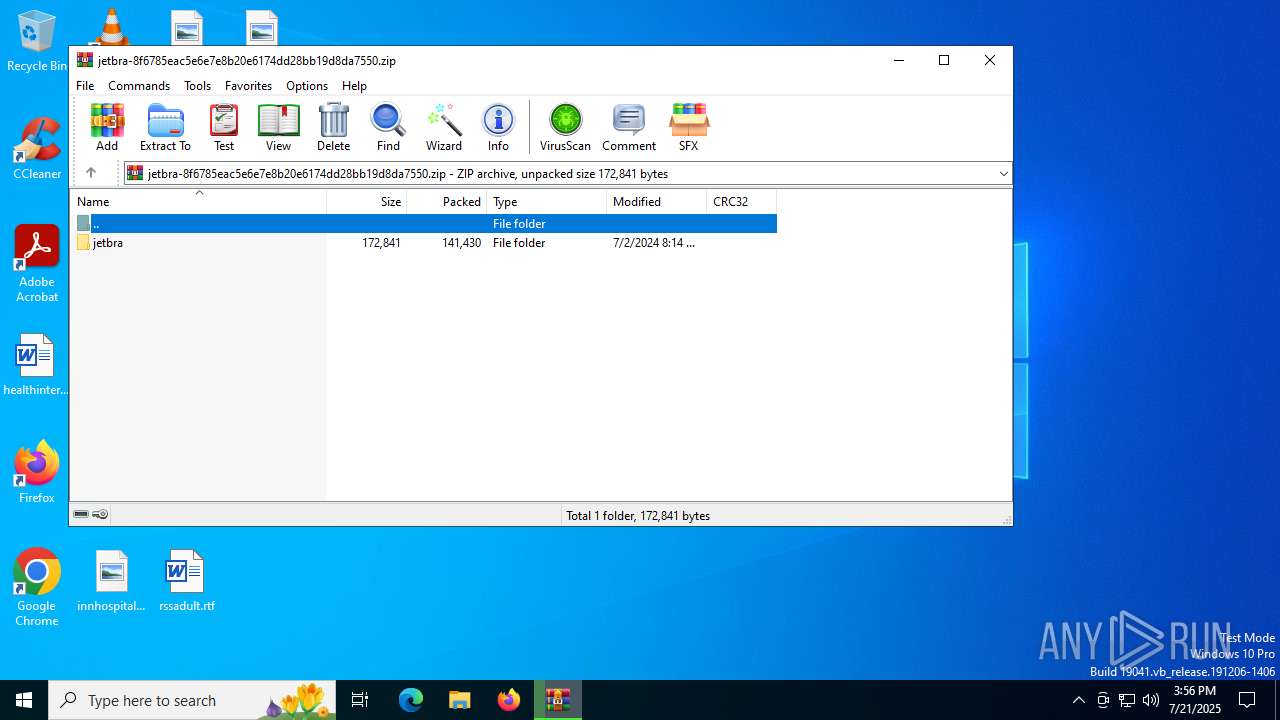
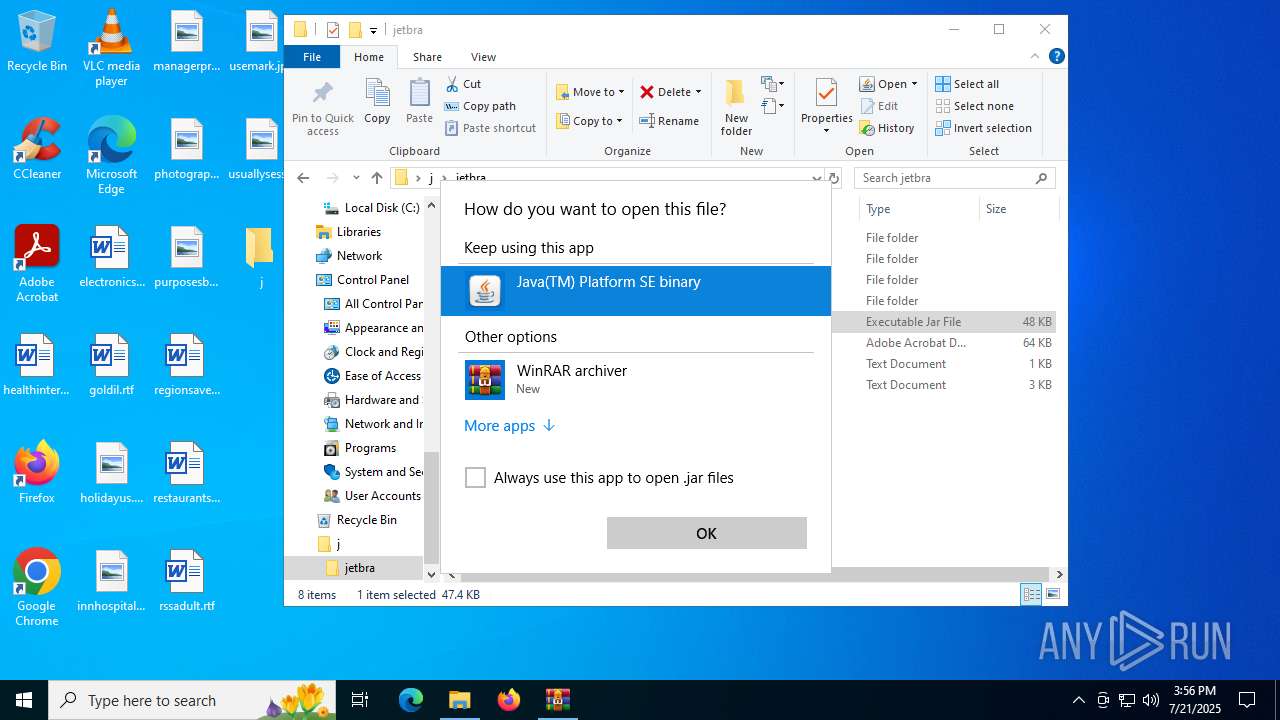
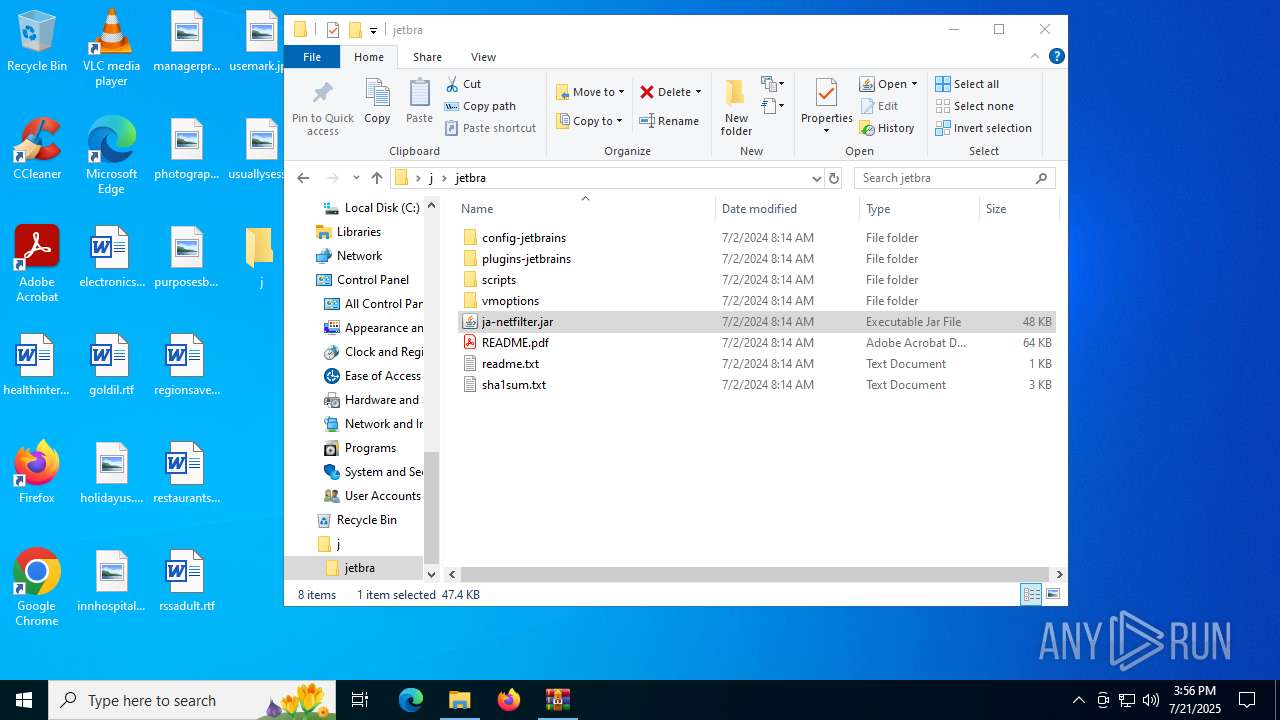
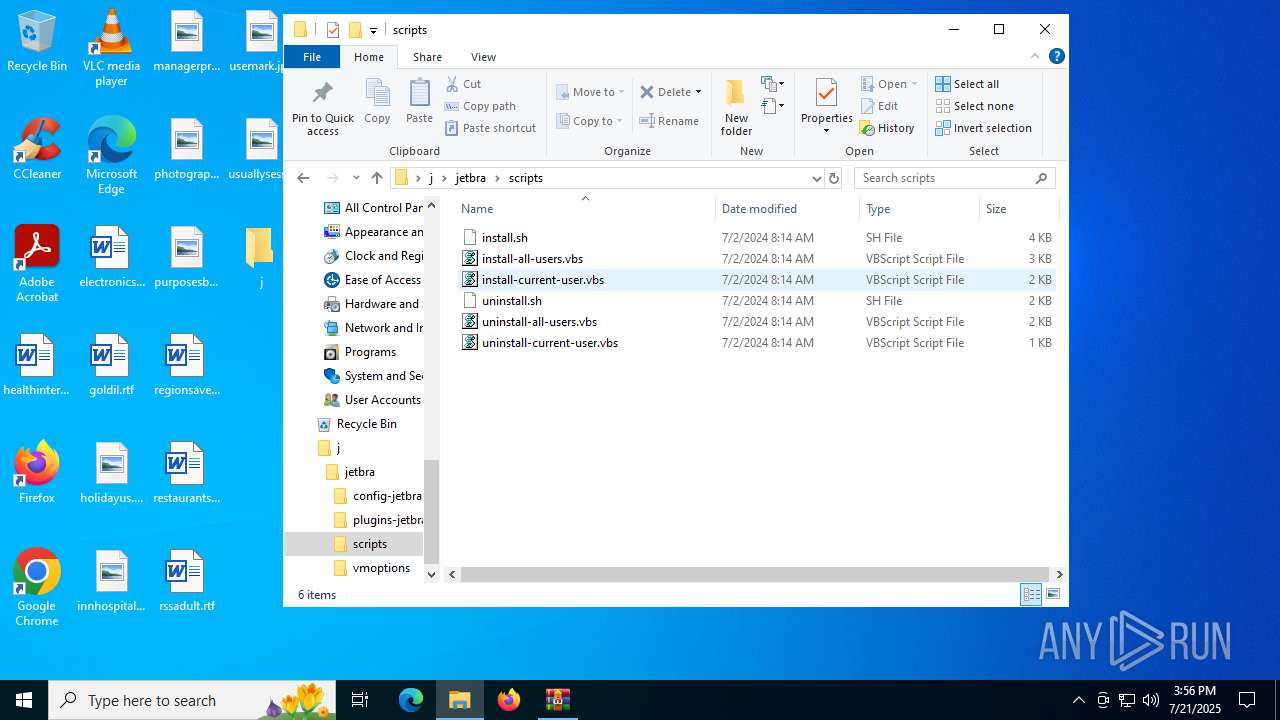
| File name: | jetbra-8f6785eac5e6e7e8b20e6174dd28bb19d8da7550.zip |
| Full analysis: | https://app.any.run/tasks/4b11b0f9-3fcb-4574-8264-c68d8d0790df |
| Verdict: | Malicious activity |
| Analysis date: | July 21, 2025, 15:55:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | A472D036E7B3519B43CA584D7A6A3B44 |
| SHA1: | 8F6785EAC5E6E7E8B20E6174DD28BB19D8DA7550 |
| SHA256: | D5D543EE8643264F50F1F30462DAAA80A4F9A07E11C0BC88B48AE0893786E865 |
| SSDEEP: | 6144:pwLS2qL5P6V2rzI95DmPyeLGzb7045+7lJzOzFI3+aop7iCaYcJ5E7:pFC2rzc59zb79+7lJz0 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3832)
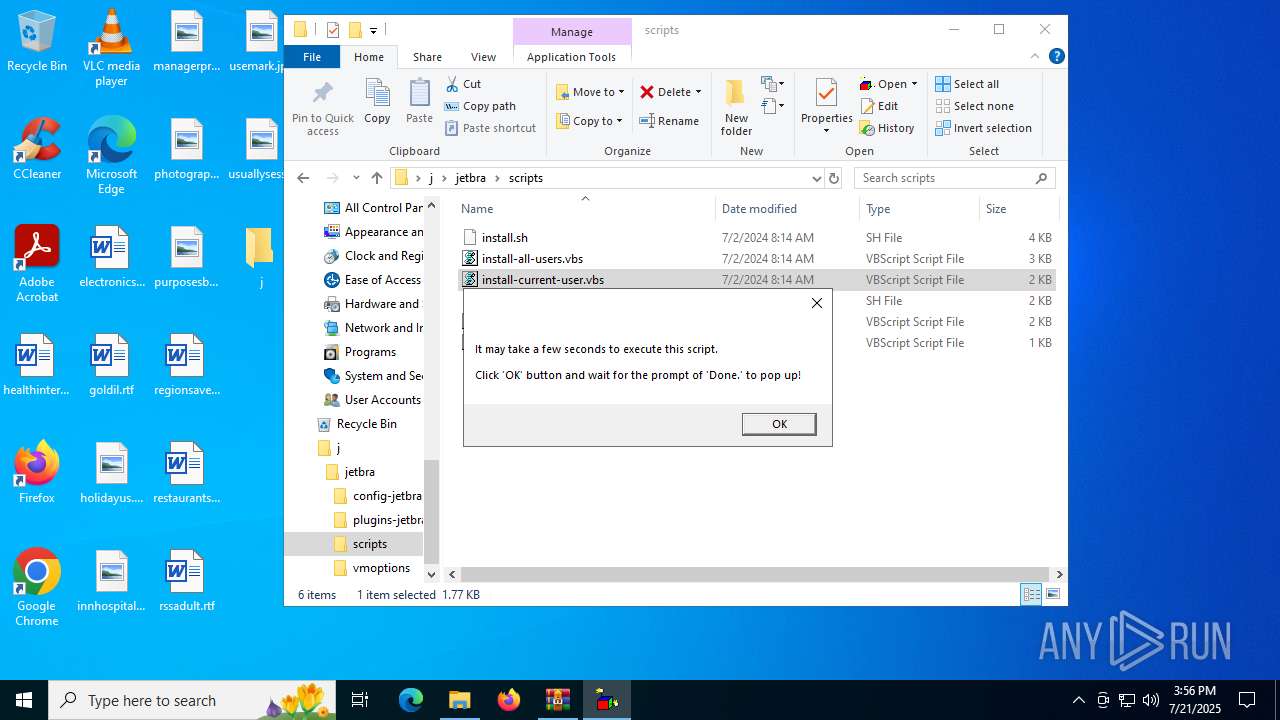
Opens a text file (SCRIPT)
- wscript.exe (PID: 7064)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7064)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 7064)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 7064)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 7064)
INFO
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4936)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4936)
Checks supported languages
- javaw.exe (PID: 4232)
Application based on Java
- javaw.exe (PID: 4232)
Create files in a temporary directory
- javaw.exe (PID: 4232)
Creates files in the program directory
- javaw.exe (PID: 4232)
Manual execution by a user
- wscript.exe (PID: 7064)
Matches regexp pattern (SCRIPT)
- wscript.exe (PID: 7064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:02 16:14:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | jetbra/ |
Total processes
142
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\jetbra-8f6785eac5e6e7e8b20e6174dd28bb19d8da7550.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4232 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\j\jetbra\ja-netfilter.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4936 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5744 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5980 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
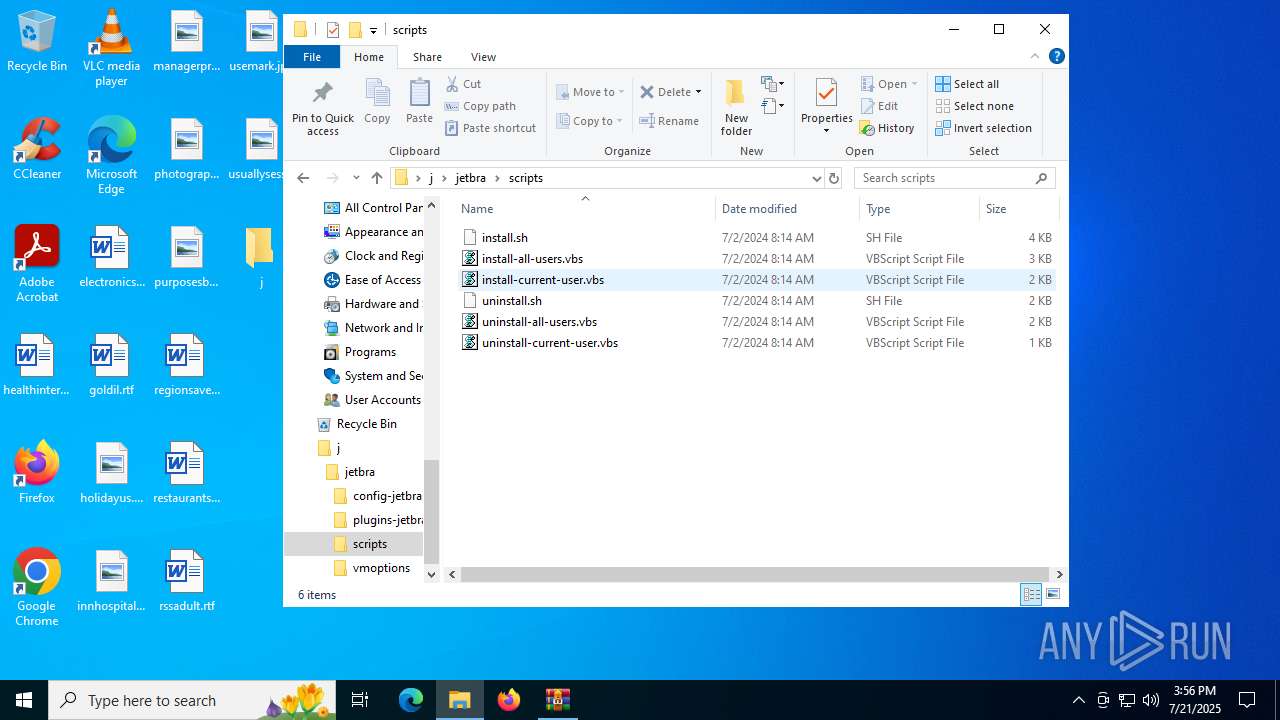
| 7064 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\j\jetbra\scripts\install-current-user.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
4 044
Read events
3 999
Write events
32
Delete events
13
Modification events
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\jetbra-8f6785eac5e6e7e8b20e6174dd28bb19d8da7550.zip | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
5
Suspicious files
1
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\plugins-jetbrains\dns.jar | java | |
MD5:4F3C516C1704A5569725246D57DD1AE7 | SHA256:D1150B1831B112B93D74A34A10CE6C11606E0D2255D532C29F91F1D92B40A552 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\config-jetbrains\dns.conf | text | |
MD5:0C730E2E849916568D7F519306777A95 | SHA256:B9BE9C700786B411395A66DEF0B259670074C32BCED59B33BE2DDD486ABCBE06 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\config-jetbrains\url.conf | text | |
MD5:FEA2BFBEDDA20D5AD9429F537E15F4CE | SHA256:88E1DCA8019AD412CF2C6FBD947A83786CFFC7B32F1EE35594D25D1F38FAE5F8 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\config-jetbrains\power.conf | text | |
MD5:D75324051D905F817C2B44584714038B | SHA256:3D3D1AED8D206C932BF3A94F4E1149C47C4276F6275A63BD3B0812DABF6C702C | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\ja-netfilter.jar | java | |
MD5:2FA1B1364515DCE93EB67C423B570DEB | SHA256:3ACC4E9D91793F6909458A4761B75B6DA45C8868E75DCA33C9FEC63659202995 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\scripts\uninstall-current-user.vbs | text | |
MD5:05E0D4CA0EFC751C1606FB4924251EF4 | SHA256:9D467BDAFBA79B8F253F3D9EB15D11B83CF92644912C497C44B0BF070BF6C653 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\plugins-jetbrains\url.jar | java | |
MD5:6B181E5B8255DB4CD9BEB1C6AF5F420E | SHA256:CE5A83AEE31153CCA30274AC94467B316EDEA8CB28ACF72F52F5A72D455B1B43 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\scripts\install.sh | text | |
MD5:A85F5496AF75C1475B68AFA7676445D2 | SHA256:43A5B6F4114459B8DEC929EF63F795A2114827F2340CEED05CDAE43B4C76C191 | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\scripts\uninstall.sh | text | |
MD5:DD3EF94B2C3632B798C25E9422E8BD2F | SHA256:5C408982BCACDCC0AF3F0FC9DE74D36E8051FBBCF71CBFA5E4DDC1CF3BD5425D | |||
| 3832 | WinRAR.exe | C:\Users\admin\Desktop\j\jetbra\vmoptions\datagrip.vmoptions | text | |
MD5:505D97467EA81E9B83A09A7738561AB7 | SHA256:F5A4F7AEC84EB0A45DD6ABE9D4BFD2096E4BAB775855F1447DC1BF8346C35B28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2528 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6840 | SIHClient.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6840 | SIHClient.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4580 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2528 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2528 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |