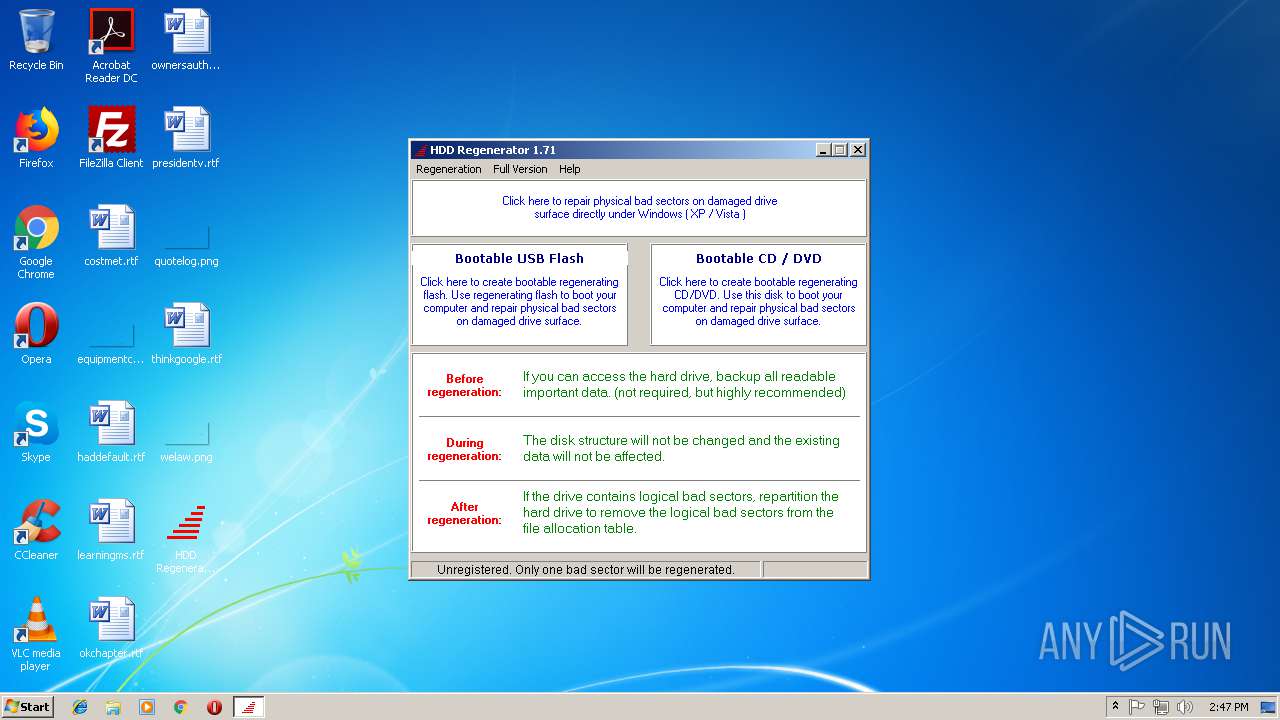
| File name: | HDD Regenerator 1.71 Portable.exe |
| Full analysis: | https://app.any.run/tasks/c974efe7-26f6-4a64-b857-179a140ce055 |
| Verdict: | Suspicious activity |
| Analysis date: | October 07, 2018, 13:47:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 22BB5551B9D214193B3EEA25D748E58D |
| SHA1: | 82E6AE5A6B1A2D91AAC158CF99E9C48B1E62BADF |
| SHA256: | D5C0C3B023B3E8338D0EC3EC681764E6EDCC8BF045D834B6D0CDFDC3029DAEC8 |
| SSDEEP: | 98304:y9fVTVj4xcMjUsJusHSfZAYFxKboz/GprqXIWEvWm++XIVgM2O3ynC8vKGPZf8+r:SVTV67Z4J2MKEGQY7WRAIHLyn5U5C |
MALICIOUS
Application was dropped or rewritten from another process
- HDD Regenerator.exe (PID: 2228)
- HDD Regenerator.exe (PID: 4076)
- HDD Regenerator.exe (PID: 3416)
Loads dropped or rewritten executable
- HDD Regenerator.exe (PID: 2228)
SUSPICIOUS
Executable content was dropped or overwritten
- HDD Regenerator 1.71 Portable.exe (PID: 1644)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.3) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Win32 Executable Watcom C++ (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:09:16 16:17:44+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 81920 |
| InitializedDataSize: | 22528 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Sep-2008 14:17:44 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 16-Sep-2008 14:17:44 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00014000 | 0x00013A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.48361 |
.data | 0x00015000 | 0x00008000 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.93186 |
.idata | 0x0001D000 | 0x00002000 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.78952 |
.rsrc | 0x0001F000 | 0x00004000 | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.4522 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.06643 | 831 | Latin 1 / Western European | Russian - Russia | RT_MANIFEST |
7 | 3.24143 | 556 | Latin 1 / Western European | Russian - Russia | RT_STRING |
8 | 3.28574 | 946 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 3.04375 | 530 | Latin 1 / Western European | Russian - Russia | RT_STRING |
10 | 3.15563 | 638 | Latin 1 / Western European | Russian - Russia | RT_STRING |
100 | 1.69546 | 20 | Latin 1 / Western European | Process Default Language | RT_GROUP_ICON |
101 | 4.19099 | 2998 | Latin 1 / Western European | Russian - Russia | RT_BITMAP |
ASKNEXTVOL | 3.42606 | 642 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
GETPASSWORD1 | 3.33783 | 310 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
LICENSEDLG | 3.1404 | 232 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
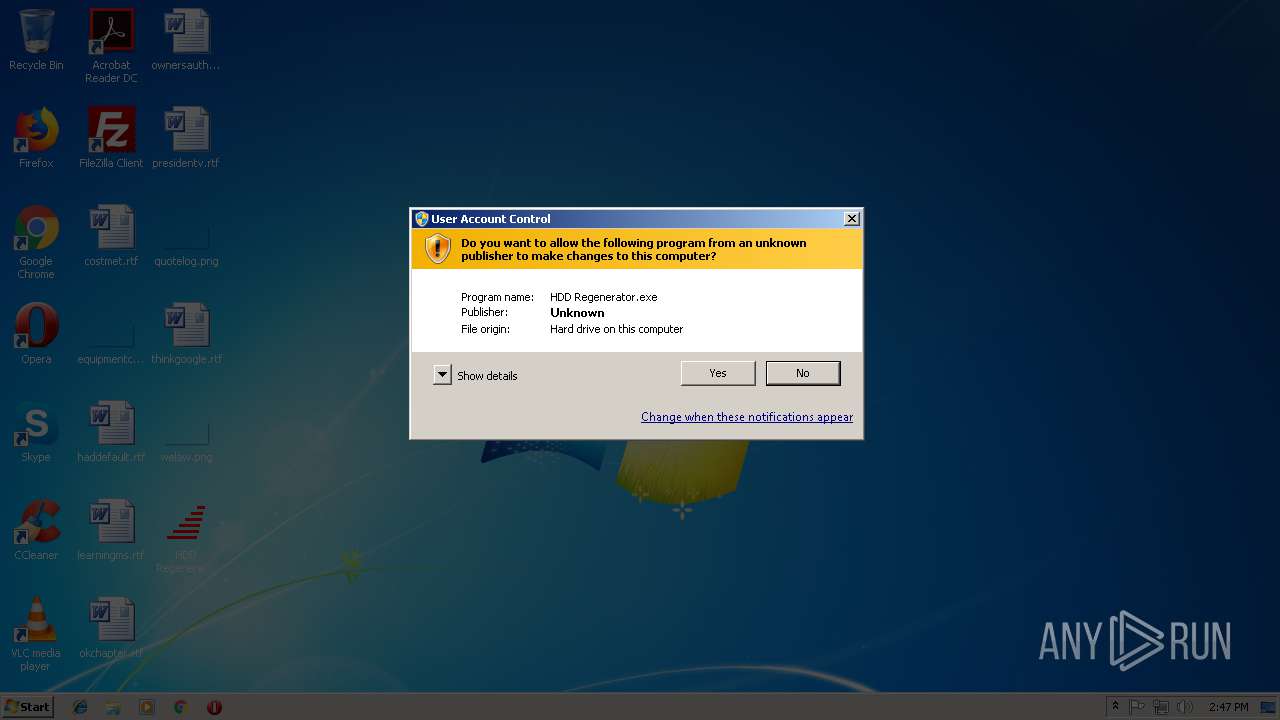
| 1644 | "C:\Users\admin\Desktop\HDD Regenerator 1.71 Portable.exe" | C:\Users\admin\Desktop\HDD Regenerator 1.71 Portable.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2228 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe | — | HDD Regenerator.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
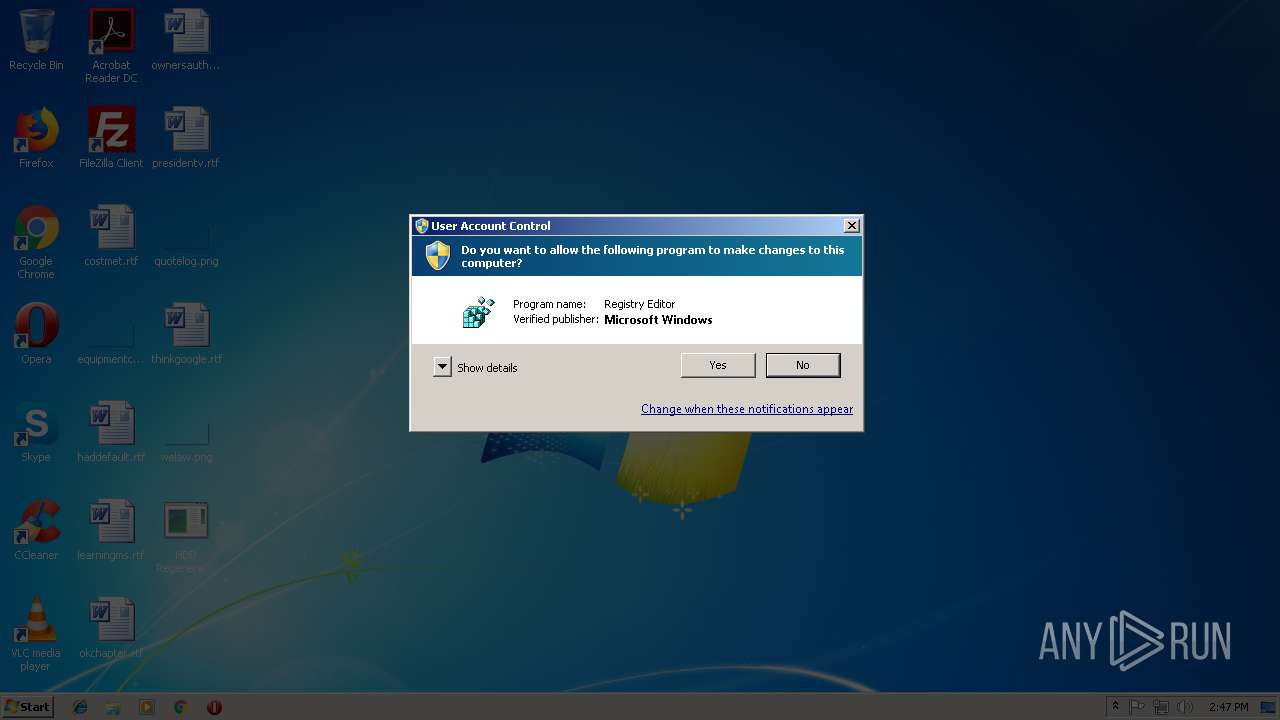
| 2832 | "C:\Windows\regedit.exe" /s Reg.reg | C:\Windows\regedit.exe | HDD Regenerator 1.71 Portable.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3416 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe | HDD Regenerator 1.71 Portable.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3604 | "C:\Windows\regedit.exe" /s Reg.reg | C:\Windows\regedit.exe | — | HDD Regenerator 1.71 Portable.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe | — | HDD Regenerator 1.71 Portable.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
427
Read events
410
Write events
17
Delete events
0
Modification events
| (PID) Process: | (1644) HDD Regenerator 1.71 Portable.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1644) HDD Regenerator 1.71 Portable.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RFC1156Agent\CurrentVersion\Parameters |
| Operation: | write | Name: | TrapPollTimeMilliSecs |
Value: 15000 | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Licenses |
| Operation: | write | Name: | {R7C0DB872A3F777C0} |
Value: AA246D5D | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Licenses |
| Operation: | write | Name: | {K7C0DB872A3F777C0} |
Value: 9F03CB01331C1FFFFFFFFFE7FDC6037EA048EB2DD9F0789FE6E132AA246D5DEB74FCCEC3A30333FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF9FE6E132331C1FFFFFFFFFE7FDC6037EA048EB2DD9F0789FE6E132AA246D5DEB74FCCEC3A30333FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF9FE6E1320000 | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{1B19CC9A-61D0-E48F-67C4-132F9066E59D}\InprocServer32 |
| Operation: | write | Name: | Assembly |
Value: Microsoft.Office.Interop.Word, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{1B19CC9A-61D0-E48F-67C4-132F9066E59D}\InprocServer32 |
| Operation: | write | Name: | Class |
Value: Microsoft.Office.Interop.Word.ParagraphFormatClass | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{1B19CC9A-61D0-E48F-67C4-132F9066E59D}\InprocServer32 |
| Operation: | write | Name: | RuntimeVersion |
Value: v2.0.50727 | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{1B19CC9A-61D0-E48F-67C4-132F9066E59D}\InprocServer32\14.0.0.0 |
| Operation: | write | Name: | Assembly |
Value: Microsoft.Office.Interop.Word, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C | |||
| (PID) Process: | (2228) HDD Regenerator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{1B19CC9A-61D0-E48F-67C4-132F9066E59D}\InprocServer32\14.0.0.0 |
| Operation: | write | Name: | Class |
Value: Microsoft.Office.Interop.Word.ParagraphFormatClass | |||
Executable files
5
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Readme.txt | text | |
MD5:21DACD13CF89A2314FBA58CF39EE2A48 | SHA256:6A87A4CAD3A30BFD287587D335CCD53B6D0A9AB853783943B55B6BDCB9BC5355 | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\hddreg.exe | executable | |
MD5:4B7FF91C170C4ABCC05D7528FE4B61DC | SHA256:C41D733A5E4BC4133AEA1F0FC1B0356A1403CDD195EC8D7576769D0552AEEB49 | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\BORLNDMM.DLL | executable | |
MD5:F585E57EF674643E2AEFBDA6DEBE2854 | SHA256:234114DFDEAC2F382CD50611B1F449395A6CE83CCB3D028EF64263C465DF7B6A | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Reg.reg | text | |
MD5:96EB8F2E950CE11D2E749373ACE420F2 | SHA256:C474CAF4500D9D0894B8201E6CA9EF7576AFA63AB7E504193987E851B033FED3 | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\DSCK.TR | executable | |
MD5:6E664095A35E7D6DA7FA4C00AF464ABC | SHA256:8B573DCCD3BF8A85AC2AE31FDC64EA84765F5407F1839BBCEC655D2D2C635668 | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\HDD Regenerator.exe | executable | |
MD5:6DFE1AAF744145E32C06BECB61D94108 | SHA256:2808BB8B825D3723F65F0DAB746B8DF6E265E14011A222FB69E374D6D93426C8 | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\UnReg.reg | text | |
MD5:E23E29980D4C755C6428C6CD420B5AE5 | SHA256:F081677D7B1863421ECC88361F4A20C3E8668DC22ECF1325D8EC63C2BF9187FB | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\License.txt | text | |
MD5:E8CB68ED28F292A00F395799CC489C8E | SHA256:5982FBFD79B45DB61DED940799AF9B9F3D06BD0FA9F1A56EAE0E771F69C44022 | |||
| 1644 | HDD Regenerator 1.71 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CC3280MT.DLL | executable | |
MD5:BFD9A3CEB66B0D3A651114A06C670E86 | SHA256:A21078F4CF335DD958323266E00F49FE20D43455CEF96EE581966F51F246E35E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|