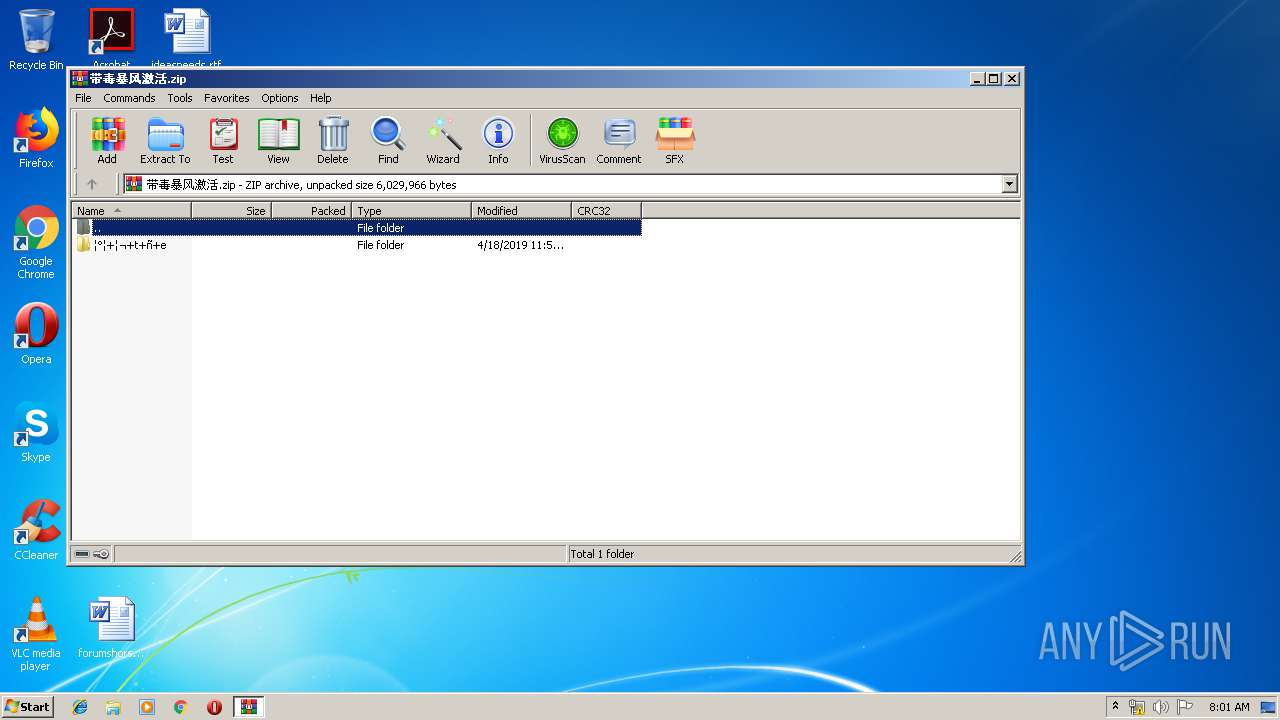
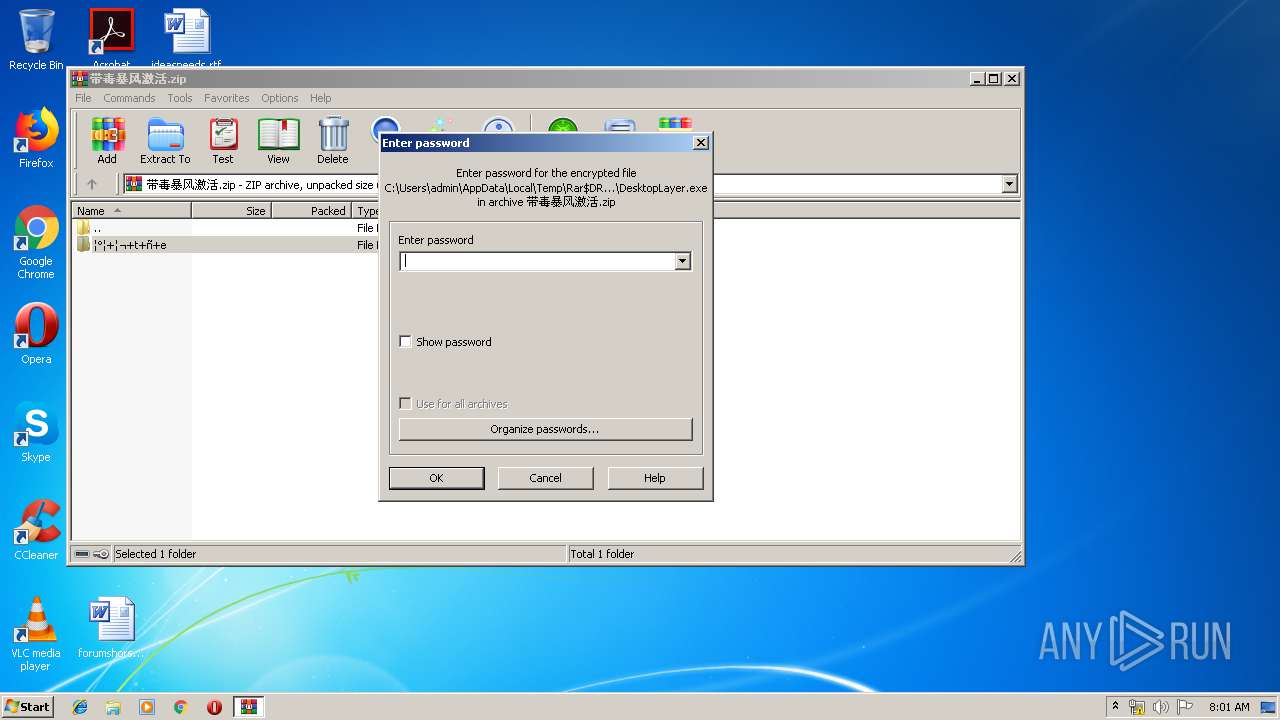
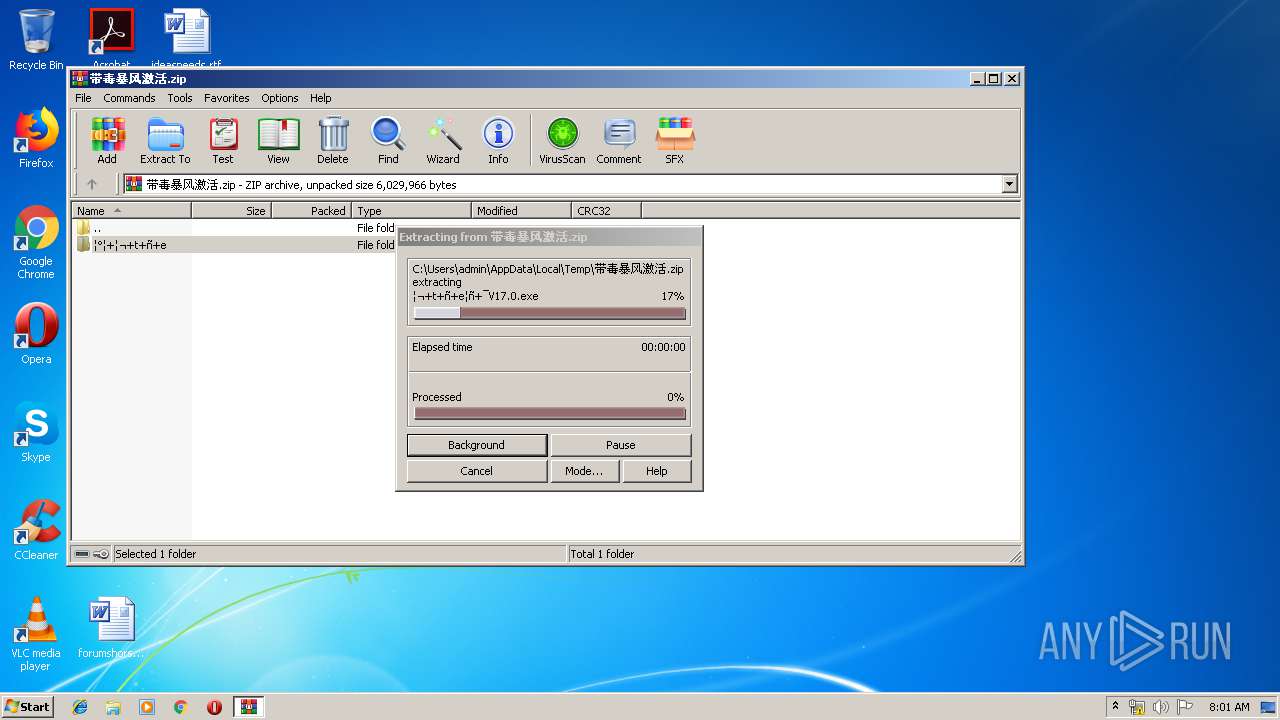
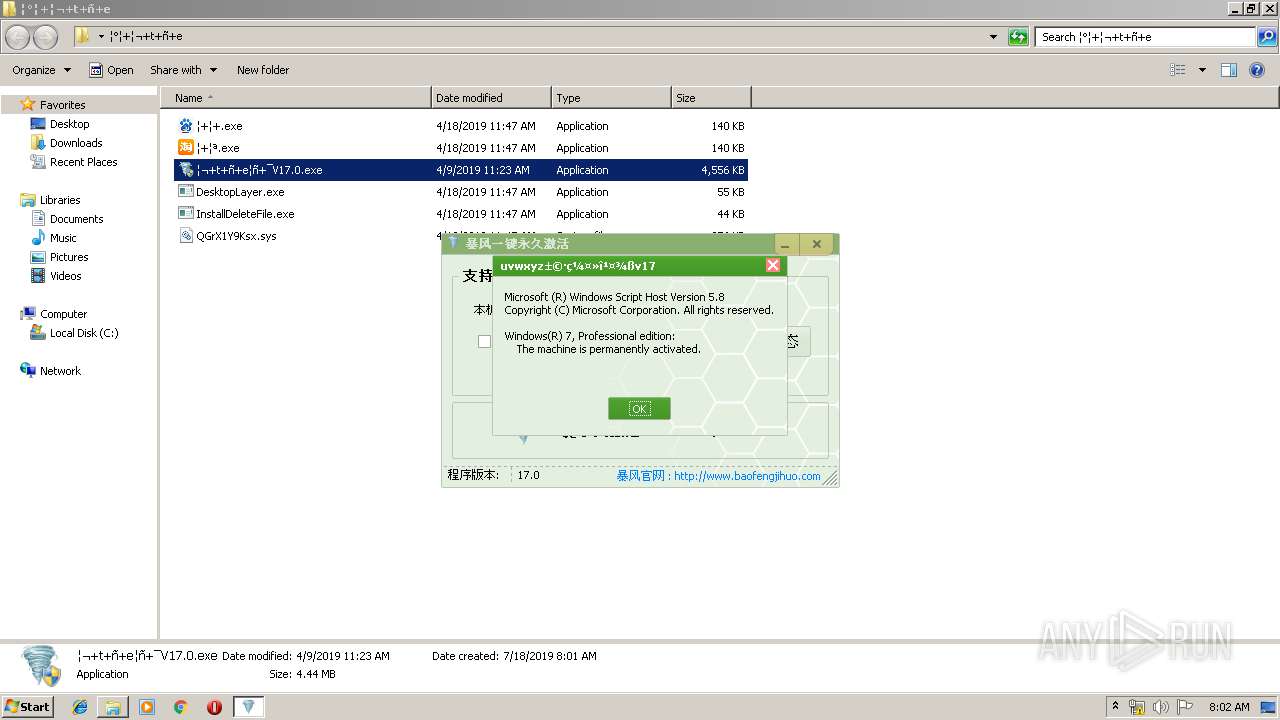
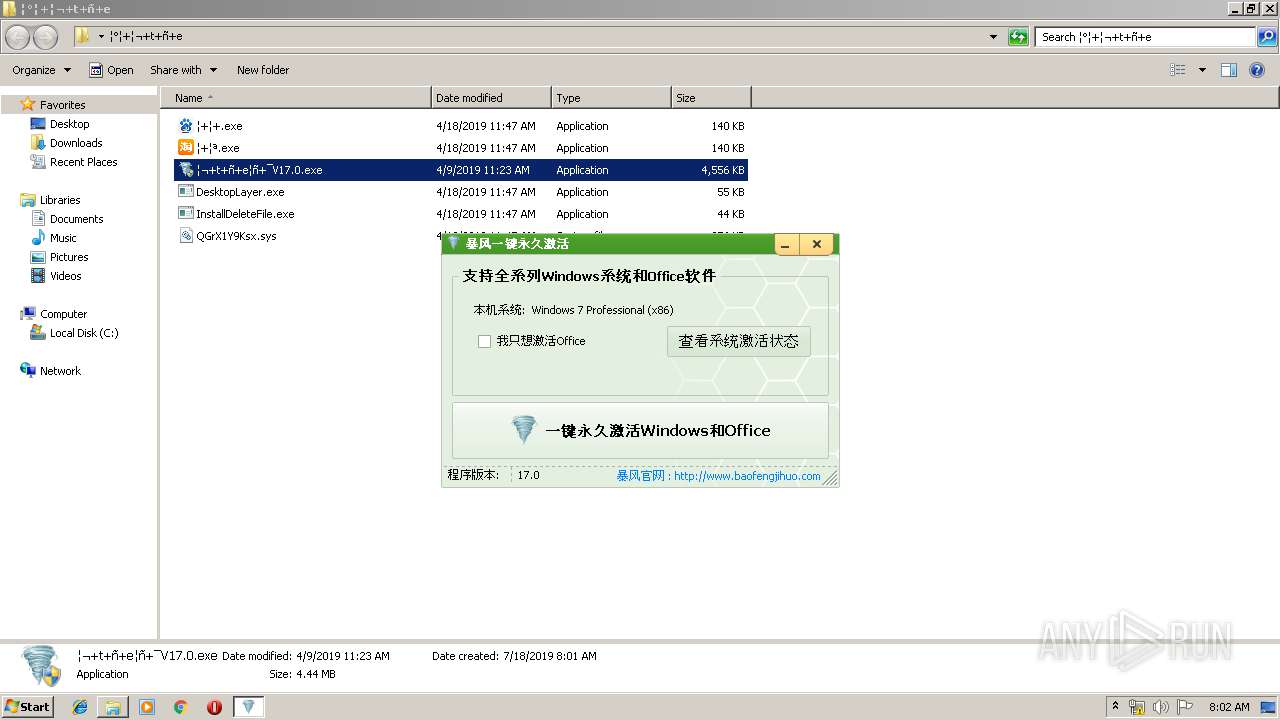
| File name: | 带毒暴风激活.zip |
| Full analysis: | https://app.any.run/tasks/b4e0e65b-82de-4a8b-8f7d-9e1ec65c5c41 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 07:00:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 348A01DC8257D9CBBFADAAE5F7E6ACF0 |
| SHA1: | A05EB641E25CAEAC7B6C17C9115FCBCA311C290B |
| SHA256: | D5B2028332CFA7C6ABD45DCC02310443C9ADA7FF61FB8C9BEDE910892E55DFD6 |
| SSDEEP: | 98304:ZQ0zOWINi5Ua0ozEW5KujzMwChFgcbr0SOFtBPjAaEPx8VX:K7/owW5KujQ1F74TFXPcnPuR |
MALICIOUS
Application was dropped or rewritten from another process
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0Srv.exe (PID: 2792)
- DesktopLayer.exe (PID: 3976)
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
- lmnopqrstuvwxyz1.exe (PID: 2680)
- klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe (PID: 1376)
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
- FavriteAdd.exe (PID: 3424)
- ghijklmnopqrstuvwxyz1227Favrite.exe (PID: 3392)
- vwxyz73351a00c84c94d3.exe (PID: 3968)
- DelNsisSelf.exe (PID: 3480)
- Del24E8.tmp (PID: 2476)
- IELink.exe (PID: 2880)
- ASBarBroker.exe (PID: 2632)
- SppExtComObjPatcher.exe (PID: 3496)
- KMSService.exe (PID: 3804)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 4064)
Loads dropped or rewritten executable
- vwxyz73351a00c84c94d3.exe (PID: 3968)
- OSPPSVC.EXE (PID: 4020)
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 4020)
Changes Image File Execution Options
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3008)
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0Srv.exe (PID: 2792)
- ¦¬+t+ñ+e¦ñ+¯V17.0.exe (PID: 3084)
- ghijklmnopqrstuvwxyz1227Favrite.exe (PID: 3392)
- klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe (PID: 1376)
- vwxyz73351a00c84c94d3.exe (PID: 3968)
- DelNsisSelf.exe (PID: 3480)
Creates files in the program directory
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0Srv.exe (PID: 2792)
- iexplore.exe (PID: 4064)
- vwxyz73351a00c84c94d3.exe (PID: 3968)
Starts itself from another location
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0Srv.exe (PID: 2792)
- DelNsisSelf.exe (PID: 3480)
Creates files in the user directory
- lmnopqrstuvwxyz1.exe (PID: 2680)
- FavriteAdd.exe (PID: 3424)
Starts Internet Explorer
- DesktopLayer.exe (PID: 3976)
Low-level read access rights to disk partition
- vwxyz73351a00c84c94d3.exe (PID: 3968)
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
Executed as Windows Service
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
- KMSService.exe (PID: 3804)
- SppExtComObjPatcher.exe (PID: 3496)
Uses WMIC.EXE to obtain a system information
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
Starts CMD.EXE for commands execution
- klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe (PID: 1376)
- FavriteAdd.exe (PID: 3424)
- Del24E8.tmp (PID: 2476)
Starts CMD.EXE for self-deleting
- klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe (PID: 1376)
Starts application with an unusual extension
- DelNsisSelf.exe (PID: 3480)
Uses NETSH.EXE for network configuration
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
Creates a software uninstall entry
- vwxyz73351a00c84c94d3.exe (PID: 3968)
Creates COM task schedule object
- vwxyz73351a00c84c94d3.exe (PID: 3968)
Uses TASKKILL.EXE to kill process
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
Creates files in the Windows directory
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
Executes scripts
- uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe (PID: 752)
Removes files from Windows directory
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
Reads Environment values
- ¼¤»î¹¤¾ß2.exe (PID: 2504)
INFO
Manual execution by user
- ¦¬+t+ñ+e¦ñ+¯V17.0.exe (PID: 2892)
- ¦¬+t+ñ+e¦ñ+¯V17.0.exe (PID: 3084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:18 18:47:12 |
| ZipCRC: | 0x40c57347 |
| ZipCompressedSize: | 54767 |
| ZipUncompressedSize: | 56320 |
| ZipFileName: | ???????缤??/DesktopLayer.exe |
Total processes
98
Monitored processes
39
Malicious processes
6
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | netsh firewall delete allowedprogram "C:\Windows\KMSService.exe" | C:\Windows\system32\netsh.exe | — | uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
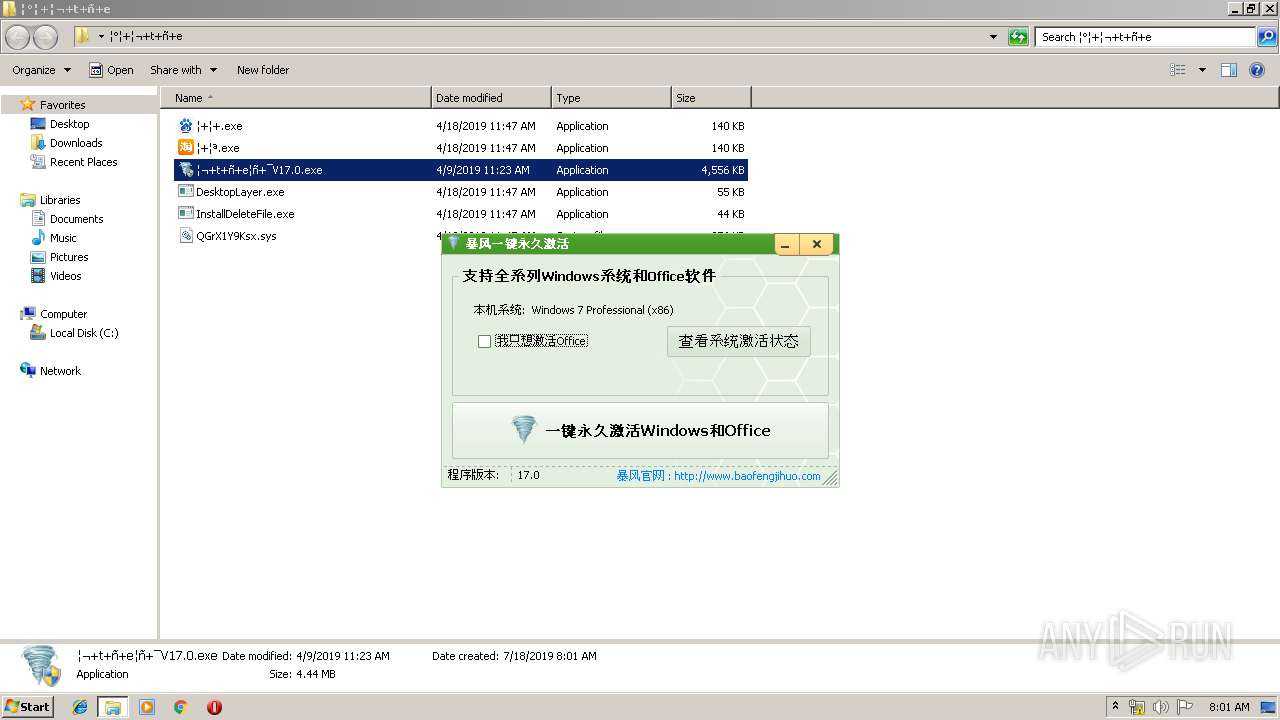
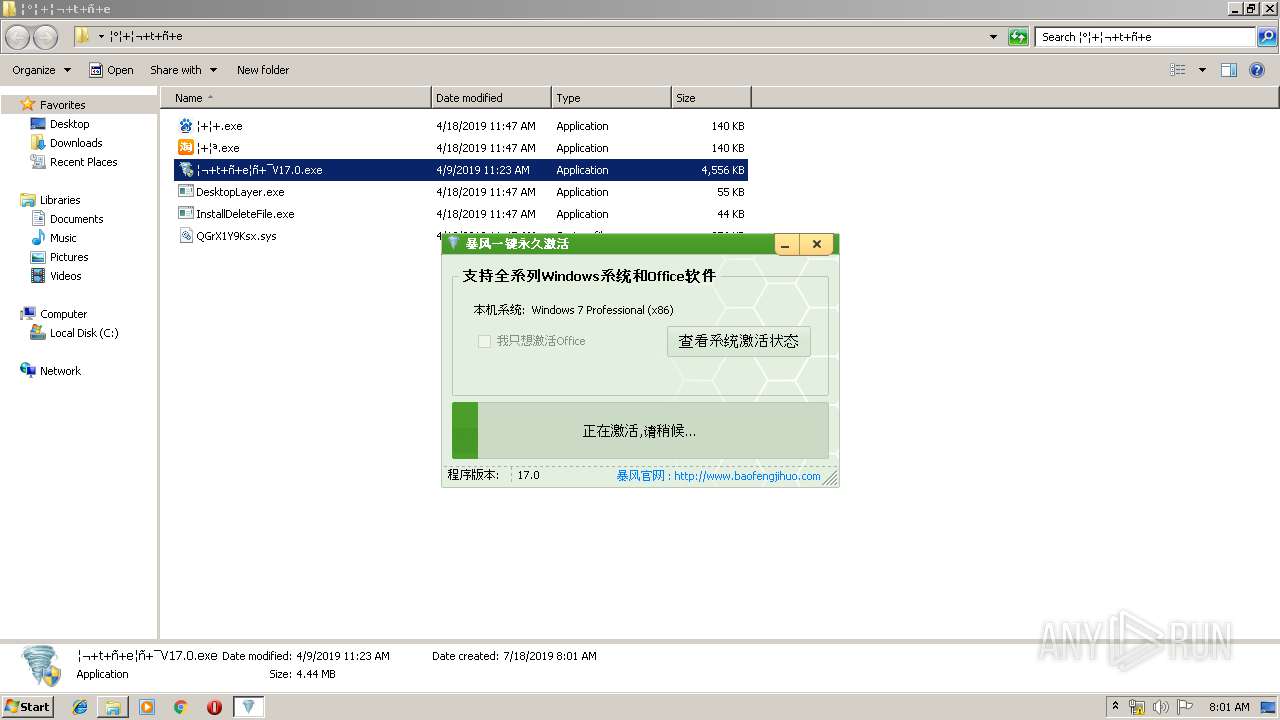
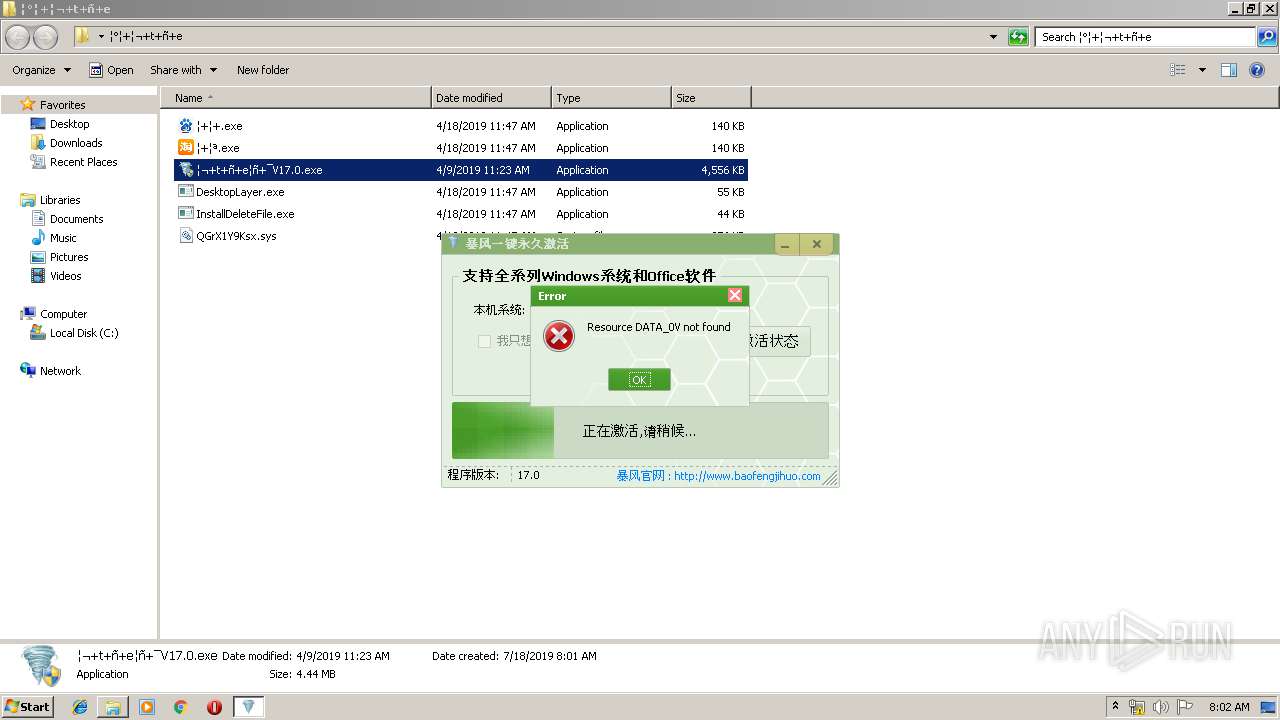
| 752 | "C:\Users\admin\AppData\Local\Temp\uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe" | C:\Users\admin\AppData\Local\Temp\uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | ¦¬+t+ñ+e¦ñ+¯V17.0.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 暴风一键激活工具 Exit code: 0 Version: 16.0.0.0 Modules
| |||||||||||||||
| 788 | taskkill /im "KMSService.exe" /t /f | C:\Windows\system32\taskkill.exe | — | uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1376 | "C:\Users\admin\AppData\Local\Temp\klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe" | C:\Users\admin\AppData\Local\Temp\klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe | ¦¬+t+ñ+e¦ñ+¯V17.0.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1604 | wmic path SoftwareLicensingService where version='6.1.7601.17514' call SetVLActivationTypeEnabled 2 | C:\Windows\System32\Wbem\wmic.exe | — | uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 44028 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | netsh firewall add allowedprogram "C:\Windows\KMSService.exe" "vlmcsd" | C:\Windows\system32\netsh.exe | — | uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2340 | cscript C:\Windows\system32\slmgr.vbs -xpr | C:\Windows\system32\cscript.exe | — | uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2472 | taskkill /im "osppsvc.exe" /t /f | C:\Windows\system32\taskkill.exe | — | uvwxyz±©·ç¼¤»î¹¤¾ßV17.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Users\admin\AppData\Local\Temp\Del24E8.tmp" /pcmd="c:\users\admin\appdata\local\temp\ghijklmnopqrstuvwxyz1227favrite.exe" /cmd="C:\Users\admin\Desktop\DelNsisSelf.exe" /ppid=3392 /pid=3480 | C:\Users\admin\AppData\Local\Temp\Del24E8.tmp | — | DelNsisSelf.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2504 | C:\Users\admin\AppData\Local\Temp\¼¤»î¹¤¾ß2.exe | C:\Users\admin\AppData\Local\Temp\¼¤»î¹¤¾ß2.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
Total events
2 319
Read events
1 986
Write events
331
Delete events
2
Modification events
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\带毒暴风激活.zip | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
35
Suspicious files
4
Text files
20
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3008.29236\¦°¦+¦¬+t+ñ+e\¦¬+t+ñ+e¦ñ+¯V17.0.exe | — | |
MD5:— | SHA256:— | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3008.29236\¦°¦+¦¬+t+ñ+e\¦+¦ª.exe | — | |
MD5:— | SHA256:— | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3008.29236\¦°¦+¦¬+t+ñ+e\¦+¦+.exe | — | |
MD5:— | SHA256:— | |||
| 3084 | ¦¬+t+ñ+e¦ñ+¯V17.0.exe | C:\Users\admin\AppData\Local\Temp\lmnopqrstuvwxyz1.exe | executable | |
MD5:— | SHA256:— | |||
| 3084 | ¦¬+t+ñ+e¦ñ+¯V17.0.exe | C:\Users\admin\AppData\Local\Temp\klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe | executable | |
MD5:— | SHA256:— | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3008.29236\¦°¦+¦¬+t+ñ+e\InstallDeleteFile.exe | executable | |
MD5:— | SHA256:— | |||
| 3392 | ghijklmnopqrstuvwxyz1227Favrite.exe | C:\Users\admin\AppData\Local\Temp\Fav\FavriteAdd.exe | executable | |
MD5:— | SHA256:— | |||
| 3424 | FavriteAdd.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Bookmarks | text | |
MD5:— | SHA256:— | |||
| 3084 | ¦¬+t+ñ+e¦ñ+¯V17.0.exe | C:\Users\admin\AppData\Local\Temp\vwxyz73351a00c84c94d3.exe | executable | |
MD5:— | SHA256:— | |||
| 1376 | klmnopqrstuvwxyz_¼¤»î¹¤¾ß2.exe | C:\Users\admin\AppData\Local\Temp\¼¤»î¹¤¾ß2.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
4
DNS requests
31
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2680 | lmnopqrstuvwxyz1.exe | GET | — | 42.180.125.194:80 | http://down.win11xz.cn/hp0409.exe | CN | — | — | suspicious |
3968 | vwxyz73351a00c84c94d3.exe | POST | — | 61.135.186.213:80 | http://dr.toolbar.baidu.com/ | CN | — | — | unknown |
