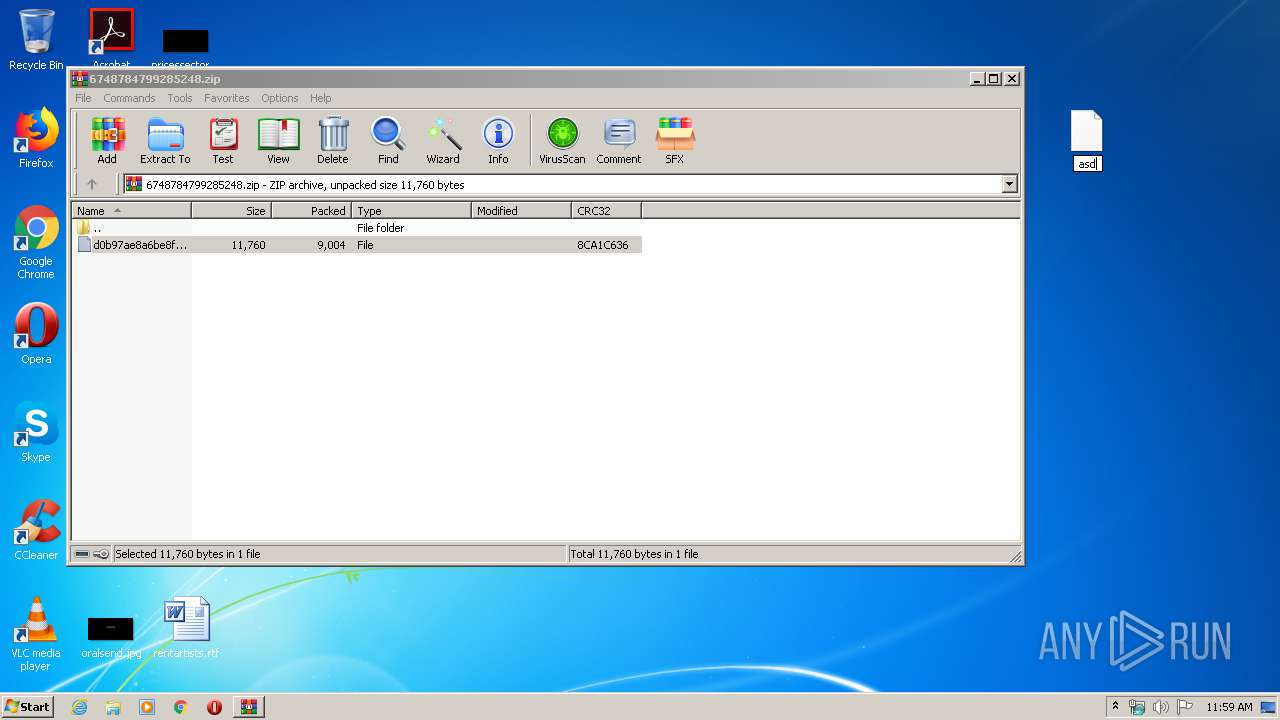
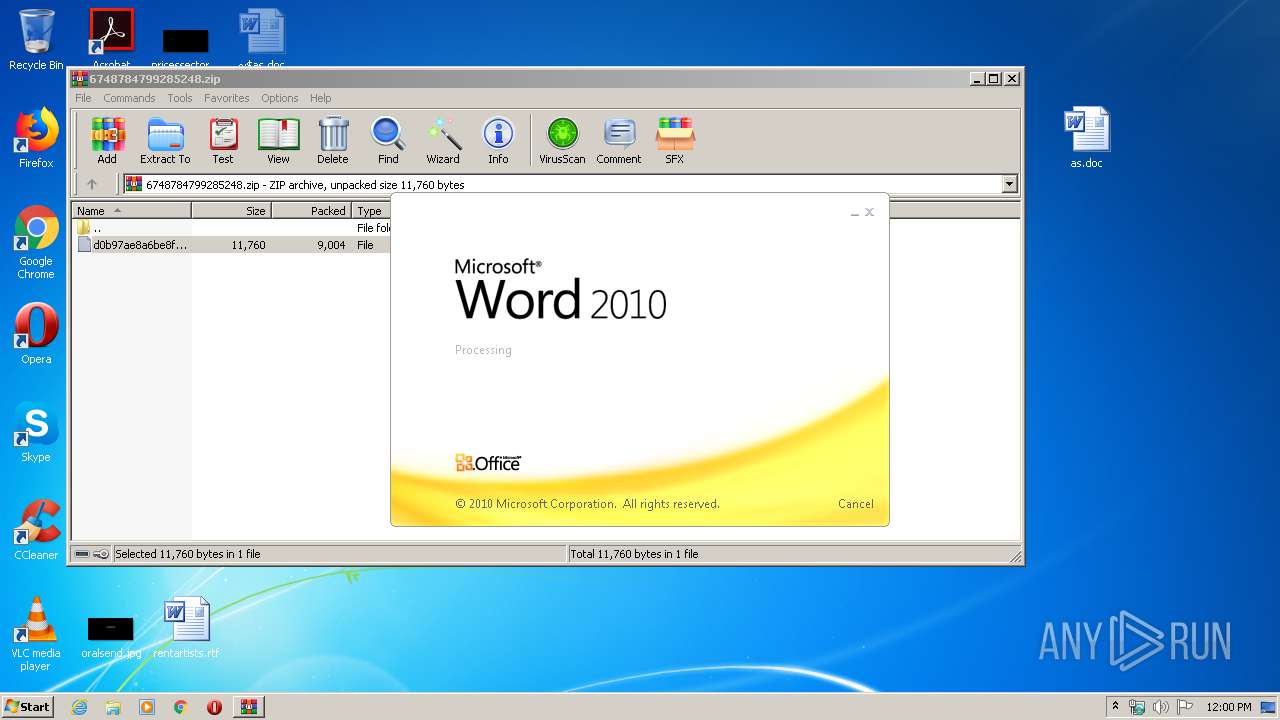
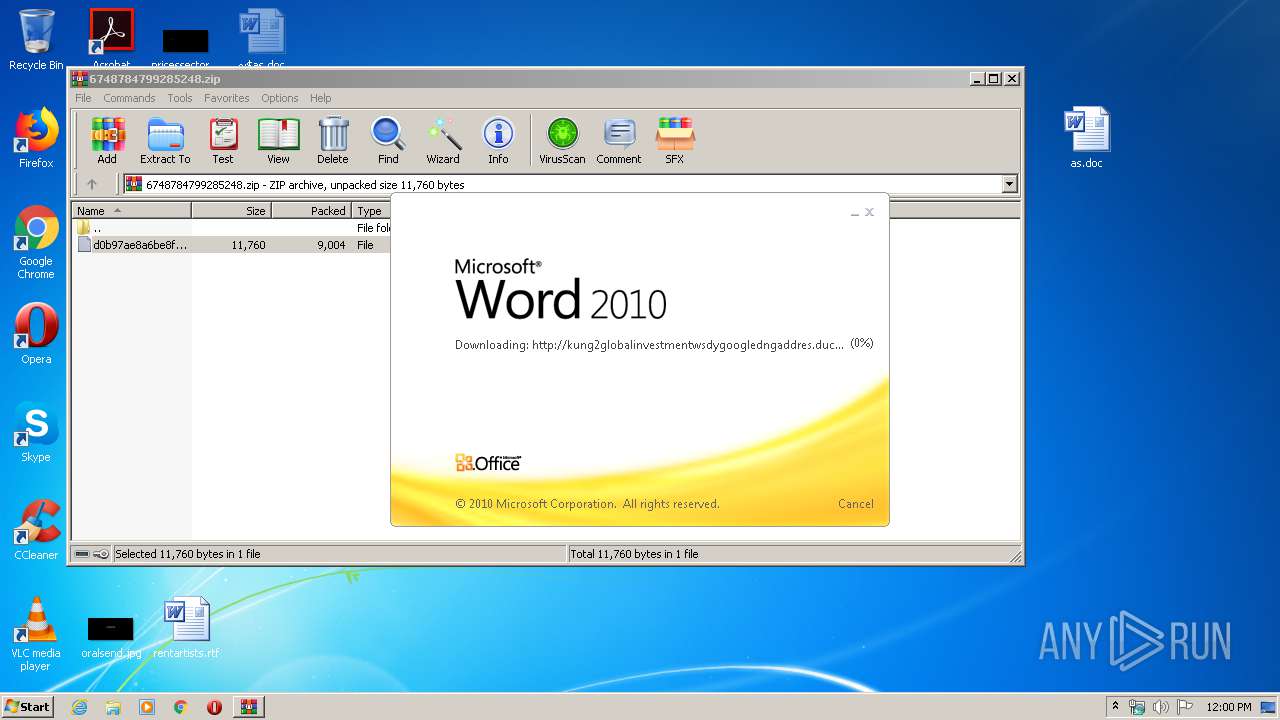
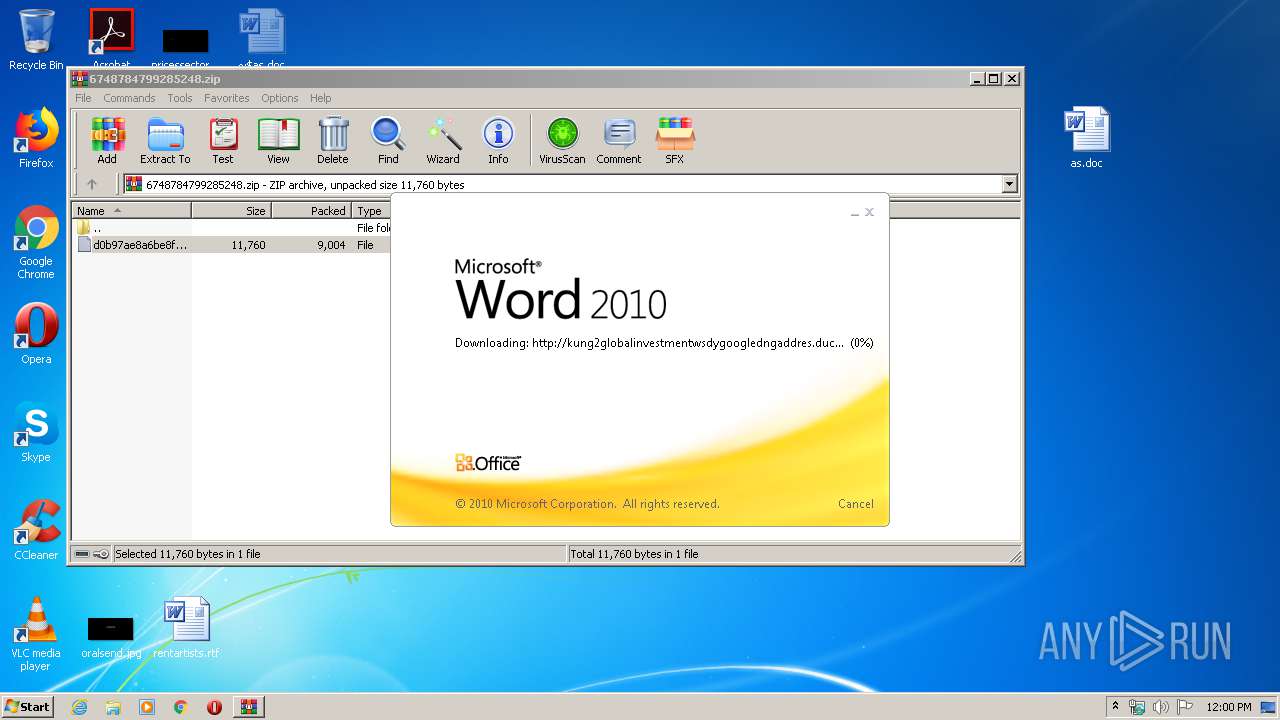
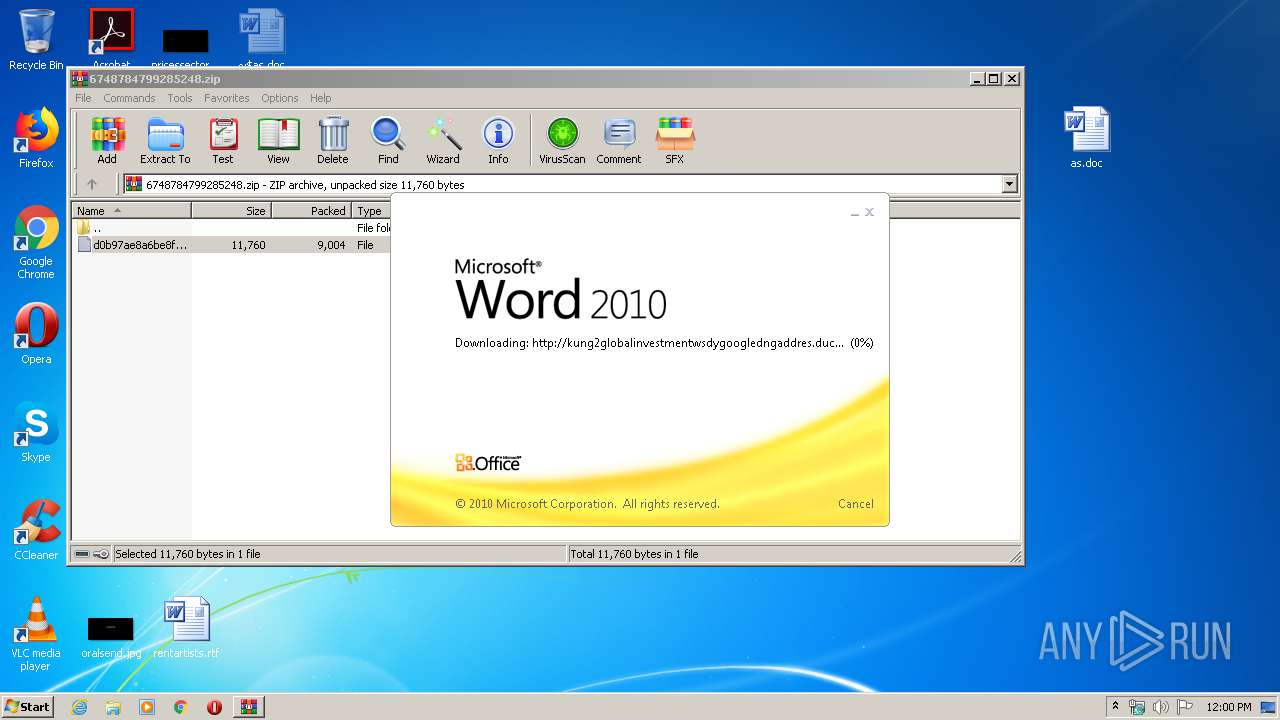
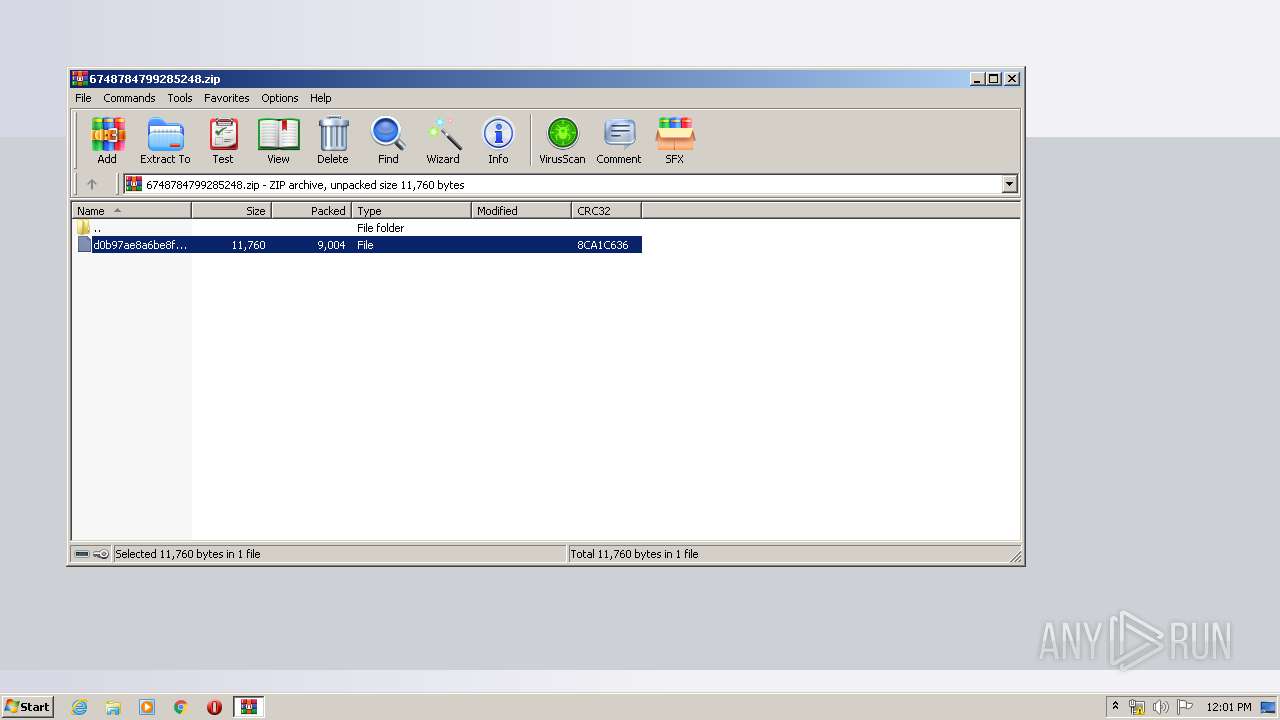
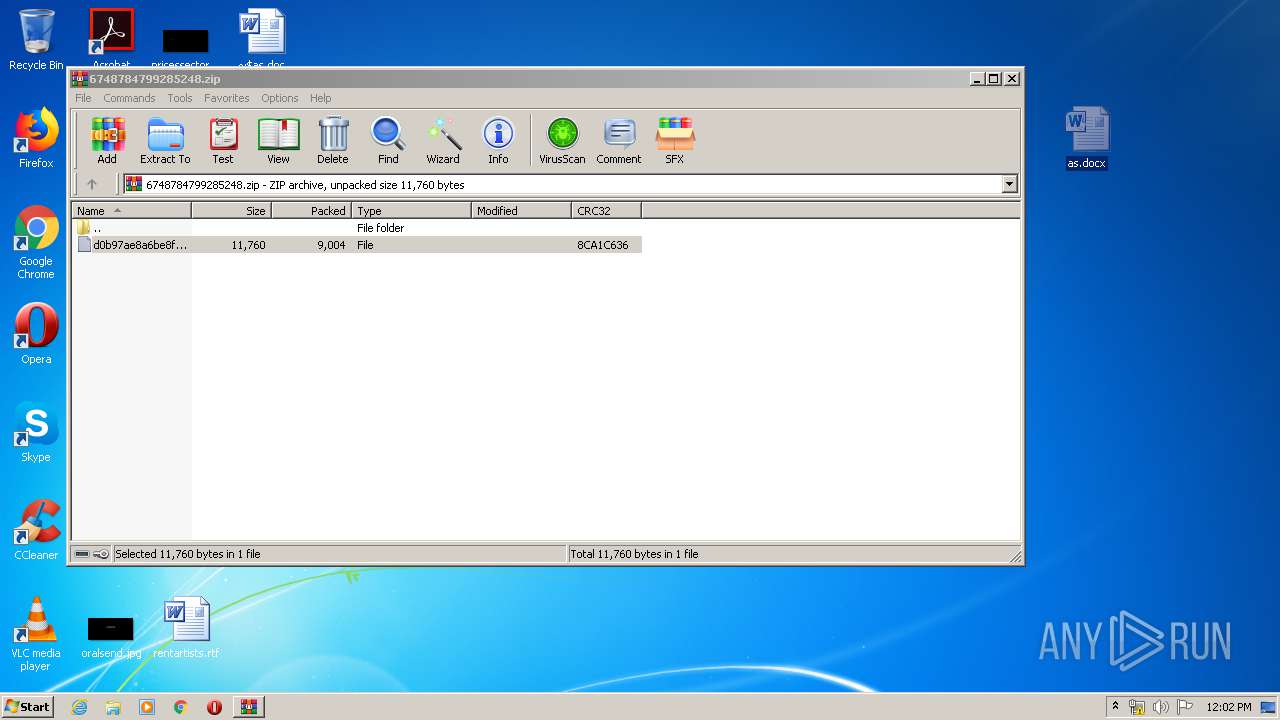
| File name: | 6748784799285248.zip |
| Full analysis: | https://app.any.run/tasks/de1857d4-a419-4c5f-bd51-df8a09f57bf0 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2020, 11:59:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 1D96324541643FA76DB00EEF242C8727 |
| SHA1: | 6BB580B51B9B3013735DEC97F078D979FA18E244 |
| SHA256: | D65C569C047982B2801987A371F1EC6905B88BF472E35DB4845727AF0B7E32B5 |
| SSDEEP: | 192:euUlUy/87Dh7bFTqpQ3JXKxVBsw03TUOKeQDk+xaNN6VIt:el87DhdqpQ3JXG2B3wOKtcb |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- WINWORD.EXE (PID: 956)
