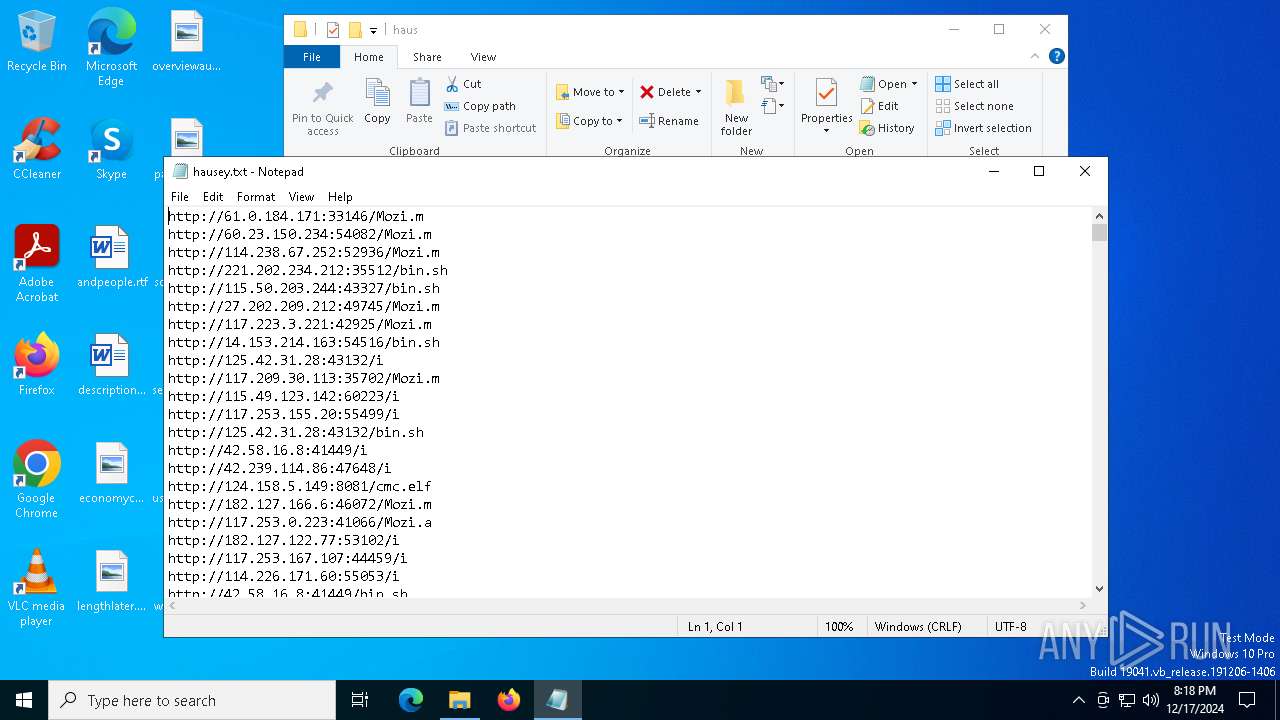
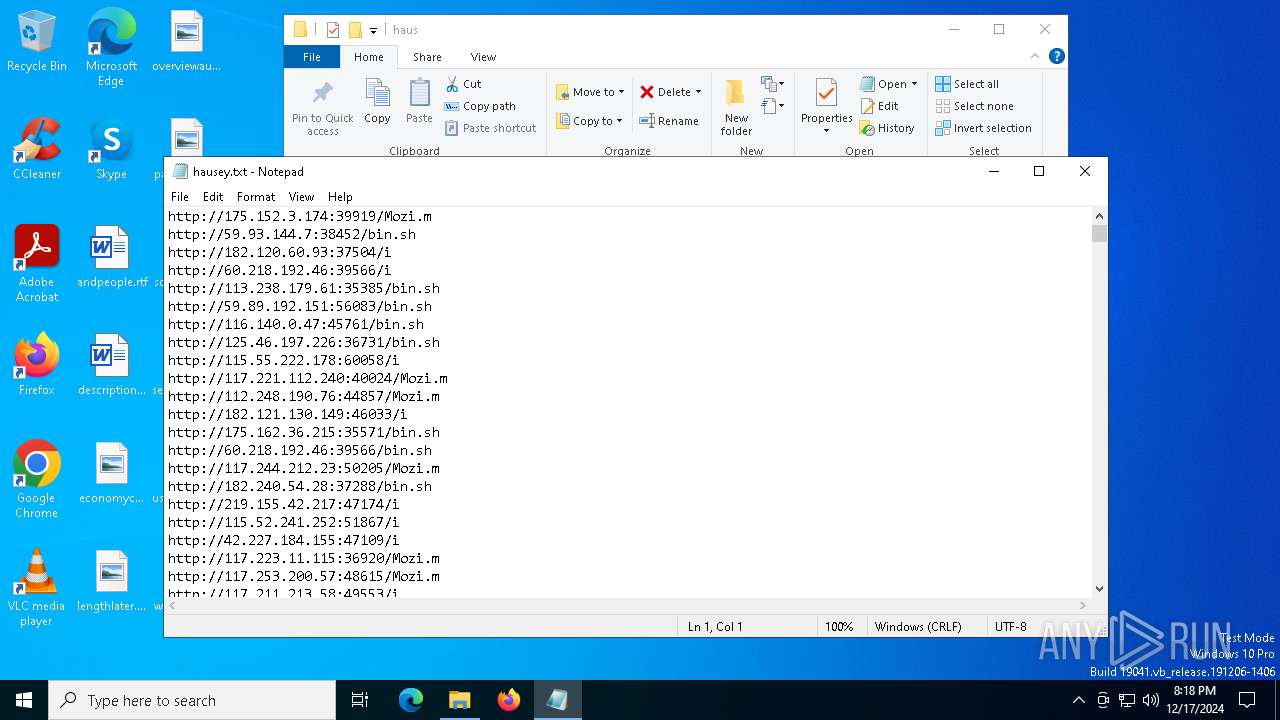
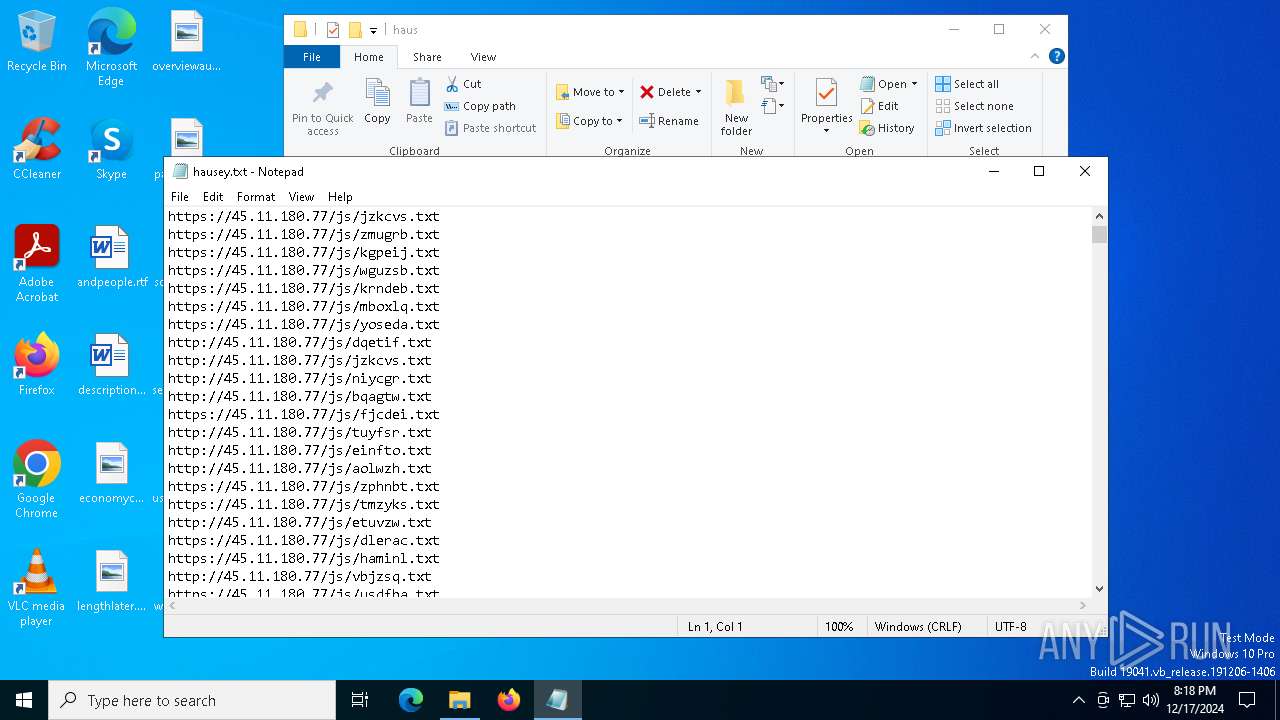
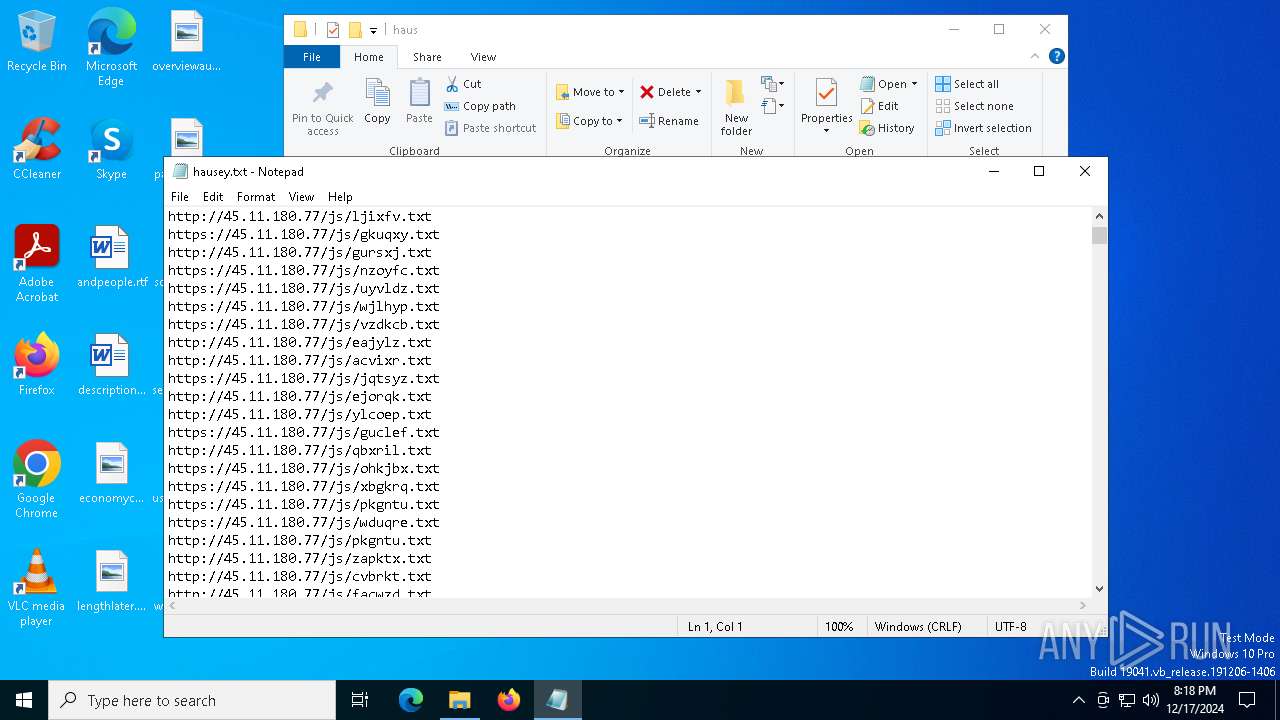
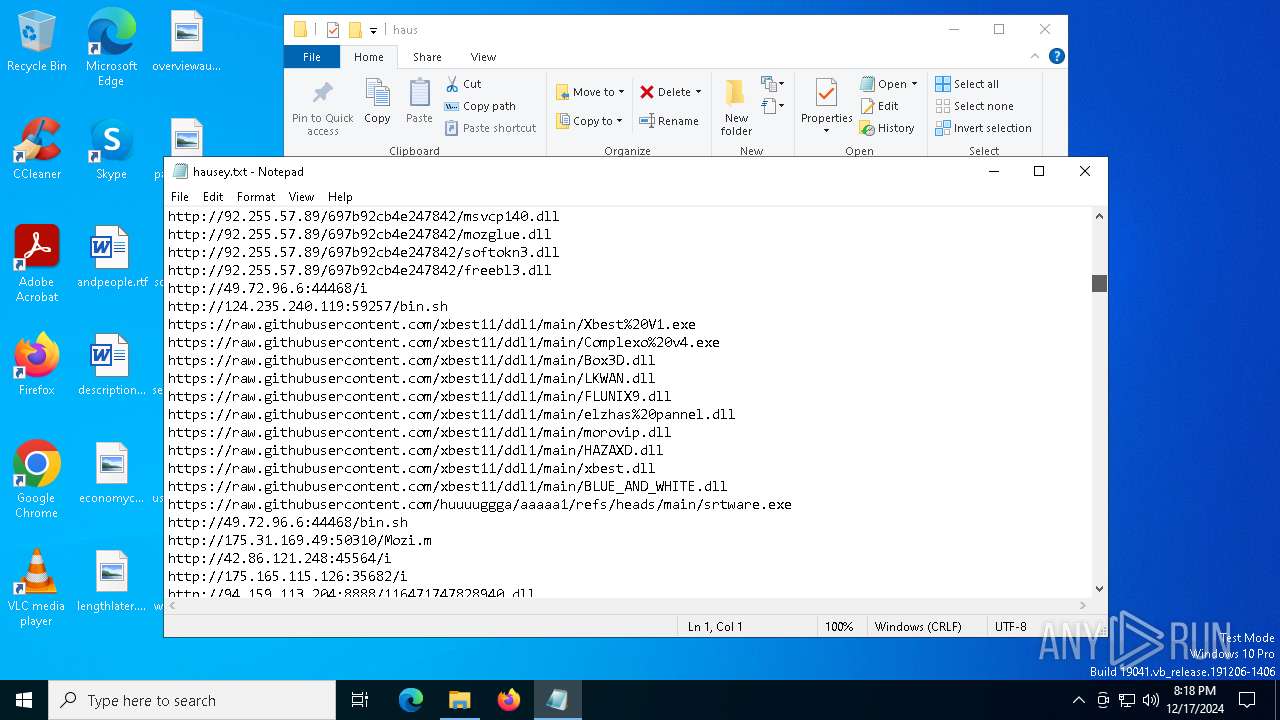
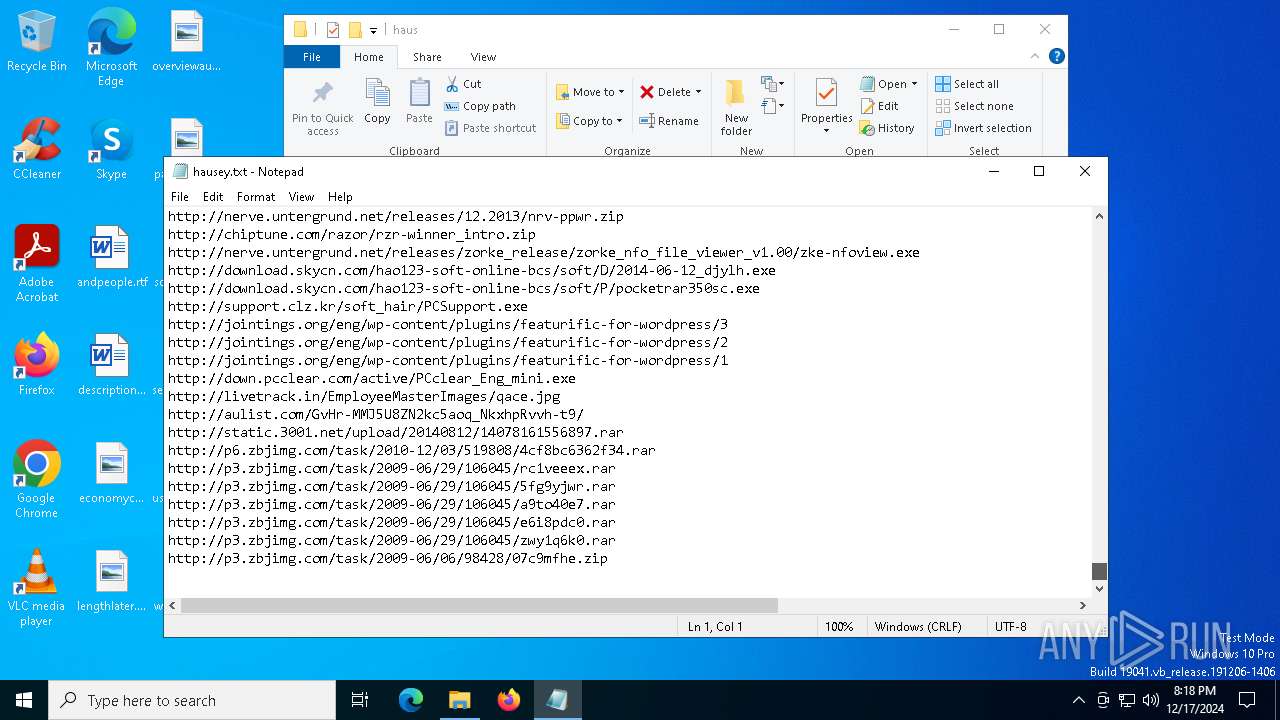
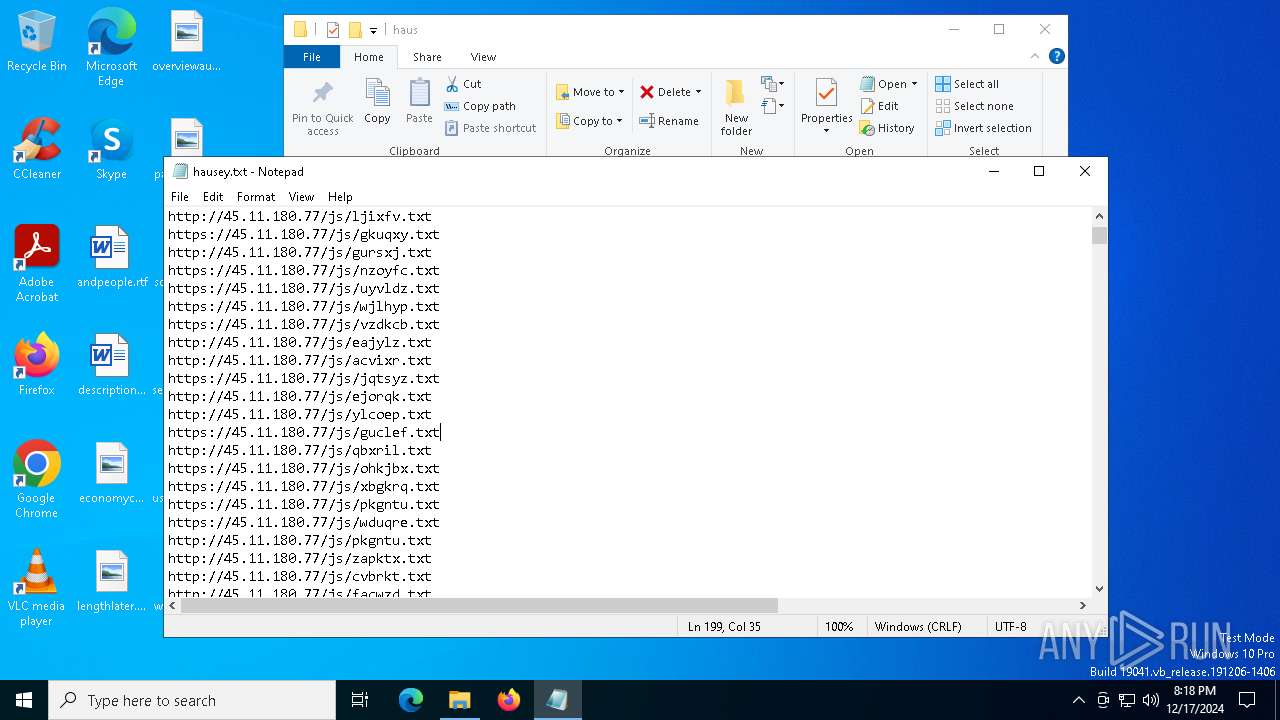
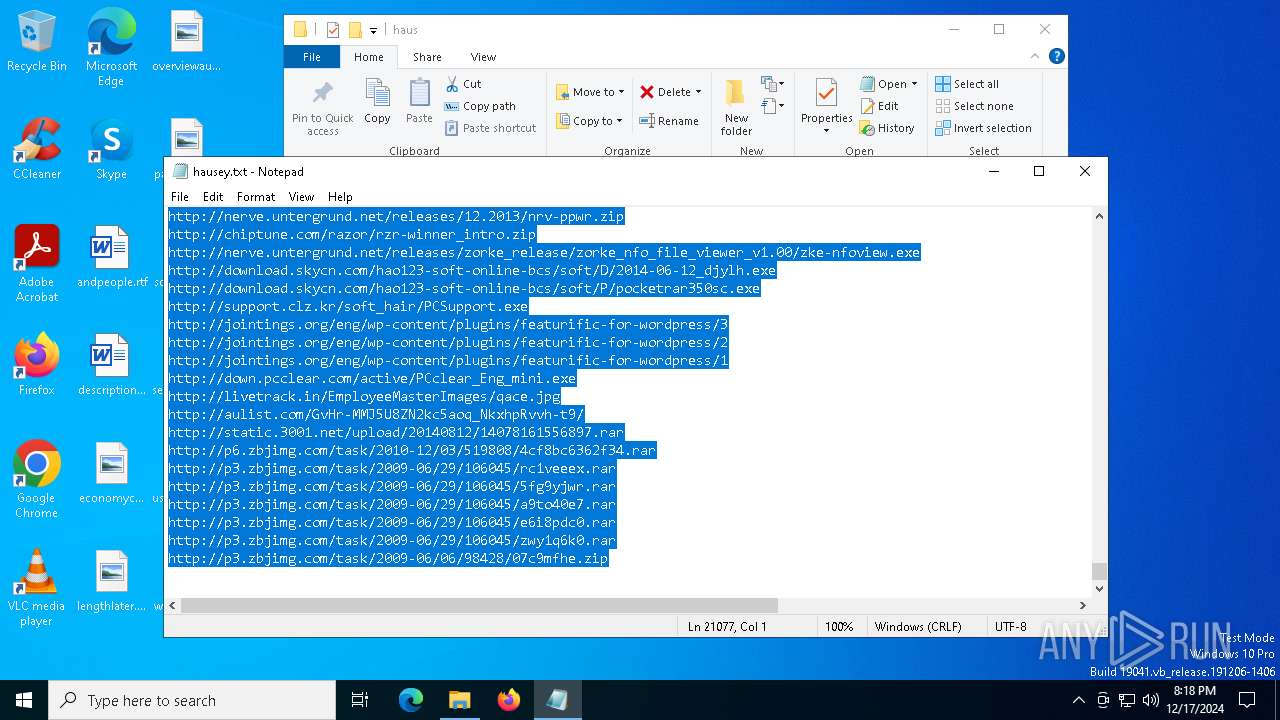
| File name: | wow.exe |
| Full analysis: | https://app.any.run/tasks/f45444e9-0cde-429f-bcf2-355bcbc0ba9e |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | December 17, 2024, 20:17:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | B2C17E4AAA1AB07E2BE2C6E08120C7FE |
| SHA1: | 67EB0FBAFB9D75D7E95DC8429C09A99E73ED5C74 |
| SHA256: | D6427E58DFA1A8BFB69F510D4C3806C36CBB7FCFAC82984CAFCD2FF539631F0D |
| SSDEEP: | 196608:+7C92OaZ2NtTeRi/BqyndOugBe0vGEmop:lnNtKRi5qEOfCw |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 420)
Changes powershell execution policy (Bypass)
- wow.exe (PID: 6868)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 420)
Uses Task Scheduler to run other applications
- powershell.exe (PID: 420)
Changes the autorun value in the registry
- reg.exe (PID: 3524)
DCRAT has been detected (YARA)
- notepad.exe (PID: 4640)
METASPLOIT has been detected (YARA)
- fern_wifi_recon%252.34.exe (PID: 3608)
XMRig has been detected
- ksoftriqd.exe (PID: 1760)
- ksoftriqd.exe (PID: 6556)
Connects to the CnC server
- ksoftriqd.exe (PID: 1760)
MINER has been detected (SURICATA)
- ksoftriqd.exe (PID: 1760)
XMRIG has been detected (YARA)
- 3iog62.exe (PID: 4592)
SUSPICIOUS
Process drops legitimate windows executable
- wow.exe (PID: 6468)
The process drops C-runtime libraries
- wow.exe (PID: 6468)
Process drops python dynamic module
- wow.exe (PID: 6468)
Reads security settings of Internet Explorer
- GameBar.exe (PID: 6700)
- wow.exe (PID: 6868)
Loads Python modules
- wow.exe (PID: 6868)
Executable content was dropped or overwritten
- wow.exe (PID: 6468)
- wow.exe (PID: 6868)
- powershell.exe (PID: 420)
- 3iog62.exe (PID: 3288)
- 3iog62.exe (PID: 4592)
- 3iog62.exe (PID: 6168)
Starts POWERSHELL.EXE for commands execution
- wow.exe (PID: 6868)
Application launched itself
- wow.exe (PID: 6468)
Reads the date of Windows installation
- wow.exe (PID: 6868)
The process executes Powershell scripts
- wow.exe (PID: 6868)
The process creates files with name similar to system file names
- wow.exe (PID: 6868)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 420)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 444)
- cmd.exe (PID: 420)
- cmd.exe (PID: 6452)
Connects to unusual port
- wow.exe (PID: 6868)
- fern_wifi_recon%252.34.exe (PID: 3608)
- 3iog62.exe (PID: 6888)
- 3iog62.exe (PID: 6168)
Process requests binary or script from the Internet
- powershell.exe (PID: 420)
Uses NETSH.EXE to change the status of the firewall
- powershell.exe (PID: 420)
Connects to the server without a host name
- powershell.exe (PID: 420)
Potential Corporate Privacy Violation
- powershell.exe (PID: 420)
- wow.exe (PID: 6868)
- ksoftriqd.exe (PID: 1760)
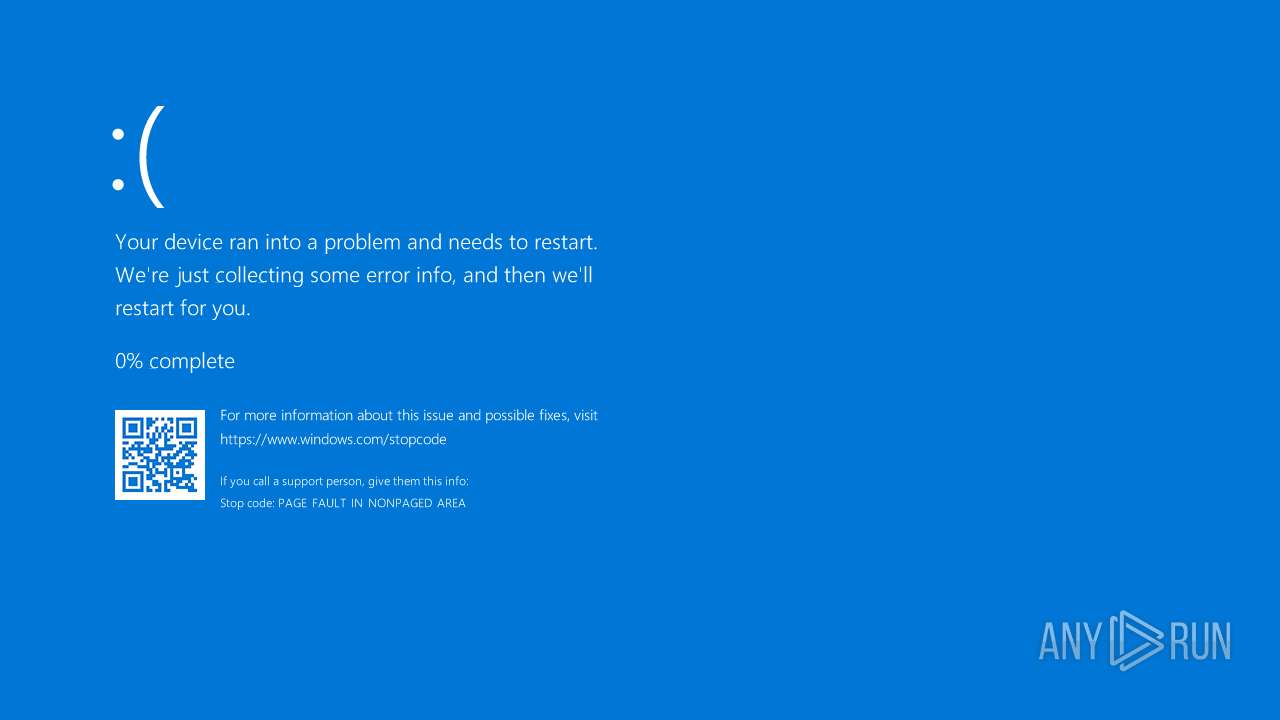
Drops a system driver (possible attempt to evade defenses)
- 3iog62.exe (PID: 3288)
- 3iog62.exe (PID: 4592)
- 3iog62.exe (PID: 6168)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 420)
Starts CMD.EXE for commands execution
- 3iog62.exe (PID: 3288)
- 3iog62.exe (PID: 6888)
- 3iog62.exe (PID: 4592)
- 3iog62.exe (PID: 6168)
Starts SC.EXE for service management
- cmd.exe (PID: 4556)
- cmd.exe (PID: 4592)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 3152)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 4444)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 5880)
- cmd.exe (PID: 6412)
- cmd.exe (PID: 6332)
- cmd.exe (PID: 6372)
- cmd.exe (PID: 6292)
The process executes via Task Scheduler
- 3iog62.exe (PID: 6888)
- 3iog62.exe (PID: 4592)
- PLUGScheduler.exe (PID: 3028)
- 3iog62.exe (PID: 5700)
The executable file from the user directory is run by the CMD process
- ksoftriqd.exe (PID: 1760)
- ksoftriqd.exe (PID: 6556)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- 3iog62.exe (PID: 4592)
- 3iog62.exe (PID: 6168)
Crypto Currency Mining Activity Detected
- ksoftriqd.exe (PID: 1760)
INFO
Checks supported languages
- wow.exe (PID: 6468)
- GameBar.exe (PID: 6700)
- wow.exe (PID: 6868)
- fern_wifi_recon%252.34.exe (PID: 3608)
- 3iog62.exe (PID: 3288)
- 3iog62.exe (PID: 6888)
Reads the computer name
- wow.exe (PID: 6468)
- GameBar.exe (PID: 6700)
- 3iog62.exe (PID: 3288)
- 3iog62.exe (PID: 6888)
Create files in a temporary directory
- wow.exe (PID: 6468)
- 3iog62.exe (PID: 3288)
- 3iog62.exe (PID: 6888)
The sample compiled with english language support
- wow.exe (PID: 6468)
- wow.exe (PID: 6868)
Process checks computer location settings
- wow.exe (PID: 6868)
The process uses the downloaded file
- wow.exe (PID: 6868)
Reads Microsoft Office registry keys
- wow.exe (PID: 6868)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 420)
Checks proxy server information
- powershell.exe (PID: 420)
Gets data length (POWERSHELL)
- powershell.exe (PID: 420)
Disables trace logs
- powershell.exe (PID: 420)
The executable file from the user directory is run by the Powershell process
- 3iog62.exe (PID: 3288)
Creates files or folders in the user directory
- 3iog62.exe (PID: 3288)
Drops encrypted JS script (Microsoft Script Encoder)
- 3iog62.exe (PID: 3288)
Drops encrypted VBS script (Microsoft Script Encoder)
- 3iog62.exe (PID: 3288)
Manual execution by a user
- notepad.exe (PID: 4640)
- 3iog62.exe (PID: 6168)
Application based on Golang
- 3iog62.exe (PID: 4592)
The sample compiled with japanese language support
- 3iog62.exe (PID: 4592)
- 3iog62.exe (PID: 6168)
UPX packer has been detected
- 3iog62.exe (PID: 4592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:17 20:15:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 152576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
309
Monitored processes
76
Malicious processes
13
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
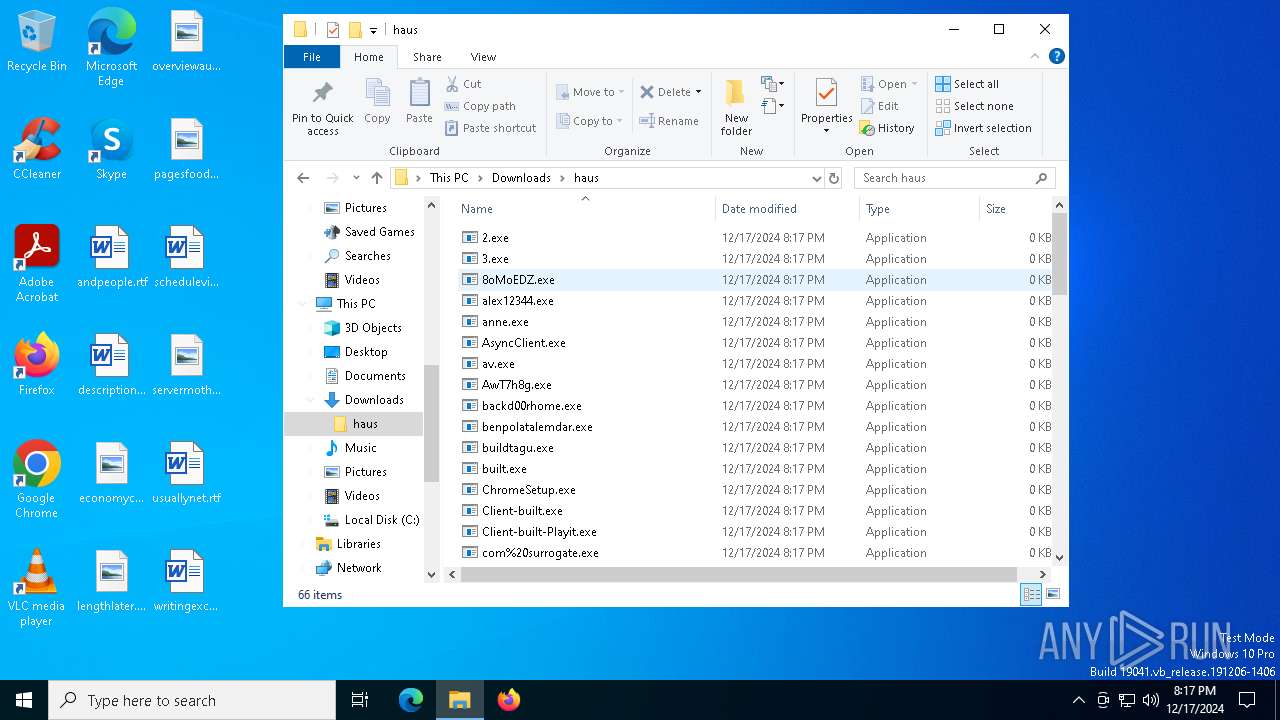
| 420 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Downloads\haus\ldr.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wow.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | cmd.exe /c "netstat -ano | findstr TCP" | C:\Windows\System32\cmd.exe | — | 3iog62.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | cmd.exe /c "netstat -ano | findstr TCP" | C:\Windows\System32\cmd.exe | — | 3iog62.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 3iog62.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1476 | sc stop npf | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | netstat -ano | C:\Windows\System32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | findstr TCP | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | C:\Users\admin\AppData\Local\Temp\td30hh\ksoftriqd.exe | C:\Users\admin\AppData\Local\Temp\td30hh\ksoftriqd.exe | cmd.exe | ||||||||||||
User: admin Company: www.xmrig.com Integrity Level: MEDIUM Description: XMRig miner Exit code: 0 Version: 6.21.1 Modules
| |||||||||||||||
| 1944 | findstr TCP | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\WINDOWS\system32\netsh.exe" advfirewall set allprofiles state off | C:\Windows\System32\netsh.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 138
Read events
14 129
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | InstalledVersionMajor |
Value: 02005C5CAFB1C050DB01 | |||
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | InstalledVersionMinor |
Value: 22005C5CAFB1C050DB01 | |||
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | InstalledVersionBuild |
Value: 616D5C5CAFB1C050DB01 | |||
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | InstalledVersionRevision |
Value: 00005C5CAFB1C050DB01 | |||
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | PreviousAppTerminationFromSuspended |
Value: 005C5CAFB1C050DB01 | |||
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | CurrentDisplayMonitor |
Value: 670061006D0065000000DABFB1B1C050DB01 | |||
| (PID) Process: | (6700) GameBar.exe | Key: | \REGISTRY\A\{42ee1597-018a-576c-a6e2-8d7ecb5bad48}\LocalState |
| Operation: | write | Name: | StartupTipIndex |
Value: 010000000000000085EDB8B1C050DB01 | |||
| (PID) Process: | (6868) wow.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ps1\OpenWithProgids |
| Operation: | write | Name: | Microsoft.PowerShellConsole.1 |
Value: | |||
| (PID) Process: | (3524) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Run |
Value: C:\Users\admin\AppData\Roaming\3iog62.exe | |||
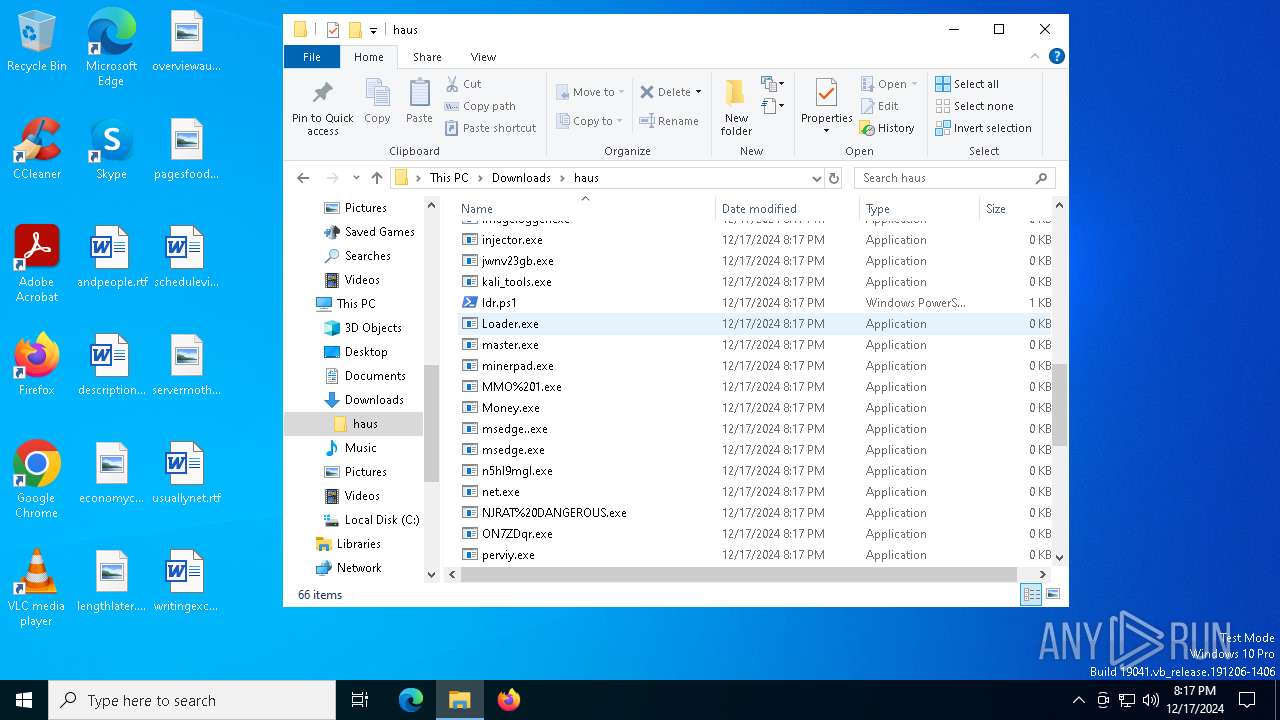
Executable files
43
Suspicious files
47
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\_bz2.pyd | executable | |
MD5:4101128E19134A4733028CFAAFC2F3BB | SHA256:5843872D5E2B08F138A71FE9BA94813AFEE59C8B48166D4A8EB0F606107A7E80 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\_decimal.pyd | executable | |
MD5:D47E6ACF09EAD5774D5B471AB3AB96FF | SHA256:D0DF57988A74ACD50B2D261E8B5F2C25DA7B940EC2AAFBEE444C277552421E6E | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\VCRUNTIME140_1.dll | executable | |
MD5:75E78E4BF561031D39F86143753400FF | SHA256:1758085A61527B427C4380F0C976D29A8BEE889F2AC480C356A3F166433BF70E | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\_cffi_backend.cp311-win_amd64.pyd | executable | |
MD5:739D352BD982ED3957D376A9237C9248 | SHA256:9AEE90CF7980C8FF694BB3FFE06C71F87EB6A613033F73E3174A732648D39980 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\_multiprocessing.pyd | executable | |
MD5:1386DBC6DCC5E0BE6FEF05722AE572EC | SHA256:0AE3BF383FF998886F97576C55D6BF0A076C24395CF6FCD2265316E9A6E8C007 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\_ctypes.pyd | executable | |
MD5:6A9CA97C039D9BBB7ABF40B53C851198 | SHA256:E662D2B35BB48C5F3432BDE79C0D20313238AF800968BA0FAA6EA7E7E5EF4535 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\attrs-24.2.0.dist-info\INSTALLER | text | |
MD5:365C9BFEB7D89244F2CE01C1DE44CB85 | SHA256:CEEBAE7B8927A3227E5303CF5E0F1F7B34BB542AD7250AC03FBCDE36EC2F1508 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\attrs-24.2.0.dist-info\WHEEL | text | |
MD5:52ADFA0C417902EE8F0C3D1CA2372AC3 | SHA256:D7215D7625CC9AF60AED0613AAD44DB57EBA589D0CCFC3D8122114A0E514C516 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\_socket.pyd | executable | |
MD5:8140BDC5803A4893509F0E39B67158CE | SHA256:39715EF8D043354F0AB15F62878530A38518FB6192BC48DA6A098498E8D35769 | |||
| 6468 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI64682\attrs-24.2.0.dist-info\RECORD | csv | |
MD5:8037E693EAFED6C3D0CCE916BABB50C4 | SHA256:688073F6556808D9139FEA52BEC3802D8C0D7CE07978B98AAE8DB5C98FACC0DF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
55 421
DNS requests
37
Threats
131
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6868 | wow.exe | GET | — | 8.130.24.191:80 | http://8.130.24.191/02.08.2022.exe | unknown | — | — | unknown |
6868 | wow.exe | GET | 301 | 140.82.121.4:80 | http://github.com/tiraUnderCode/rev/raw/main/Client-built.exe | unknown | — | — | shared |
2736 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6868 | wow.exe | GET | — | 31.41.244.11:80 | http://31.41.244.11/files/6546212505/ON7ZDqr.exe | unknown | — | — | unknown |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6868 | wow.exe | GET | — | 31.41.244.11:80 | http://31.41.244.11/files/6989783370/8oMoEDZ.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2736 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2736 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
github.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6868 | wow.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
6868 | wow.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
6868 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6 ETPRO signatures available at the full report