2504 | ¼¤»î¹¤¾ß2.exe | GET | 200 | 103.235.46.39:80 | http://www.baidu.com/s?ie=utf-8&wd=ip | HK | html | 416 Kb | whitelisted |
2504 | ¼¤»î¹¤¾ß2.exe | POST | — | 119.23.216.188:80 | http://report.win10999.com/reportStatistics/ | CN | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2680 | lmnopqrstuvwxyz1.exe | 42.180.125.194:80 | down.win11xz.cn | CHINA UNICOM China169 Backbone | CN | suspicious |
3968 | vwxyz73351a00c84c94d3.exe | 61.135.186.213:80 | dr.toolbar.baidu.com | China Unicom Beijing Province Network | CN | unknown |
2504 | ¼¤»î¹¤¾ß2.exe | 103.235.46.39:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | unknown |
2504 | ¼¤»î¹¤¾ß2.exe | 119.23.216.188:80 | report.win10999.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
down.win11xz.cn |
| suspicious |
dr.toolbar.baidu.com |
| unknown |
www.baidu.com |
| whitelisted |
dr.addressbar.baidu.com |
| unknown |
dns.msftncsi.com |
| shared |
report.win10999.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2680 | lmnopqrstuvwxyz1.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Malicious Macro DL EXE Feb 2016 |
2680 | lmnopqrstuvwxyz1.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Malicious Macro EXE DL AlphaNumL |
1 ETPRO signatures available at the full report