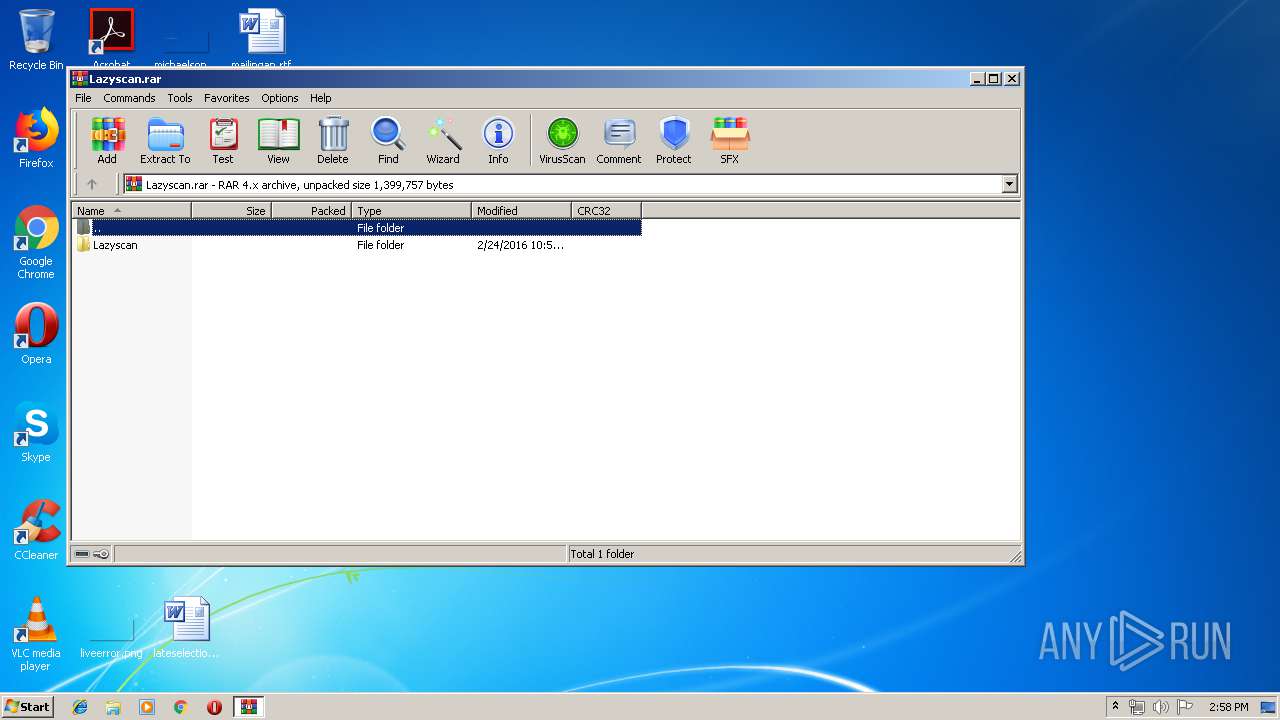
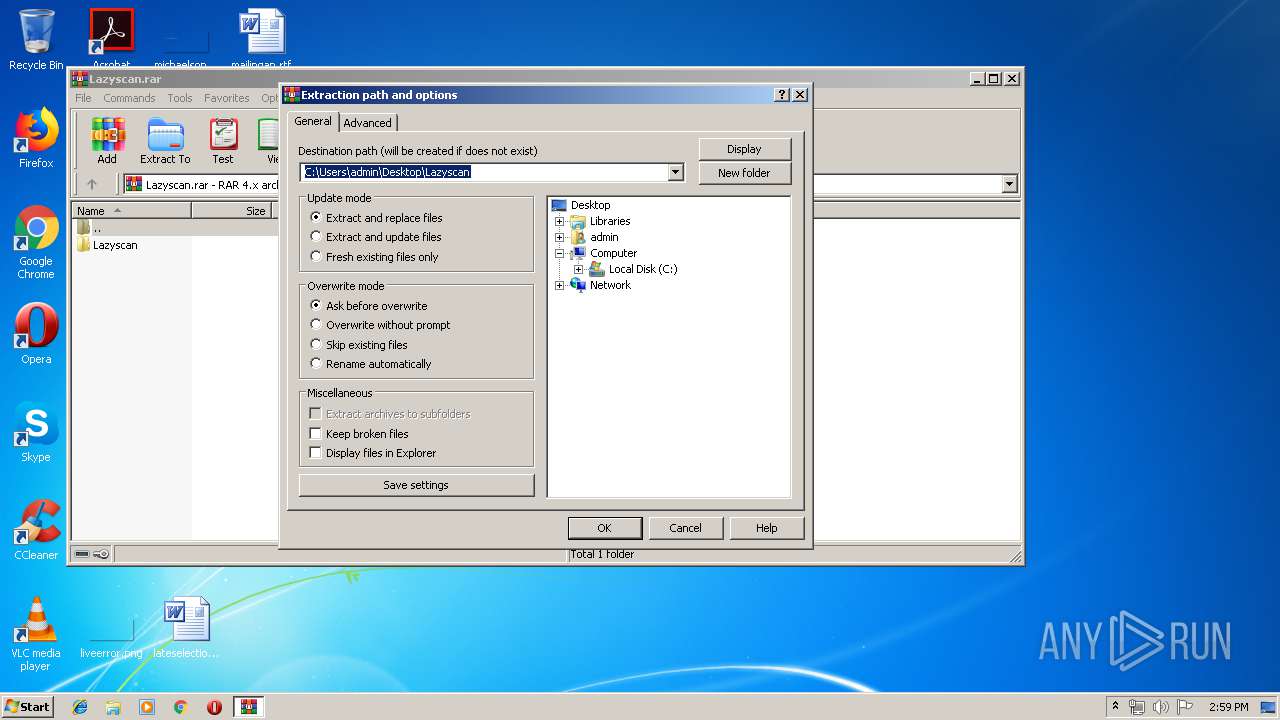
| File name: | Lazyscan.rar |
| Full analysis: | https://app.any.run/tasks/6dbba2a9-9160-4fea-8cf7-16dd0f8f3bff |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2019, 13:58:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 3E22BECD03E56CCB874A2732B4CE890A |
| SHA1: | 28221C6D07B4B2EF68E62072844ECA8DB49C0386 |
| SHA256: | D5CC93519A3C7CE6ED3D51EF1FA889D957A4E8FB95019EB5D06367214AC16275 |
| SSDEEP: | 24576:jGWZ/yK5XS1TgcuzPgoZszMMiHROYI/W7xPrR6dJW014EAiftUhhJLh9Zi50/DpD:P/yy6TeT6wHROY8W7drUTW0SotUh3kWZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 41804 |
|---|---|
| UncompressedSize: | 45453 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:01:16 15:58:15 |
| PackingMethod: | Normal |
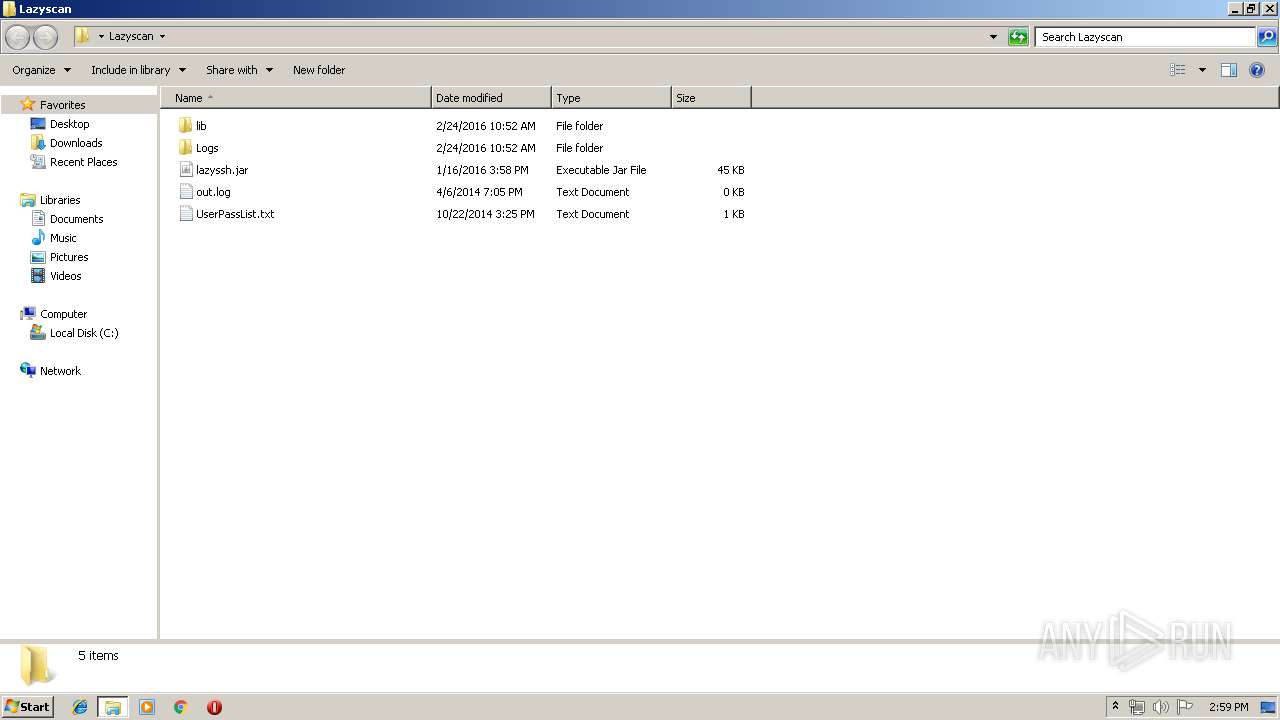
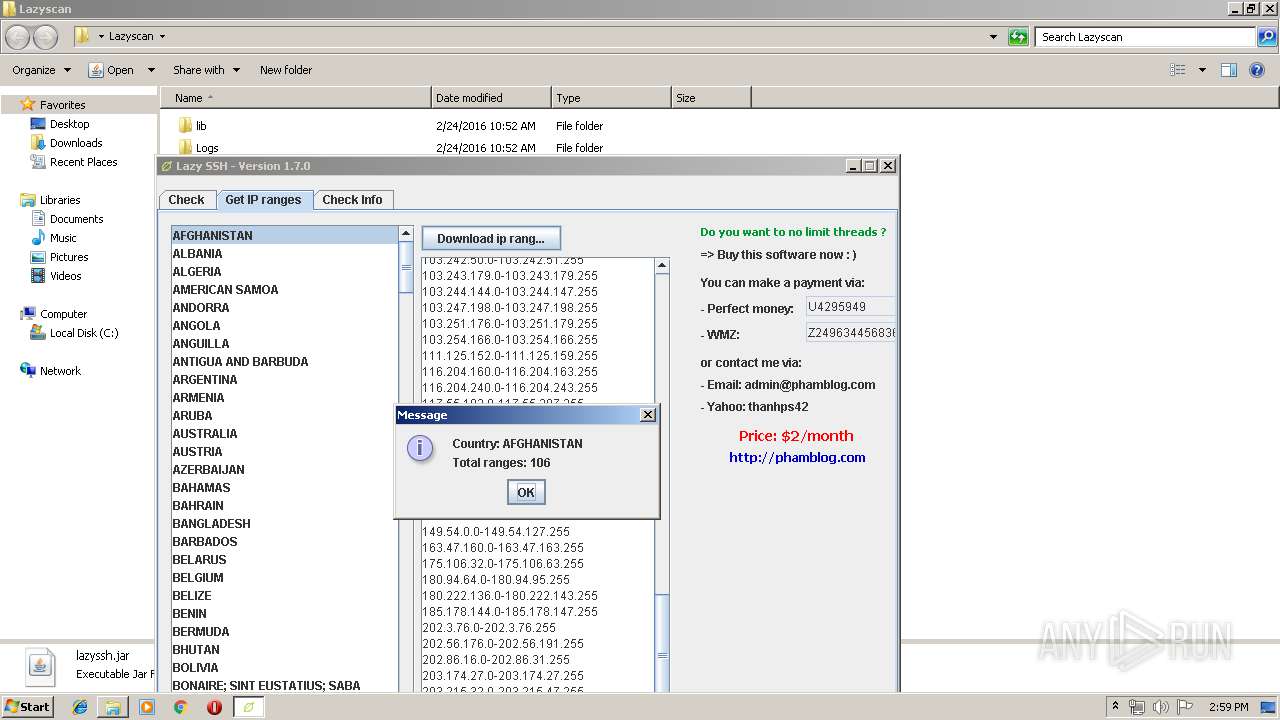
| ArchivedFileName: | Lazyscan\lazyssh.jar |
Total processes
34
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
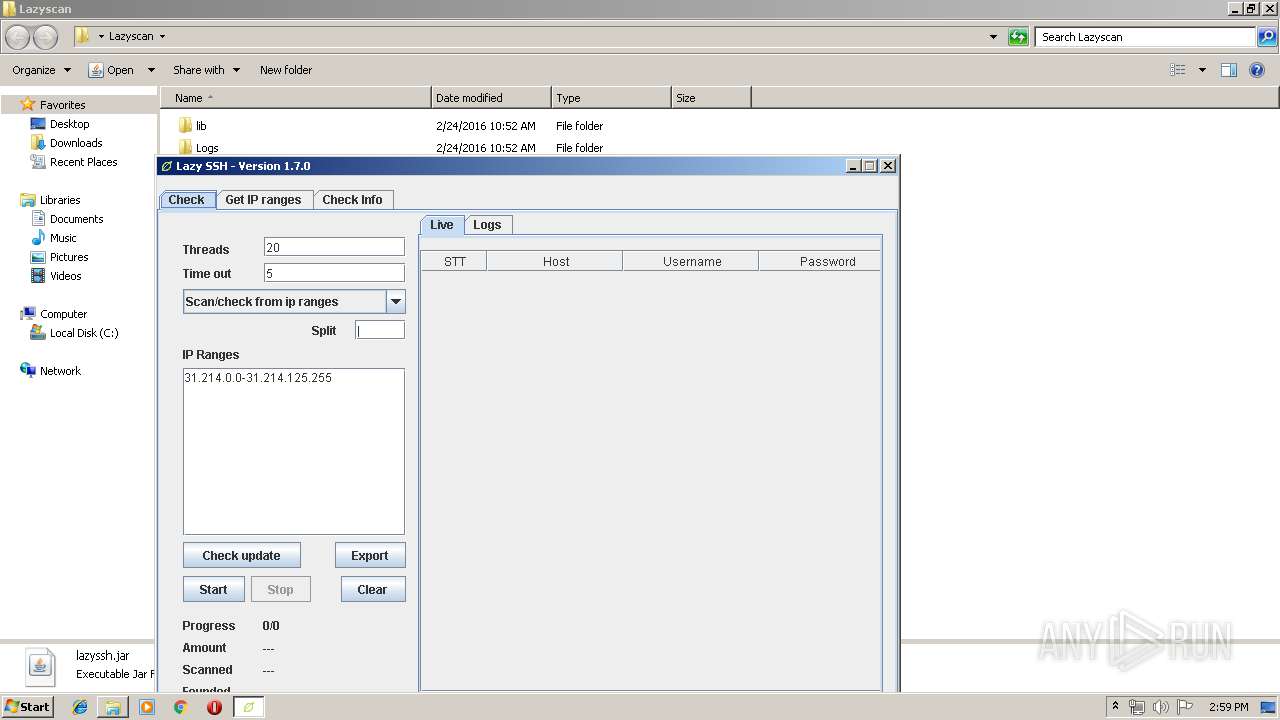
| 1688 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Lazyscan\lazyssh.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2816 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Lazyscan.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
359
Read events
337
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Lazyscan.rar | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2816) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
3
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\lazyssh.jar | compressed | |
MD5:— | SHA256:— | |||
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\Logs\LIVE.txt | text | |
MD5:— | SHA256:— | |||
| 1688 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\Logs\WRONG.txt | text | |
MD5:— | SHA256:— | |||
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\lib\mysql-connector-java-5.1.33-bin.jar | java | |
MD5:— | SHA256:— | |||
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\UserPassList.txt | text | |
MD5:— | SHA256:— | |||
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\lib\zip4j_1.3.2.jar | java | |
MD5:63EBDE69F7BE7EDBDA8DC4BC7A4580A4 | SHA256:92524AA1BF716F1D15E75FB66C2212EE903E118677CA625506F94487628317F7 | |||
| 2816 | WinRAR.exe | C:\Users\admin\Desktop\Lazyscan\lib\jsch-0.1.51.jar | java | |
MD5:DE3A2B0D03295F167FEA1904939443CF | SHA256:C65E3BD079EB46B0FDBD444E249252C647B0F0727D8B73B58D94D24097893E6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
61
DNS requests
1
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1688 | javaw.exe | GET | 200 | 149.210.169.168:80 | http://services.ce3c.be/ciprg/?countrys=AFGHANISTAN%2C&format=by+input&format2=%7Bstartip%7D-%7Bendip%7D%0D%0A | NL | text | 3.00 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1688 | javaw.exe | 31.214.0.10:22 | — | Mada Communications CJSC | KW | suspicious |
1688 | javaw.exe | 31.214.0.12:22 | — | Mada Communications CJSC | KW | suspicious |
1688 | javaw.exe | 31.214.0.11:22 | — | Mada Communications CJSC | KW | suspicious |
1688 | javaw.exe | 31.214.0.15:22 | — | Mada Communications CJSC | KW | suspicious |
1688 | javaw.exe | 31.214.0.8:22 | — | Mada Communications CJSC | KW | unknown |
1688 | javaw.exe | 31.214.0.6:22 | — | Mada Communications CJSC | KW | suspicious |
1688 | javaw.exe | 31.214.0.3:22 | — | Mada Communications CJSC | KW | suspicious |
1688 | javaw.exe | 149.210.169.168:80 | services.ce3c.be | Transip B.V. | NL | suspicious |
1688 | javaw.exe | 31.214.0.0:22 | — | Mada Communications CJSC | KW | unknown |
1688 | javaw.exe | 31.214.0.1:22 | — | Mada Communications CJSC | KW | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
services.ce3c.be |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
1688 | javaw.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |