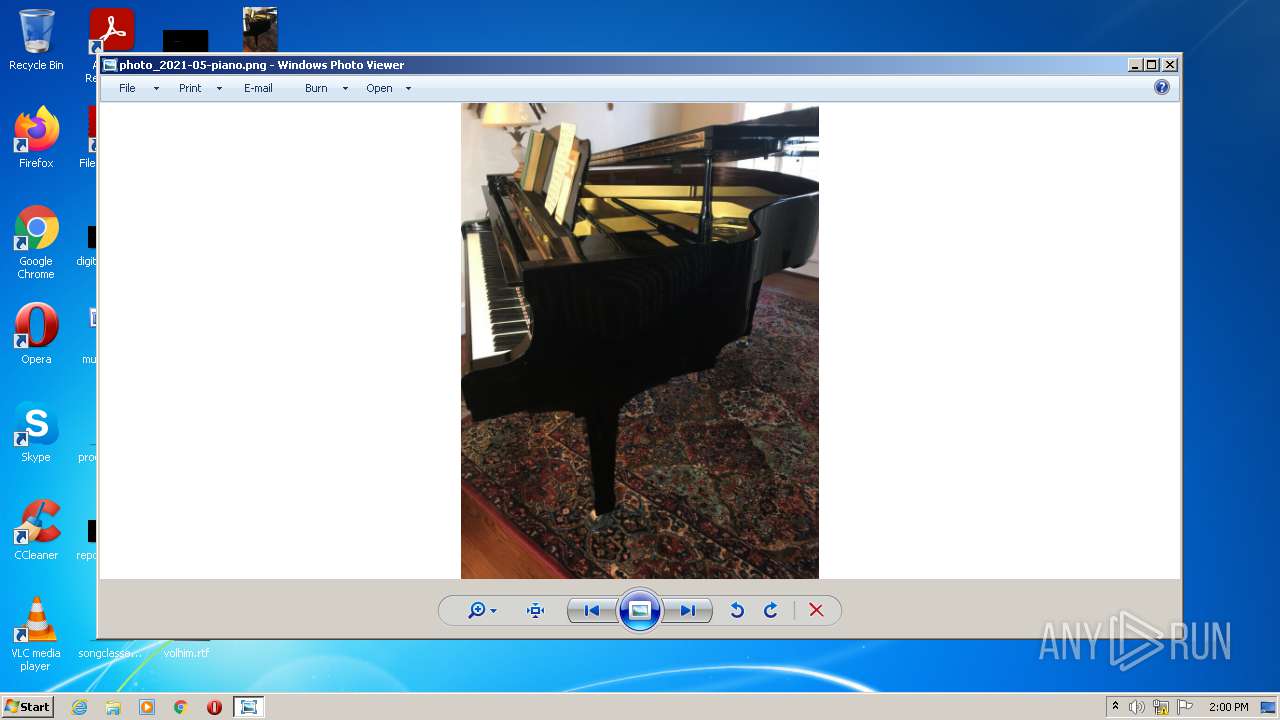
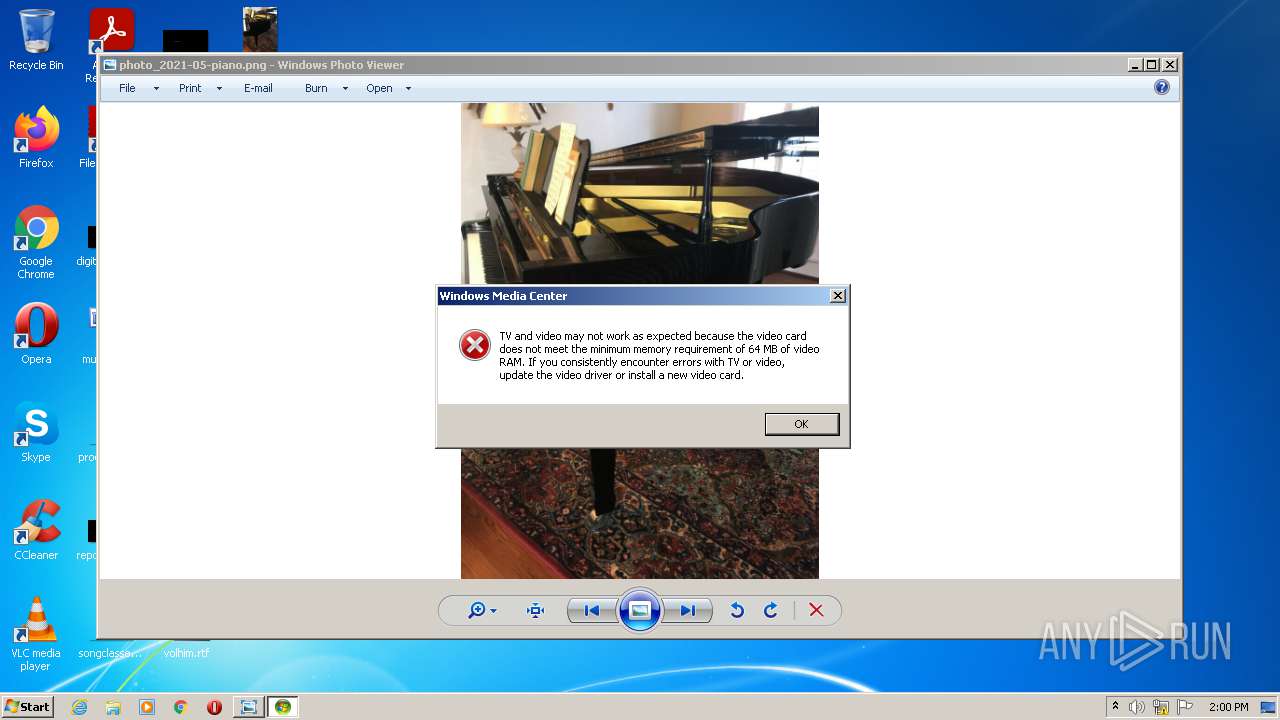
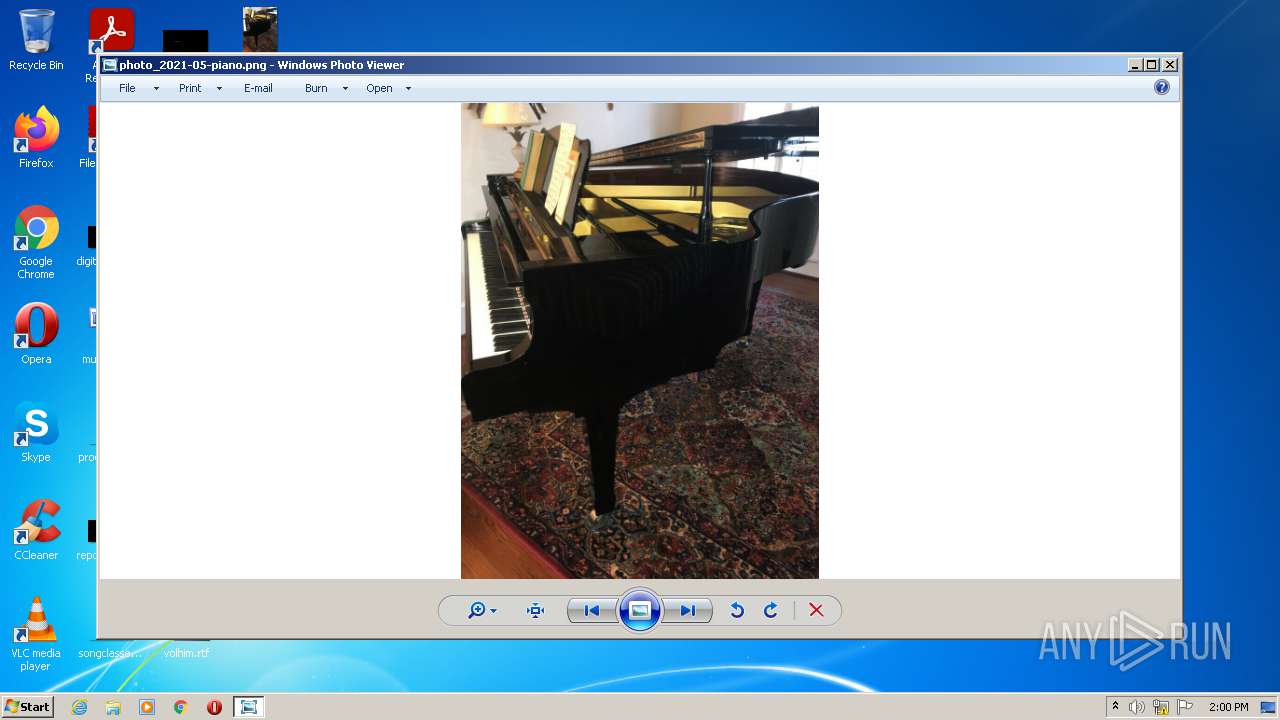
| File name: | photo_2021-05-piano.png |
| Full analysis: | https://app.any.run/tasks/83cd1af7-54ec-4441-895e-805698174318 |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2021, 12:59:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | image/png |
| File info: | PNG image data, 768 x 1024, 8-bit/color RGBA, interlaced |
| MD5: | 50837DCD4151F3C6A2D710B09BBBDBDD |
| SHA1: | 162ACEA53285B484517D2F7C251F0CAD76387B2C |
| SHA256: | D5AFD66945790D608A01FDF1E72D262735A5C06D0C4B84F7B13BD97AD20ABA5C |
| SSDEEP: | 24576:agrnZTwiQr02JFAvYFYEVhw+8lULEceKYWHZckKUz3RNMkw2NBHKm1WtNNQmnh5Y:XrZTwnr/LEKLBr5SUzrMk/nH71WTP5on |
MALICIOUS
Loads the Task Scheduler COM API
- ehRec.exe (PID: 3592)
- ehshell.exe (PID: 3216)
SUSPICIOUS
Creates files in the user directory
- ehshell.exe (PID: 3216)
- EhTray.exe (PID: 3092)
Reads the date of Windows installation
- DllHost.exe (PID: 3264)
Checks supported languages
- ehshell.exe (PID: 3216)
- ehsched.exe (PID: 1660)
- EhTray.exe (PID: 3092)
- ehRec.exe (PID: 3592)
Reads the computer name
- ehshell.exe (PID: 3216)
- ehsched.exe (PID: 1660)
- EhTray.exe (PID: 3092)
- ehRec.exe (PID: 3592)
Executed via COM
- DllHost.exe (PID: 3264)
- ehRec.exe (PID: 3592)
Creates files in the program directory
- ehshell.exe (PID: 3216)
- ehRec.exe (PID: 3592)
Creates files in the Windows directory
- ehRec.exe (PID: 3592)
Executed as Windows Service
- ehsched.exe (PID: 1660)
INFO
Reads the computer name
- DllHost.exe (PID: 3264)
Checks supported languages
- DllHost.exe (PID: 3264)
- rundll32.exe (PID: 1832)
Manual execution by user
- EhTray.exe (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
Composite
| Megapixels: | 0.786 |
|---|---|
| ImageSize: | 768x1024 |
PNG
| PixelUnits: | meters |
|---|---|
| PixelsPerUnitY: | 3779 |
| PixelsPerUnitX: | 3779 |
| Gamma: | 2.2 |
| SRGBRendering: | Perceptual |
| Interlace: | Adam7 Interlace |
| Filter: | Adaptive |
| Compression: | Deflate/Inflate |
| ColorType: | RGB with Alpha |
| BitDepth: | 8 |
| ImageHeight: | 1024 |
| ImageWidth: | 768 |
Total processes
39
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1660 | C:\Windows\ehome\ehsched.exe | C:\Windows\ehome\ehsched.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Scheduler Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen "C:\Users\admin\Desktop\photo_2021-05-piano.png" | C:\Windows\System32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3092 | "C:\Windows\eHome\EhTray.exe" /nav:-2 | C:\Windows\eHome\EhTray.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3216 | "C:\Windows\eHome\ehshell.exe" "C:\Users\admin\Desktop\photo_2021-05-piano.png" | C:\Windows\eHome\ehshell.exe | — | DllHost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3264 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3592 | C:\Windows\ehome\ehRec.exe -Embedding | C:\Windows\ehome\ehRec.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Host Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 131
Read events
4 778
Write events
353
Delete events
0
Modification events
| (PID) Process: | (1832) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: rundll32.exe | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\OpenWithProgids |
| Operation: | write | Name: | pngfile |
Value: | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rUbzr\rufuryy.rkr |
Value: 00000000010000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF606678901D6CD70100000000 | |||
| (PID) Process: | (3264) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000003A010000620200000D490D013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E45102000000006D0000001CC85C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000094011CE4940100000000000000000000000000000000480B67020000000005000000D80B670200000000340C670230E4940178E494010000000000000000E8B9670205000000200000000100000064666C7464666C7400000000400000000459D8768805015E00000000000000000100000000000000000000000000000000000000E803000000000000FFFFFFFF000000000000000088FD68021CE4940105000000FFFFFFFF0000000000000000AC54D87600000000C054D8768805015E88FD68020000000088FD680205000000D80B67020000000090E6940198E69401E8B96702940A670220000000780B670200000000000000000000000000000000000000000500000000000000010000006C61746E64666C740000000011000000104F7B00084F7B0050E594016CE500004A6E853170E50000426E853124E594015E901D7670E594010CD400006E6E853138E59401929B1D7610D40A024C06000050E5940180CF0A025CE5940111000000104F7B00084F7B0050E59401A0CF0A02C0E50000166E853170E594015E901D76C0E5940174E5940103941D76000000000CD40A029CE59401A9931D760CD40A0248E6940180CF0A02BD931D760000000080CF0A0248E69401A4E59401000000006D0000001CC85C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000094011CE4940100000000000000000000000000000000480B67020000000005000000D80B670200000000340C670230E4940178E494010000000000000000E8B9670205000000200000000100000064666C7464666C7400000000400000000459D8768805015E00000000000000000100000000000000000000000000000000000000E803000000000000FFFFFFFF000000000000000088FD68021CE4940105000000FFFFFFFF0000000000000000AC54D87600000000C054D8768805015E88FD68020000000088FD680205000000D80B67020000000090E6940198E69401E8B96702940A670220000000780B670200000000000000000000000000000000000000000500000000000000010000006C61746E64666C740000000011000000104F7B00084F7B0050E594016CE500004A6E853170E50000426E853124E594015E901D7670E594010CD400006E6E853138E59401929B1D7610D40A024C06000050E5940180CF0A025CE5940111000000104F7B00084F7B0050E59401A0CF0A02C0E50000166E853170E594015E901D76C0E5940174E5940103941D76000000000CD40A029CE59401A9931D760CD40A0248E6940180CF0A02BD931D760000000080CF0A0248E69401A4E59401 | |||
Executable files
0
Suspicious files
5
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | ehshell.exe | C:\programdata\microsoft\ehome\mcepg2-0.db | binary | |
MD5:— | SHA256:— | |||
| 3216 | ehshell.exe | C:\ProgramData\Microsoft\eHome\Logs\FirstRun.log | xml | |
MD5:— | SHA256:— | |||
| 3092 | EhTray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b91050d8b077a4e8.customDestinations-ms | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 3092 | EhTray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OYNIHH48DL7C8EEUVF3K.temp | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 3216 | ehshell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\8f96978fc46d9f00d8780351026924d7_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:DB733E033C397FEC5917611957620271 | SHA256:1F3FFADD3B80C7F95BE06E245410768E8302A24E573868DA3C6FD91230025BDC | |||
| 3592 | ehRec.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-20\8f96978fc46d9f00d8780351026924d7_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:DB733E033C397FEC5917611957620271 | SHA256:1F3FFADD3B80C7F95BE06E245410768E8302A24E573868DA3C6FD91230025BDC | |||
| 3092 | EhTray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b91050d8b077a4e8.customDestinations-ms~RF2bc6b9.TMP | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 3092 | EhTray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GP3AS6RJQJ2JO76M8XBY.temp | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report