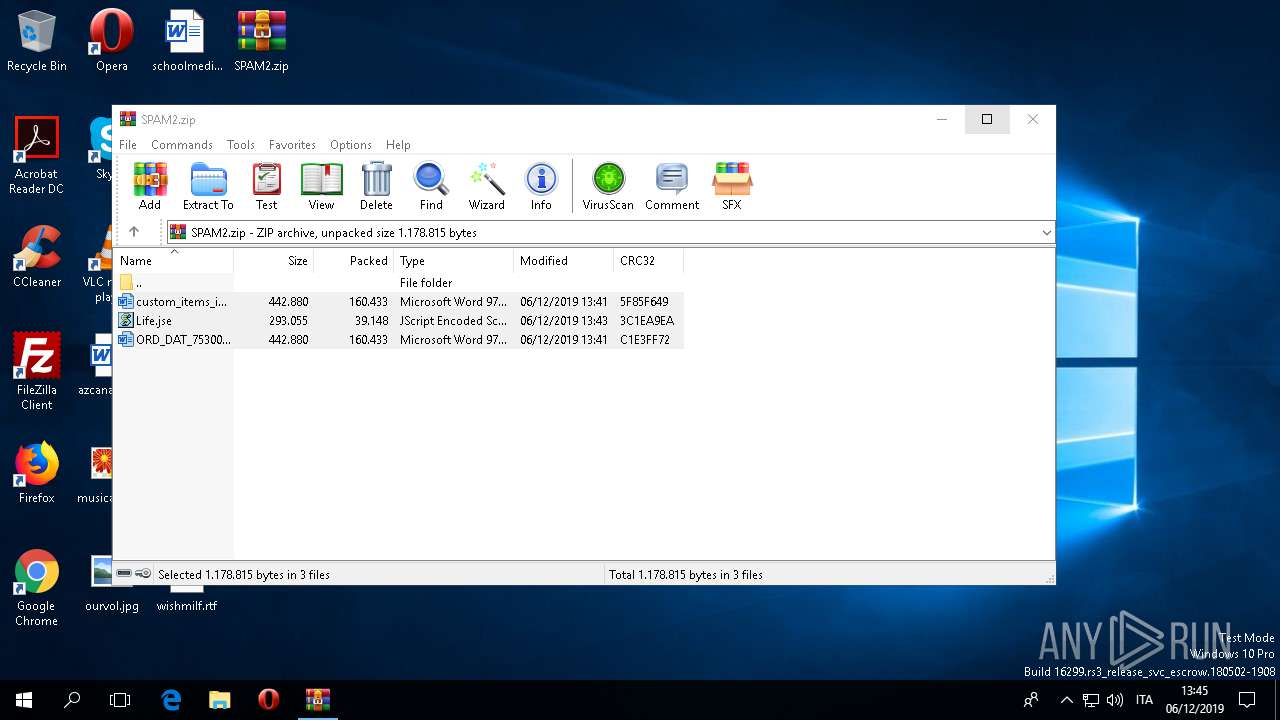
| File name: | SPAM2.zip |
| Full analysis: | https://app.any.run/tasks/98dab8f0-e5af-476b-a00e-2df359a7b871 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 12:44:22 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E514D180BC4AC2EACBE0566523E7334F |
| SHA1: | 608139A2C9FA6664B379193D06F103FC0565A01B |
| SHA256: | D60047CA9D086265A84B7C17211EE912CA5E24AE386AFE0965E9F790A076316A |
| SSDEEP: | 6144:qAz36yWdiksDRpeu1ls/qZ2Ei1ElHmFla3q/XJ4Az36yWdiksDRpeu1ls/qZ2Eiy:l2YxYu1lGRVmhqaa/X52YxYu1lGRVmhB |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
Executes scripts
- WINWORD.EXE (PID: 3216)
- WINWORD.EXE (PID: 444)
SUSPICIOUS
Reads the machine GUID from the registry
- WScript.exe (PID: 2520)
- WScript.exe (PID: 6060)
- WScript.exe (PID: 5632)
Executed via COM
- RuntimeBroker.exe (PID: 5300)
- BackgroundTaskHost.exe (PID: 1160)
Reads Environment values
- WINWORD.EXE (PID: 3216)
- WINWORD.EXE (PID: 444)
INFO
Manual execution by user
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
- WScript.exe (PID: 2520)
Reads the software policy settings
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
Reads settings of System Certificates
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
Creates files in the user directory
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 444)
- WINWORD.EXE (PID: 3216)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3216)
- WINWORD.EXE (PID: 444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:12:06 13:41:18 |
| ZipCRC: | 0x5f85f649 |
| ZipCompressedSize: | 160433 |
| ZipUncompressedSize: | 442880 |
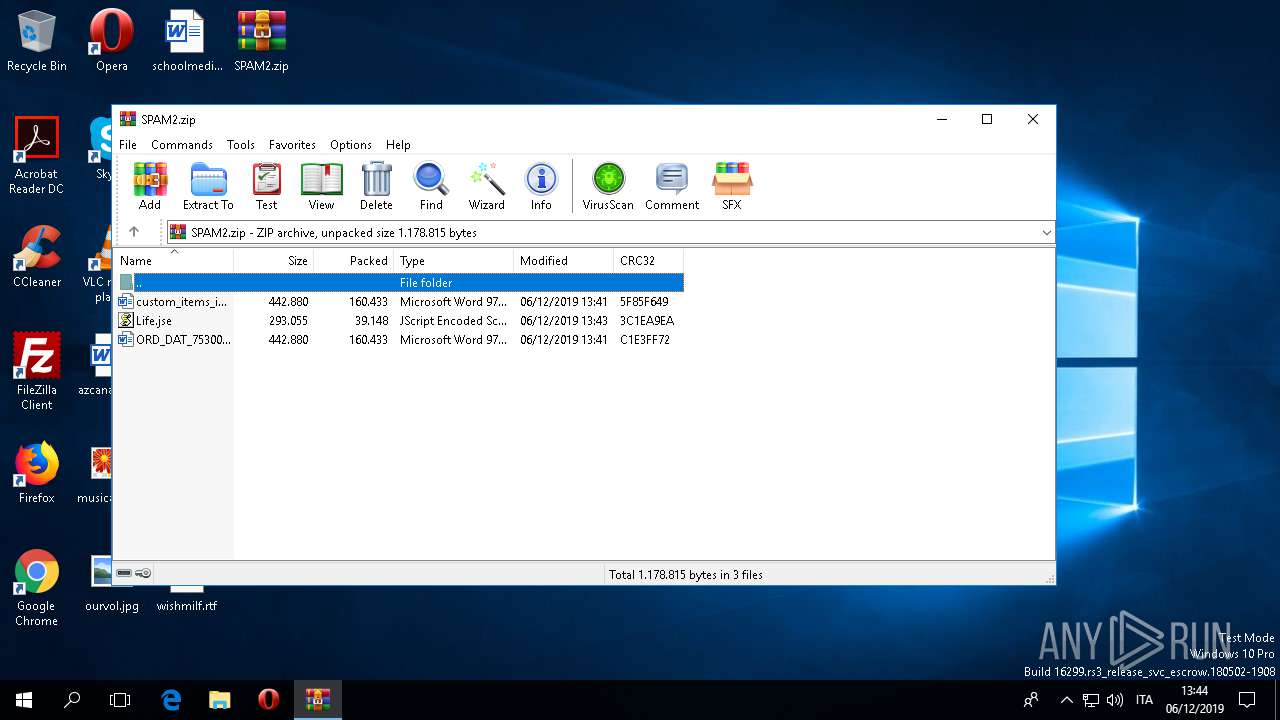
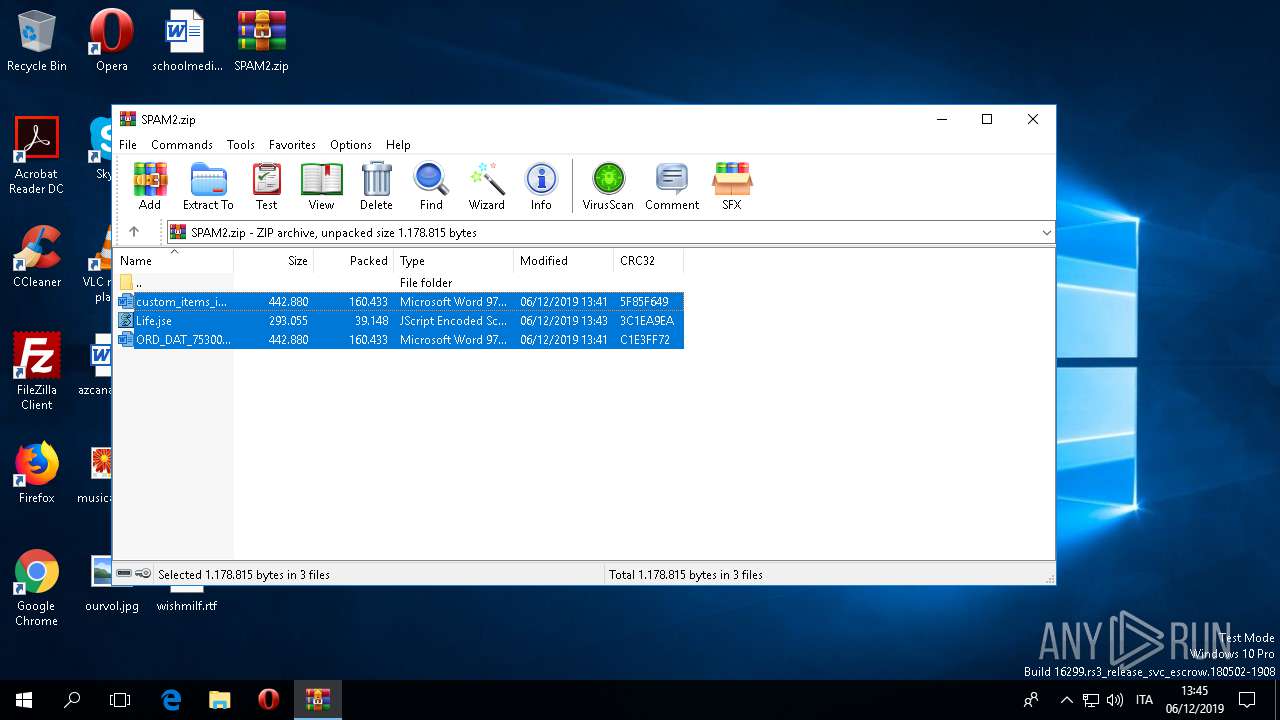
| ZipFileName: | custom_items_inv_97772837.doc |
Total processes
105
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
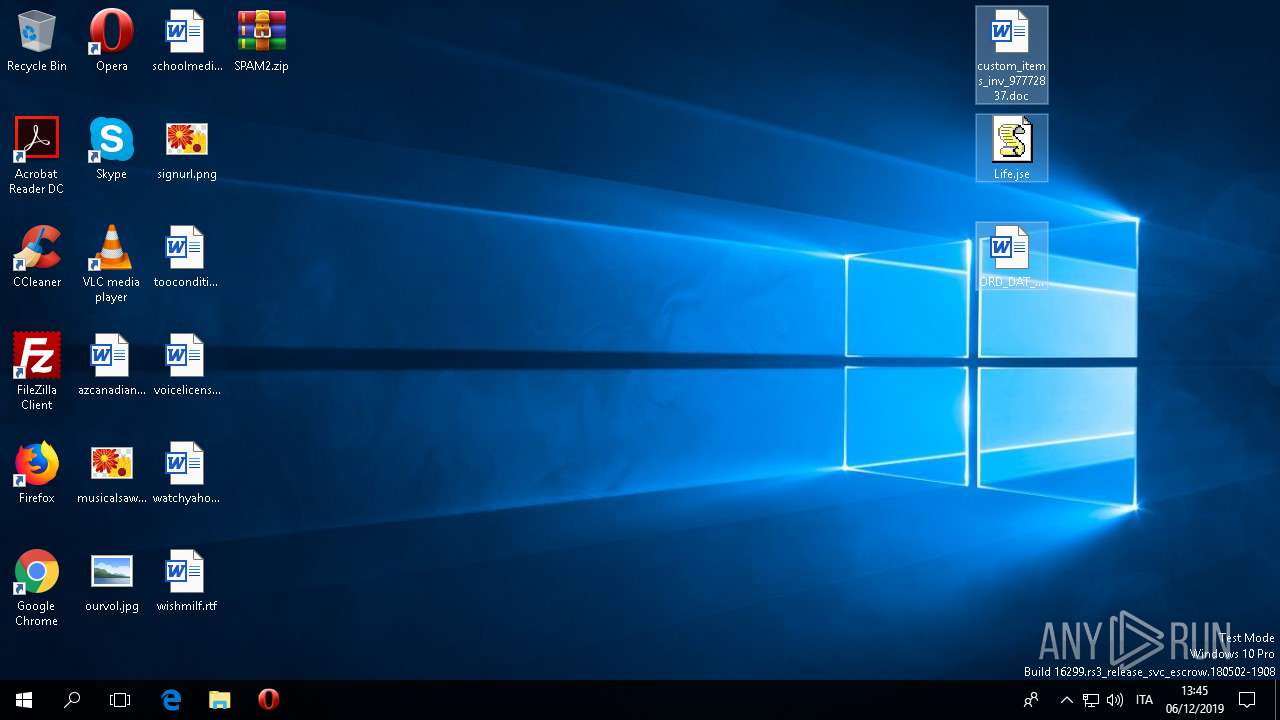
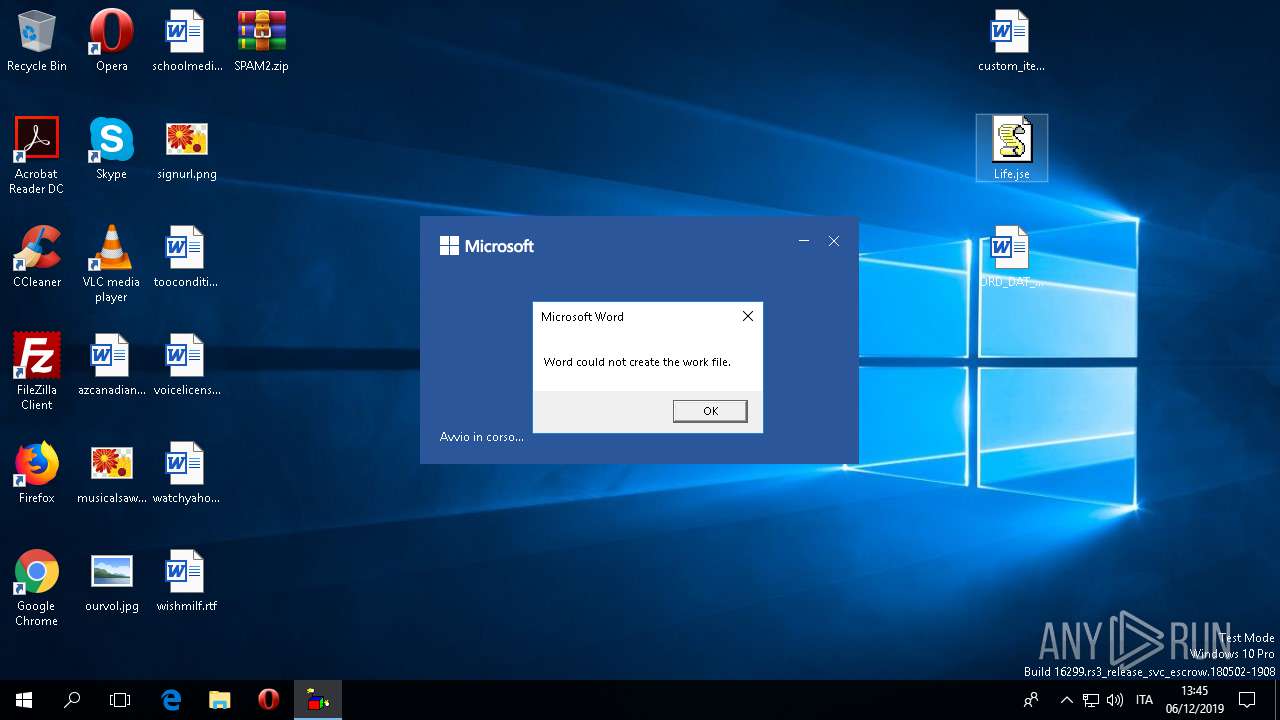
| 444 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\ORD_DAT_75300250.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 1160 | "C:\WINDOWS\system32\BackgroundTaskHost.exe" -ServerName:BackgroundTaskHost.WebAccountProvider | C:\WINDOWS\system32\BackgroundTaskHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Background Task Host Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2388 | C:\WINDOWS\splwow64.exe 8192 | C:\WINDOWS\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
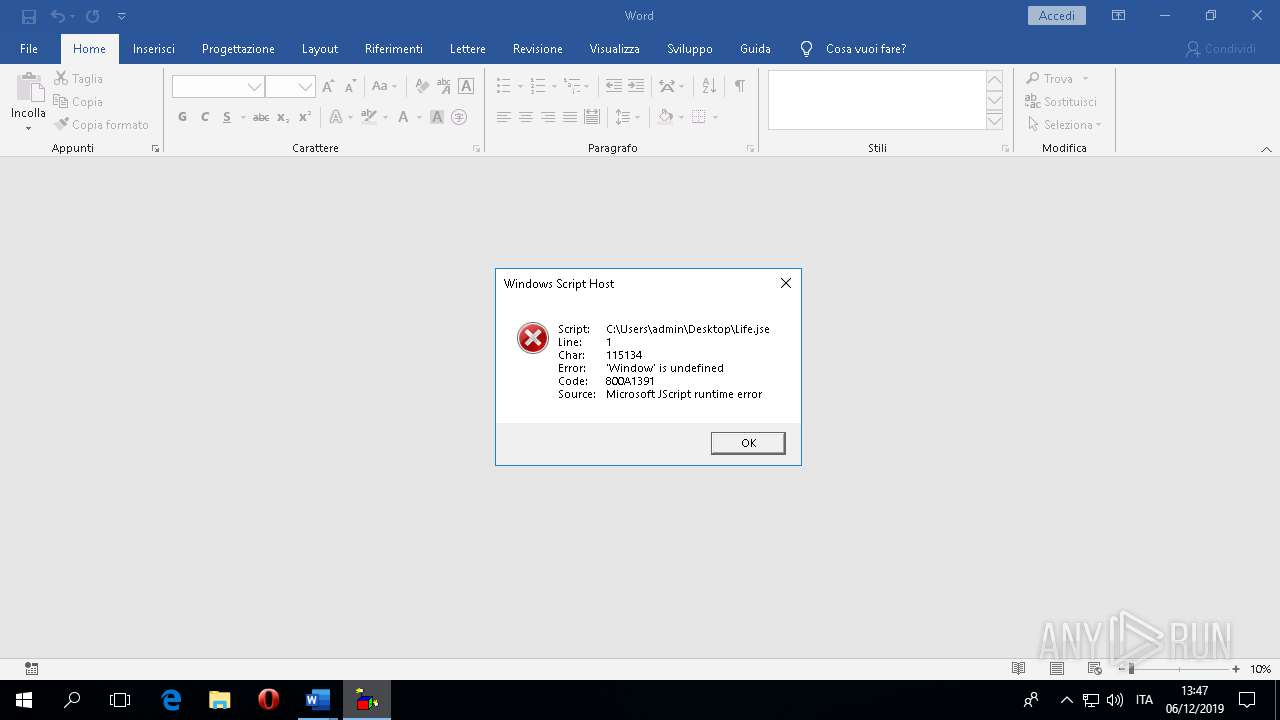
| 2520 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Life.jse" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
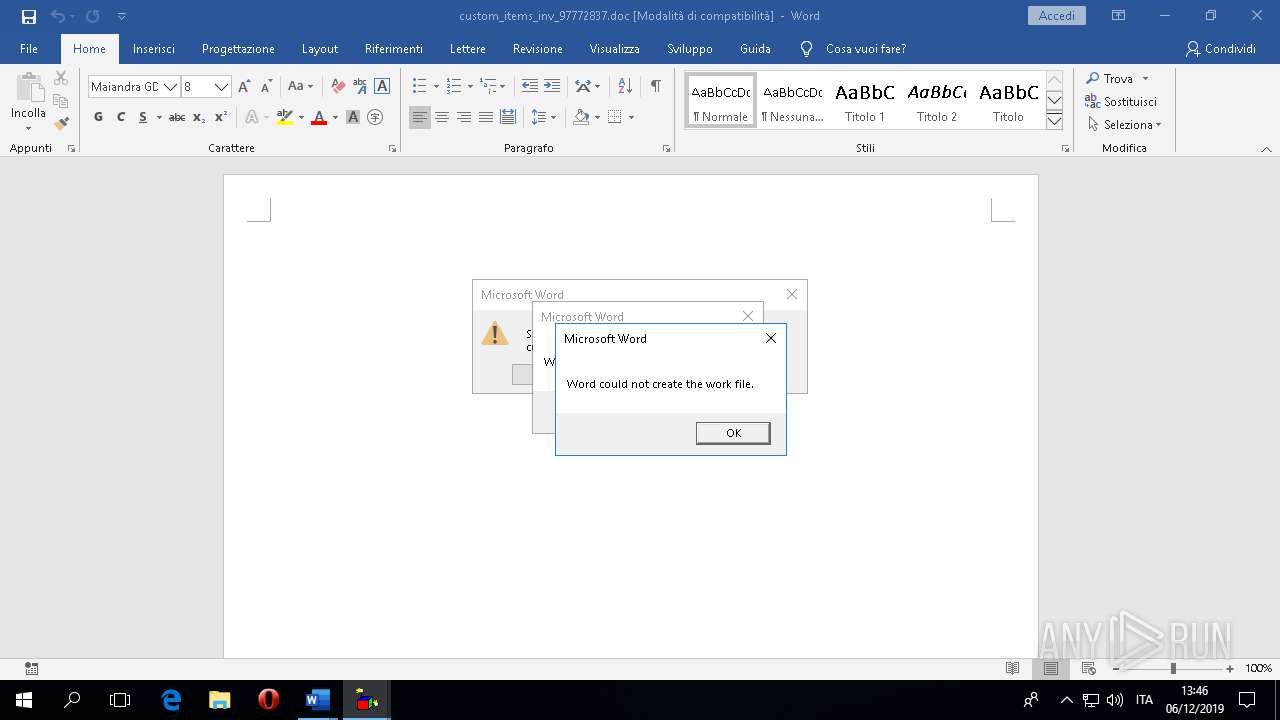
| 3216 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\custom_items_inv_97772837.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 3264 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SPAM2.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 5300 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5632 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Word\Activ\Life.jse" 1 | C:\Windows\System32\WScript.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6060 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Word\Activ\Life.jse" 1 | C:\Windows\System32\WScript.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
6 748
Read events
5 987
Write events
704
Delete events
57
Modification events
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\192\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SPAM2.zip | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF68000000680000002804000051020000 | |||
| (PID) Process: | (3264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
0
Suspicious files
89
Text files
42
Unknown types
67
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 444 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\VH9R4CV4D1QBLPXFWS16.temp | — | |
MD5:— | SHA256:— | |||
| 444 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AF7P3T5V8NDUR7VECMJS.temp | — | |
MD5:— | SHA256:— | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HJZ946I5IEFSQ73SL6B8.temp | — | |
MD5:— | SHA256:— | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GFCY3IXGC26AYKRHLQOW.temp | — | |
MD5:— | SHA256:— | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\7E5BEDC7.wmf | — | |
MD5:— | SHA256:— | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\58C4E26D.wmf | — | |
MD5:— | SHA256:— | |||
| 444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\D098A5C8.wmf | — | |
MD5:— | SHA256:— | |||
| 3216 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\122CE355-1878-43CB-BDE0-A646917CD3CD | xml | |
MD5:— | SHA256:— | |||
| 444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\CC32B716.wmf | — | |
MD5:— | SHA256:— | |||
| 444 | WINWORD.EXE | C:\Users\admin\Desktop\~$D_DAT_75300250.doc | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
114
TCP/UDP connections
110
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3216 | WINWORD.EXE | GET | 200 | 52.109.76.6:443 | https://officeclient.microsoft.com/config16/?lcid=1040&syslcid=1040&uilcid=1040&build=16.0.12026&crev=3 | IE | xml | 111 Kb | whitelisted |
444 | WINWORD.EXE | GET | 200 | 13.107.3.128:443 | https://config.edge.skype.com/config/v2/Office/word/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=it-IT&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bF0D55F9A-572D-45C1-AA2D-F34D70400287%7d&LabMachine=false | US | text | 66.1 Kb | malicious |
3472 | svchost.exe | POST | 200 | 40.90.22.191:443 | https://login.live.com/RST2.srf | US | xml | 1.29 Kb | whitelisted |
3472 | svchost.exe | POST | 400 | 40.90.22.191:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
3216 | WINWORD.EXE | GET | 200 | 13.107.3.128:443 | https://config.edge.skype.com/config/v2/Office/word/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=it-IT&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bFA94B8BA-A423-4F35-B871-840D707FA08D%7d&LabMachine=false | US | text | 66.1 Kb | malicious |
3472 | svchost.exe | POST | 400 | 40.90.22.191:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
3472 | svchost.exe | POST | 200 | 40.90.22.191:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 261 b | whitelisted |
444 | WINWORD.EXE | GET | 200 | 52.109.52.36:443 | https://messaging.office.com/lifecycle/legacygetcustommessage16?app=0&ui=it-IT&src=Office_CanvasLocalSaveDocument_Win32&messagetype=Canvas&hwid=04111-083-043729&ver=16.0.12026&lc=it-IT&platform=10%3A0%3A16299%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA044%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BF0D55F9A-572D-45C1-AA2D-F34D70400287%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofgg6vdq3anjh131%2Cof3ttwdwizkwt531%2Cofskuekmq22yki31%2Cofhpex3jznepoo31%22%7D | JP | xml | 495 b | whitelisted |
3472 | svchost.exe | POST | 400 | 40.90.22.191:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
444 | WINWORD.EXE | GET | 200 | 23.210.248.85:443 | https://fs.microsoft.com/fs/4.9/flatFontAssets.pkg | NL | compressed | 381 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
444 | WINWORD.EXE | 52.109.76.6:443 | officeclient.microsoft.com | Microsoft Corporation | IE | whitelisted |
444 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
3216 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
444 | WINWORD.EXE | 52.114.128.8:443 | self.events.data.microsoft.com | Microsoft Corporation | US | unknown |
3216 | WINWORD.EXE | 2.20.174.205:443 | templateservice.office.com | Akamai Technologies, Inc. | — | unknown |
3216 | WINWORD.EXE | 52.109.76.6:443 | officeclient.microsoft.com | Microsoft Corporation | IE | whitelisted |
3472 | svchost.exe | 40.90.22.191:443 | login.live.com | Microsoft Corporation | US | malicious |
444 | WINWORD.EXE | 52.109.52.36:443 | messaging.office.com | Microsoft Corporation | JP | unknown |
3216 | WINWORD.EXE | 23.210.248.85:443 | fs.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | WINWORD.EXE | 52.109.52.36:443 | messaging.office.com | Microsoft Corporation | JP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
self.events.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
login.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
messaging.office.com |
| whitelisted |
templateservice.office.com |
| whitelisted |
omextemplates.content.office.net |
| whitelisted |
crl.microsoft.com |
| whitelisted |