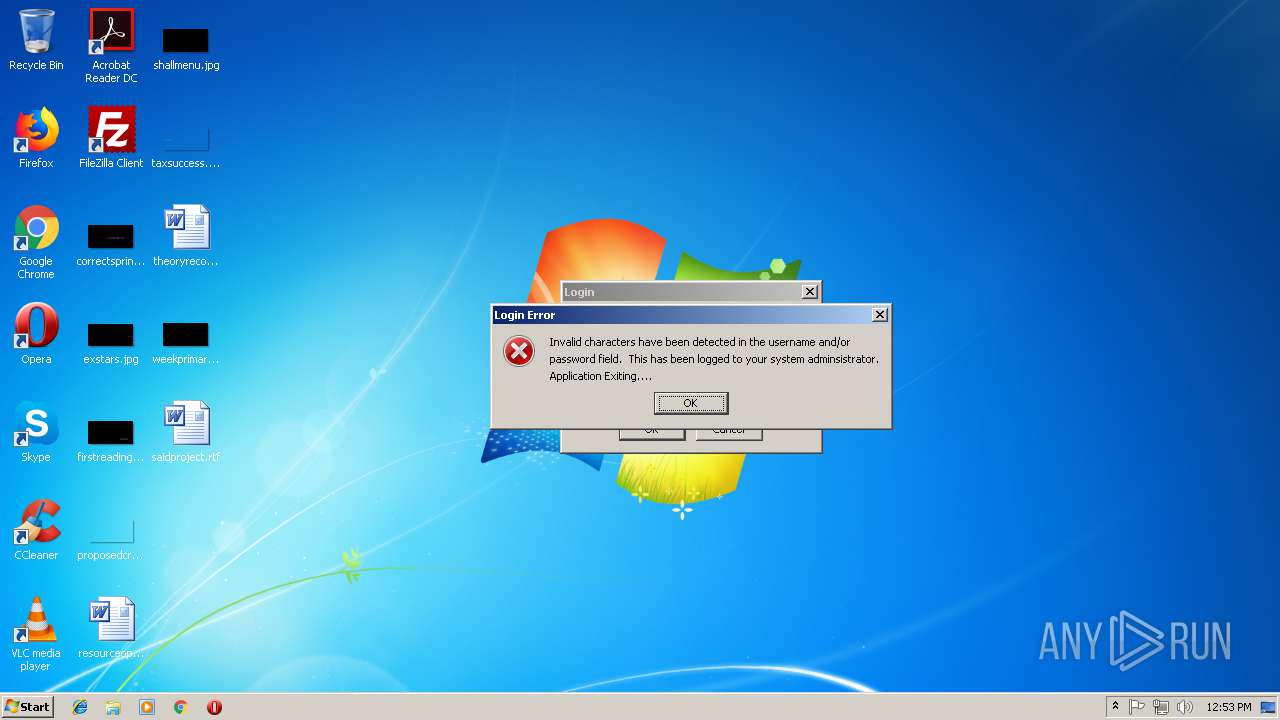
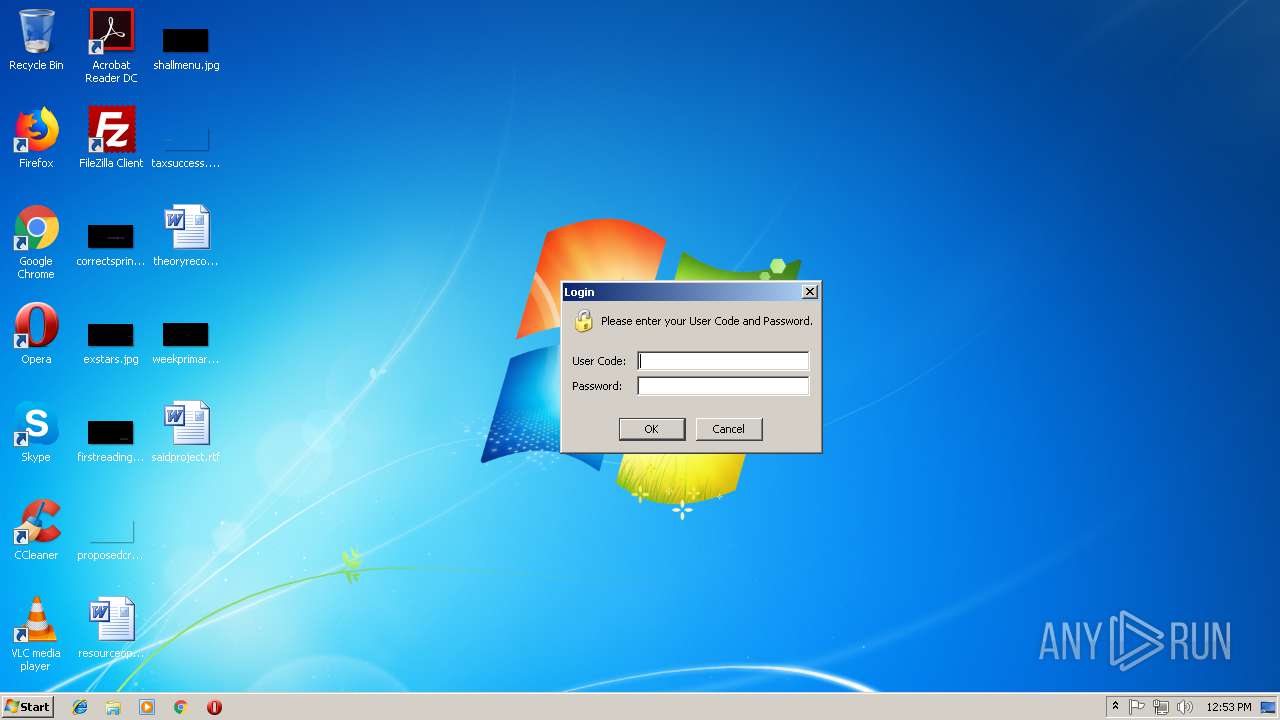
| File name: | iCapture.jnlp |
| Full analysis: | https://app.any.run/tasks/1fe5e64c-a061-4229-85ed-f00ea6e13659 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 12:51:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text, with CRLF line terminators |
| MD5: | 374C3C4F82E4B9DACDD47DDBEB3F75CC |
| SHA1: | 9630D19478A97135E7FD926995837CE75F2AA73D |
| SHA256: | D5E48BEC5F07FC3FB83B5ED2D1CC8F0C13AE233980250FE99F0EA8817B7E6B3C |
| SSDEEP: | 24:2daMgR4BIpU2p4Fa8jGPAZkLgYUzY4HBEQsR4BoVEsR4BoZom9zvn:caYB4uPBEQDBoyDBoZomJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
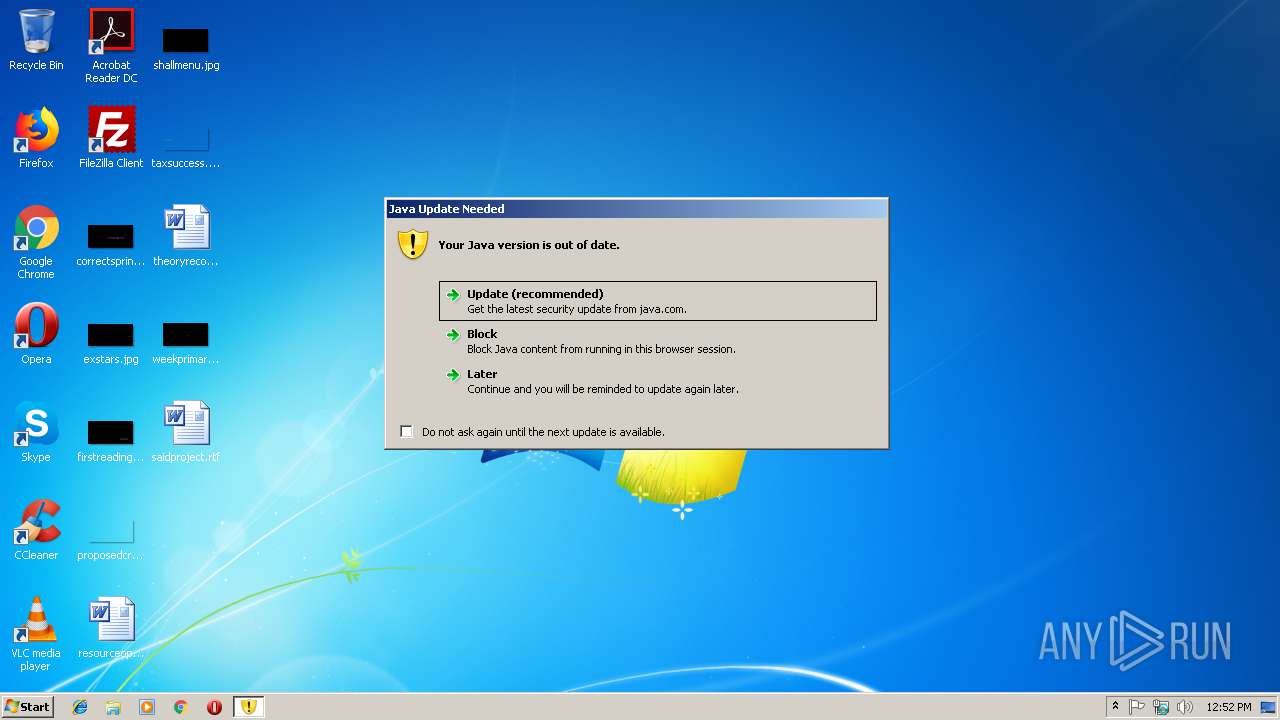
Check for Java to be installed
- javaws.exe (PID: 3668)
Connects to unusual port
- jp2launcher.exe (PID: 292)
Application launched itself
- javaws.exe (PID: 3668)
Executes JAVA applets
- javaws.exe (PID: 3668)
Creates files in the user directory
- jp2launcher.exe (PID: 292)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (88.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (11.6) |
EXIF
XMP
| JnlpSpec: | 1.0+ |
|---|---|
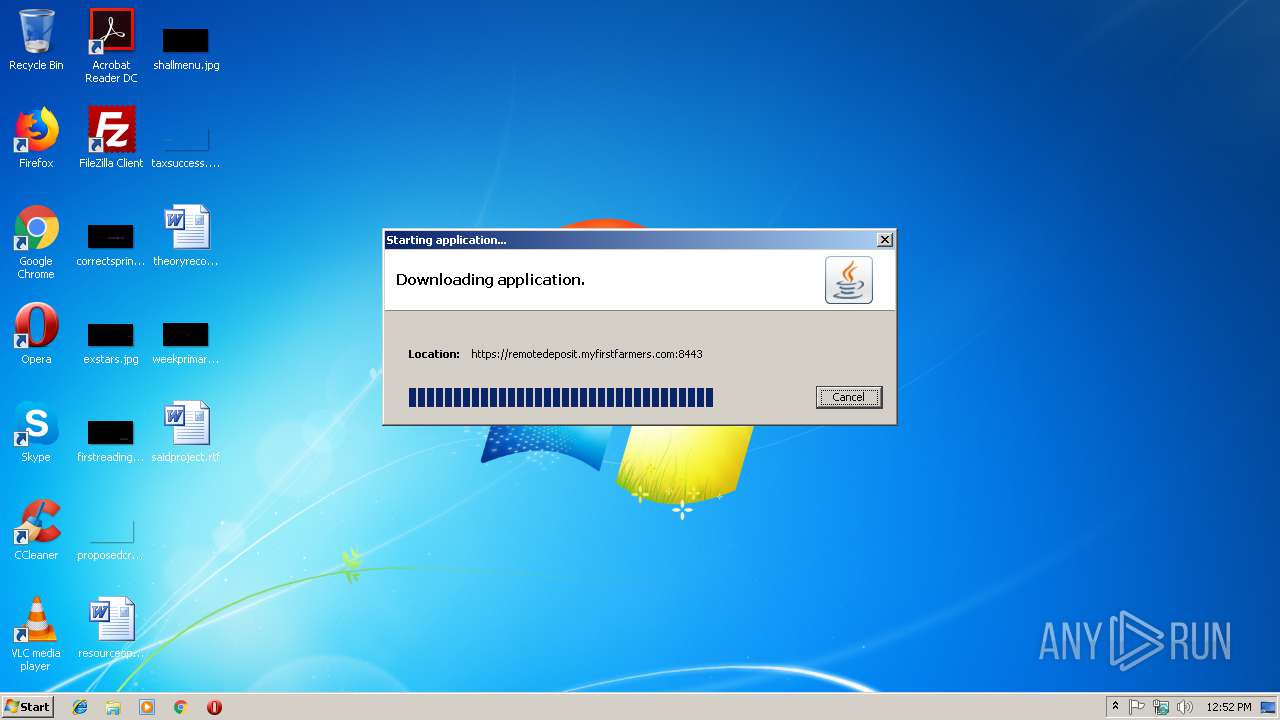
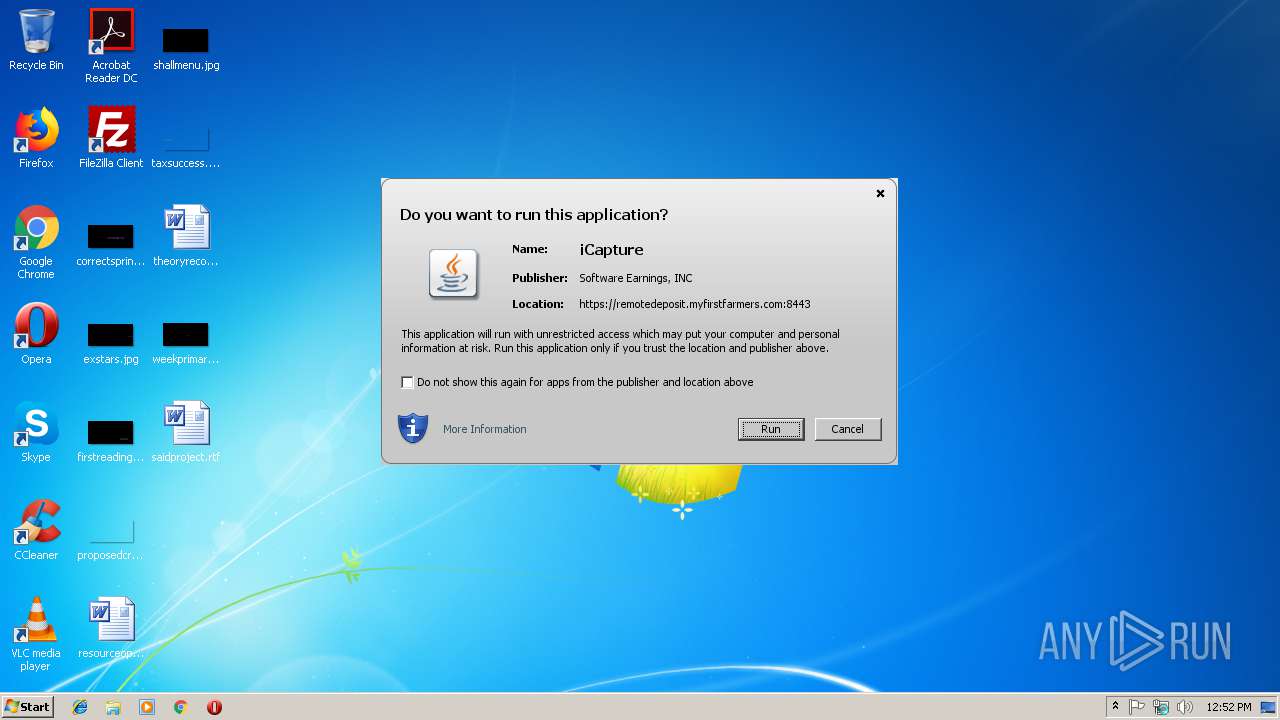
| JnlpCodebase: | https://remotedeposit.myfirstfarmers.com:8443/iCapWeb |
| JnlpHref: | iCapture.jnlp |
| JnlpInformationTitle: | iCapture Thin Client |
| JnlpInformationVendor: | SEI 3.2.12.5 |
| JnlpInformationHomepageHref: | http://www.softwareearnings.com |
| JnlpInformationDescription: | iCapture Thin Client |
| JnlpInformationDescriptionKind: | short |
| JnlpInformationOffline-allowed: | - |
| JnlpSecurityAll-permissions: | - |
| JnlpResourcesOs: | Windows |
| JnlpResourcesJ2seVersion: | 1.6+ |
| JnlpResourcesJ2seHref: | http://java.sun.com/products/autodl/j2se |
| JnlpResourcesJarHref: | sThinClient.jar |
| JnlpResourcesJarMain: | |
| JnlpApplication-descMain-class: | com.sei.swing.client.MainFrame |
| JnlpApplication-descArgument: | remotedeposit.myfirstfarmers.com |
Total processes
36
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Java\jre1.8.0_92\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_92" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfOTJcbGliXGRlcGxveS5qYXIALURqYXZhLnNlY3VyaXR5LnBvbGljeT1maWxlOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxsaWJcc2VjdXJpdHlcamF2YXdzLnBvbGljeQAtRHRydXN0UHJveHk9dHJ1ZQAtWHZlcmlmeTpyZW1vdGUALURqbmxweC5ob21lPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURqbmxweC5vcmlnRmlsZW5hbWVBcmc9QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGlDYXB0dXJlLmpubHAALURqbmxweC5yZW1vdmU9dHJ1ZQAtRHN1bi5hd3Qud2FybXVwPXRydWUALVhib290Y2xhc3NwYXRoL2E6QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzkyXGxpYlxqYXZhd3MuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfOTJcbGliXHBsdWdpbi5qYXIALURqbmxweC5zcGxhc2hwb3J0PTQ5MzE2AC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxiaW5camF2YXcuZXhl -ma QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGphdmF3czI= | C:\Program Files\Java\jre1.8.0_92\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.92.2.14 Modules
| |||||||||||||||
| 2244 | JavaWSSplashScreen -splash 49314 "C:\Program Files\Java\jre1.8.0_92\lib\deploy\splash.gif" | C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.92.2.14 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.92.2" "later" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3120 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.92.2" "1541681539" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\iCapture.jnlp" | C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.92.2.14 Modules
| |||||||||||||||
| 3728 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.92.2" "false" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
203
Read events
93
Write events
100
Delete events
10
Modification events
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1541681539788 | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.version |
Value: 8 | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.92.2 |
Value: later | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expired.version |
Value: 11.92.2 | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.browser.path |
Value: C:\Program Files\Internet Explorer\iexplore.exe | |||
| (PID) Process: | (3120) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.timestamp.11.92.2 |
Value: 1541681539 | |||
| (PID) Process: | (2904) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2904) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1535457890299 | |||
Executable files
10
Suspicious files
4
Text files
30
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 292 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\47\202866f-79fc3457-temp | — | |
MD5:— | SHA256:— | |||
| 292 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\43\743d94ab-79867acf-temp | — | |
MD5:— | SHA256:— | |||
| 292 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\security\blacklist.cache | binary | |
MD5:— | SHA256:— | |||
| 3120 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 2904 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3120 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 3120 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 292 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\45\1738982d-720bdf47-temp | — | |
MD5:— | SHA256:— | |||
| 2904 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 292 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\27\6c1eef9b-6f75035c-temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
59
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
292 | jp2launcher.exe | POST | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com/ | NL | der | 1.74 Kb | whitelisted |
292 | jp2launcher.exe | POST | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com/ | NL | der | 1.66 Kb | whitelisted |
292 | jp2launcher.exe | POST | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com/ | NL | der | 1.66 Kb | whitelisted |
292 | jp2launcher.exe | POST | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com/ | NL | der | 1.69 Kb | whitelisted |
292 | jp2launcher.exe | POST | 200 | 23.37.43.27:80 | http://sv.symcd.com/ | NL | der | 1.57 Kb | shared |
292 | jp2launcher.exe | POST | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com/ | NL | der | 1.69 Kb | whitelisted |
292 | jp2launcher.exe | POST | 200 | 188.121.36.239:80 | http://ocsp.godaddy.com/ | NL | der | 1.74 Kb | whitelisted |
292 | jp2launcher.exe | POST | 200 | 23.37.43.27:80 | http://s2.symcb.com/ | NL | der | 1.71 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
292 | jp2launcher.exe | 188.121.36.239:80 | ocsp.godaddy.com | GoDaddy.com, LLC | NL | unknown |
292 | jp2launcher.exe | 12.23.248.187:8443 | remotedeposit.myfirstfarmers.com | AT&T Services, Inc. | US | unknown |
292 | jp2launcher.exe | 23.37.43.27:80 | s2.symcb.com | Akamai Technologies, Inc. | NL | whitelisted |
292 | jp2launcher.exe | 184.31.87.231:443 | javadl-esd-secure.oracle.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
remotedeposit.myfirstfarmers.com |
| unknown |
ocsp.godaddy.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
sv.symcd.com |
| shared |