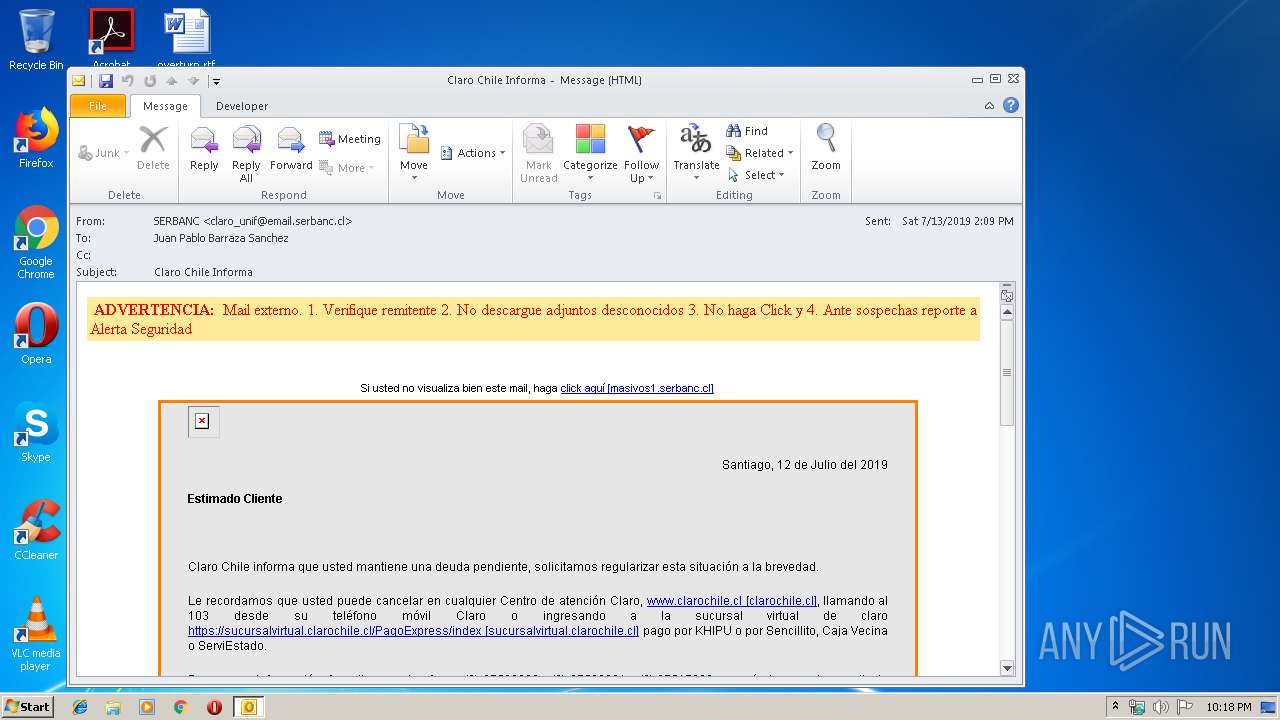
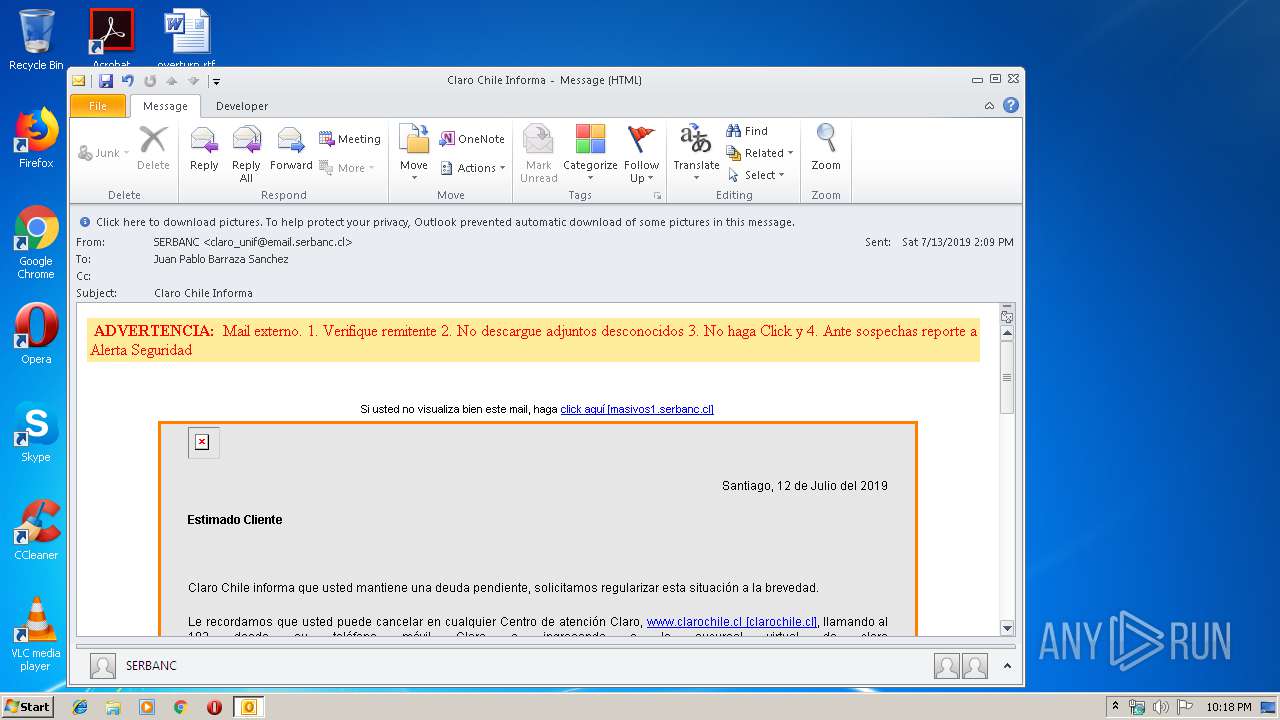
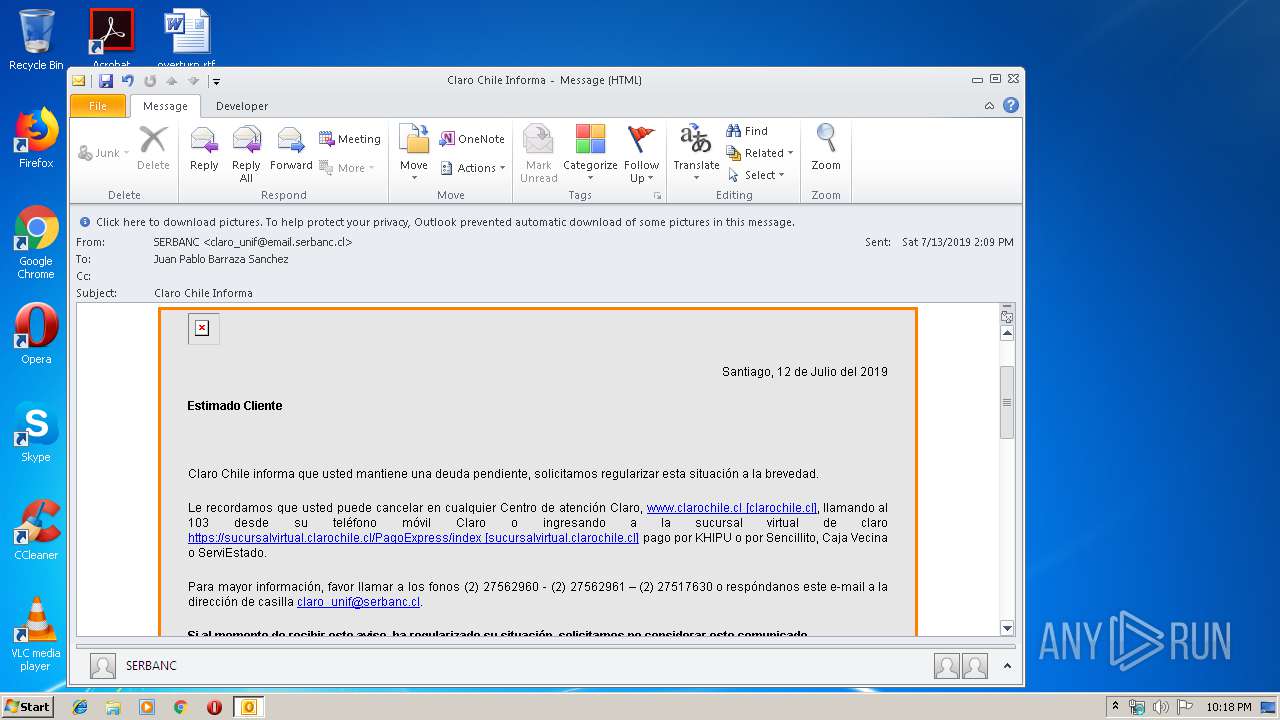
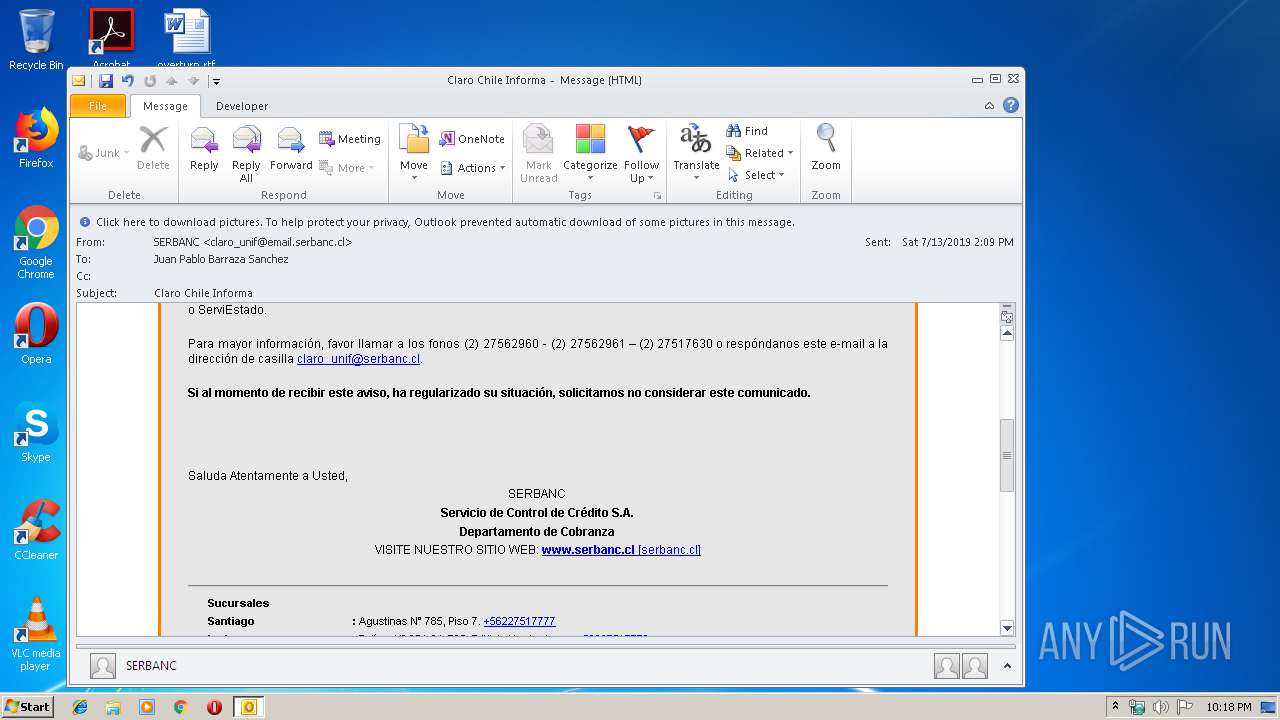
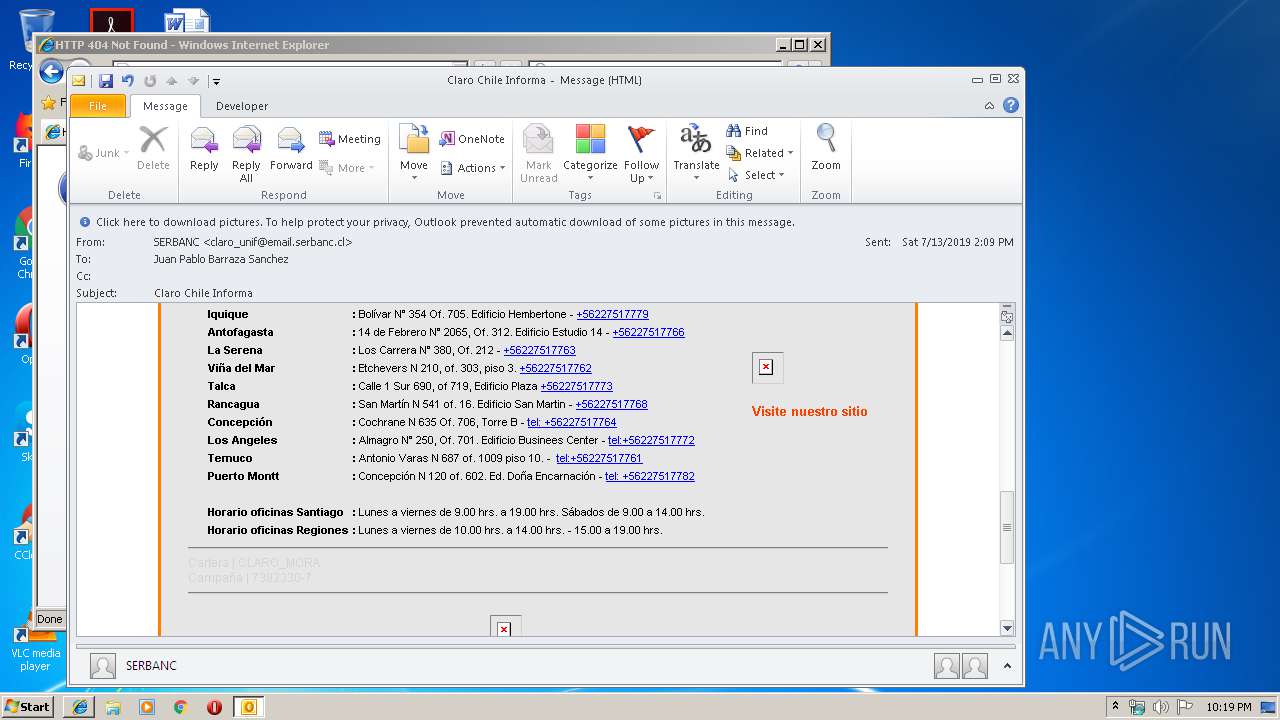
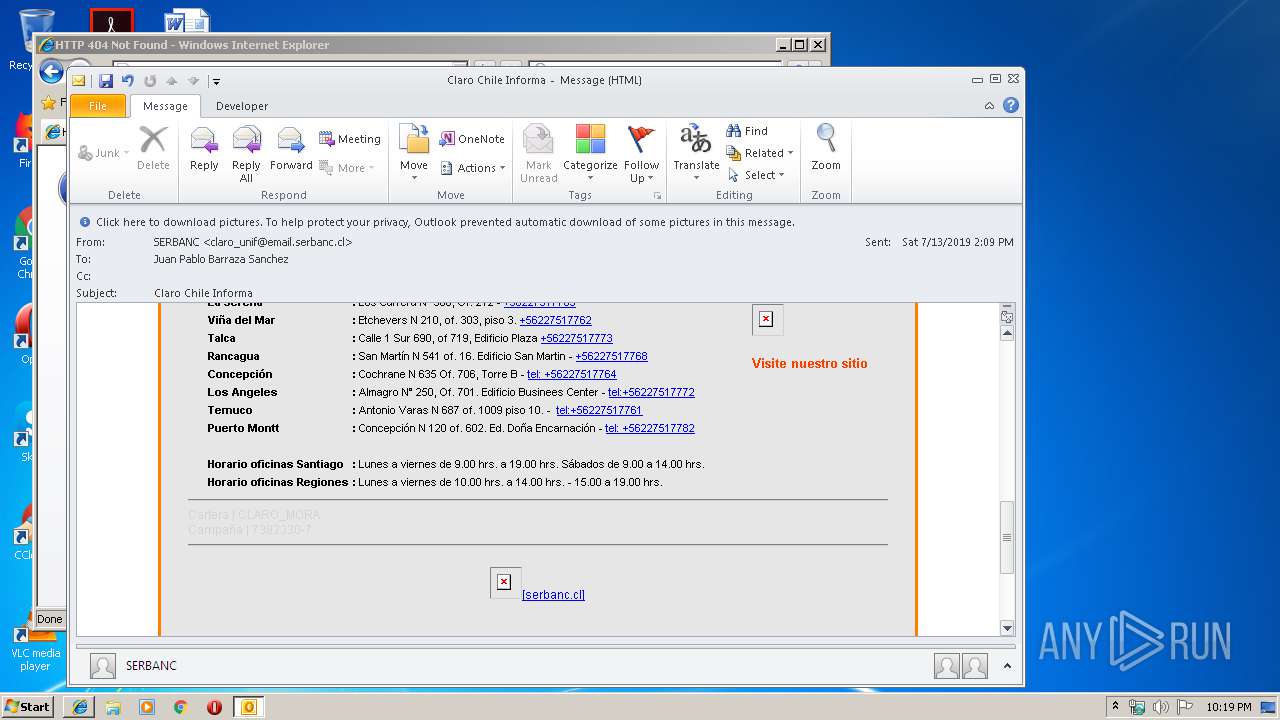
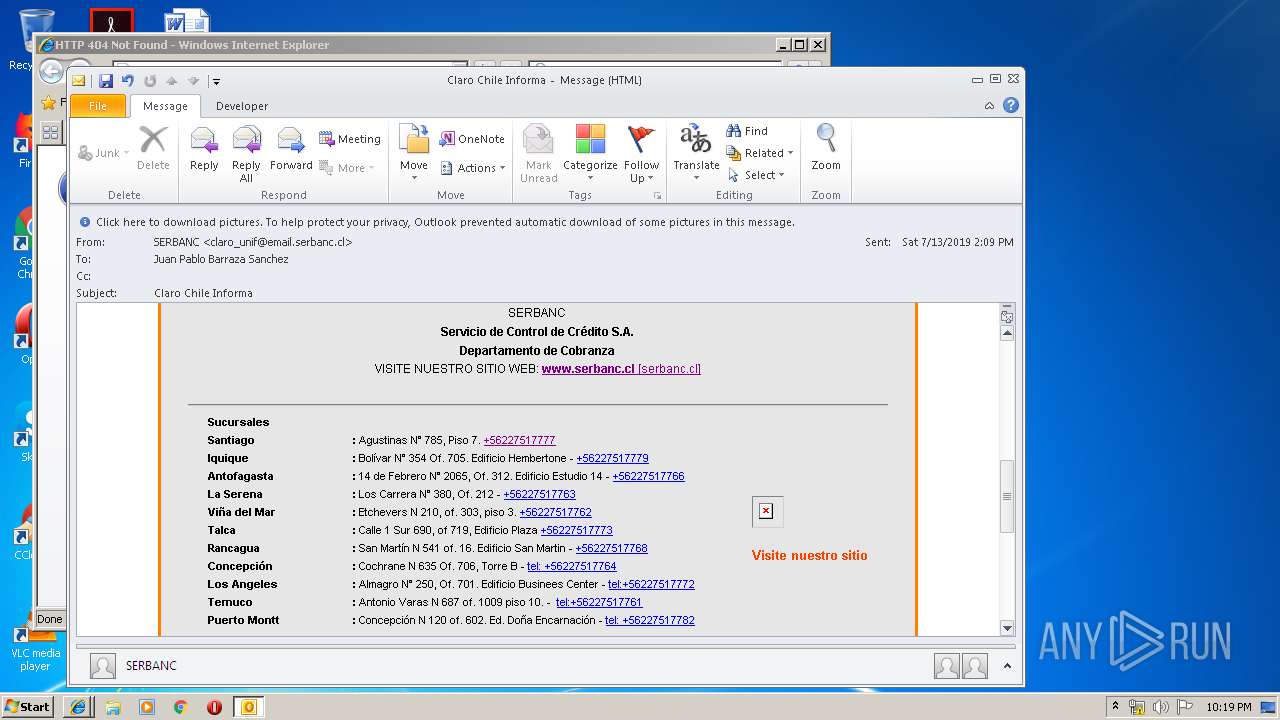
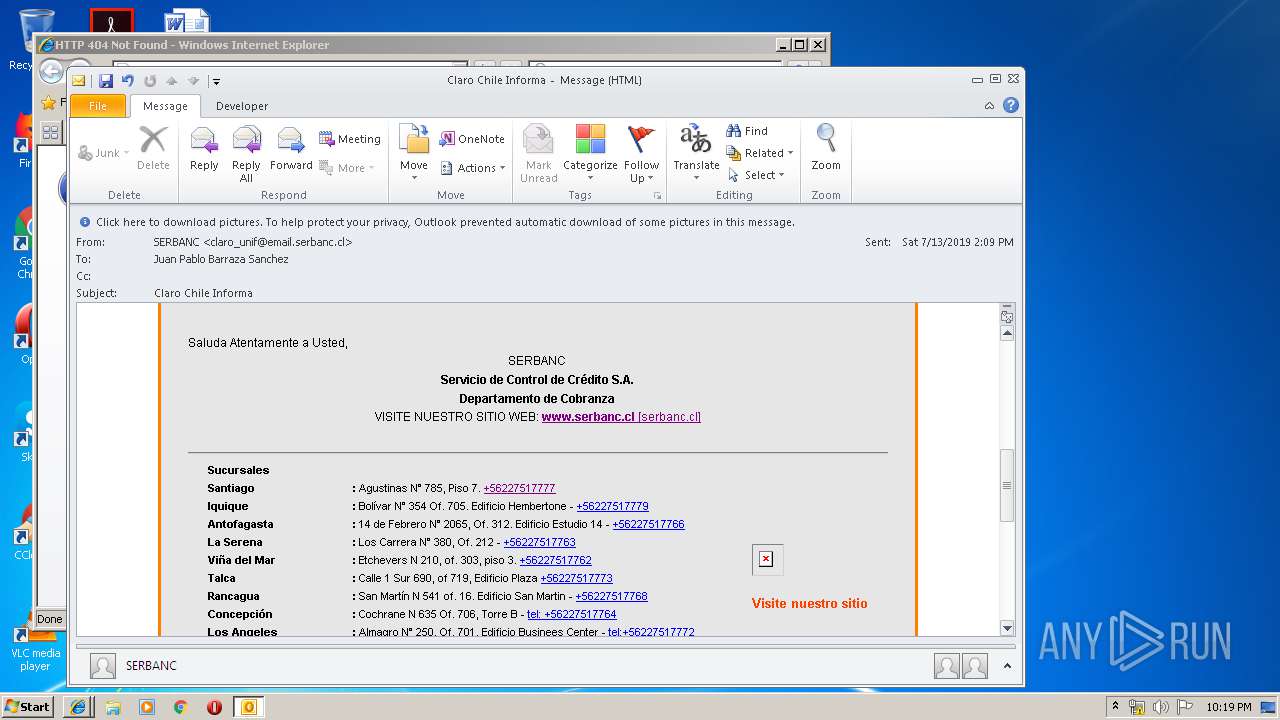
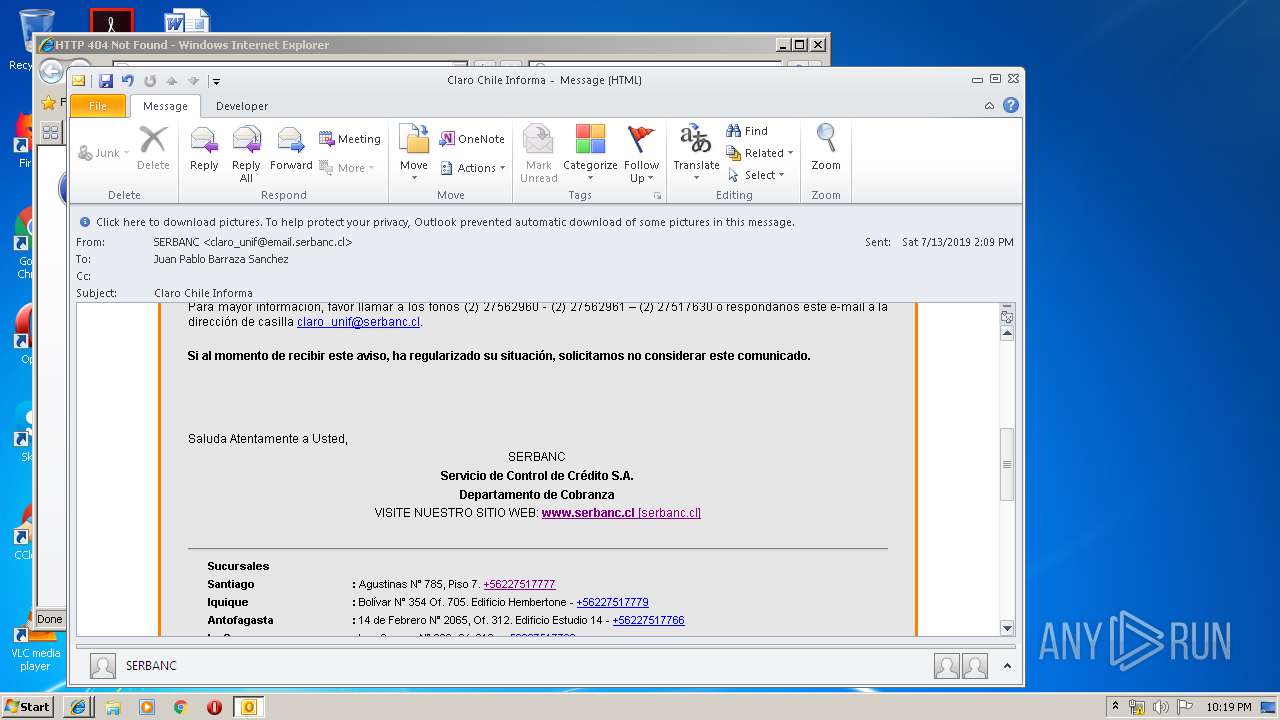
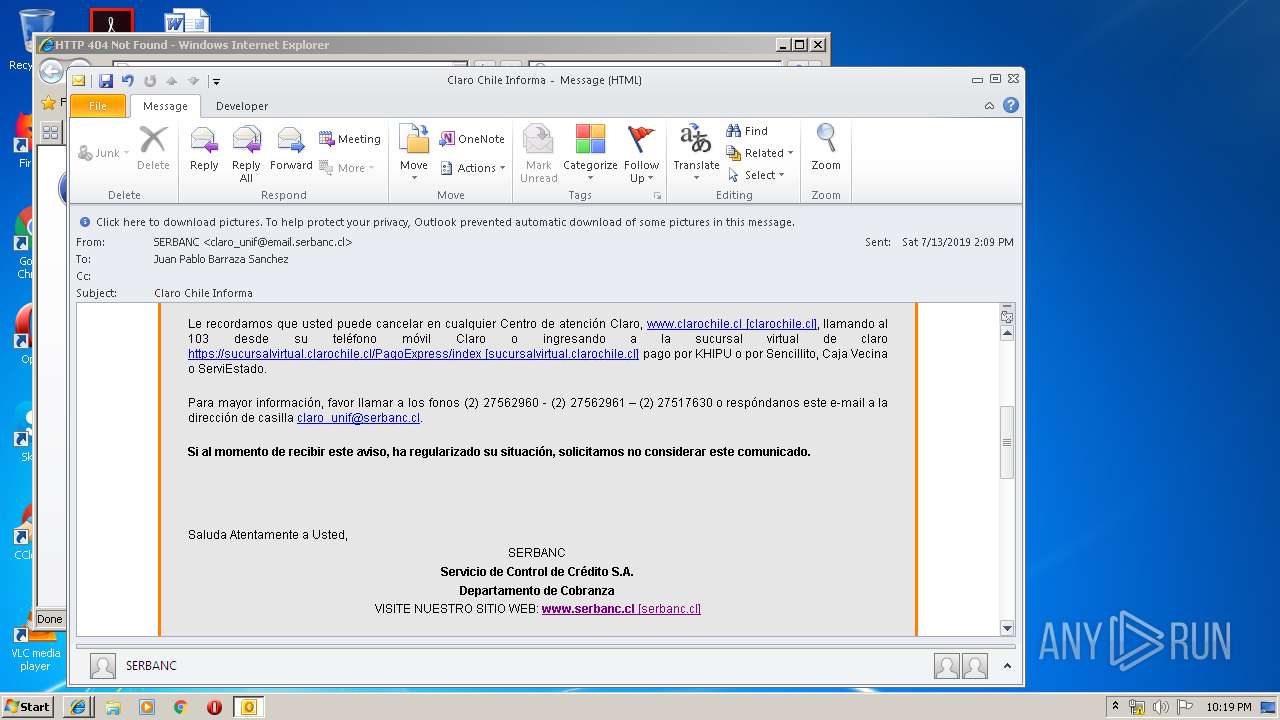
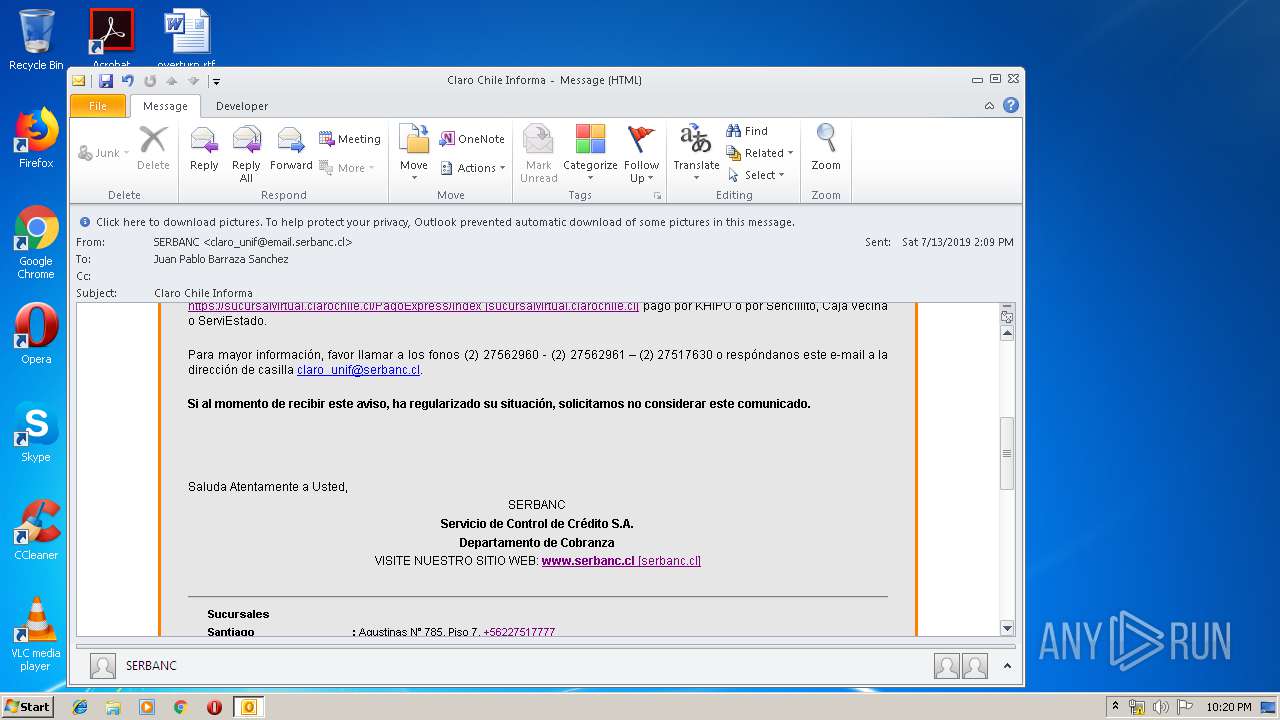
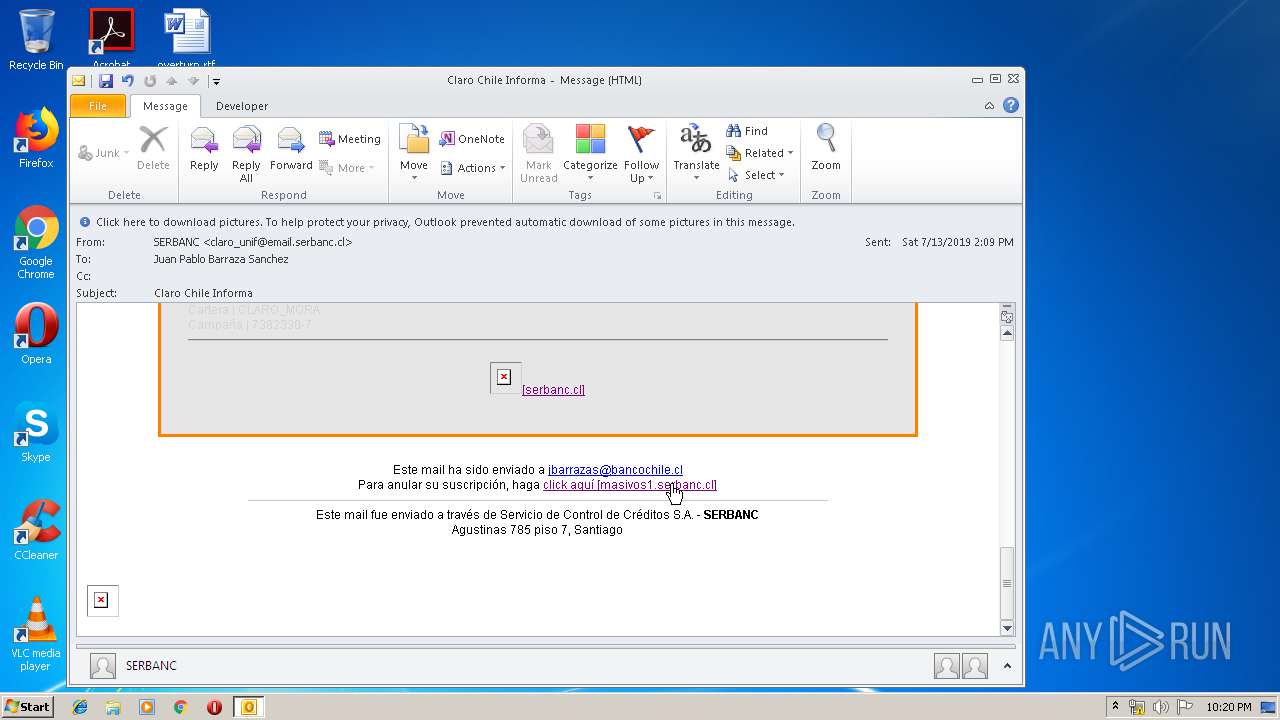
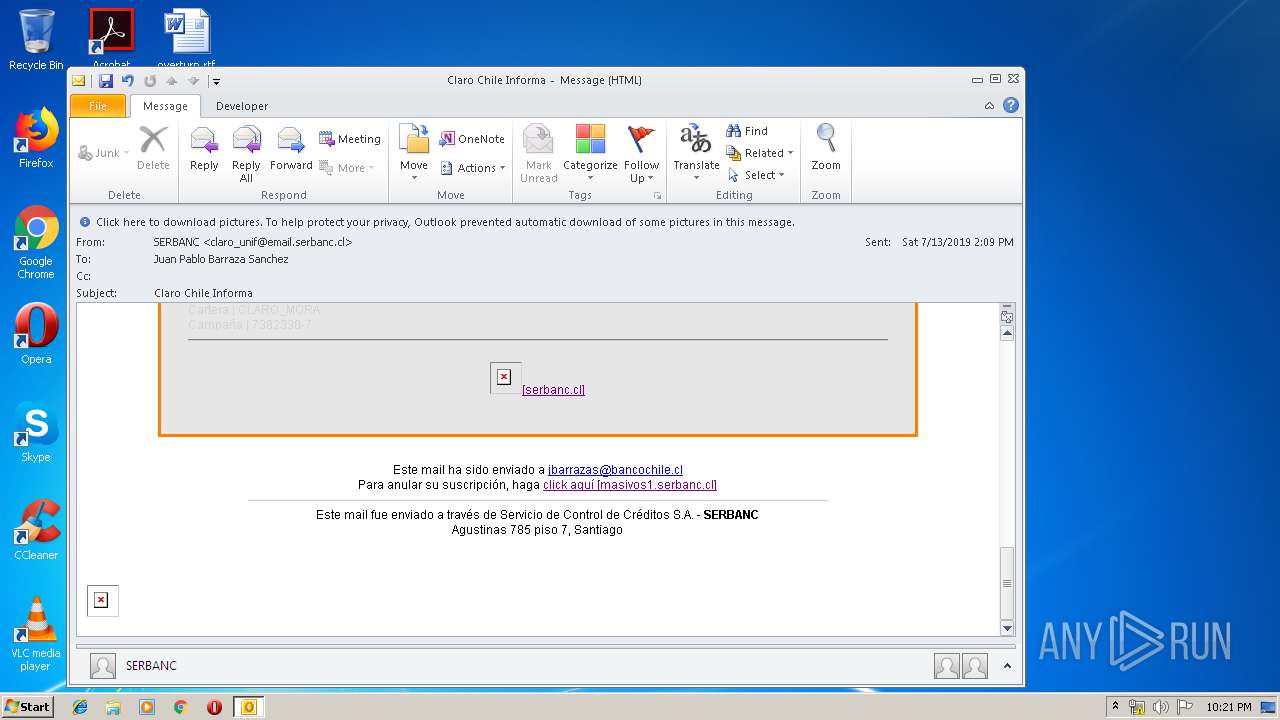
| File name: | Claro Chile Informa.msg |
| Full analysis: | https://app.any.run/tasks/8ded2e69-fb11-420c-835c-a3e6a5583048 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 21:18:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | A3935E93C946E9A9003C21AFE55AF9FD |
| SHA1: | A0D264E064F561FF81C87833F29327477489D75D |
| SHA256: | D589255CF335A23AEF08C536CE4B564D127BAC66F10281116CF44C8677BBA453 |
| SSDEEP: | 768:Bzkzr9VP45s60NLxgKSIknZ/0hWmT4K6Cef/zFC4JO9sKAsEOWRRg224zMAisKA1:VOAWhWTKHe5YYOWwpTYmOX |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3708)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3708)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3708)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3708)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3172)
Uses RUNDLL32.EXE to load library
- OUTLOOK.EXE (PID: 3708)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3464)
- iexplore.exe (PID: 1316)
Application launched itself
- iexplore.exe (PID: 3464)
- AcroRd32.exe (PID: 3216)
Creates files in the user directory
- iexplore.exe (PID: 2592)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3172)
- iexplore.exe (PID: 2084)
- iexplore.exe (PID: 128)
- iexplore.exe (PID: 3464)
Reads Internet Cache Settings
- iexplore.exe (PID: 2592)
- iexplore.exe (PID: 2084)
- iexplore.exe (PID: 128)
- iexplore.exe (PID: 996)
Reads internet explorer settings
- iexplore.exe (PID: 2592)
- iexplore.exe (PID: 2084)
- iexplore.exe (PID: 128)
- iexplore.exe (PID: 996)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3708)
Reads settings of System Certificates
- iexplore.exe (PID: 3464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
51
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3464 CREDAT:6406 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1316 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
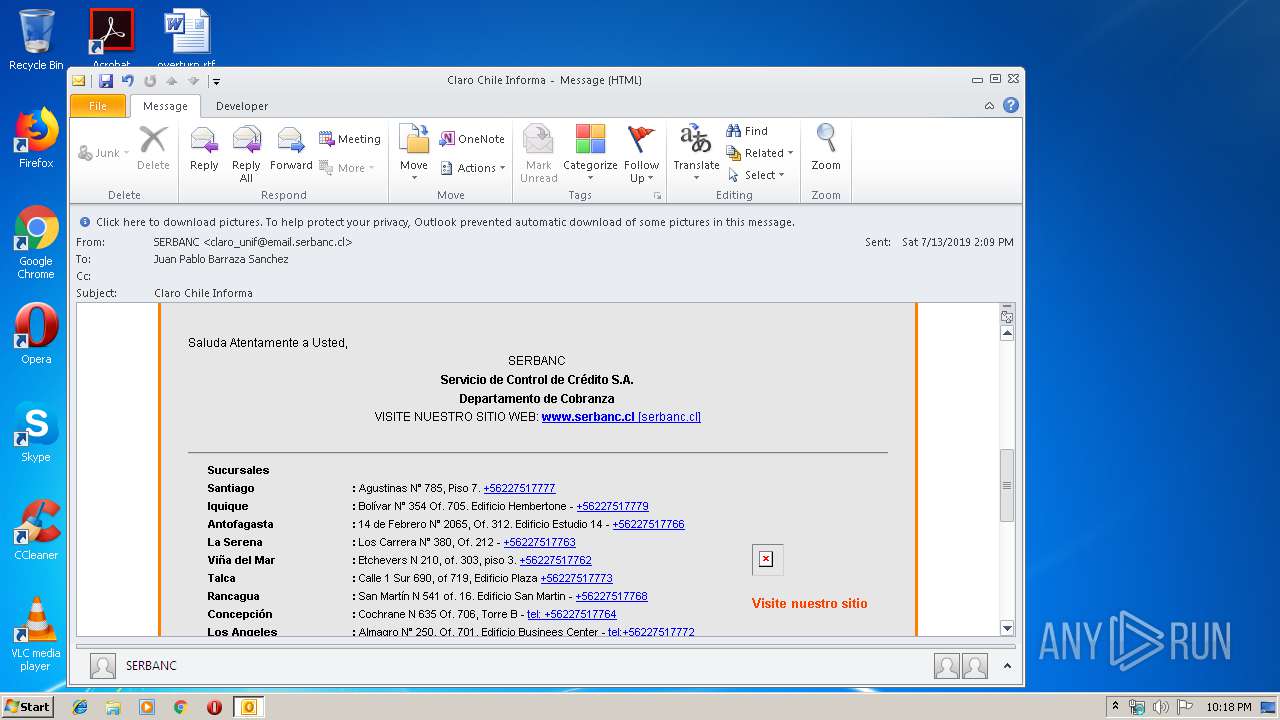
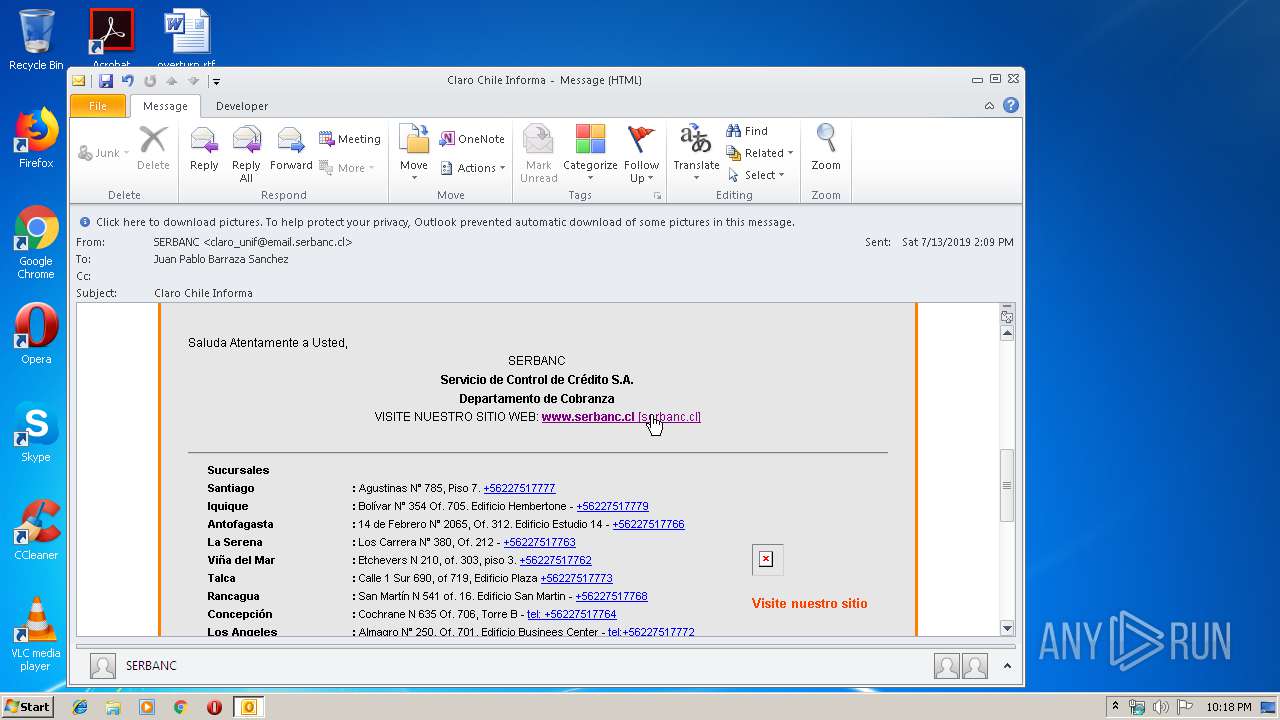
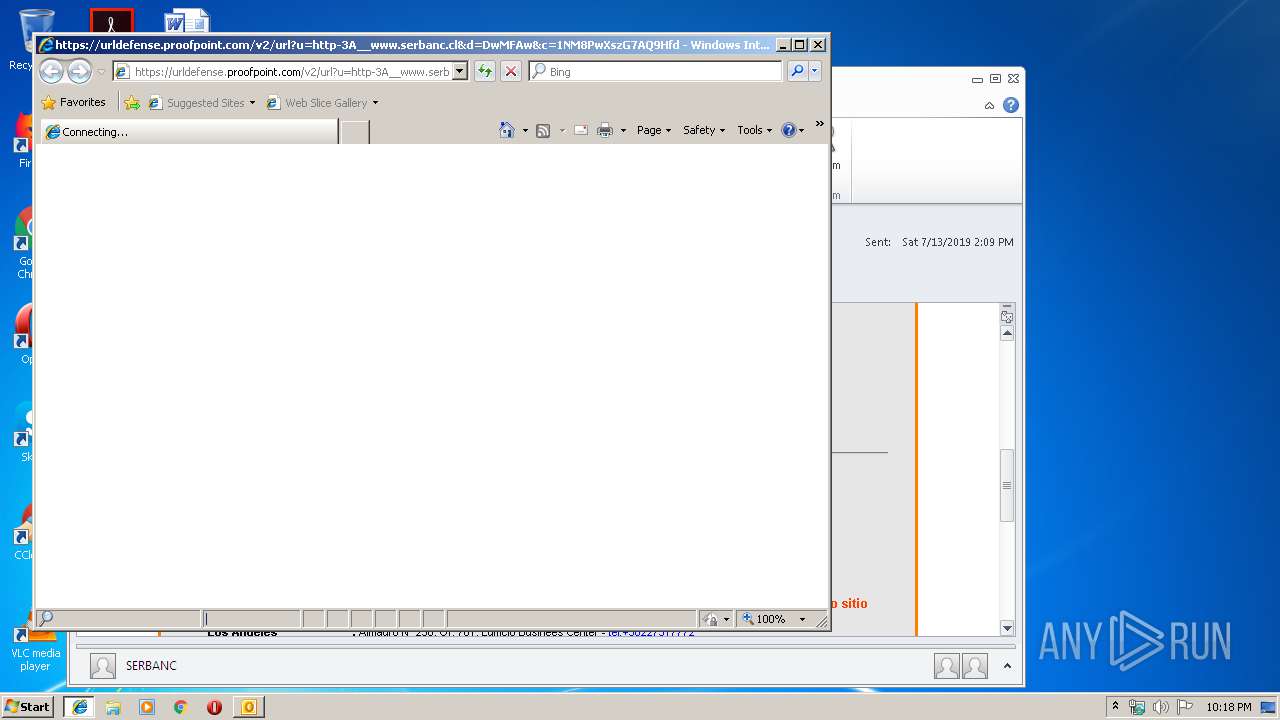
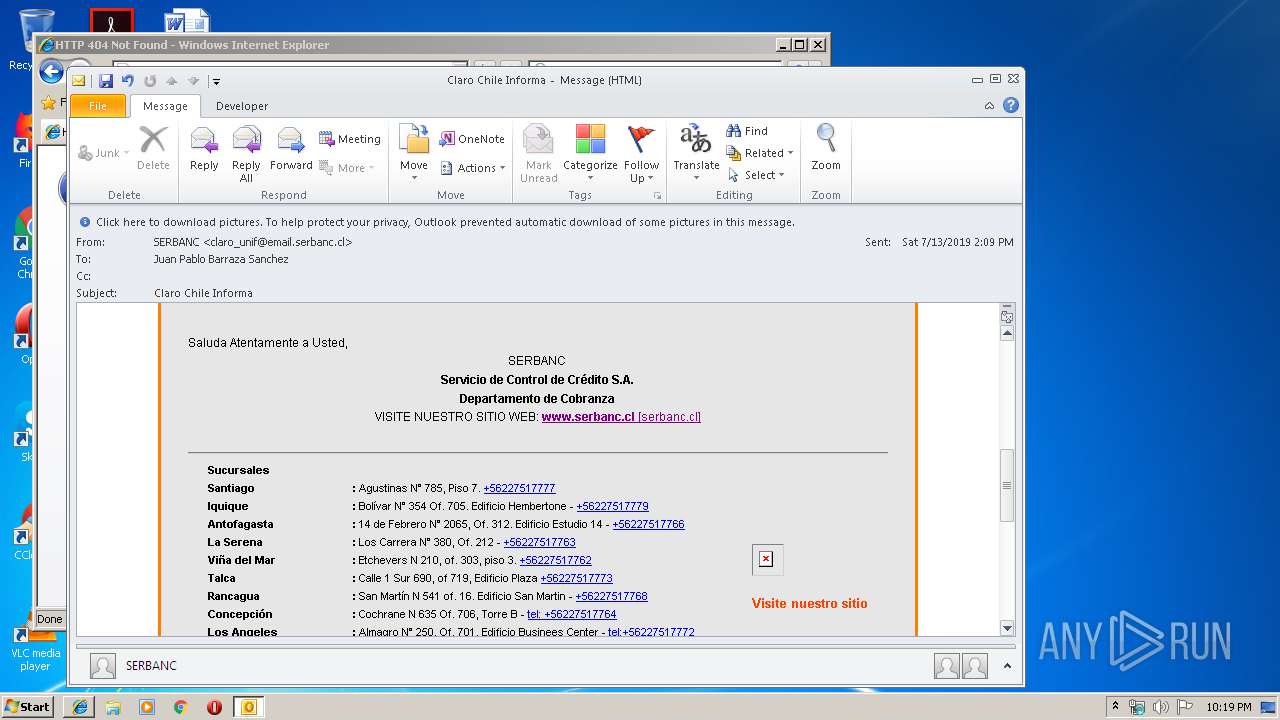
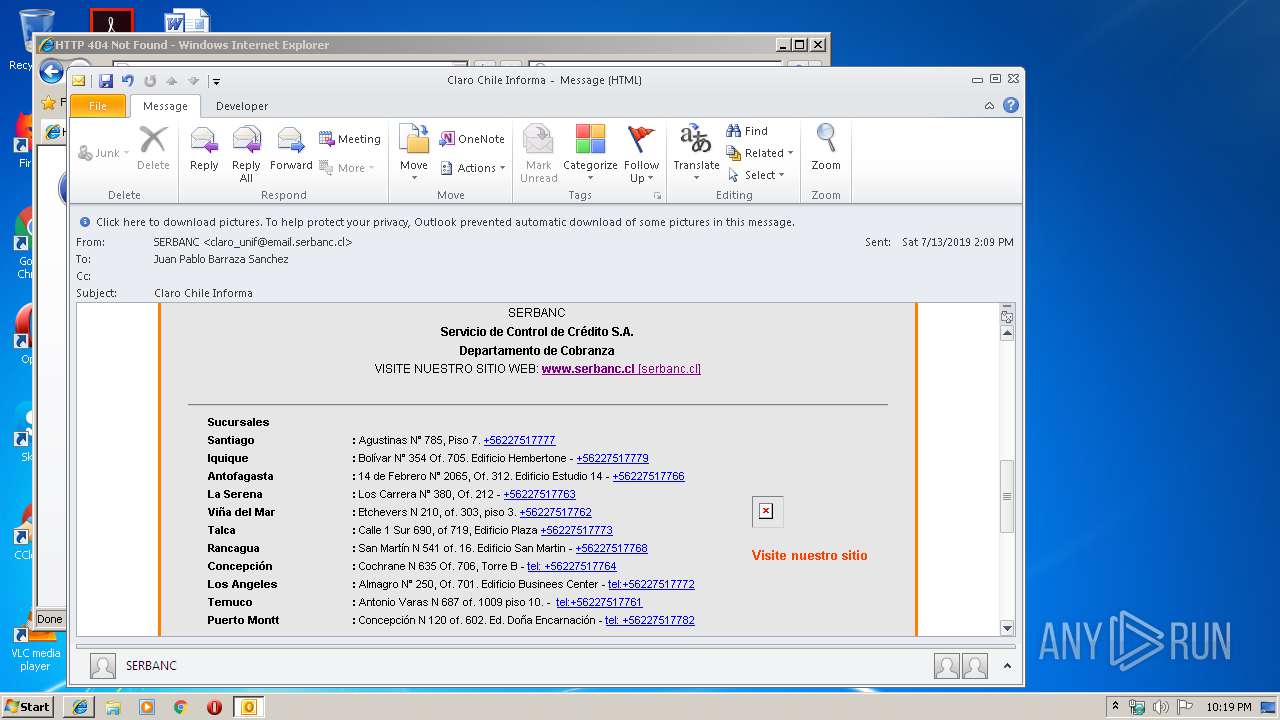
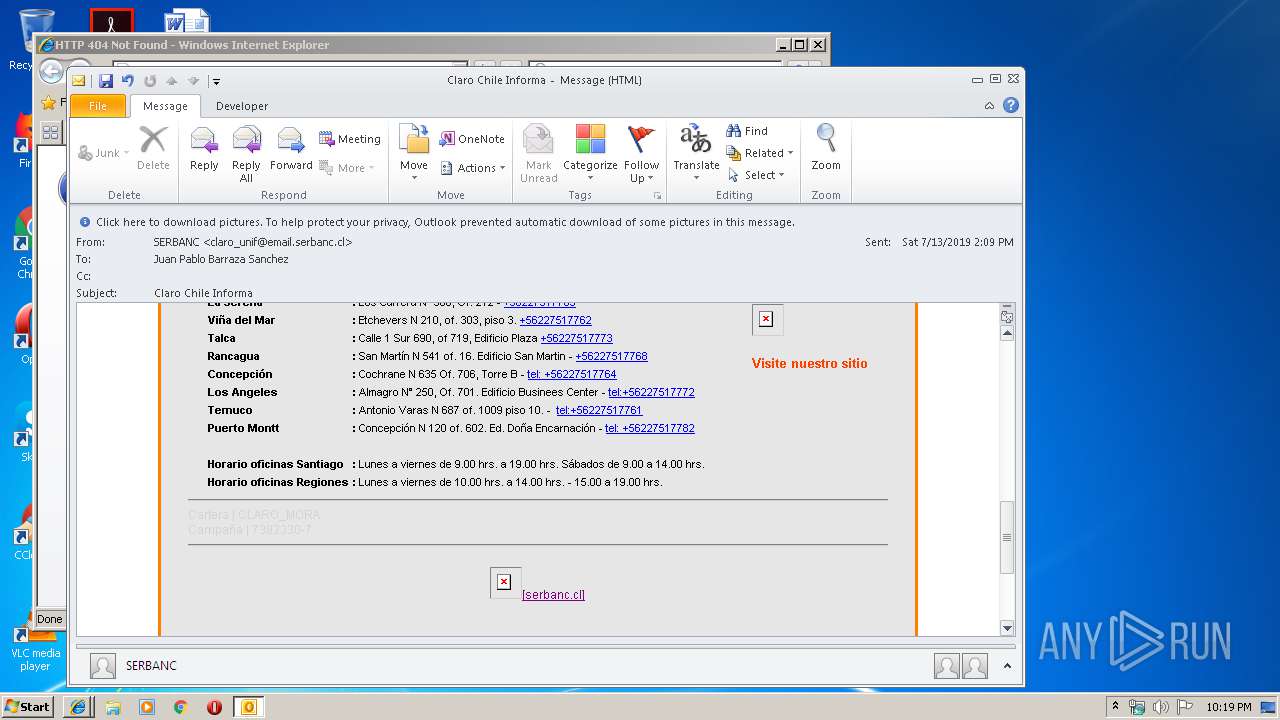
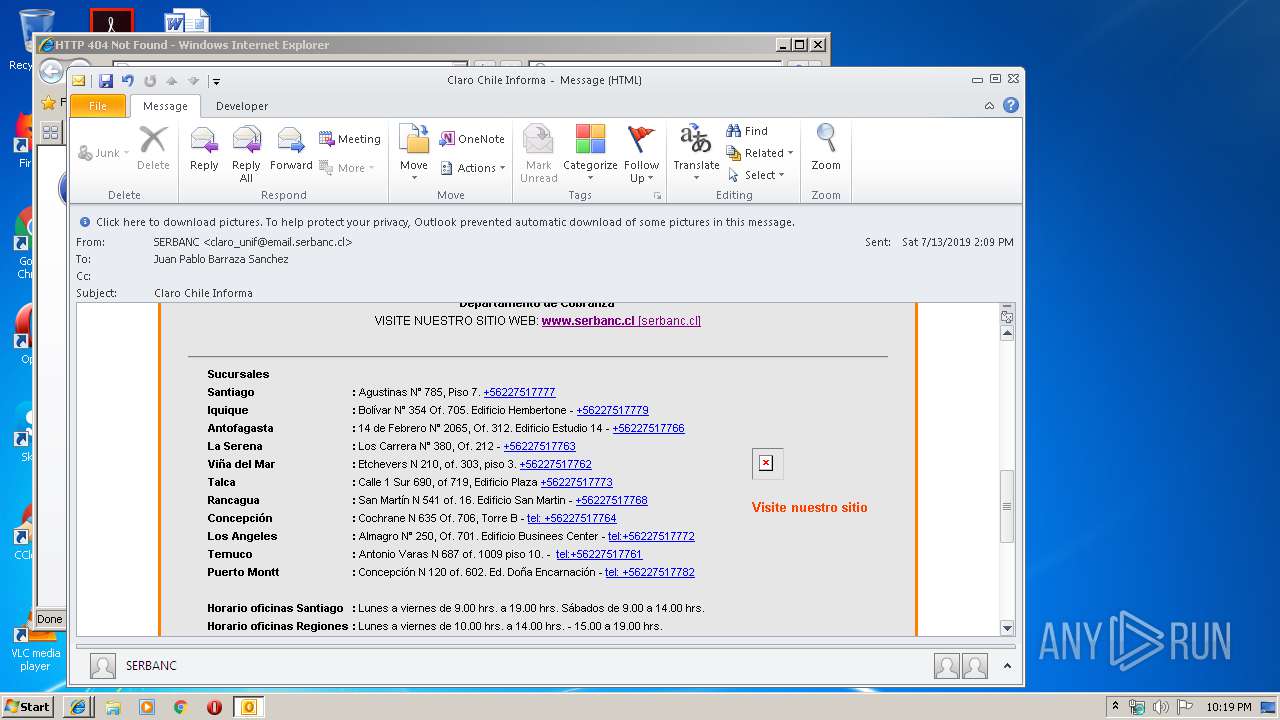
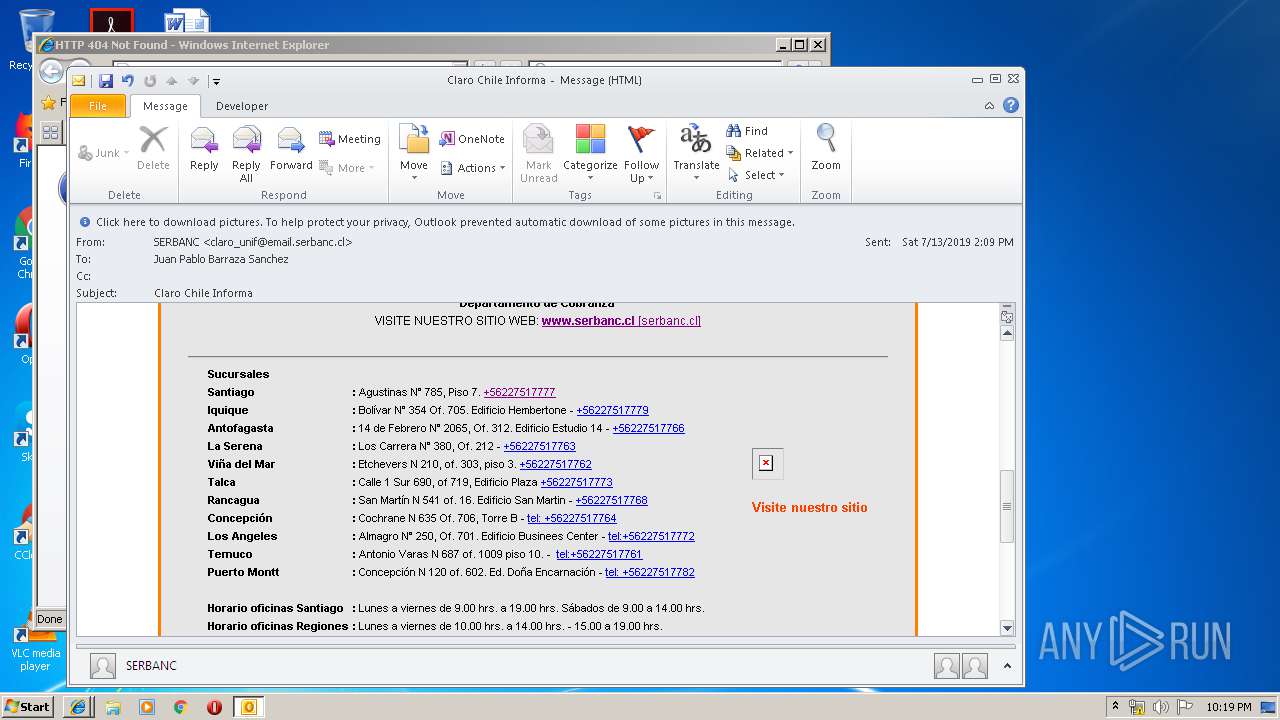
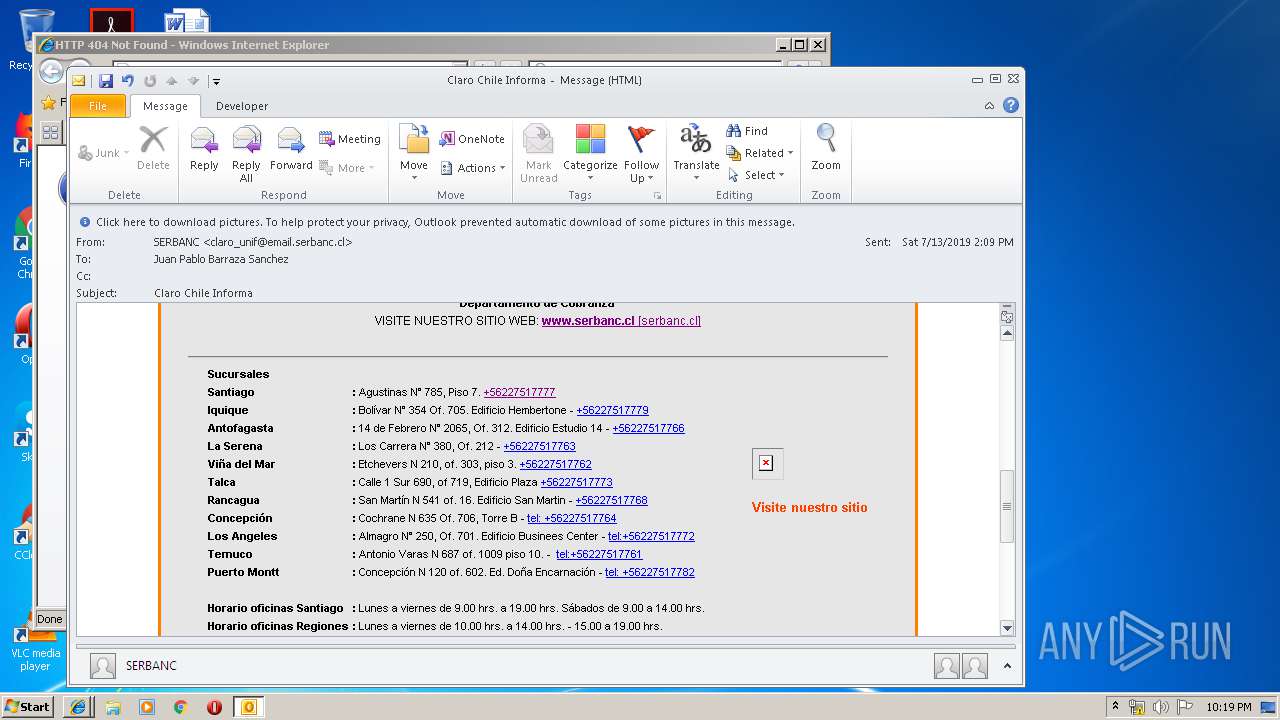
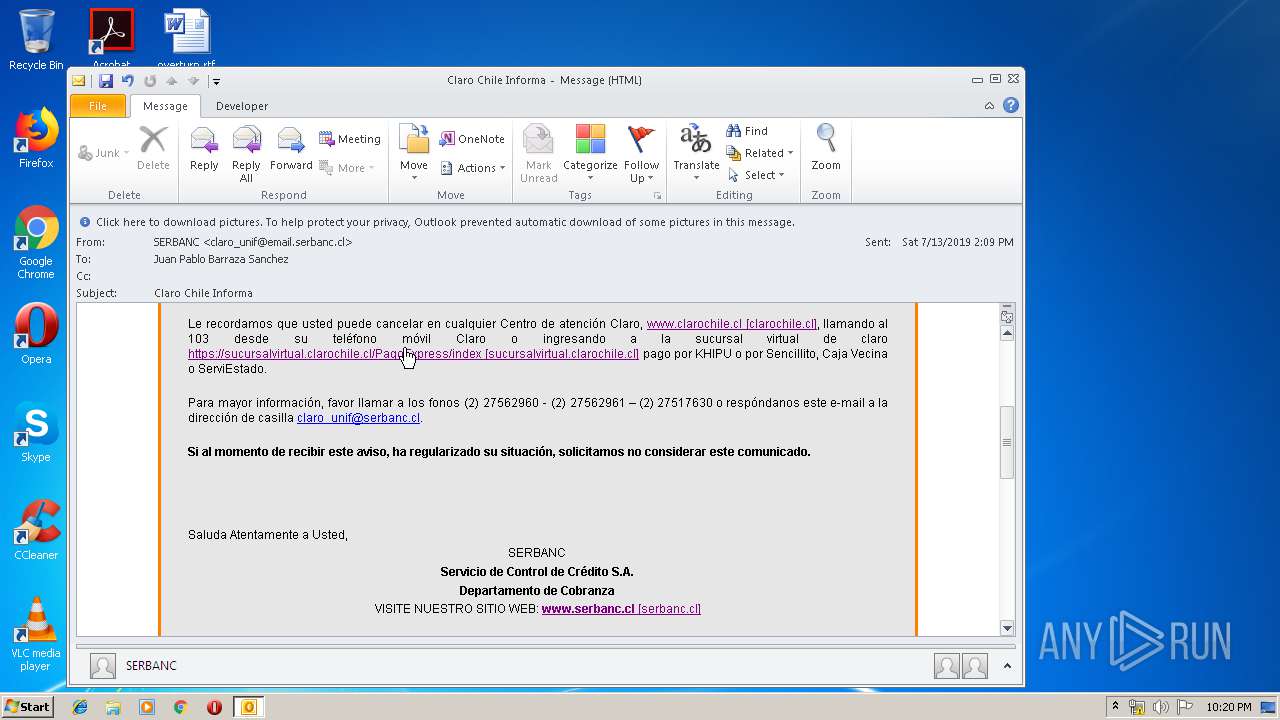
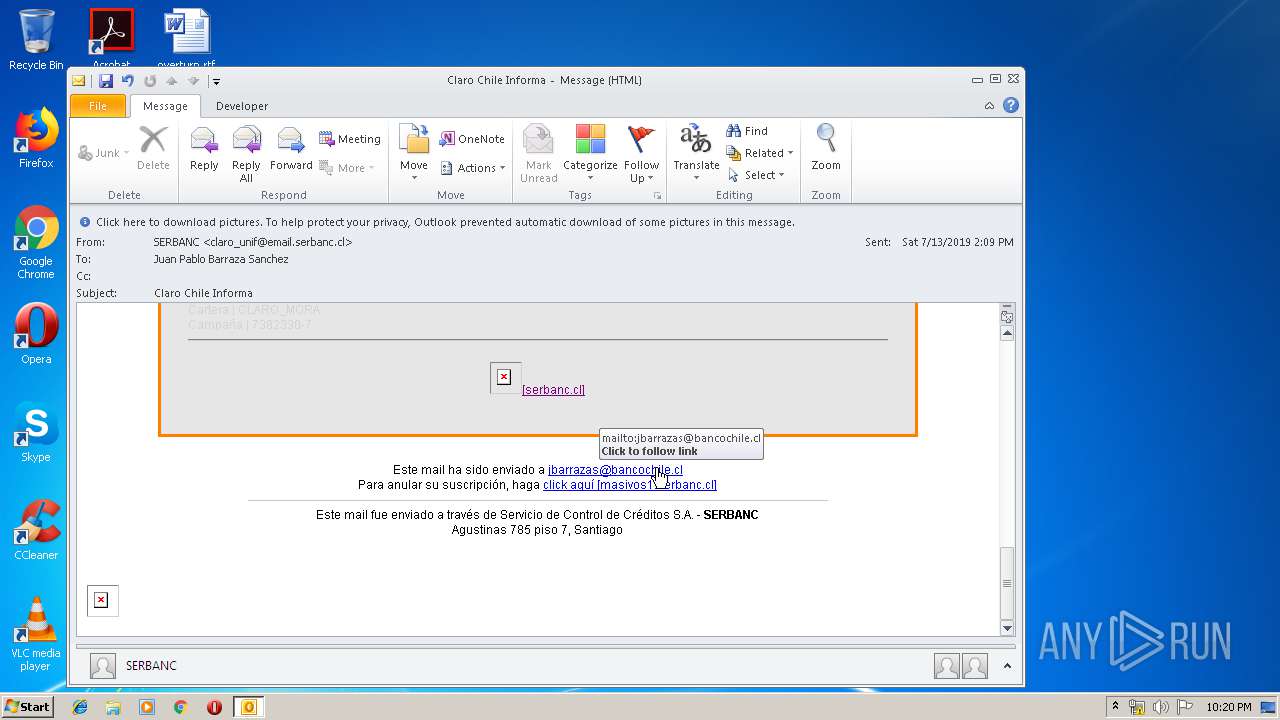
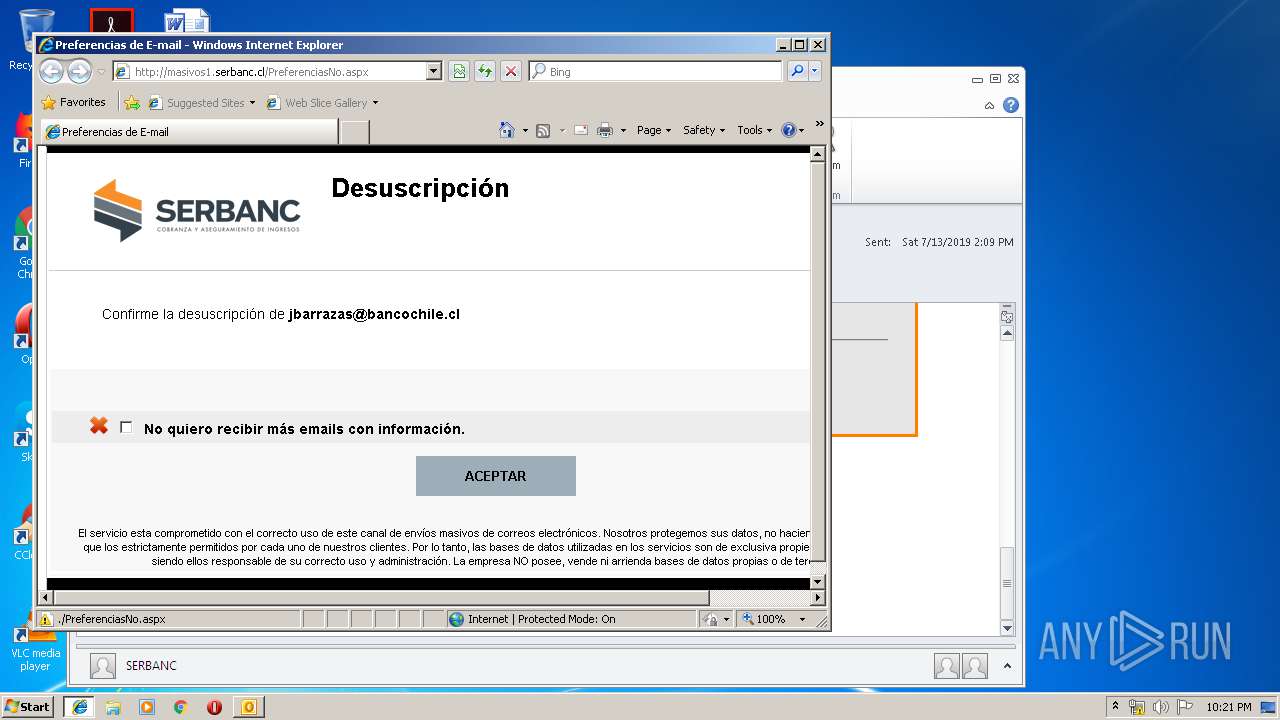
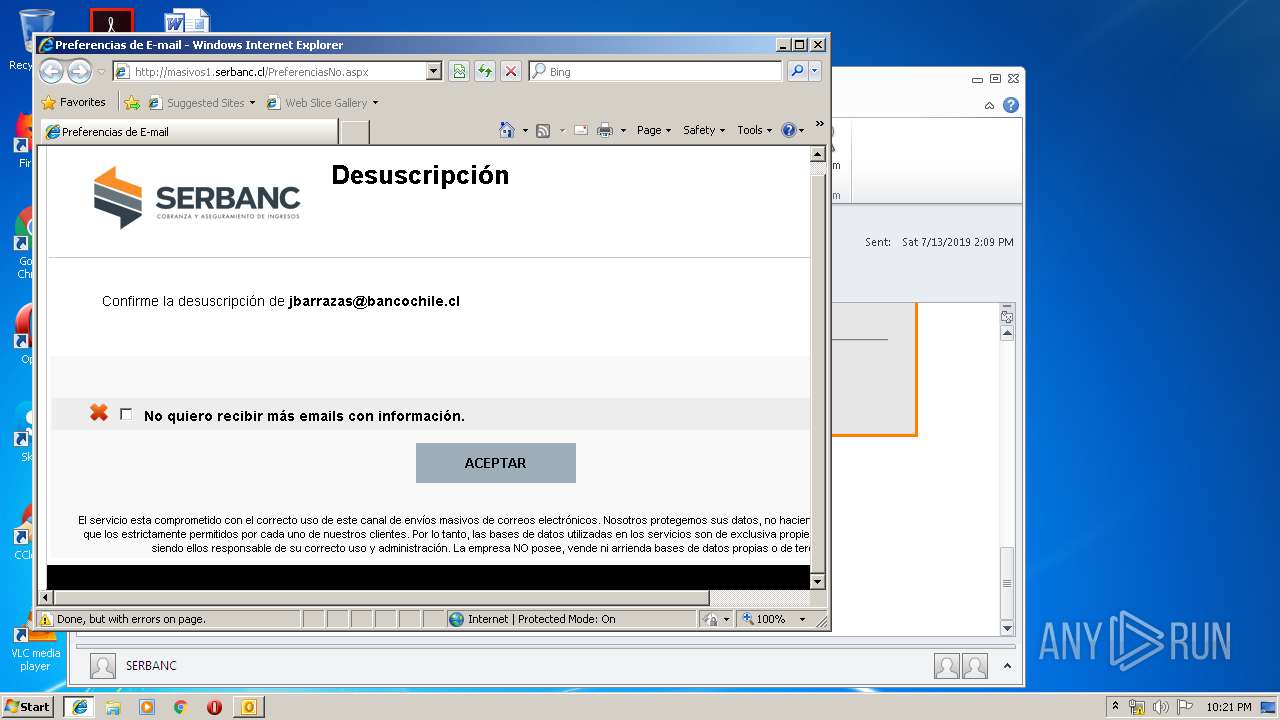
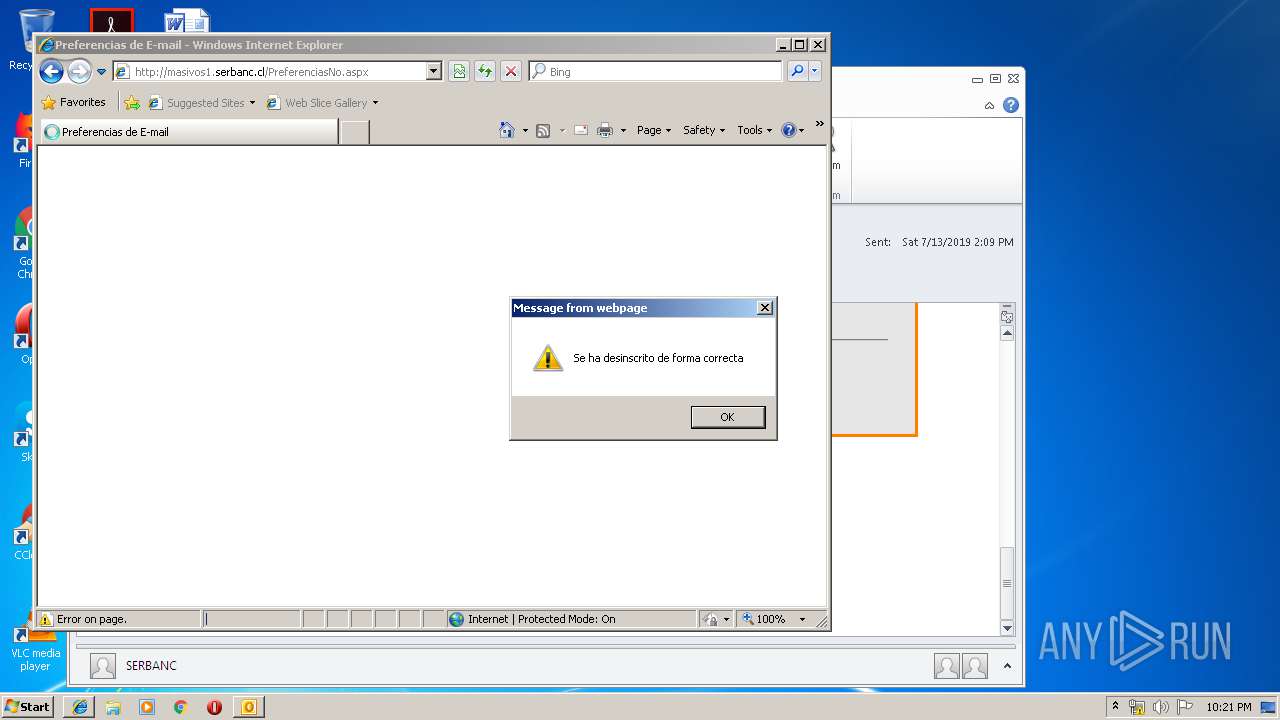
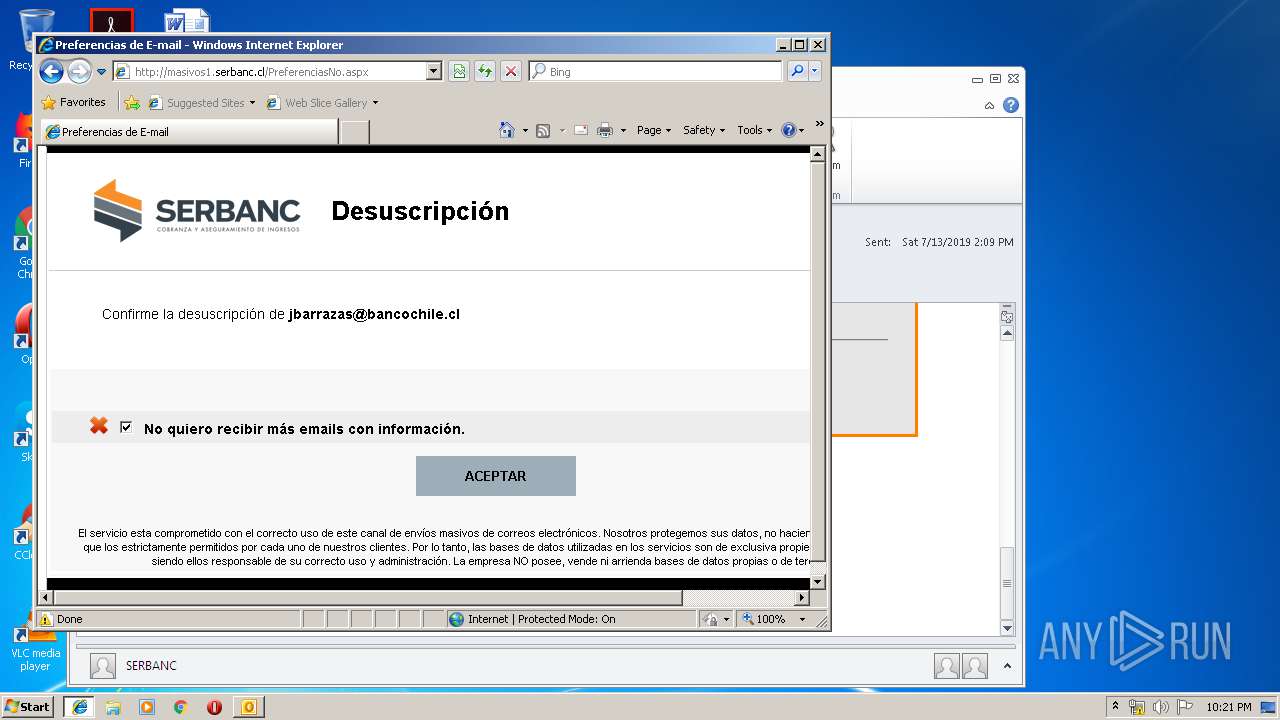
| 1316 | "C:\Program Files\Internet Explorer\iexplore.exe" https://urldefense.proofpoint.com/v2/url?u=http-3A__masivos1.serbanc.cl_Preferencia.aspx-3Fid-5Fenvio-3D419661624-26email-3Djbarrazas-40bancochile.cl&d=DwMFAw&c=1NM8PwXszG7AQ9HfdmWbEEMkVRRTYdMYEy55pO9feSo&r=94iIEJXDvHwuAiJ60lGeTTH577QkmKPRyVkAciLqzao&m=_rHDe3mGn6cFfk2vEoGMcV7JcqPAdK5cp8MPgjC8QtE&s=pTPPN7qQTXpLzRzeBDgyiiQm3Qd6-0WtwlCbj3MHUcU&e= | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
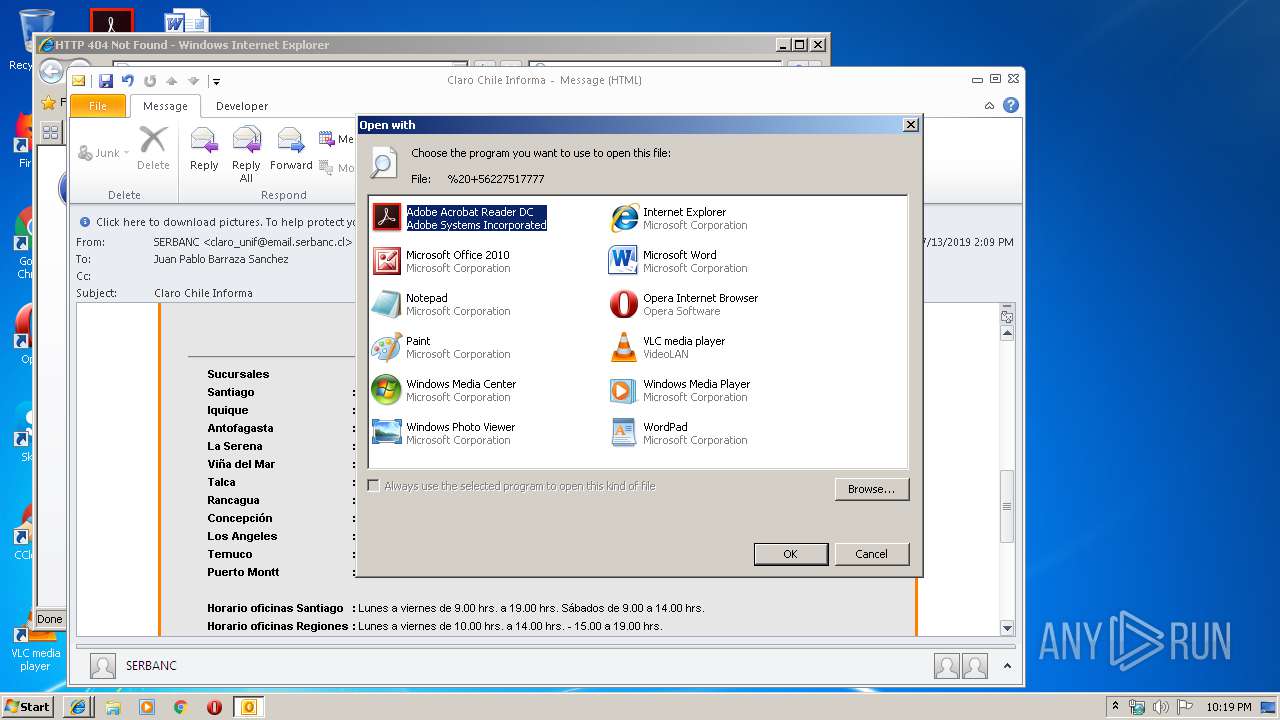
| 1548 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer tel:%20+56227517777 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3464 CREDAT:6403 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3464 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3172 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 3216 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "tel:%20+56227517777" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3404 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2044.0.1293320633\405795612" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
3 122
Read events
2 319
Write events
779
Delete events
24
Modification events
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | b7& |
Value: 623726007C0E0000010000000000000000000000 | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 7C0E0000A8E8DA31E53CD50100000000 | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220129920 | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3708) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1324417045 | |||
Executable files
0
Suspicious files
16
Text files
144
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3708 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRCFE2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3464 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3708 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@proofpoint[1].txt | text | |
MD5:— | SHA256:— | |||
| 3708 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_4294368B3FFB514EA9D770C01E851F0D.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 2592 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BMMJUTOA\serbanc_cl[1].txt | — | |
MD5:— | SHA256:— | |||
| 3708 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3708 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ContactPrefs_2_73D2E390B052314D80110E88B463A2E2.dat | xml | |
MD5:BBCF400BD7AE536EB03054021D6A6398 | SHA256:383020065C1F31F4FB09F448599A6D5E532C390AF4E5B8AF0771FE17A23222AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
63
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3708 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
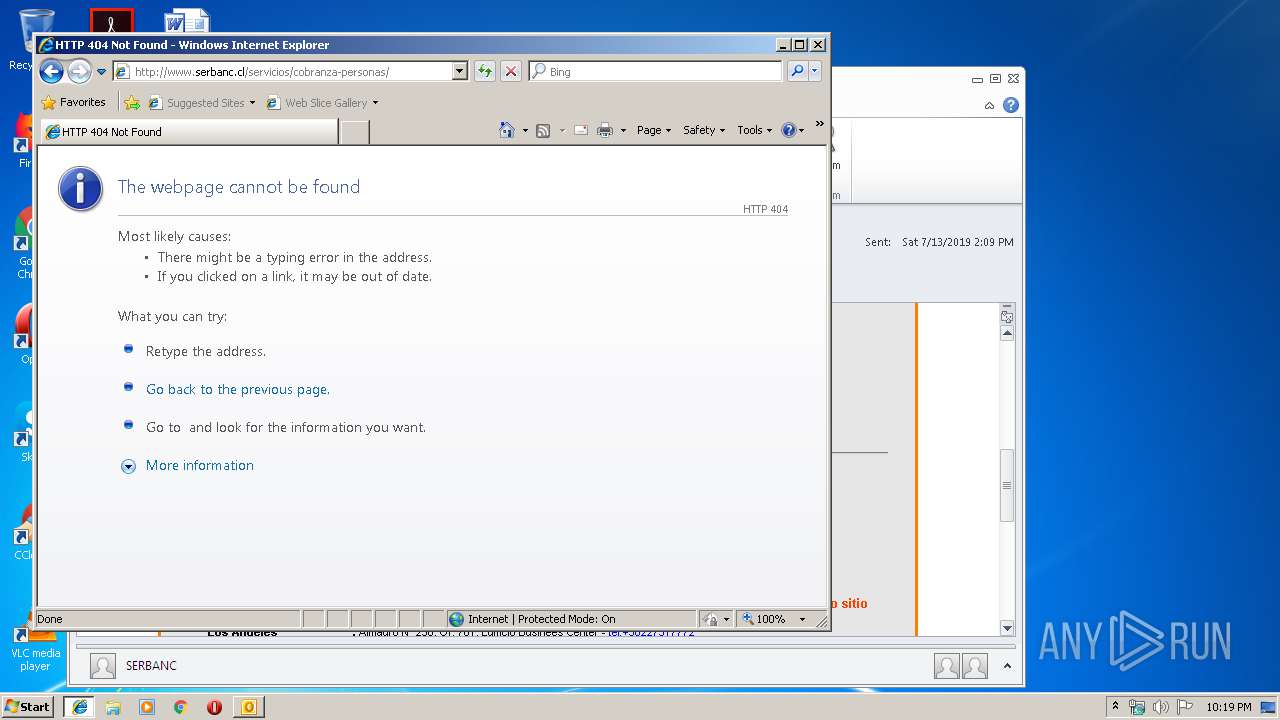
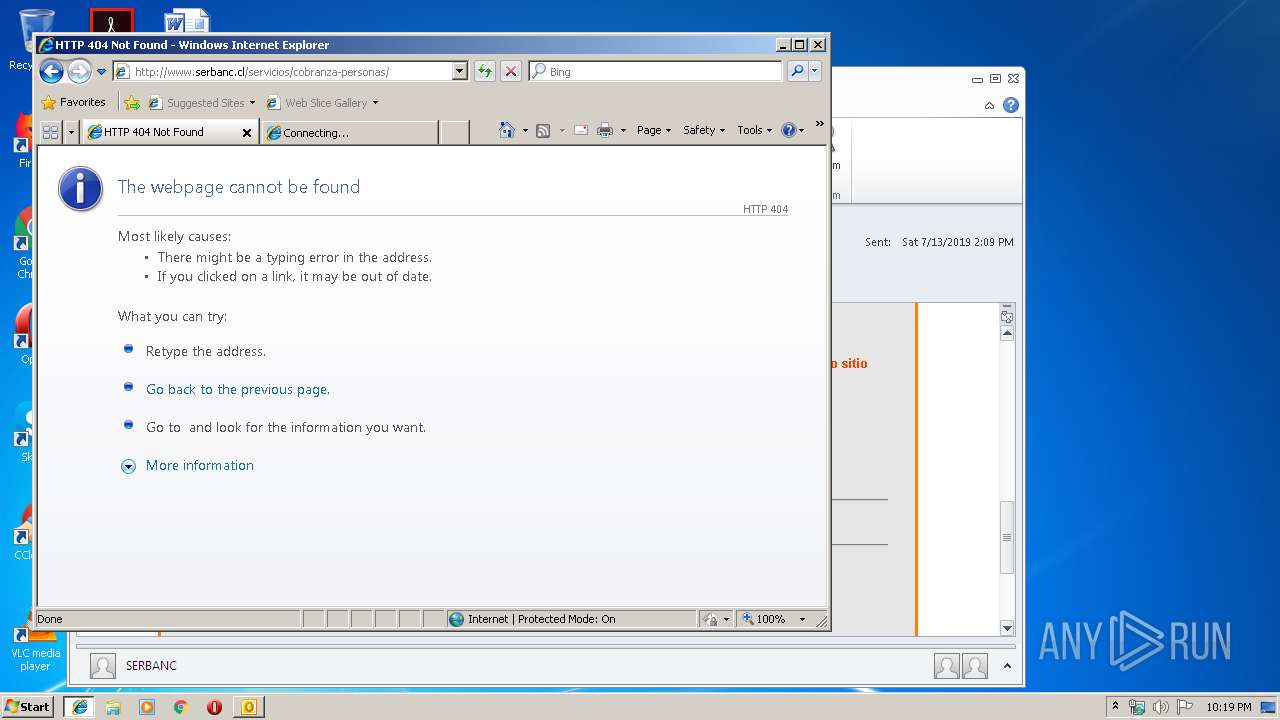
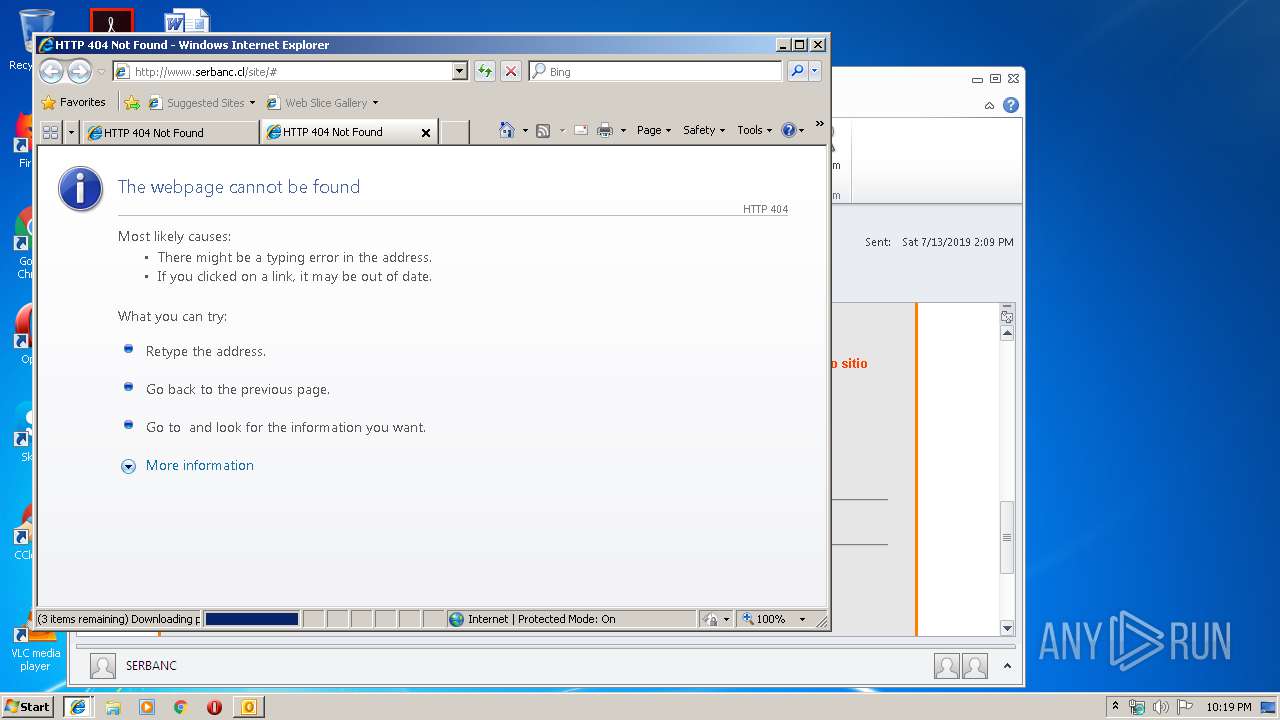
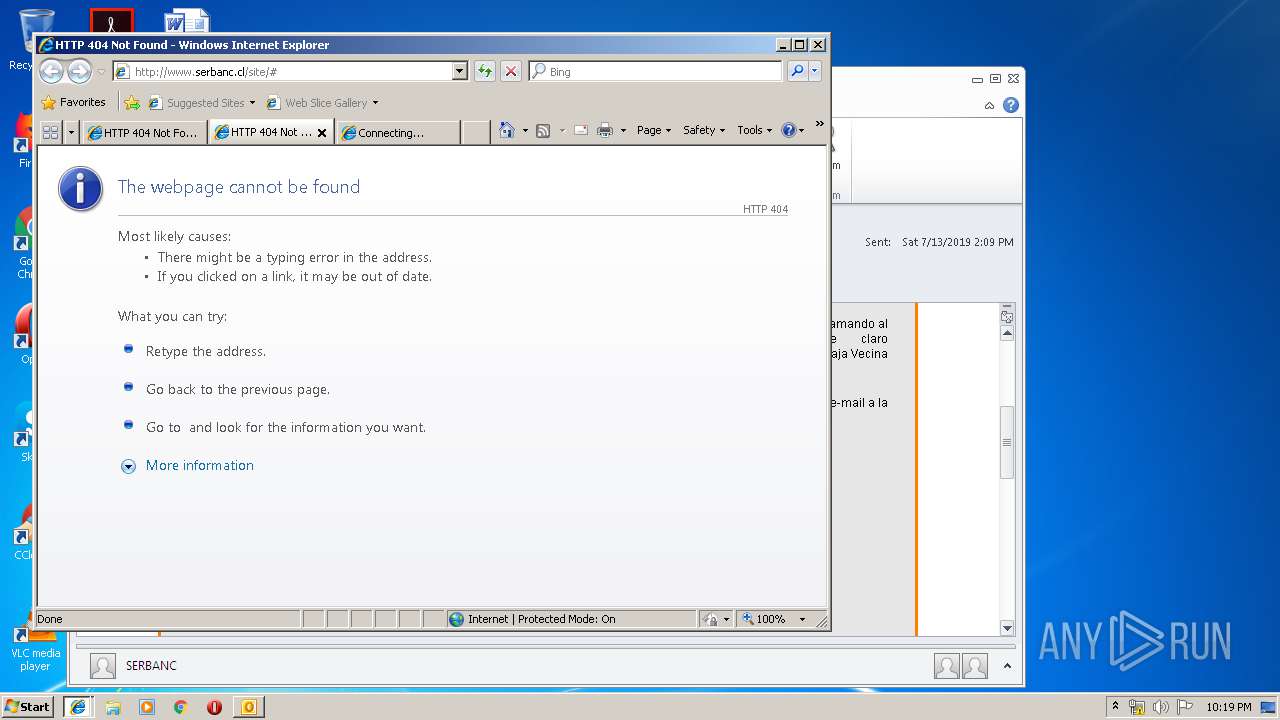
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/js/vendor/modernizr-2.6.2-respond-1.1.0.min.js | CL | html | 270 b | unknown |
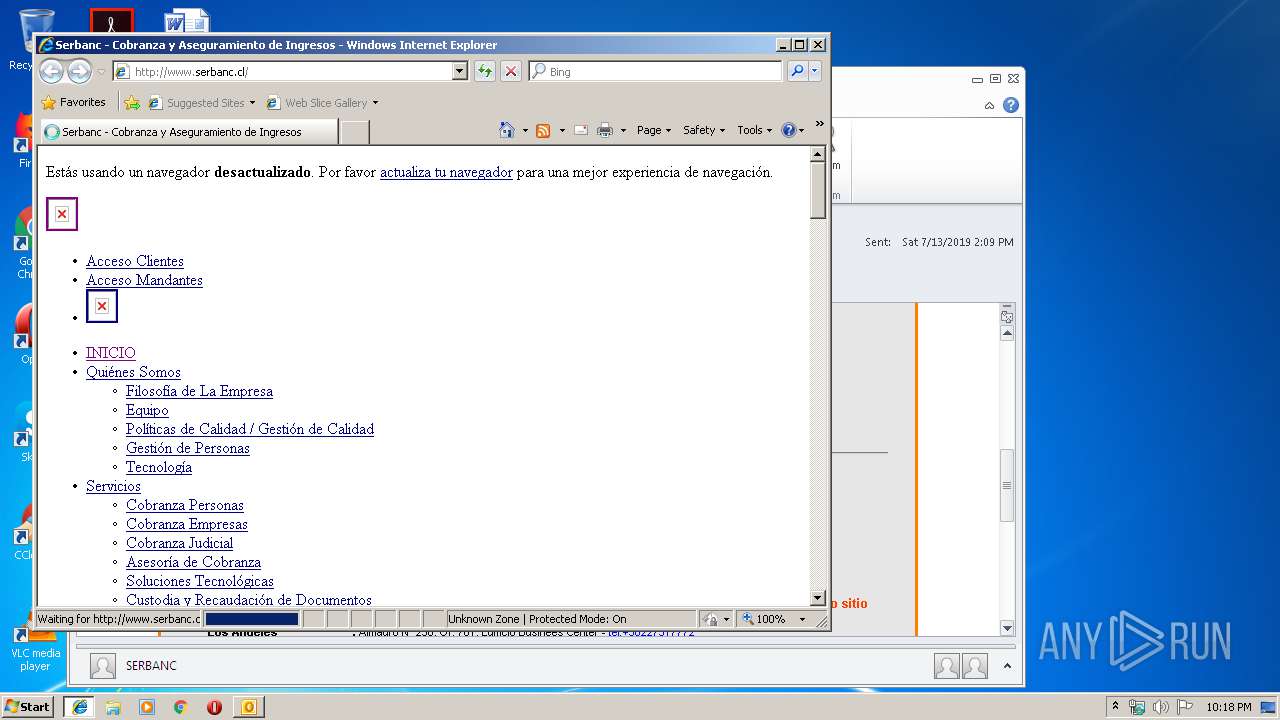
2592 | iexplore.exe | GET | 200 | 200.119.246.196:80 | http://www.serbanc.cl/ | CL | html | 20.1 Kb | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/style.css?v=3 | CL | html | 233 b | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/js/vendor/jquery-1.10.1.min.js | CL | html | 254 b | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/css/bootstrap.min.css | CL | html | 245 b | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/js/bootstrap.min.js | CL | html | 243 b | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/css/normalize.min.css | CL | html | 245 b | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/js/main.js | CL | html | 234 b | unknown |
2592 | iexplore.exe | GET | 404 | 200.119.246.196:80 | http://www.serbanc.cl/wp-content/themes/serbanc/css/ie.css | CL | html | 234 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
128 | iexplore.exe | 172.217.23.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
128 | iexplore.exe | 216.58.207.72:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
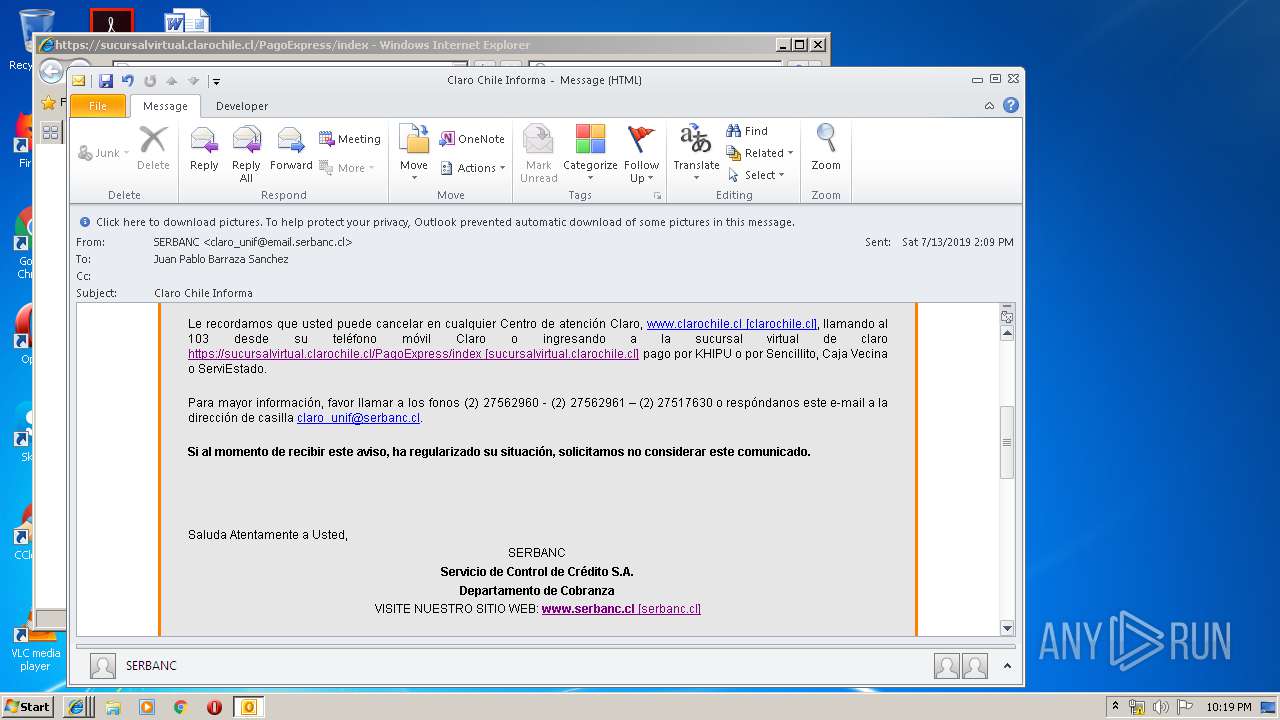
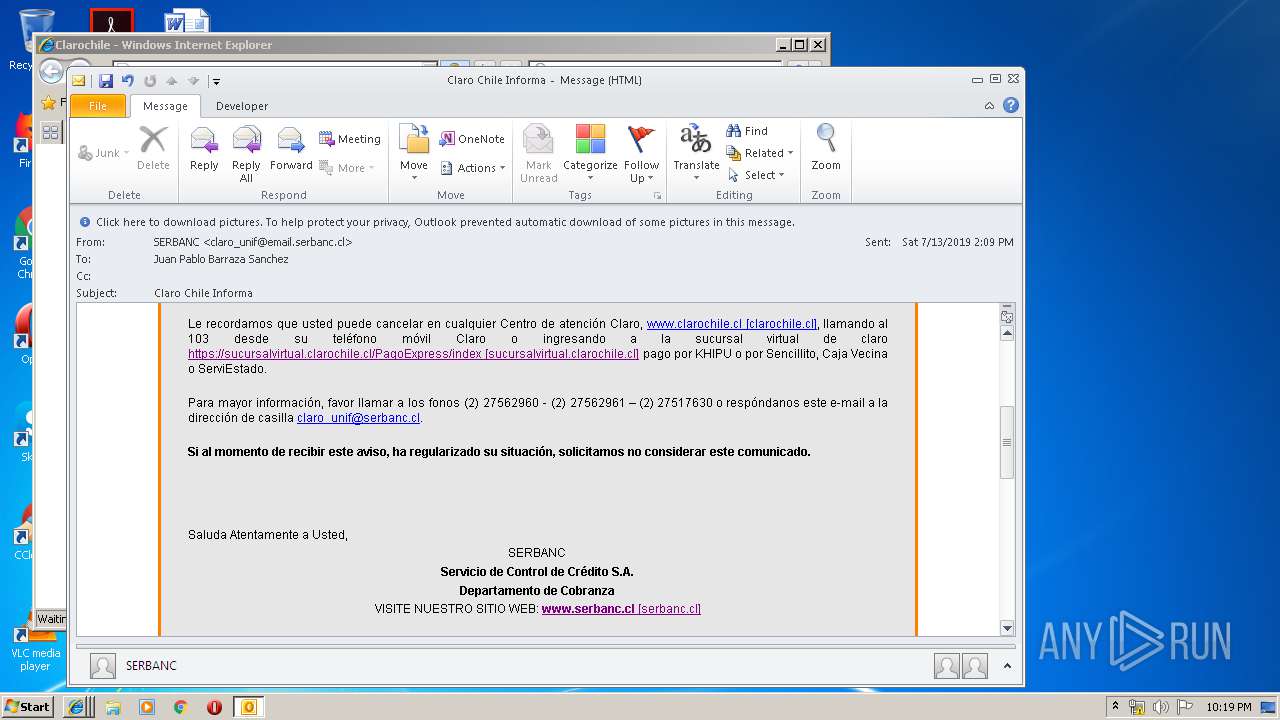
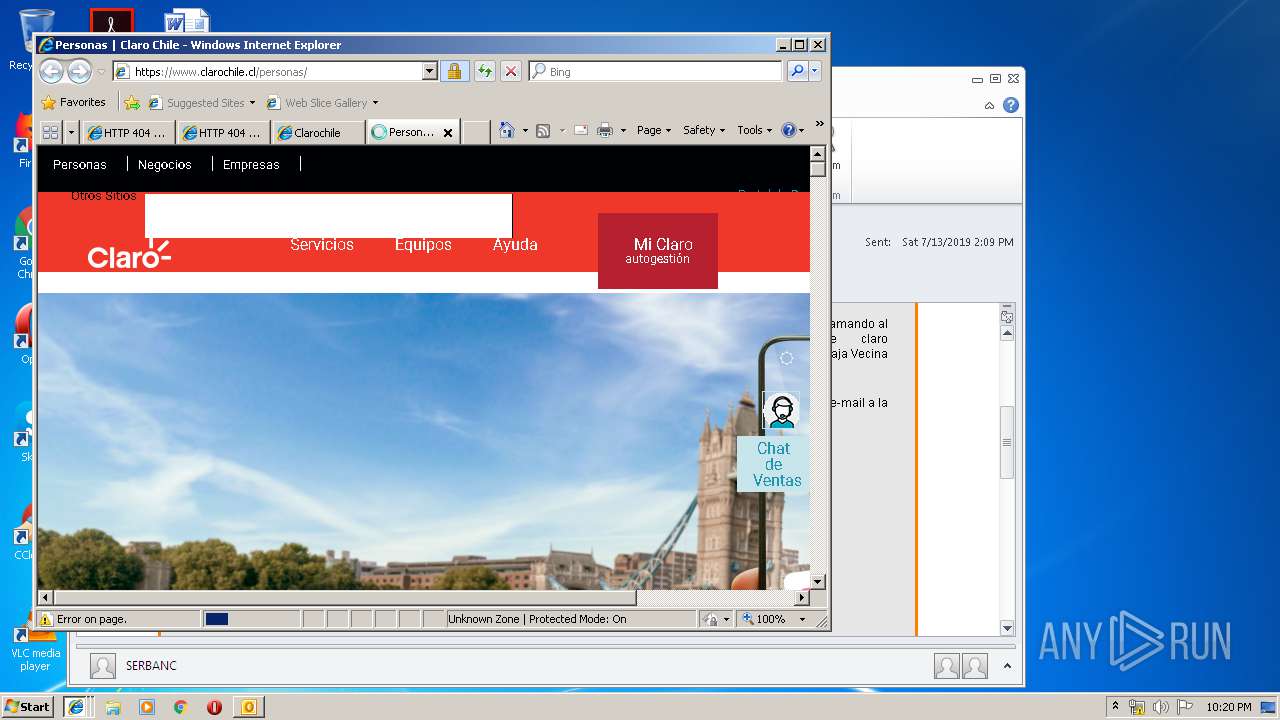
2592 | iexplore.exe | 104.111.219.192:443 | www.clarochile.cl | Akamai International B.V. | NL | whitelisted |
2592 | iexplore.exe | 104.111.219.192:80 | www.clarochile.cl | Akamai International B.V. | NL | whitelisted |
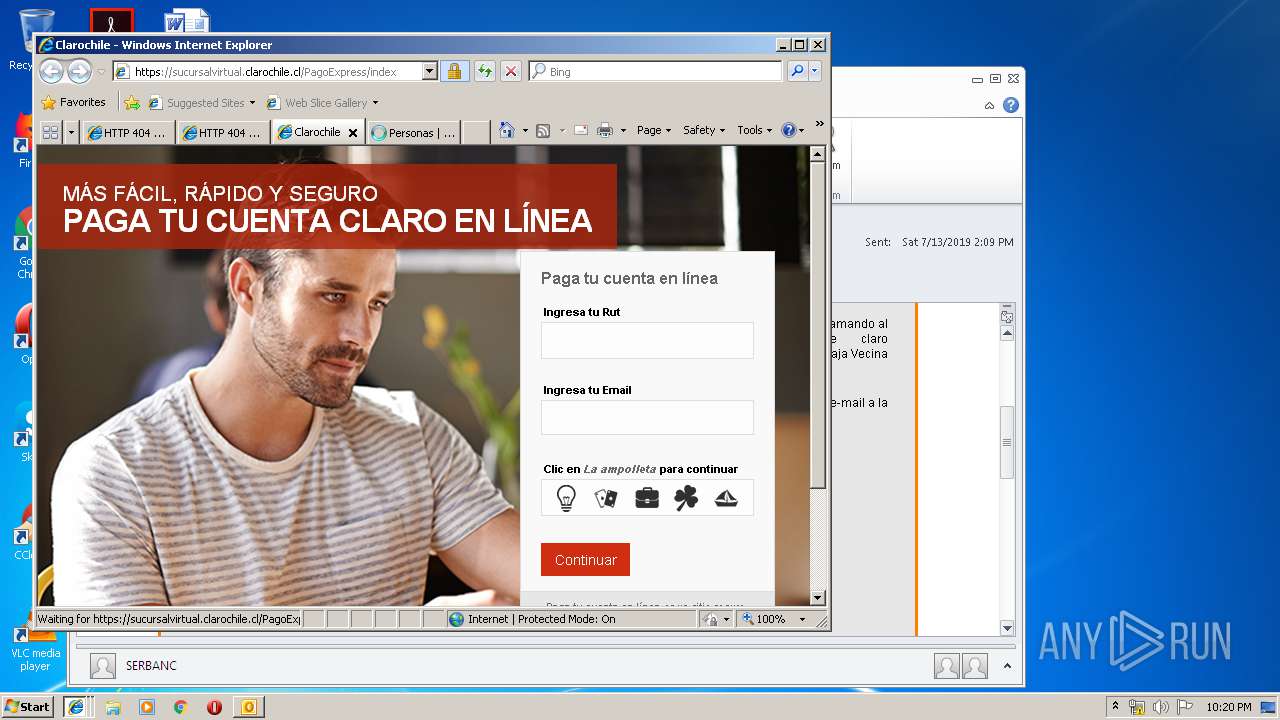
3464 | iexplore.exe | 200.29.129.227:443 | sucursalvirtual.clarochile.cl | Telmex Chile Internet S.A. | CL | unknown |
3708 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3464 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
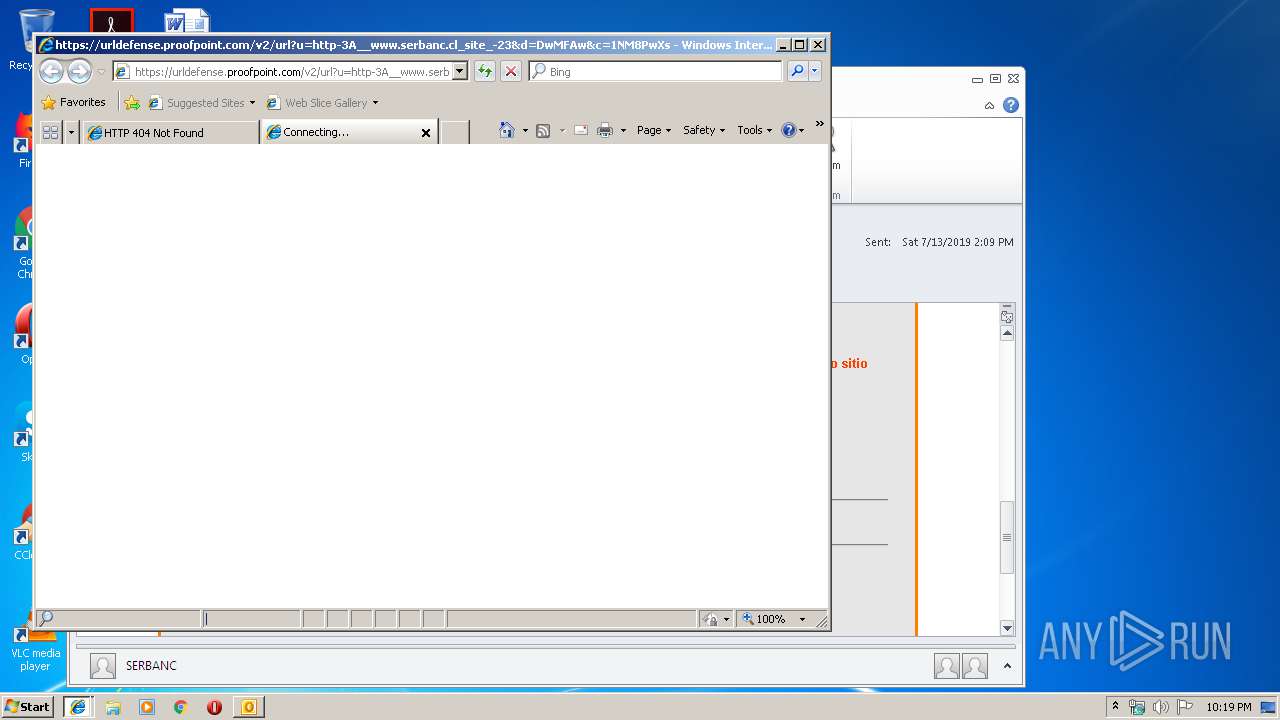
2592 | iexplore.exe | 67.231.146.66:443 | urldefense.proofpoint.com | Proofpoint, Inc. | US | suspicious |
2592 | iexplore.exe | 200.119.246.196:80 | www.serbanc.cl | Gtd Internet S.A. | CL | unknown |
2592 | iexplore.exe | 172.217.23.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
urldefense.proofpoint.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.serbanc.cl |
| unknown |
www.google-analytics.com |
| whitelisted |
sucursalvirtual.clarochile.cl |
| unknown |
ssl.google-analytics.com |
| whitelisted |
www.clarochile.cl |
| unknown |
www.googletagmanager.com |
| whitelisted |
static.hotjar.com |
| whitelisted |