- WINWORD.EXE (PID: 3684)
Starts Internet Explorer
- MSOXMLED.EXE (PID: 3560)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 3772)
- iexplore.exe (PID: 2840)
Creates files in the user directory
- WINWORD.EXE (PID: 956)
- WINWORD.EXE (PID: 3684)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 956)
- WINWORD.EXE (PID: 3684)
- EXCEL.EXE (PID: 2704)
- WINWORD.EXE (PID: 548)
Manual execution by user
- MSOXMLED.EXE (PID: 3560)
- WINWORD.EXE (PID: 956)
- WINWORD.EXE (PID: 3684)
- EXCEL.EXE (PID: 2704)
- WINWORD.EXE (PID: 548)
Reads Internet Cache Settings
- iexplore.exe (PID: 2592)
- iexplore.exe (PID: 2840)
Changes internet zones settings
- iexplore.exe (PID: 2592)
Application launched itself
- iexplore.exe (PID: 2592)
Reads settings of System Certificates
- iexplore.exe (PID: 2592)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2592)
Changes settings of System certificates
- iexplore.exe (PID: 2592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x8ca1c636 |
| ZipCompressedSize: | 9004 |
| ZipUncompressedSize: | 11760 |
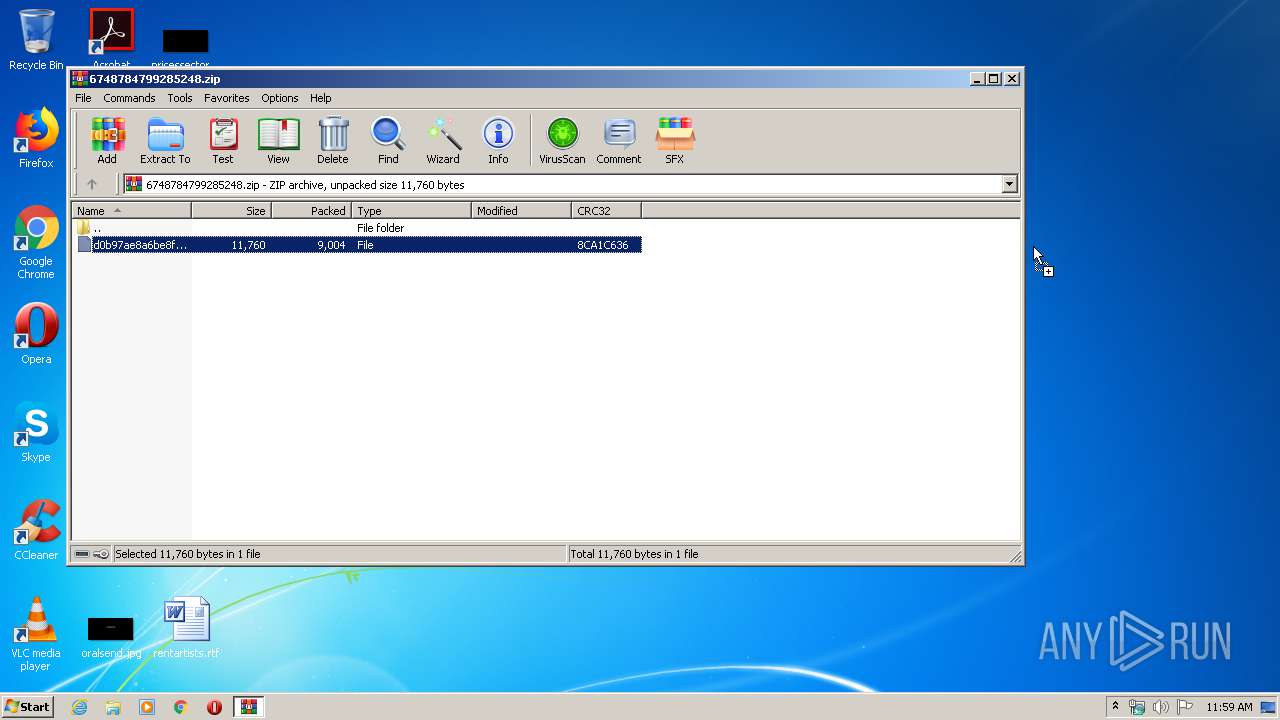
| ZipFileName: | d0b97ae8a6be8f1142ae78abc8d96a7401bb94434daedcff0b7b35f0654e3b4a |
Total processes
55
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\asd.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
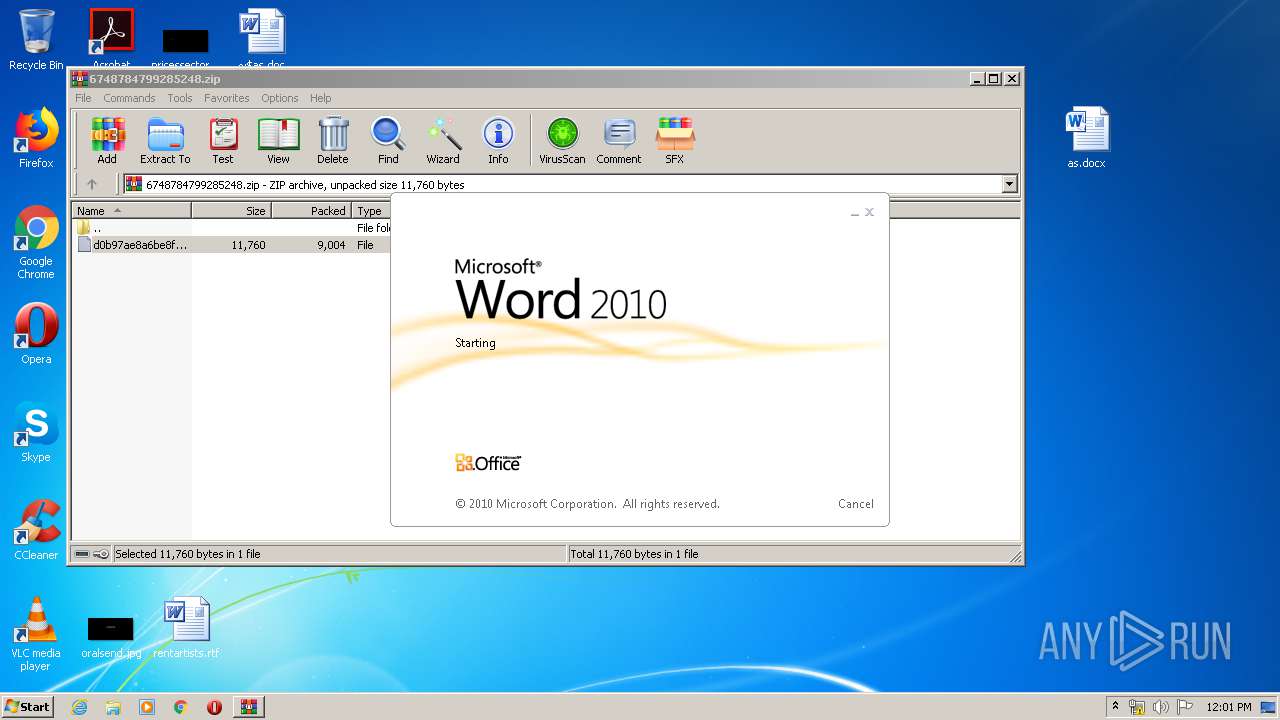
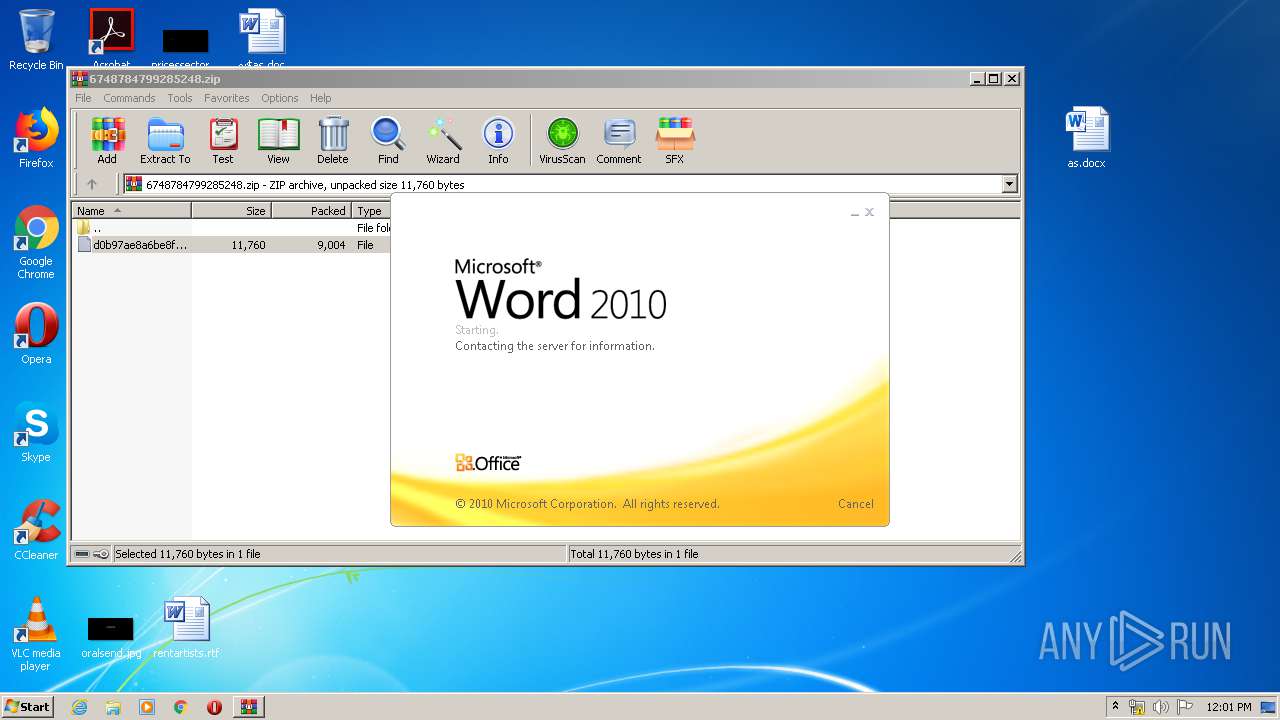
| 956 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\as.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\6748784799285248.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2592 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | MSOXMLED.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2840 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2592 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3560 | "C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE" /verb open "C:\Users\admin\Desktop\asd.xml" | C:\Program Files\Common Files\Microsoft Shared\OFFICE14\MSOXMLED.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: XML Editor Exit code: 0 Version: 14.0.4750.1000 Modules
| |||||||||||||||
| 3684 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\as.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3772 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2592 CREDAT:78849 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
13 420
Read events
4 347
Write events
6 178
Delete events
2 895
Modification events
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\6748784799285248.zip | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3560) MSOXMLED.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
34
Text files
6
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1348.27960\d0b97ae8a6be8f1142ae78abc8d96a7401bb94434daedcff0b7b35f0654e3b4a | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD831BE33F0A8D150.TMP | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF957235AFB689CFA.TMP | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF46F651F9EFF4C402.TMP | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF070088AB240C508A.TMP | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE526C22779D76424.TMP | — | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF14DB2CB672B1FA89.TMP | — | |
MD5:— | SHA256:— | |||
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1689.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{0F8DAE4A-9A5E-4F02-9B60-730410652F38} | — | |
MD5:— | SHA256:— | |||
| 956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{CCEF1B87-6D18-461C-AA74-FEB4E082418D} | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
14
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
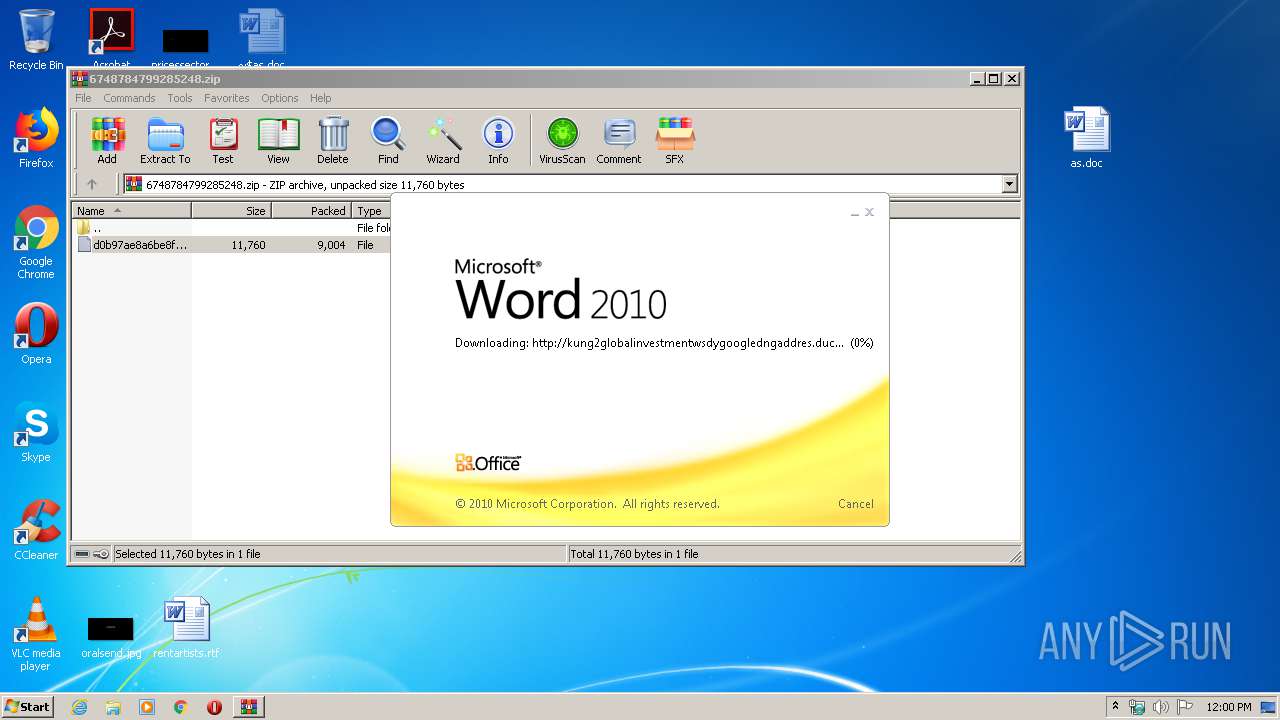
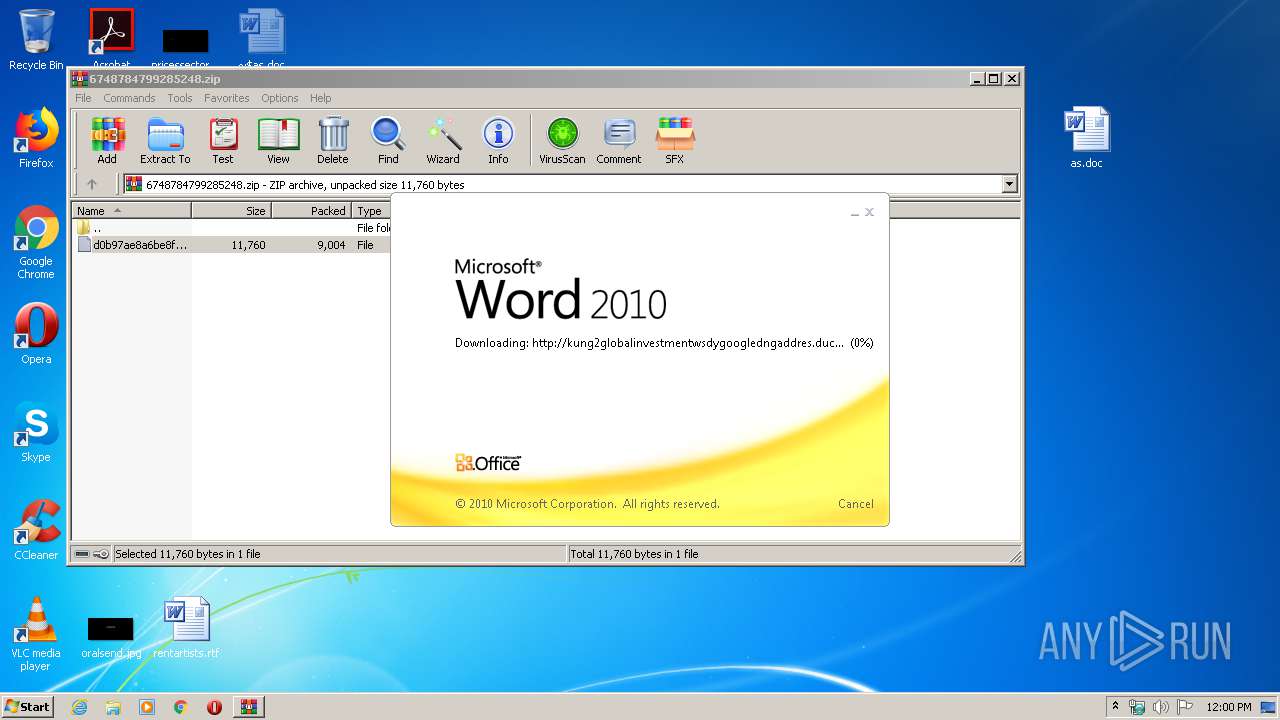
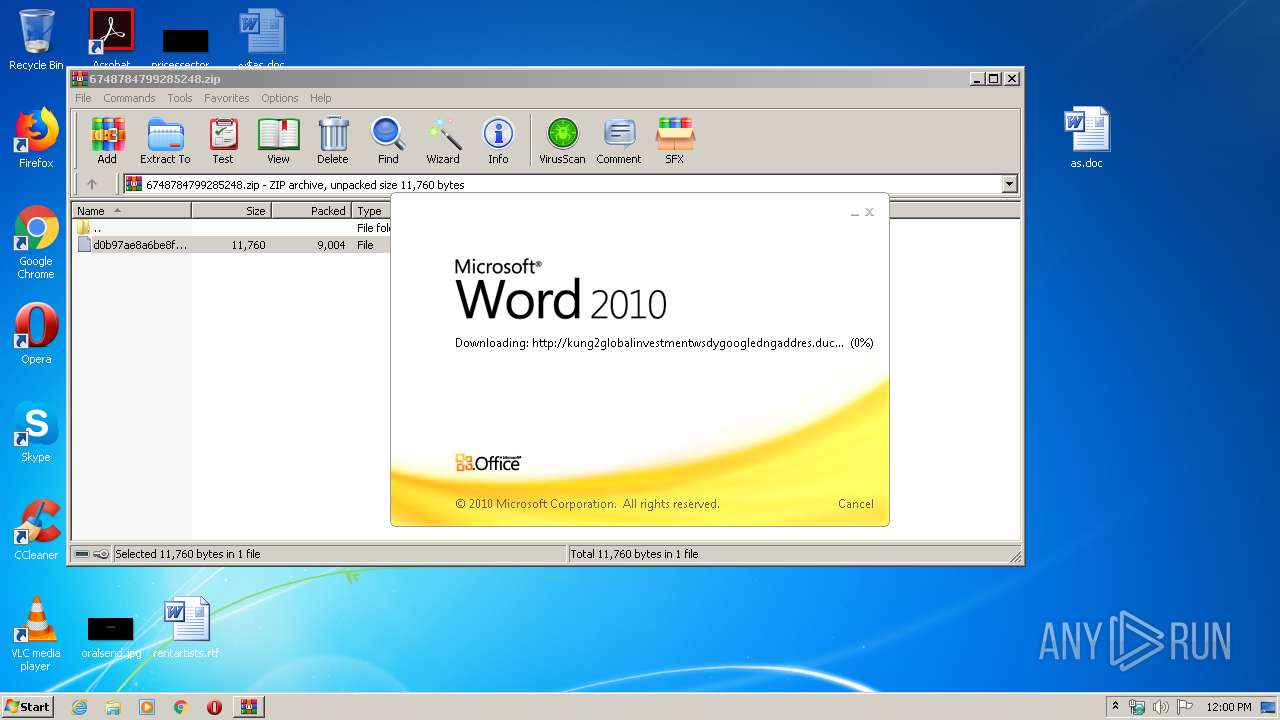
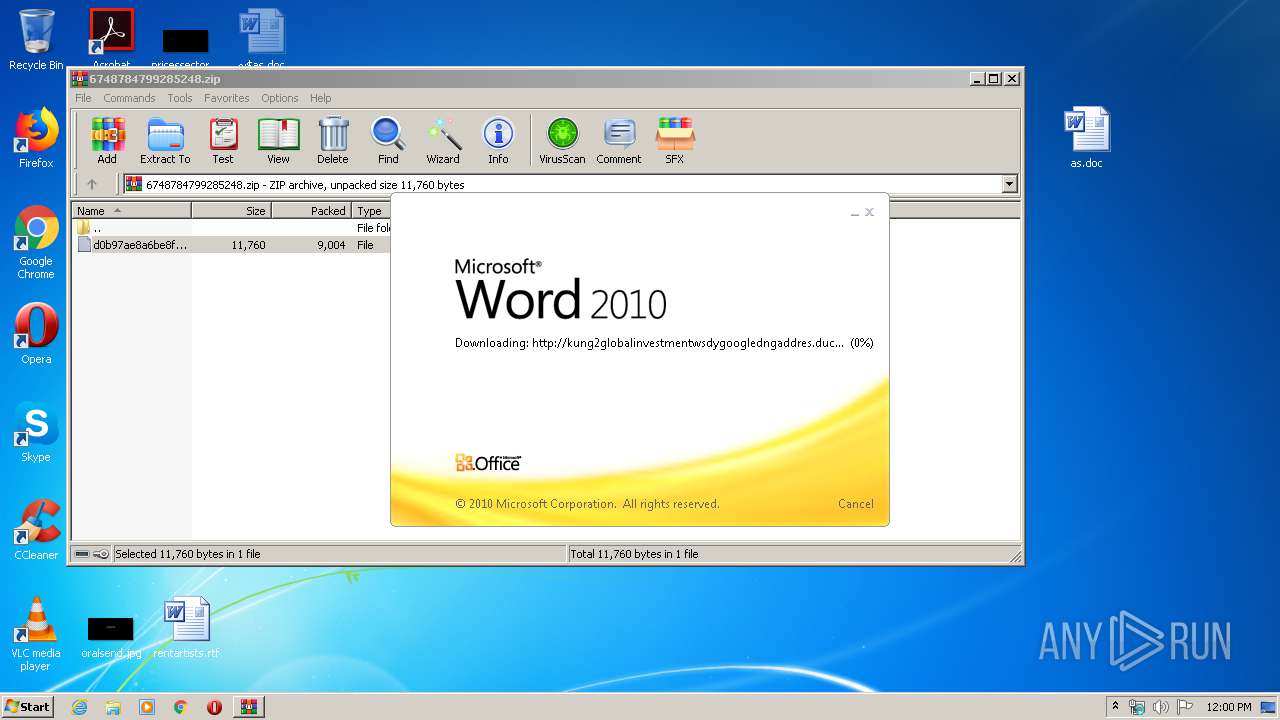
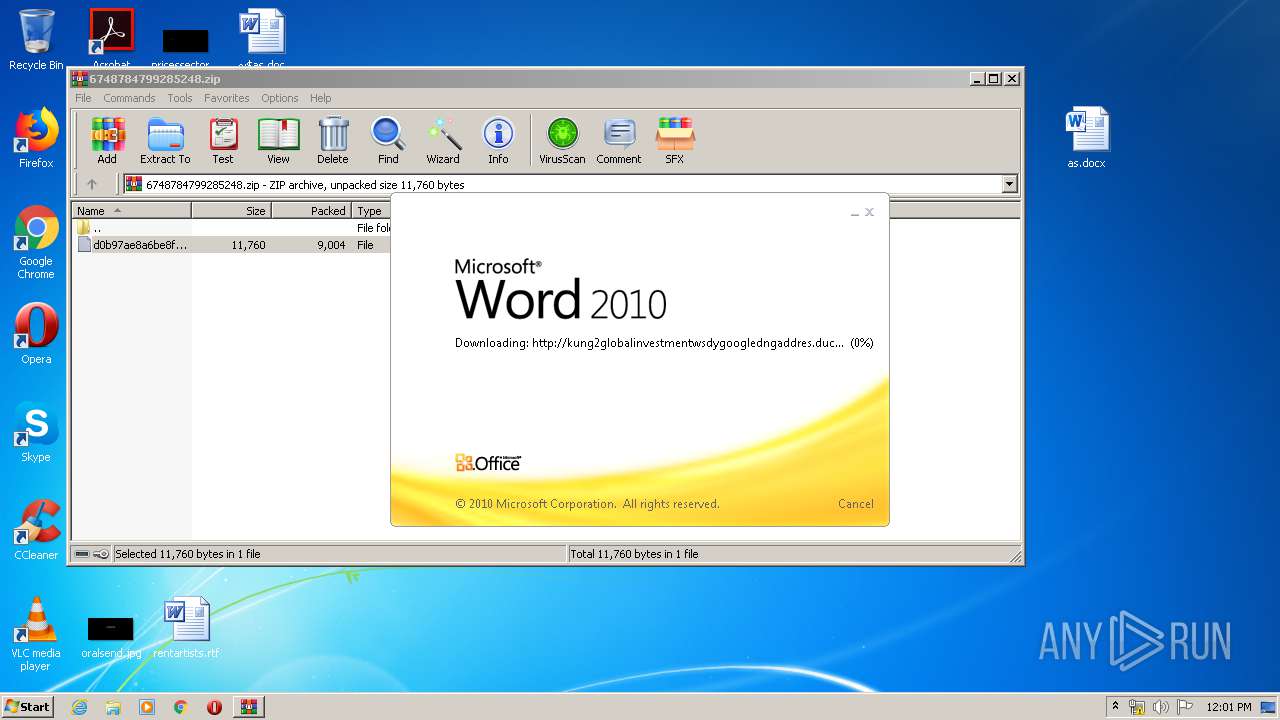
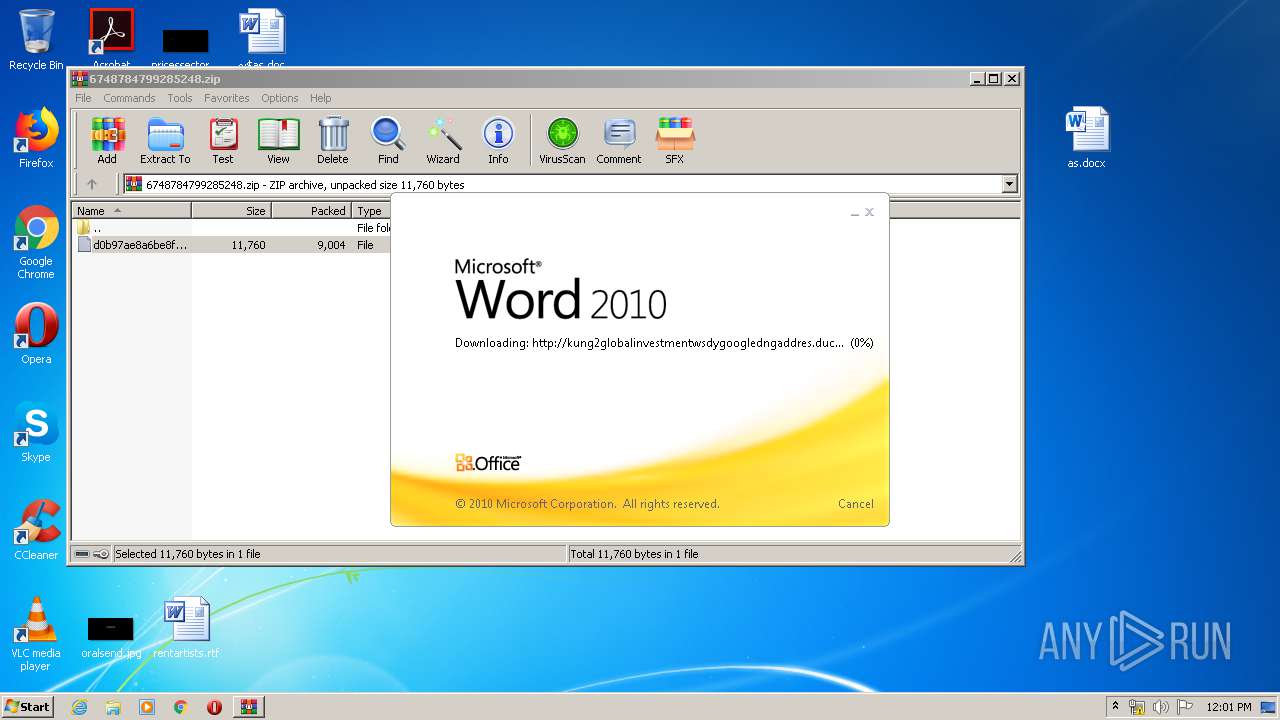
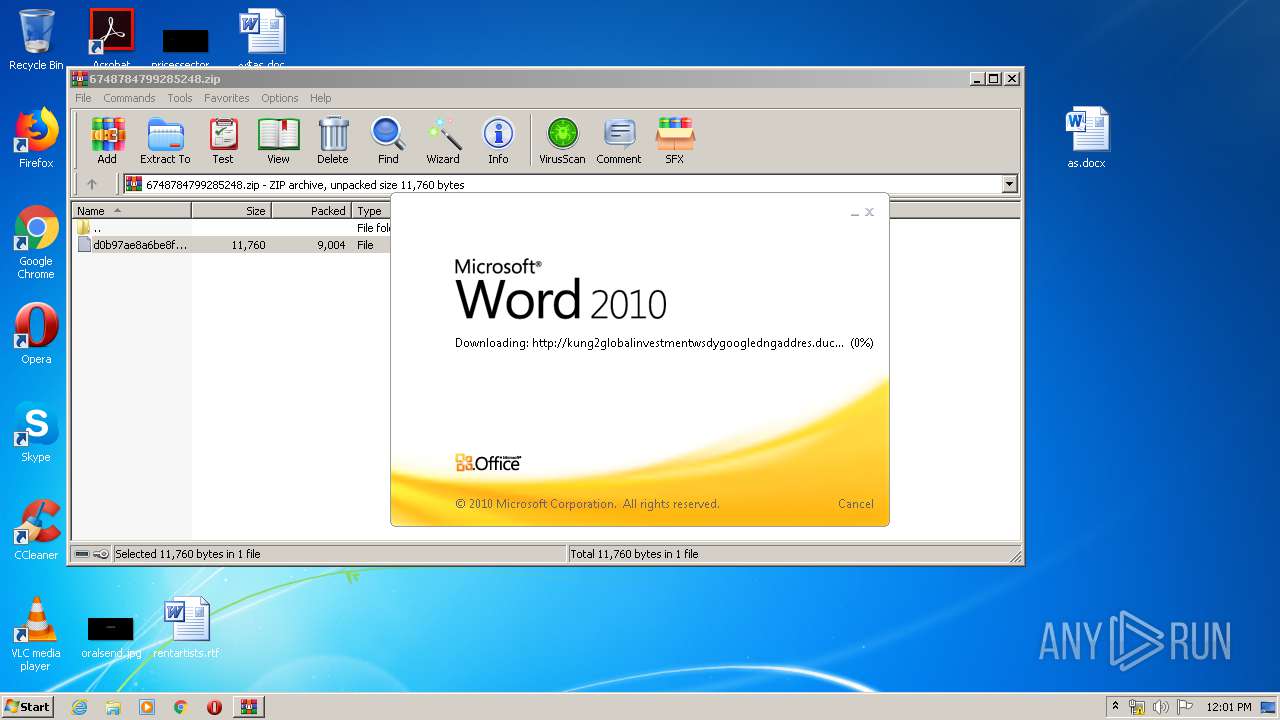
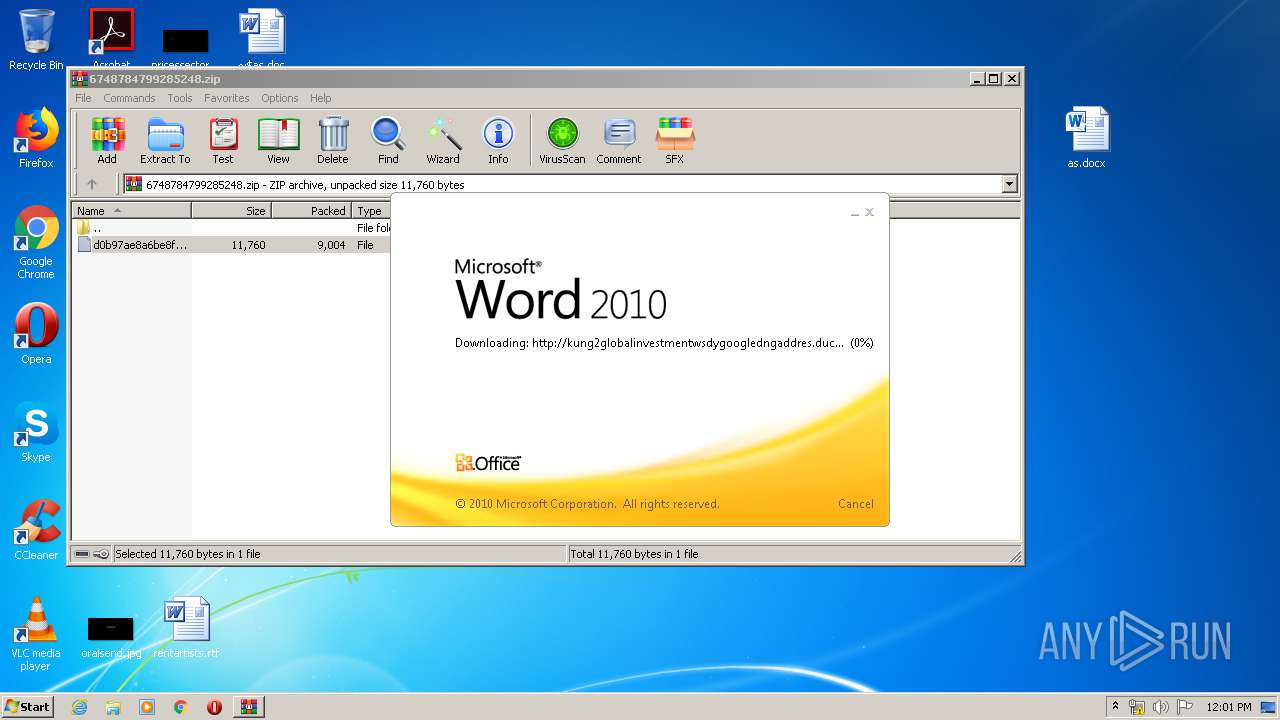
956 | WINWORD.EXE | OPTIONS | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office/ | US | — | — | malicious |
824 | svchost.exe | OPTIONS | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office | US | — | — | malicious |
956 | WINWORD.EXE | HEAD | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office/invoice_11131.doc | US | — | — | malicious |
824 | svchost.exe | OPTIONS | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office | US | — | — | malicious |
956 | WINWORD.EXE | GET | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office/invoice_11131.doc | US | — | — | malicious |
3684 | WINWORD.EXE | OPTIONS | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office/ | US | — | — | malicious |
3684 | WINWORD.EXE | HEAD | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office/invoice_11131.doc | US | — | — | malicious |
3684 | WINWORD.EXE | GET | — | 192.169.69.25:80 | http://kung2globalinvestmentwsdygoogledngaddres.duckdns.org/office/invoice_11131.doc | US | — | — | malicious |
2592 | iexplore.exe | GET | 200 | 72.21.91.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2592 | iexplore.exe | GET | 200 | 72.21.91.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
956 | WINWORD.EXE | 192.169.69.25:80 | kung2globalinvestmentwsdygoogledngaddres.duckdns.org | Wowrack.com | US | malicious |
824 | svchost.exe | 192.169.69.25:80 | kung2globalinvestmentwsdygoogledngaddres.duckdns.org | Wowrack.com | US | malicious |
2592 | iexplore.exe | 72.21.91.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3684 | WINWORD.EXE | 192.169.69.25:80 | kung2globalinvestmentwsdygoogledngaddres.duckdns.org | Wowrack.com | US | malicious |
2592 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kung2globalinvestmentwsdygoogledngaddres.duckdns.org |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |