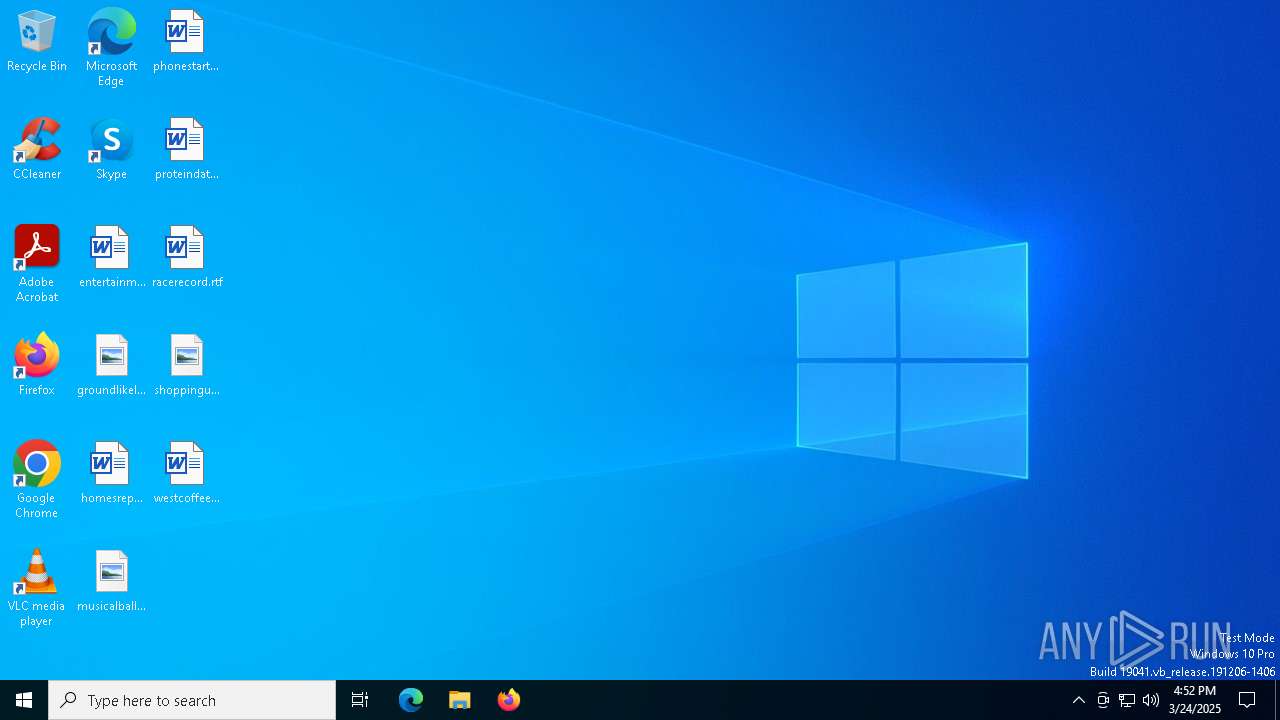
| File name: | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit |
| Full analysis: | https://app.any.run/tasks/f207dd2e-55fe-44d2-8052-482a4a6d2e79 |
| Verdict: | Malicious activity |
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | March 24, 2025, 16:52:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 3DFD85447B58DD8369F27C495E846E98 |
| SHA1: | ED991B92EC7161442C449EDF62B22A3D3CF20C95 |
| SHA256: | D64F55A0EAFC1E08231B95D4CB1F89AA60E7A8F8A6D99F2976D4DDEFB5A94F2D |
| SSDEEP: | 3072:SmhXodguLP/5qUpfDT6zT73g9uMkHUOE8CVSrB85R:yKzAMS8CAr+5 |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 4776)
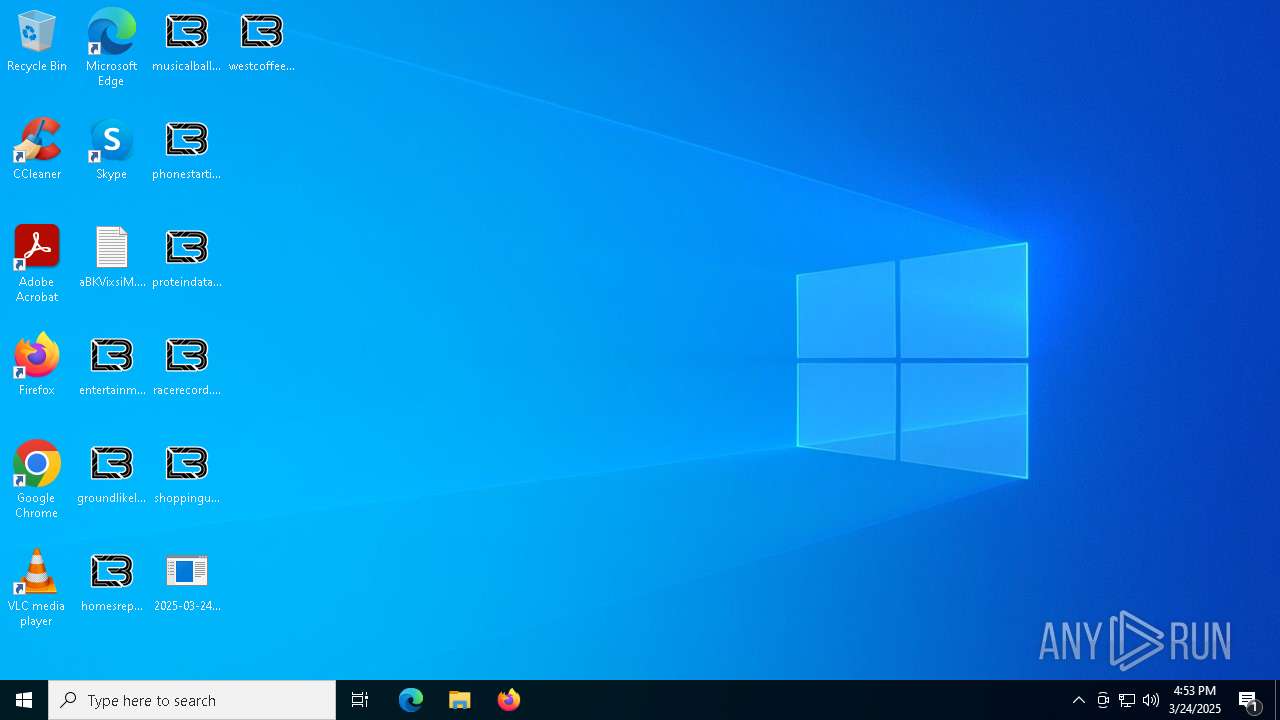
Renames files like ransomware
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
[YARA] LockBit is detected
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
Actions looks like stealing of personal data
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
Steals credentials from Web Browsers
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
RANSOMWARE has been detected
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 2108)
Write to the desktop.ini file (may be used to cloak folders)
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
INFO
Checks supported languages
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 4784)
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
- ShellExperienceHost.exe (PID: 2108)
- SearchApp.exe (PID: 6660)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 4776)
Creates files in the program directory
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
Reads the computer name
- ShellExperienceHost.exe (PID: 2108)
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 4784)
- SearchApp.exe (PID: 6660)
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
Creates files or folders in the user directory
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
Manual execution by a user
- OpenWith.exe (PID: 6404)
- notepad.exe (PID: 4628)
- OpenWith.exe (PID: 5072)
- wscript.exe (PID: 2404)
- OpenWith.exe (PID: 6572)
- OpenWith.exe (PID: 3020)
- wscript.exe (PID: 6480)
- OpenWith.exe (PID: 456)
- OpenWith.exe (PID: 4380)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6404)
- OpenWith.exe (PID: 456)
- OpenWith.exe (PID: 5072)
- OpenWith.exe (PID: 6572)
- OpenWith.exe (PID: 4380)
- OpenWith.exe (PID: 3020)
Reads the machine GUID from the registry
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 4784)
- SearchApp.exe (PID: 6660)
Create files in a temporary directory
- 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe (PID: 1512)
Checks proxy server information
- SearchApp.exe (PID: 6660)
Process checks computer location settings
- SearchApp.exe (PID: 6660)
Reads the software policy settings
- SearchApp.exe (PID: 6660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:09 01:27:01+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.12 |
| CodeSize: | 99328 |
| InitializedDataSize: | 50688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1946f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
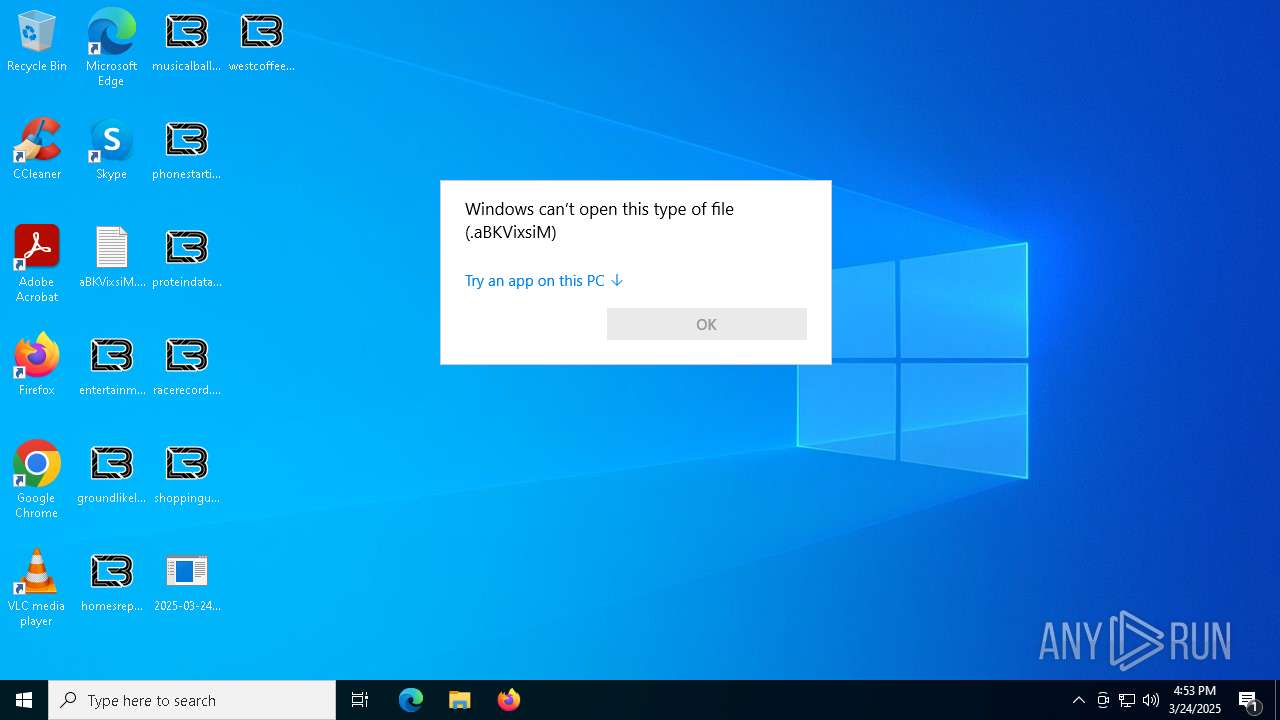
| 456 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\operationsbeginning.jpg.aBKVixsiM | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe" | C:\Users\admin\Desktop\2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2108 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2404 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\background.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3020 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\bringwall.jpg.aBKVixsiM | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\manifest.json | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\aBKVixsiM.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | "C:\Users\admin\Desktop\2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe" | C:\Users\admin\Desktop\2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5072 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\boyscustom.png.aBKVixsiM | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 161
Read events
11 106
Write events
54
Delete events
1
Modification events
| (PID) Process: | (4776) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2108) ShellExperienceHost.exe | Key: | \REGISTRY\A\{4d4642ac-28c5-fc95-4165-b6249677214f}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000F825A02FDD9CDB01 | |||
| (PID) Process: | (6404) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aBKVixsiM\OpenWithProgids |
| Operation: | write | Name: | aBKVixsiM |
Value: | |||
| (PID) Process: | (5072) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aBKVixsiM\OpenWithProgids |
| Operation: | write | Name: | aBKVixsiM |
Value: | |||
| (PID) Process: | (6572) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aBKVixsiM\OpenWithProgids |
| Operation: | write | Name: | aBKVixsiM |
Value: | |||
| (PID) Process: | (3020) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aBKVixsiM\OpenWithProgids |
| Operation: | write | Name: | aBKVixsiM |
Value: | |||
| (PID) Process: | (456) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aBKVixsiM\OpenWithProgids |
| Operation: | write | Name: | aBKVixsiM |
Value: | |||
| (PID) Process: | (6660) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (6660) SearchApp.exe | Key: | \REGISTRY\A\{98a1ed5b-dd81-869b-b290-5f8c70aa1ea0}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000187DA377DD9CDB01 | |||
| (PID) Process: | (6660) SearchApp.exe | Key: | \REGISTRY\A\{98a1ed5b-dd81-869b-b290-5f8c70aa1ea0}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 0000FEE2A677DD9CDB01 | |||
Executable files
13
Suspicious files
1 487
Text files
1 638
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\ProgramData\aBKVixsiM.ico | image | |
MD5:88D9337C4C9CFE2D9AFF8A2C718EC76B | SHA256:95E059EF72686460884B9AEA5C292C22917F75D56FE737D43BE440F82034F438 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\GGGGGGGGGGG | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\AAAAAAAAAAA | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\LLLLLLLLLLL | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\CCCCCCCCCCC | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\DDDDDDDDDDD | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\FFFFFFFFFFF | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\EEEEEEEEEEE | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\RRRRRRRRRRR | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
| 1512 | 2025-03-24_3dfd85447b58dd8369f27c495e846e98_darkside_lockbit.exe | C:\$Recycle.Bin\S-1-5-18\IIIIIIIIIII | binary | |
MD5:350EB1DA59F2BE1A1119F36B1023C738 | SHA256:8DF95694F22989F9AC5DFC4FA3C4ABDBB1118F18B4617B872B5105D845F73D22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
22
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 204 | 2.23.227.208:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.227.208:443 | https://www.bing.com/rb/3C/ortl,cc,nc/AptopUBu7_oVDubJxwvaIprW-lI.css?bu=A4gCjAKPAg&or=w | unknown | text | 15.5 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.215:443 | https://www.bing.com/rb/6i/cir3,ortl,cc,nc/Q6mzjrsCw2J4u7BHEvcLILQ0jdw.css?bu=M9AKygrWCsoKugvKCsALygrKCsoKywvKCtILygrYC8oK3gvKCuQLygroCsoK7grKCuIKygrKCrELygr9CsoKgwvKCvcKygqJC5MLlgvKCsoKrgucC8oKogulC8oKkAzKCuoLygrJDA&or=w | unknown | text | 449 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.215:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Init | unknown | html | 127 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.208:443 | https://www.bing.com/rb/19/cir3,ortl,cc,nc/FgBbpIj0thGWZOh_xFnM9i4O7ek.css?bu=C_QJ-AOrBcoKrgmYCbcHZGRkZA&or=w | unknown | text | 19.8 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.208:443 | https://www.bing.com/rb/6i/ortl,cc,nc/QNBBNqWD9F_Blep-UqQSqnMp-FI.css?bu=AcoK&or=w | unknown | text | 6 b | whitelisted |
— | — | GET | 200 | 2.23.227.208:443 | https://www.bing.com/rp/-iNIzuEypRdgRJ6xnyVHizZ3bpM.br.js | unknown | binary | 17.0 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.215:443 | https://www.bing.com/rb/6i/ortl,cc,nc/fvNdnrKxhhxDQUEi09cCaSWpzzE.css?bu=CbYMygq7DMoKvwzKCsoKygrKCg&or=w | unknown | text | 428 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.215:443 | https://www.bing.com/rp/0u2b9EXo8LdXut1MFm4AD0phBuM.br.js | unknown | binary | 1.44 Kb | whitelisted |
— | — | GET | 200 | 2.23.227.215:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | binary | 21.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6660 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |