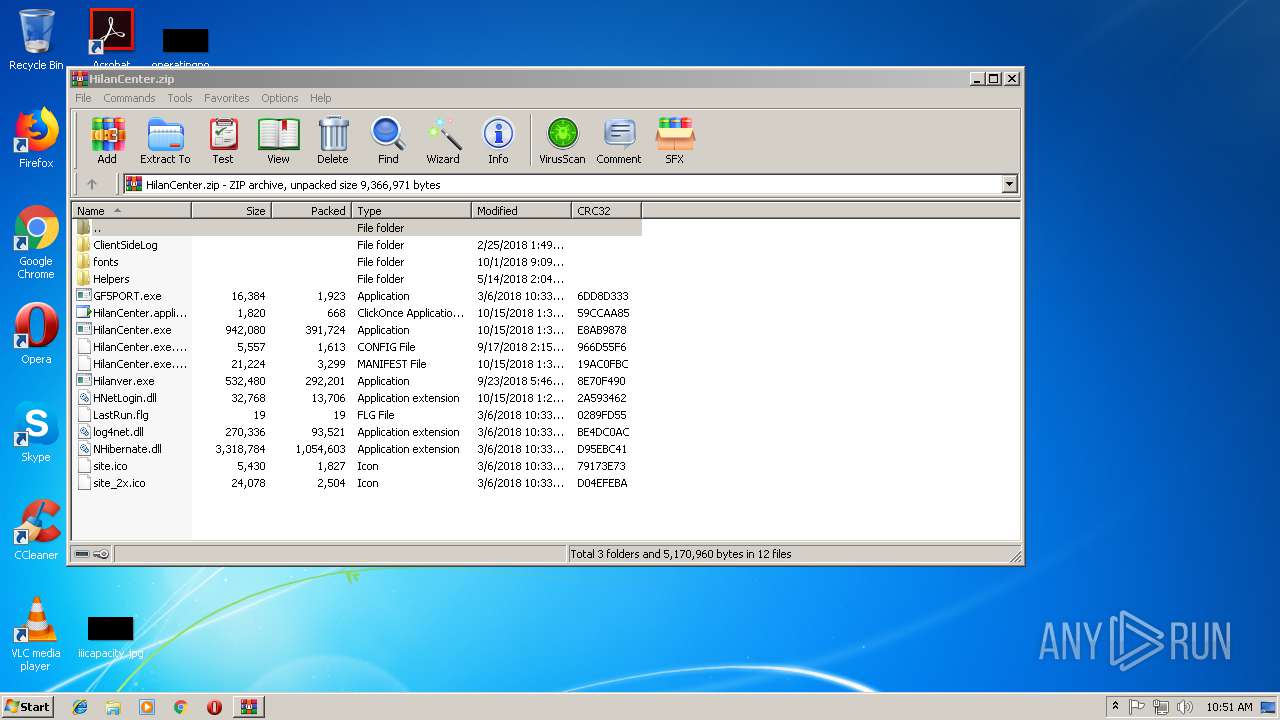
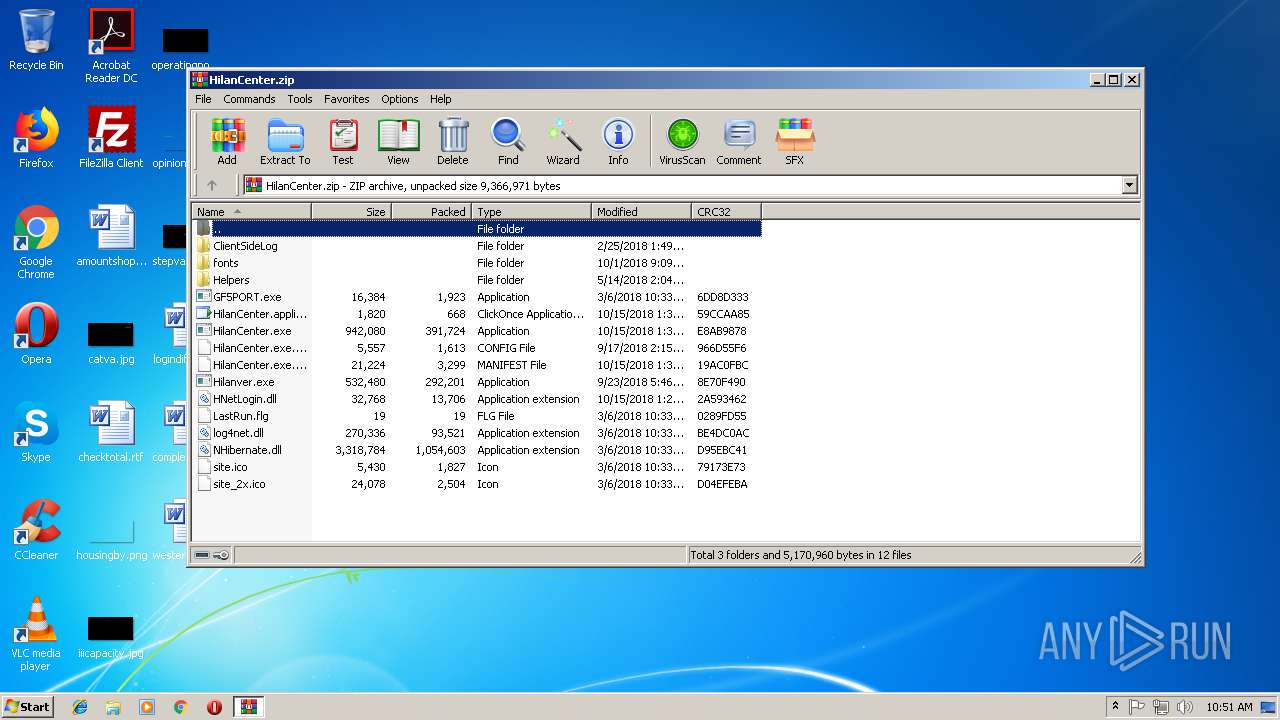
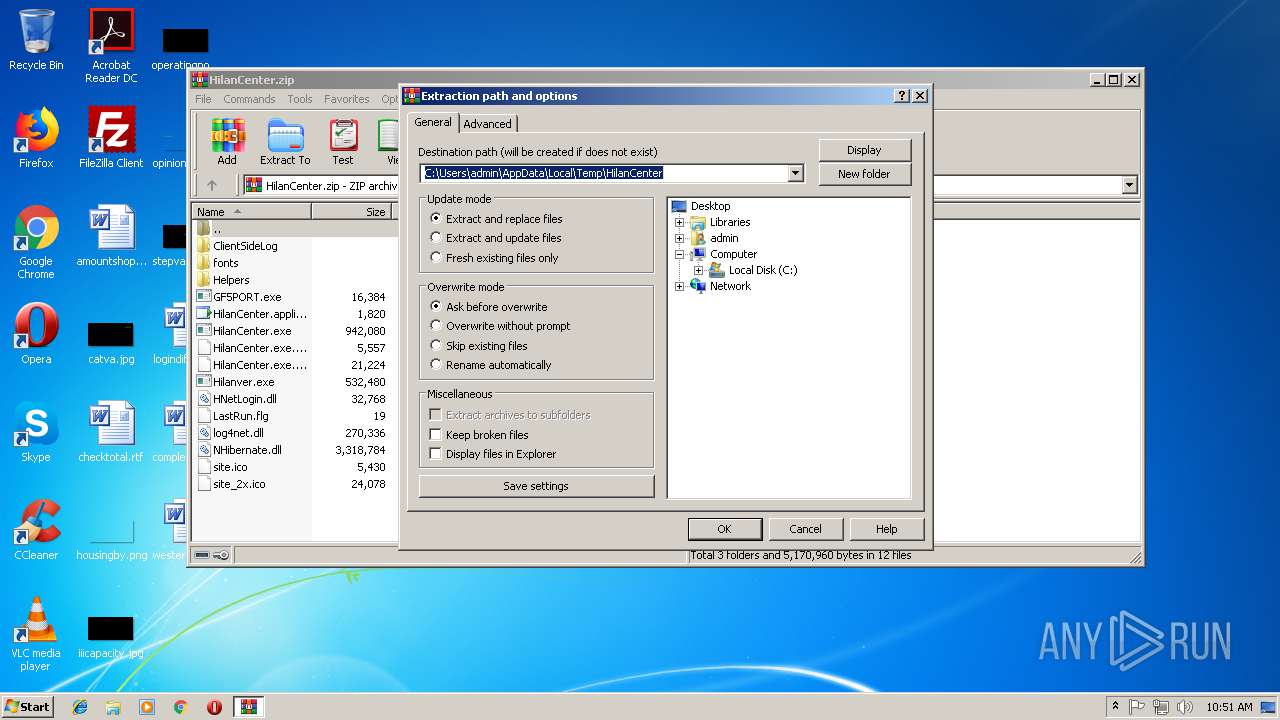
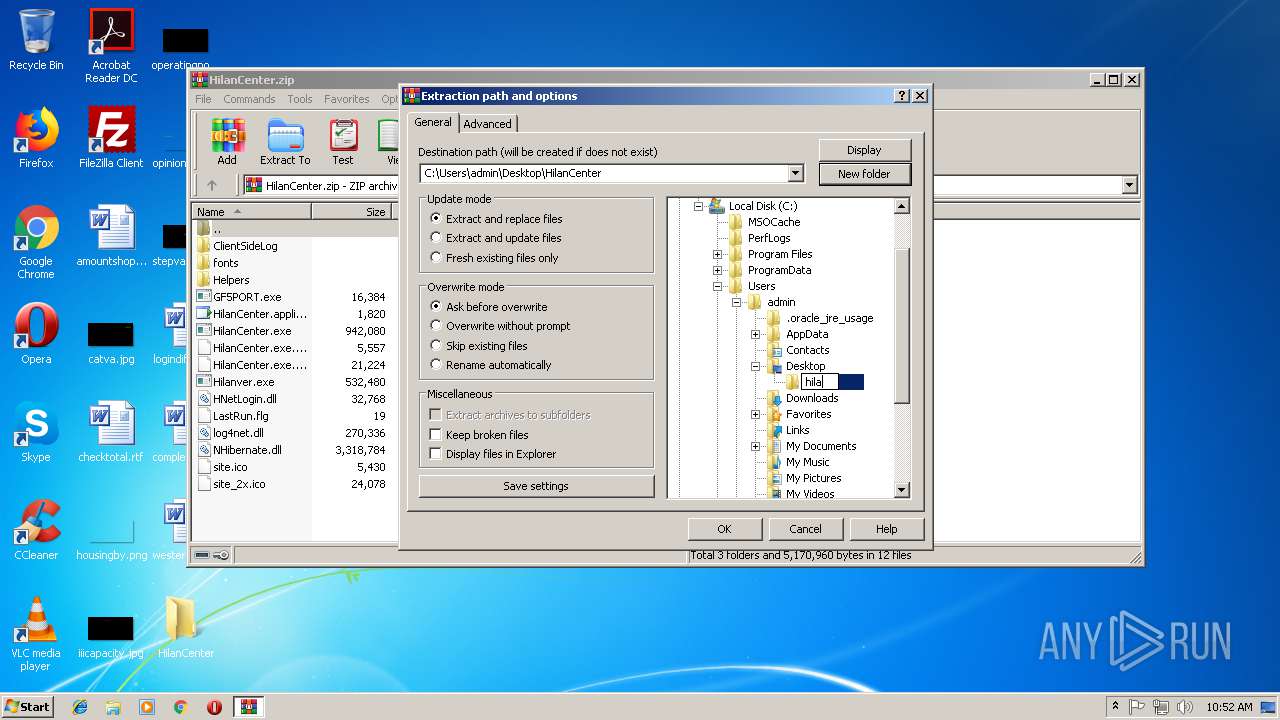
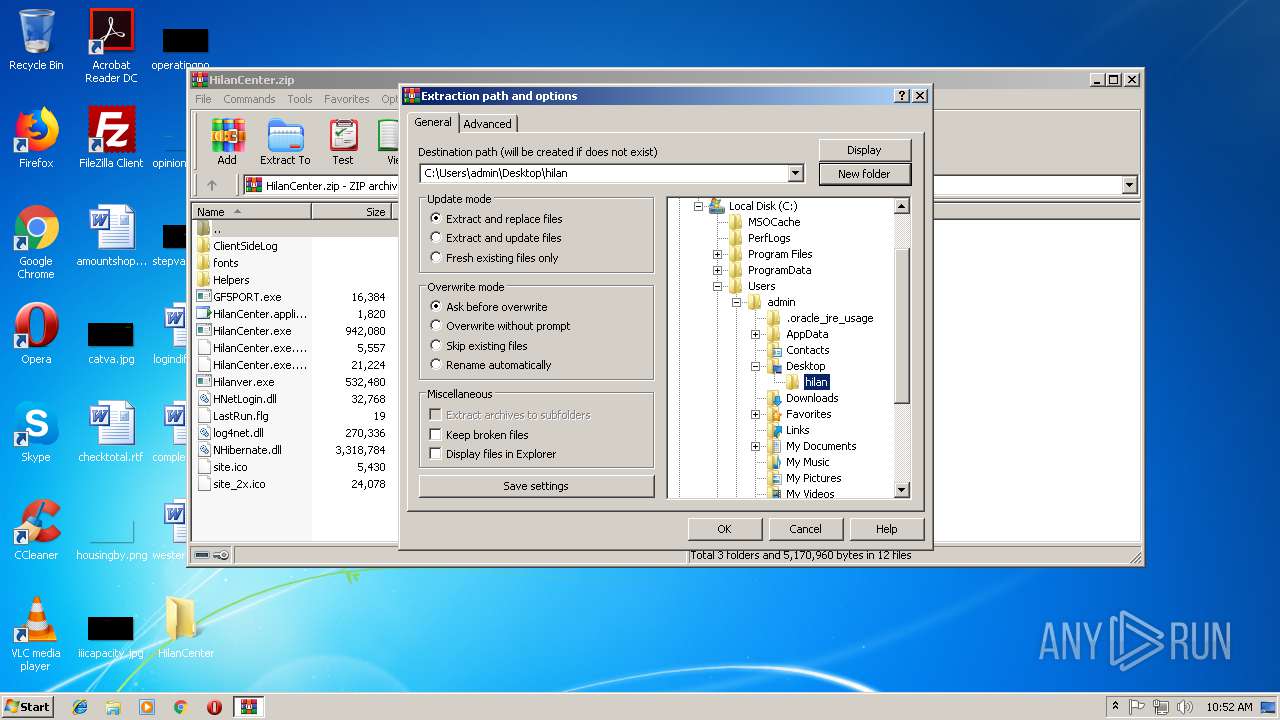
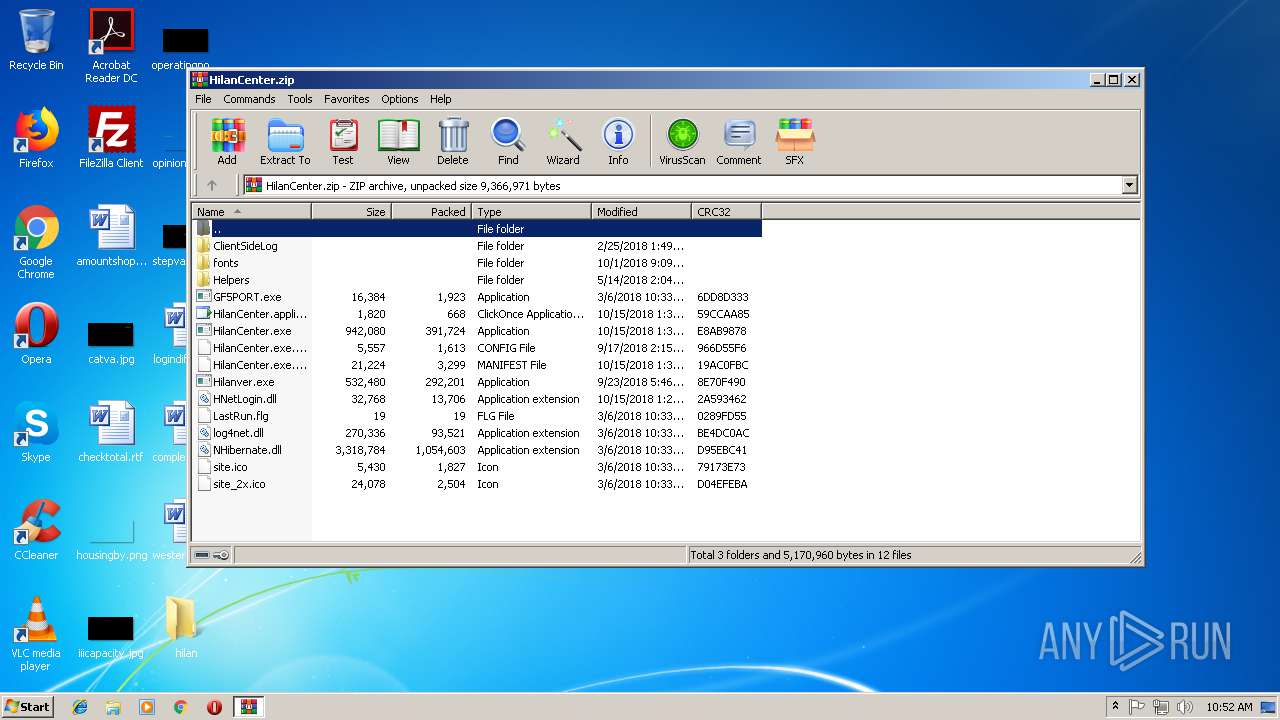
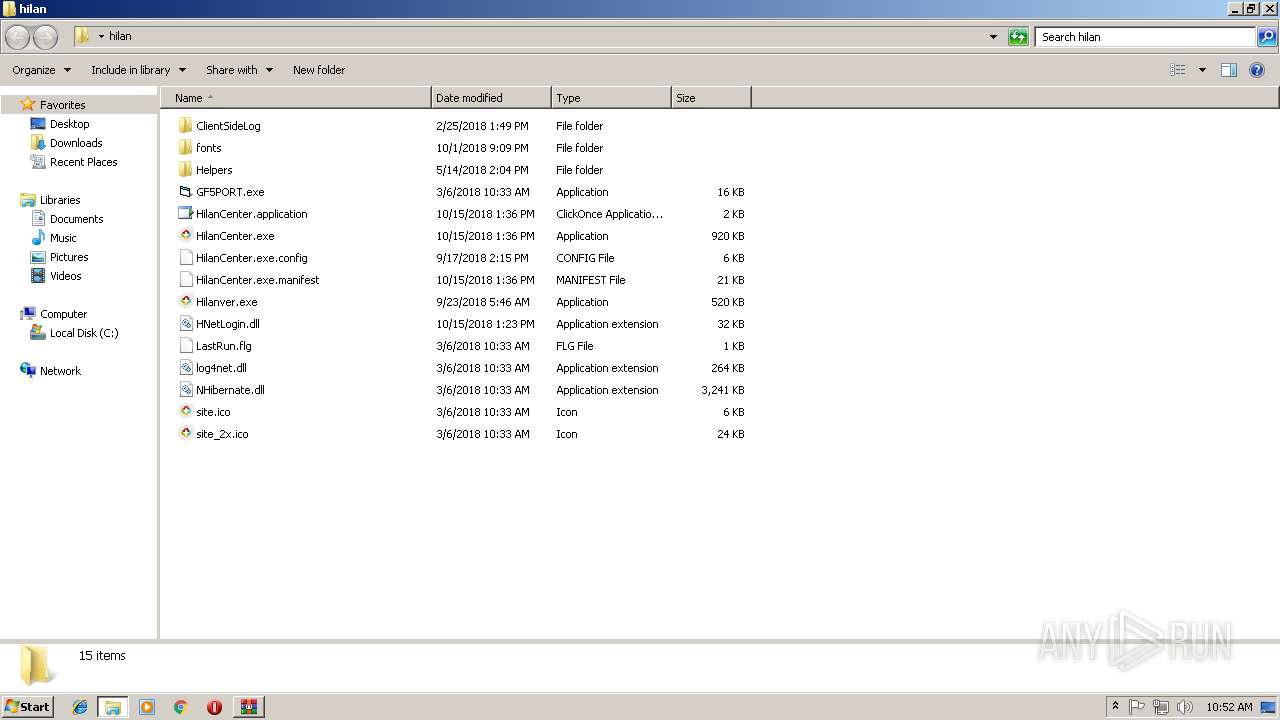
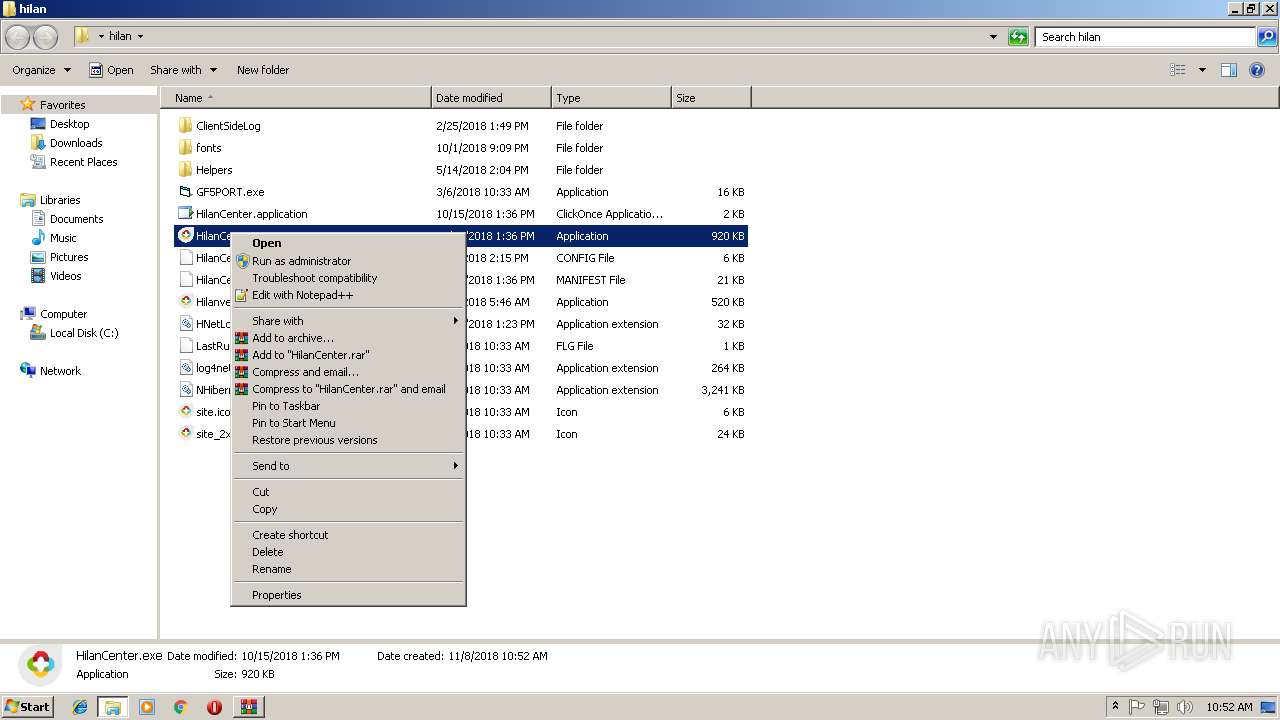
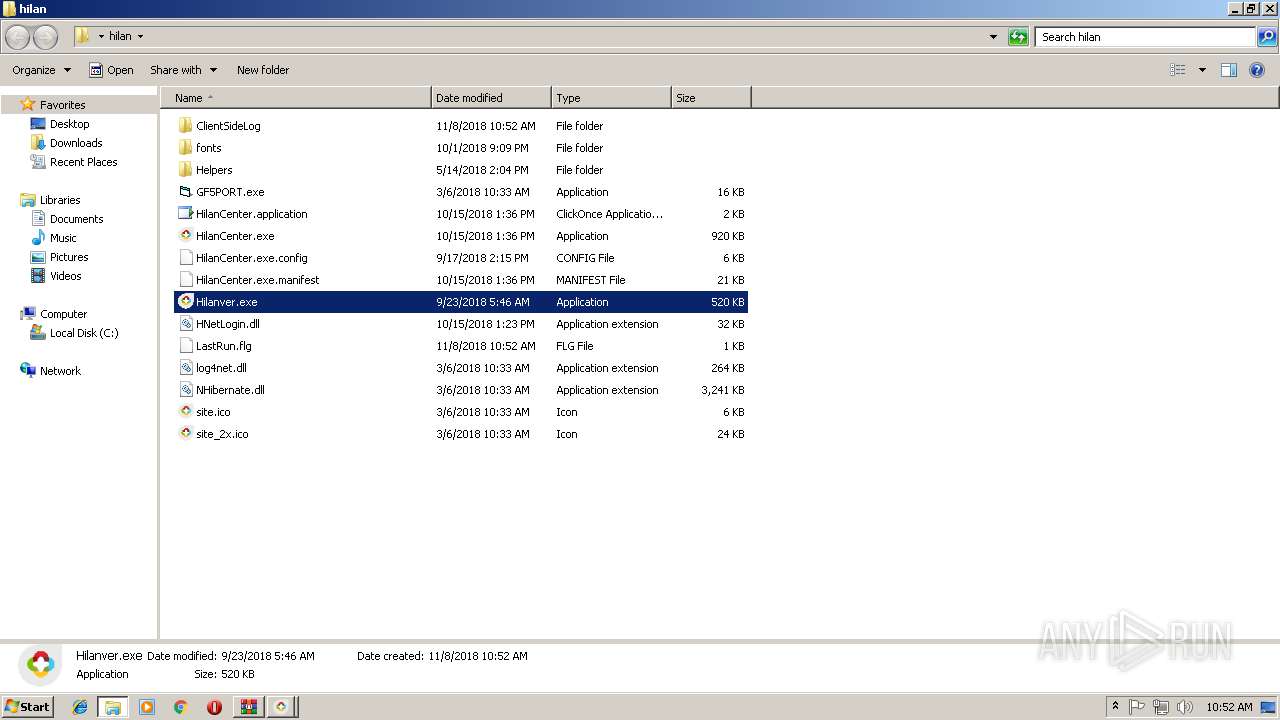
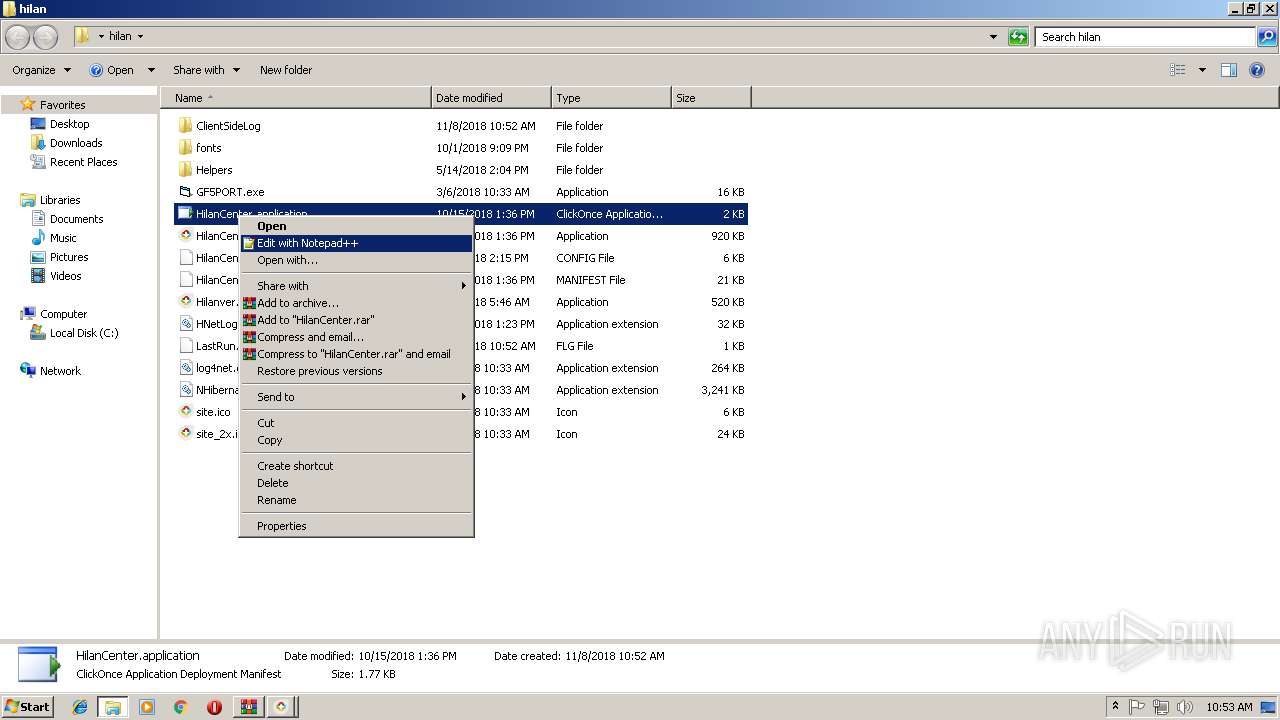
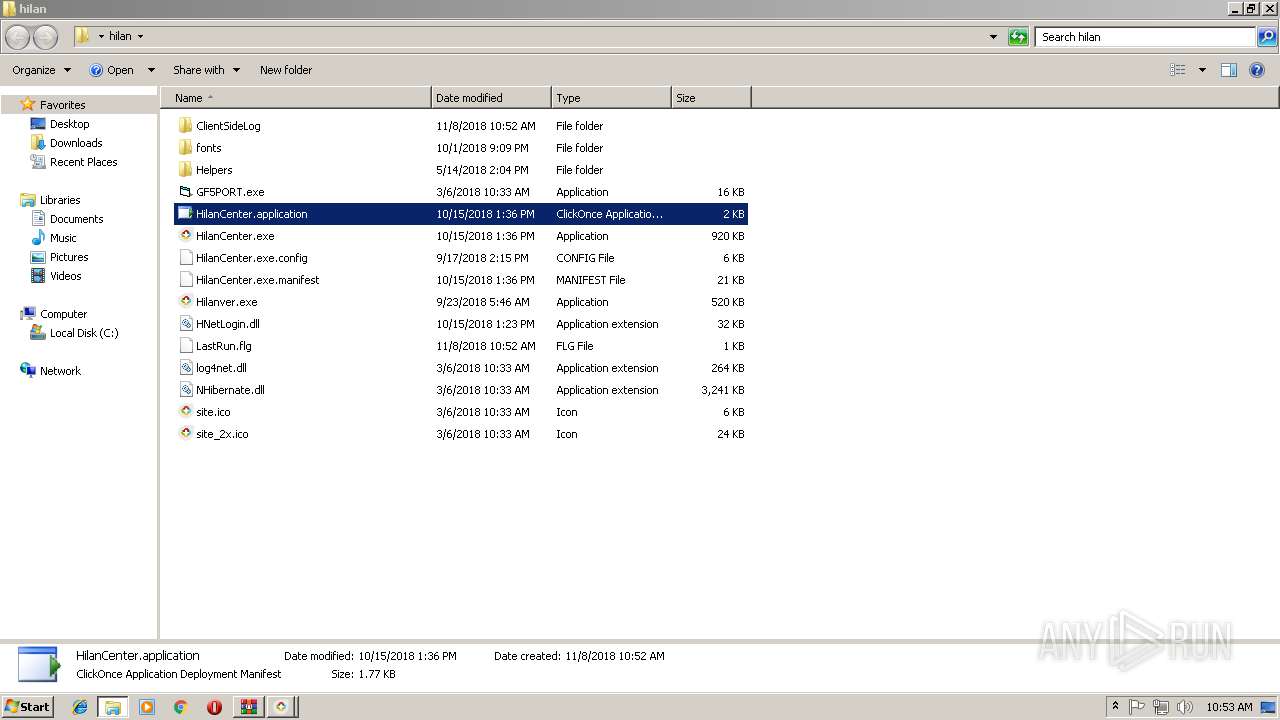
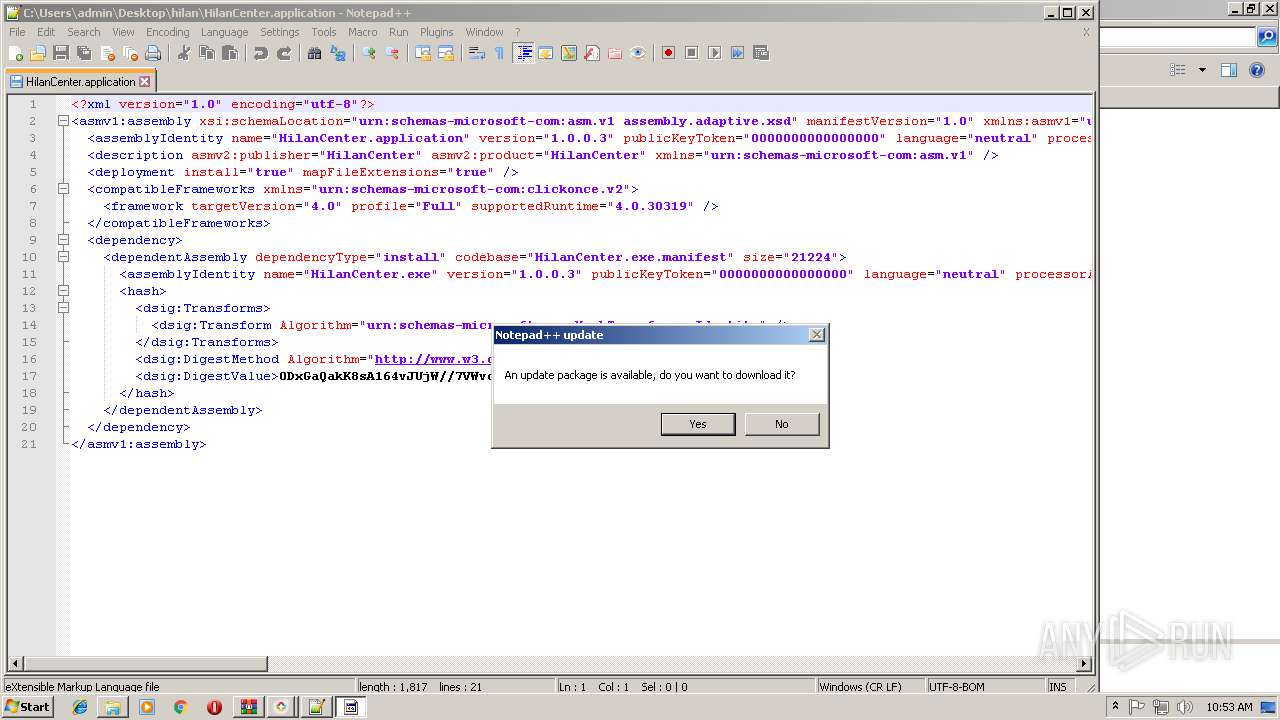
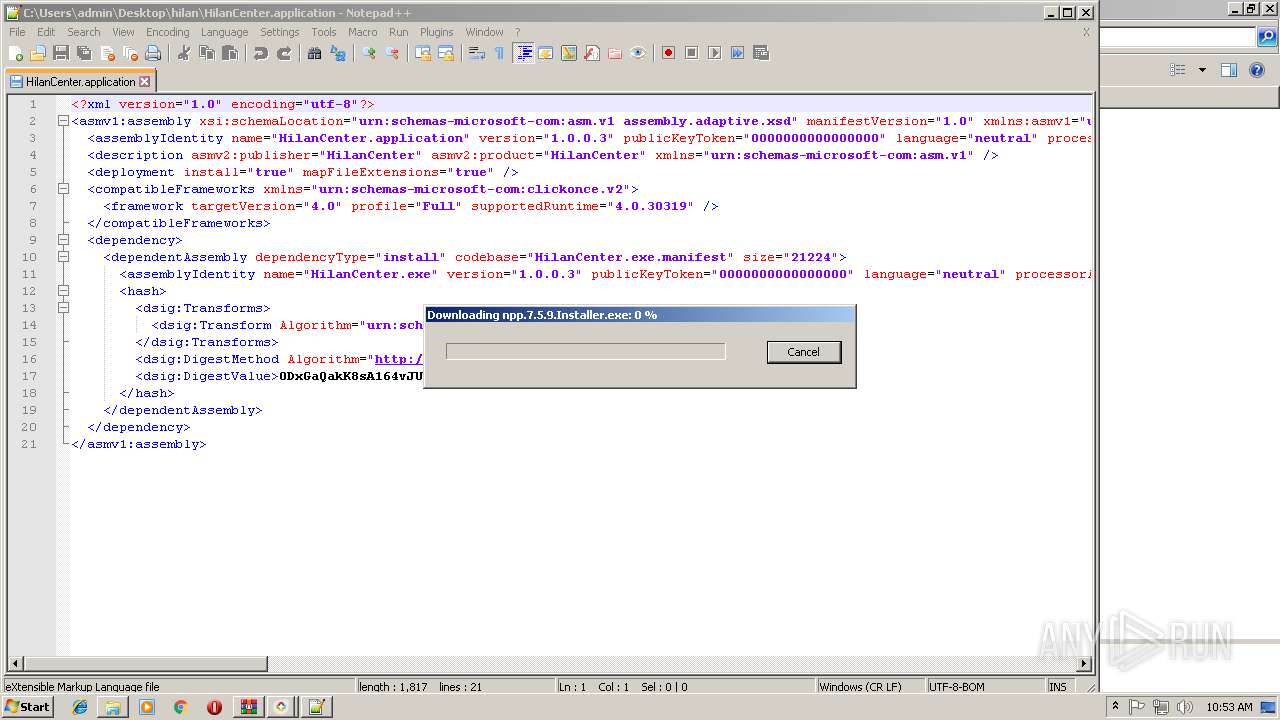
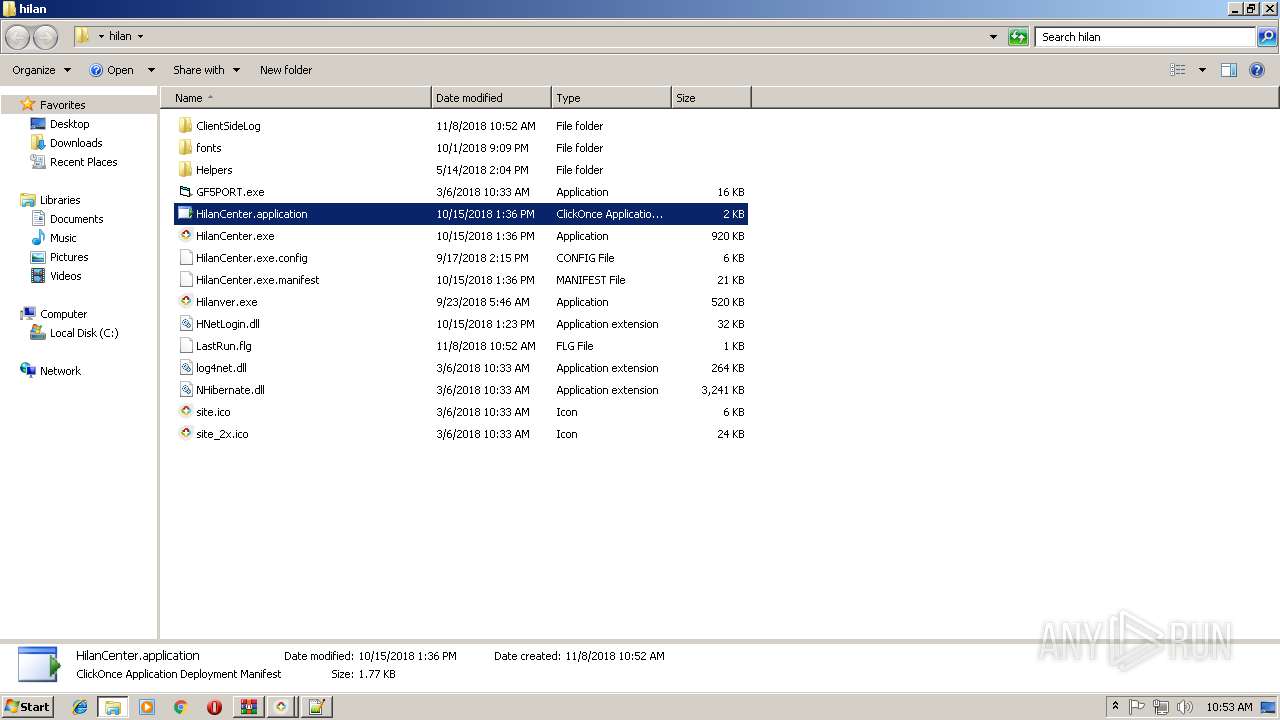
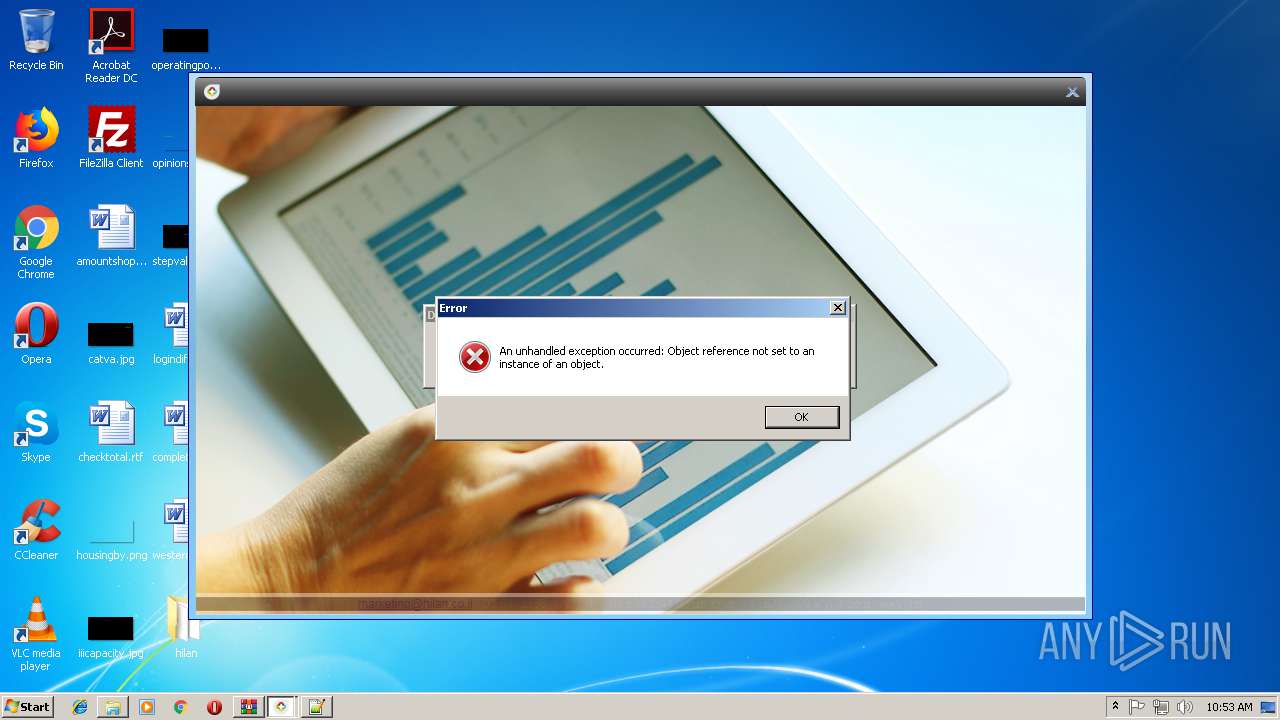
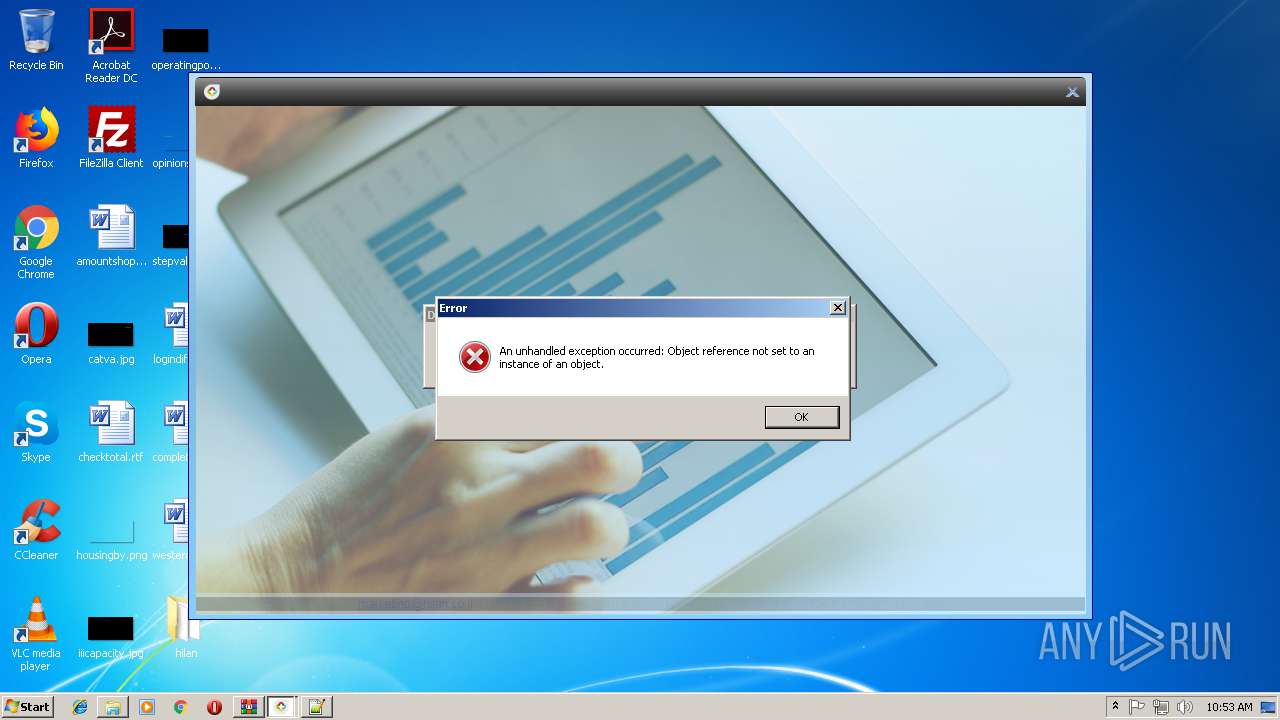
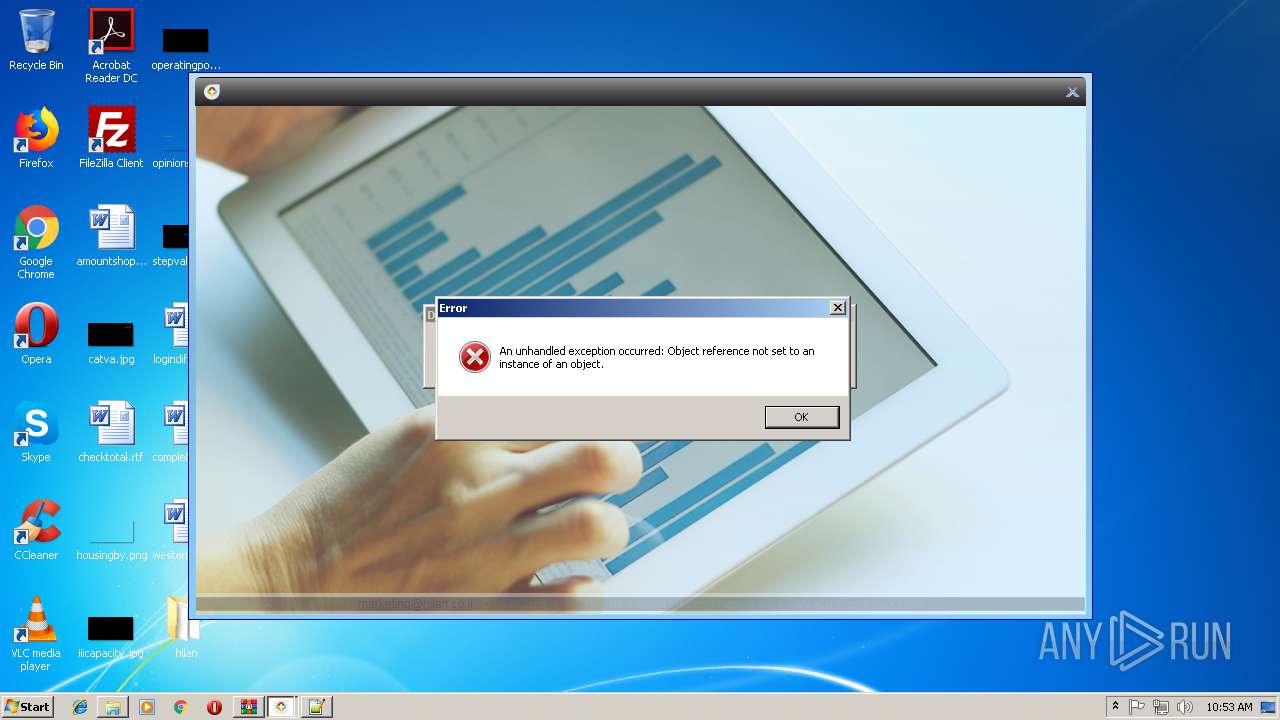
| File name: | HilanCenter.zip |
| Full analysis: | https://app.any.run/tasks/48d5883b-3d6f-49ce-b1f9-0c53ce487577 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 10:51:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D2CED3227488CD6BF6F519C072EC1BA6 |
| SHA1: | 8BD65954EDD1F620707E837CF6FD480337E82808 |
| SHA256: | D64D5FBEB41450E7C8DDD97F389D9EEA7CE1B2291B793519CB2BA0BE4E62B30E |
| SSDEEP: | 98304:Kiie/nSOkoSDc3bAaKLBgDXas/ftJEVAgaxeSP3ZRAhUdtv:Kii0VFAHLB+XD9xd8kJRGUdt |
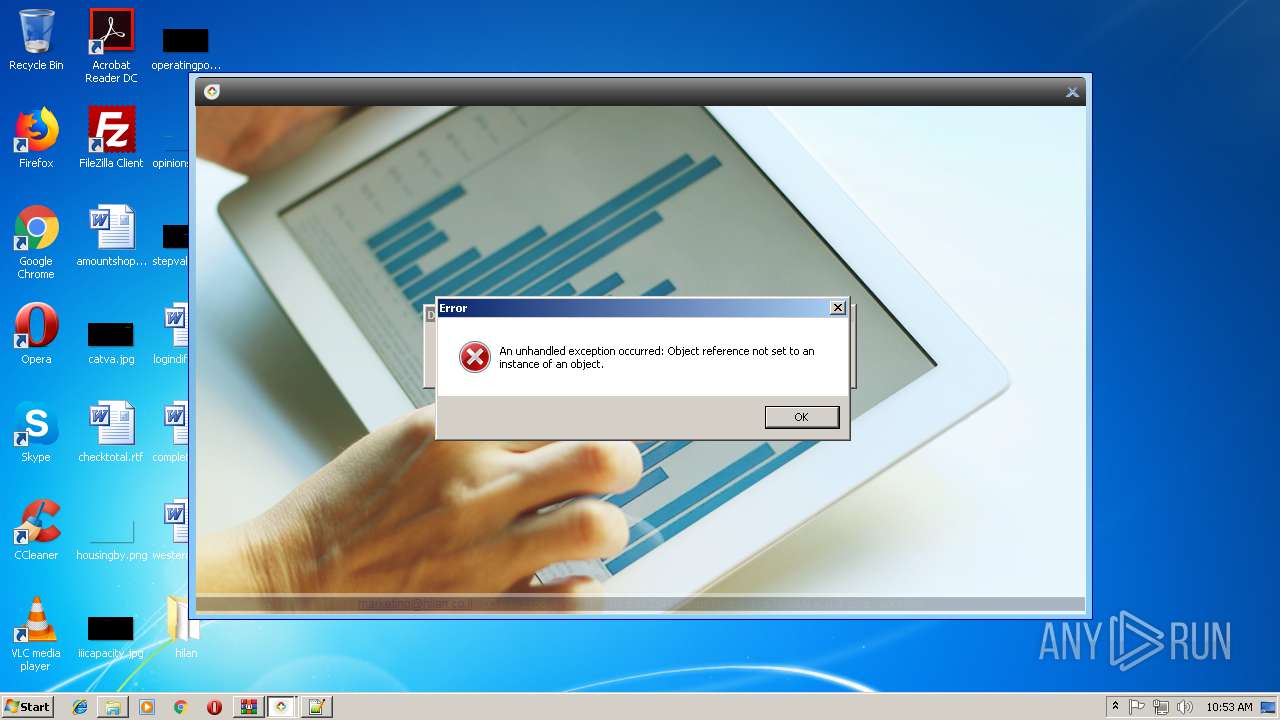
MALICIOUS
Application was dropped or rewritten from another process
- HilanCenter.exe (PID: 2116)
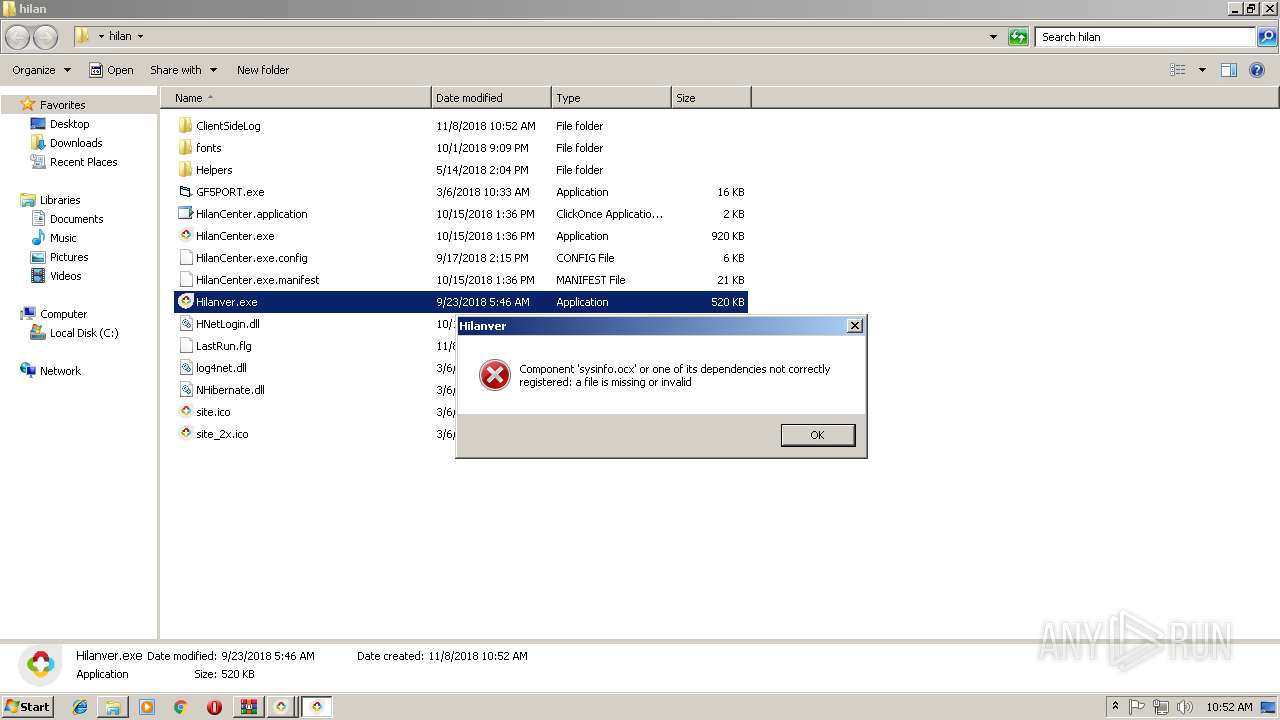
- Hilanver.exe (PID: 1484)
- GF5PORT.exe (PID: 1540)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 716)
- HilanCenter.exe (PID: 2116)
- explorer.exe (PID: 1604)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3532)
- gup.exe (PID: 2888)
Reads Environment values
- HilanCenter.exe (PID: 2116)
Reads Internet Cache Settings
- HilanCenter.exe (PID: 2116)
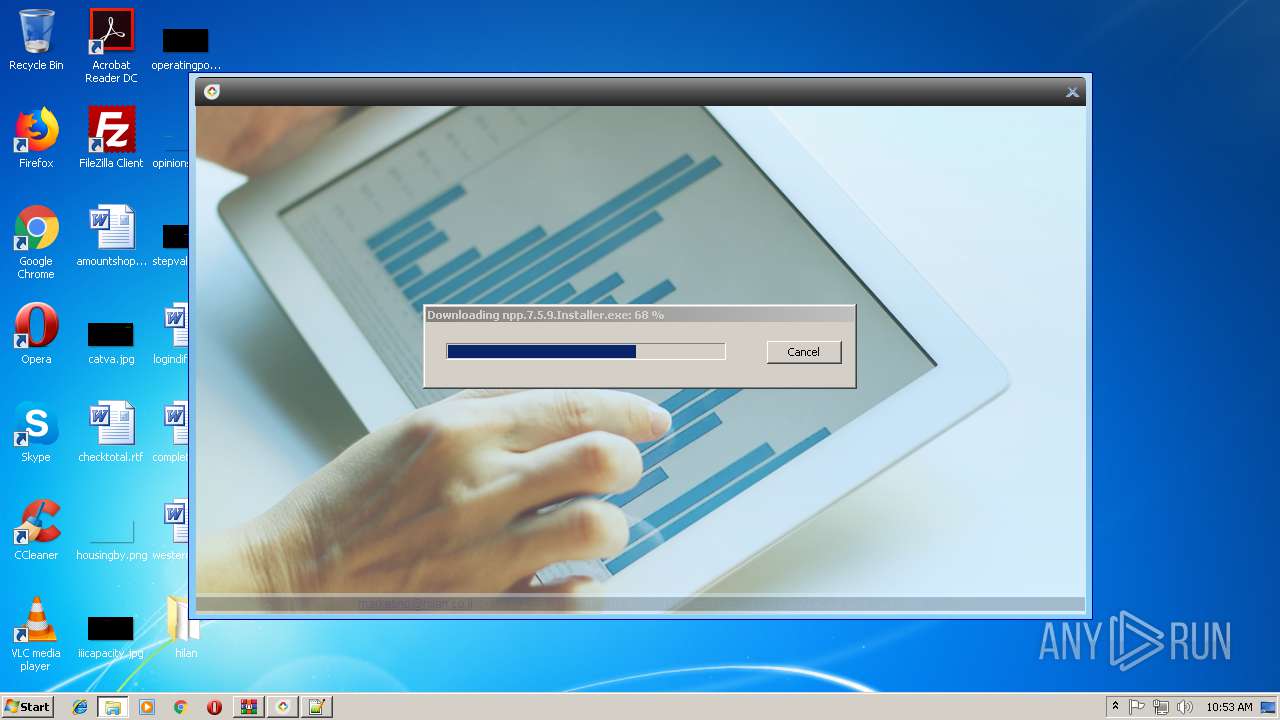
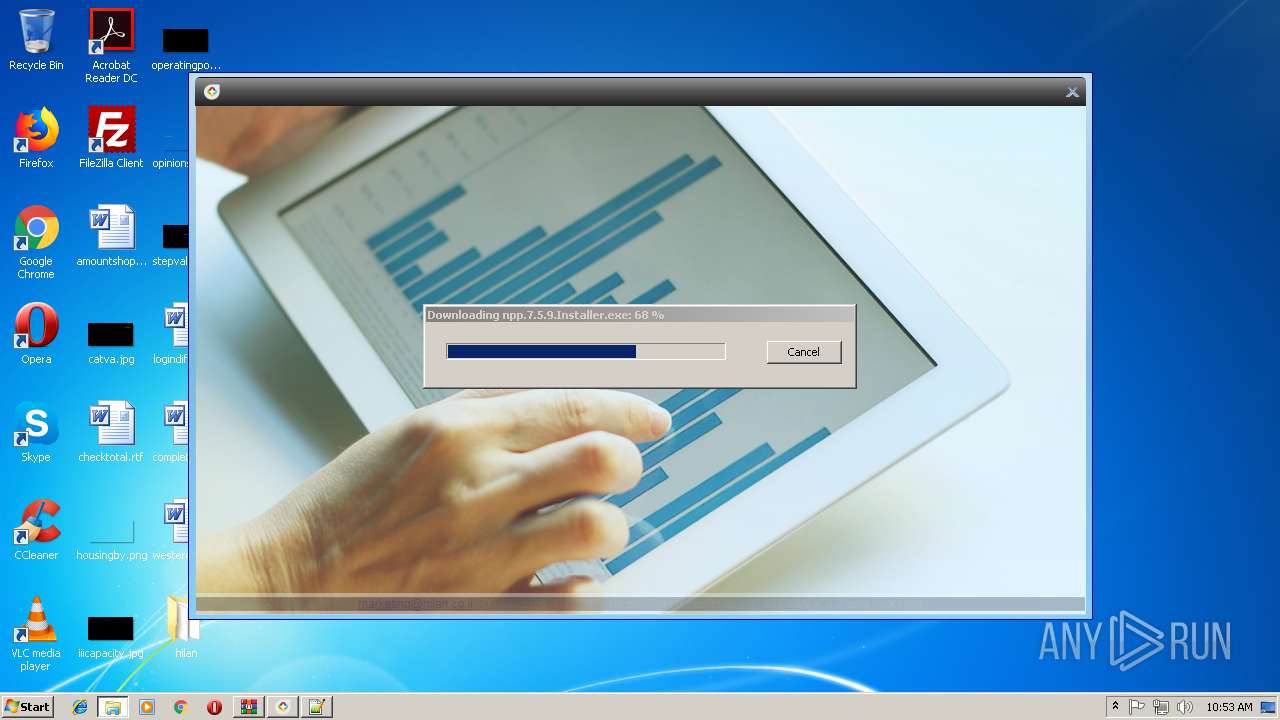
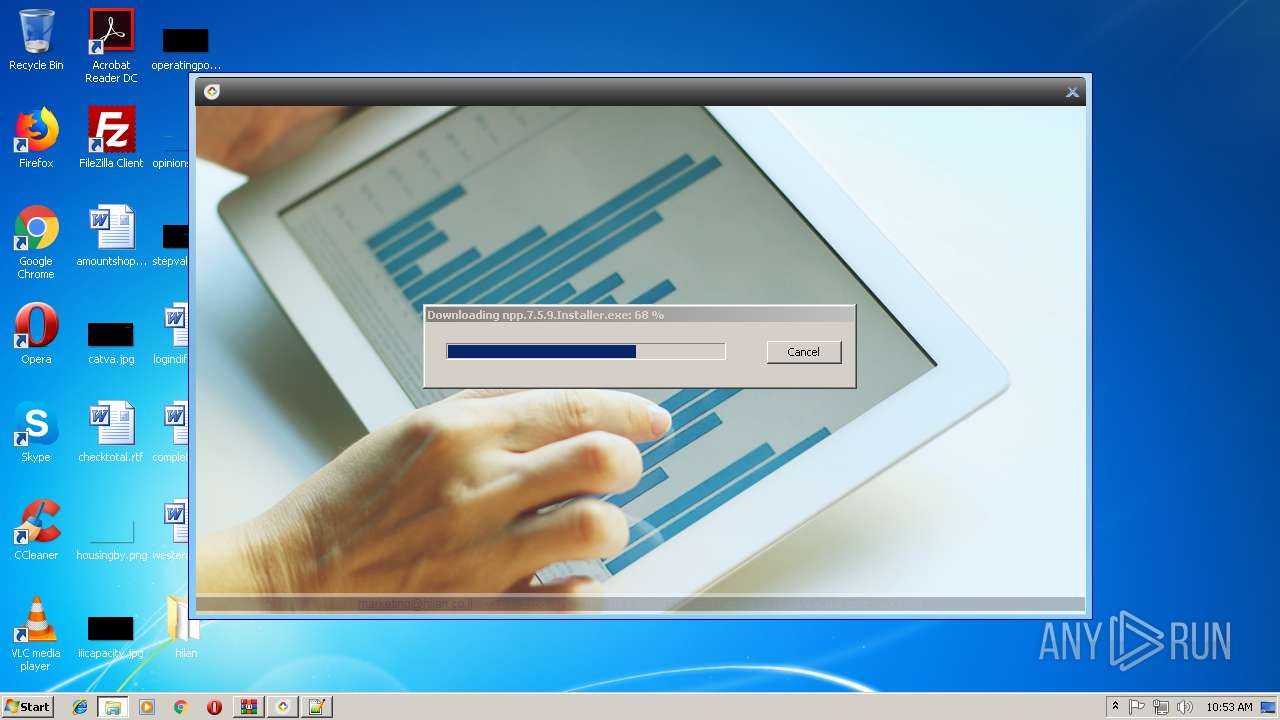
Creates files in the user directory
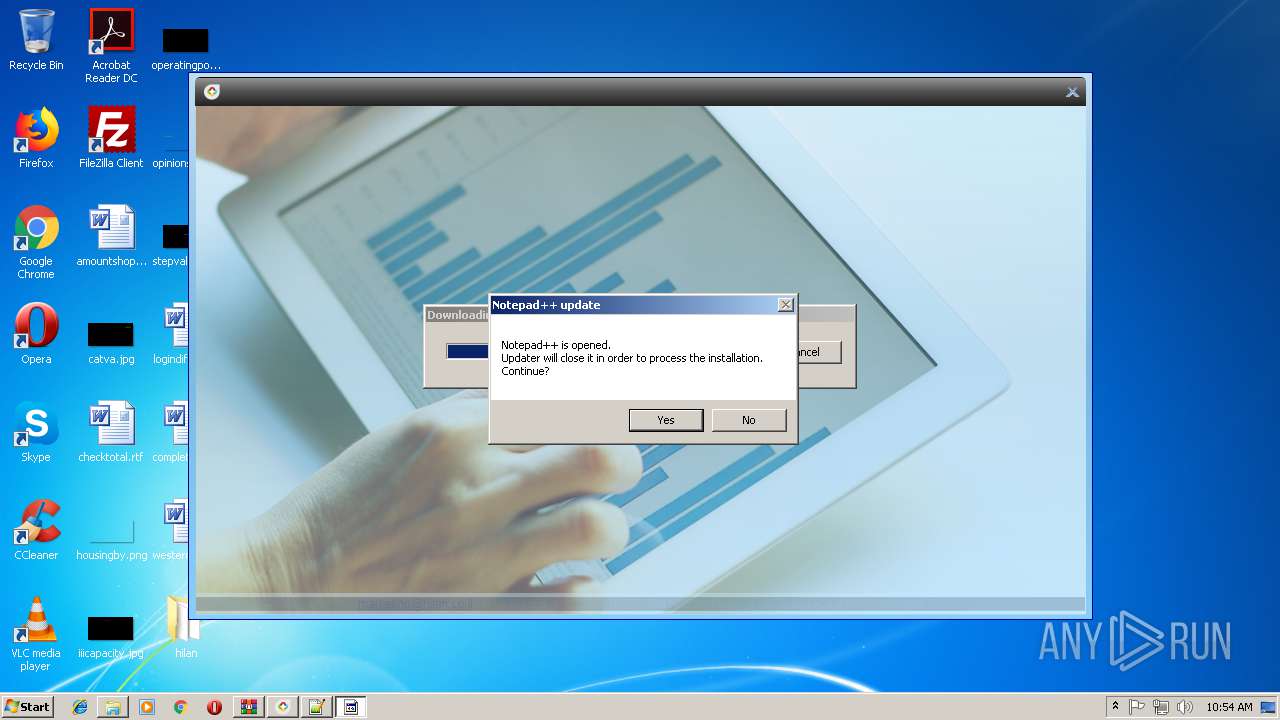
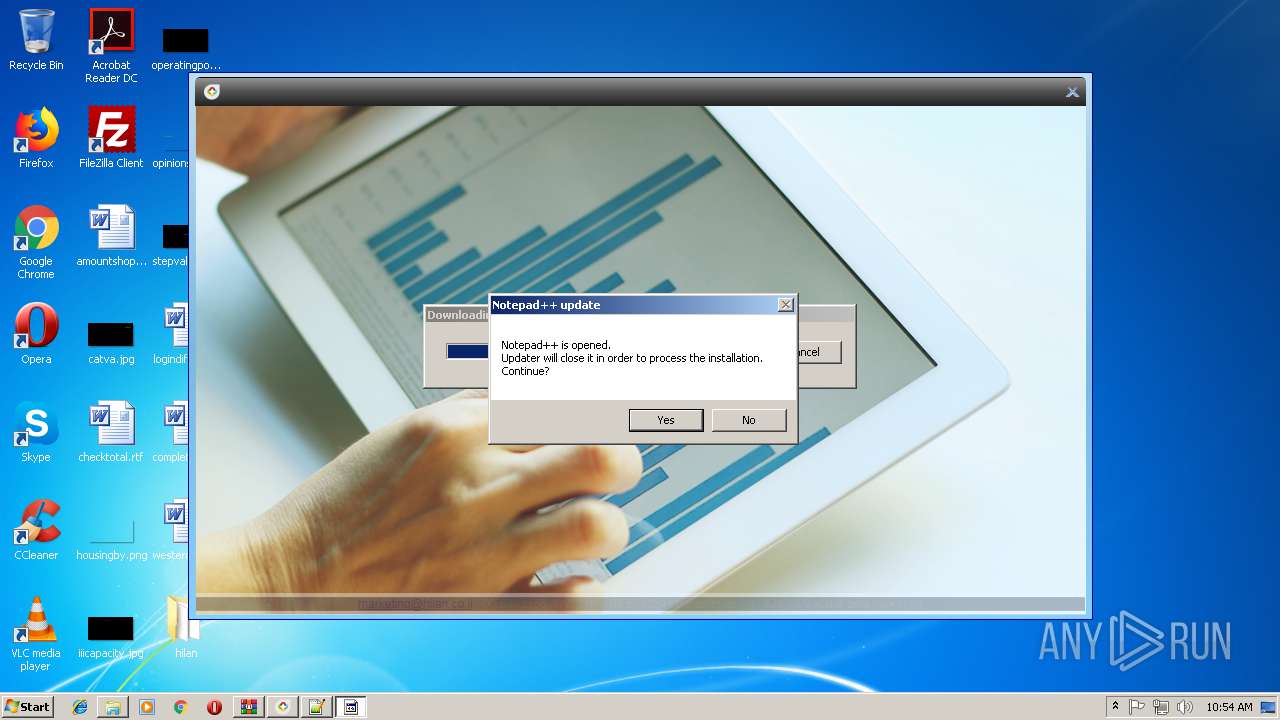
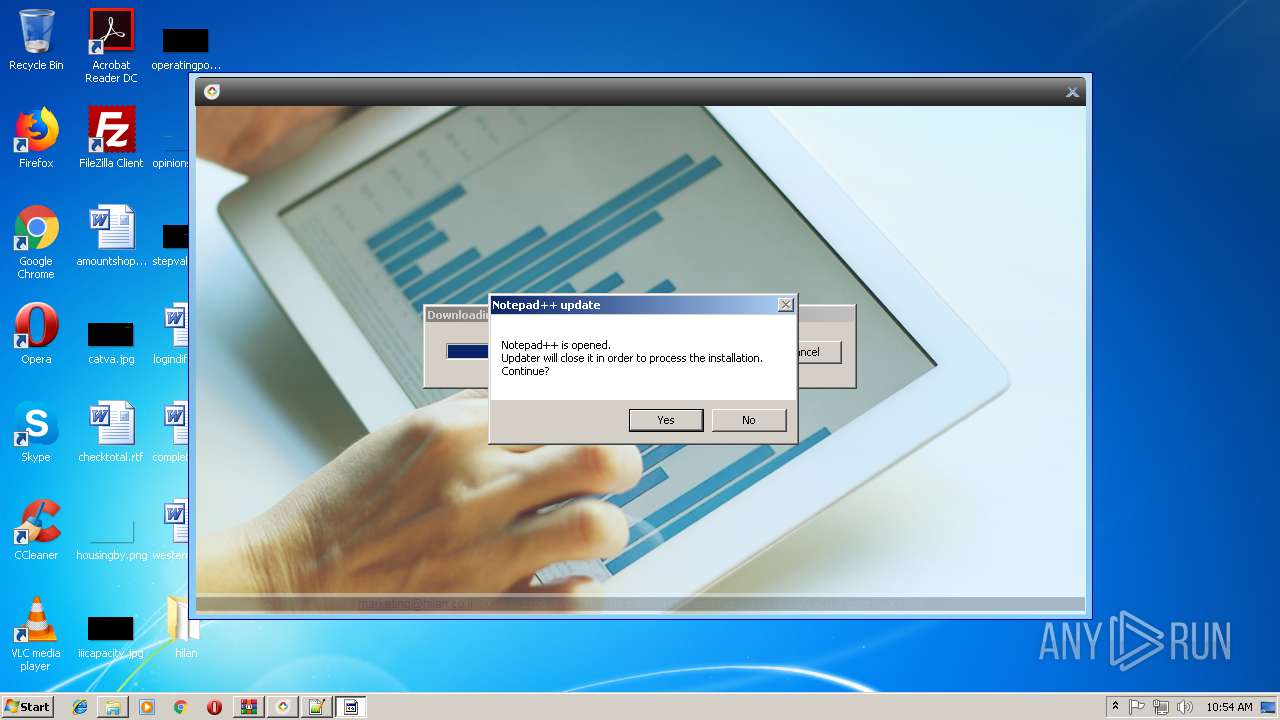
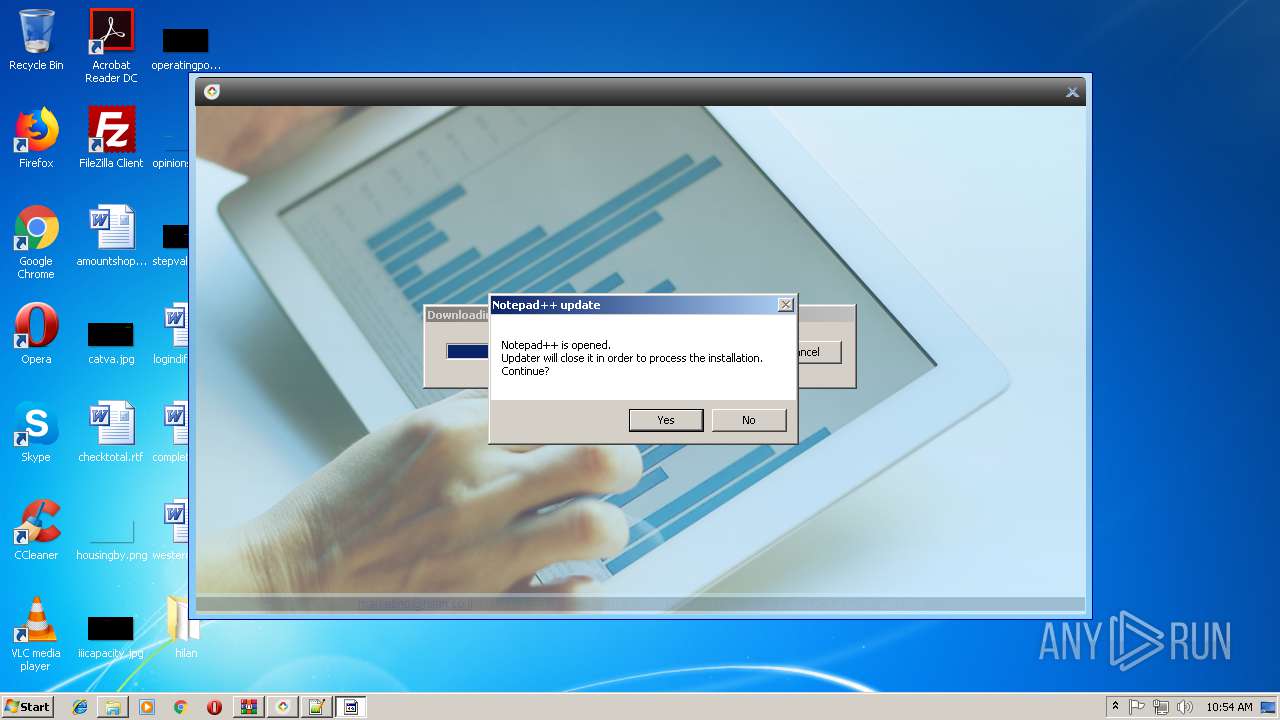
- notepad++.exe (PID: 236)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:02:25 16:49:15 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ClientSideLog/ |
Total processes
48
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\hilan\HilanCenter.application" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 716 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe14_ Global\UsGthrCtrlFltPipeMssGthrPipe14 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | "C:\Users\admin\Desktop\hilan\Hilanver.exe" | C:\Users\admin\Desktop\hilan\Hilanver.exe | explorer.exe | ||||||||||||
User: admin Company: zzz Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1540 | "C:\Users\admin\Desktop\hilan\GF5PORT.exe" | C:\Users\admin\Desktop\hilan\GF5PORT.exe | explorer.exe | ||||||||||||
User: admin Company: Hilan Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1604 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2116 | "C:\Users\admin\Desktop\hilan\HilanCenter.exe" | C:\Users\admin\Desktop\hilan\HilanCenter.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: HilanCenter Exit code: 0 Version: 1.0.6862.28081 Modules
| |||||||||||||||
| 2888 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3532 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HilanCenter.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
5 713
Read events
5 493
Write events
220
Delete events
0
Modification events
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HilanCenter.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @dfshim.dll,-200 |
Value: ClickOnce Application Deployment Manifest | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
17
Suspicious files
0
Text files
17
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan | — | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Bold.woff | woff | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Bold.svg | image | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Regular.otf | otf | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Bold.otf | otf | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Regular.eot | eot | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-BoldItalic.ttf | ttf | |
MD5:4E9F8E0FA0748B6D113150A7E282F468 | SHA256:54C77B9CE8D69F041F4E53EF67ACCB80F04E6A456FC143EB5D49A9DA7C8C2702 | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Regular.svg | image | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-Italic.ttf | ttf | |
MD5:B862AA707A3A06050BF8E8B3F9611F3C | SHA256:0CF61C26E02649E44AE9A44F3942C611D697226A6ED4B061C0CF9AEC93447344 | |||
| 3532 | WinRAR.exe | C:\Users\admin\Desktop\hilan\fonts\OpenSansHebrew-ExtraBold.ttf | ttf | |
MD5:612A355682445E4301C8186044D6C1E7 | SHA256:9F8374AB9D0B400A0F2533D75A782072582091F187BAC09DB1CDEF1C633A92A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.186.32:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | unknown | der | 471 b | whitelisted |
— | — | GET | 200 | 2.16.186.32:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | unknown | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2888 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 2.16.186.32:80 | ocsp.usertrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
portal.hilan.co.il |
| unknown |
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|