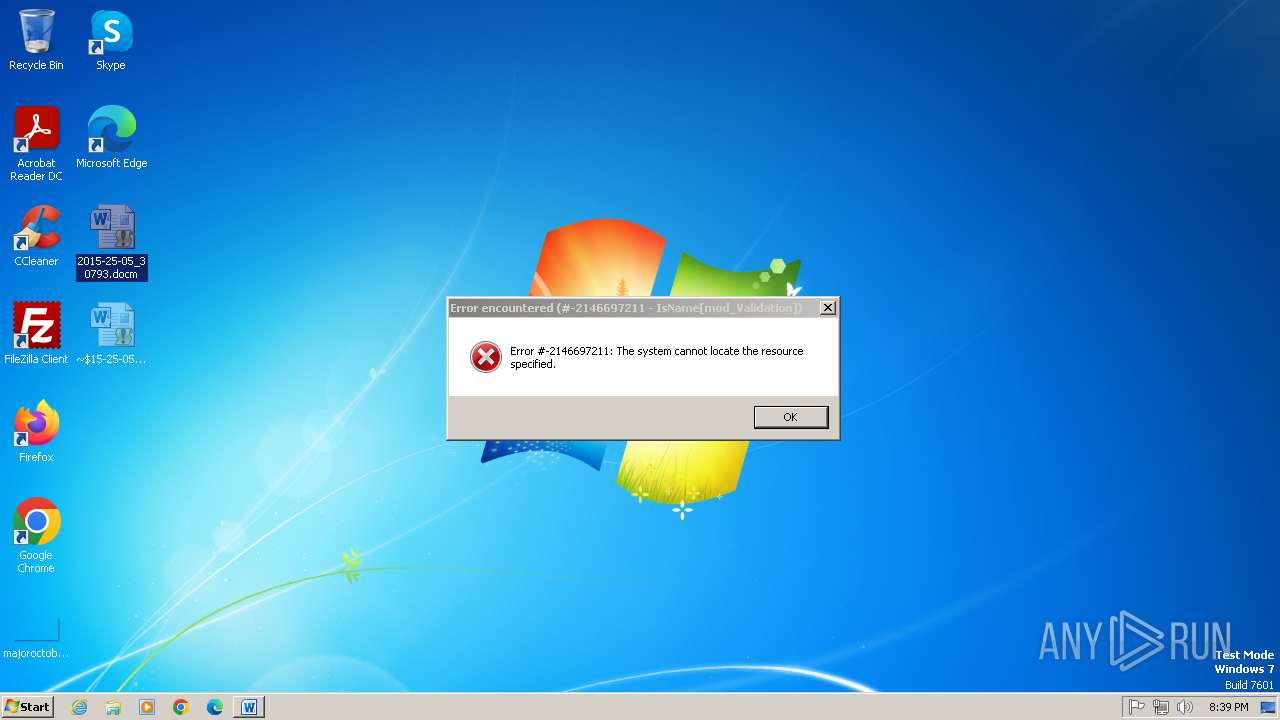
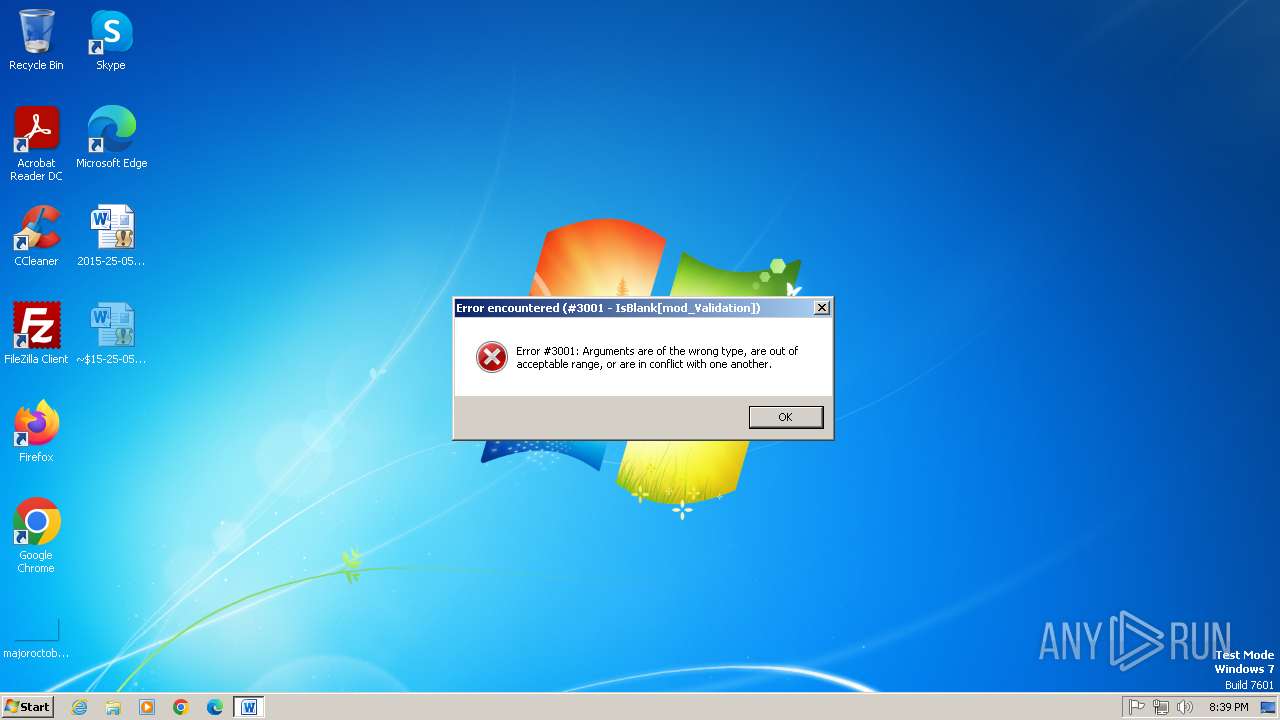
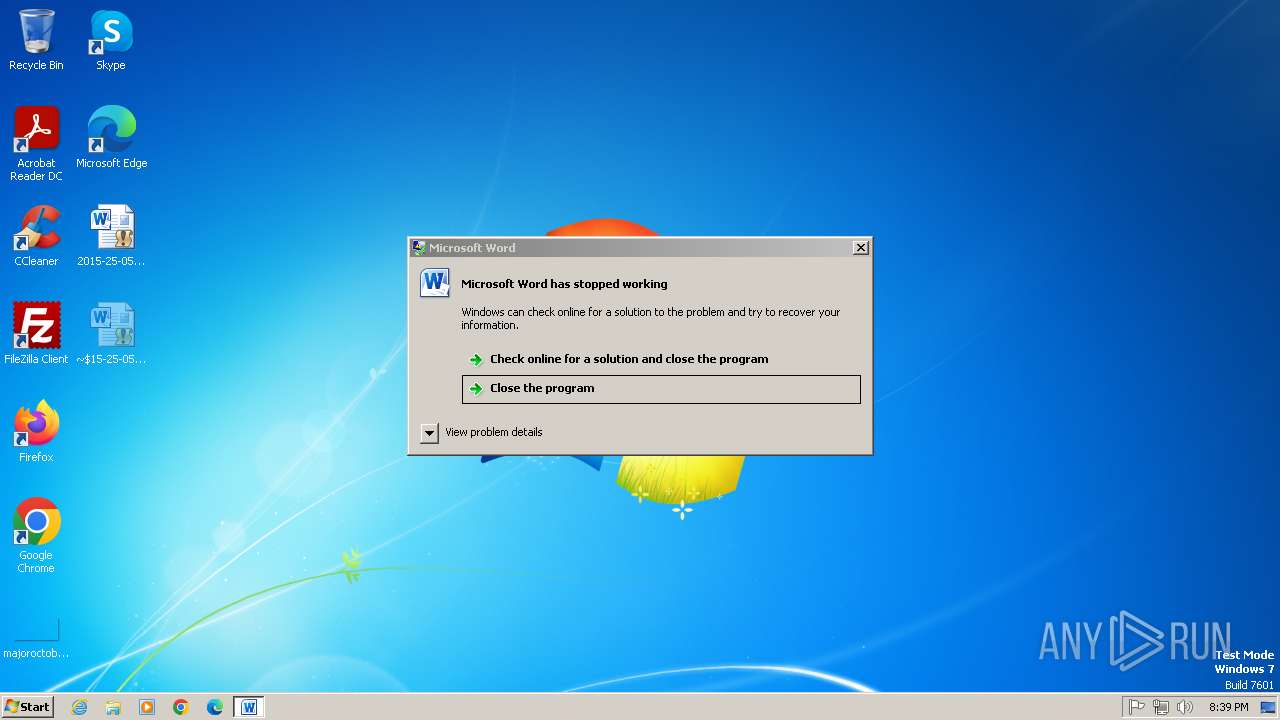
| File name: | 2015-25-05_30793.docm |
| Full analysis: | https://app.any.run/tasks/2389d697-72d5-4da1-9ece-e90d5f2a8300 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2025, 20:39:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | EEC1137E2F6A8C335DC4AD95E89138CA |
| SHA1: | E29945A203A6026DB3CE54AD888902DC7203F3F4 |
| SHA256: | D58EEF794DC08E1D1B24B437C091182A28432AA75188189F76E97A9A3C9D1294 |
| SSDEEP: | 1536:/jxA5+a1Py77FAcfkHuEwLz51+h85rjD2sk:/jDauLfkH6Lt1+h8gsk |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- WINWORD.EXE (PID: 2676)
Creates internet connection object (SCRIPT)
- WINWORD.EXE (PID: 2676)
Sends HTTP request (SCRIPT)
- WINWORD.EXE (PID: 2676)
Unusual execution from MS Office
- WINWORD.EXE (PID: 2676)
SUSPICIOUS
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- WINWORD.EXE (PID: 2676)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 2676)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 2676)
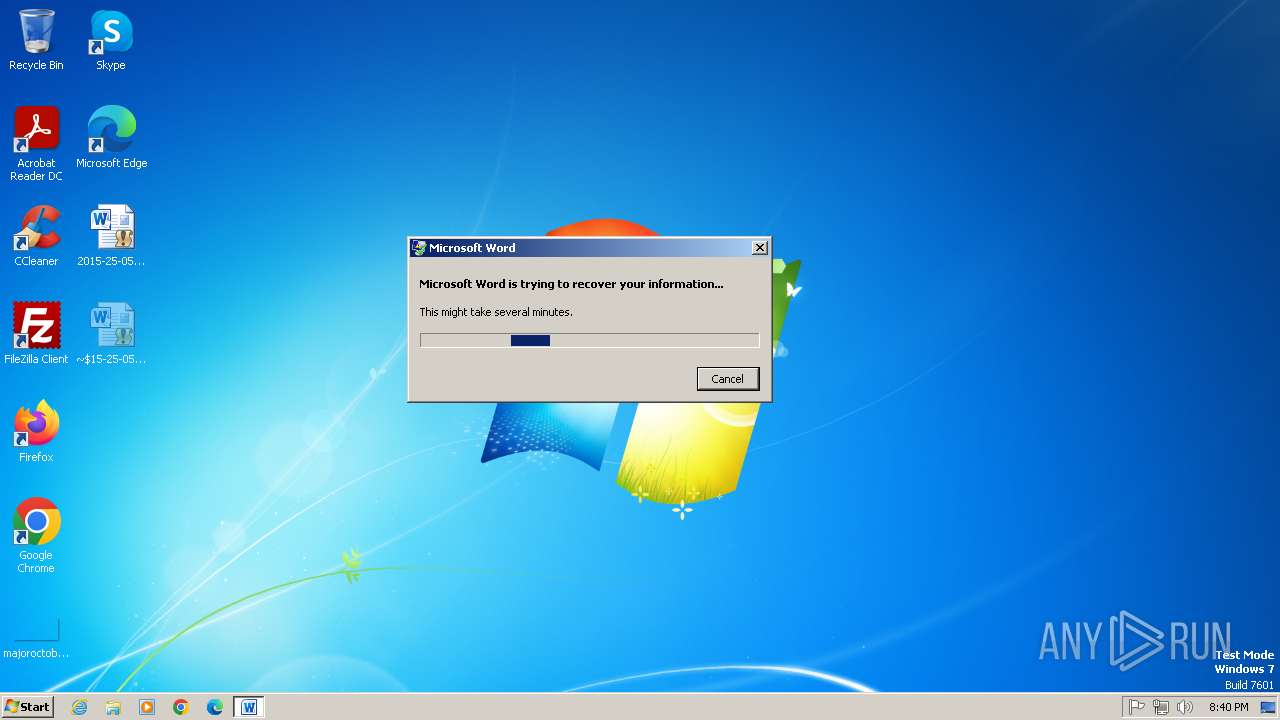
An automatically generated document
- WINWORD.EXE (PID: 2676)
Matches regexp pattern (SCRIPT)
- WINWORD.EXE (PID: 2676)
Manual execution by a user
- WINWORD.EXE (PID: 1824)
Checks supported languages
- DW20.EXE (PID: 3104)
Creates files or folders in the user directory
- DWWIN.EXE (PID: 2960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x4dc12e6a |
| ZipCompressedSize: | 419 |
| ZipUncompressedSize: | 1563 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | 1 |
|---|
XML
| LastModifiedBy: | 1 |
|---|---|
| RevisionNumber: | 2 |
| CreateDate: | 2016:05:25 10:51:00Z |
| ModifyDate: | 2016:05:25 10:51:00Z |
| Template: | Normal |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | - |
| Paragraphs: | - |
| ScaleCrop: | No |
| Company: | Home |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1824 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\2015-25-05_30793.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2676 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\2015-25-05_30793.docm.docx | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2960 | C:\Windows\system32\dwwin.exe -x -s 2304 | C:\Windows\System32\DWWIN.EXE | — | DW20.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Watson Client Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3104 | "C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE" -x -s 2304 | C:\Program Files\Common Files\microsoft shared\DW\DW20.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Application Error Reporting Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
Total events
8 326
Read events
7 094
Write events
647
Delete events
585
Modification events
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 740A00001C9778246A90DB0100000000 | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\Themes\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\WordDocParts\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\SmartArt\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: | |||
| (PID) Process: | (2676) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ft% |
Value: 66742500740A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
Executable files
1
Suspicious files
12
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1604.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1824 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA786.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2960 | DWWIN.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_WINWORD.EXE_a8bd75d32469daa4c1e826c2e8e91c8a2cac2d_0b8901db\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:8ADE243EED316584576E1C6C0E5A9806 | SHA256:9748F6F9570D72ADE74A45A147F3921A441534C47B18217C69E15C67D495DFA6 | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\2015-25-05_30793.docm.LNK | binary | |
MD5:C9954DF78C67D8FB83AE8819410D41C3 | SHA256:40E1C0F3E3C7681E20CCC0590034DB85E00DAC18F5CB912DF3FD281DC5766305 | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:DC03E5E65D4850720F5E8F231D2C2AE8 | SHA256:71A98FD8D47D6A1F9461E2FDF335524BAC73152934C77FE8989F89B1132F44AB | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$15-25-05_30793.docm.docx | binary | |
MD5:68B378CEDA2BD0FD97F1DD786B2882C0 | SHA256:BC20902FE6F97C00F72836DC6148BEAC1B054CE1CDBC669D9A59D6A30AD80AE8 | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:04685443DF4F766621910AC9A8B61CF4 | SHA256:5C5FB74BA201235BF57B2116EECCB527C45EB502E75F4C925256083CF3905D7C | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{DCCFC062-5103-4039-8784-2F74A14C3CA7}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2676 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{469C6FF6-6EBF-407E-95C1-23D8CEEF0A63}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
2676 | WINWORD.EXE | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
2676 | WINWORD.EXE | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2676 | WINWORD.EXE | 23.35.238.131:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
2676 | WINWORD.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
majaz.co.uk |
| unknown |