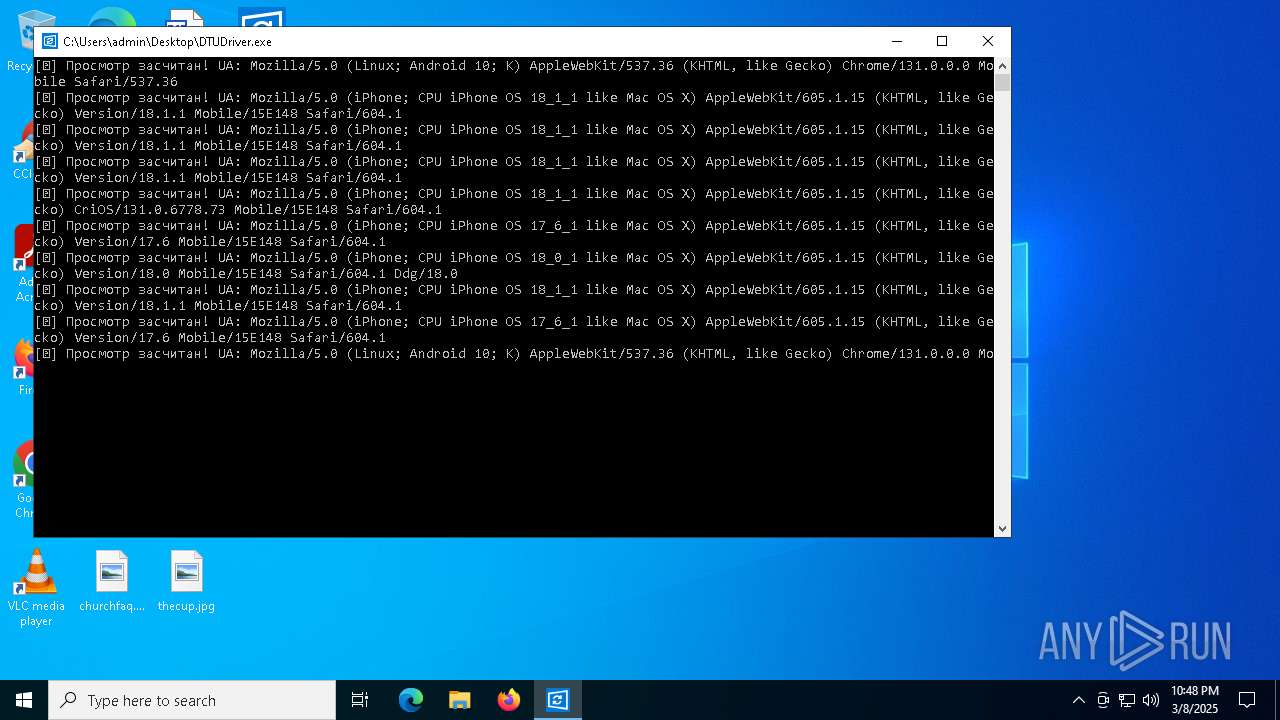
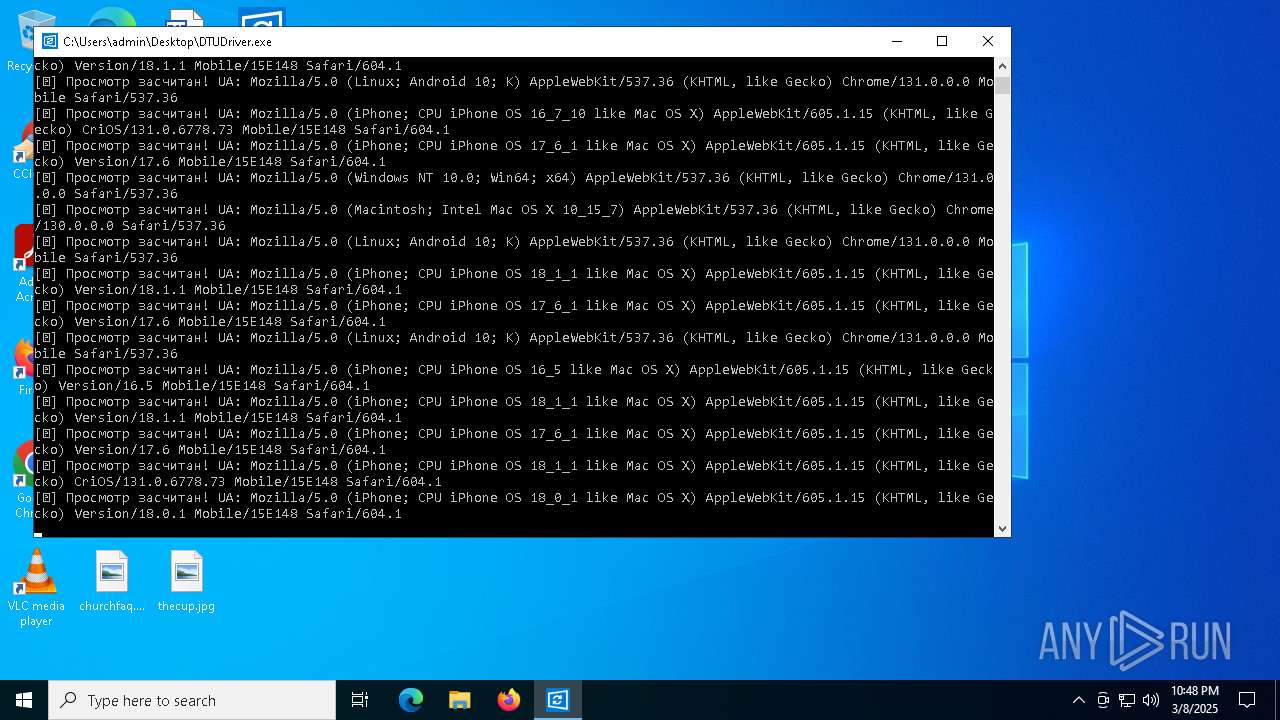
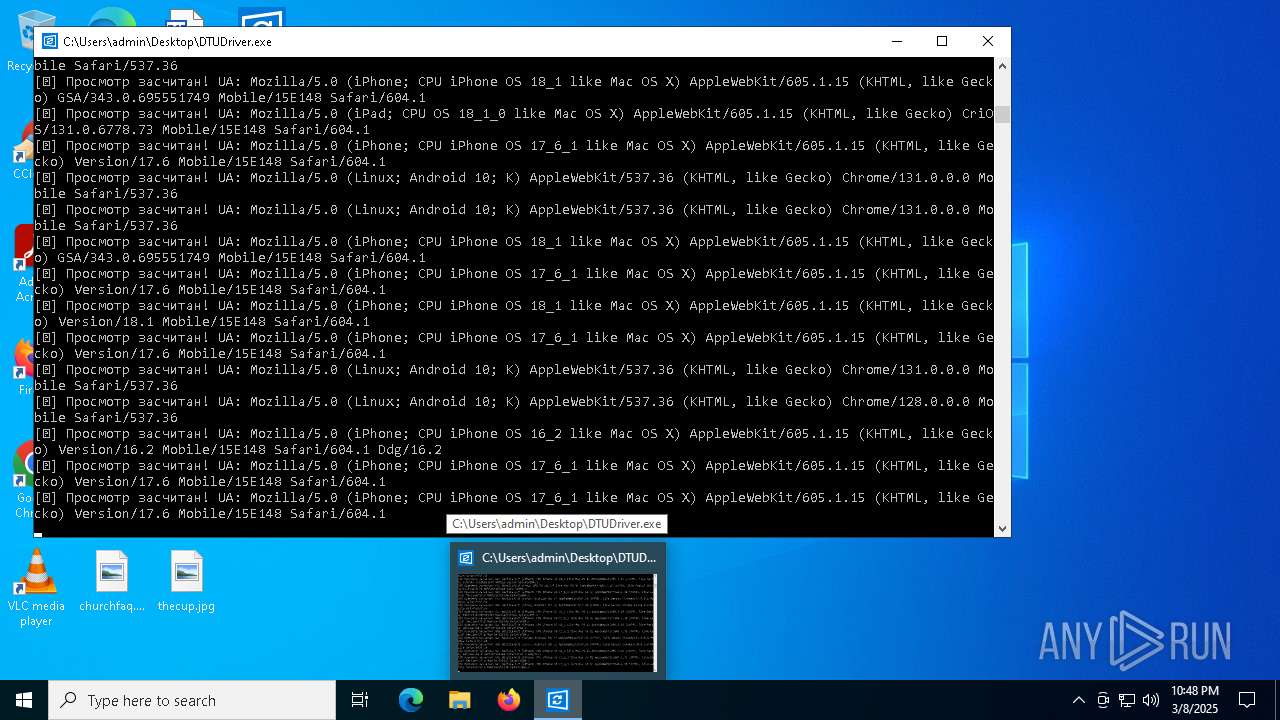
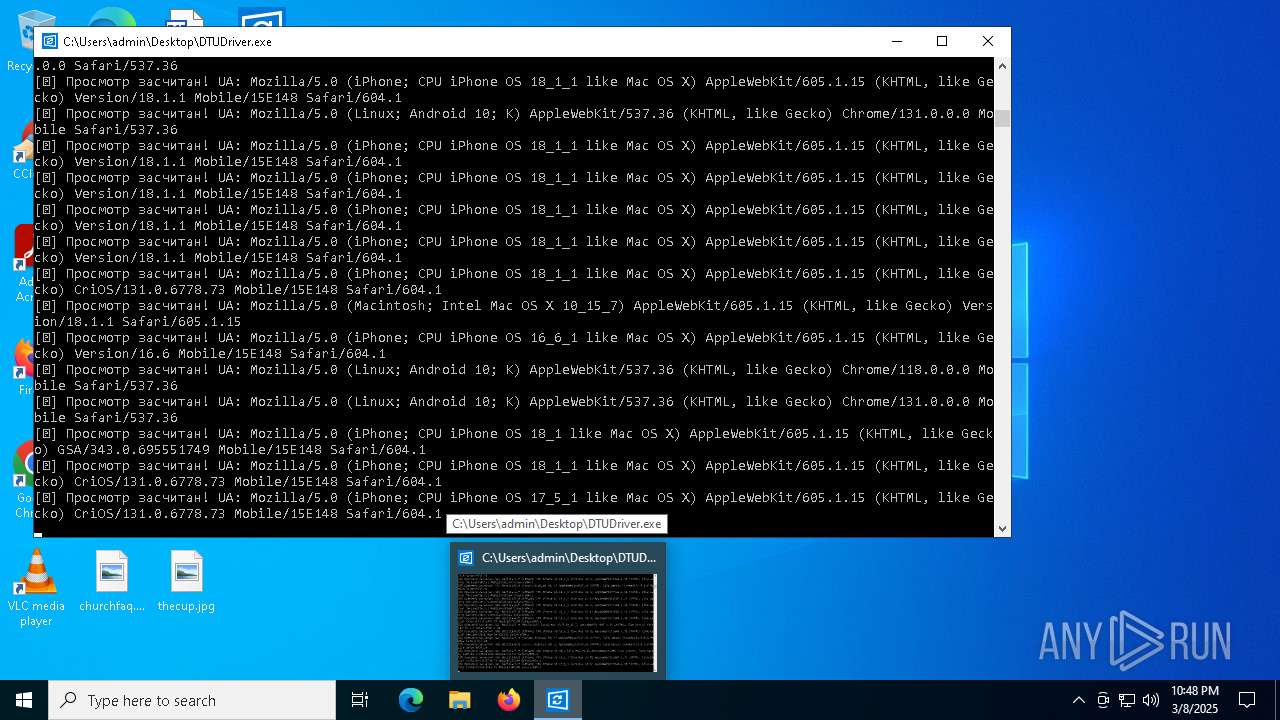
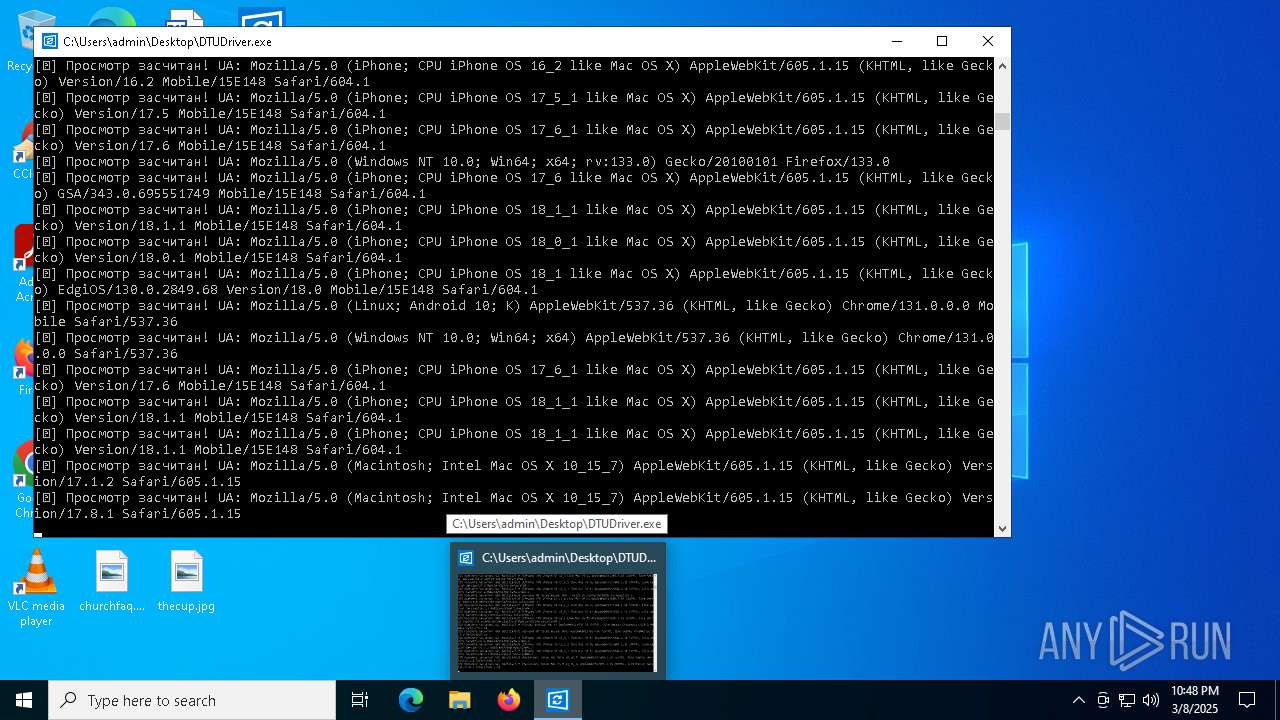
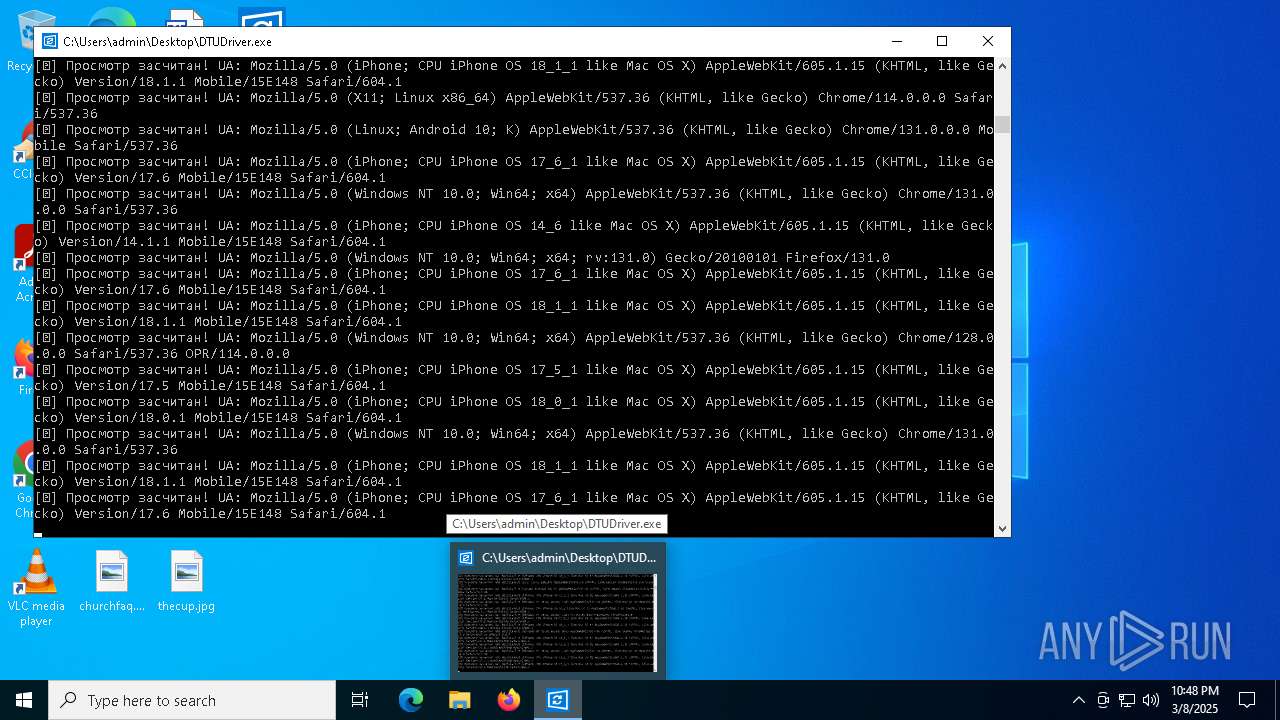
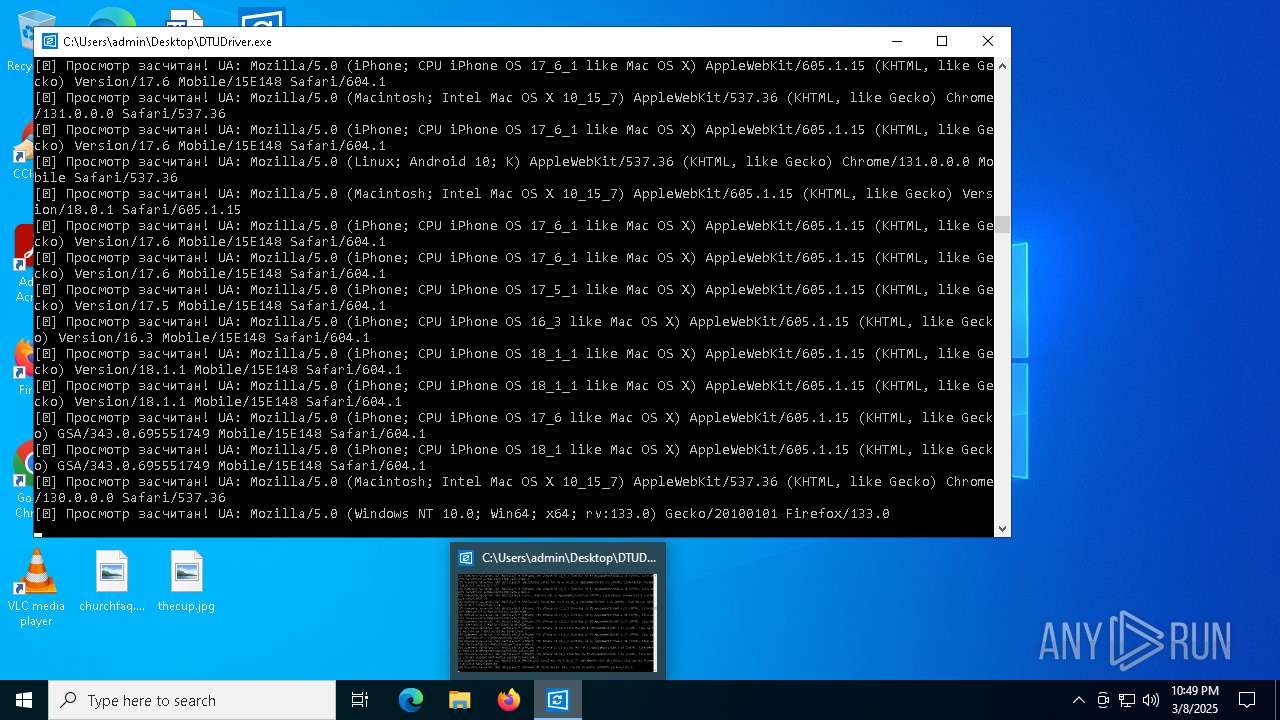
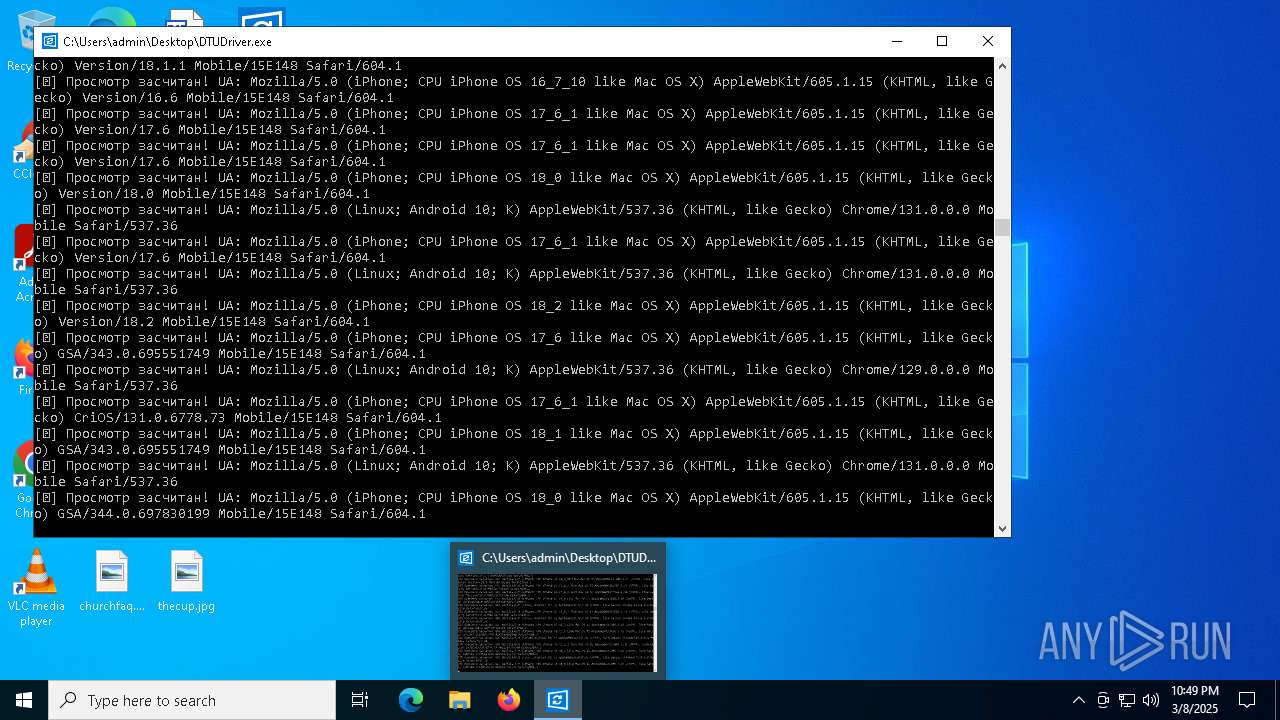
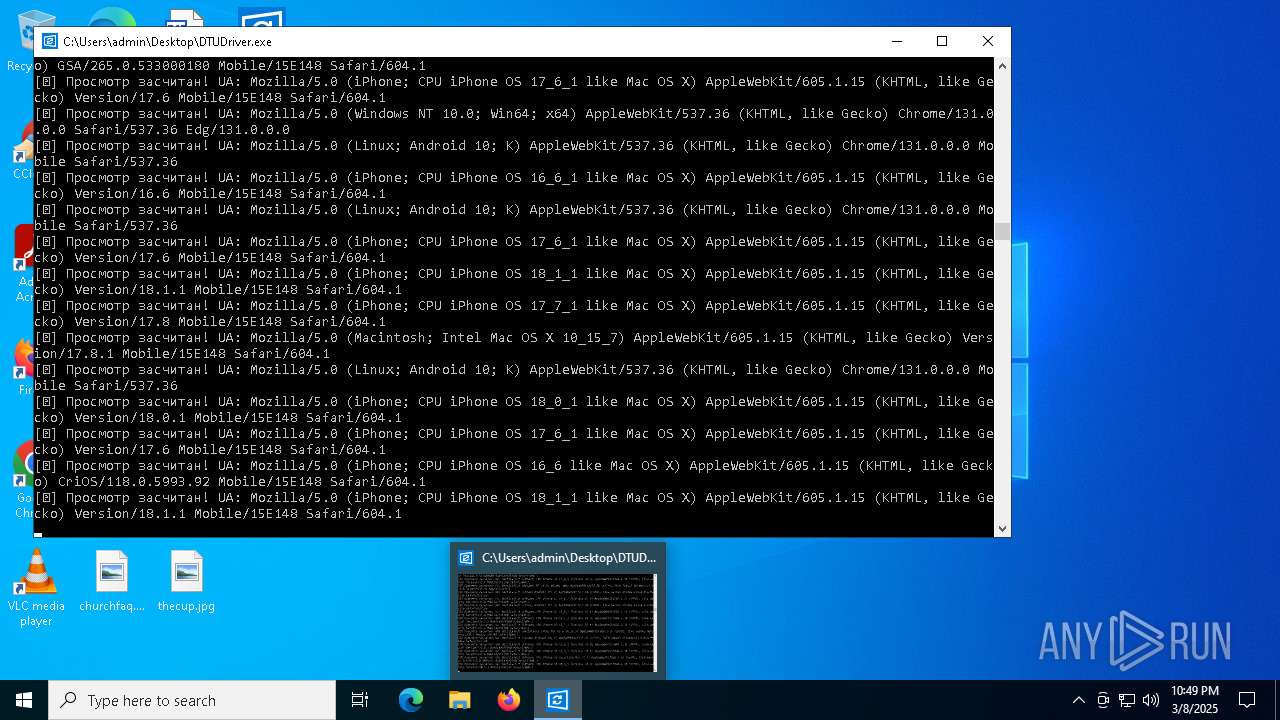
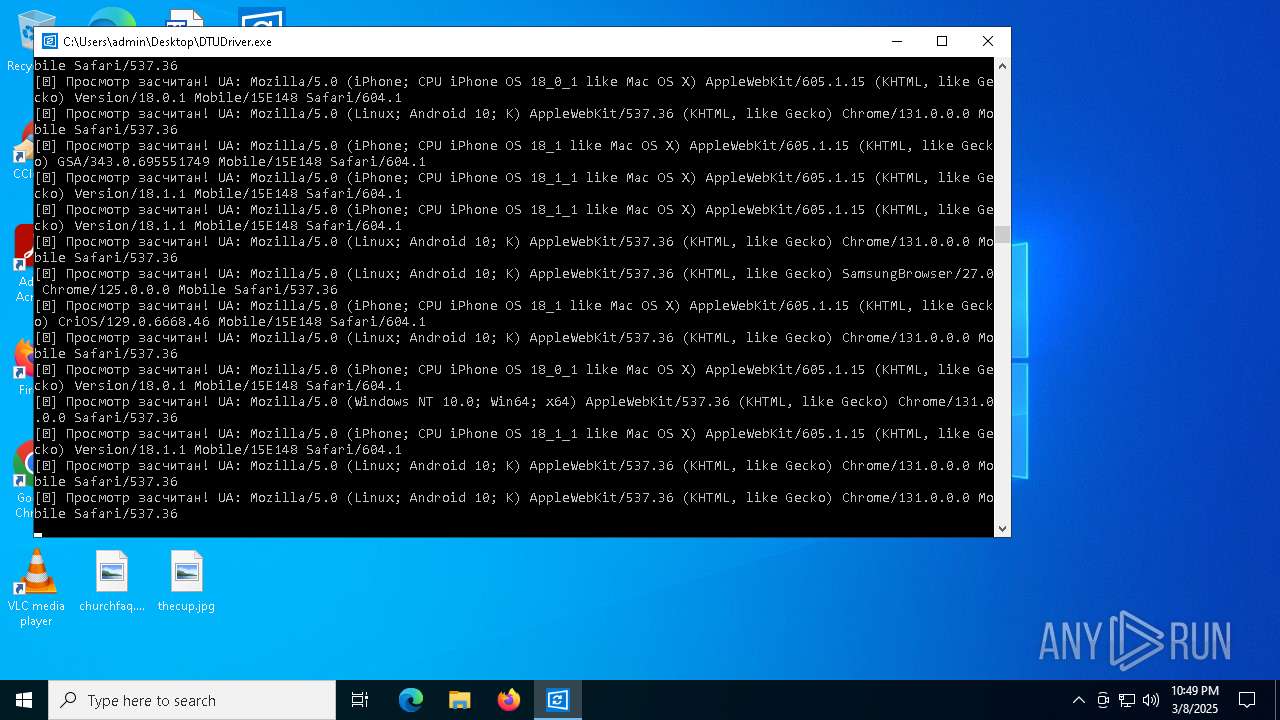
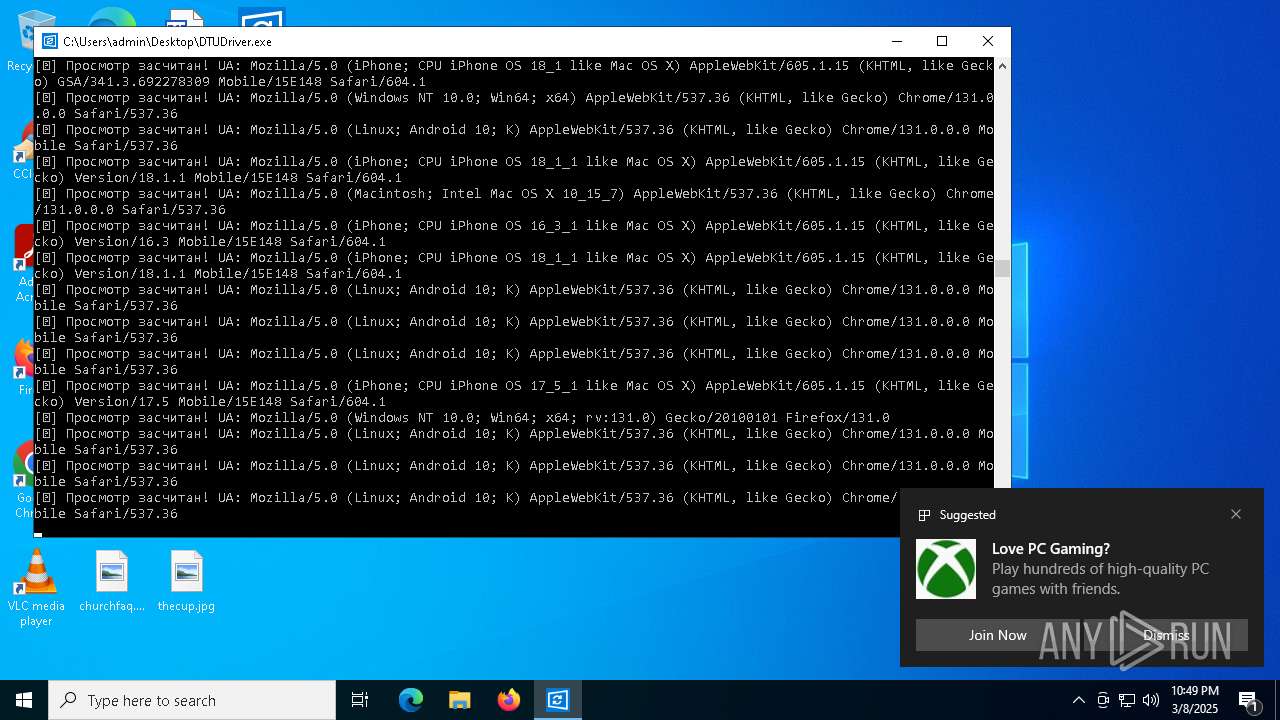
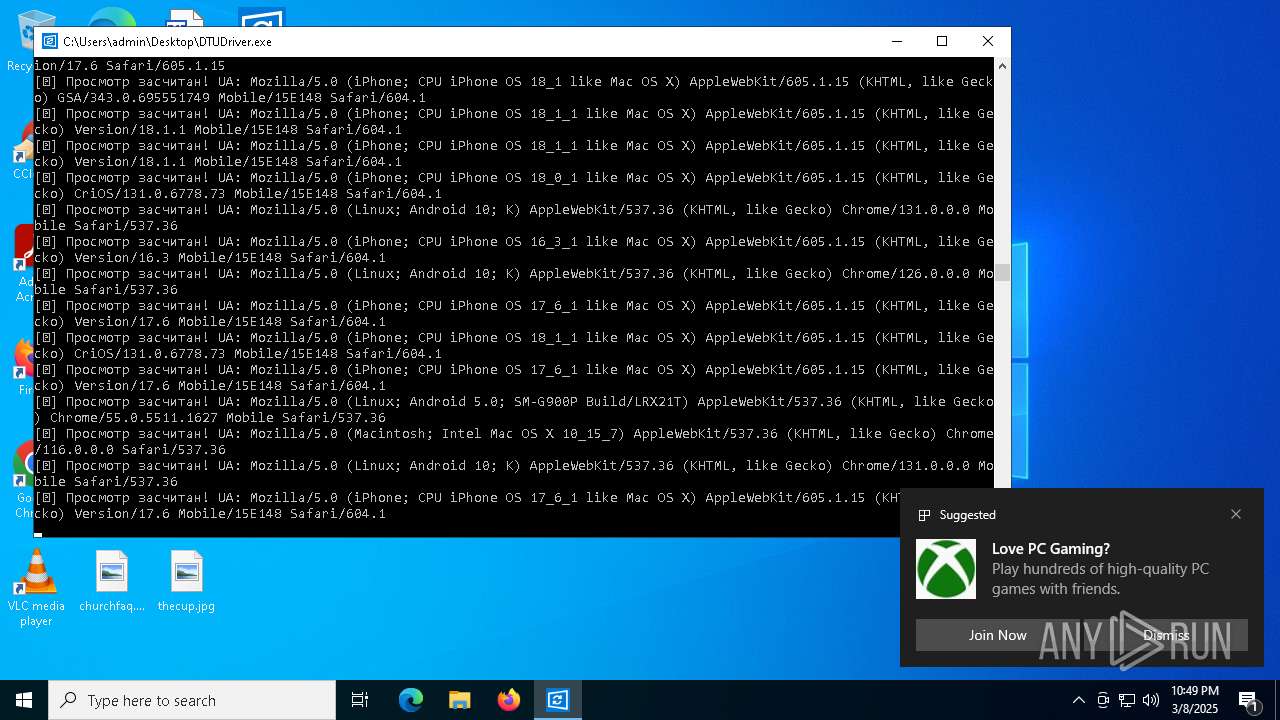
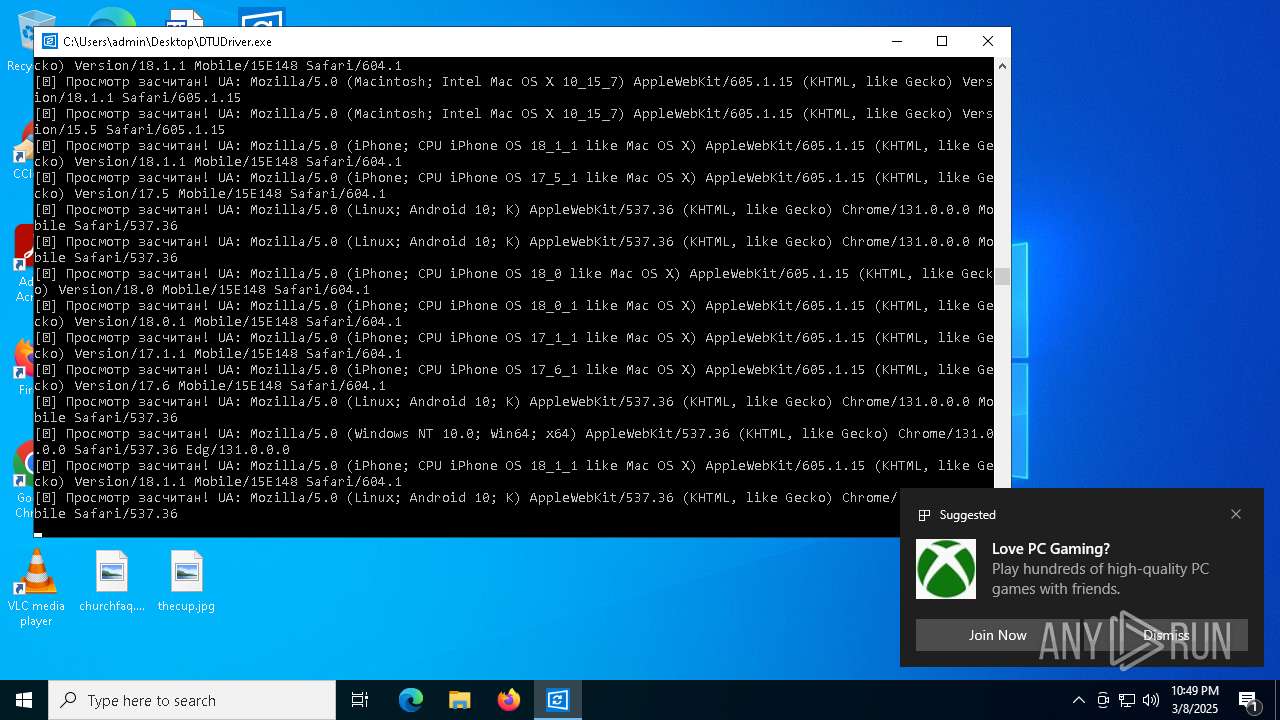
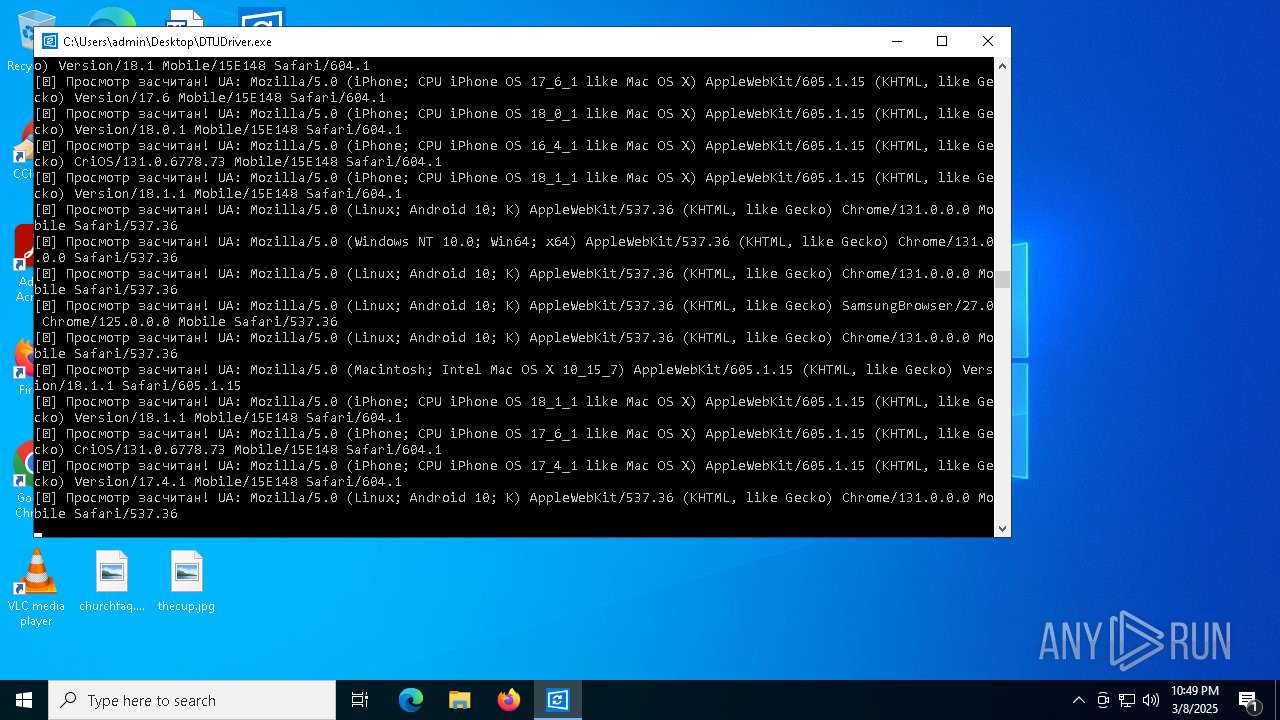
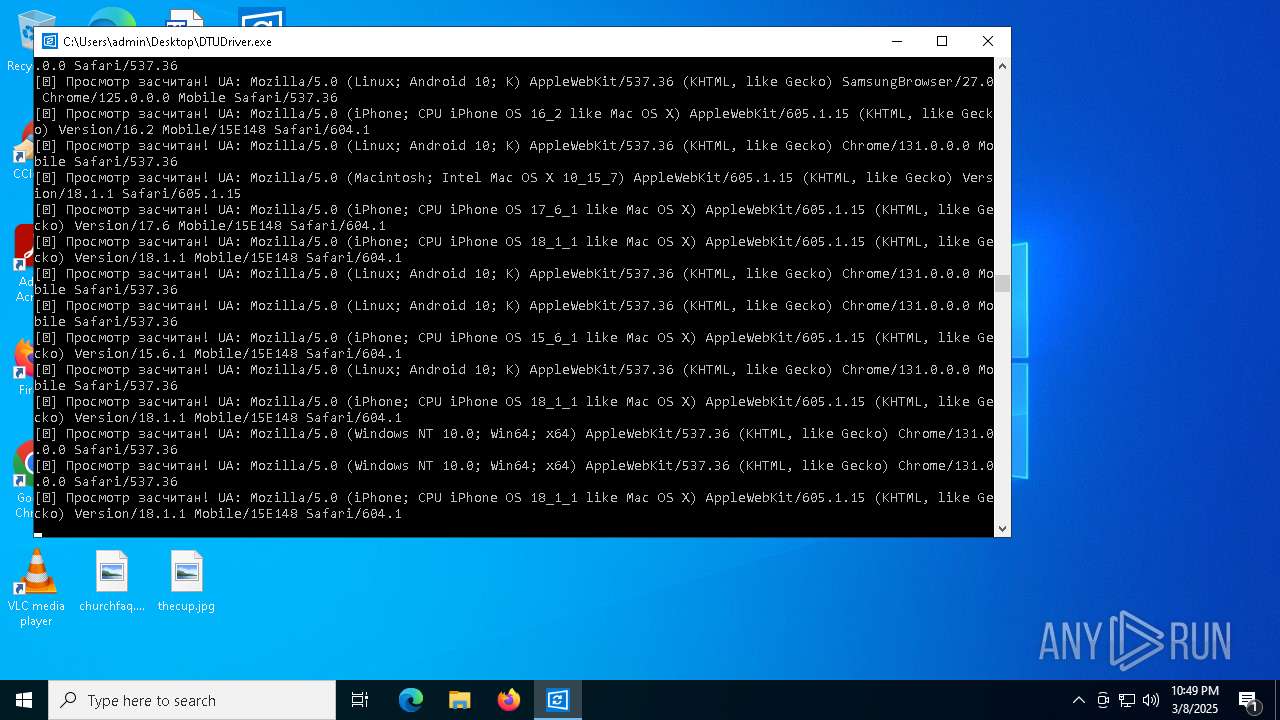
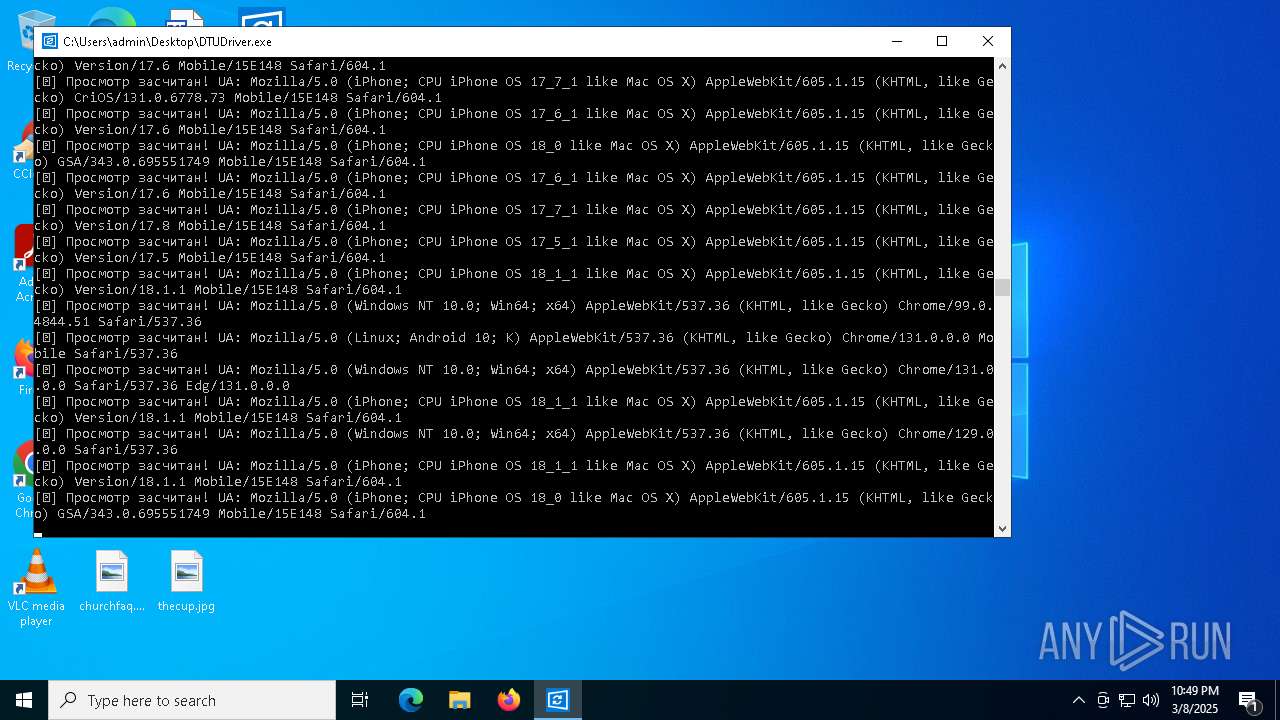
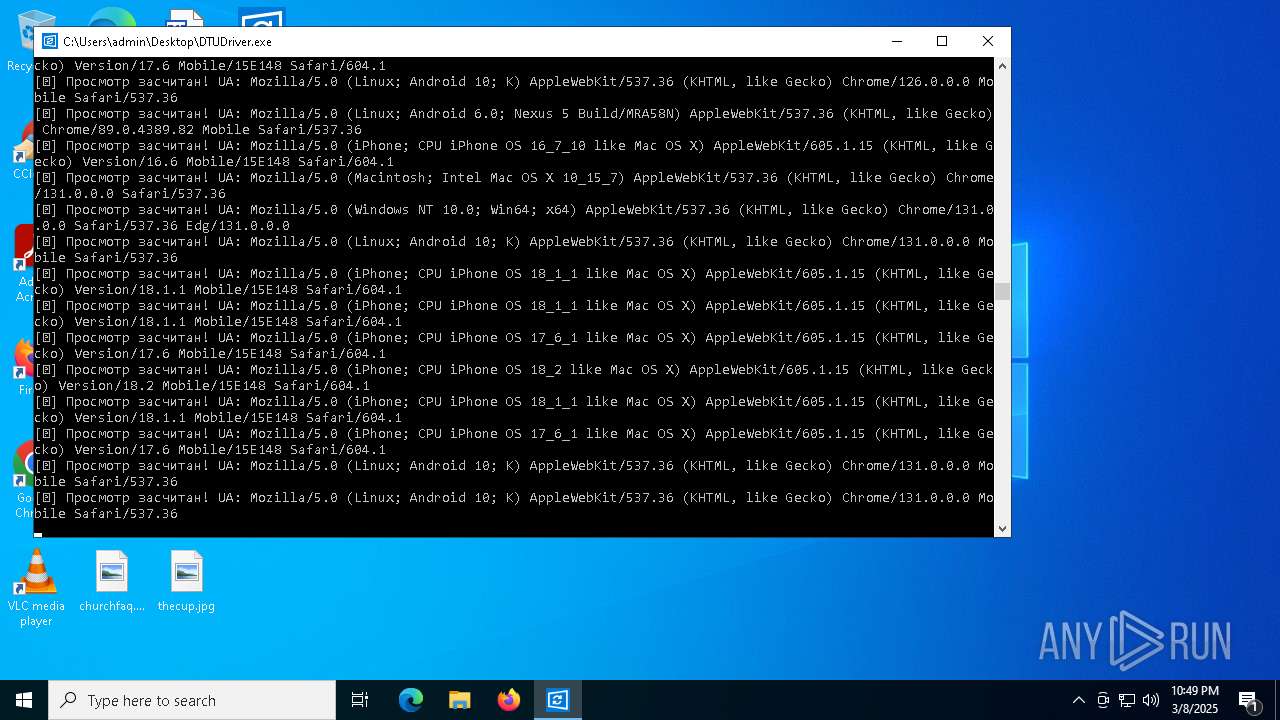
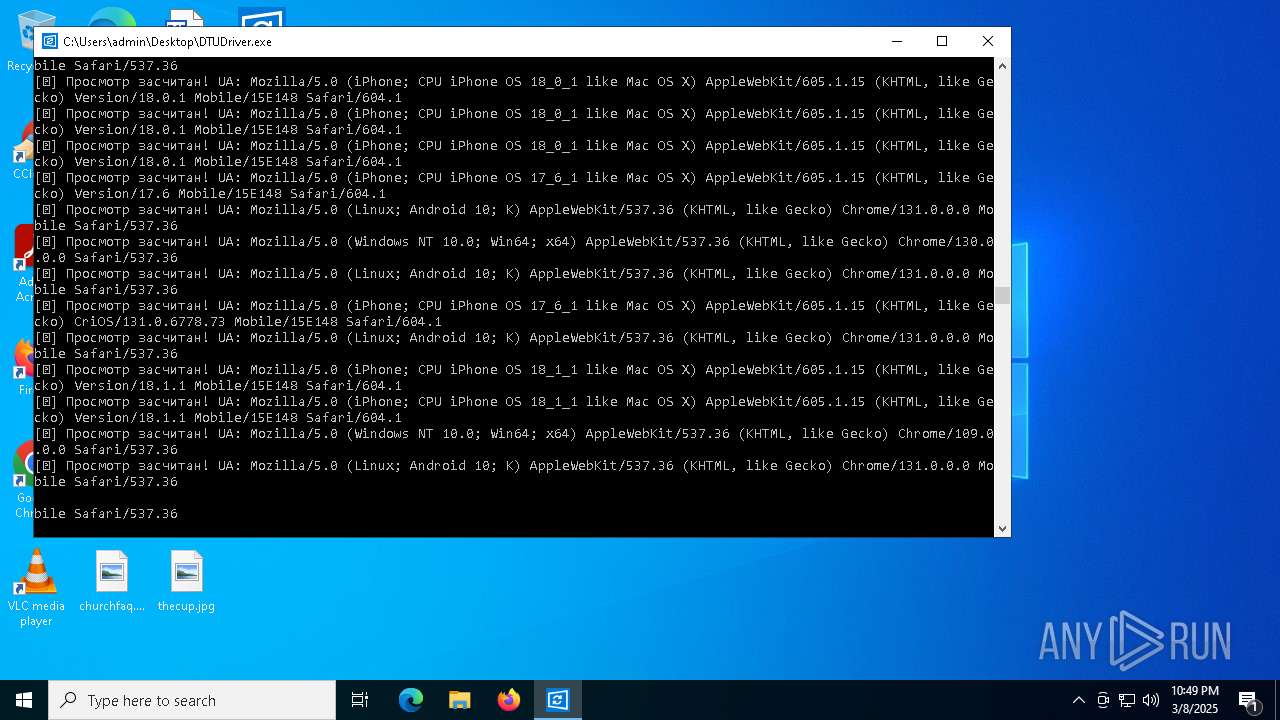
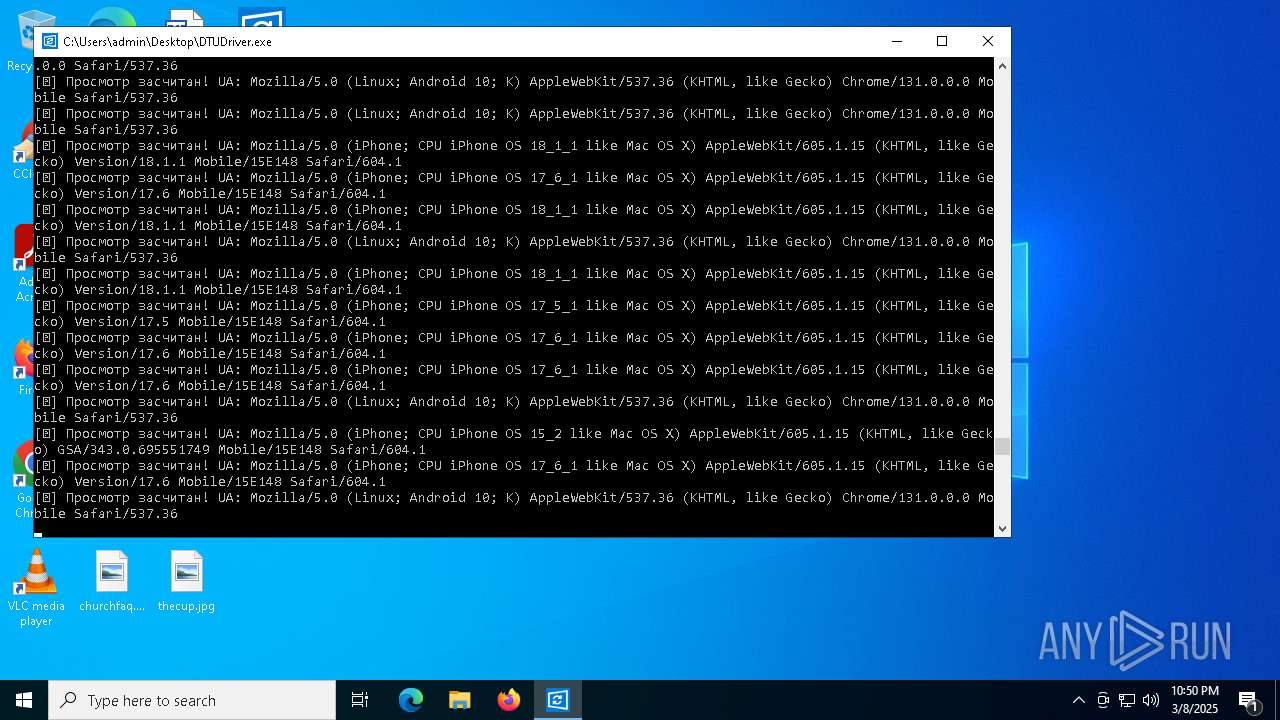
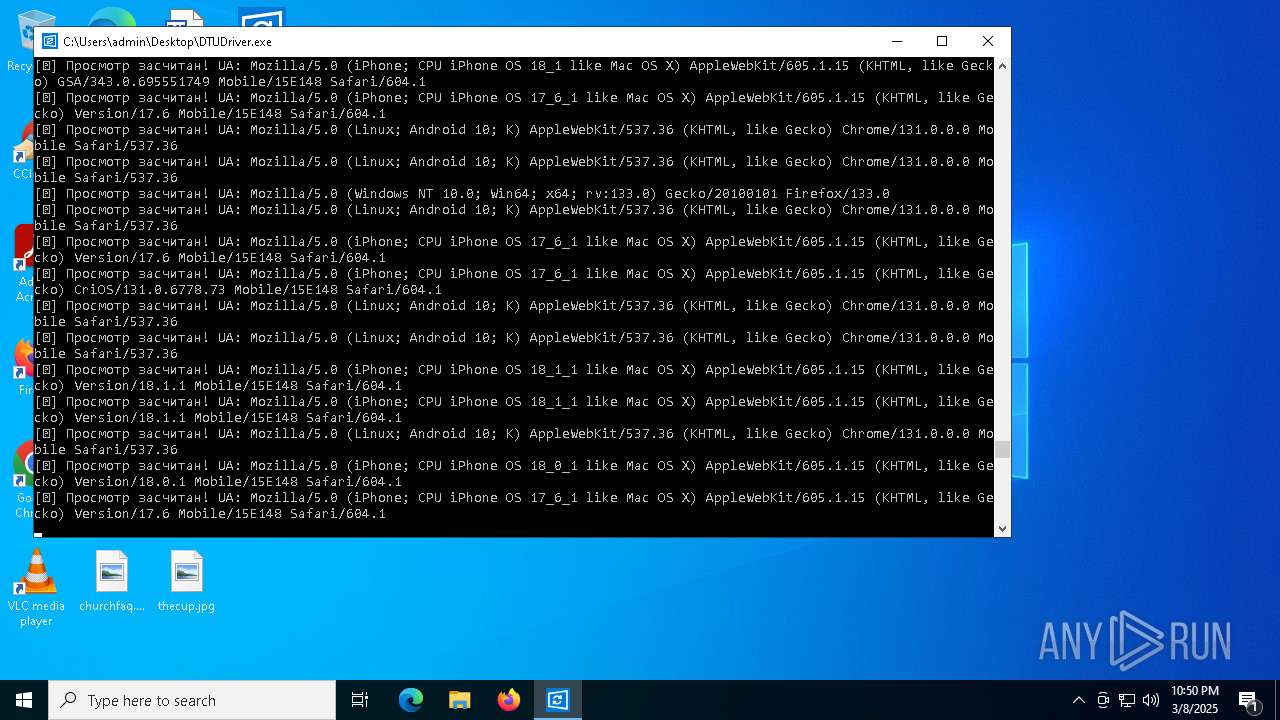
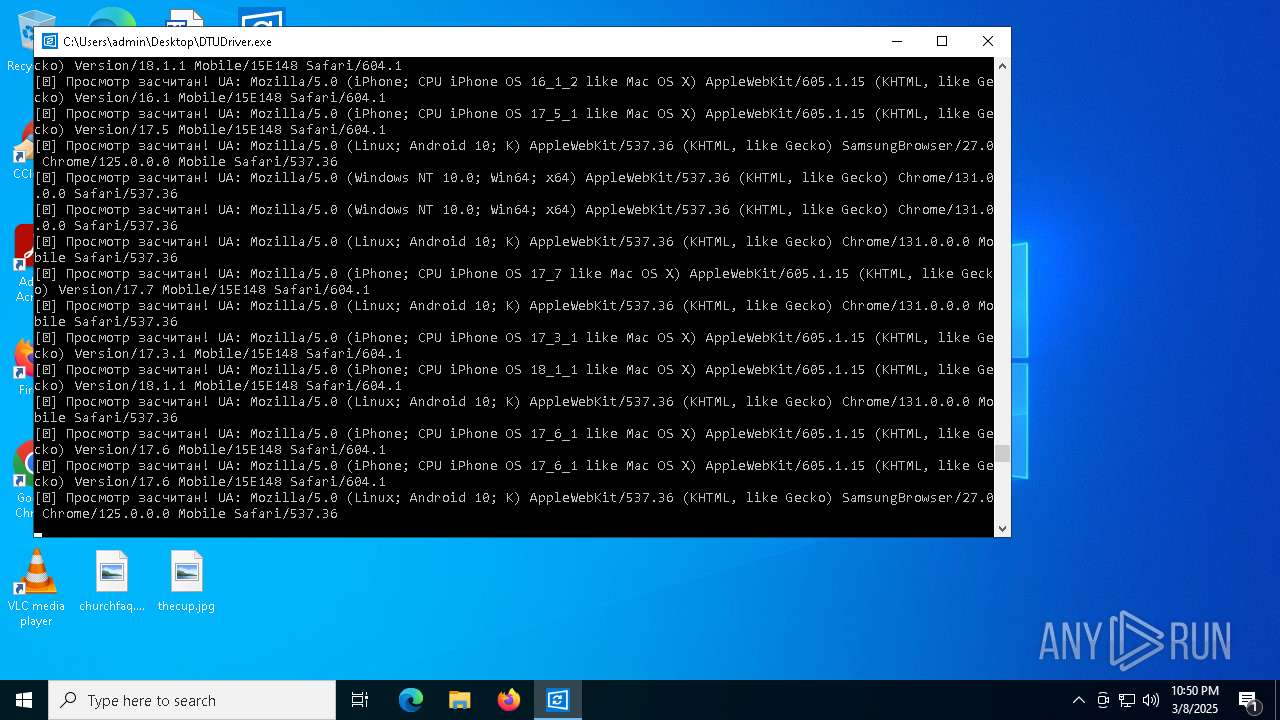
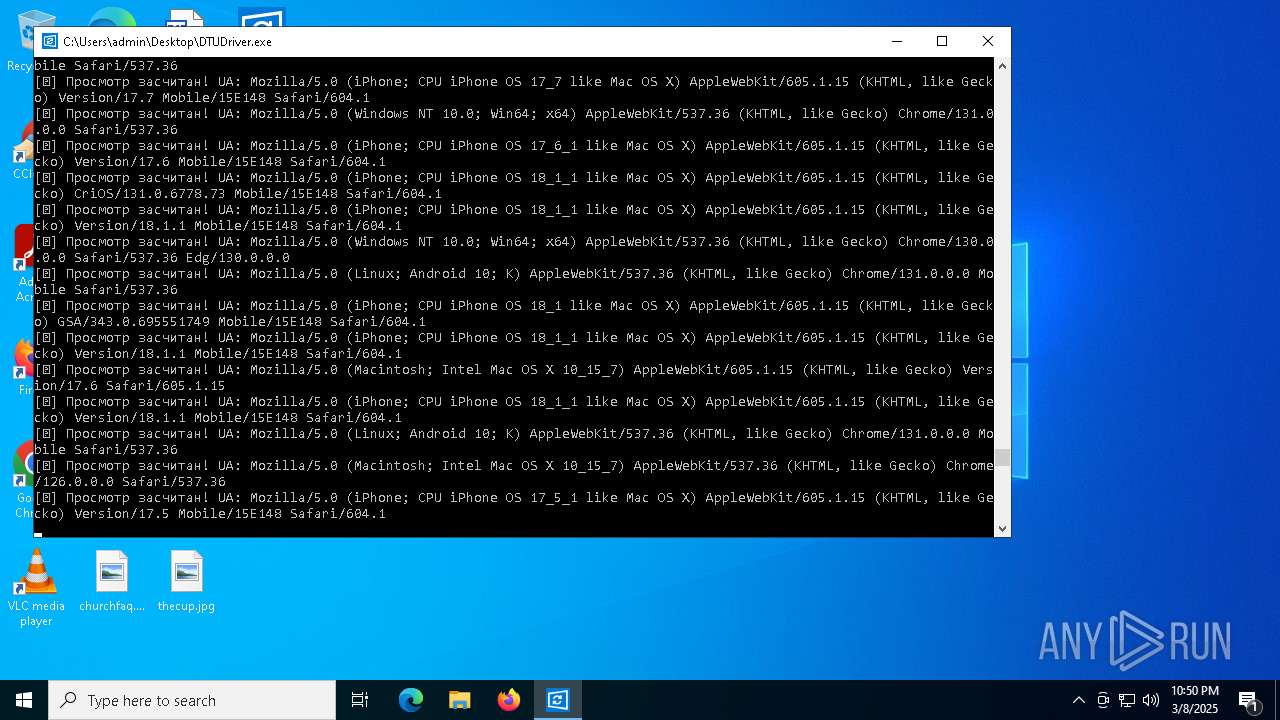
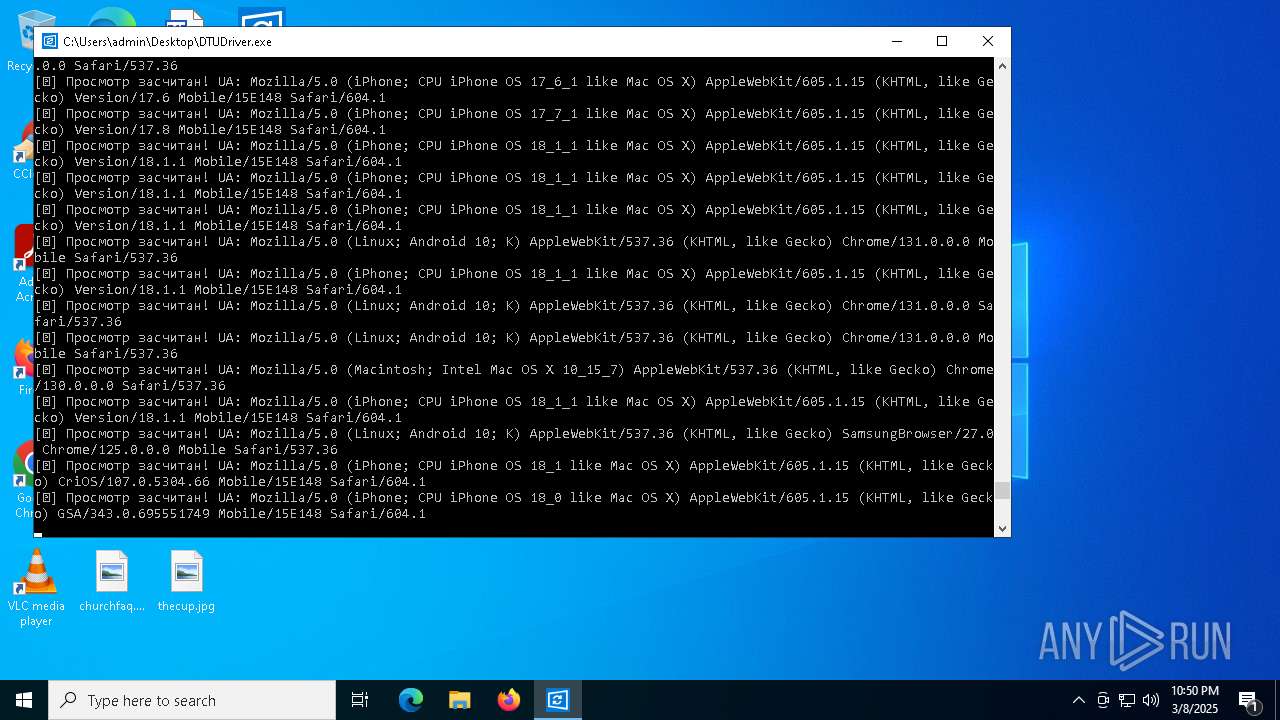
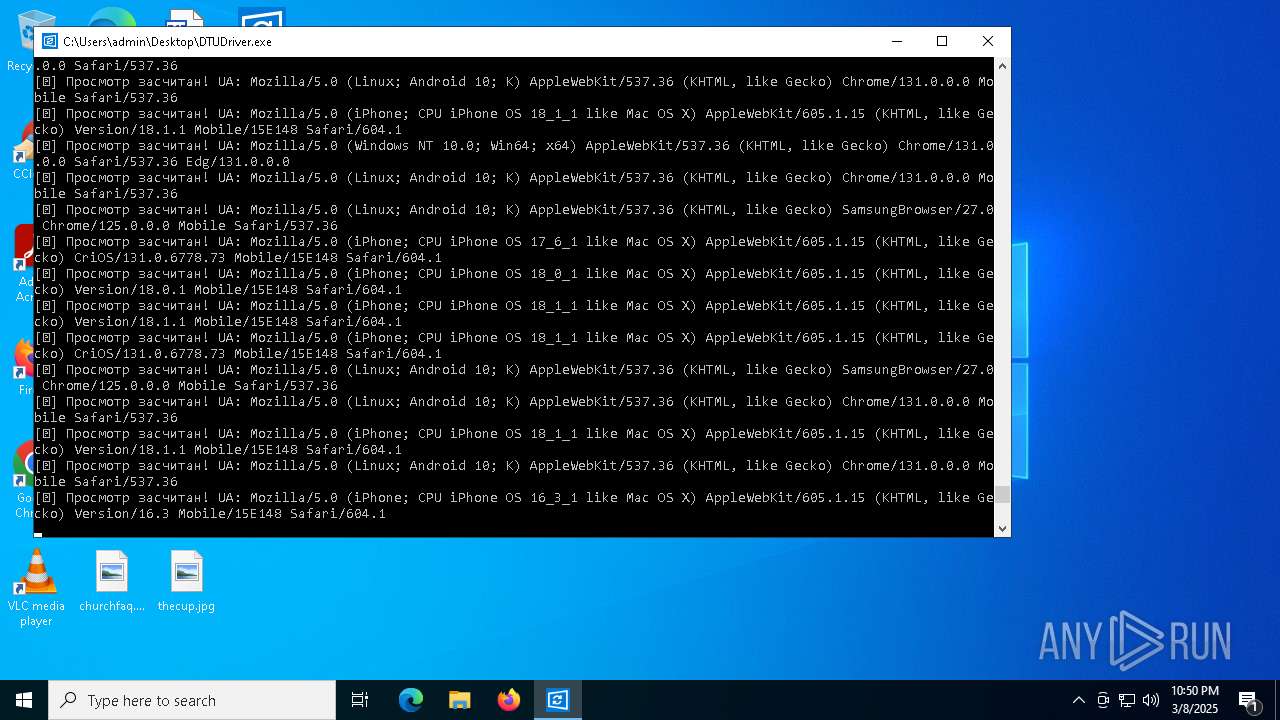
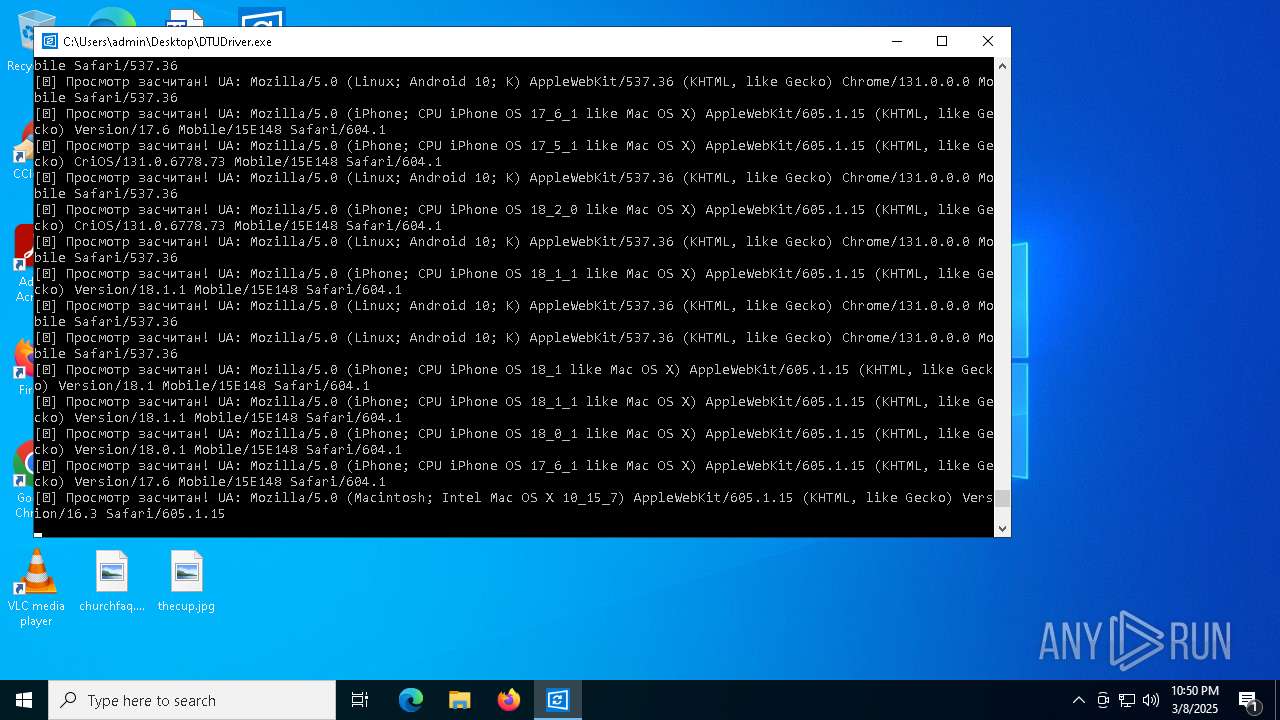
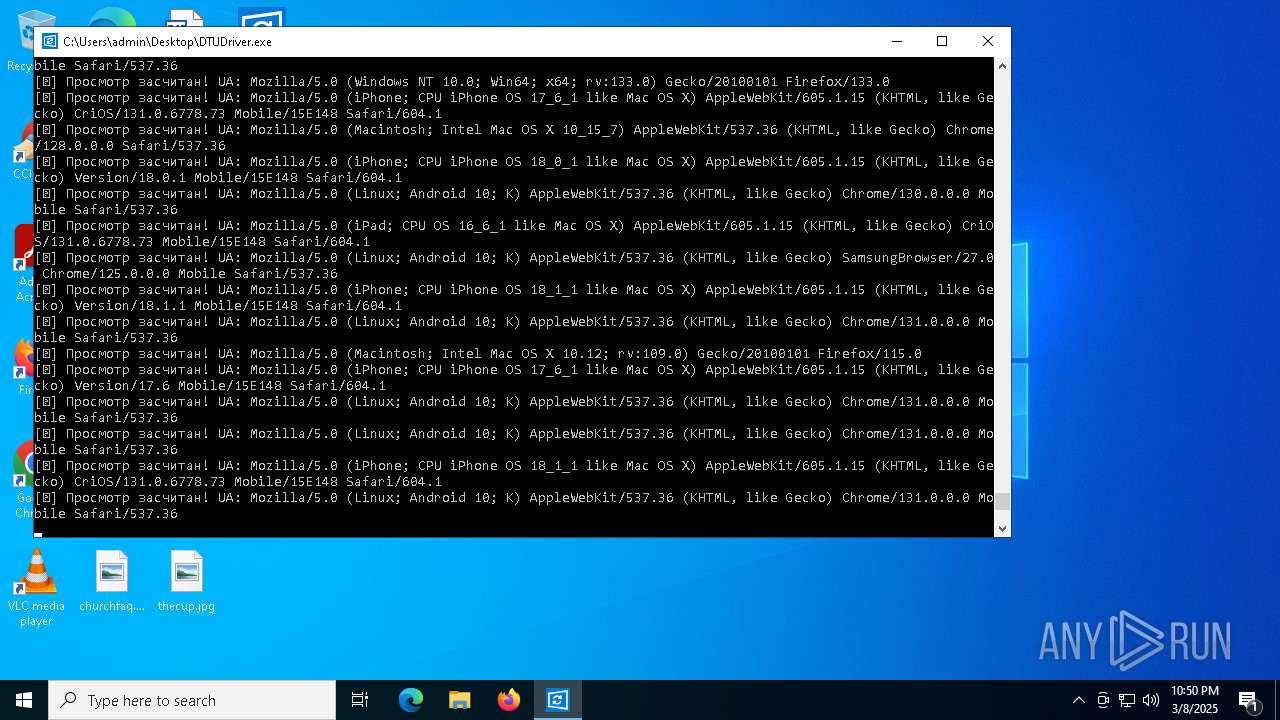
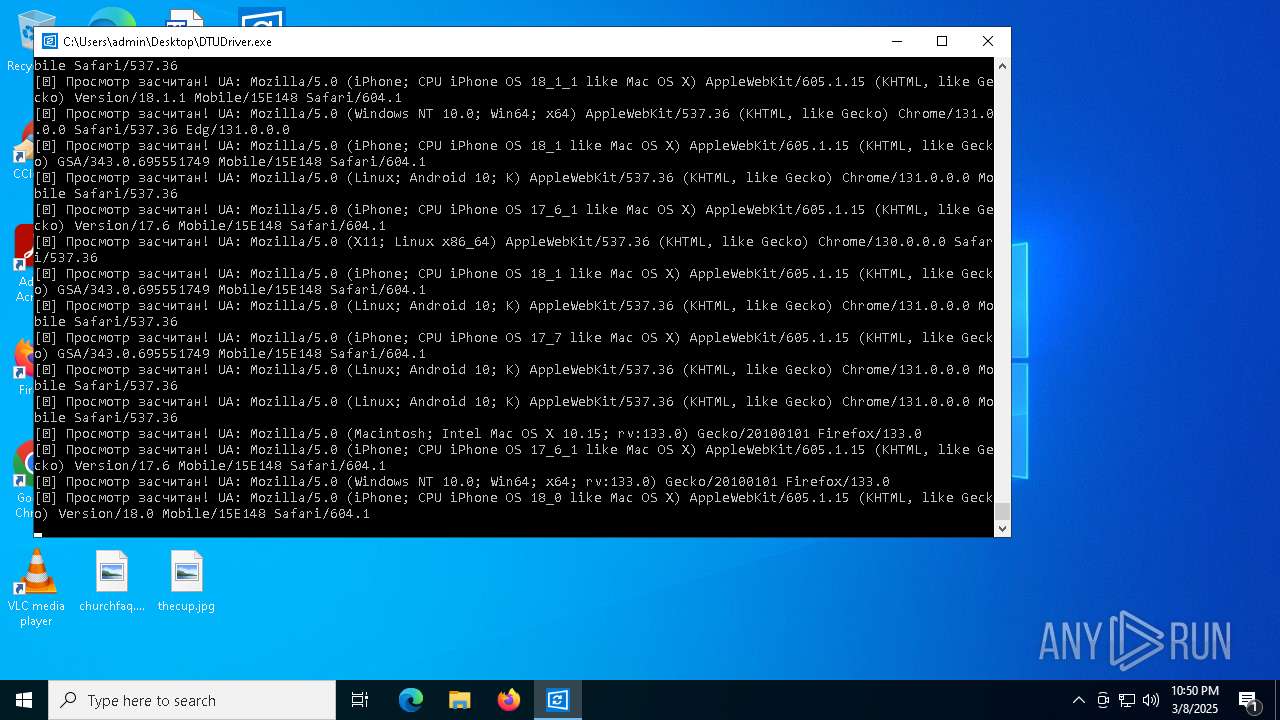
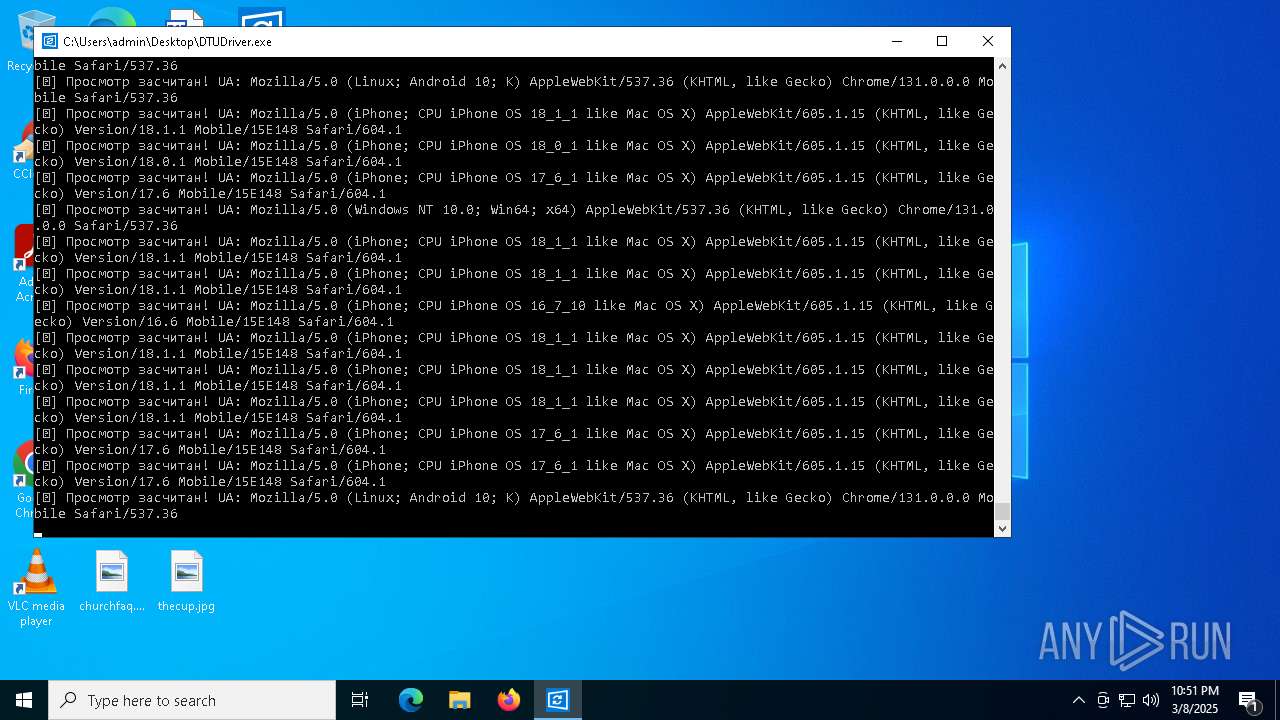
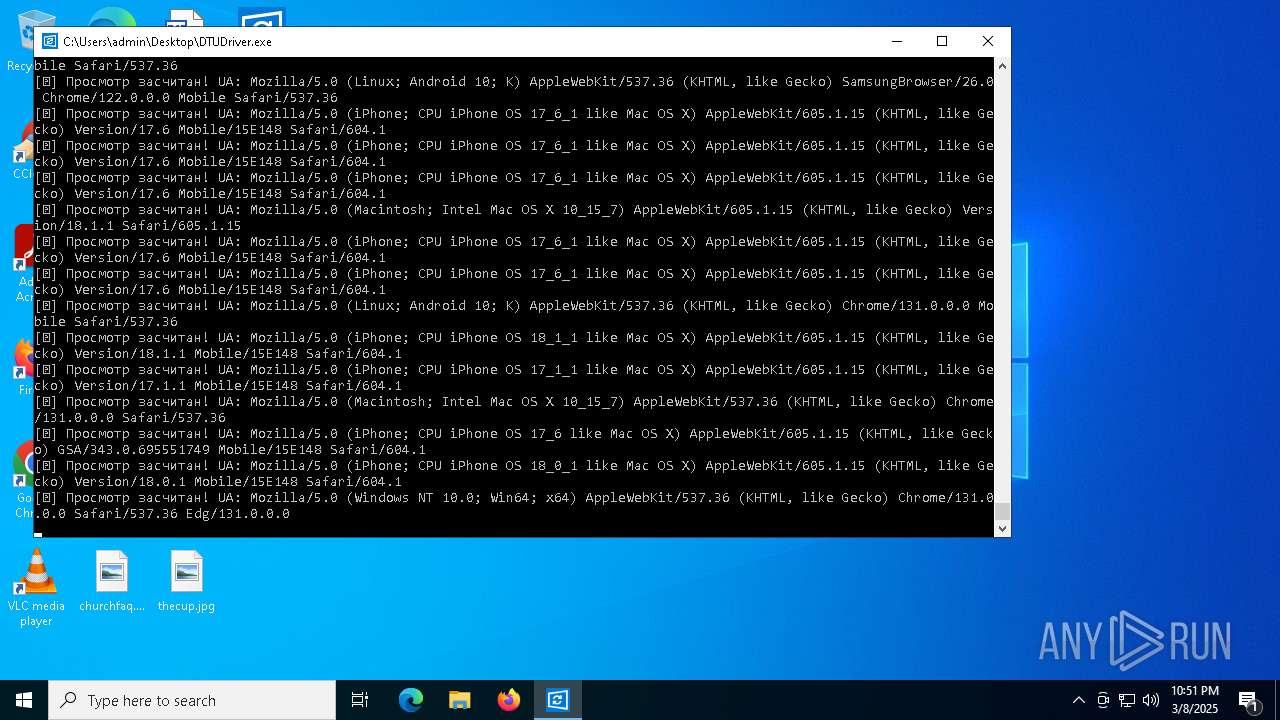
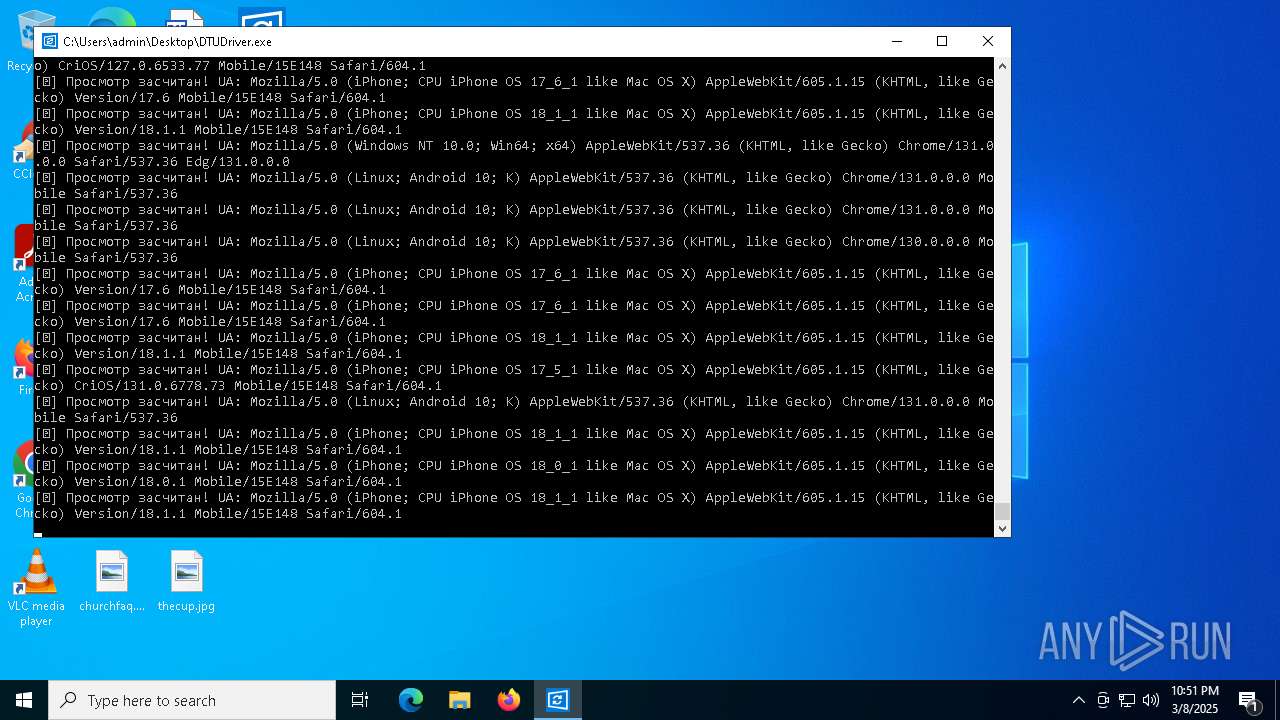
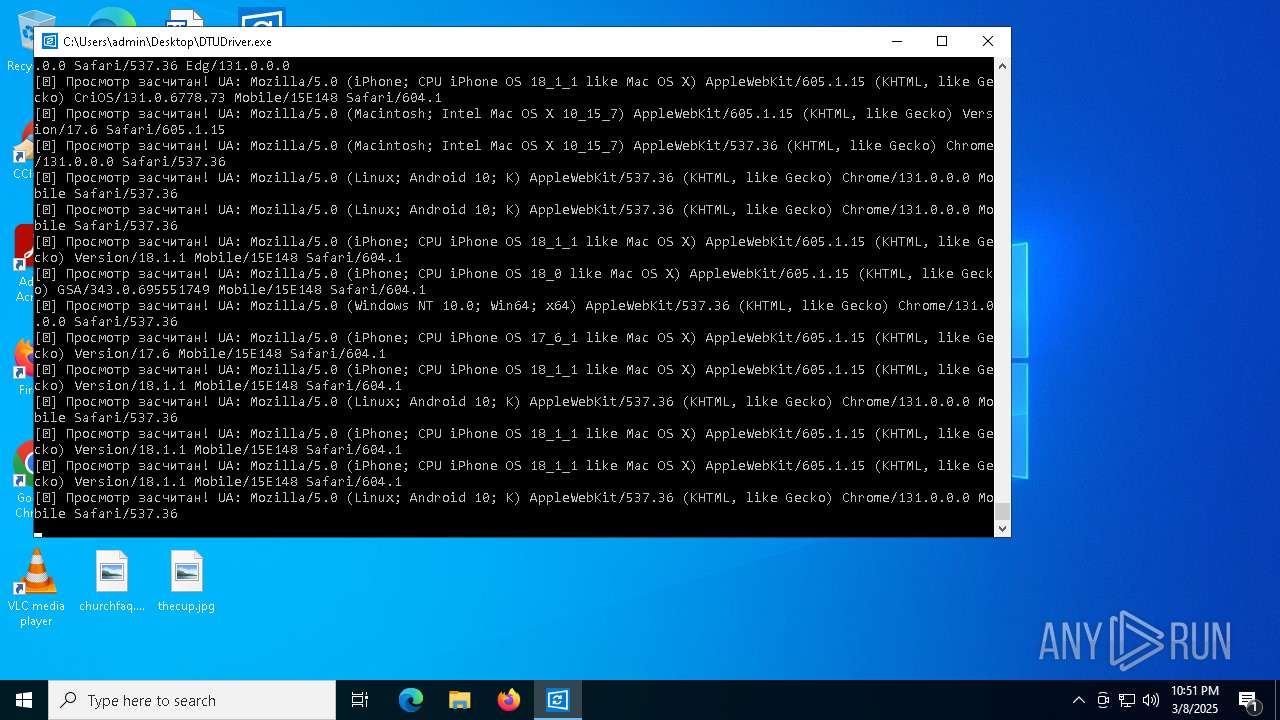
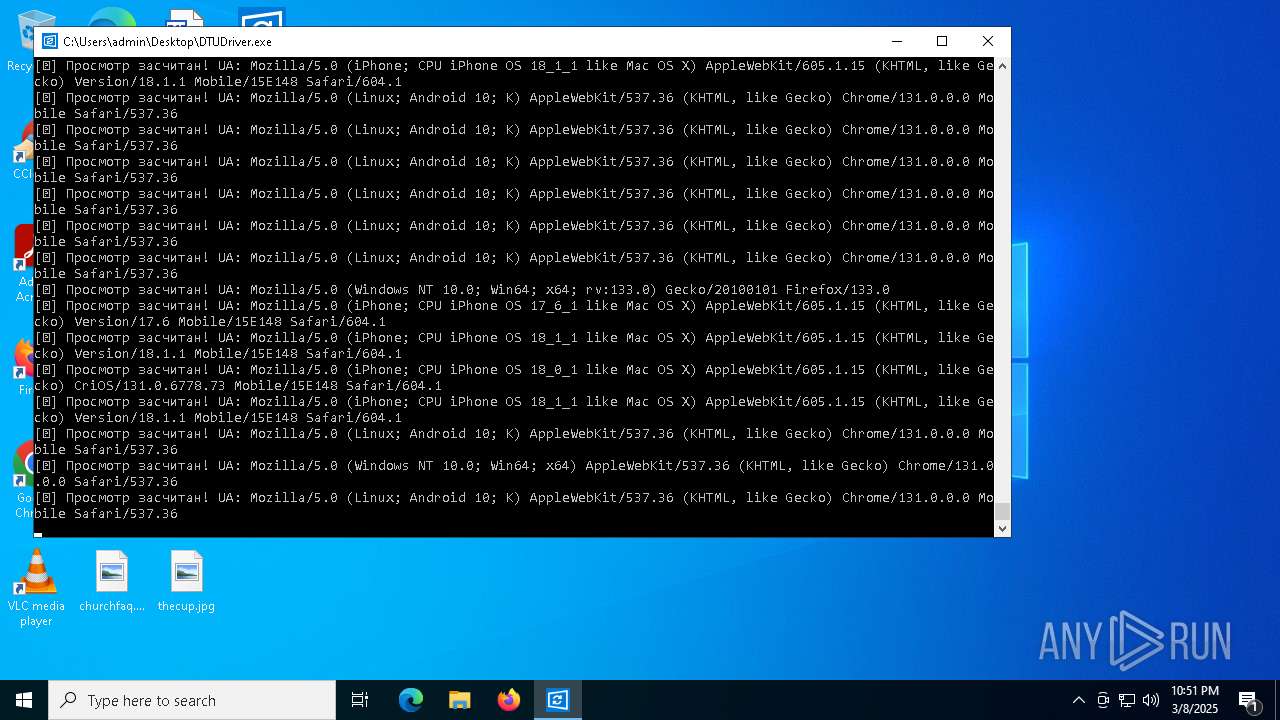
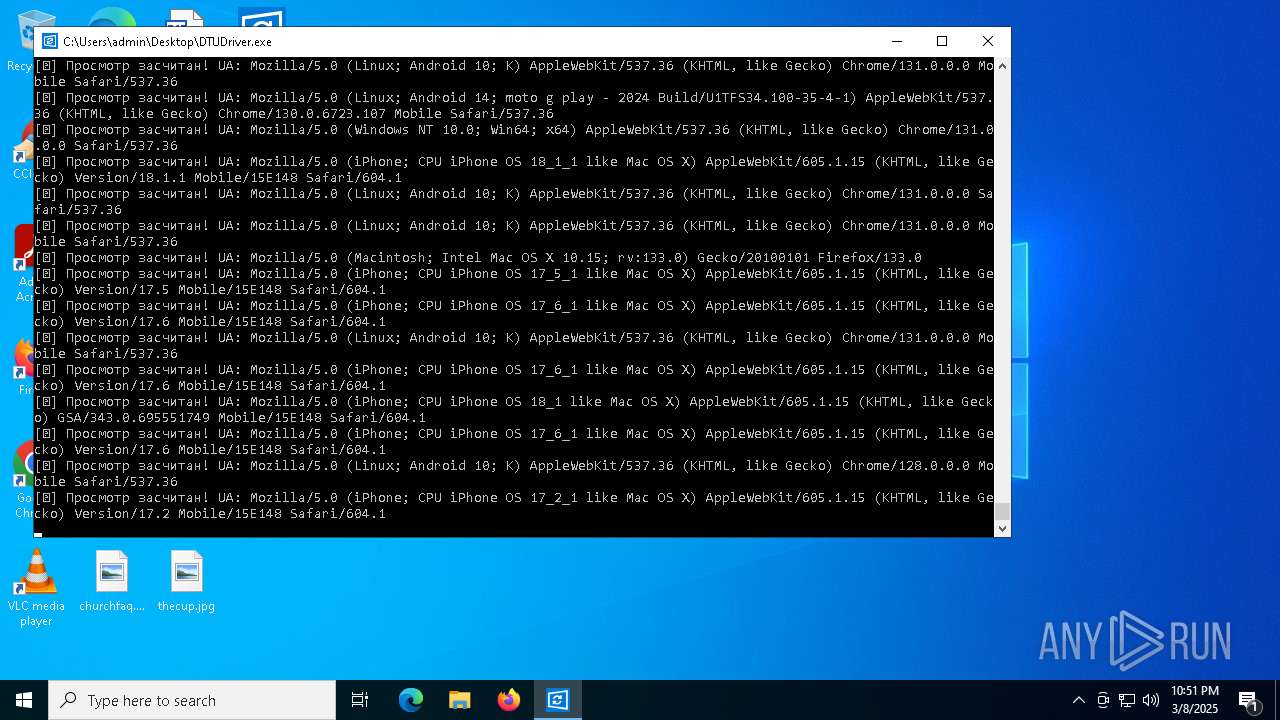
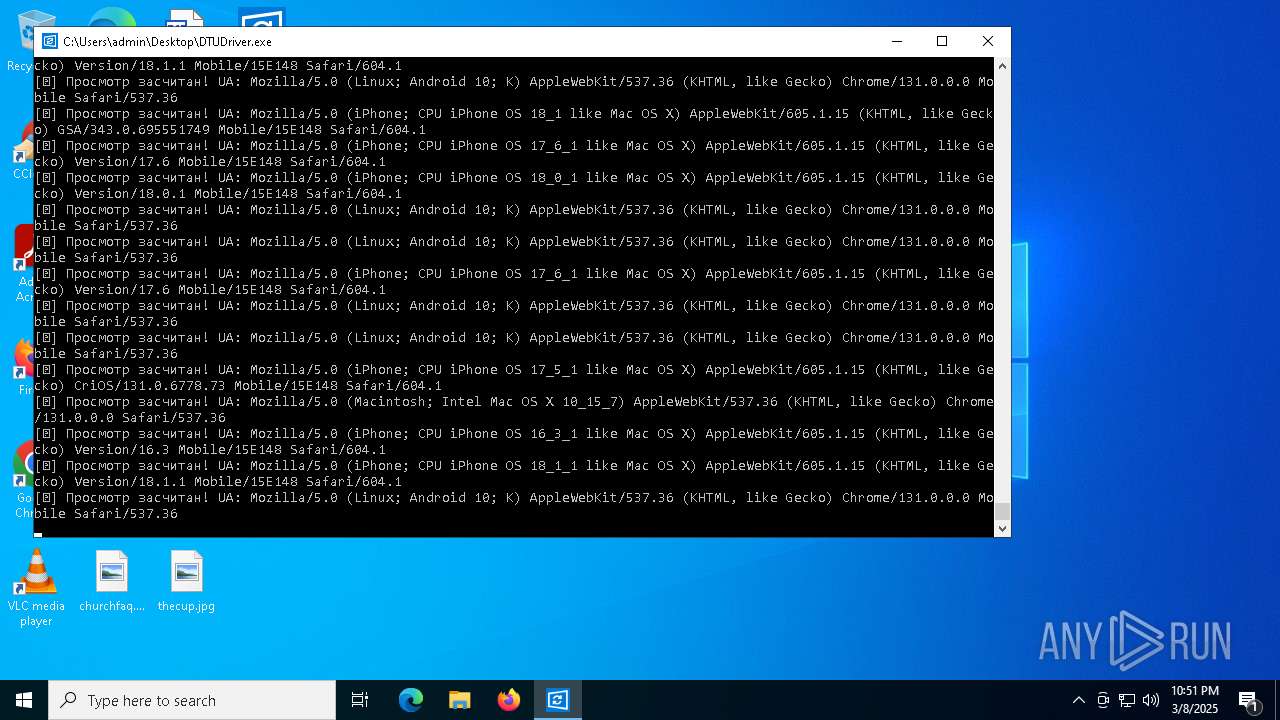
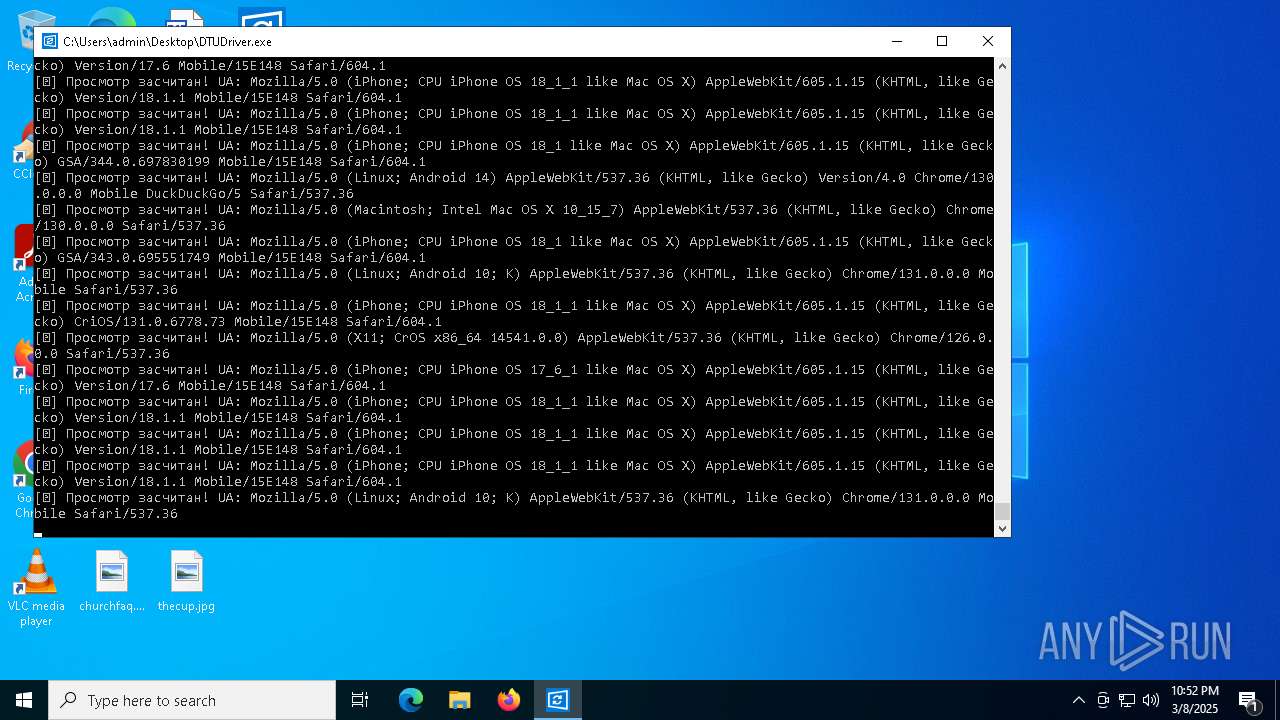
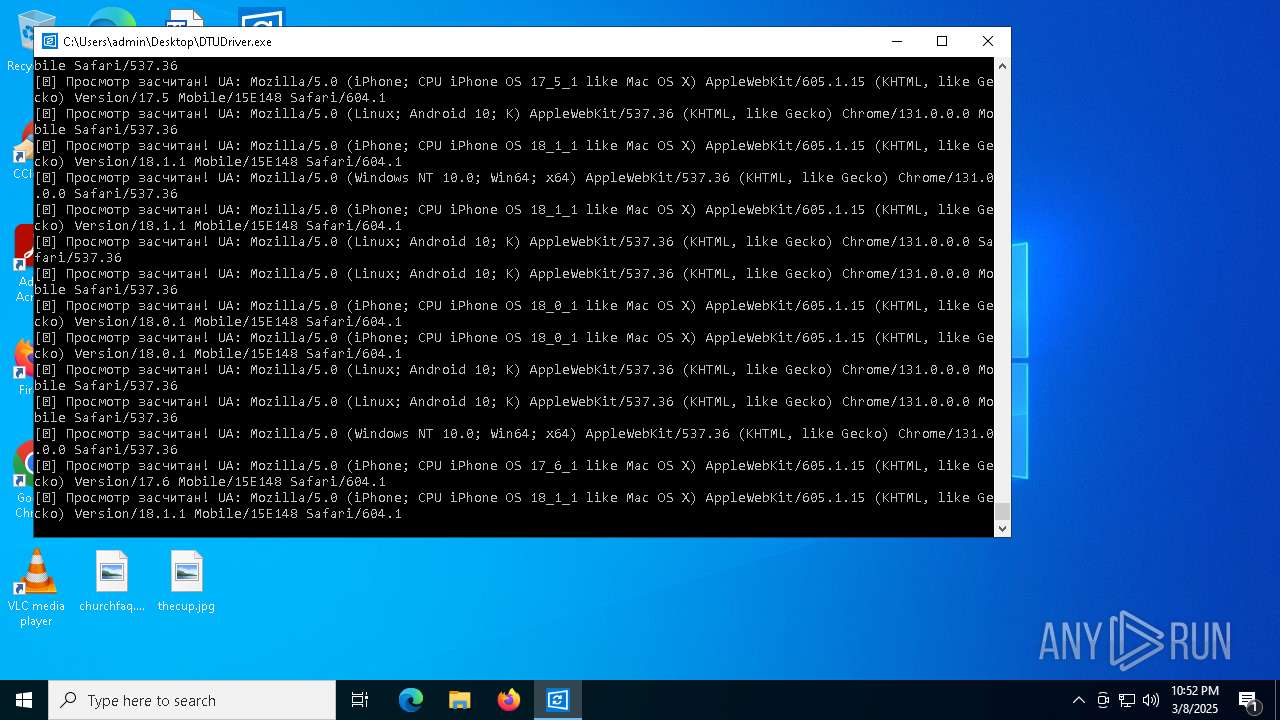
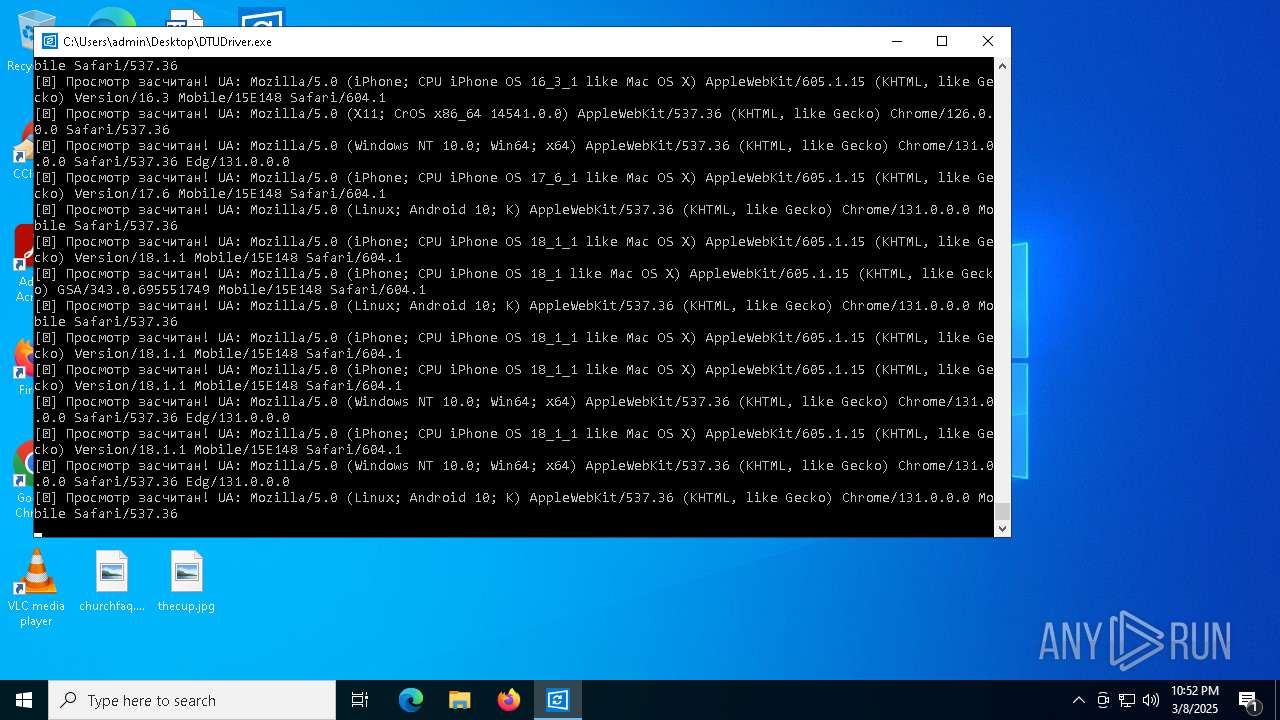
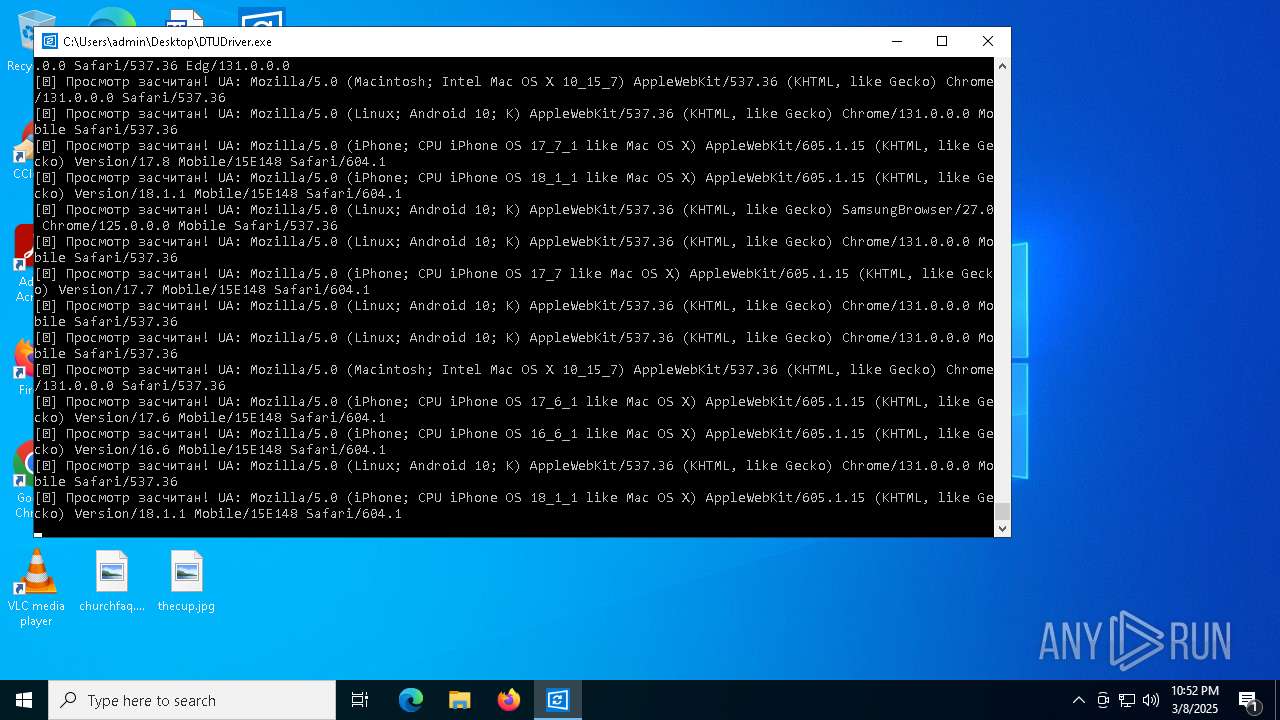
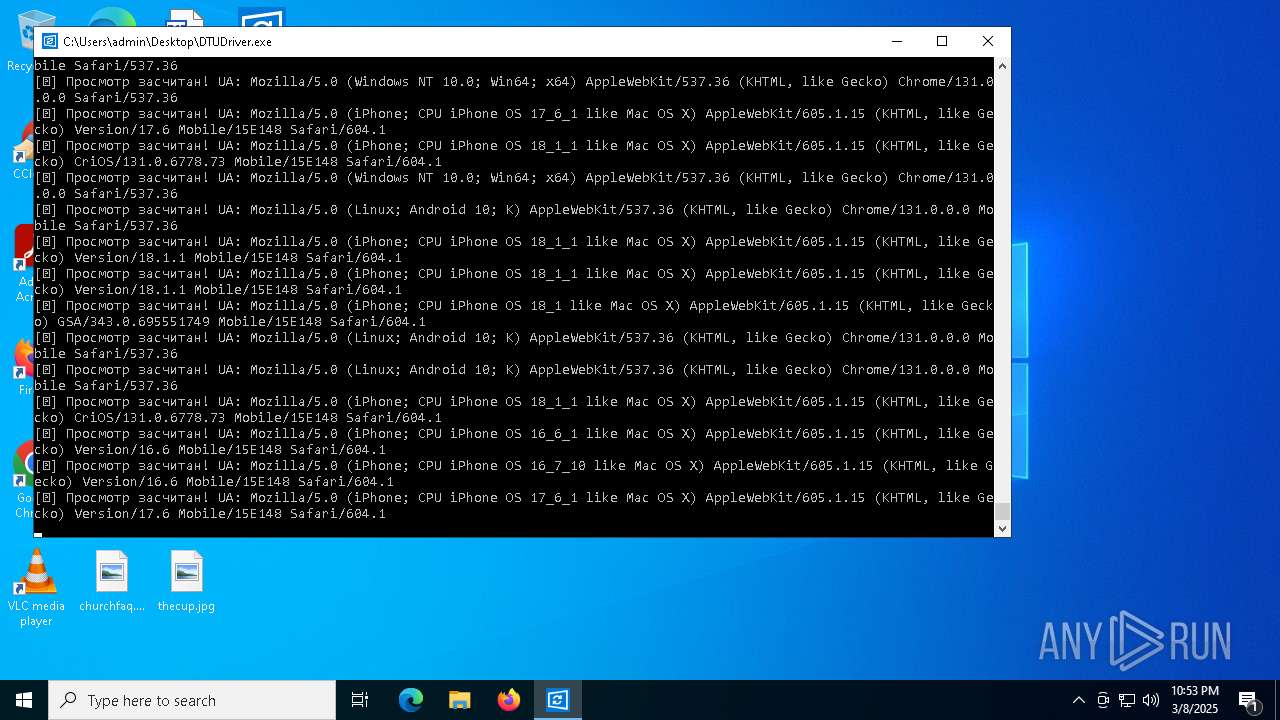
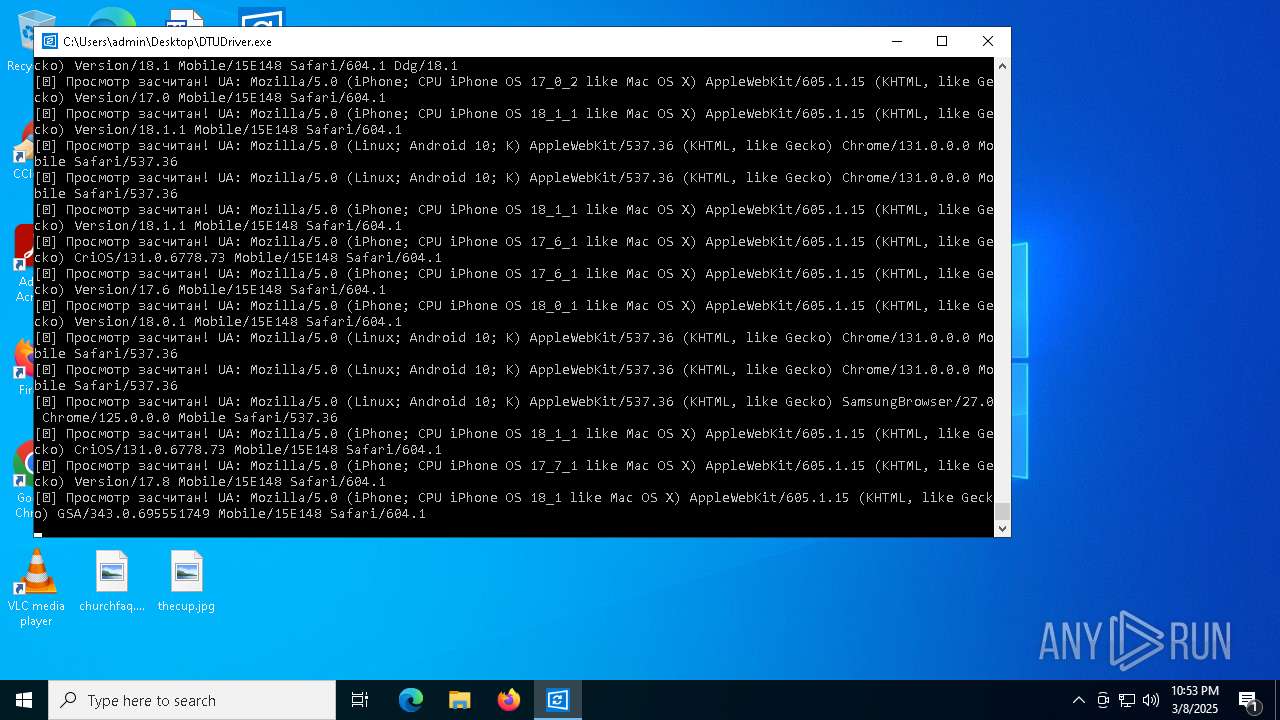
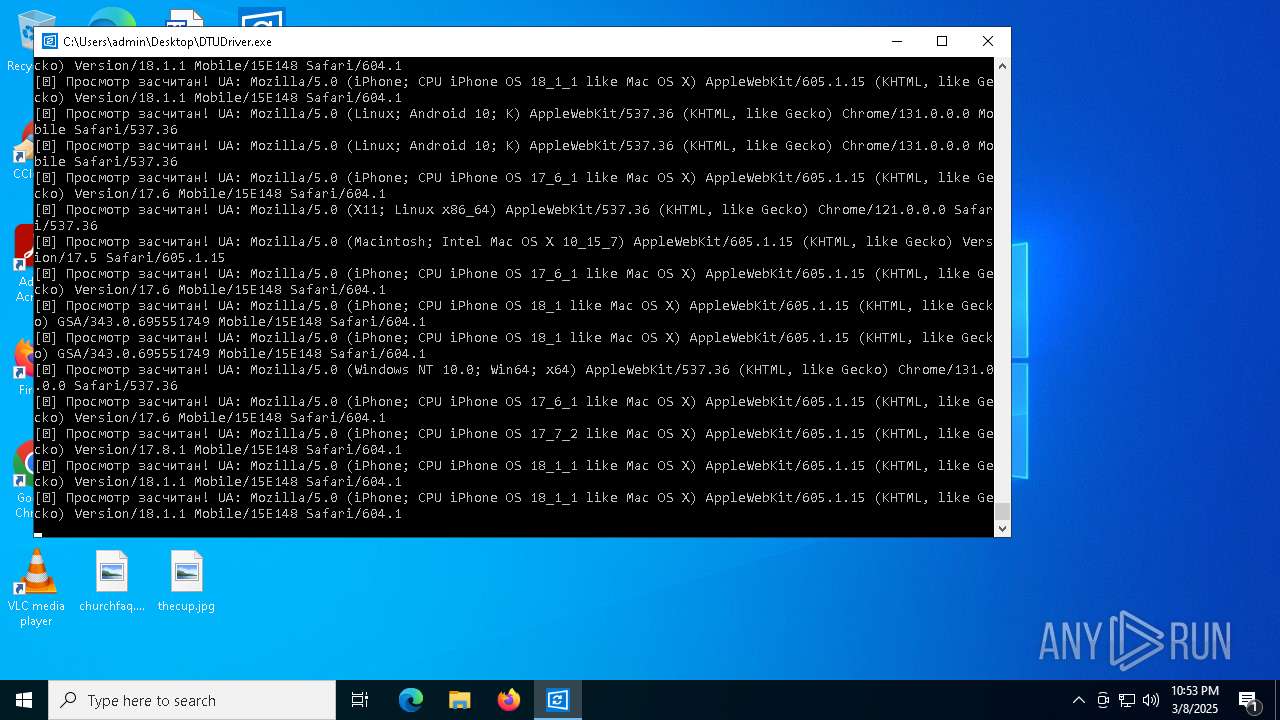
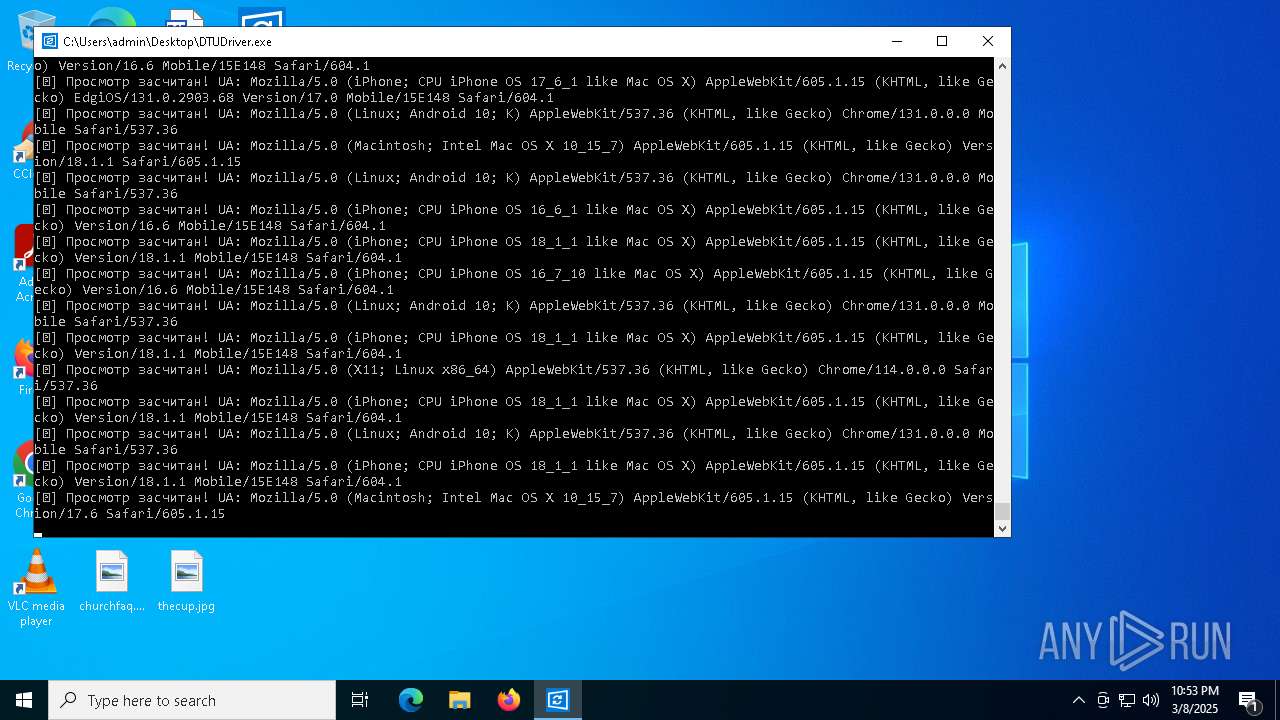
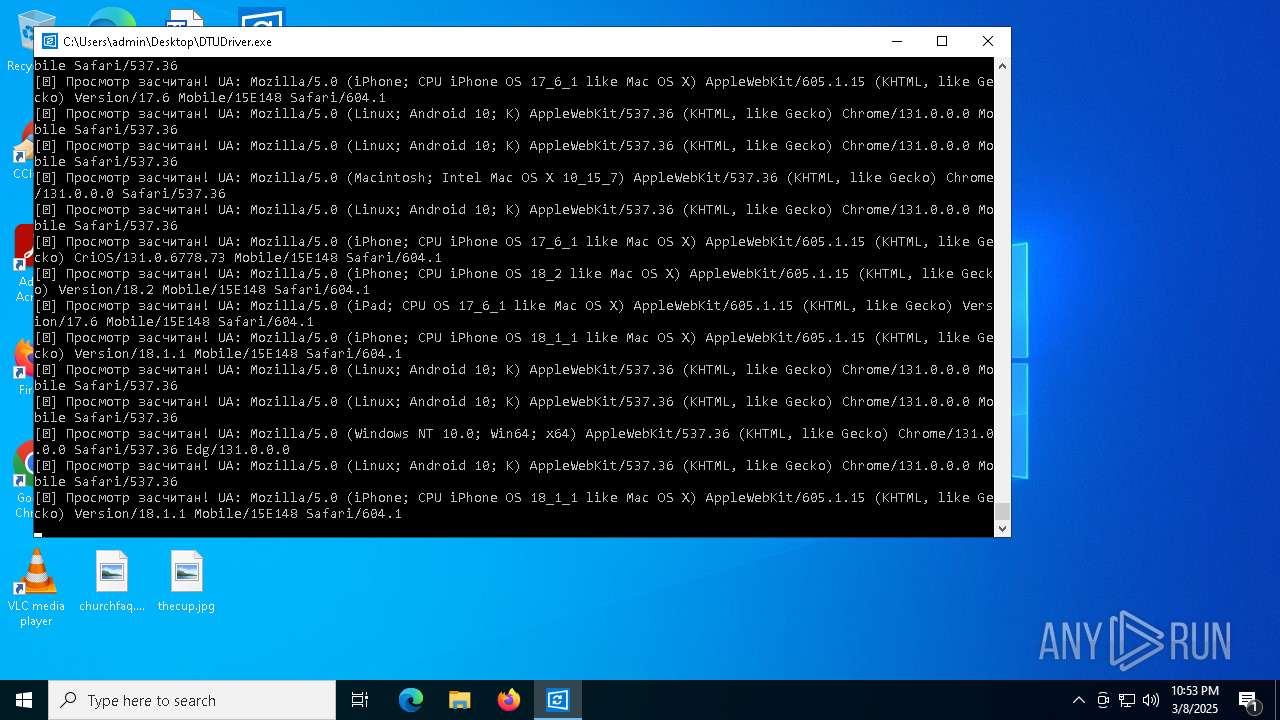
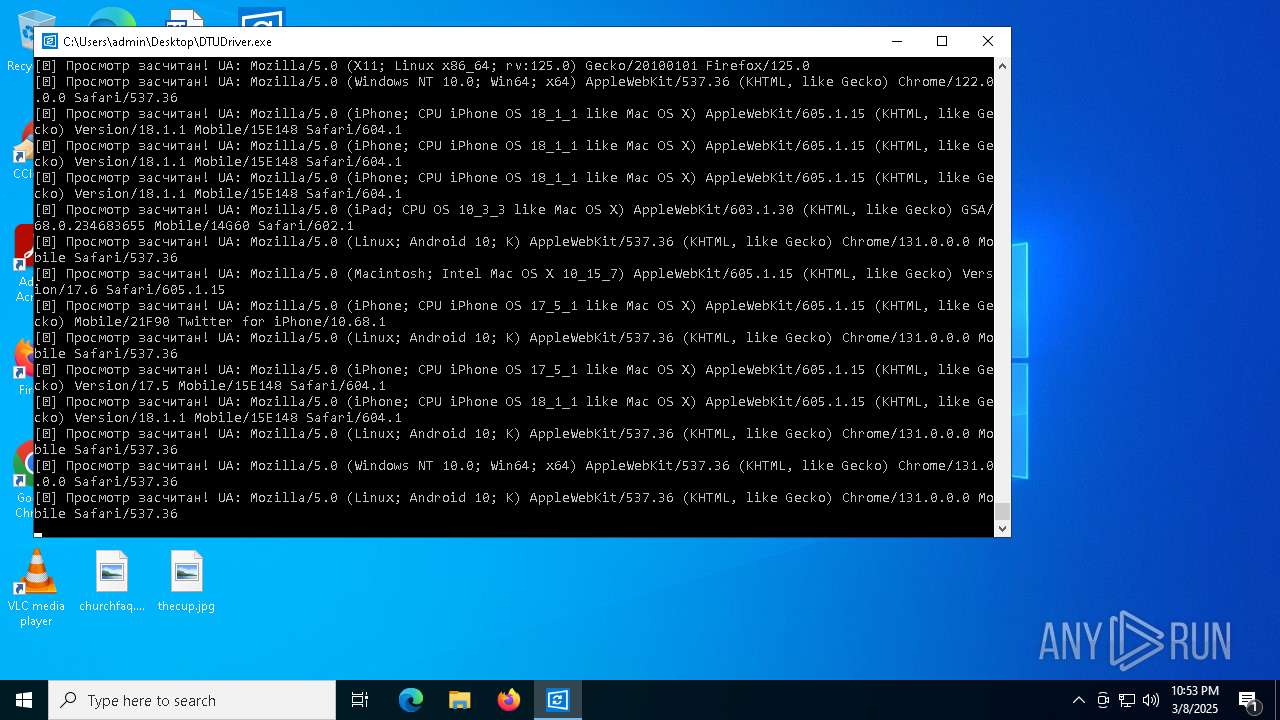
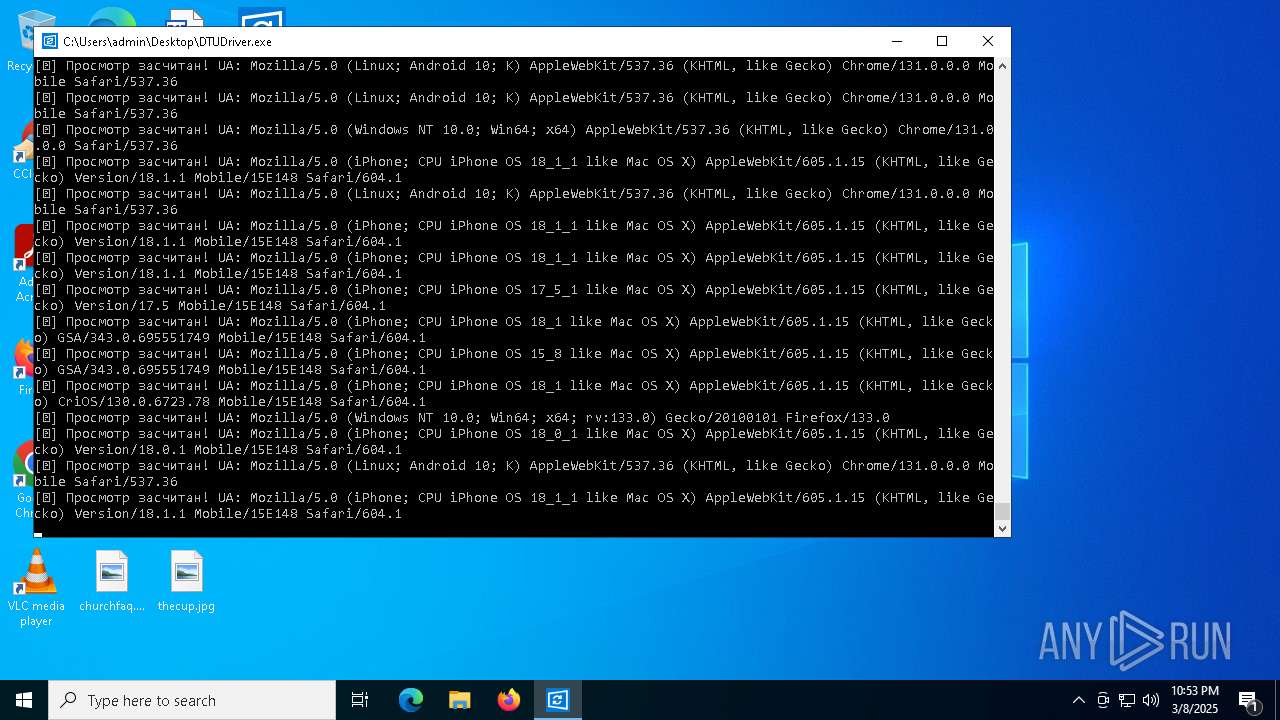
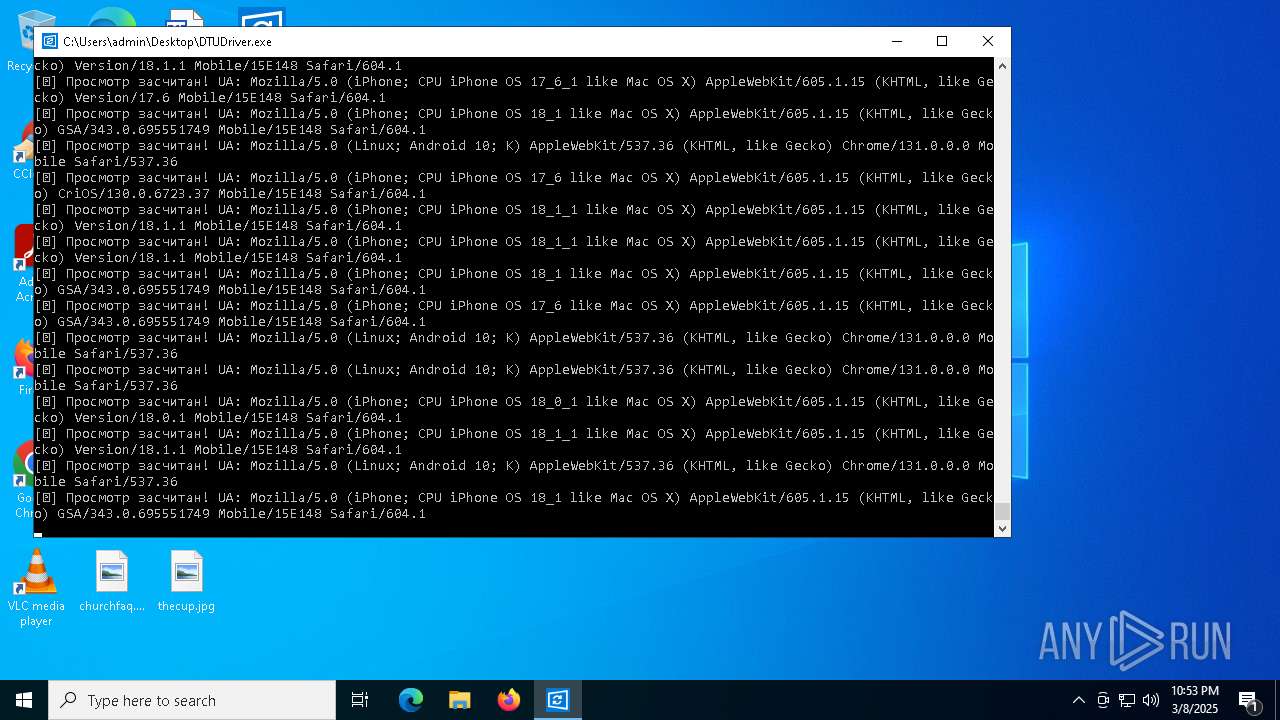
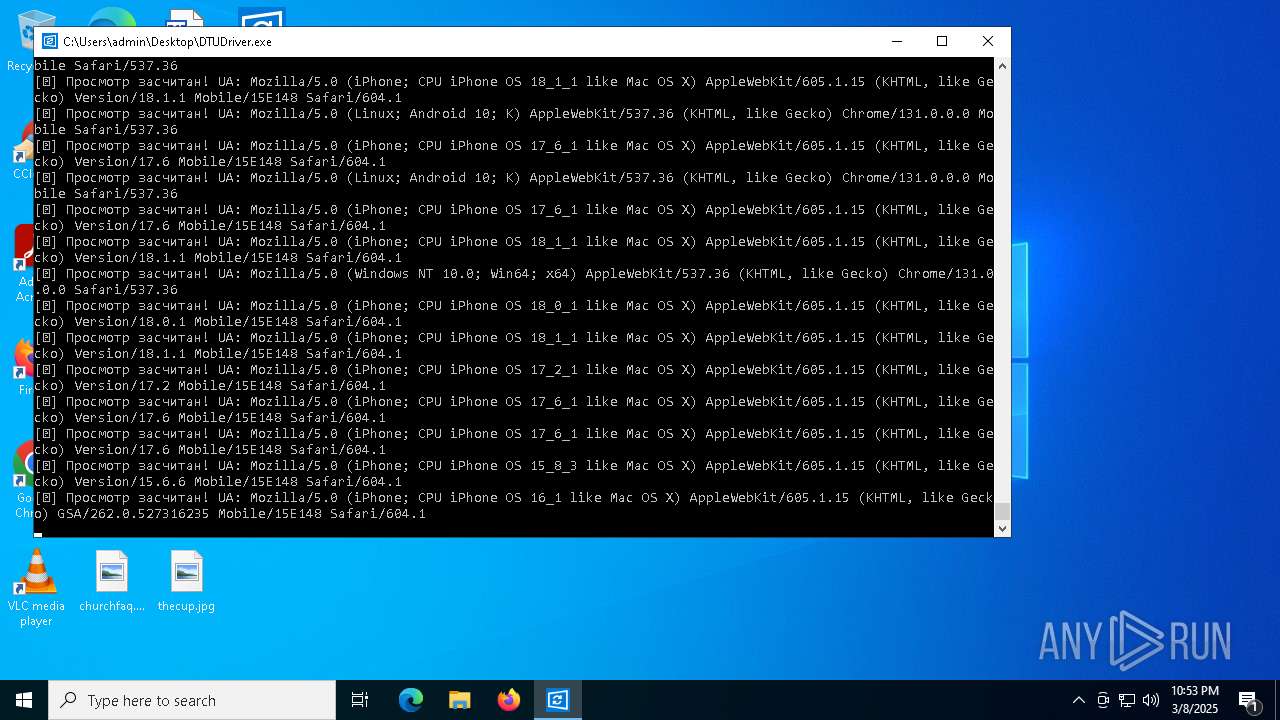
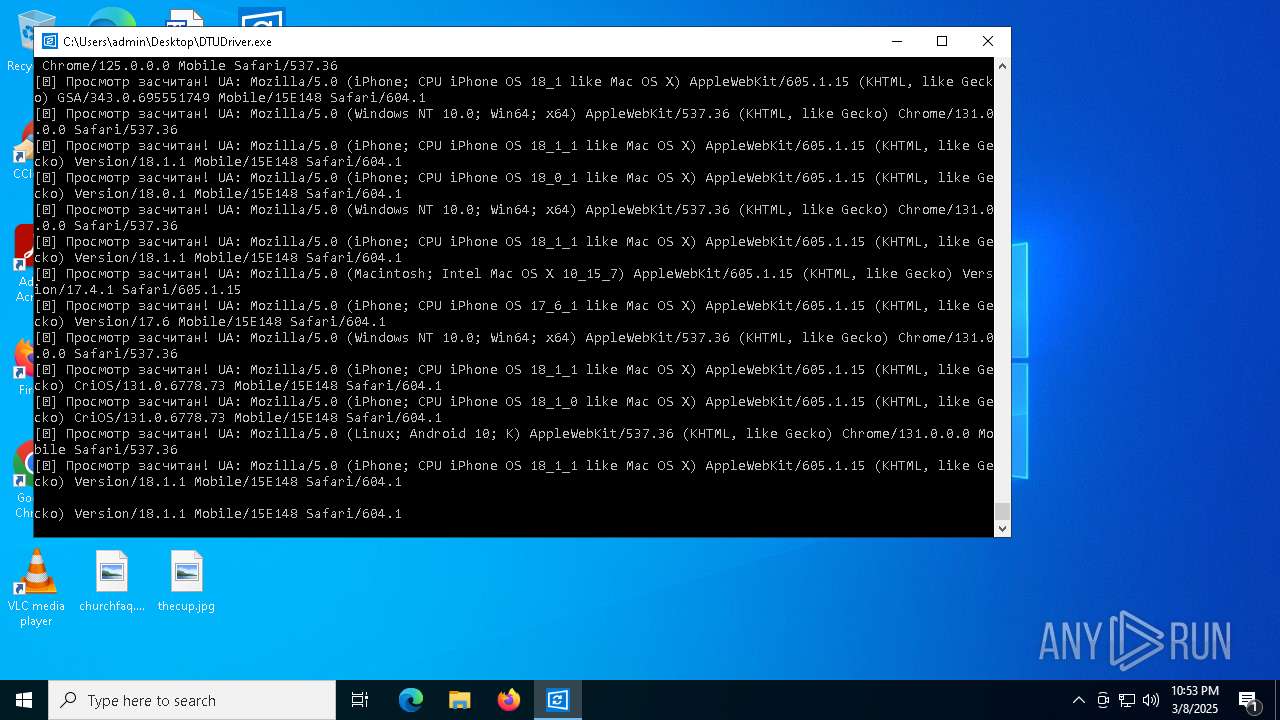
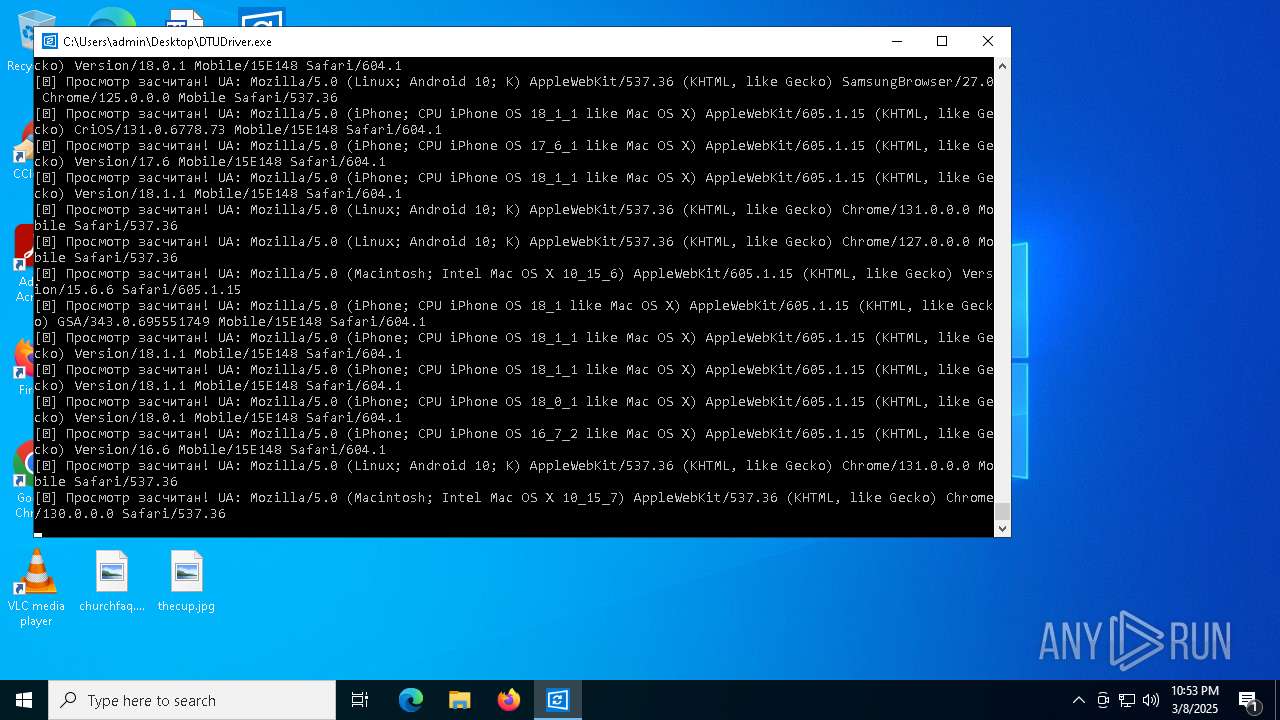
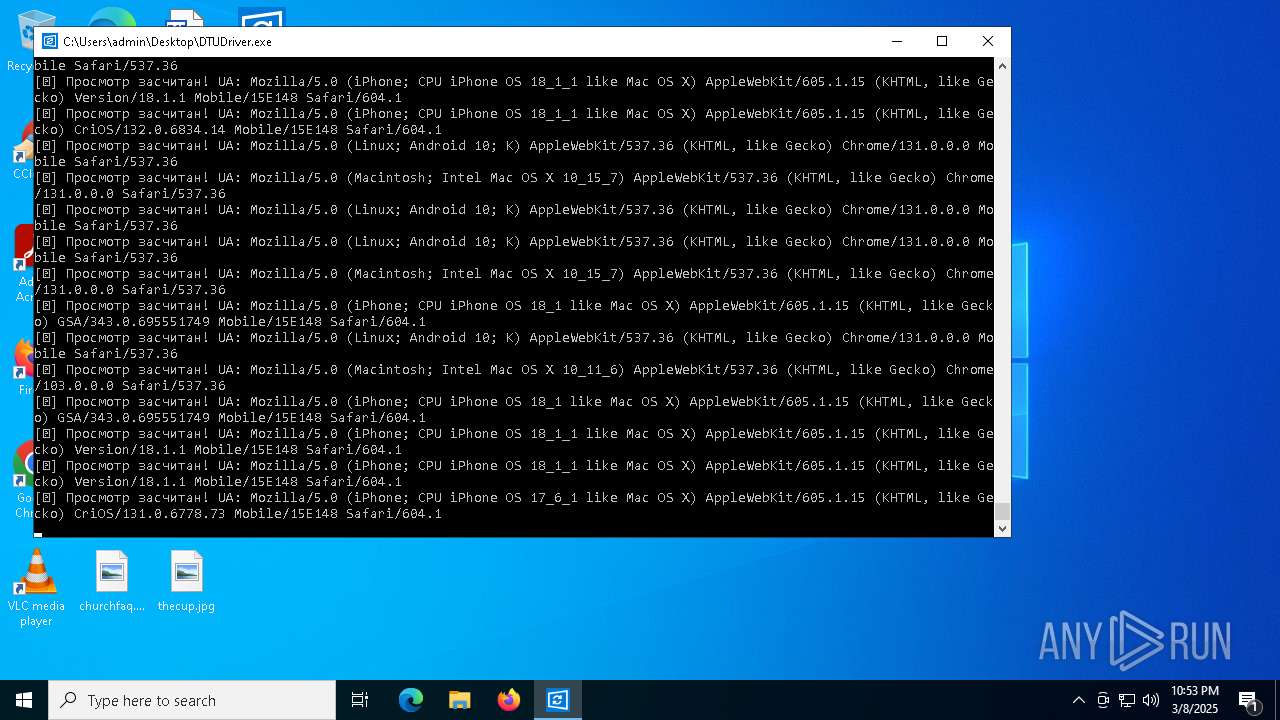
| File name: | DTUDriver.exe |
| Full analysis: | https://app.any.run/tasks/72285c3d-6cc4-4274-8b7c-77d47b5a31a0 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2025, 22:48:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 95EAF5446BA5B1BEC5875AC9436B24E8 |
| SHA1: | EAAC08FF3F441830A1A93C311EDE326C6A6636BB |
| SHA256: | D5677C0F0F2D30833E75F0C556DBEC07D89539B10FDE02EC07033900724E69EB |
| SSDEEP: | 98304:rxb2bKAp7qZ721zD4I8q4QCNE4gst+KkJKNueaoPr0sie69B0bZqPJx69XzOx9AS:kp3A5TyYpGtx++tj6vkxJhGpct |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- DTUDriver.exe (PID: 5308)
Process drops legitimate windows executable
- DTUDriver.exe (PID: 5308)
Starts a Microsoft application from unusual location
- DTUDriver.exe (PID: 5308)
- DTUDriver.exe (PID: 6456)
The process drops C-runtime libraries
- DTUDriver.exe (PID: 5308)
Application launched itself
- DTUDriver.exe (PID: 5308)
Executable content was dropped or overwritten
- DTUDriver.exe (PID: 5308)
Loads Python modules
- DTUDriver.exe (PID: 6456)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7148)
INFO
The sample compiled with english language support
- DTUDriver.exe (PID: 5308)
Checks supported languages
- DTUDriver.exe (PID: 5308)
- DTUDriver.exe (PID: 6456)
- ShellExperienceHost.exe (PID: 7148)
Create files in a temporary directory
- DTUDriver.exe (PID: 5308)
Reads the computer name
- DTUDriver.exe (PID: 6456)
- DTUDriver.exe (PID: 5308)
- ShellExperienceHost.exe (PID: 7148)
Checks proxy server information
- DTUDriver.exe (PID: 6456)
- BackgroundTransferHost.exe (PID: 1616)
- slui.exe (PID: 3024)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1616)
- BackgroundTransferHost.exe (PID: 5960)
- BackgroundTransferHost.exe (PID: 6080)
- BackgroundTransferHost.exe (PID: 4244)
- BackgroundTransferHost.exe (PID: 5404)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 1616)
- slui.exe (PID: 3024)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1616)
PyInstaller has been detected (YARA)
- DTUDriver.exe (PID: 5308)
- DTUDriver.exe (PID: 6456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:08 22:40:18+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 178688 |
| InitializedDataSize: | 168448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 10.0.19041.5067 |
| ProductVersionNumber: | 10.0.19041.5067 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Direct To Update Driver |
| FileVersion: | 10.0.19041.5067 (WinBuild.160101.0800) |
| InternalName: | Direct To Update Driver |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | DTUDriver.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.5067 |
Total processes
150
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1616 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3024 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5308 | "C:\Users\admin\Desktop\DTUDriver.exe" | C:\Users\admin\Desktop\DTUDriver.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Direct To Update Driver Version: 10.0.19041.5067 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DTUDriver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5960 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6080 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6456 | "C:\Users\admin\Desktop\DTUDriver.exe" | C:\Users\admin\Desktop\DTUDriver.exe | DTUDriver.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Direct To Update Driver Version: 10.0.19041.5067 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
59 855
Read events
59 838
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5960) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5960) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5960) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1616) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1616) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1616) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5404) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5404) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5404) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6080) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
66
Suspicious files
7
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_lzma.pyd | executable | |
MD5:9EC7F84B1976B469C4FA4001D5FF4412 | SHA256:14762C570A210D196F5FC8F89C792E093B0875695251D490CBD4BA79C8F64999 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_queue.pyd | executable | |
MD5:2CE0E1816468940A4025EFB31CD75150 | SHA256:0746DAB0FEAB5AB709FDF888A9A15B050B0FAF6C934C61788249B32E344D38F7 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_asyncio.pyd | executable | |
MD5:A577FF6DE2ADD83120127061D7C294A8 | SHA256:8A12F0E5EF034F5C9FF5C506F701A00E3CD16009E2D3431F54EAD15BC138629F | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_hashlib.pyd | executable | |
MD5:D0A2127B7AA88B6A47C170C933402438 | SHA256:2598B1D5AF9606A85CF8BA00EB5E0EFB5C405BE3AD852D1B070D08E0EE34C526 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_socket.pyd | executable | |
MD5:20631CD0C1477F9B0D3897FA61EF749D | SHA256:A4302A78958AE7F4FB2E1B4A4B2187434D39F972D7F3AA5D1E58759326B539C7 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_ctypes.pyd | executable | |
MD5:FC2DA679024ED27F02ECD1B05CF14CDA | SHA256:AB0A527BEDFD18E11B2FACC003407B6E565F114E010499F73DE35E1B01B6D340 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_overlapped.pyd | executable | |
MD5:E9436905D28DEAEF3B04E1FE2F05D7C3 | SHA256:B341E788F0E90149B24B3176A6EFB2FE1A3677BCA5E2A24EF314D24BE32EE983 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\_wmi.pyd | executable | |
MD5:39FCA3CD9A98B14C4E47225EE28063D3 | SHA256:9E65EE7978BFE5B5A392B6DF8279D2F97ED8B0F36F8F89DA4AD28C7866B92432 | |||
| 5308 | DTUDriver.exe | C:\Users\admin\AppData\Local\Temp\_MEI53082\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:D755D3165174669240CF8B4673BF13EB | SHA256:29996C70B1C4E4A8FE80E33FF0C5D0658A12AB9B2A0C578ABD6AB3C395341AD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
11 219
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6744 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2852 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2852 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1616 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6456 | DTUDriver.exe | 212.109.194.120:443 | zvonili.com | JSC IOT | RU | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6744 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
zvonili.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |