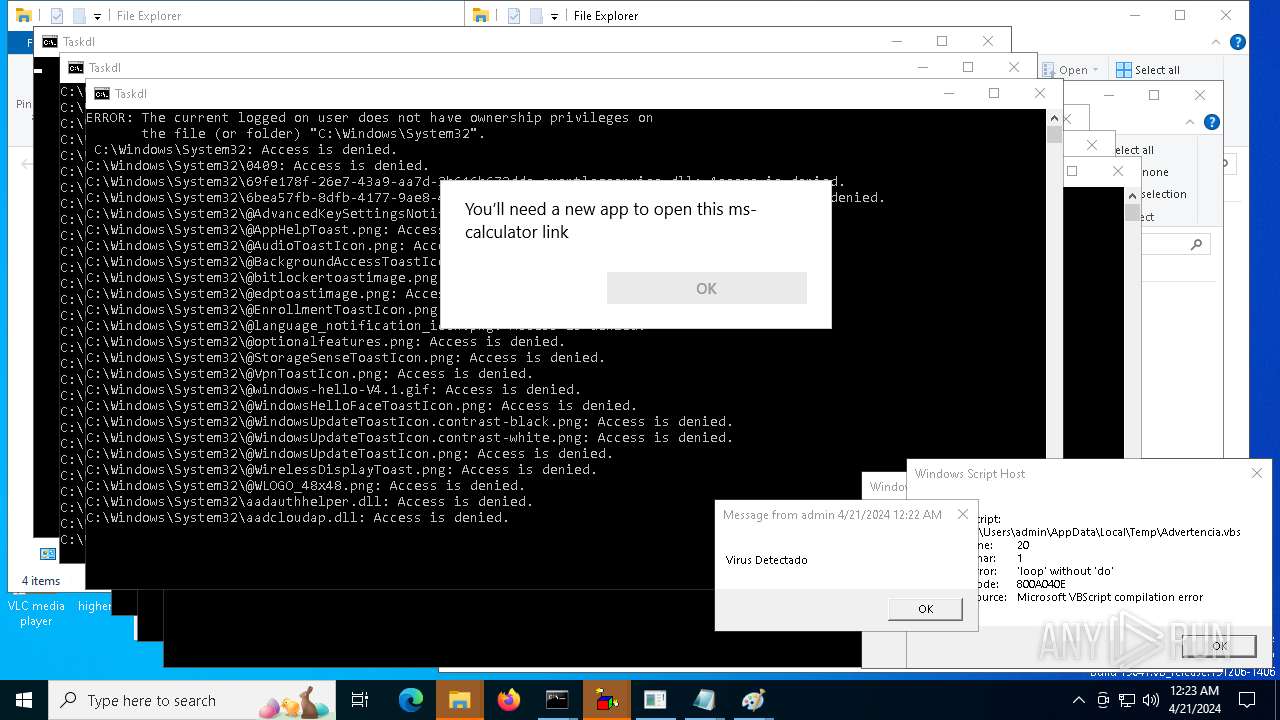
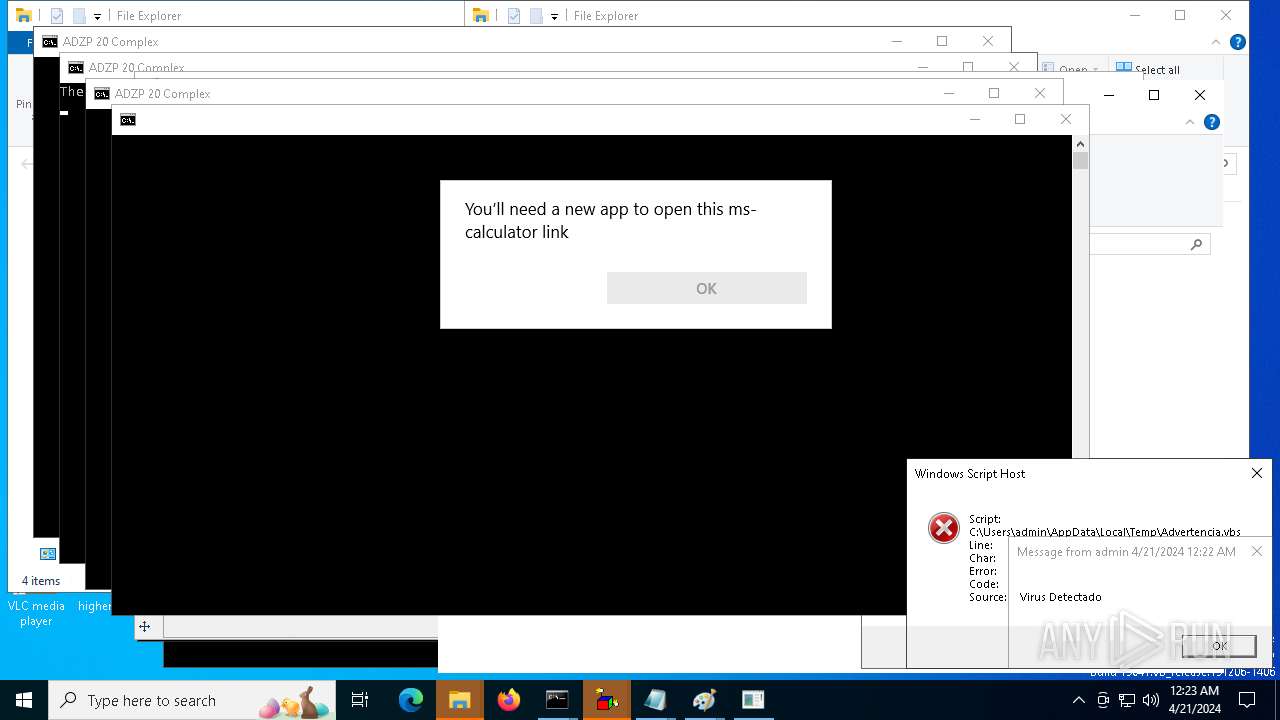
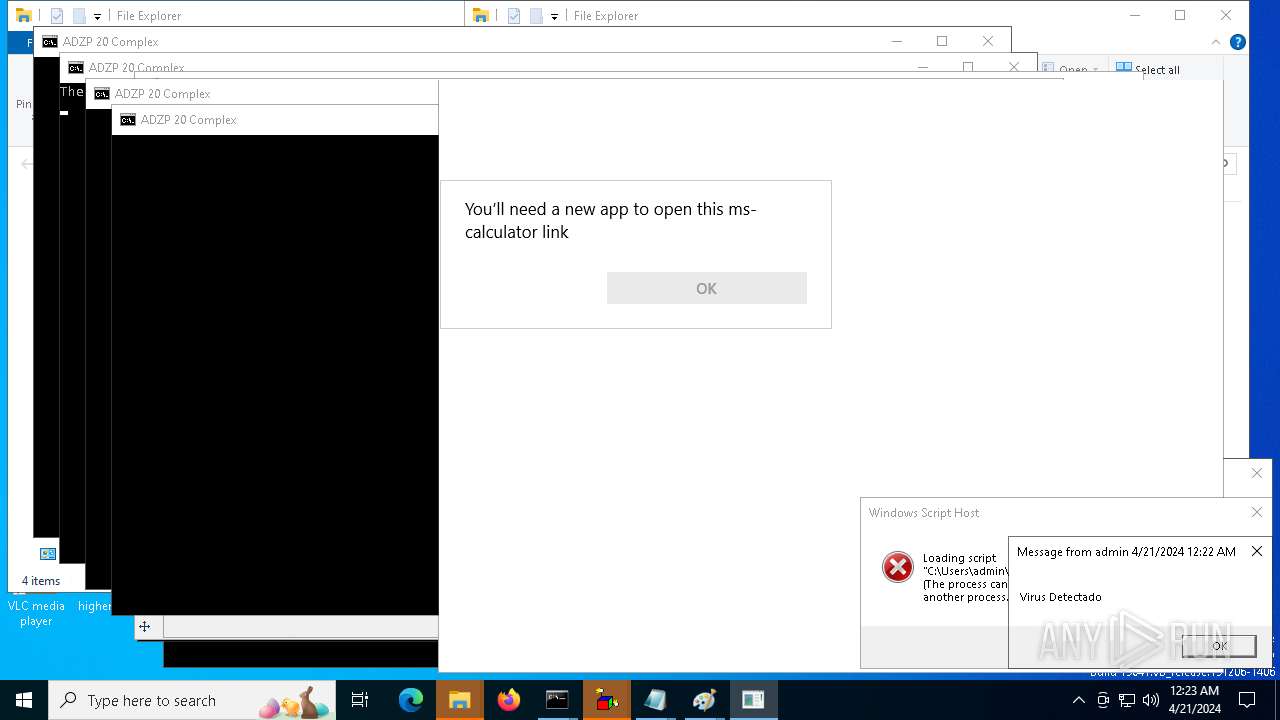
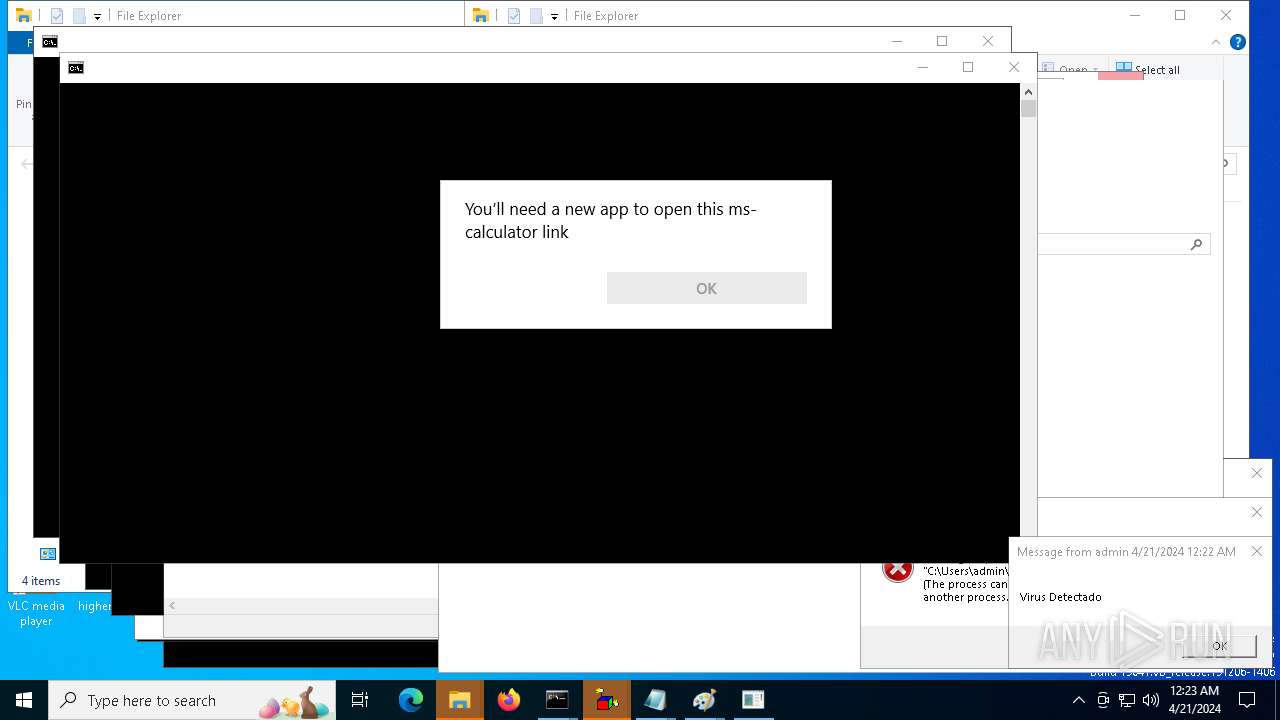
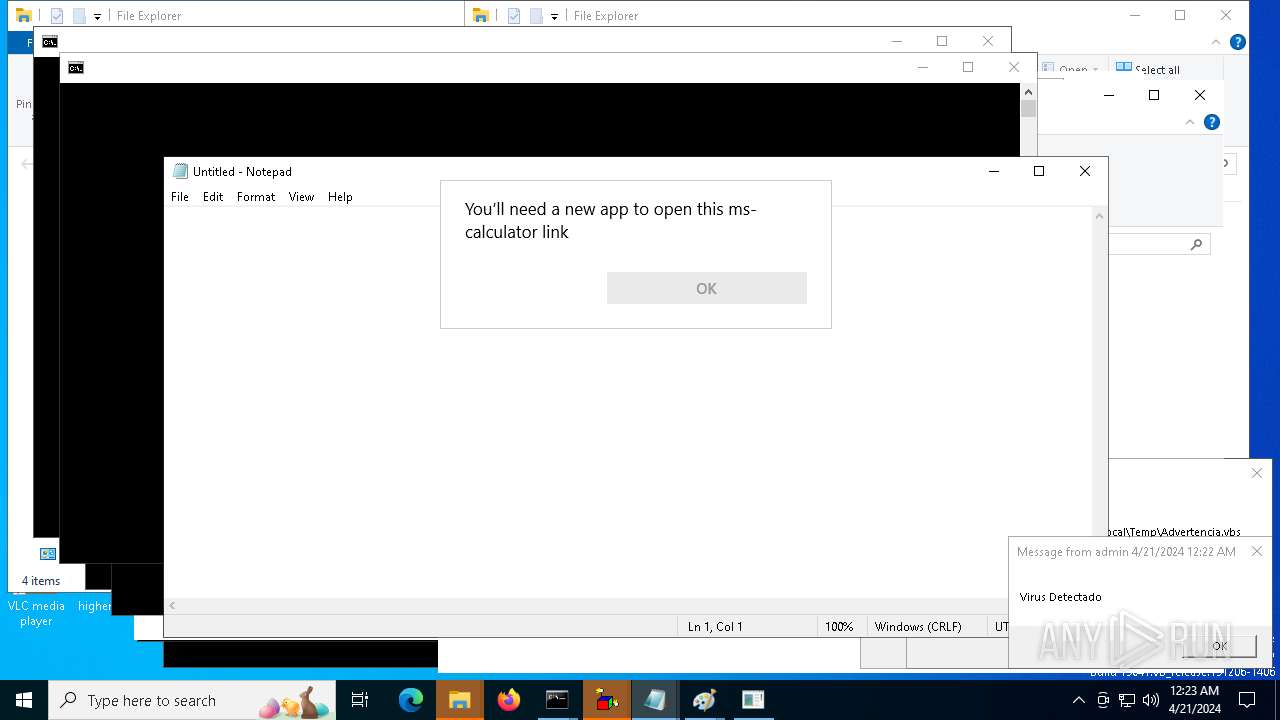
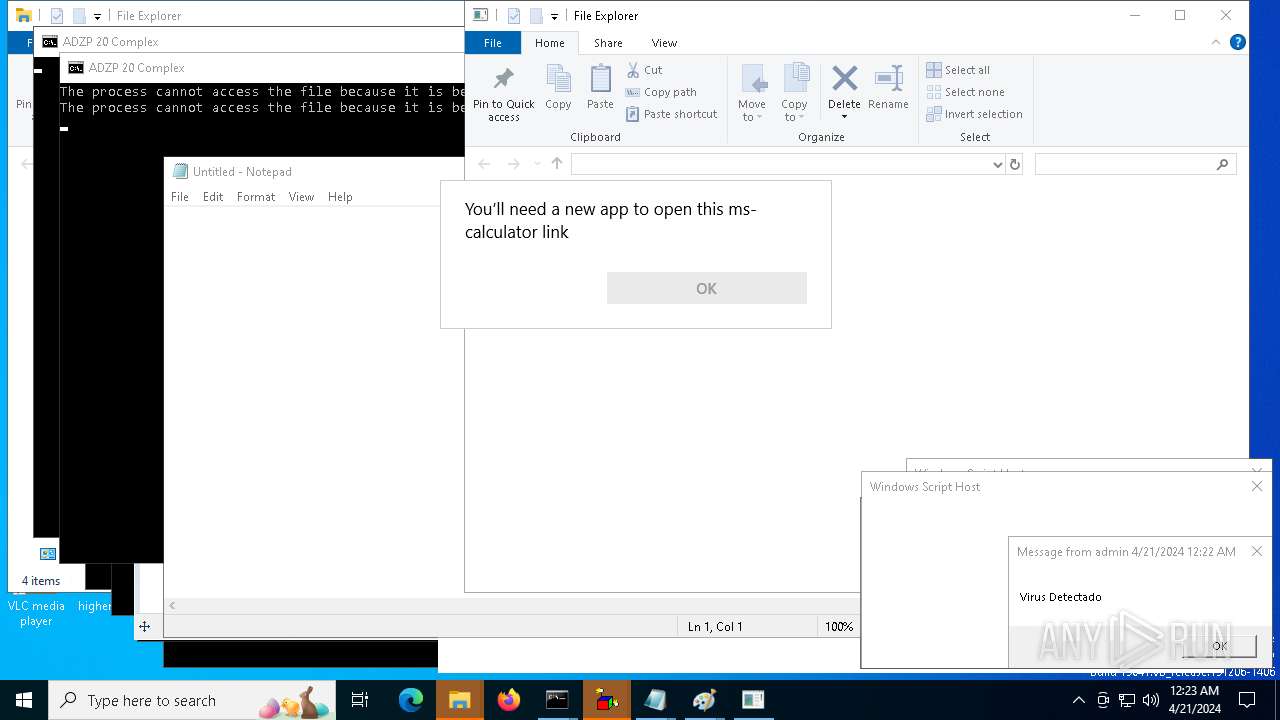
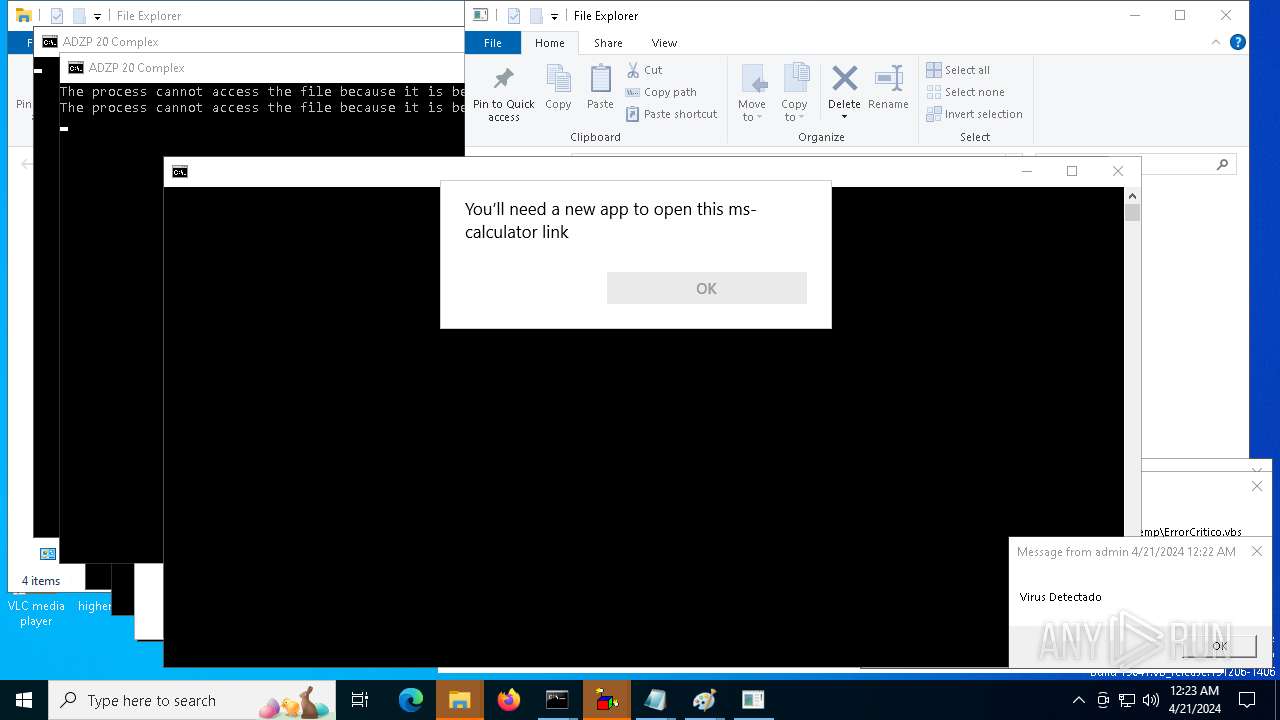
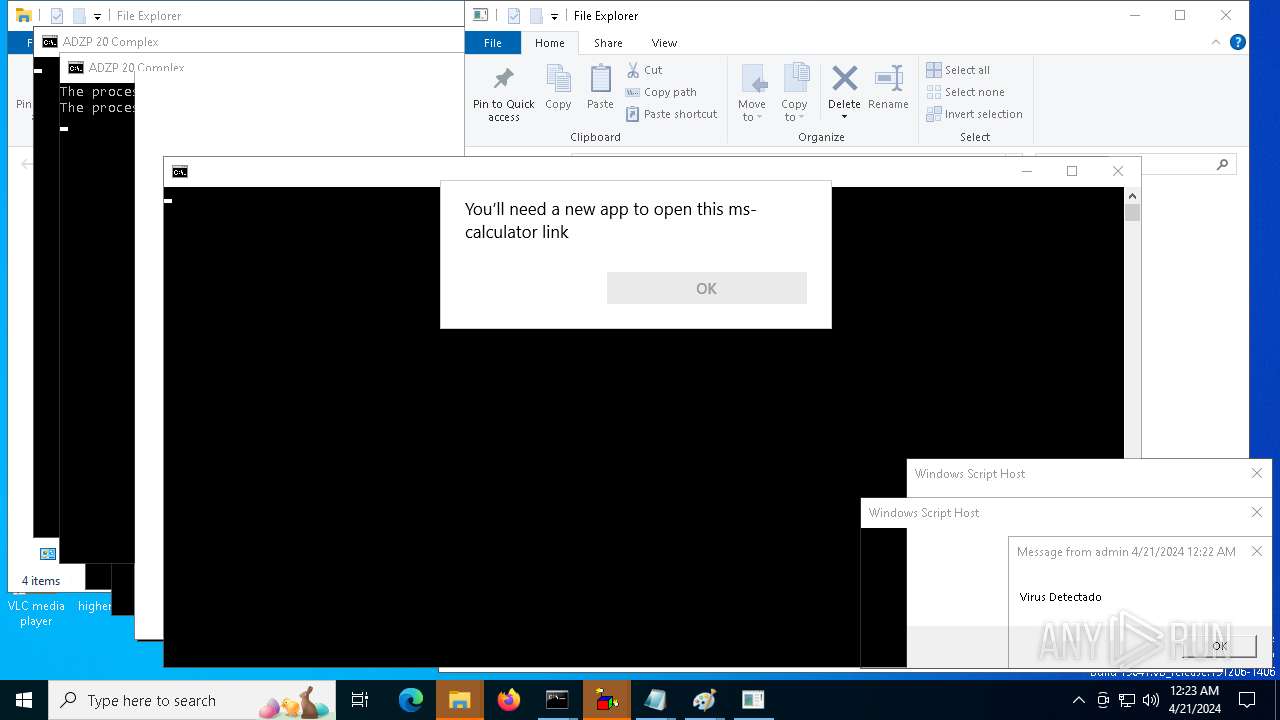
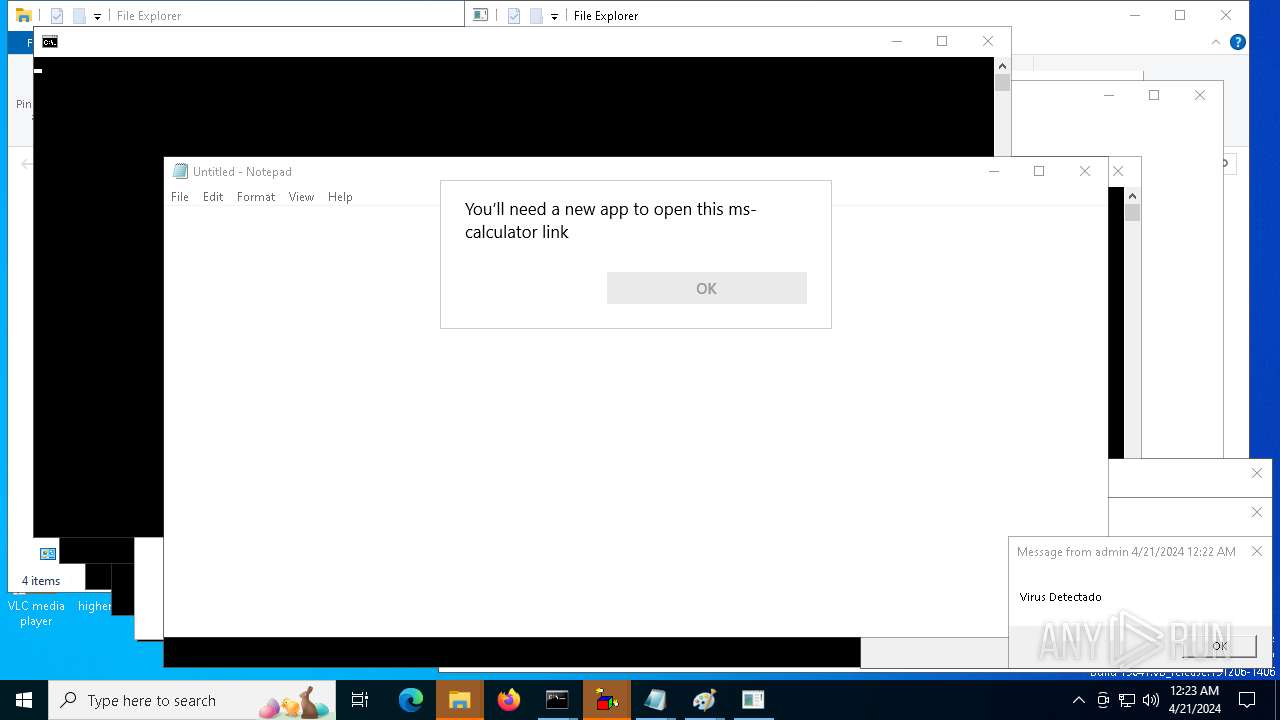
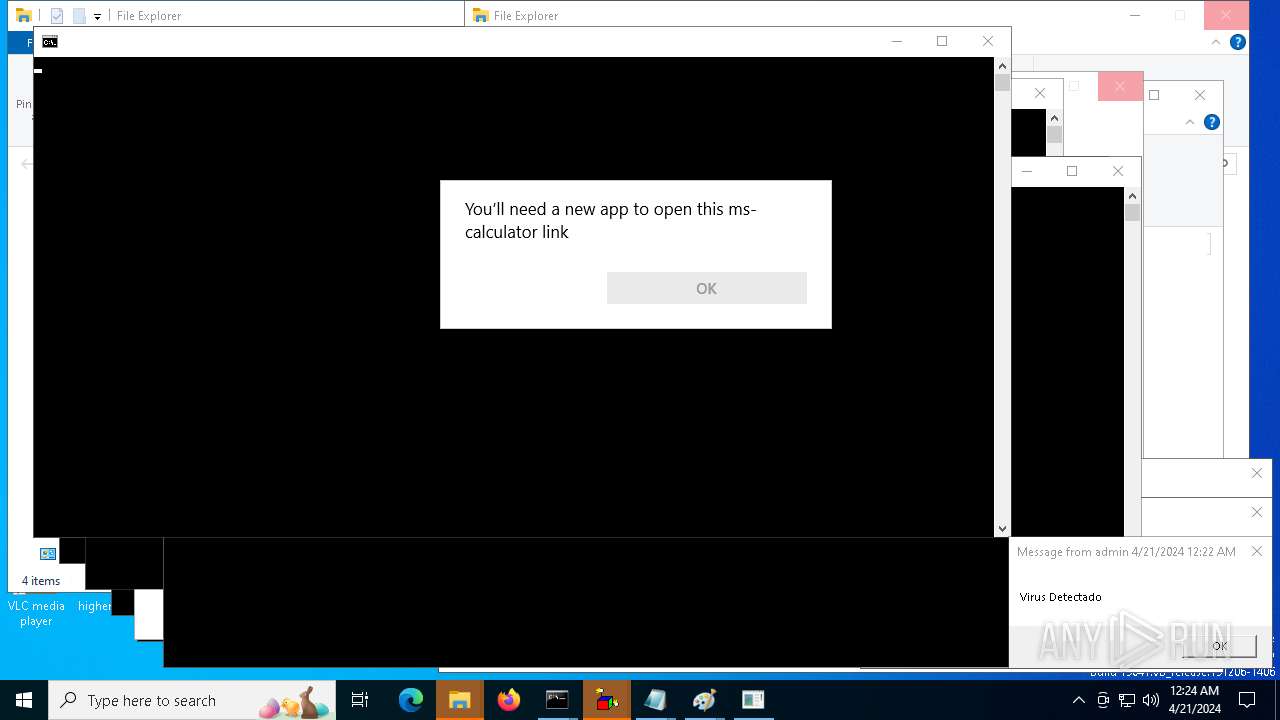
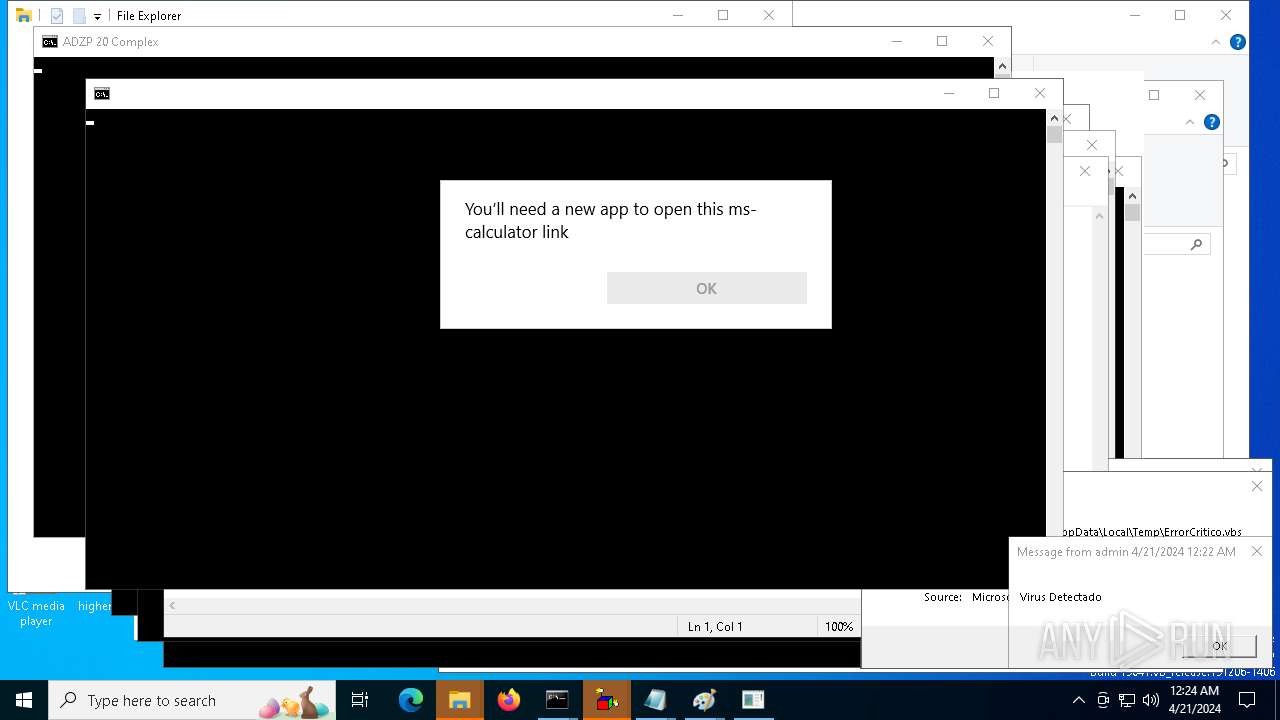
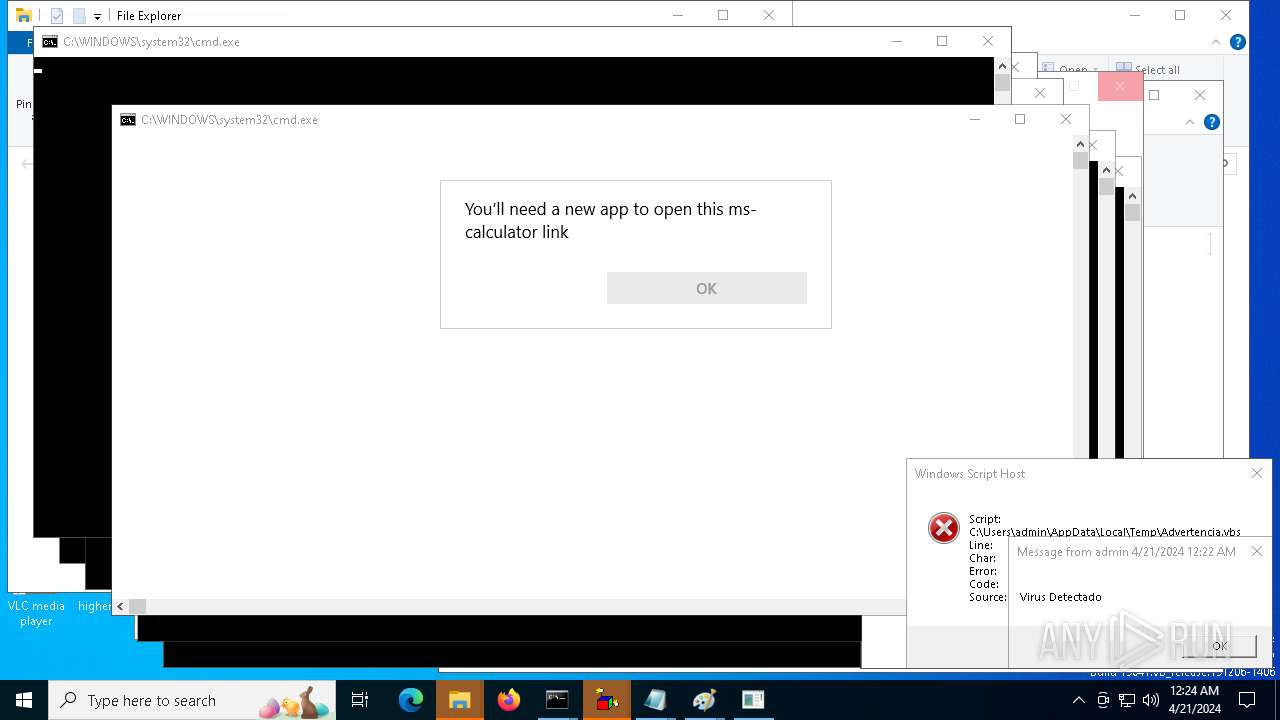
- calc.exe (PID: 5296)
- calc.exe (PID: 2836)
- OpenWith.exe (PID: 1136)
- calc.exe (PID: 4460)
- OpenWith.exe (PID: 7256)
- OpenWith.exe (PID: 7312)
- calc.exe (PID: 8416)
- calc.exe (PID: 8532)
- calc.exe (PID: 8484)
- calc.exe (PID: 9316)
- calc.exe (PID: 10036)
- OpenWith.exe (PID: 8428)
- OpenWith.exe (PID: 9104)
- OpenWith.exe (PID: 9664)
- OpenWith.exe (PID: 9252)
- OpenWith.exe (PID: 9928)
- calc.exe (PID: 9656)
- OpenWith.exe (PID: 8908)
- calc.exe (PID: 9772)
- calc.exe (PID: 8852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
793
Monitored processes
673
Malicious processes
18
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
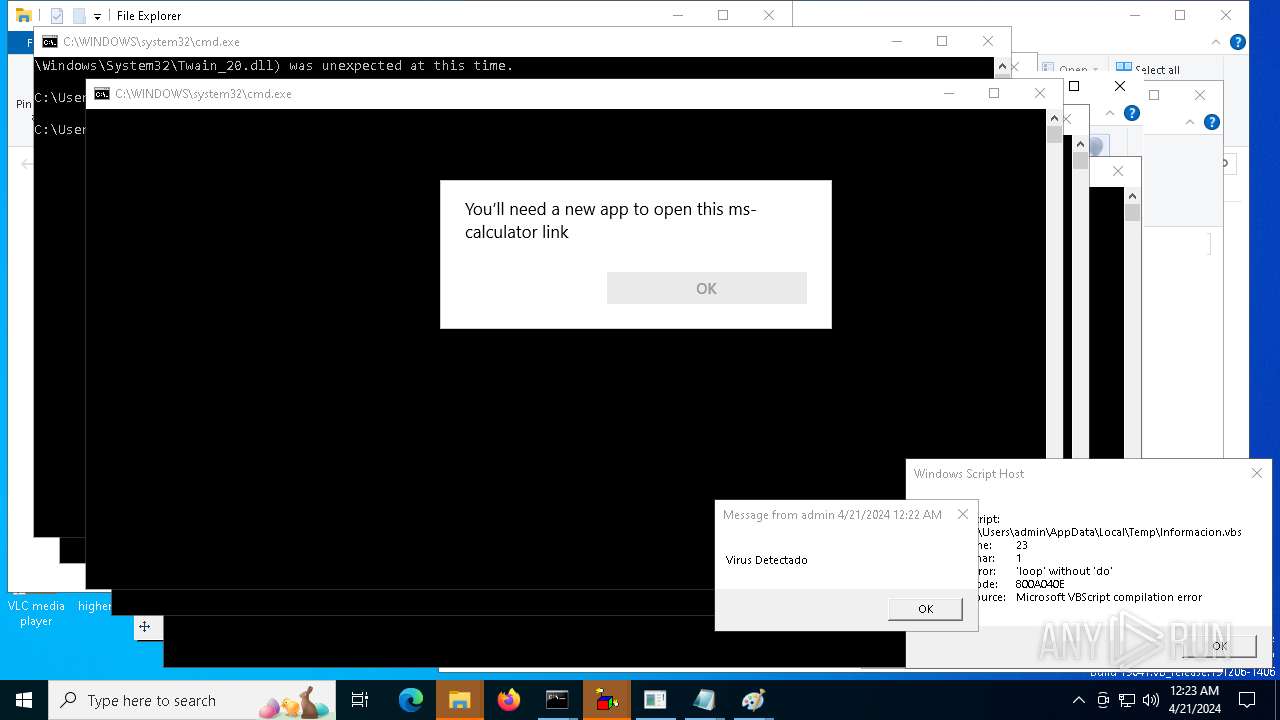
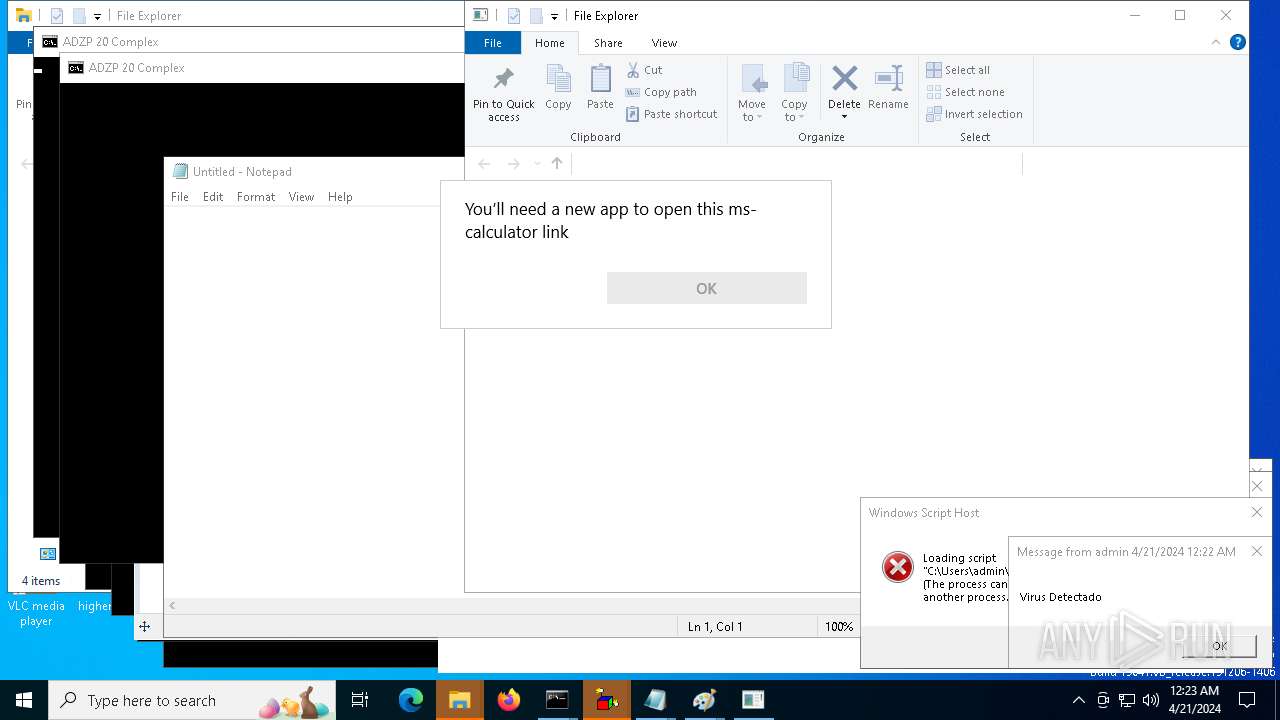
| 204 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Informacion.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
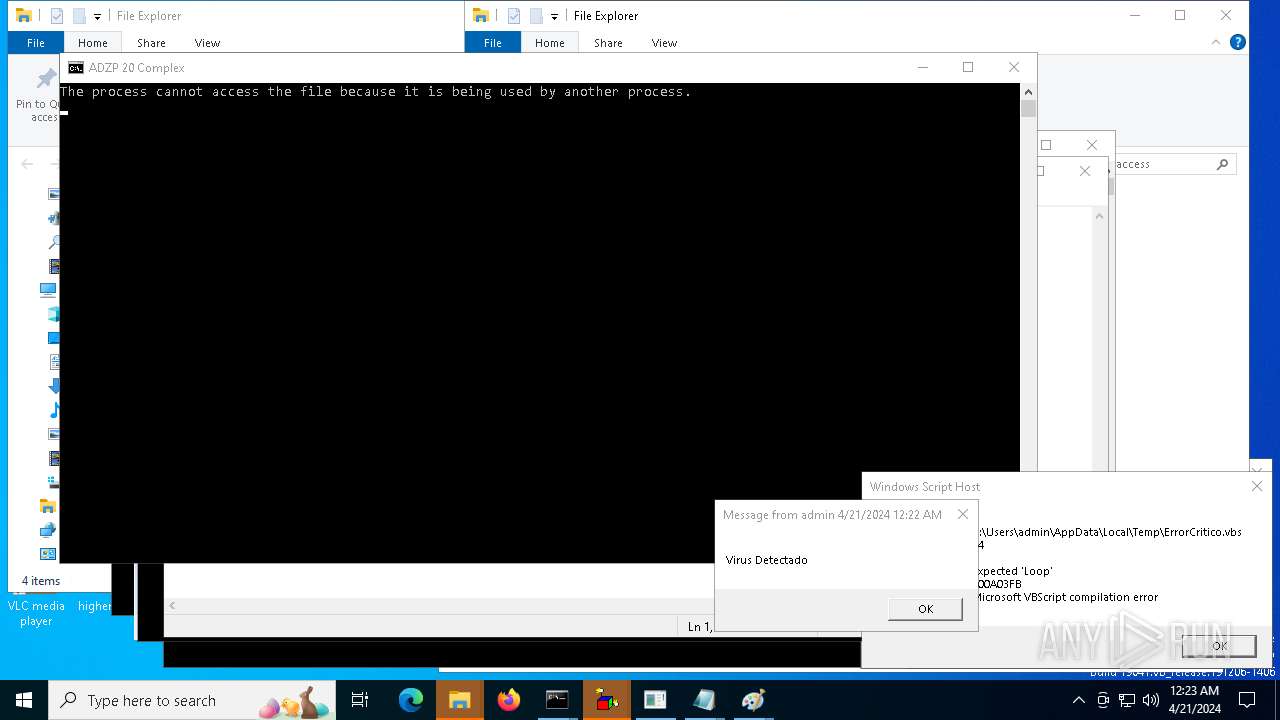
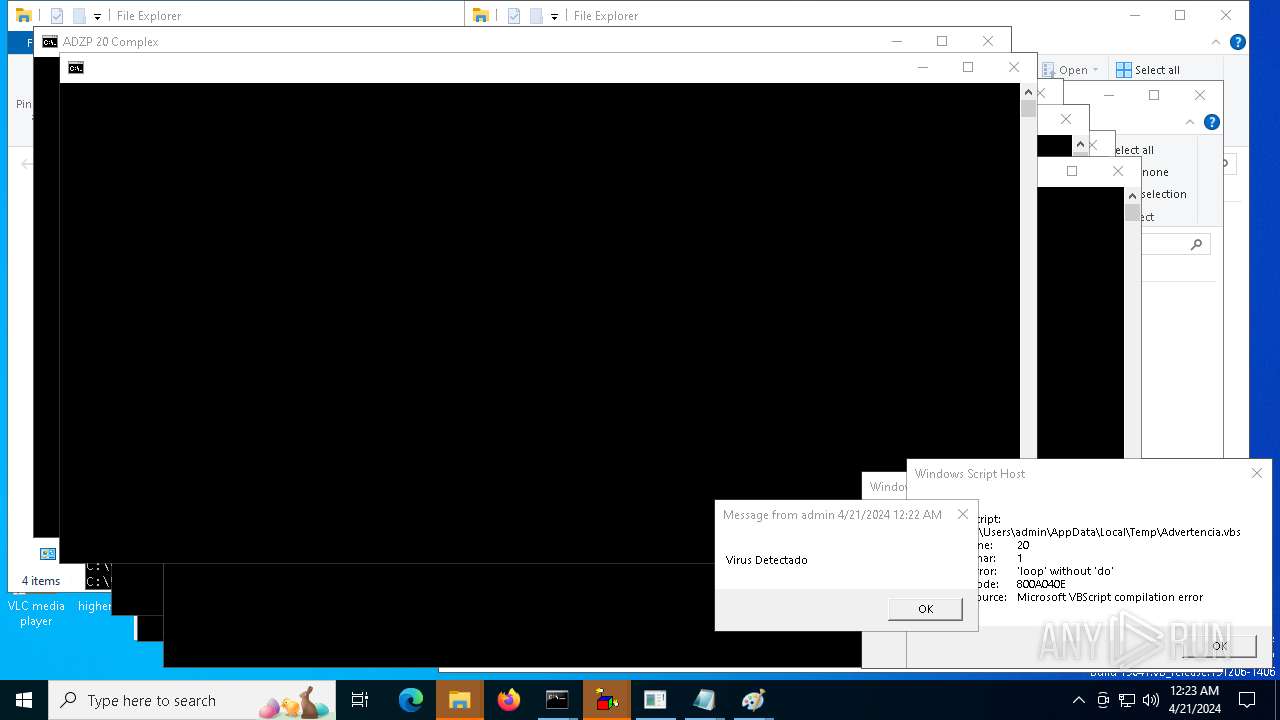
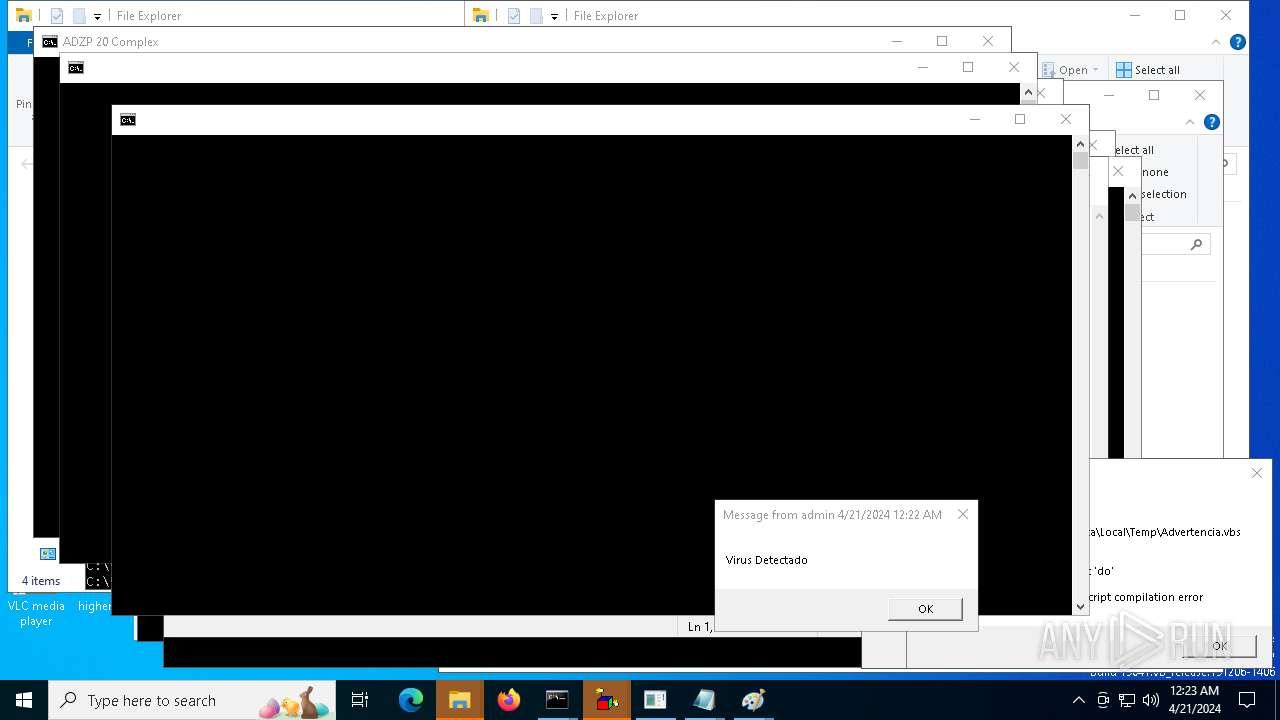
| 552 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\ErrorCritico.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 | |||||||||||||||
| 620 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\ErrorCritico.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 816 | C:\WINDOWS\system32\cmd.exe /K Twain_20.cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
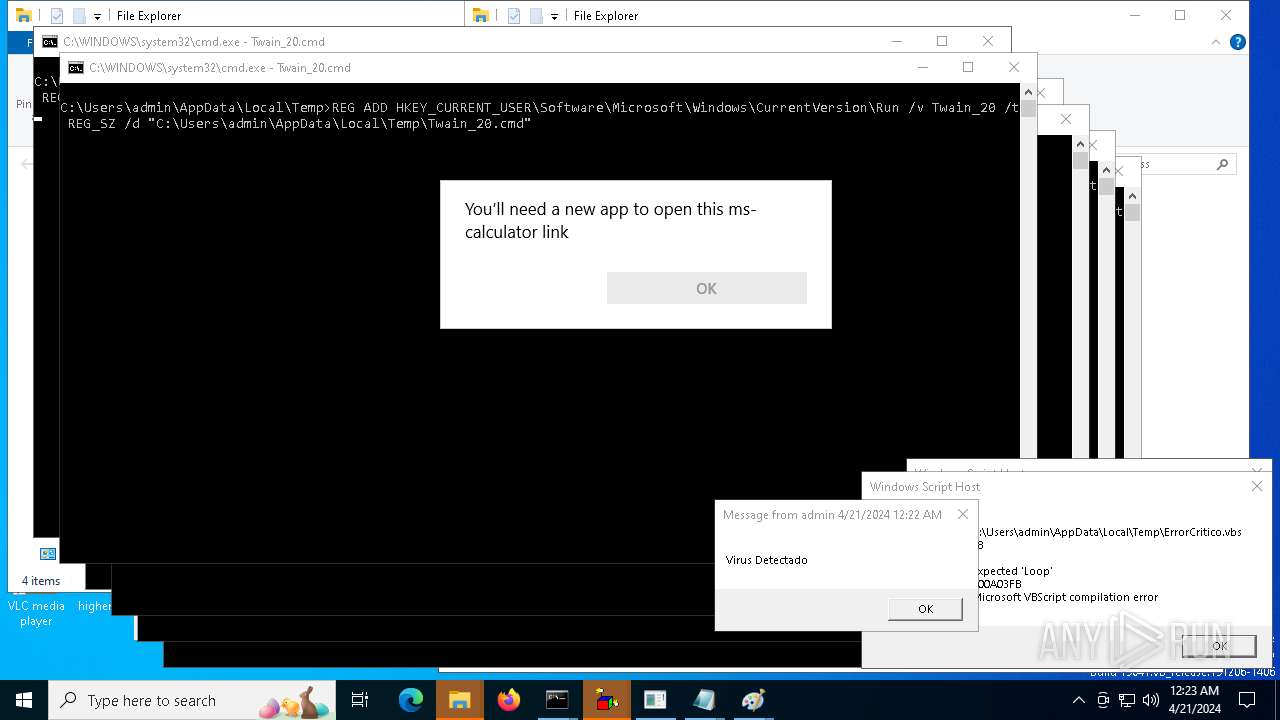
| 980 | REG ADD HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run /v Twain_20 /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\Twain_20.cmd" | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
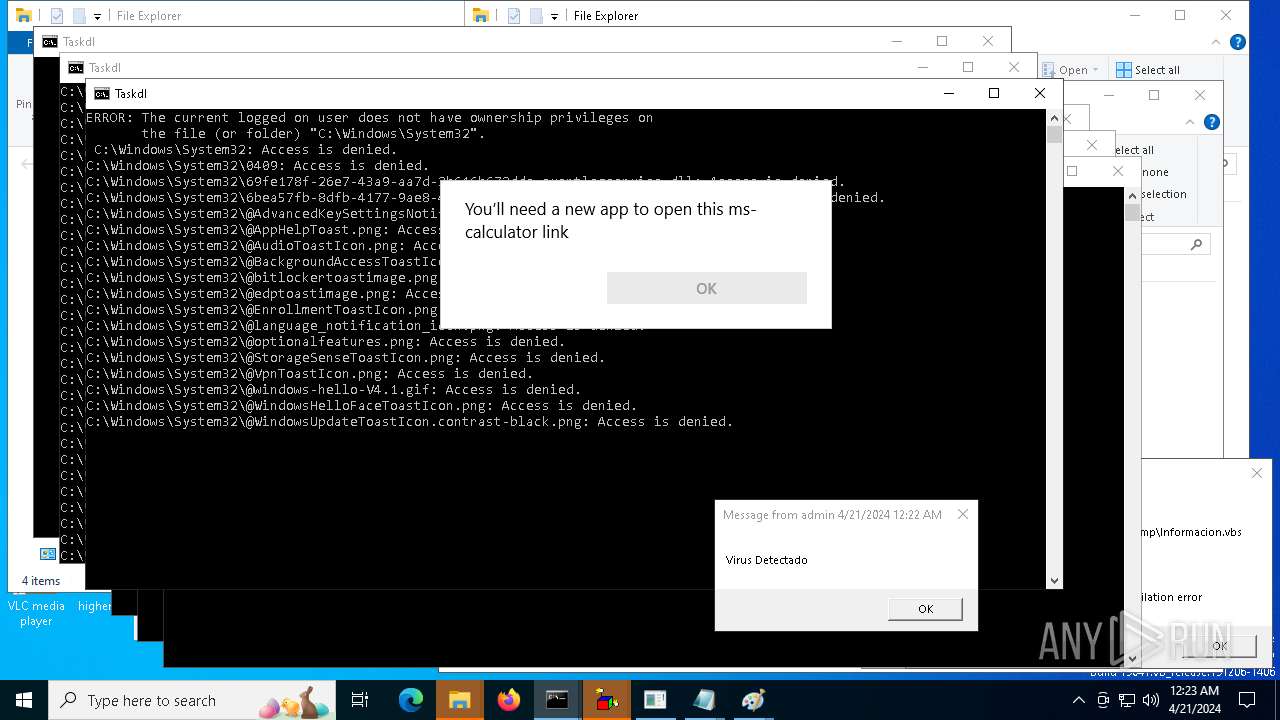
| 980 | takeown /f "C:\Windows\System32" /r | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | icacls "C:\Windows\System32" /reset /t /c /q | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1076 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\ErrorCritico.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
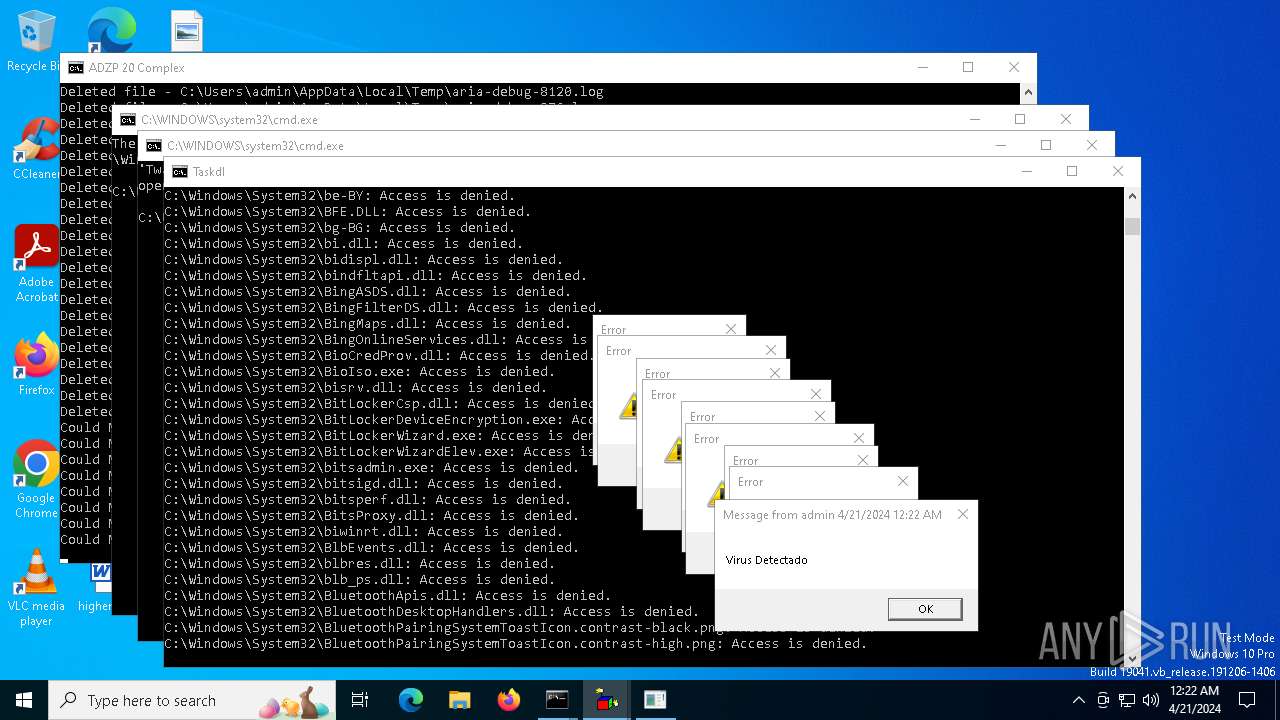
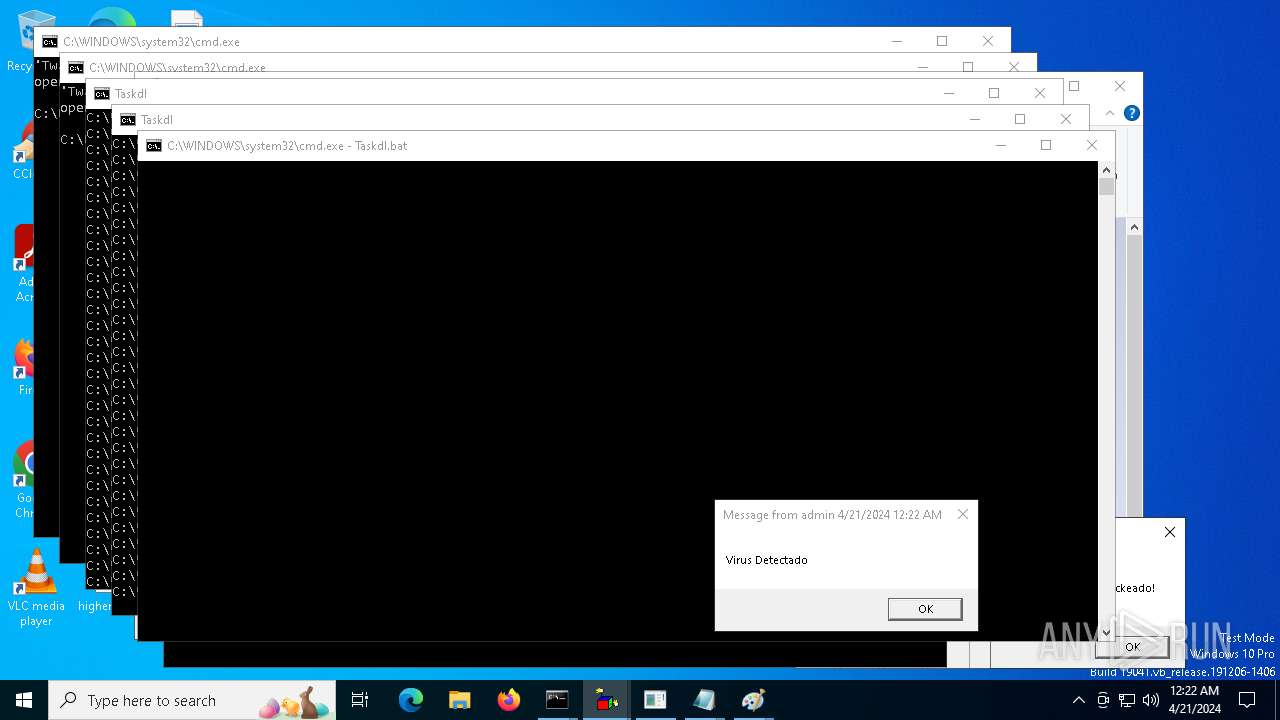
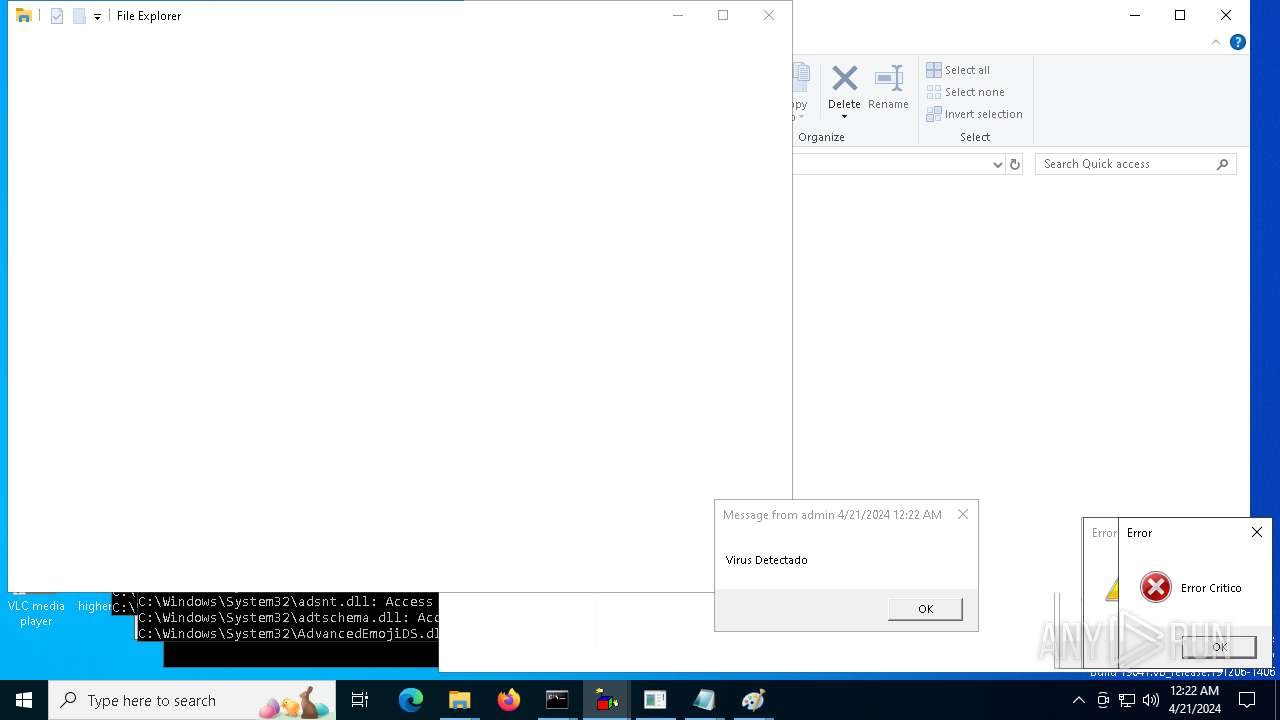
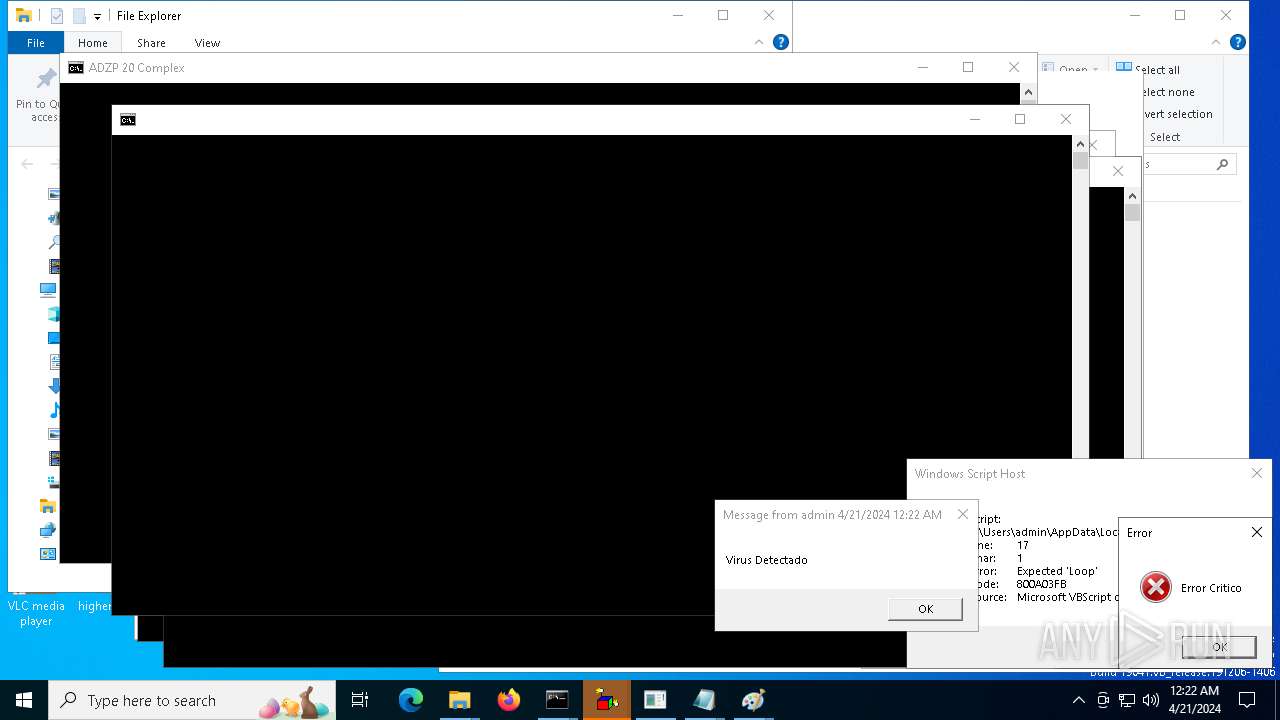
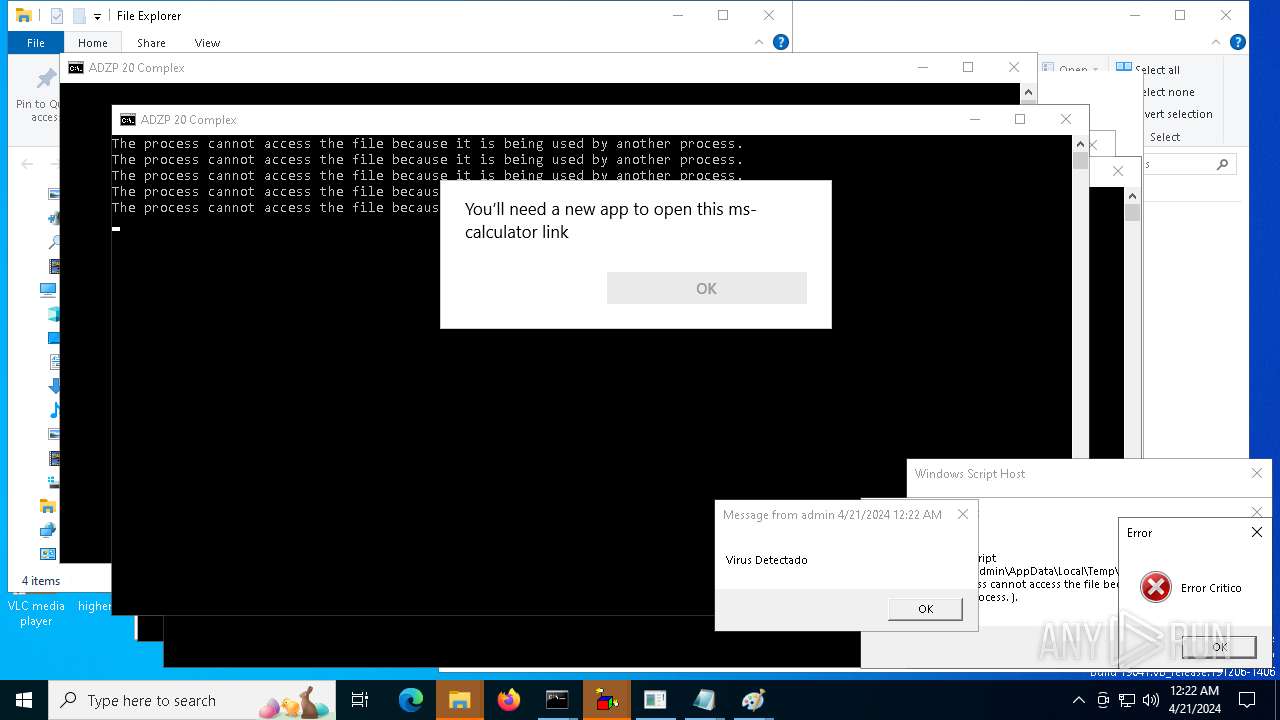
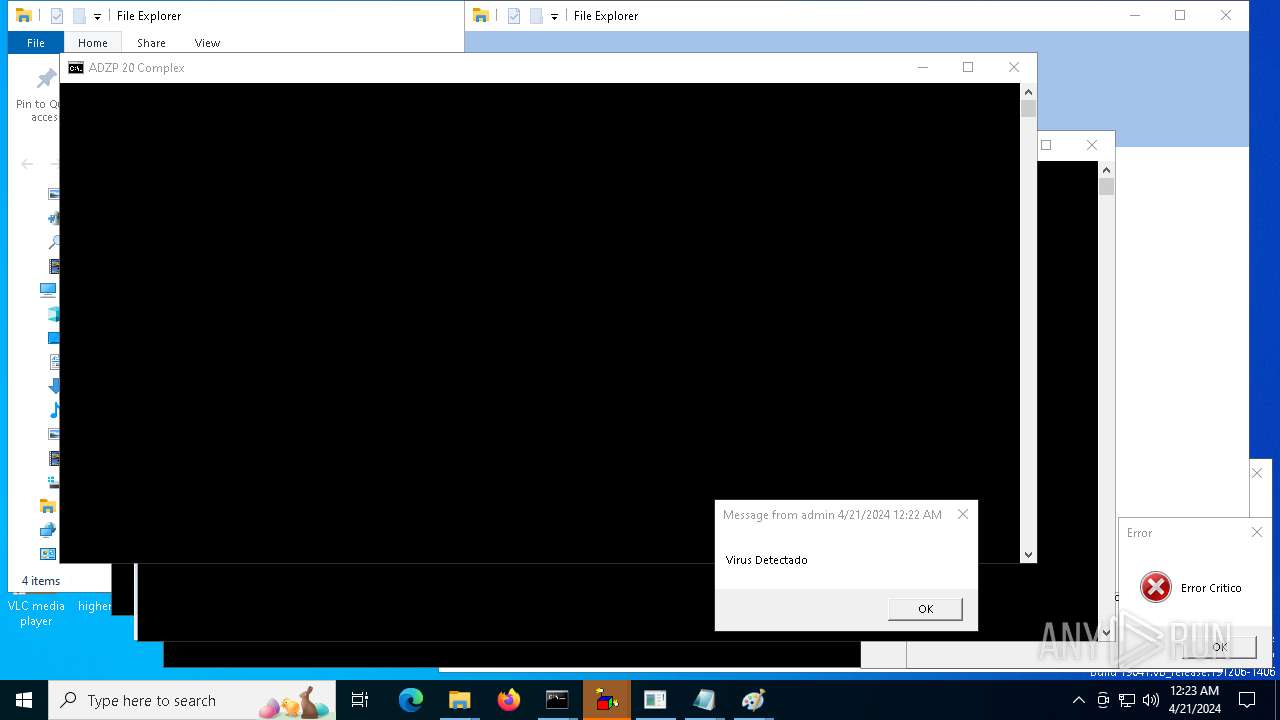
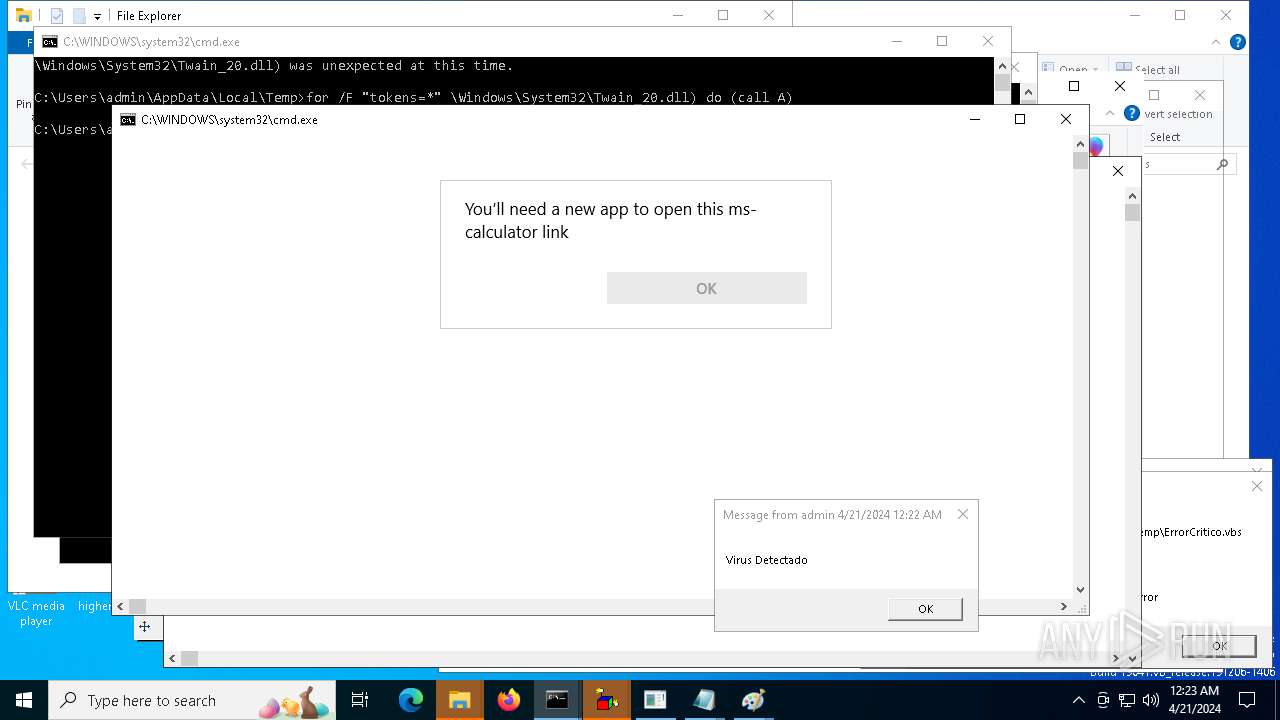
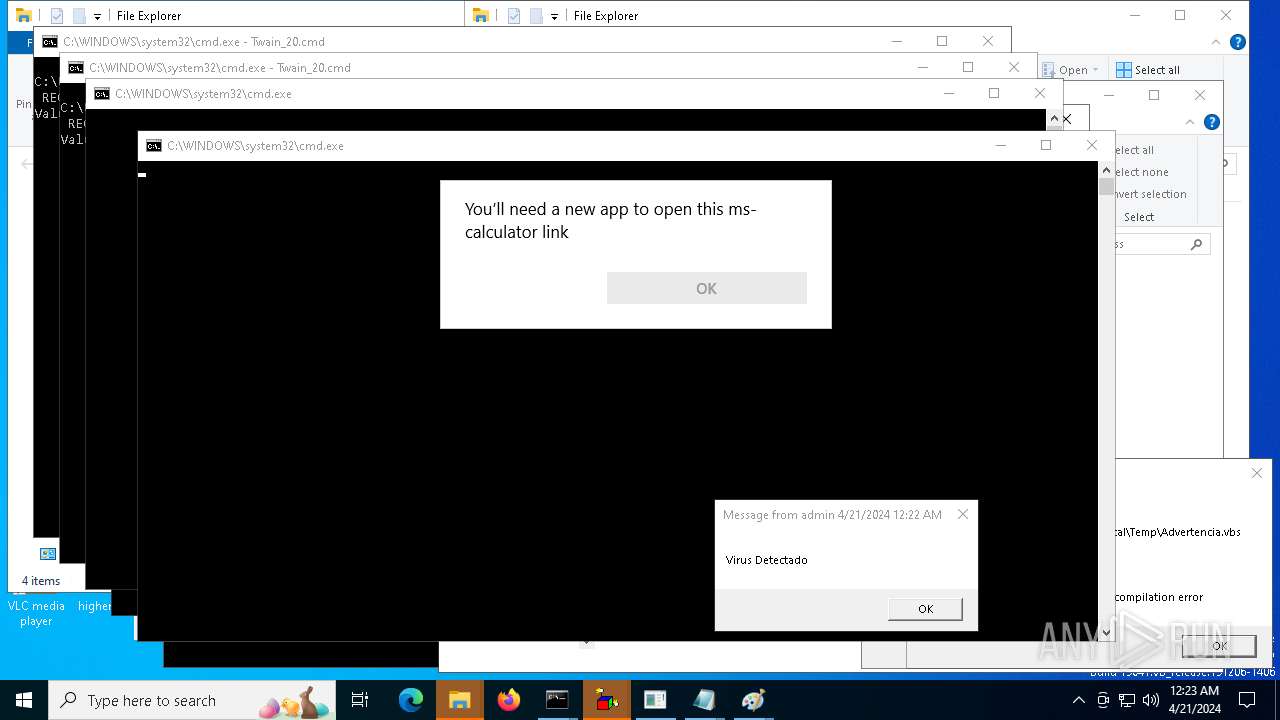
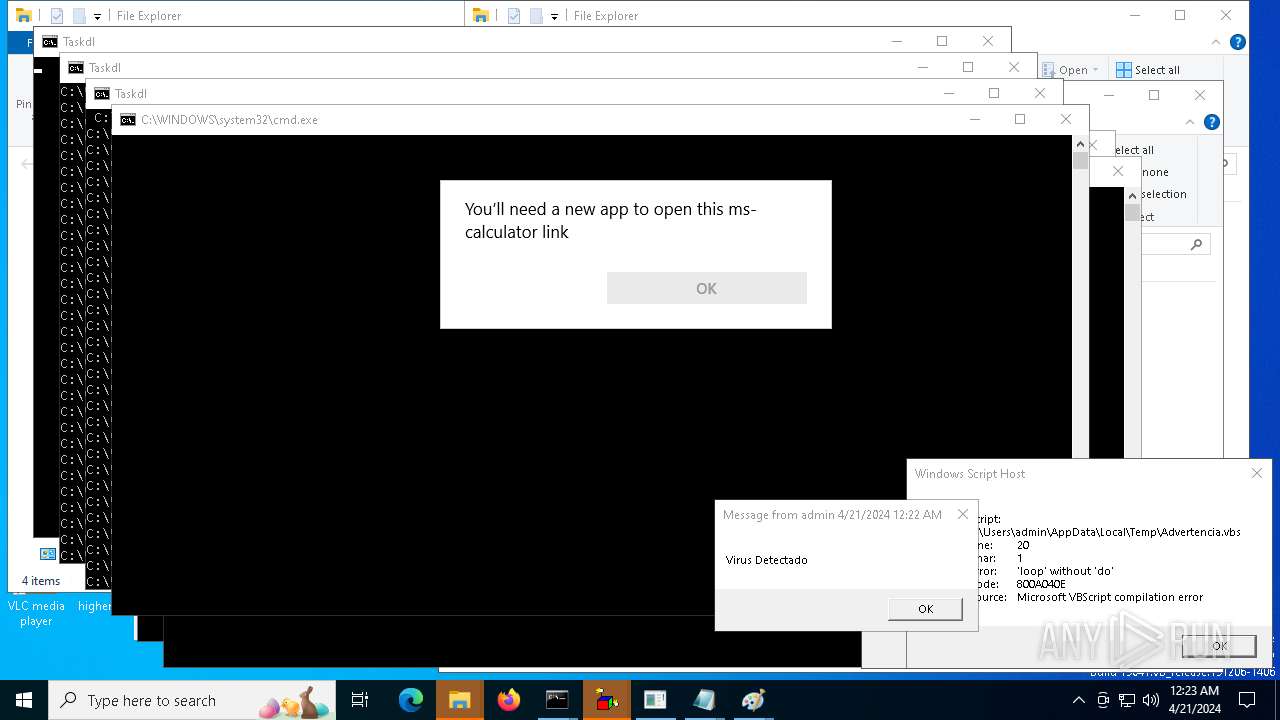
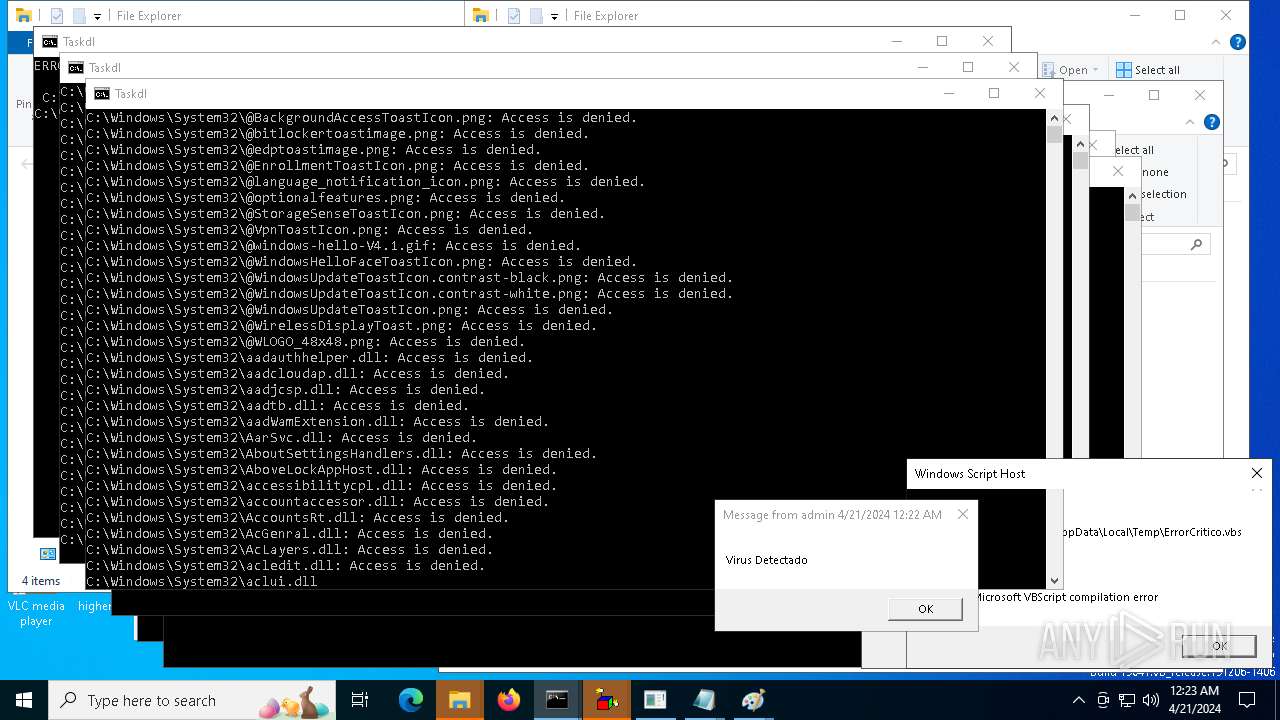
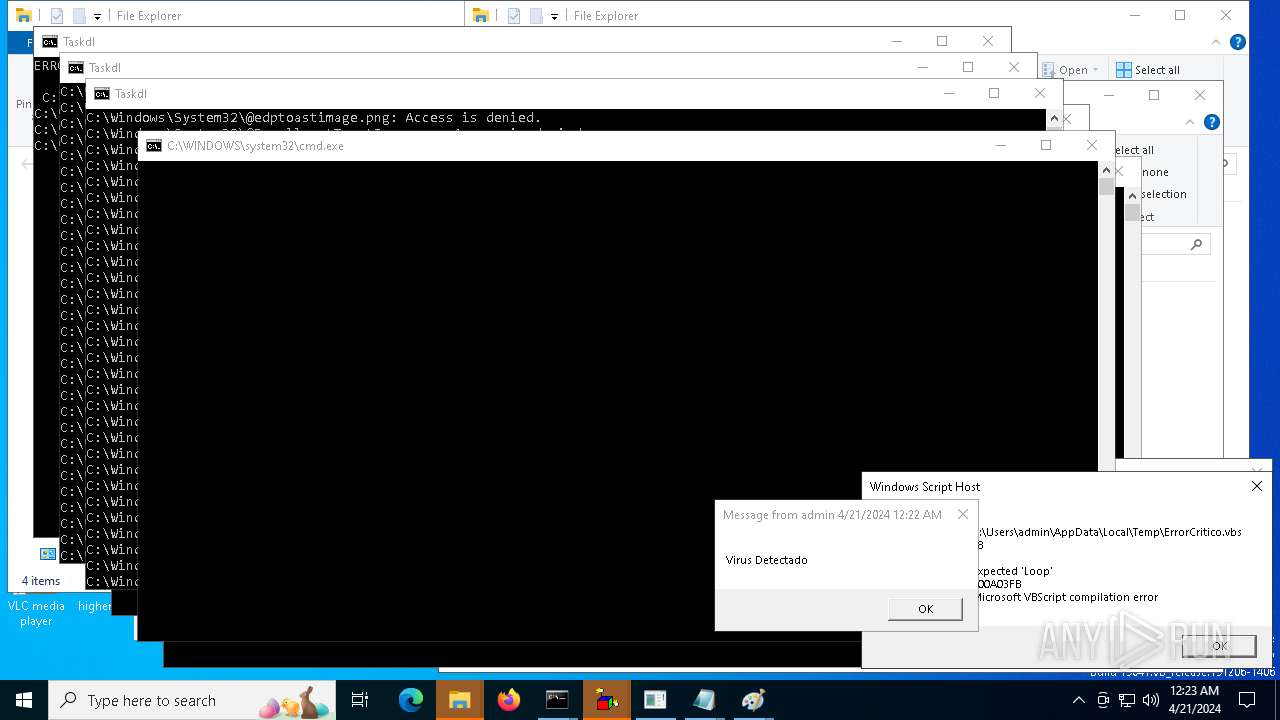
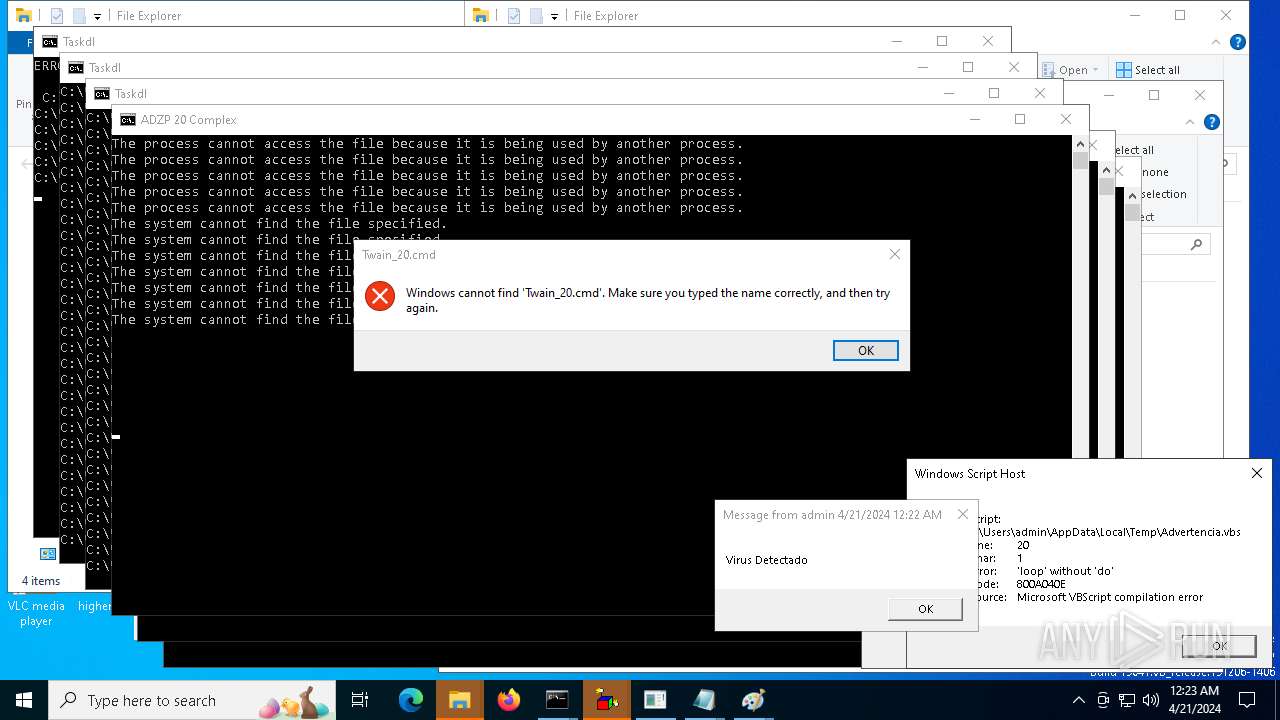
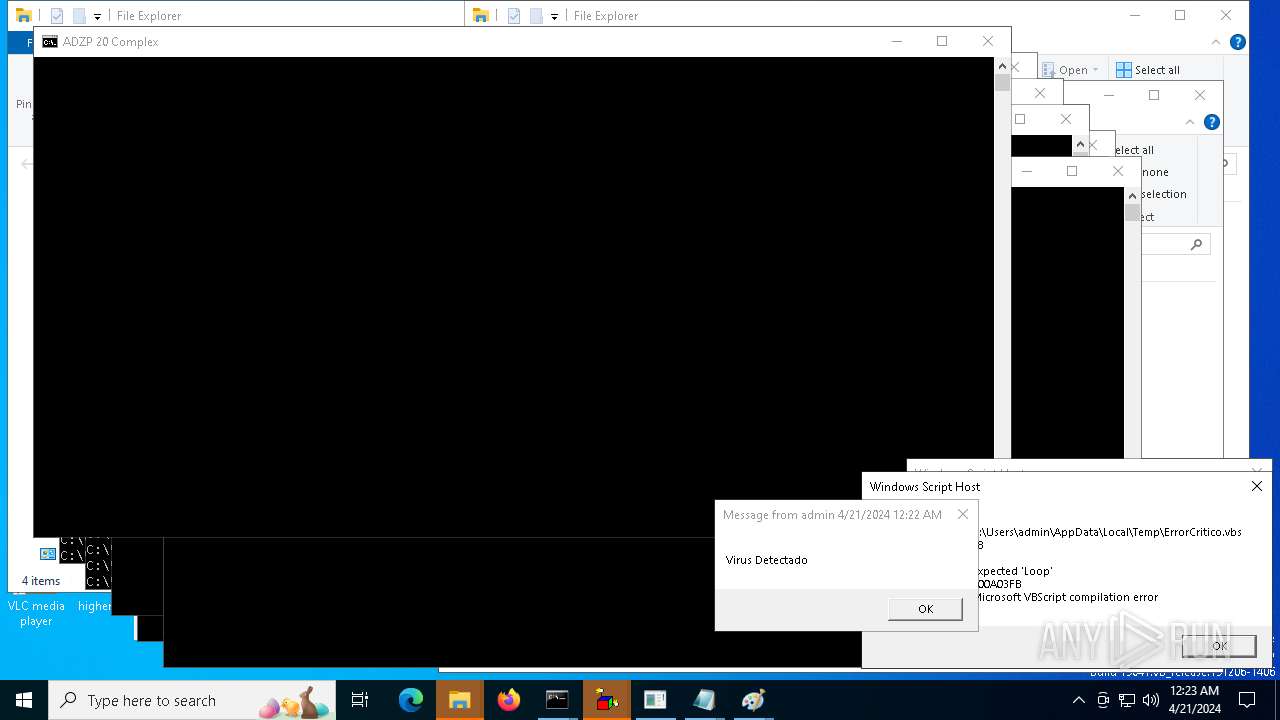
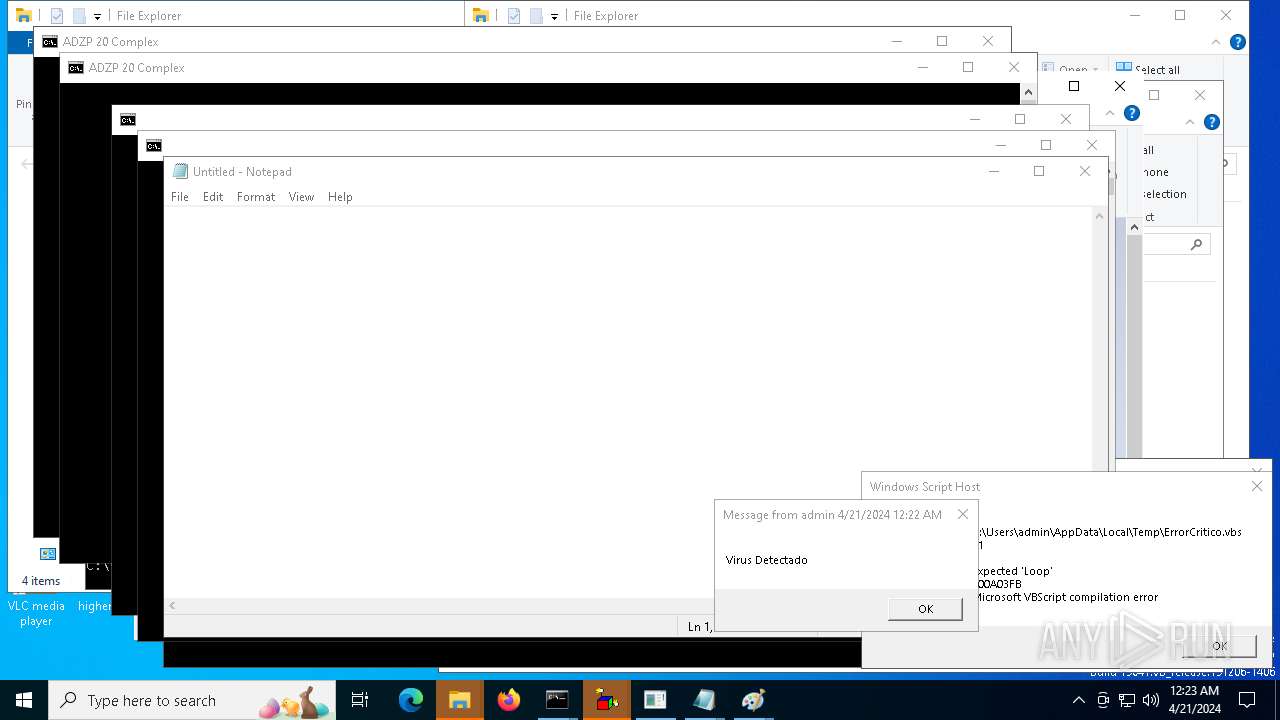
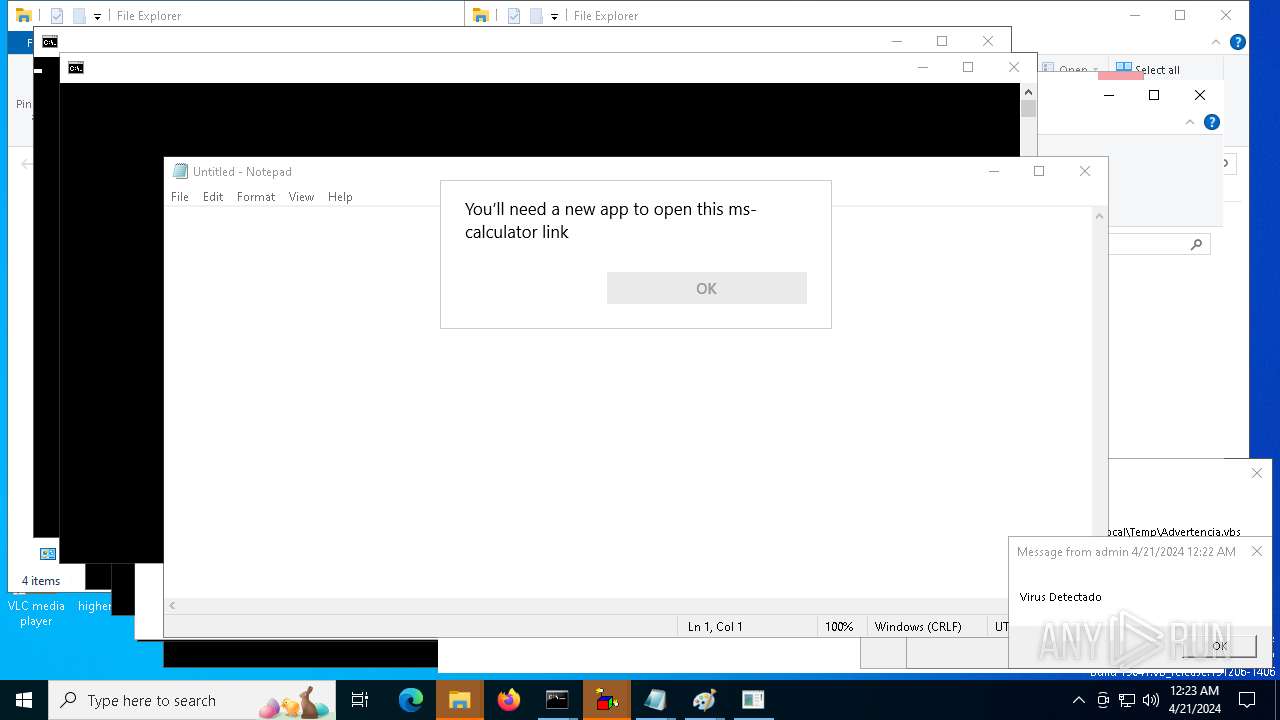
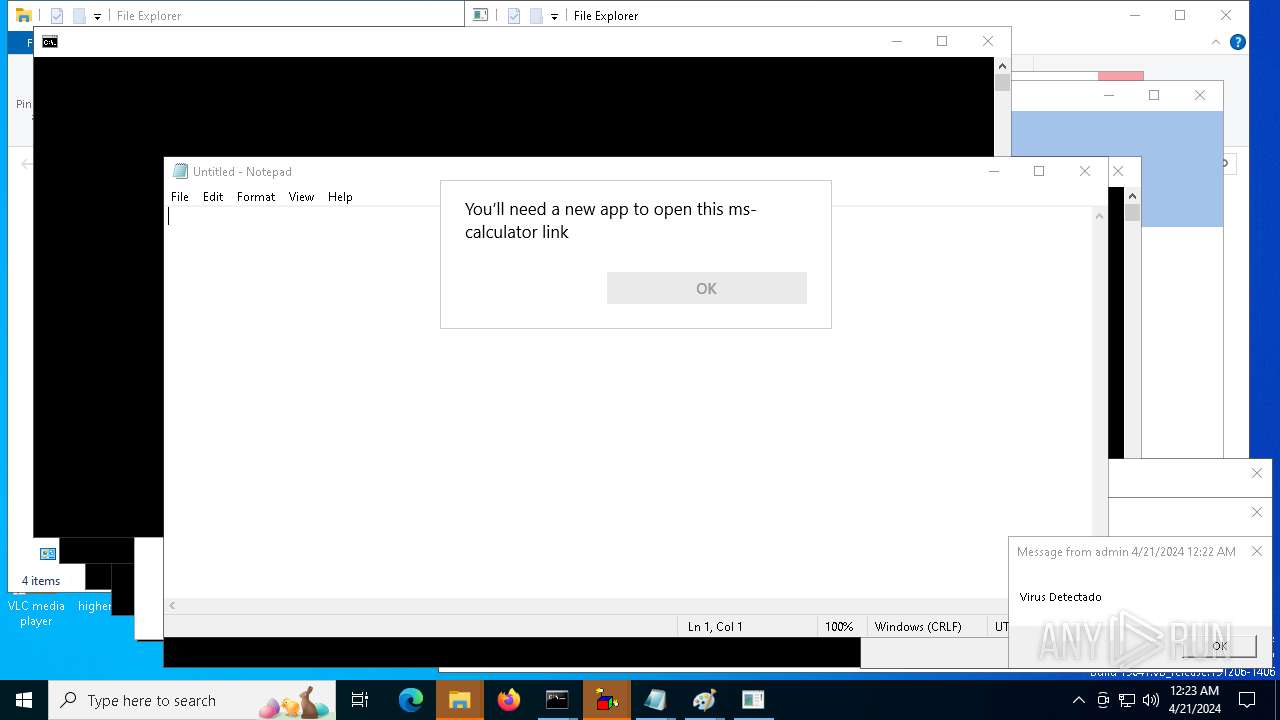
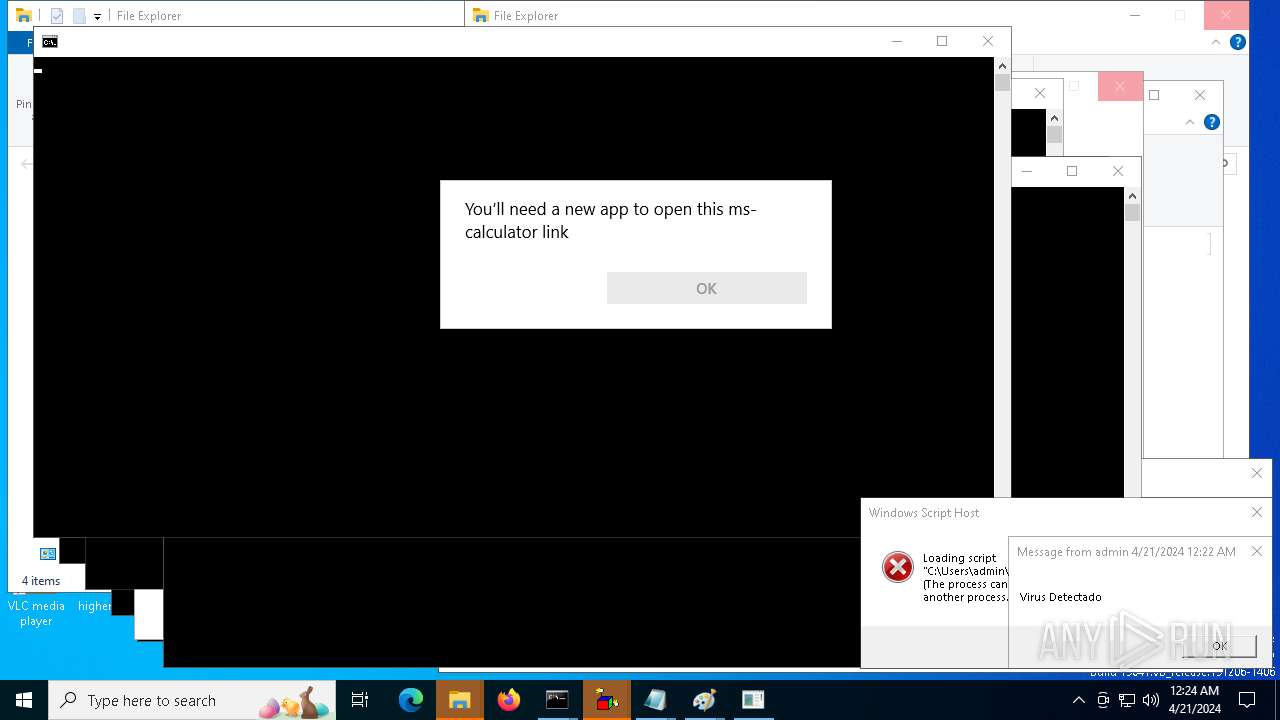
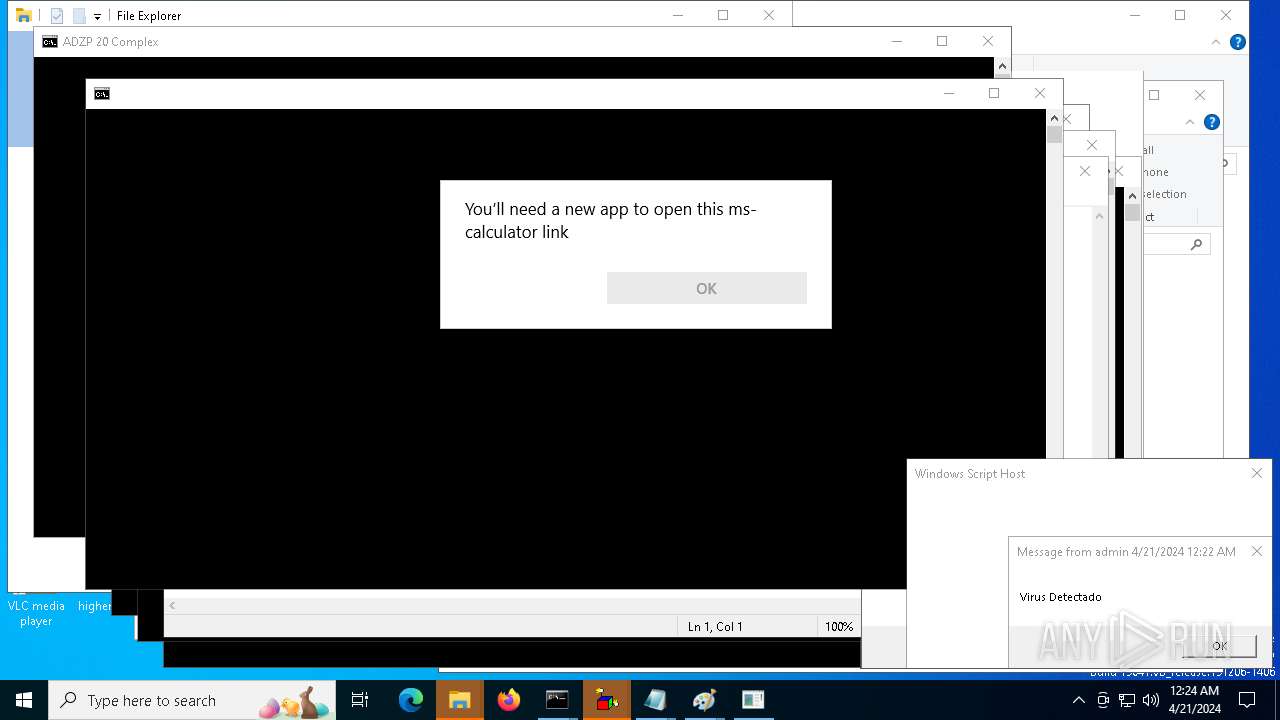
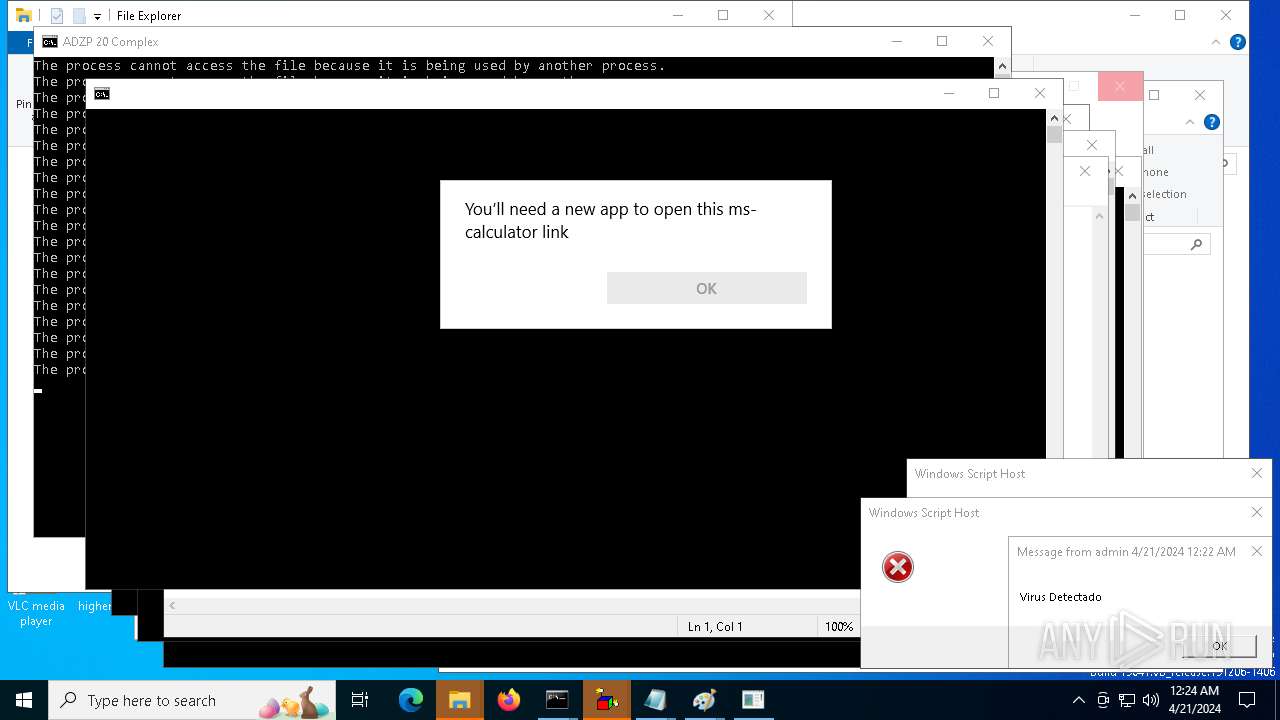
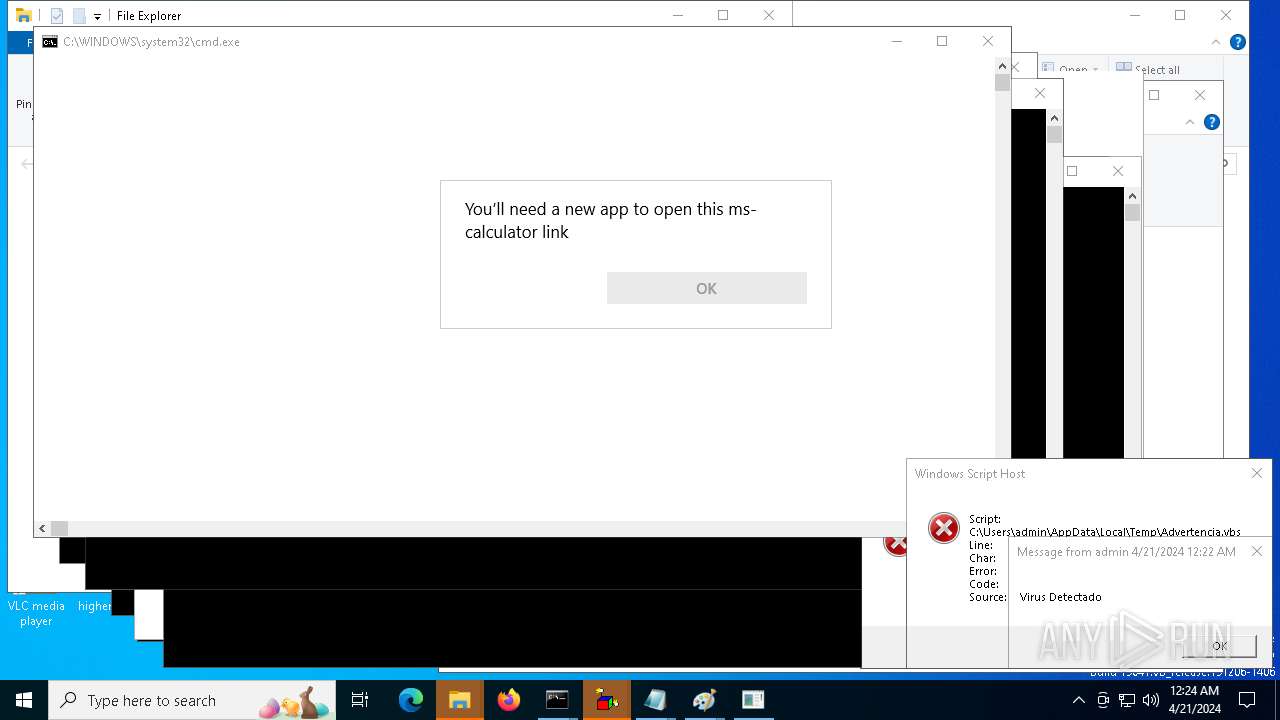
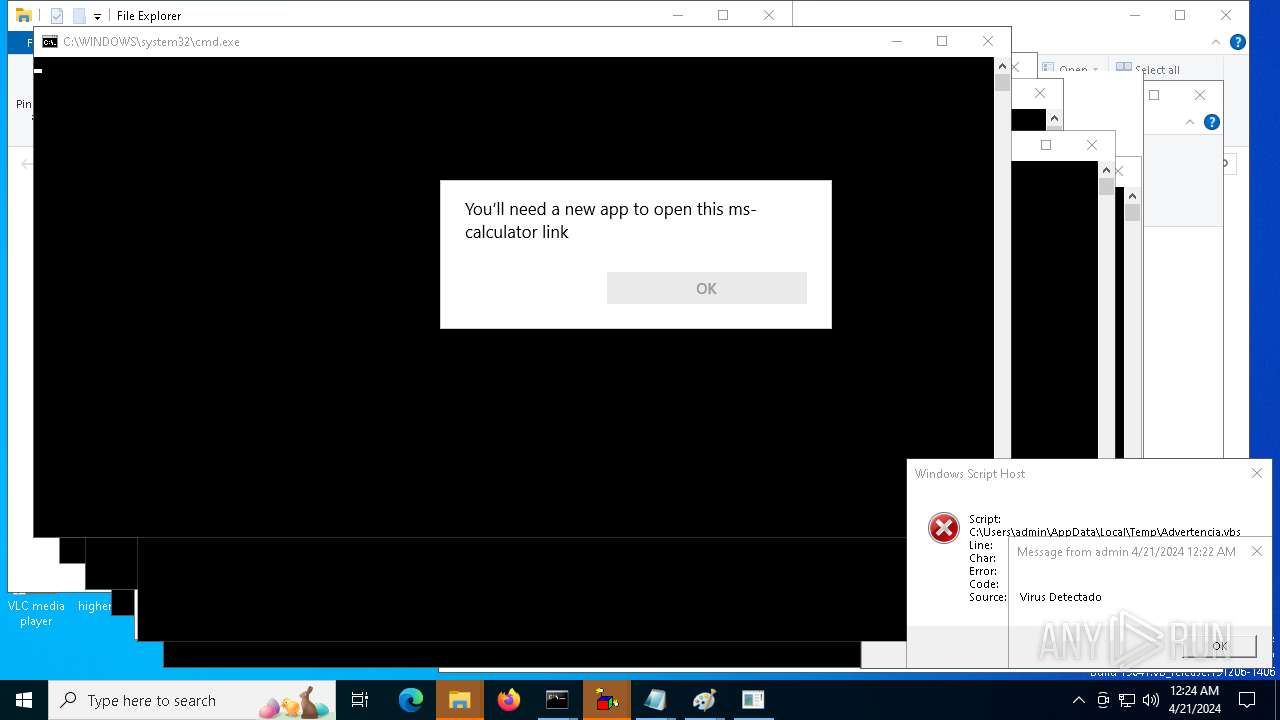
| 1136 | msg * Virus Detectado | C:\Windows\System32\msg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Message Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
87 958
Read events
87 768
Write events
190
Delete events
0
Modification events
| (PID) Process: | (4000) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4000) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4000) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4000) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (2304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (980) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Twain_20 |
Value: C:\Users\admin\AppData\Local\Temp\Twain_20.cmd | |||
Executable files
0
Suspicious files
0
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
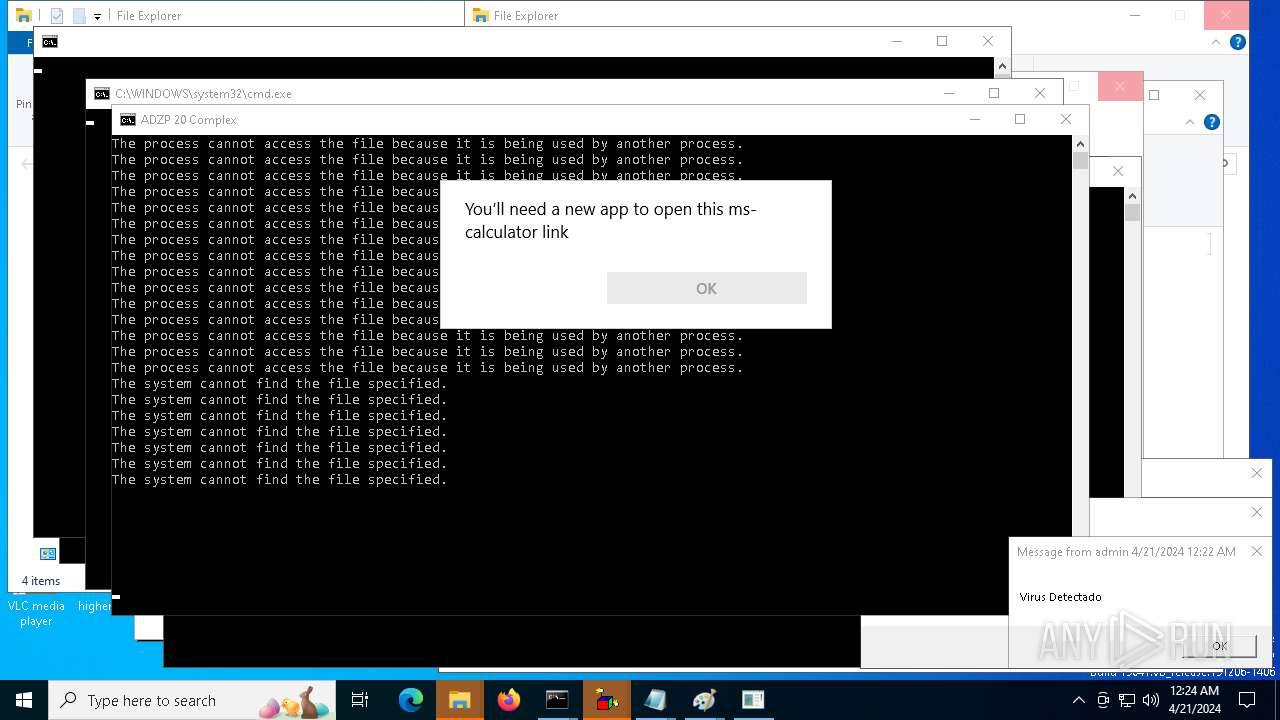
| 1296 | certutil.exe | C:\Users\admin\AppData\Local\Temp\ADZP-20-Complex.bat | text | |
MD5:591700C81FBD38CF8C83092030536C14 | SHA256:29415D32850D821D9854BFD6EDABEE920052E0920E6ECEEC187EA57B8A3C707E | |||
| 2304 | cmd.exe | C:\Users\admin\AppData\Local\Temp\x.bin | text | |
MD5:2E40C97F7790FED7606C2AB881340CE5 | SHA256:299FEDC96D0EAF4F1BF6398FB9C8D30B1F3F10571E834B93432BB02297B0648F | |||
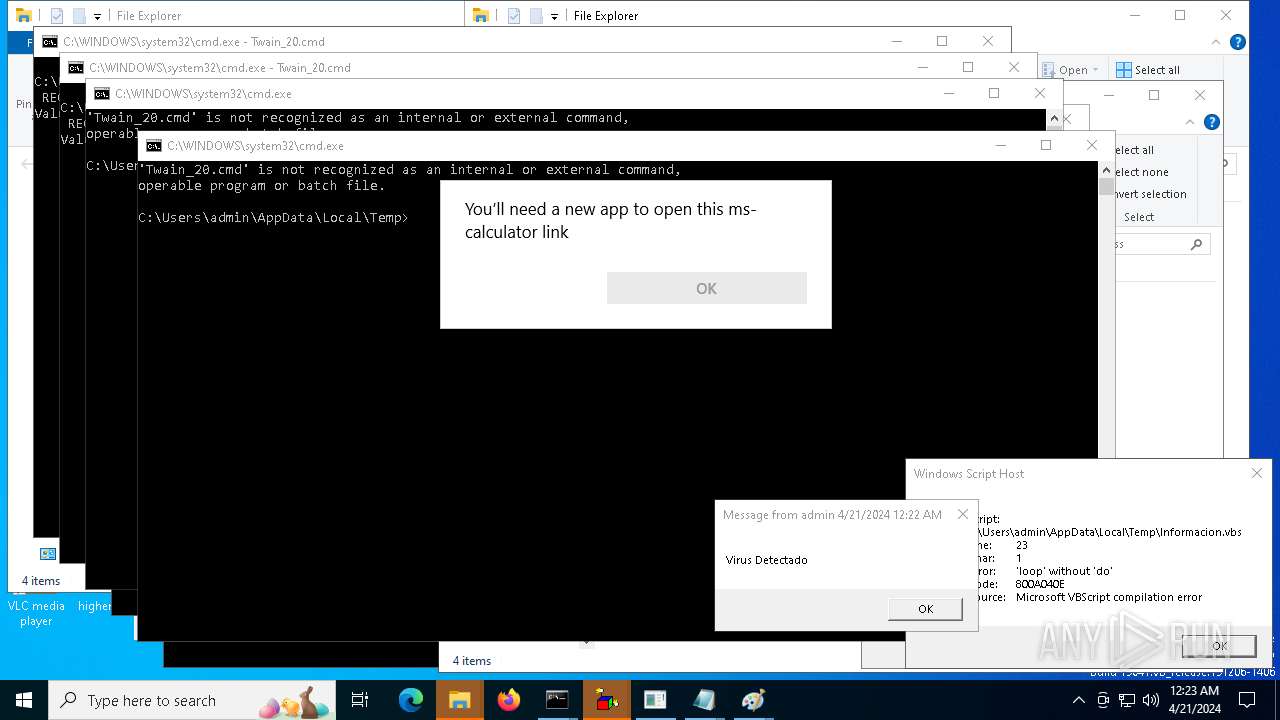
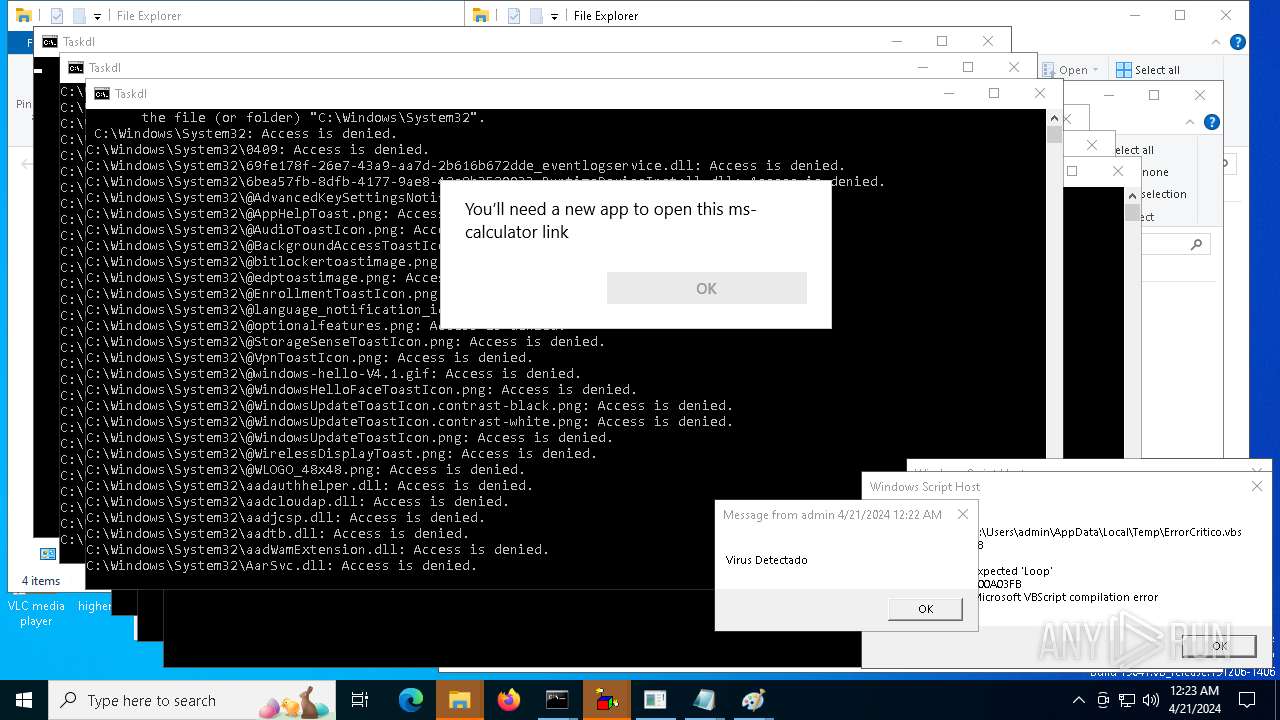
| 2304 | cmd.exe | C:\Users\admin\AppData\Local\Temp\ErrorCritico.vbs | text | |
MD5:08121EA7E3B2EB7EDFC85252B937AAEB | SHA256:31CD4463ECC62DC846DBAEE0A5446D4BF11100BEFF1B01AE88E234B6C29329C2 | |||
| 2304 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Autorun.inf | ini | |
MD5:9A9FED65AE5AECB2E2723DCCF0F0B34E | SHA256:B9EB9A01994285B8A10189321D0CF6055AD92AE659D6603F7D1FE835F39CA1D2 | |||
| 4172 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Twain_20.cmd | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
| 6268 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Twain_20.cmd | text | |
MD5:D56BB0B1144F4F8A973FB96EA18FDED7 | SHA256:78D6C4B8520F1781F540C264B143CE0357244BEB0C8F572D1533F573B32C2E66 | |||
| 8460 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Twain_20.cmd | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
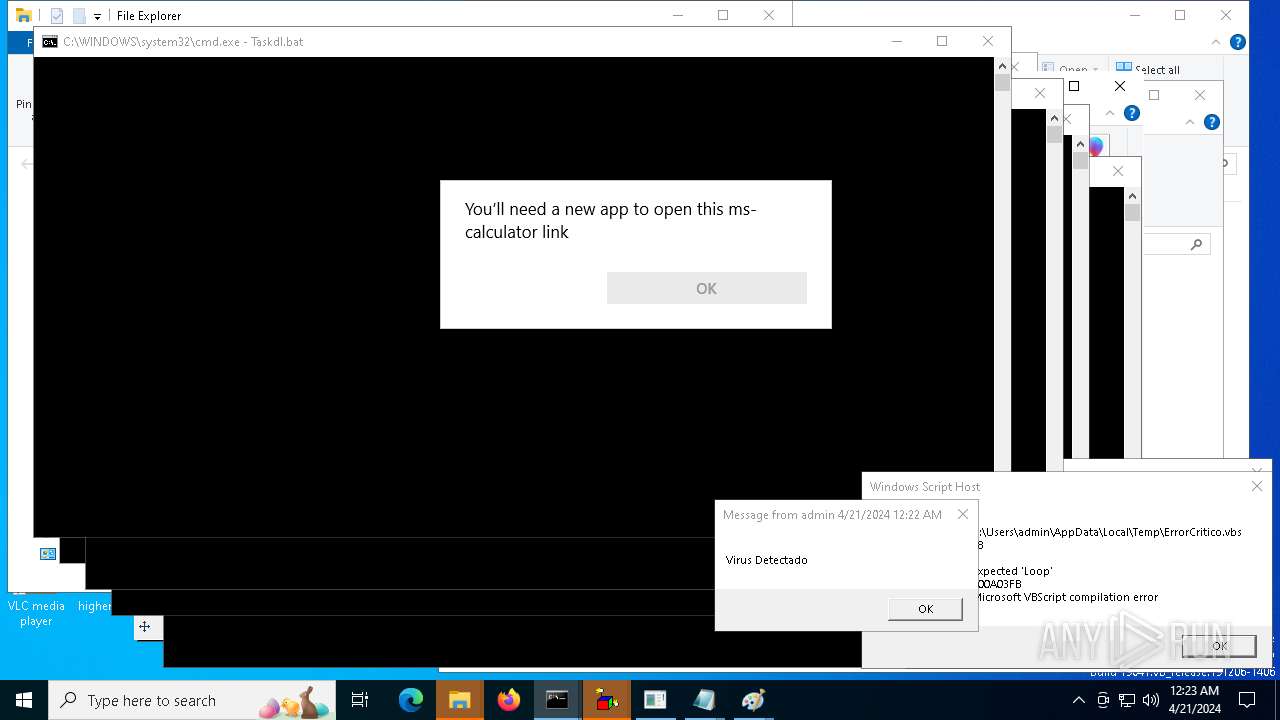
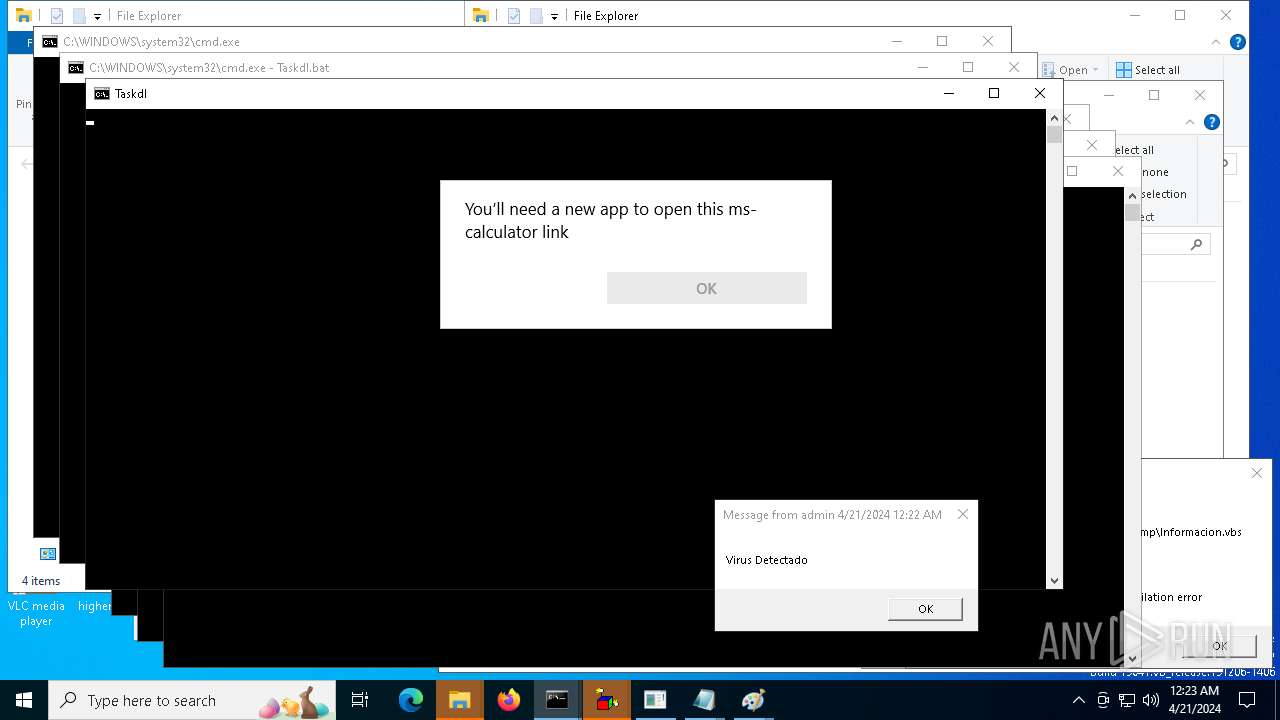
| 14724 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Taskdl.bat | text | |
MD5:5CE25367001379F6848ECBE30B0EFBA0 | SHA256:E76F2F5F180AE0D855927092E74AFBFC42866444C43B0DDD20336C33FEA4F353 | |||
| 9876 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Twain_20.cmd | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
| 9316 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Twain_20.cmd | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | svchost.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2612 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.3.crl | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
— | — | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.22.242.121:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4008 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
3952 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
552 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5152 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3952 | svchost.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3196 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
2612 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2612 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |