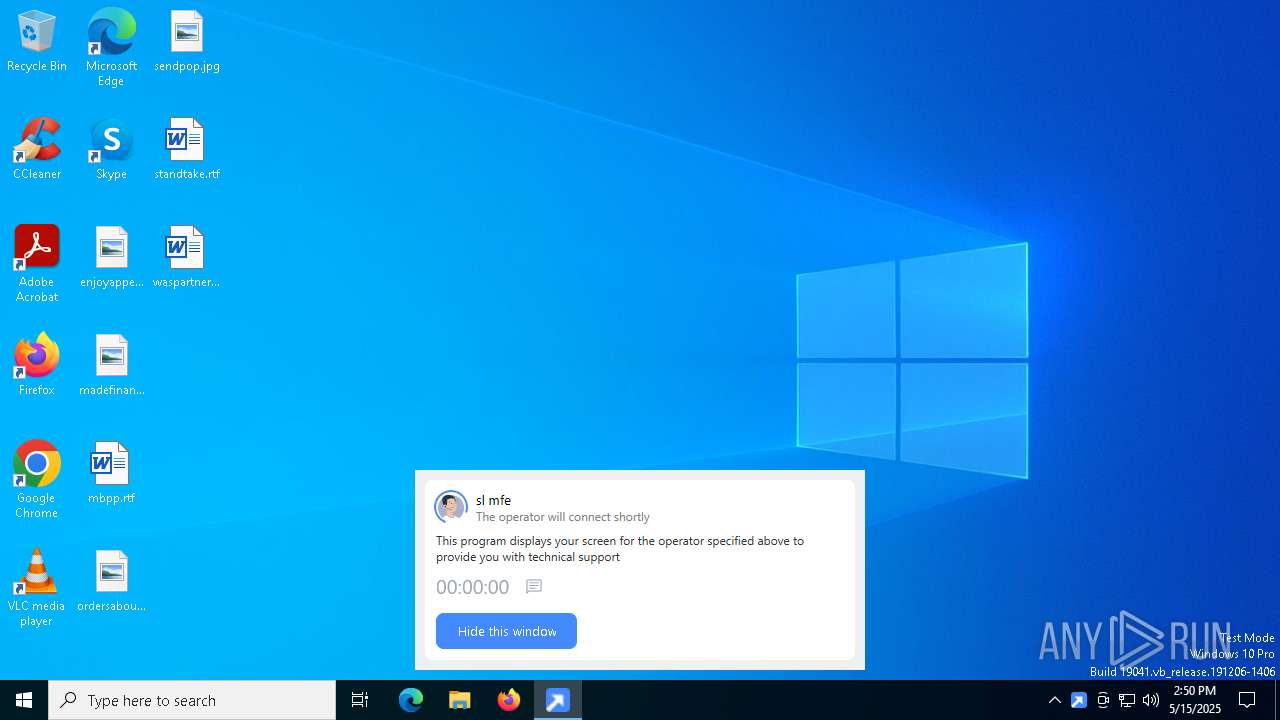
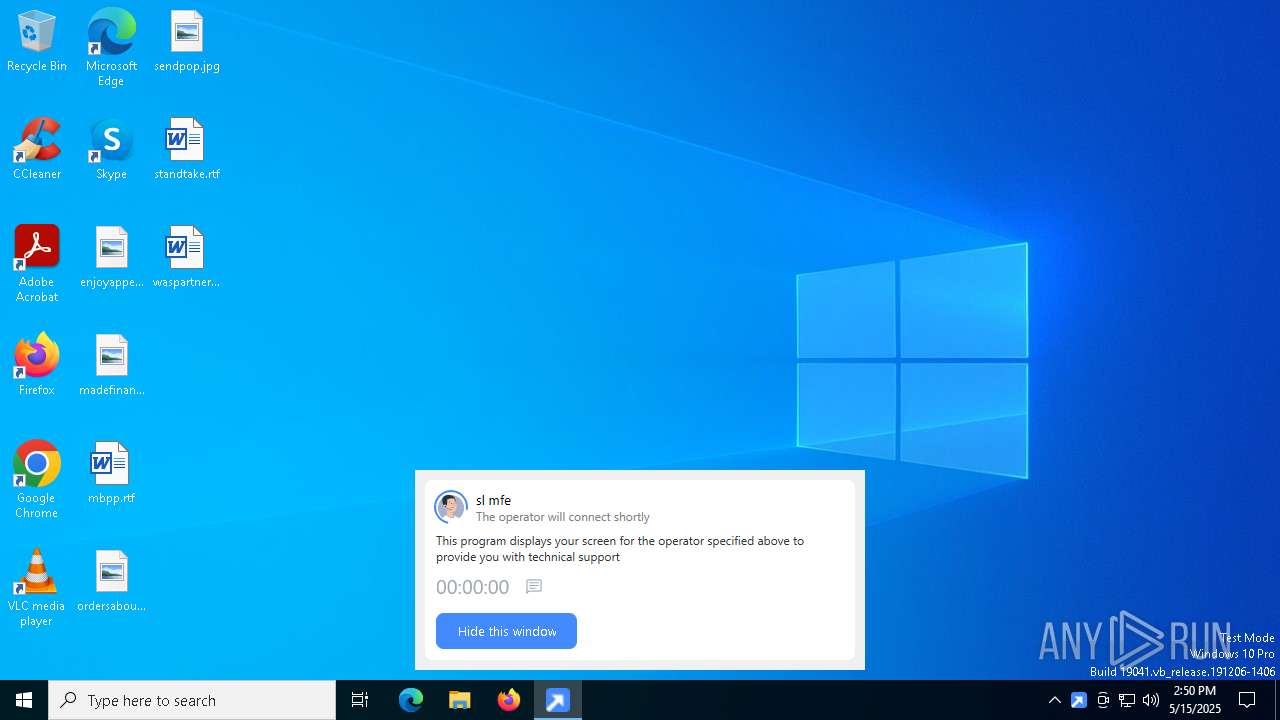
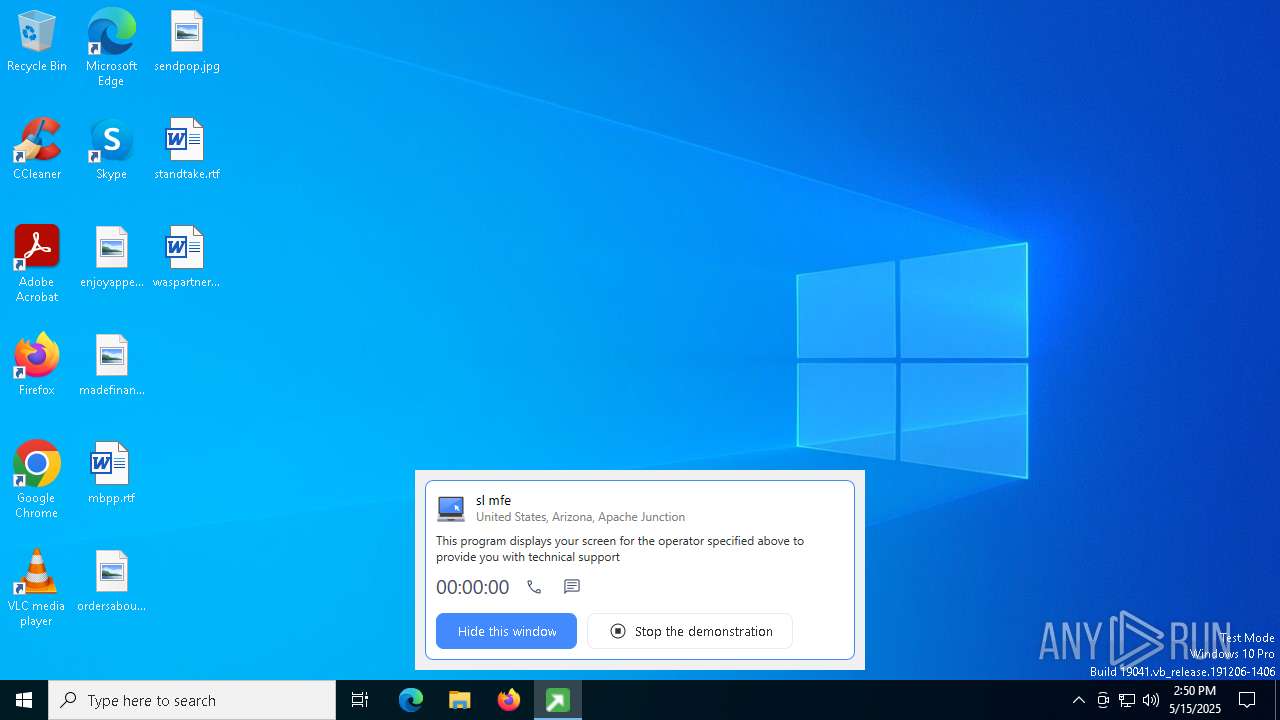
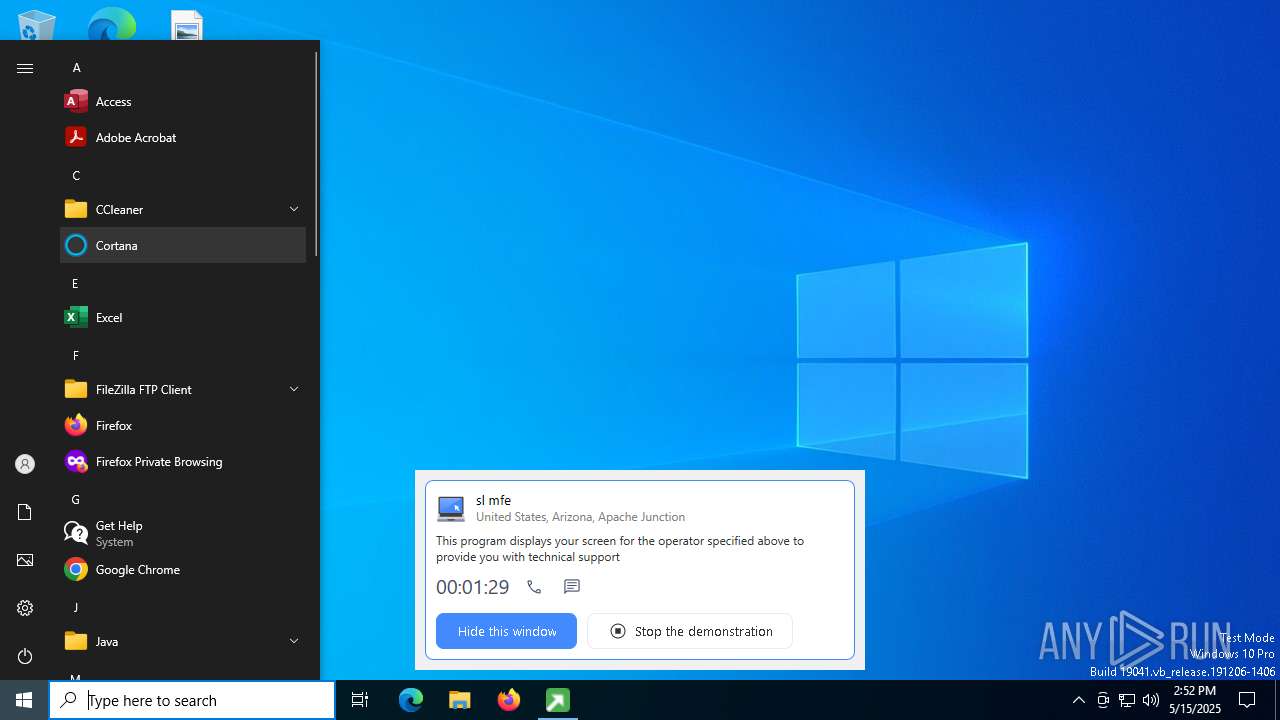
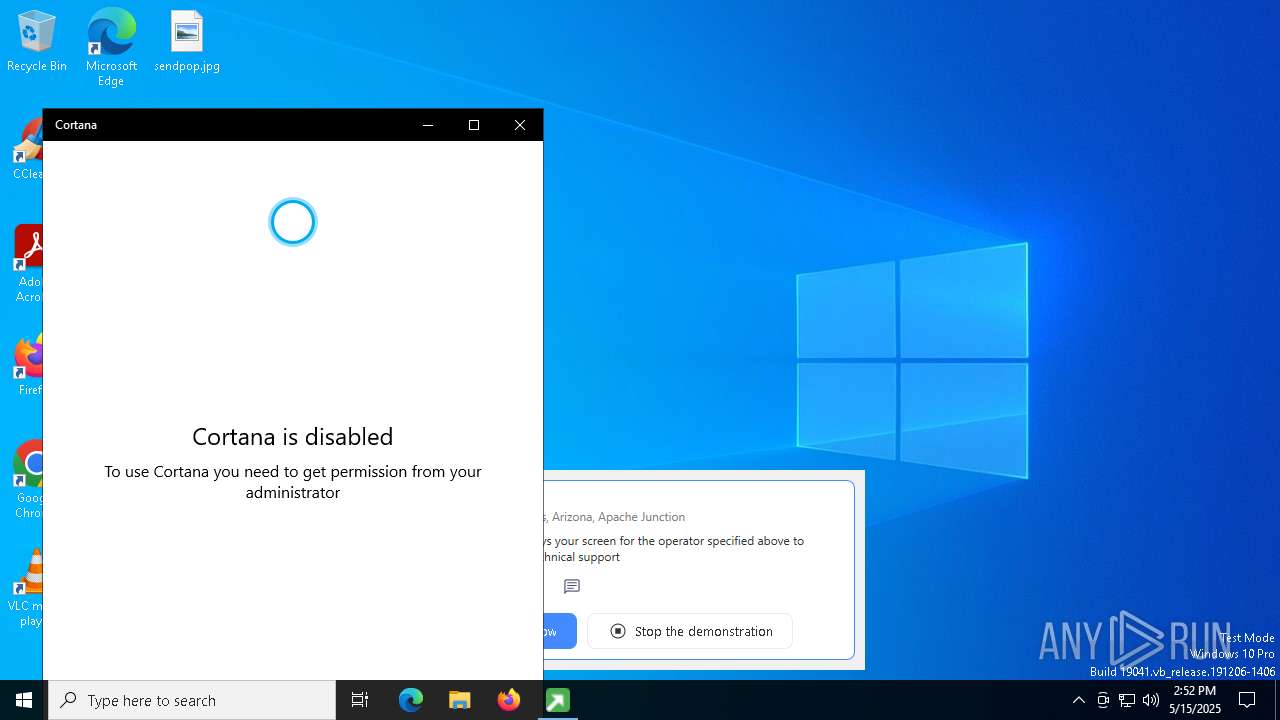
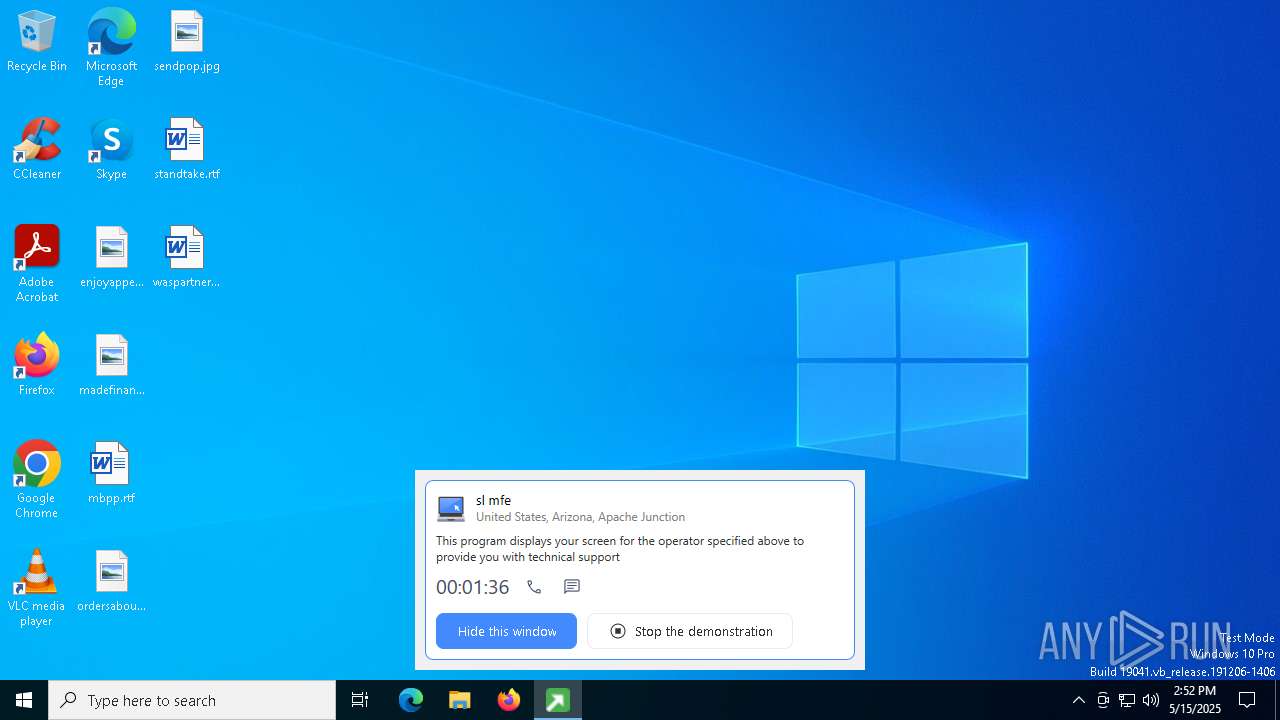
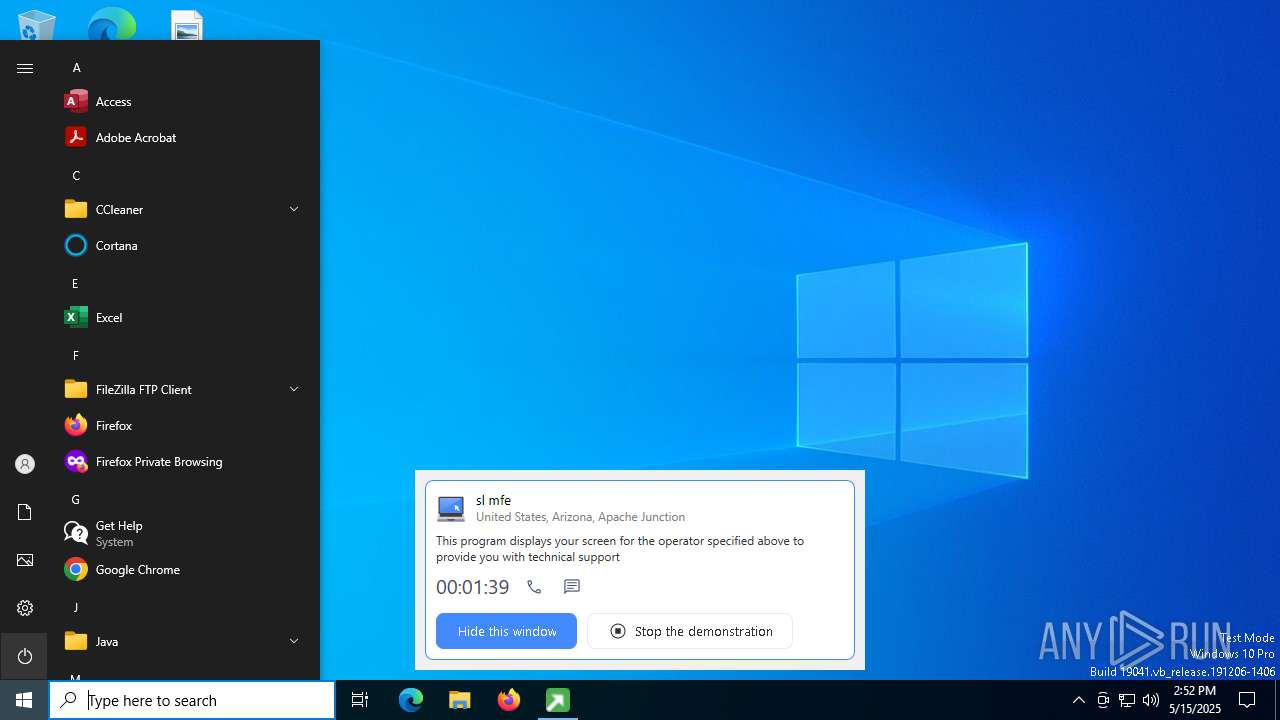
| File name: | getscreen-316735001.exe |
| Full analysis: | https://app.any.run/tasks/8242f377-5469-46ec-b962-bf006ce58ad6 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 14:50:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 3 sections |
| MD5: | BAB409F6B4C30B3CEA541FA6929163A5 |
| SHA1: | D3DF021F843645E095FC3AA17F2BB3099AD5928C |
| SHA256: | D612A3E5DE683EAD13DBE2B0C5480B9BE40ADCEFA4A583B8B6FD0BE122D537B4 |
| SSDEEP: | 98304:dnV8etgqCKyP7IJr556/UfltNhVScNaKxwuWVTteSJmT8P1kmvH9w1VRxS4+bbhW:1I8vzXM5zzp63iKzZ |
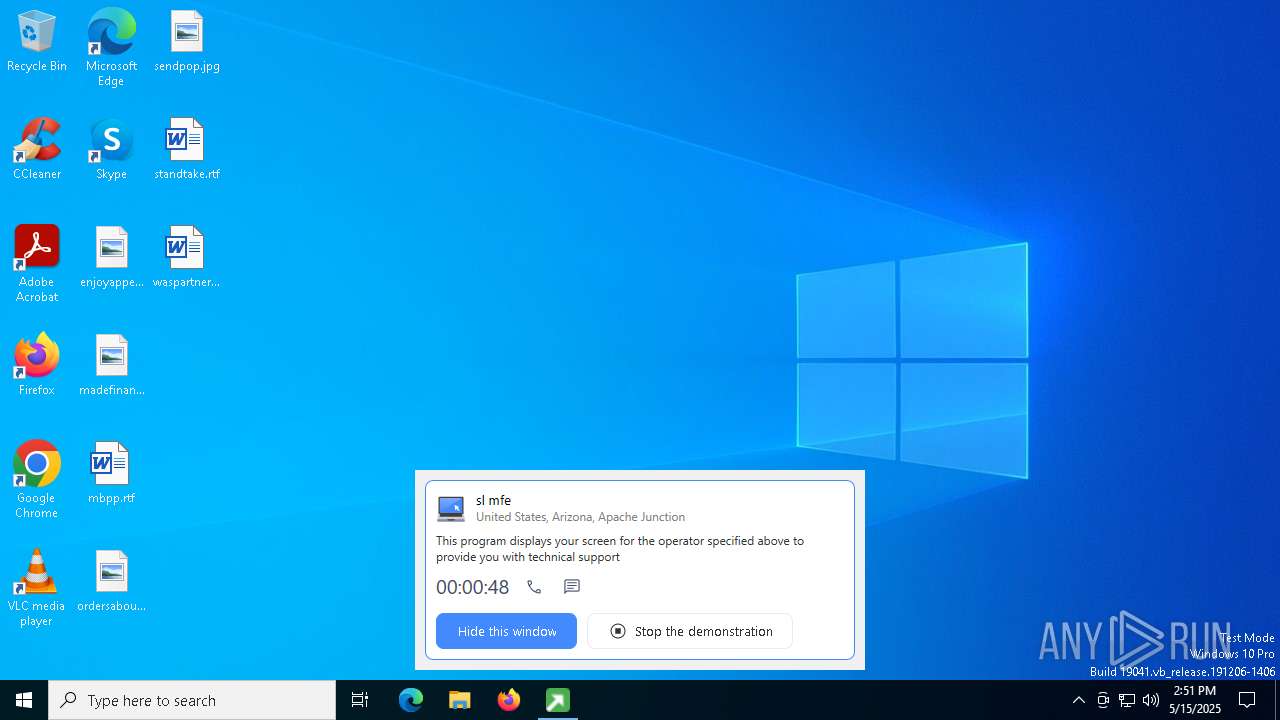
MALICIOUS
GETMESCREEN has been detected (SURICATA)
- getscreen-316735001.exe (PID: 6148)
SUSPICIOUS
Reads the date of Windows installation
- getscreen-316735001.exe (PID: 6808)
Reads security settings of Internet Explorer
- getscreen-316735001.exe (PID: 6808)
- Cortana.exe (PID: 3304)
Application launched itself
- getscreen-316735001.exe (PID: 6808)
- getscreen-316735001.exe (PID: 6148)
Executable content was dropped or overwritten
- getscreen-316735001.exe (PID: 6148)
There is functionality for taking screenshot (YARA)
- getscreen-316735001.exe (PID: 6148)
Connects to unusual port
- getscreen-316735001.exe (PID: 6148)
INFO
Process checks computer location settings
- getscreen-316735001.exe (PID: 6808)
Checks supported languages
- getscreen-316735001.exe (PID: 6808)
- getscreen-316735001.exe (PID: 6148)
- getscreen-316735001.exe (PID: 4300)
- getscreen-316735001.exe (PID: 7992)
- getscreen-316735001.exe (PID: 7648)
- Cortana.exe (PID: 3304)
Reads the computer name
- getscreen-316735001.exe (PID: 6808)
- getscreen-316735001.exe (PID: 6148)
- getscreen-316735001.exe (PID: 4300)
- getscreen-316735001.exe (PID: 7992)
- getscreen-316735001.exe (PID: 7648)
- Cortana.exe (PID: 3304)
GETSCREEN has been detected
- getscreen-316735001.exe (PID: 6808)
- getscreen-316735001.exe (PID: 6148)
- getscreen-316735001.exe (PID: 4300)
- getscreen-316735001.exe (PID: 7648)
- getscreen-316735001.exe (PID: 7992)
- getscreen-316735001.exe (PID: 1052)
Creates files in the program directory
- getscreen-316735001.exe (PID: 6808)
- getscreen-316735001.exe (PID: 6148)
- getscreen-316735001.exe (PID: 4300)
Creates files or folders in the user directory
- getscreen-316735001.exe (PID: 6148)
- Cortana.exe (PID: 3304)
Checks proxy server information
- getscreen-316735001.exe (PID: 6148)
- Cortana.exe (PID: 3304)
Reads mouse settings
- getscreen-316735001.exe (PID: 7992)
UPX packer has been detected
- getscreen-316735001.exe (PID: 6148)
Reads the software policy settings
- slui.exe (PID: 1164)
- Cortana.exe (PID: 3304)
Reads the machine GUID from the registry
- Cortana.exe (PID: 3304)
Reads security settings of Internet Explorer
- SystemSettingsBroker.exe (PID: 7896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:19 17:10:41+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 7753728 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | 27189248 |
| EntryPoint: | 0x21530e0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.2.12.0 |
| ProductVersionNumber: | 3.2.12.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0009) |
| CharacterSet: | Unicode |
| CompanyName: | Point B Ltd |
| InternalName: | Getscreen.me |
| OriginalFileName: | getscreen.exe |
| ProductName: | Getscreen.me |
| FileVersion: | 3.2.12 |
| LegalCopyright: | Copyright (C) 2025 |
| ProductVersion: | 3.2.12 |
Total processes
148
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe" -cpipe \\.\pipe\PCommand96pqgamkioyxdhvye -cmem 0000pipe0PCommand96pqgamkioyxdhvye4v1tkiydva2qqe0 -child | C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe | getscreen-316735001.exe | ||||||||||||
User: SYSTEM Company: Point B Ltd Integrity Level: SYSTEM Exit code: 1 Version: 3.2.12 Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3304 | "C:\Program Files\WindowsApps\Microsoft.549981C3F5F10_1.1911.21713.0_x64__8wekyb3d8bbwe\Cortana.exe" -ServerName:App.AppX2y379sjp88wjq1y80217mddj3fargf2y.mca | C:\Program Files\WindowsApps\Microsoft.549981C3F5F10_1.1911.21713.0_x64__8wekyb3d8bbwe\Cortana.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: CortanaApp.View Version: 1.1911.21713.0 Modules
| |||||||||||||||
| 3884 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe" -gpipe \\.\pipe\PCommand97kteoumbucmefumf5 -gui | C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe | getscreen-316735001.exe | ||||||||||||
User: SYSTEM Company: Point B Ltd Integrity Level: SYSTEM Version: 3.2.12 Modules
| |||||||||||||||
| 4620 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6148 | "C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe" | C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe | getscreen-316735001.exe | ||||||||||||
User: admin Company: Point B Ltd Integrity Level: HIGH Version: 3.2.12 Modules
| |||||||||||||||
| 6808 | "C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe" | C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe | — | explorer.exe | |||||||||||
User: admin Company: Point B Ltd Integrity Level: MEDIUM Exit code: 0 Version: 3.2.12 Modules
| |||||||||||||||
| 7648 | "C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe" -epipe \\.\pipe\PCommand98phqghumeaylnlfd -environment | C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe | — | getscreen-316735001.exe | |||||||||||
User: admin Company: Point B Ltd Integrity Level: HIGH Exit code: 1 Version: 3.2.12 Modules
| |||||||||||||||
| 7896 | C:\Windows\System32\SystemSettingsBroker.exe -Embedding | C:\Windows\System32\SystemSettingsBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Settings Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 395
Read events
5 382
Write events
13
Delete events
0
Modification events
| (PID) Process: | (4300) getscreen-316735001.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\GetScreen\Getscreen.me |
| Operation: | write | Name: | Language |
Value: en | |||
| (PID) Process: | (4300) getscreen-316735001.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001_Classes\*\shell\Download with Getscreen.me |
| Operation: | write | Name: | icon |
Value: C:\Users\admin\AppData\Local\Temp\getscreen-316735001.exe | |||
| (PID) Process: | (3304) Cortana.exe | Key: | \REGISTRY\A\{a96975fb-cafa-5299-2fcd-ae7f0a503d36}\LocalState |
| Operation: | write | Name: | launchedWithDefaultSize |
Value: 011540A9FBA8C5DB01 | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\Content |
| Operation: | write | Name: | CacheVersion |
Value: 1 | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\Content |
| Operation: | write | Name: | CacheLimit |
Value: 51200 | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CacheVersion |
Value: 1 | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CacheLimit |
Value: 1 | |||
| (PID) Process: | (3304) Cortana.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.549981c3f5f10_8wekyb3d8bbwe\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
10
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1052 | getscreen-316735001.exe | C:\ProgramData\Getscreen.me\memory\0000pipe0PCommand96pqgamkioyxdhvye4v1tkiydva2qqe0 | — | |
MD5:— | SHA256:— | |||
| 6148 | getscreen-316735001.exe | C:\ProgramData\Getscreen.me\memory\CC761D2FA6C5DB01EC08B7C4A8C5DB0104180000FFFFFFFF | — | |
MD5:— | SHA256:— | |||
| 6148 | getscreen-316735001.exe | C:\Users\admin\AppData\Local\Getscreen.me\folder\settings.dat | binary | |
MD5:594D0E4B4AC2DC740D2E500C3277C093 | SHA256:1705FE3250F8B539490A1BEB556FBD1D34DA9A55B250E838ADDD81CB85D07DA2 | |||
| 6148 | getscreen-316735001.exe | C:\ProgramData\Getscreen.me\folder\settings.dat | binary | |
MD5:594D0E4B4AC2DC740D2E500C3277C093 | SHA256:1705FE3250F8B539490A1BEB556FBD1D34DA9A55B250E838ADDD81CB85D07DA2 | |||
| 6808 | getscreen-316735001.exe | C:\ProgramData\Getscreen.me\logs\20250515.log | text | |
MD5:C979AF46779924DF03D4021E448E6EC3 | SHA256:FFCD910A003A5BBC48880F88F7FEE9448A988BA29A421A7BFC621E6AA184C0AB | |||
| 6148 | getscreen-316735001.exe | C:\ProgramData\Getscreen.me\bhhfyjtroaexgkhkuhhdllyelyxuklq-elevate.exe | executable | |
MD5:BAB409F6B4C30B3CEA541FA6929163A5 | SHA256:D612A3E5DE683EAD13DBE2B0C5480B9BE40ADCEFA4A583B8B6FD0BE122D537B4 | |||
| 3304 | Cortana.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.549981C3F5F10_8wekyb3d8bbwe\AC\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:5B63C0144C61100C949E65C9B4C7B790 | SHA256:51E7A9D4403161514027724D012C19E4717FD92CC87B31049944A37B40228B8E | |||
| 3304 | Cortana.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.549981C3F5F10_8wekyb3d8bbwe\LocalState\FeatureSettings_v2.sqlite | binary | |
MD5:232665D5F6F437AE406A18B4EFDBEE97 | SHA256:302E2E80DB3893666664CD4835B8DF54A3DC430447F8390D53E1F8C56990D784 | |||
| 3304 | Cortana.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.549981C3F5F10_8wekyb3d8bbwe\AC\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:143CAEE3E0443403717F03727235457C | SHA256:E7078CE133E5F28DF46B195D693D50AC989F4B380478DC728E01BAEFE232D3FC | |||
| 3304 | Cortana.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.549981C3F5F10_8wekyb3d8bbwe\AC\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:2792F007CEC0E3E790E68A71A9DD1BD4 | SHA256:0A9BFB432AACECFDE0A238816BCC96272290DDC037D91D944979C8CC200B0B4C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
130
DNS requests
47
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7188 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7188 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3304 | Cortana.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3304 | Cortana.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6148 | getscreen-316735001.exe | 51.89.95.37:443 | getscreen.me | OVH SAS | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
getscreen.me |
| unknown |
px-br1.getscreen.me |
| unknown |
px-us2.getscreen.me |
| unknown |
px-kr1.getscreen.me |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6148 | getscreen-316735001.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |