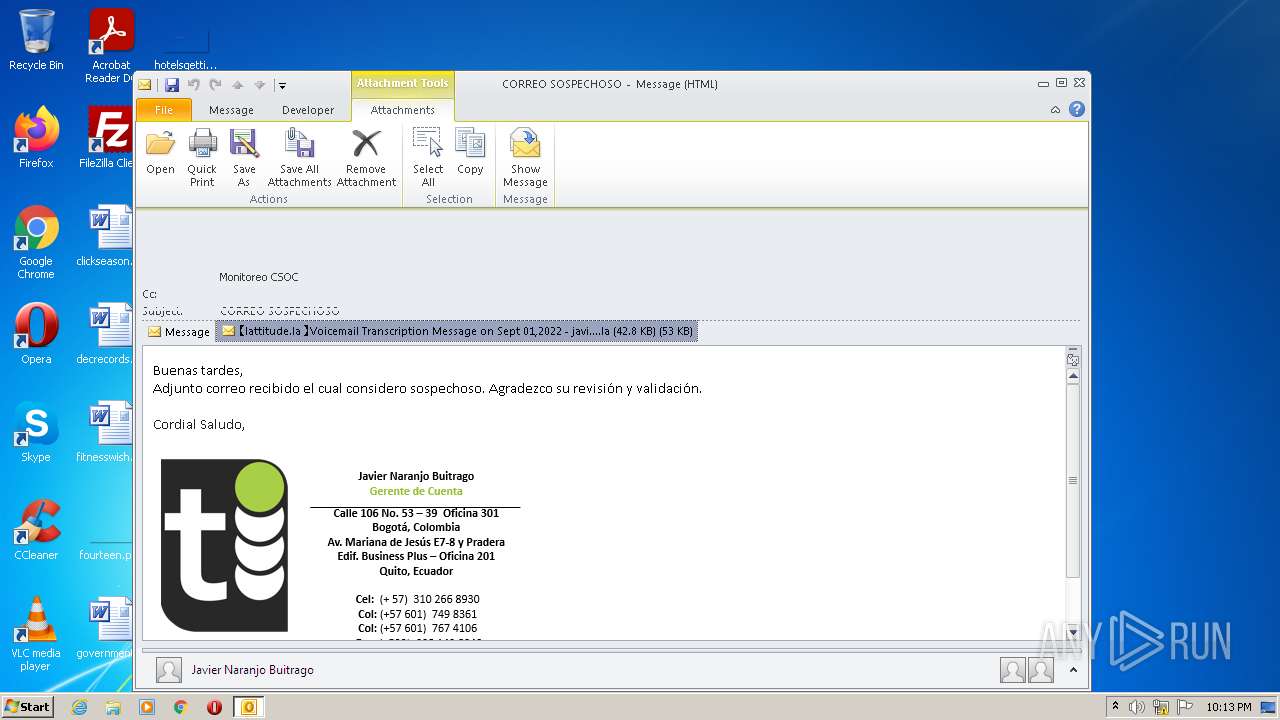
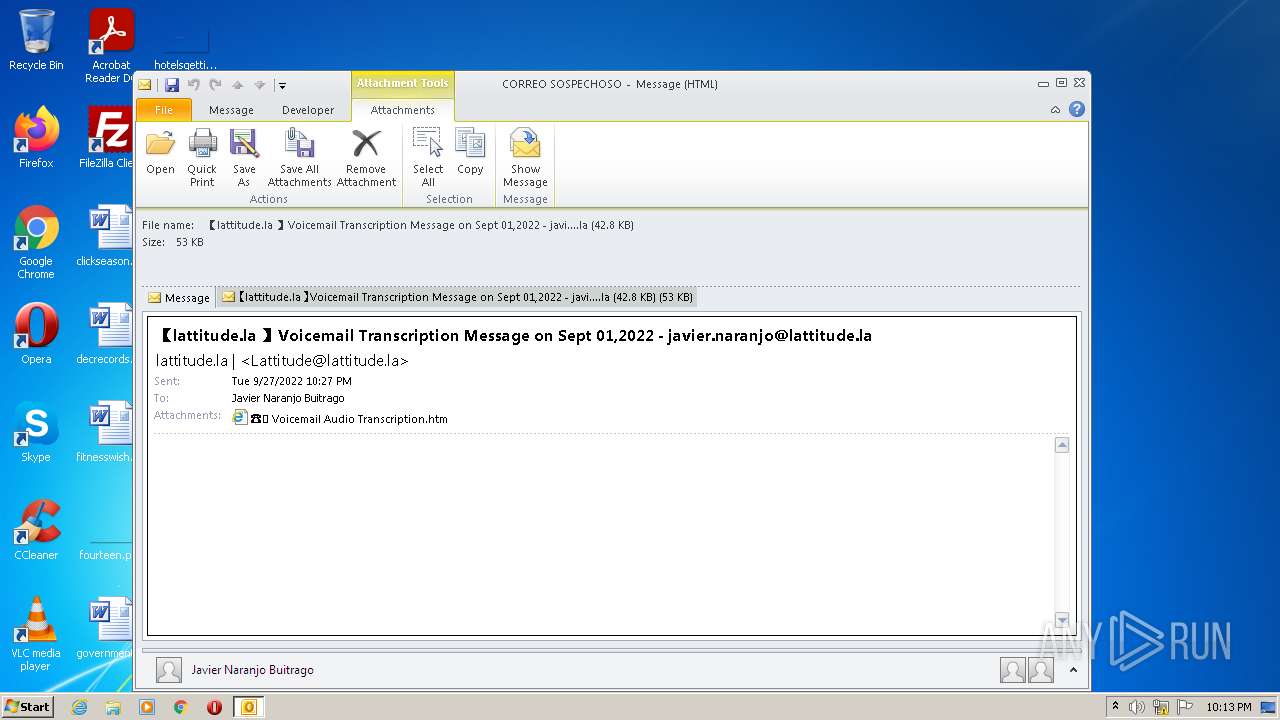
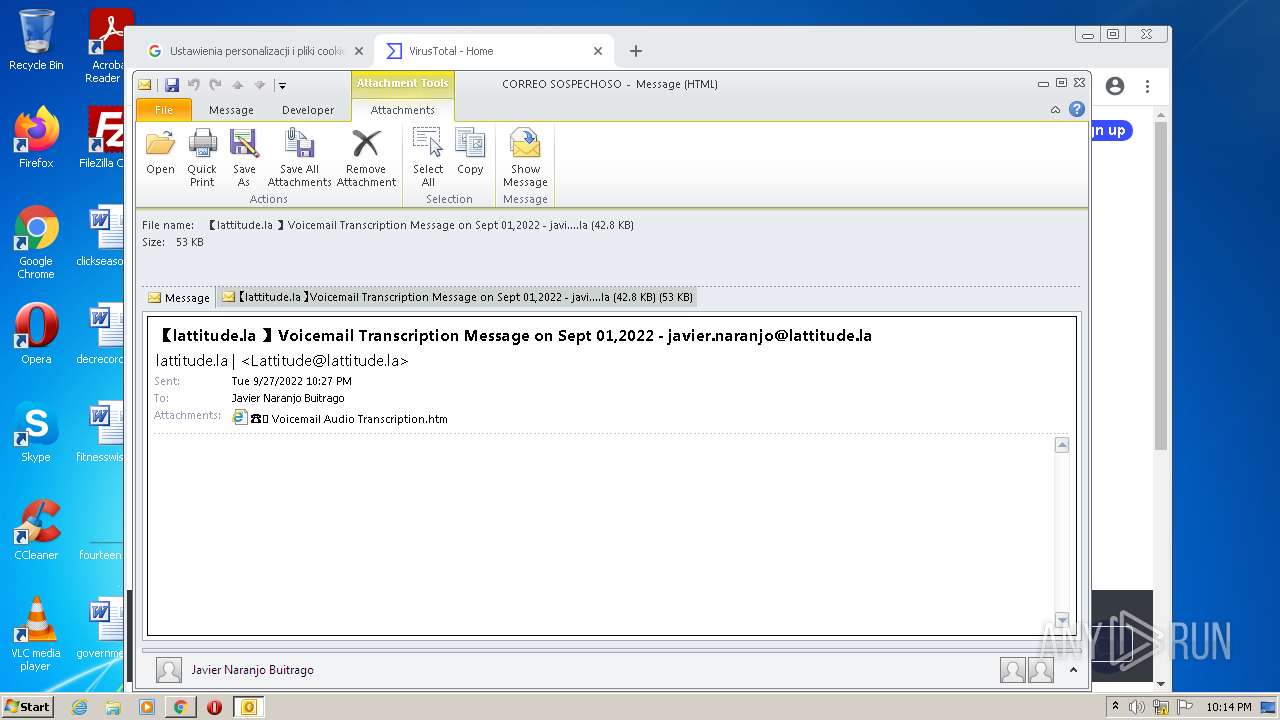
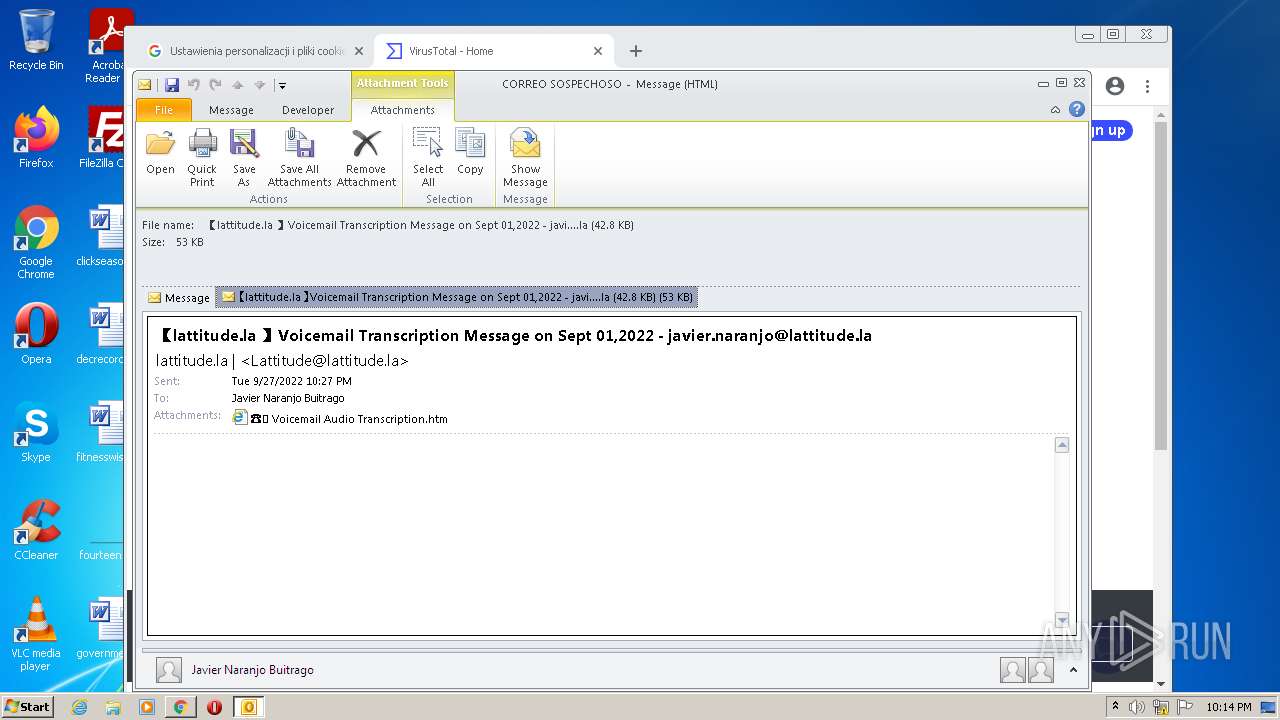
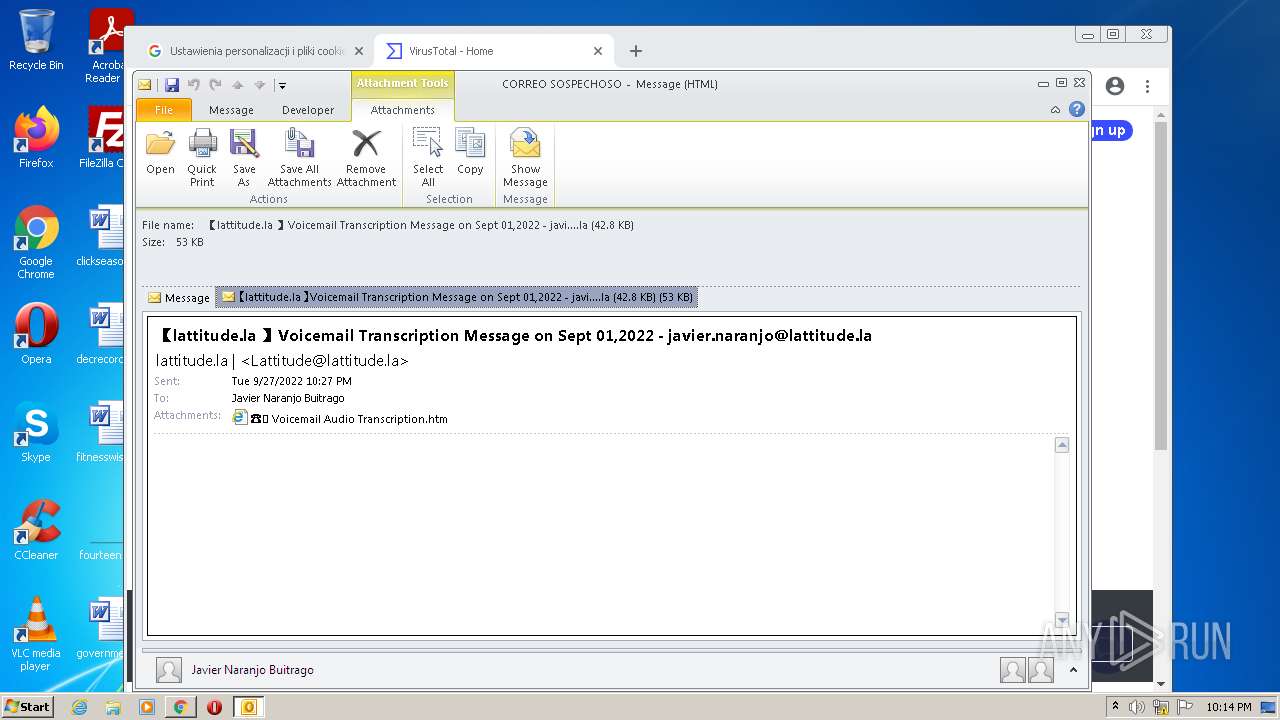
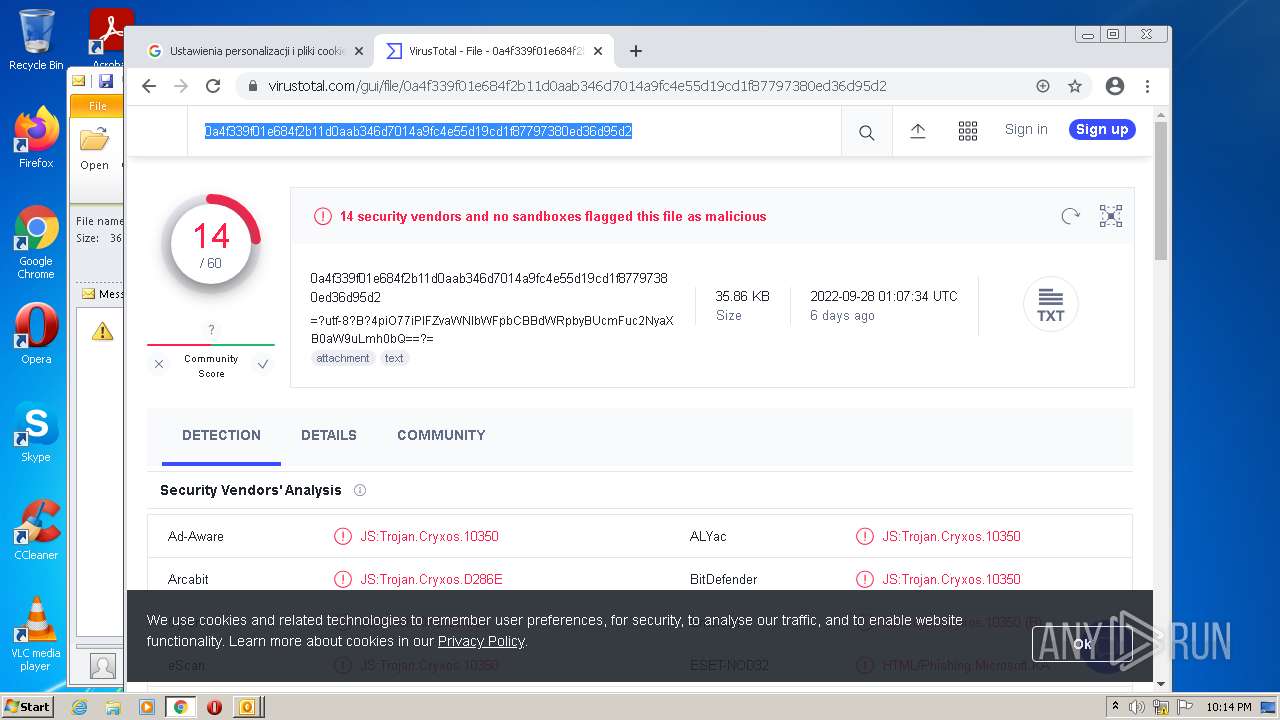
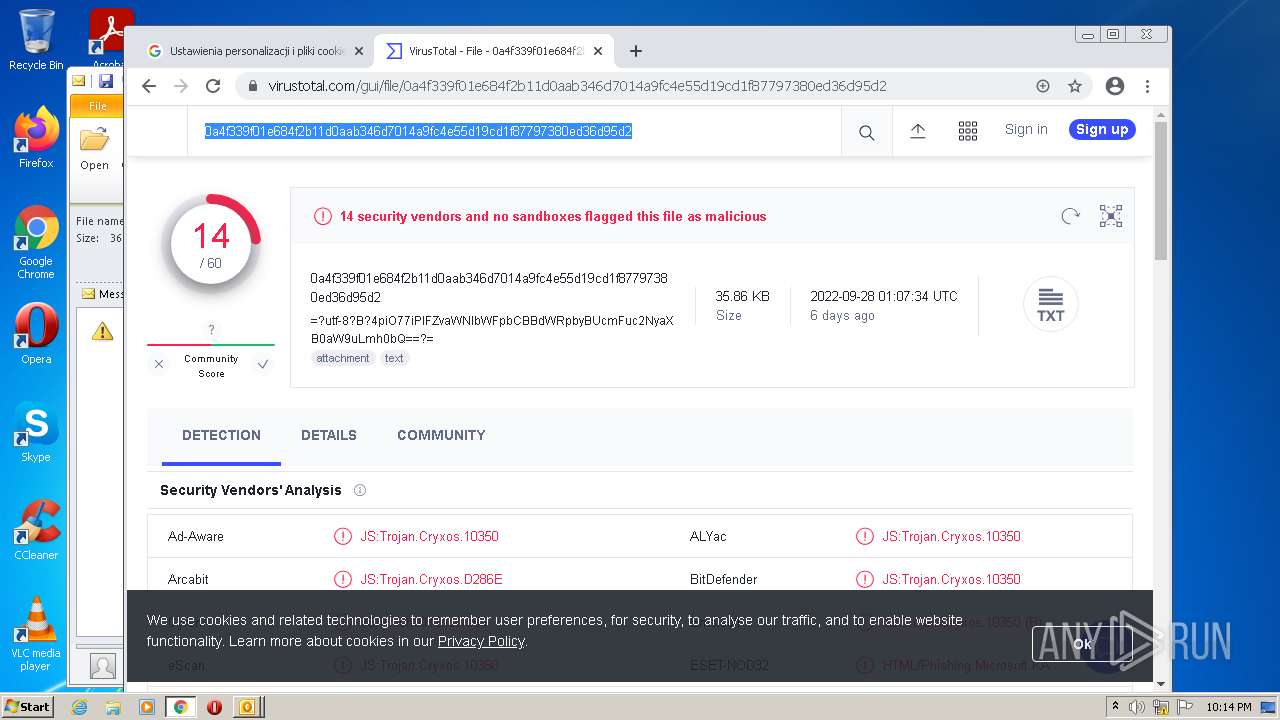
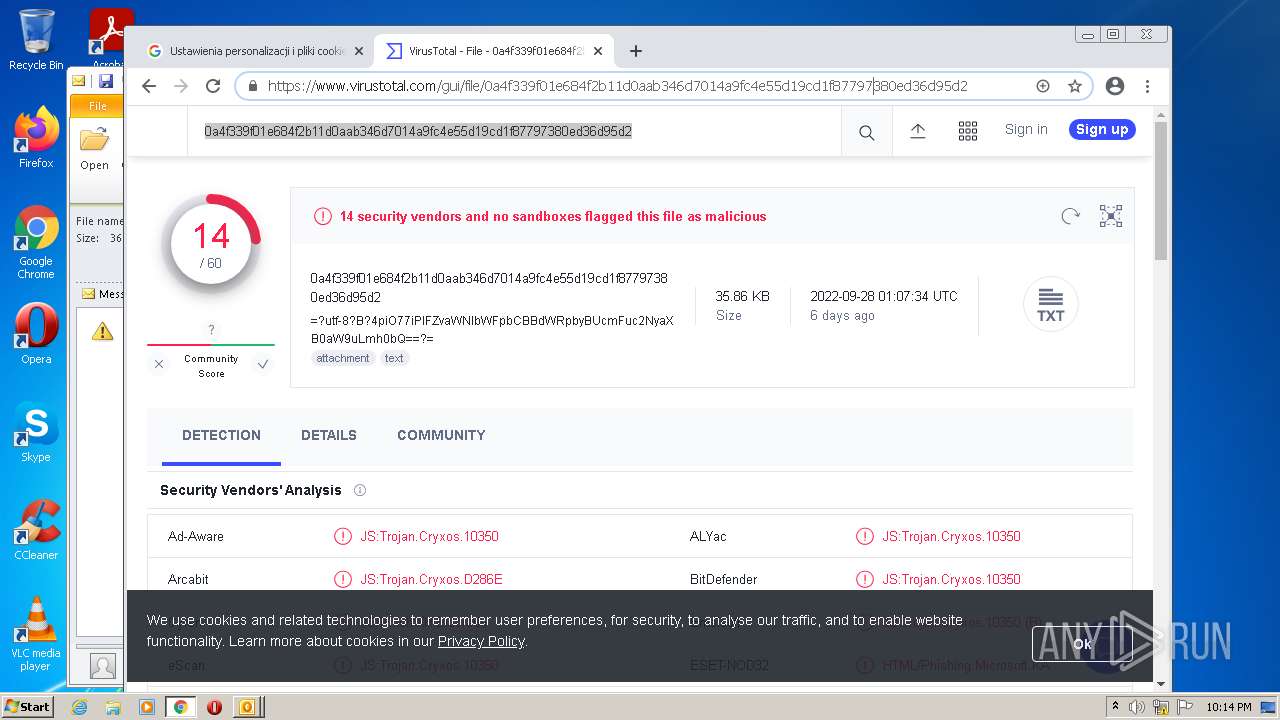
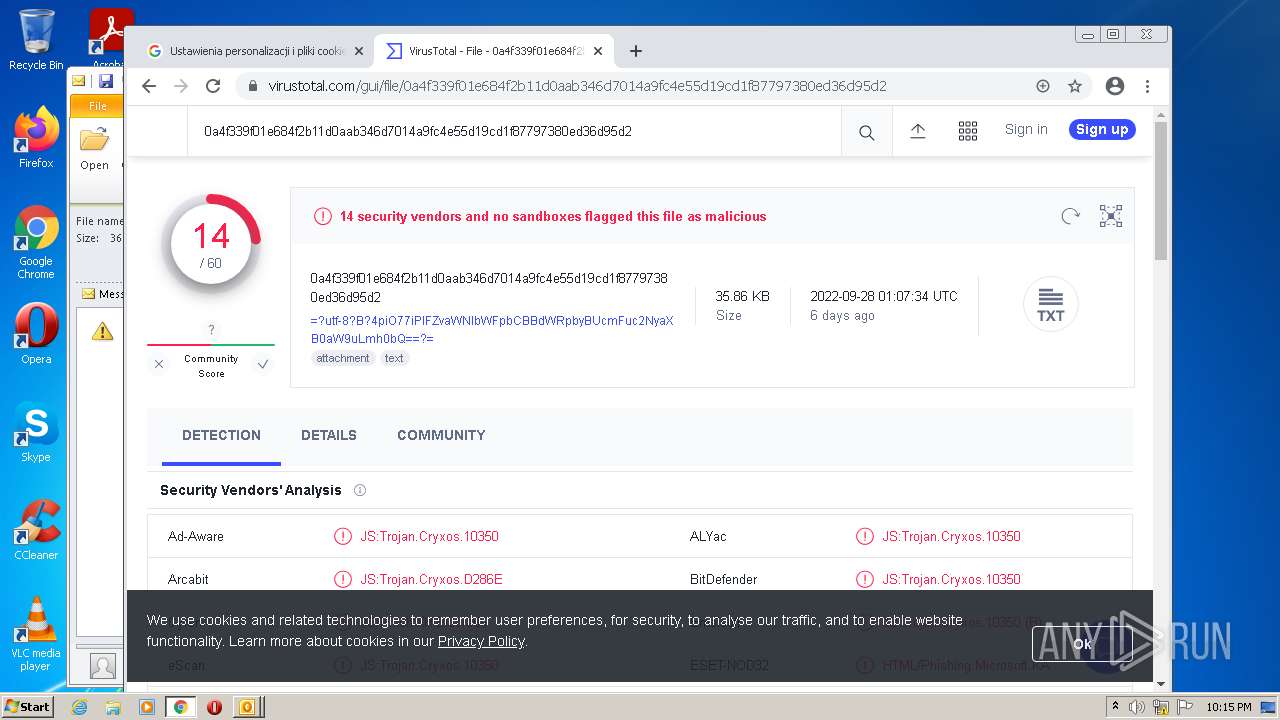
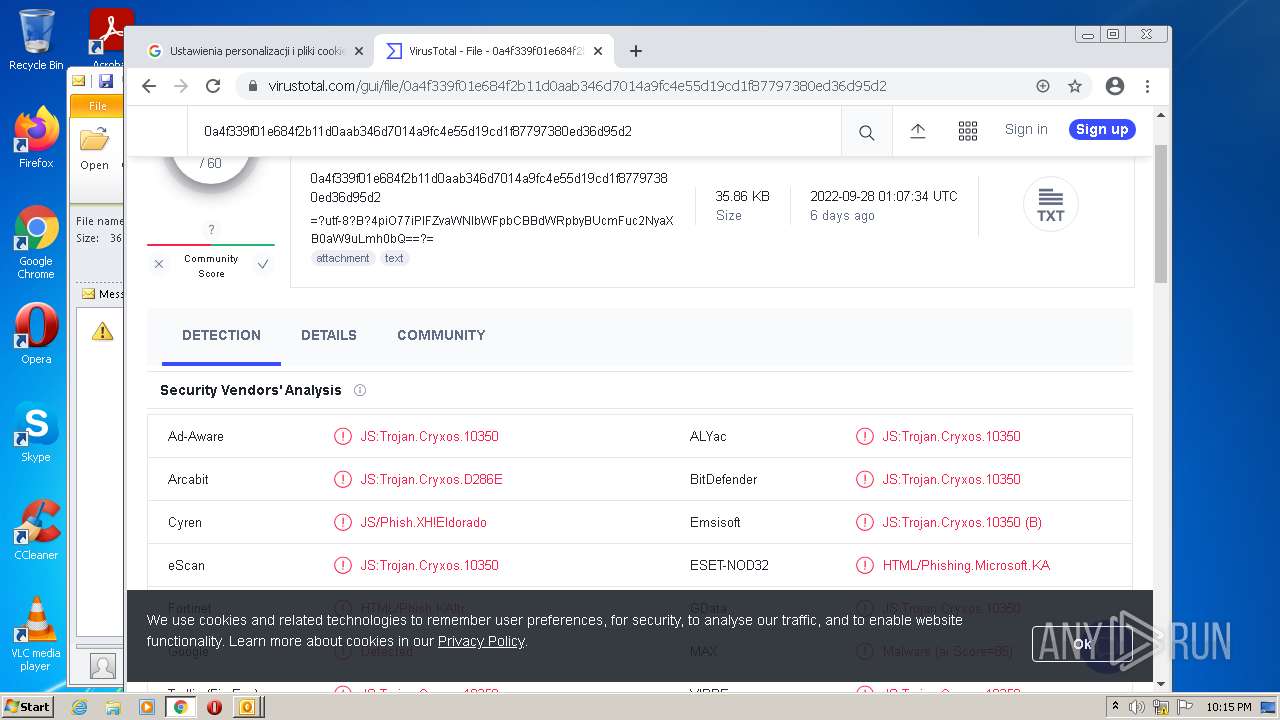
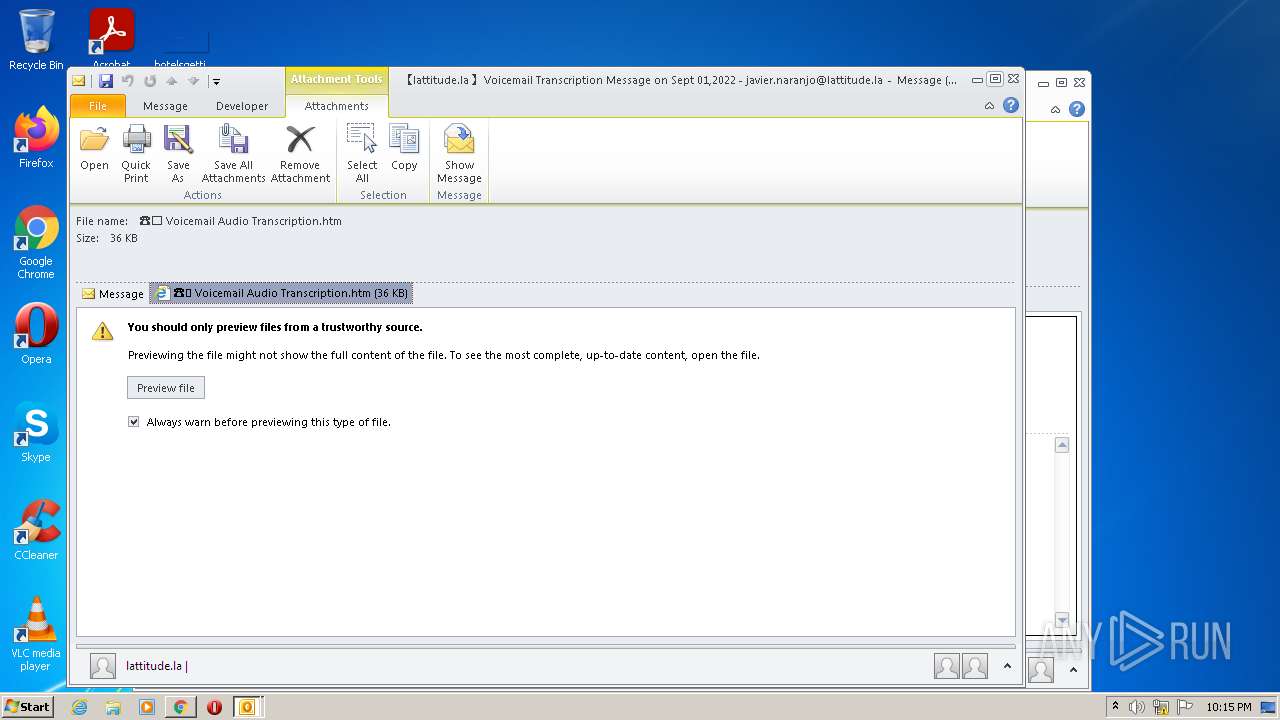
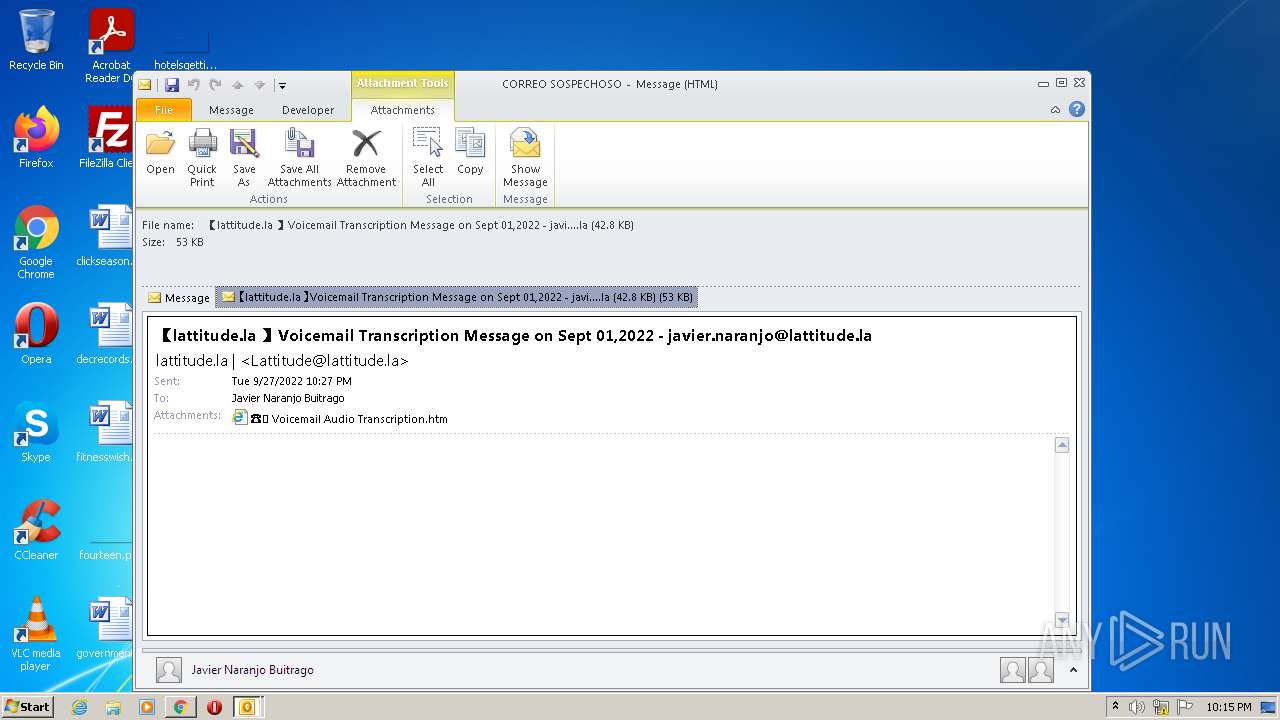
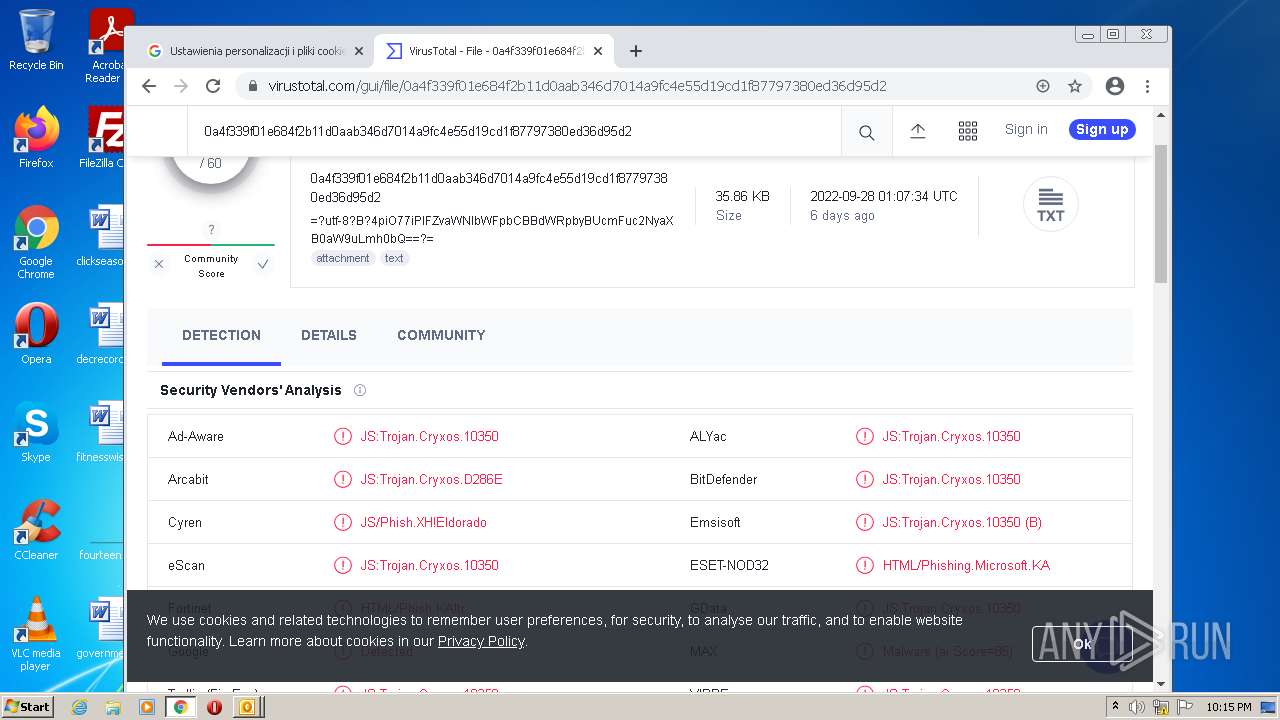
| File name: | 【lattitude.la 】Voicemail Transcription Message on Sept 01,2022 - javier.naranjo@lattitude.la.eml |
| Full analysis: | https://app.any.run/tasks/65834eee-31d8-480b-b029-04a7e7d05c3e |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 21:12:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | F6221A23140F8751DCB2C91B627C74A6 |
| SHA1: | 6823FF3EB6A9CAA89E06ED44136F24D665FDAA97 |
| SHA256: | D5B0781329189BC818924B082BFBEC7E982D2BB293E6CA6EC0D83EA3BD0BF8EF |
| SSDEEP: | 1536:hdFwtiurkSuPJVbSYZWIFe3JBcciu/TEQXZzbuRWh4eBWsFeshECz:HFSwSuxVbSYe3JEu/lp54AFesik |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 1148)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 2356)
SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 3276)
Searches for installed software
- OUTLOOK.EXE (PID: 3276)
Reads the computer name
- OUTLOOK.EXE (PID: 3276)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3276)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3292)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3960)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3276)
Executable content was dropped or overwritten
- chrome.exe (PID: 1148)
- chrome.exe (PID: 2356)
Drops a file with a compile date too recent
- chrome.exe (PID: 1828)
- chrome.exe (PID: 2356)
- chrome.exe (PID: 1148)
INFO
Checks supported languages
- chrome.exe (PID: 3292)
- chrome.exe (PID: 3500)
- chrome.exe (PID: 1628)
- chrome.exe (PID: 288)
- chrome.exe (PID: 2804)
- chrome.exe (PID: 2832)
- chrome.exe (PID: 2876)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 3280)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 3196)
- chrome.exe (PID: 2296)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 2364)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 3644)
- chrome.exe (PID: 340)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 3252)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 1848)
- chrome.exe (PID: 1260)
- chrome.exe (PID: 760)
- chrome.exe (PID: 316)
- chrome.exe (PID: 2496)
- chrome.exe (PID: 3312)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 2268)
- chrome.exe (PID: 3180)
- chrome.exe (PID: 2396)
- chrome.exe (PID: 2036)
- chrome.exe (PID: 3252)
- chrome.exe (PID: 2228)
- chrome.exe (PID: 1320)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 2532)
- chrome.exe (PID: 2888)
- chrome.exe (PID: 720)
- chrome.exe (PID: 2484)
- chrome.exe (PID: 3620)
- chrome.exe (PID: 1780)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 1472)
- chrome.exe (PID: 2976)
- chrome.exe (PID: 4056)
- chrome.exe (PID: 2364)
- chrome.exe (PID: 2352)
- chrome.exe (PID: 4012)
- chrome.exe (PID: 3608)
- chrome.exe (PID: 3408)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 3740)
- chrome.exe (PID: 332)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 2100)
- chrome.exe (PID: 1940)
- chrome.exe (PID: 772)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 1576)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 2680)
- chrome.exe (PID: 3752)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 2128)
- chrome.exe (PID: 2124)
- iexplore.exe (PID: 2680)
- chrome.exe (PID: 3928)
- chrome.exe (PID: 2588)
- iexplore.exe (PID: 3960)
- chrome.exe (PID: 3560)
- chrome.exe (PID: 3296)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 3352)
- chrome.exe (PID: 2392)
- chrome.exe (PID: 1148)
- chrome.exe (PID: 2328)
- chrome.exe (PID: 3316)
- chrome.exe (PID: 2308)
- chrome.exe (PID: 2356)
Reads the computer name
- chrome.exe (PID: 3292)
- chrome.exe (PID: 1628)
- chrome.exe (PID: 288)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 3644)
- chrome.exe (PID: 2396)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 2976)
- chrome.exe (PID: 4012)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 1576)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 772)
- chrome.exe (PID: 1940)
- iexplore.exe (PID: 3960)
- iexplore.exe (PID: 2680)
- chrome.exe (PID: 2124)
- chrome.exe (PID: 2328)
Manual execution by user
- chrome.exe (PID: 3292)
- chrome.exe (PID: 1828)
Reads the hosts file
- chrome.exe (PID: 1628)
- chrome.exe (PID: 3292)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 1940)
Reads settings of System Certificates
- chrome.exe (PID: 1628)
- chrome.exe (PID: 1828)
- iexplore.exe (PID: 3960)
- iexplore.exe (PID: 2680)
Application launched itself
- chrome.exe (PID: 3292)
- chrome.exe (PID: 1828)
- iexplore.exe (PID: 2680)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3276)
Reads the date of Windows installation
- chrome.exe (PID: 2068)
- chrome.exe (PID: 2328)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3292)
Checks Windows Trust Settings
- iexplore.exe (PID: 3960)
- iexplore.exe (PID: 2680)
Reads internet explorer settings
- iexplore.exe (PID: 3960)
Changes internet zones settings
- iexplore.exe (PID: 2680)
Creates files in the user directory
- iexplore.exe (PID: 2680)
Changes settings of System certificates
- iexplore.exe (PID: 2680)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2680)
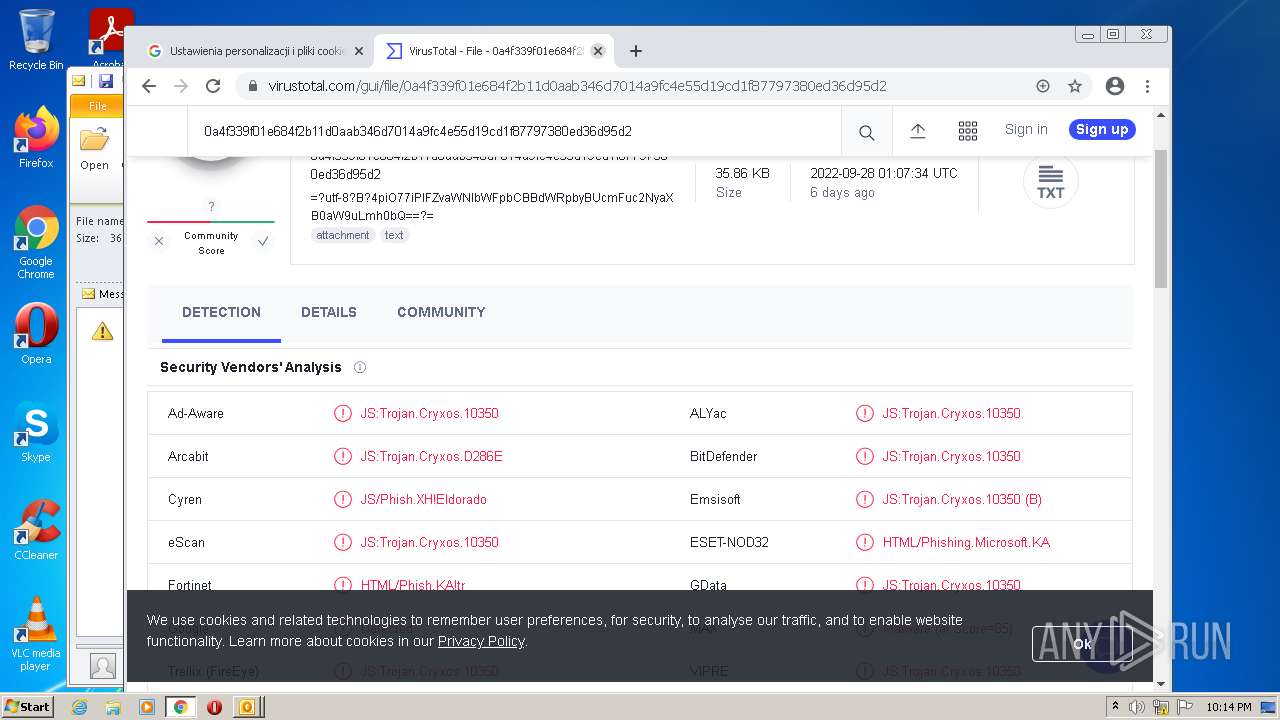
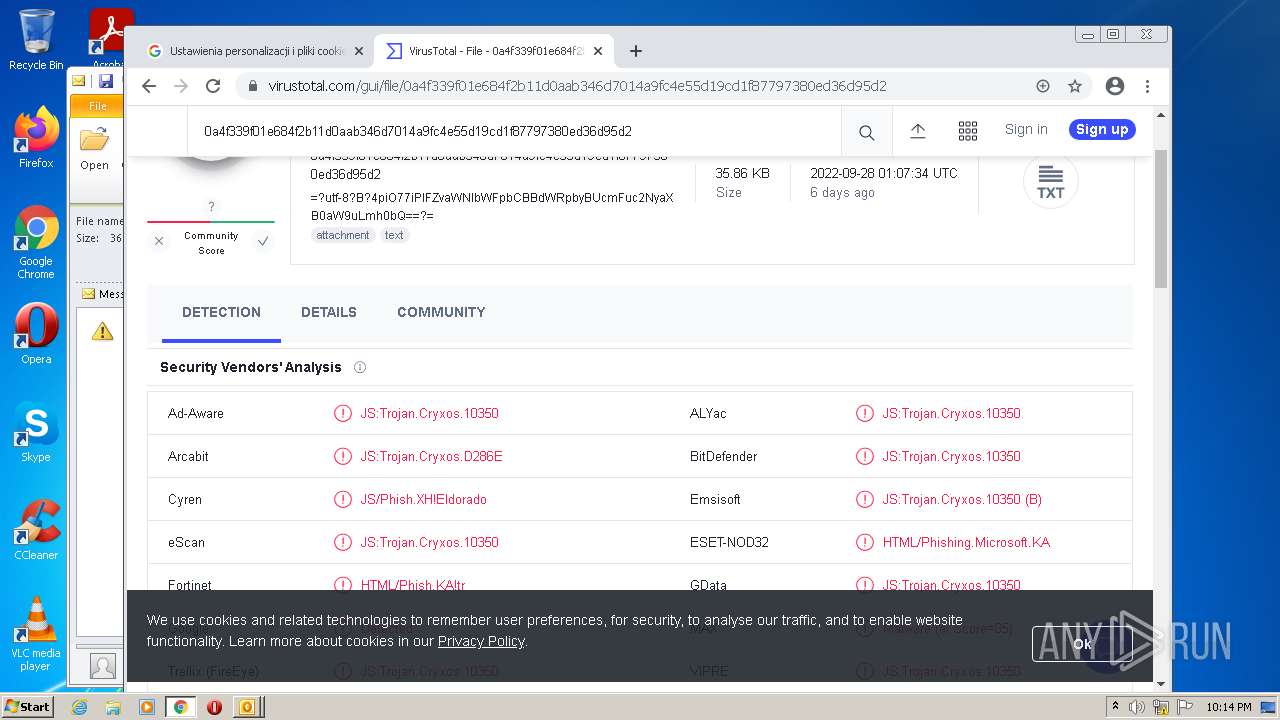
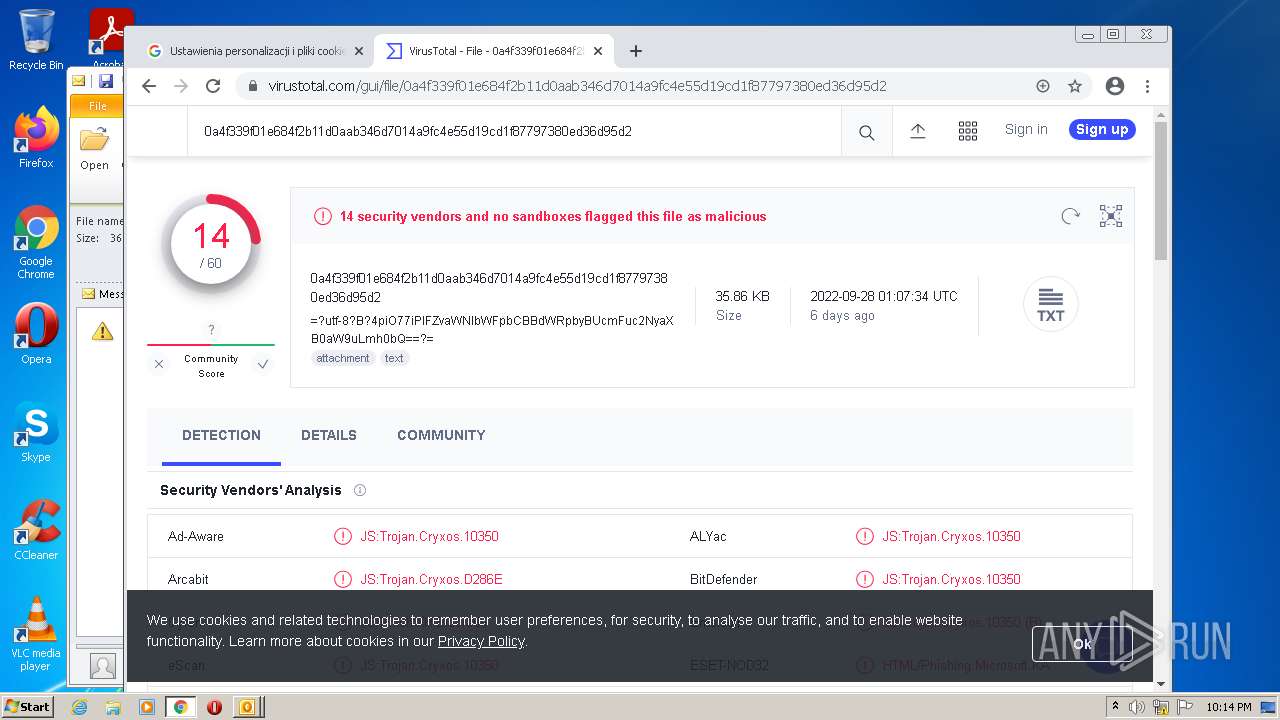
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
127
Monitored processes
84
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1084 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3556 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2176 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3748 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3188 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=992,842720576650673710,13723559516371392726,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1052 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=992,842720576650673710,13723559516371392726,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2148 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3196 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,11583090505408293460,7557798709721482229,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1768 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
48 159
Read events
47 066
Write events
1 057
Delete events
36
Modification events
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
2
Suspicious files
283
Text files
320
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR58DB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-633CA1E6-CDC.pma | — | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C5125764.dat | image | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\R3N1CK78\【lattitude la 】Voicemail Transcription Message on Sept 012022 - javi la (42 8 KB).msg | msg | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF78280AD28B7DA9B4.TMP | atn | |
MD5:— | SHA256:— | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{57C7E5AA-2149-4906-B534-B41898007CE1}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
60
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
808 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kwwzs7t4dq4pu3zh4drhohnhia_2875/jflookgnkcckhobaglndicnbbgbonegd_2875_all_acr4yh57ursmal3v5c7ephahtyxq.crx3 | US | binary | 7.39 Kb | whitelisted |
808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kwwzs7t4dq4pu3zh4drhohnhia_2875/jflookgnkcckhobaglndicnbbgbonegd_2875_all_acr4yh57ursmal3v5c7ephahtyxq.crx3 | US | binary | 9.74 Kb | whitelisted |
808 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 38 b | whitelisted |
808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kwwzs7t4dq4pu3zh4drhohnhia_2875/jflookgnkcckhobaglndicnbbgbonegd_2875_all_acr4yh57ursmal3v5c7ephahtyxq.crx3 | US | binary | 20.9 Kb | whitelisted |
808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 360 Kb | whitelisted |
3960 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 24.4 Kb | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kwwzs7t4dq4pu3zh4drhohnhia_2875/jflookgnkcckhobaglndicnbbgbonegd_2875_all_acr4yh57ursmal3v5c7ephahtyxq.crx3 | US | binary | 38 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3276 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1628 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
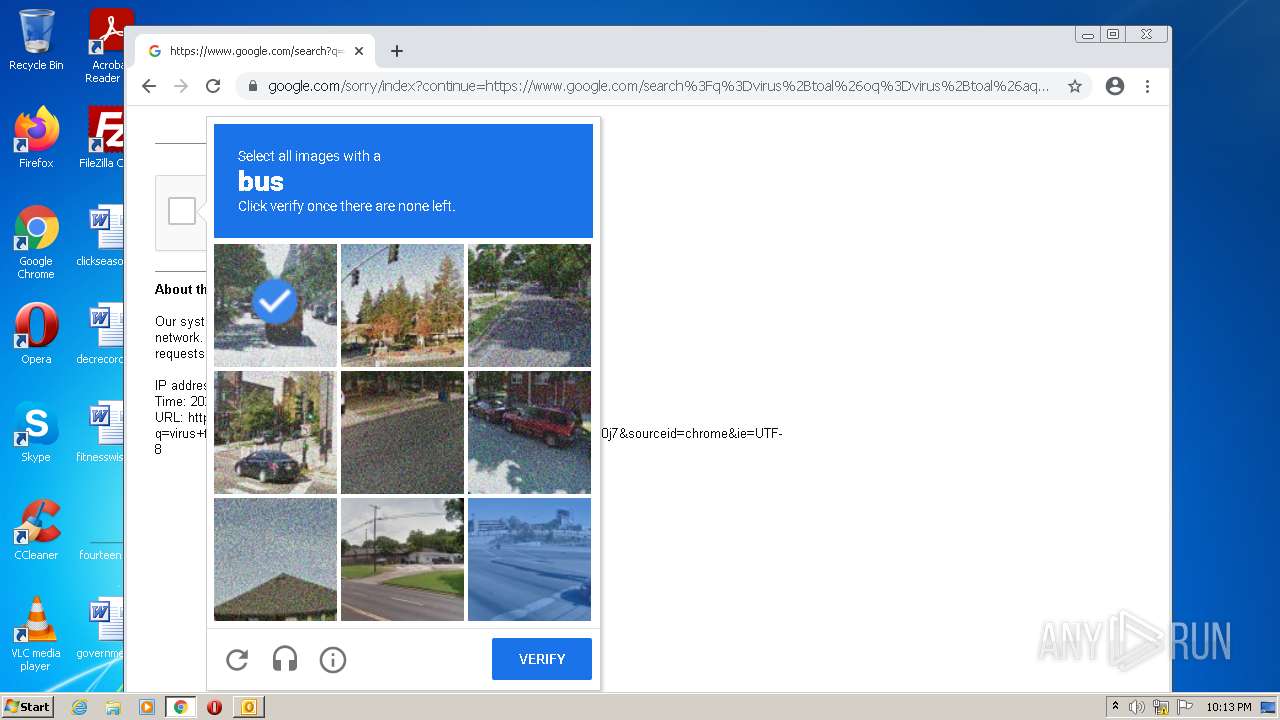
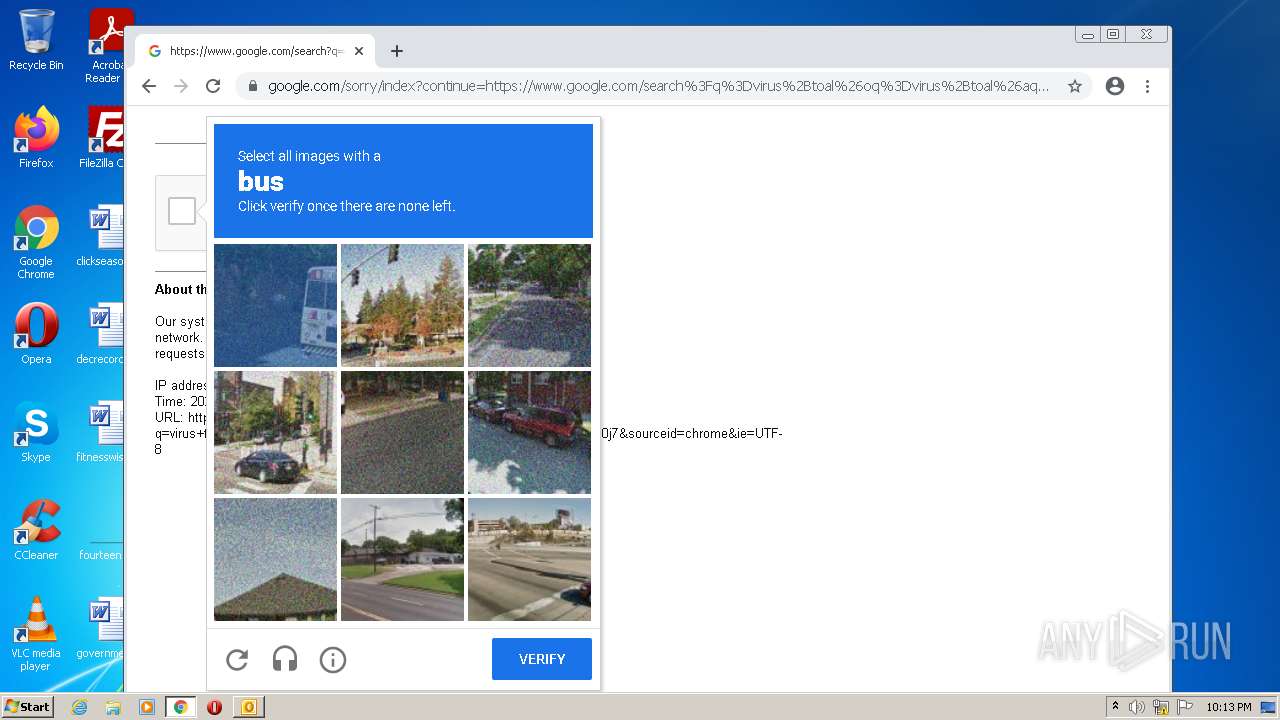
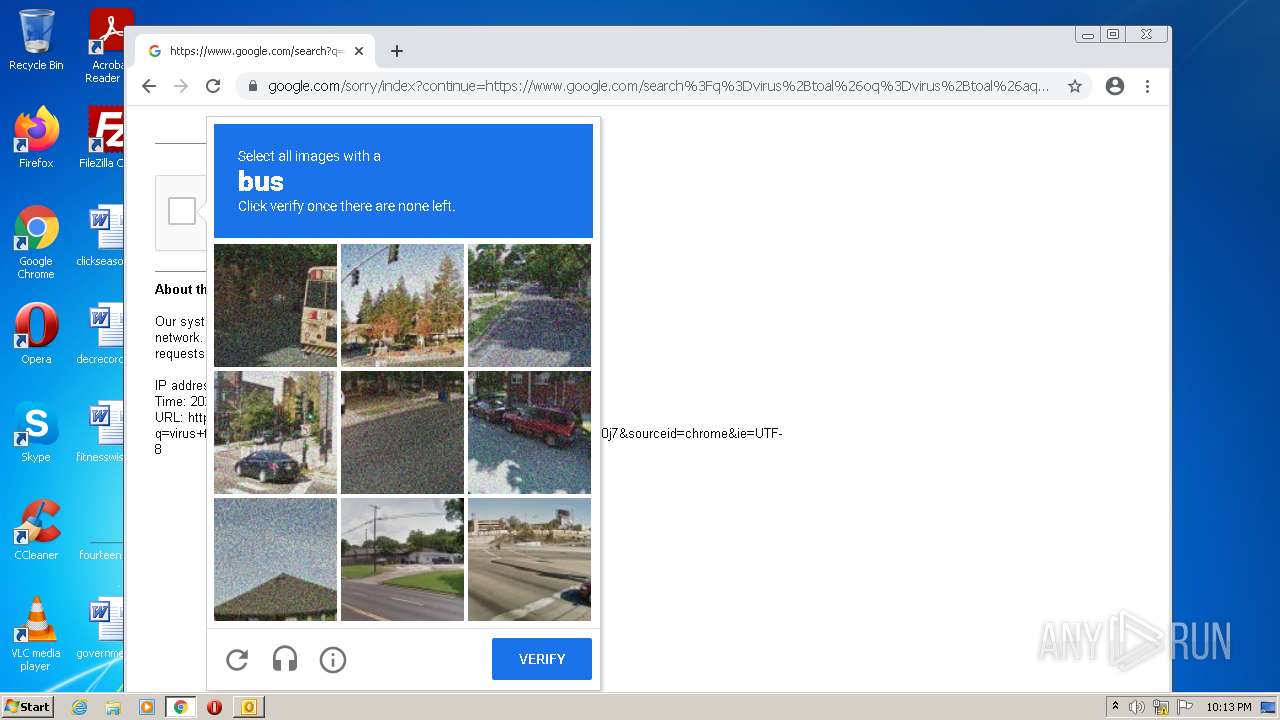
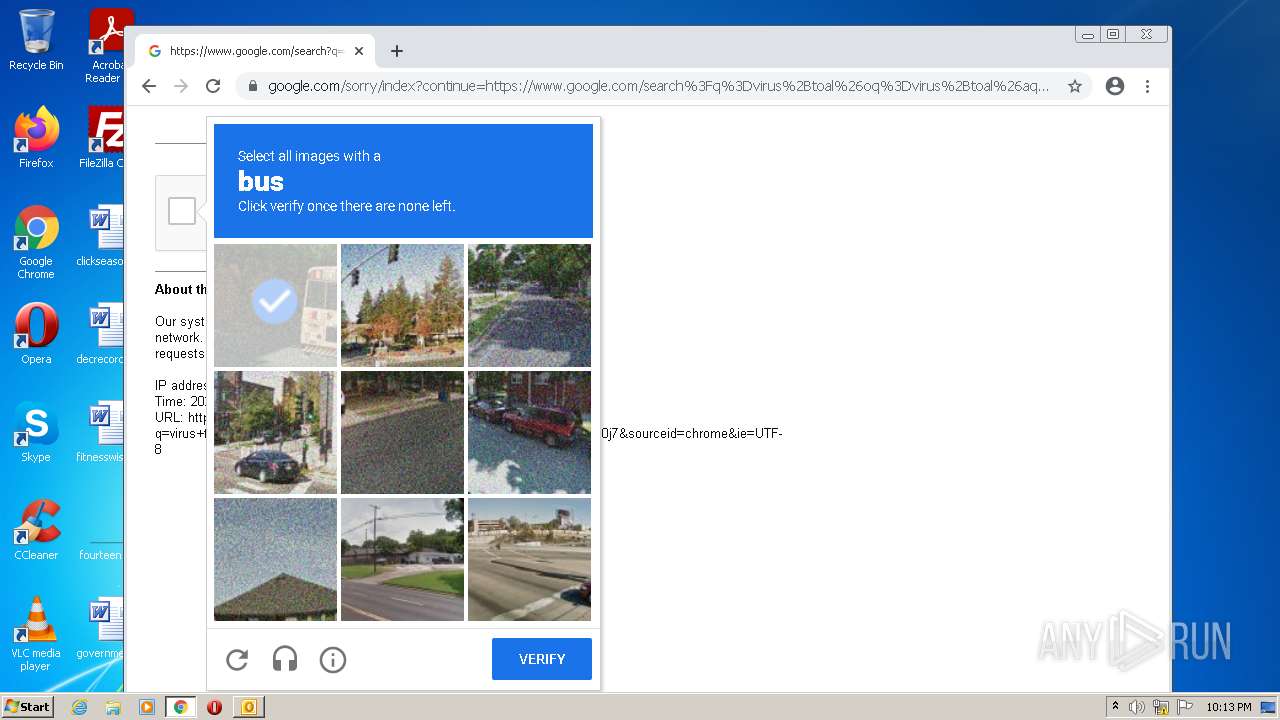
1628 | chrome.exe | 142.250.186.173:443 | accounts.google.com | GOOGLE | US | suspicious |
1628 | chrome.exe | 172.217.23.110:443 | clients2.google.com | GOOGLE | US | whitelisted |
1628 | chrome.exe | 216.58.212.174:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
1628 | chrome.exe | 172.217.18.1:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
1628 | chrome.exe | 142.250.184.195:443 | update.googleapis.com | GOOGLE | US | whitelisted |
1628 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | GOOGLE | US | whitelisted |
1628 | chrome.exe | 172.217.17.227:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
1628 | chrome.exe | 142.250.184.131:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
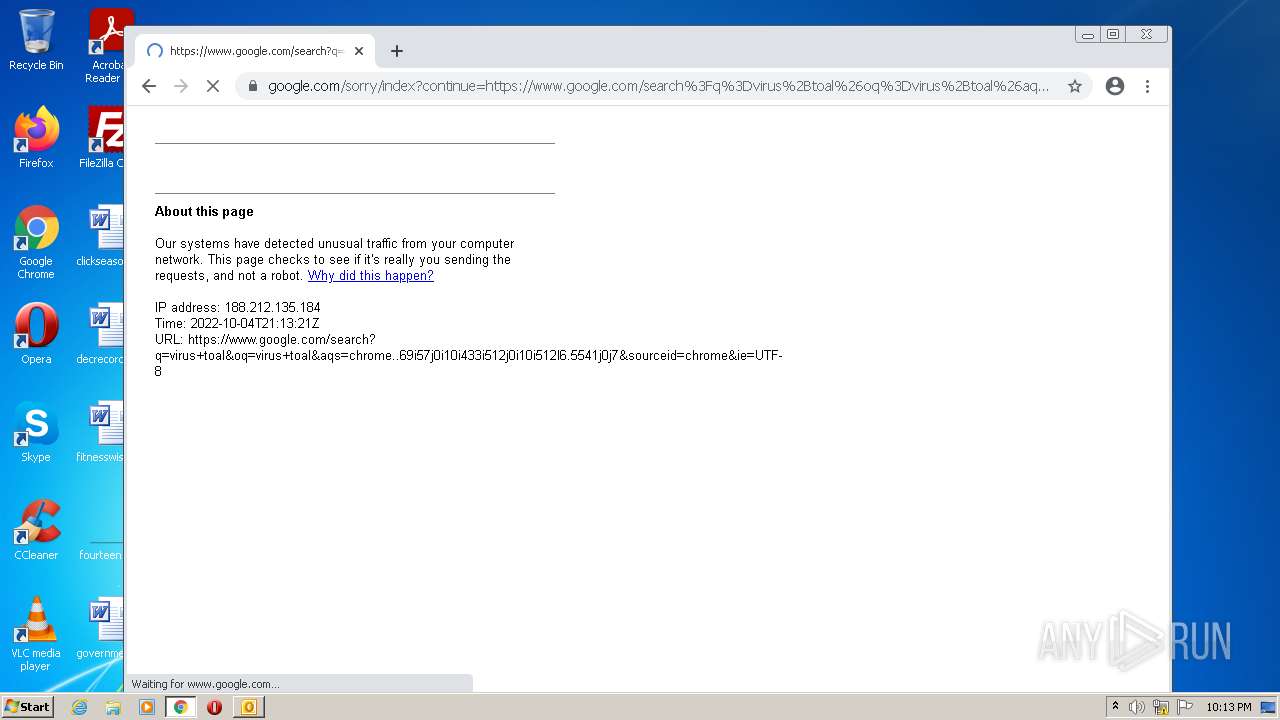
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |