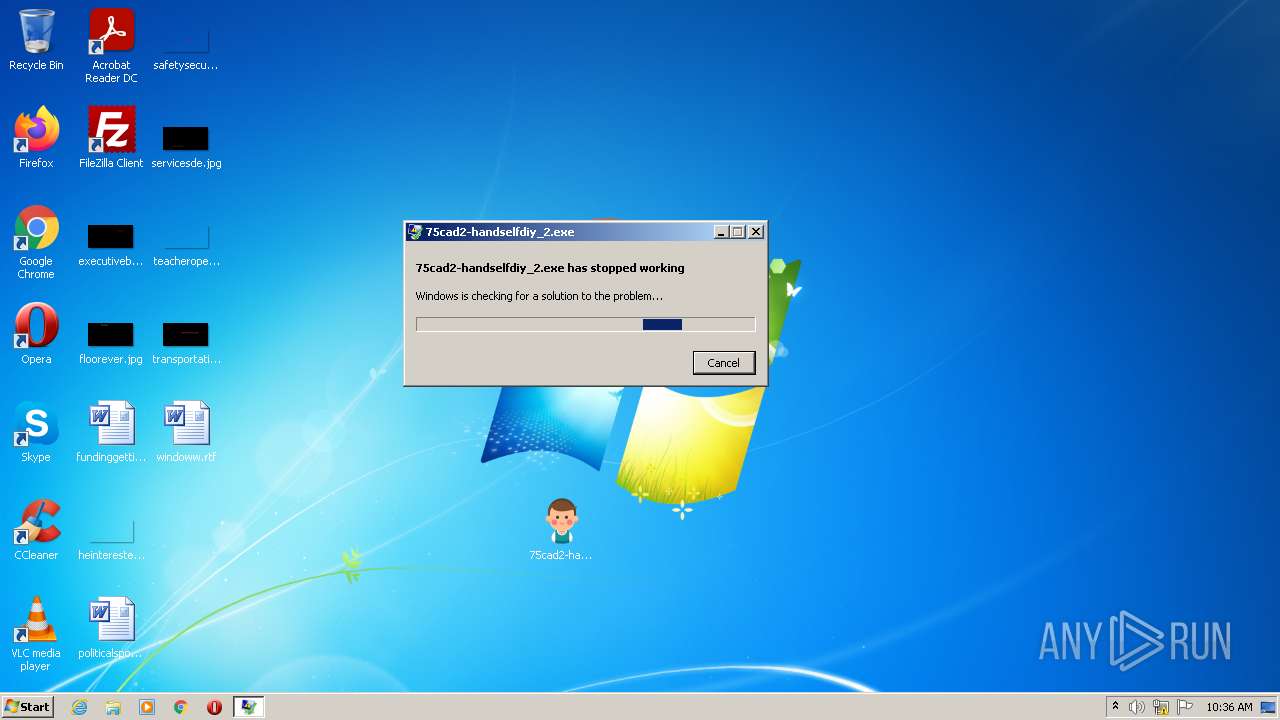
| File name: | 75cad2-handselfdiy_2.exe.zip |
| Full analysis: | https://app.any.run/tasks/8ff482a8-5fe9-402d-b3d6-5bb2c855859d |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 09:35:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B26D0614CCC727AFC5B40299CE002111 |
| SHA1: | EA18D869DAA9094F3DF2EA56C1A504E301EA6F94 |
| SHA256: | D624CD4DDFAFB9B4EF610036307549833937C56F398CE5B609D2476E3A2A5078 |
| SSDEEP: | 12288:KwDTf+S42DTE+1bhEEZYIVmLkfUMo0h/KVuUX/lOHzodzJul4QnlJlO4EAO:P/WF2nbq6mcqVdvMmzJulPHlO4EAO |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 2492)
Application was dropped or rewritten from another process
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 524)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Changes settings of System certificates
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Known privilege escalation attack
- DllHost.exe (PID: 2628)
SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2492)
Checks supported languages
- WinRAR.exe (PID: 2492)
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 524)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Reads the computer name
- WinRAR.exe (PID: 2492)
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 524)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2492)
Adds / modifies Windows certificates
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Checks for external IP
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Executed via COM
- DllHost.exe (PID: 2628)
INFO
Manual execution by user
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 524)
Reads settings of System Certificates
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Checks Windows Trust Settings
- 75cad2-handselfdiy_2.exe (PID: 3468)
- 75cad2-handselfdiy_2.exe (PID: 2848)
Checks supported languages
- DllHost.exe (PID: 2628)
Reads the computer name
- DllHost.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 75cad2-handselfdiy_2.exe |
|---|---|
| ZipUncompressedSize: | 1793024 |
| ZipCompressedSize: | 810481 |
| ZipCRC: | 0x35f26a1c |
| ZipModifyDate: | 2022:06:27 11:31:23 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
48
Monitored processes
5
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | "C:\Users\admin\Desktop\75cad2-handselfdiy_2.exe" | C:\Users\admin\Desktop\75cad2-handselfdiy_2.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
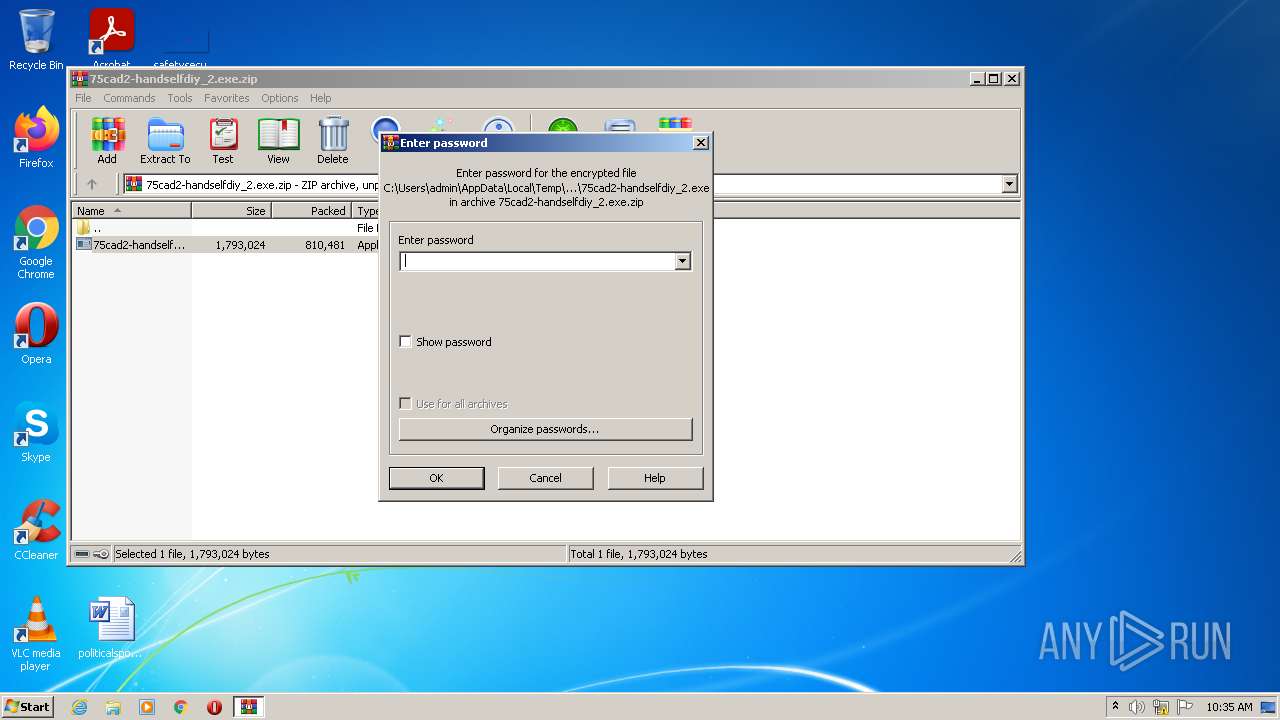
| 2492 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\75cad2-handselfdiy_2.exe.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2628 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\Desktop\75cad2-handselfdiy_2.exe" | C:\Users\admin\Desktop\75cad2-handselfdiy_2.exe | DllHost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3468 | "C:\Users\admin\Desktop\75cad2-handselfdiy_2.exe" | C:\Users\admin\Desktop\75cad2-handselfdiy_2.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
10 042
Read events
9 935
Write events
106
Delete events
1
Modification events
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\75cad2-handselfdiy_2.exe.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
8
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3468 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3468 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_BE25D0FE540174A4A87E2295C663329D | der | |
MD5:— | SHA256:— | |||
| 3468 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_BE25D0FE540174A4A87E2295C663329D | binary | |
MD5:— | SHA256:— | |||
| 2848 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3468 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9DD071679C018B2129B579E1C864DC6B | der | |
MD5:— | SHA256:— | |||
| 2848 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2848 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\Local\Temp\CabDBEB.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2848 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2492.20770\75cad2-handselfdiy_2.exe | executable | |
MD5:— | SHA256:— | |||
| 3468 | 75cad2-handselfdiy_2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9DD071679C018B2129B579E1C864DC6B | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
12
DNS requests
7
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3468 | 75cad2-handselfdiy_2.exe | GET | 200 | 79.133.177.216:80 | http://ocsp.trust-provider.cn/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQDhvjmfMdSVsHZ9u52p9jqu3rd8gQUXzp8ERB%2BDGdxYdyLo7UAA2f1VxwCEQCMXk%2BMGFdCQ4Wss7oZvYg0 | RU | der | 600 b | suspicious |
3468 | 75cad2-handselfdiy_2.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEQCyDO1VLjGgvzQ6dSh0O%2Bmr | US | der | 472 b | whitelisted |
2848 | 75cad2-handselfdiy_2.exe | GET | 200 | 96.16.145.230:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
3468 | 75cad2-handselfdiy_2.exe | GET | 200 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ef57c6086ee3a9c6 | ZA | compressed | 4.70 Kb | whitelisted |
2848 | 75cad2-handselfdiy_2.exe | GET | 200 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8f238310612a843d | ZA | compressed | 60.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3468 | 75cad2-handselfdiy_2.exe | 149.28.253.196:443 | www.icodeps.com | — | US | suspicious |
3468 | 75cad2-handselfdiy_2.exe | 41.63.96.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | ZA | suspicious |
3468 | 75cad2-handselfdiy_2.exe | 104.18.32.68:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
3468 | 75cad2-handselfdiy_2.exe | 79.133.177.216:80 | ocsp.trust-provider.cn | SOT LINE Limited Company | RU | suspicious |
3468 | 75cad2-handselfdiy_2.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
2848 | 75cad2-handselfdiy_2.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
2848 | 75cad2-handselfdiy_2.exe | 41.63.96.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | ZA | suspicious |
2848 | 75cad2-handselfdiy_2.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
2092 | WerFault.exe | 20.189.173.20:443 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
2848 | 75cad2-handselfdiy_2.exe | 149.28.253.196:443 | www.icodeps.com | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.icodeps.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.trust-provider.cn |
| suspicious |
iplogger.org |
| shared |
x1.c.lencr.org |
| whitelisted |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in DNS Lookup) |
3468 | 75cad2-handselfdiy_2.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
2848 | 75cad2-handselfdiy_2.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |