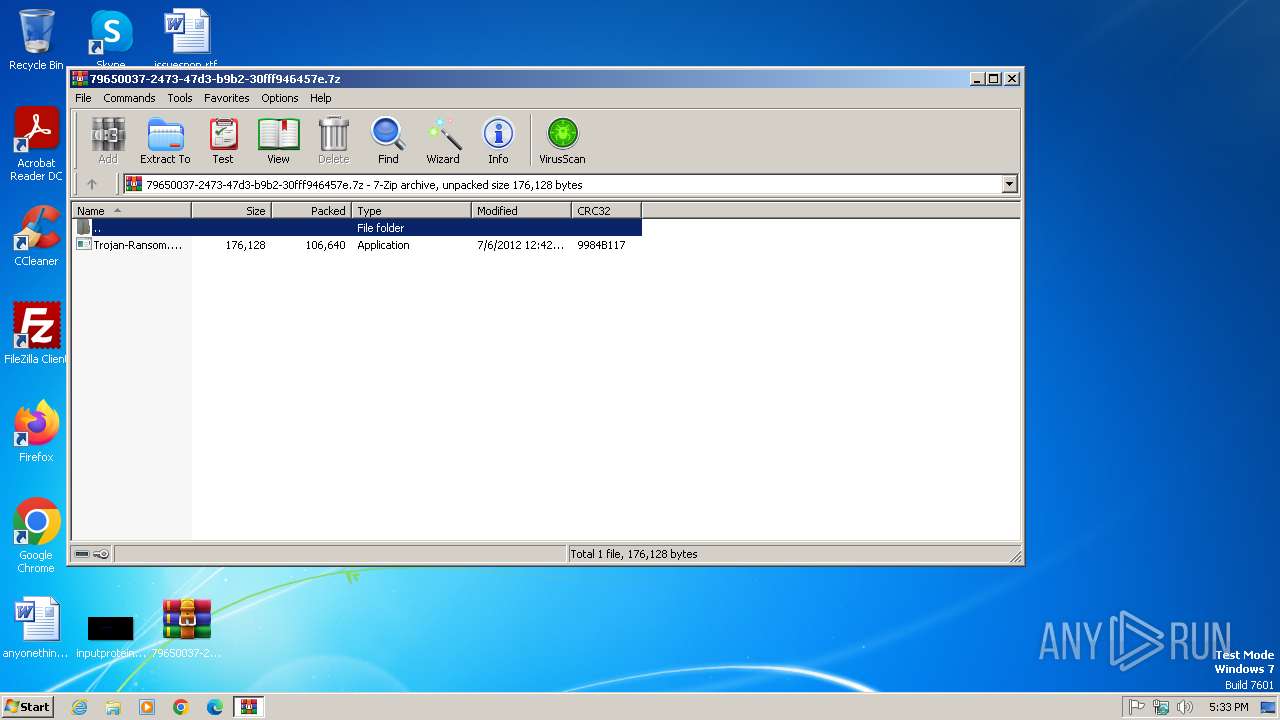
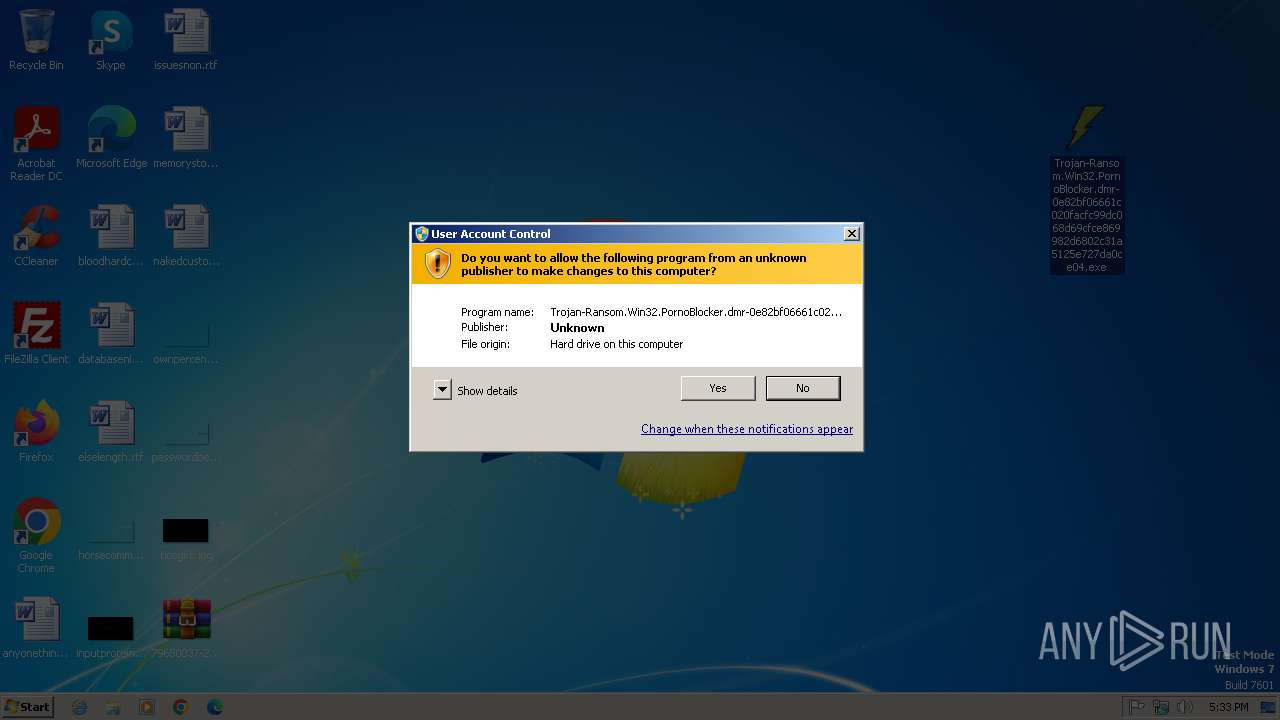
| File name: | Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.7z |
| Full analysis: | https://app.any.run/tasks/79650037-2473-47d3-b9b2-30fff946457e |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2025, 16:32:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EBA6ED0B88C16022D592B4964E86E6BB |
| SHA1: | E4C14A33148AE55317F30CFA2021FAA6A3046886 |
| SHA256: | D6022A4DC3FCBA9FABFE540B18037CC5F30F0FFA1EFAD51FBCC3AD7EC75496FB |
| SSDEEP: | 3072:O861V7V/MRjSFTaw2lHCnMMWf4QUf2k1S76agtc7w4:O861VxERjyTaiMtf4z/1+wqN |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 1452)
Runs injected code in another process
- cleansweep.exe (PID: 2420)
- Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe (PID: 1380)
Changes the autorun value in the registry
- explorer.exe (PID: 1452)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 1452)
Application launched itself
- cleansweep.exe (PID: 1396)
- Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe (PID: 1980)
Modifies the phishing filter of IE
- explorer.exe (PID: 1452)
Changes internet zones settings
- explorer.exe (PID: 1452)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1572)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1452)
Reads the Internet Settings
- explorer.exe (PID: 1452)
Reads the computer name
- Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe (PID: 1380)
- cleansweep.exe (PID: 2420)
Checks supported languages
- cleansweep.exe (PID: 1396)
- cleansweep.exe (PID: 2420)
- Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe (PID: 1980)
- Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe (PID: 1380)
Checks proxy server information
- explorer.exe (PID: 1452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2012:07:06 11:42:20+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe |
Total processes
44
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1380 | C:\Users\admin\Desktop\Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe | C:\Users\admin\Desktop\Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe | — | Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe | |||||||||||
User: admin Company: nmsz Integrity Level: HIGH Description: goods Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1396 | "C:\cleansweep\cleansweep.exe" | C:\cleansweep\cleansweep.exe | — | explorer.exe | |||||||||||
User: admin Company: nmsz Integrity Level: MEDIUM Description: goods Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1452 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\79650037-2473-47d3-b9b2-30fff946457e.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1980 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe | explorer.exe | ||||||||||||
User: admin Company: nmsz Integrity Level: HIGH Description: goods Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2420 | C:\cleansweep\cleansweep.exe | C:\cleansweep\cleansweep.exe | cleansweep.exe | ||||||||||||
User: admin Company: nmsz Integrity Level: MEDIUM Description: goods Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
6 446
Read events
6 308
Write events
125
Delete events
13
Modification events
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithProgids |
| Operation: | write | Name: | WinRAR |
Value: | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.7z |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs |
| Operation: | write | Name: | 6 |
Value: 370039003600350030003000330037002D0032003400370033002D0034003700640033002D0062003900620032002D003300300066006600660039003400360034003500370065002E0037007A000000BE0032000000000000000000000037393635303033372D323437332D343764332D623962322D3330666666393436343537652E377A2E6C6E6B00840008000400EFBE00000000000000002A00000000000000000000000000000000000000000000000000370039003600350030003000330037002D0032003400370033002D0034003700640033002D0062003900620032002D003300300066006600660039003400360034003500370065002E0037007A002E006C006E006B0000003A000000 | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.7z |
| Operation: | write | Name: | 0 |
Value: 370039003600350030003000330037002D0032003400370033002D0034003700640033002D0062003900620032002D003300300066006600660039003400360034003500370065002E0037007A000000BE0032000000000000000000000037393635303033372D323437332D343764332D623962322D3330666666393436343537652E377A2E6C6E6B00840008000400EFBE00000000000000002A00000000000000000000000000000000000000000000000000370039003600350030003000330037002D0032003400370033002D0034003700640033002D0062003900620032002D003300300066006600660039003400360034003500370065002E0037007A002E006C006E006B0000003A000000 | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.7z |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1452) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
3
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1452 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | binary | |
MD5:7C7631D32035A43897621B0B08249E69 | SHA256:7E8F619E3CDEFDCD385F97FA1B7DBC6F40D665E48BBB2D260237CC27D65C27F8 | |||
| 1572 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1572.29875\Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe | executable | |
MD5:26B2D586CE574390DCF7635572C30C95 | SHA256:34087EE11726348247527D3D398B07A9DF36259107CF9EC5A1D5B408CF053769 | |||
| 1452 | explorer.exe | C:\Users\admin\Desktop\Trojan-Ransom.Win32.PornoBlocker.dmr-0e82bf06661c020facfc99dc068d69cfce869982d6802c31a5125e727da0ce04.exe | executable | |
MD5:26B2D586CE574390DCF7635572C30C95 | SHA256:34087EE11726348247527D3D398B07A9DF36259107CF9EC5A1D5B408CF053769 | |||
| 1452 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | binary | |
MD5:66E36EA7FC90C37E9347F9862EF115ED | SHA256:CD05B06A88AE251D4F7A66772ACC30F0813E664DD40B04E954952F6A9EE6358E | |||
| 1452 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\79650037-2473-47d3-b9b2-30fff946457e.7z.lnk | binary | |
MD5:B64B5B6DCE04940AFB32B28A9BE4014B | SHA256:BB51A59151AFF01A3676A67167B78C8E73AD70CB47D674C17B805197533466D5 | |||
| 1452 | explorer.exe | C:\cleansweep\cleansweep.exe | executable | |
MD5:26B2D586CE574390DCF7635572C30C95 | SHA256:34087EE11726348247527D3D398B07A9DF36259107CF9EC5A1D5B408CF053769 | |||
| 2420 | cleansweep.exe | C:\cleansweep\config.bin | binary | |
MD5:BA4BCC97ED1D93CAB5FE26B1143D9DA5 | SHA256:505B9617C0B805823E22F664B4804FD48BFA02548C3290E908CAD16B9E3AA765 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1452 | explorer.exe | GET | — | 2.16.253.202:80 | http://www.microsoft.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1452 | explorer.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
dontstop21523510.com |
| unknown |
www.dontstop21523510.com |
| unknown |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1452 | explorer.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User Agent (Microsoft Internet Explorer) |
Process | Message |
|---|---|
cleansweep.exe | k0pa |