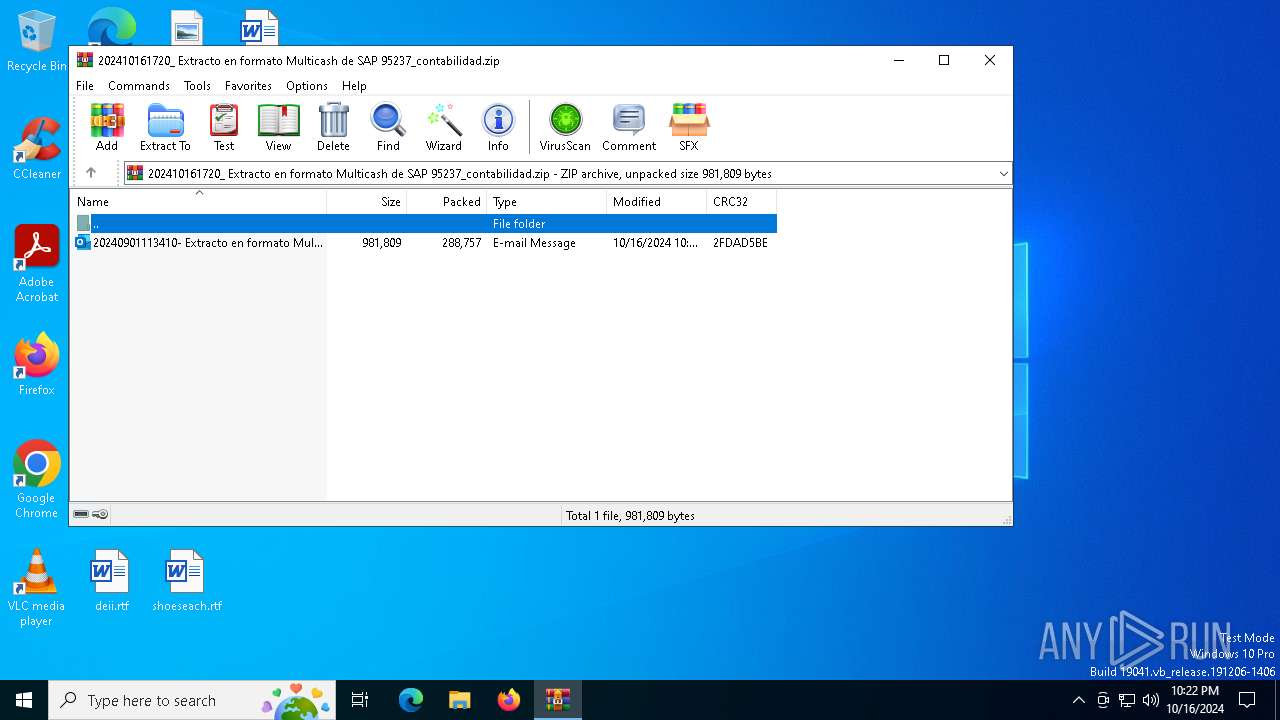
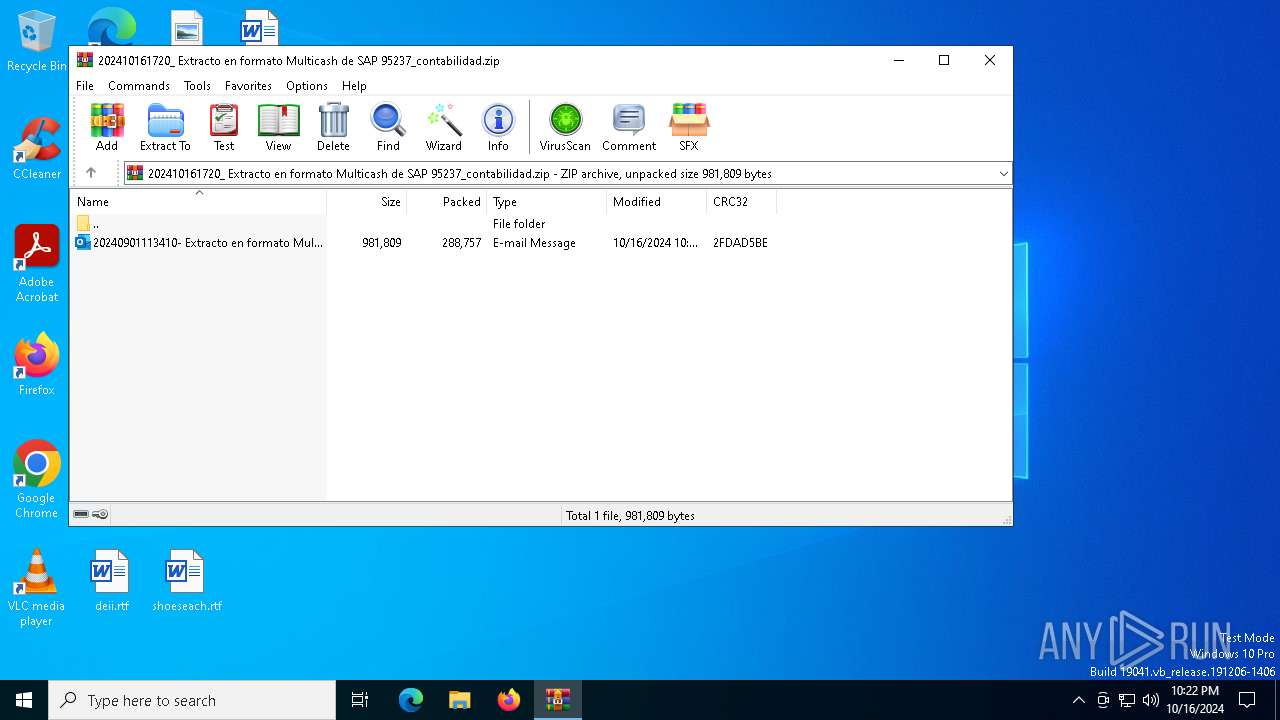
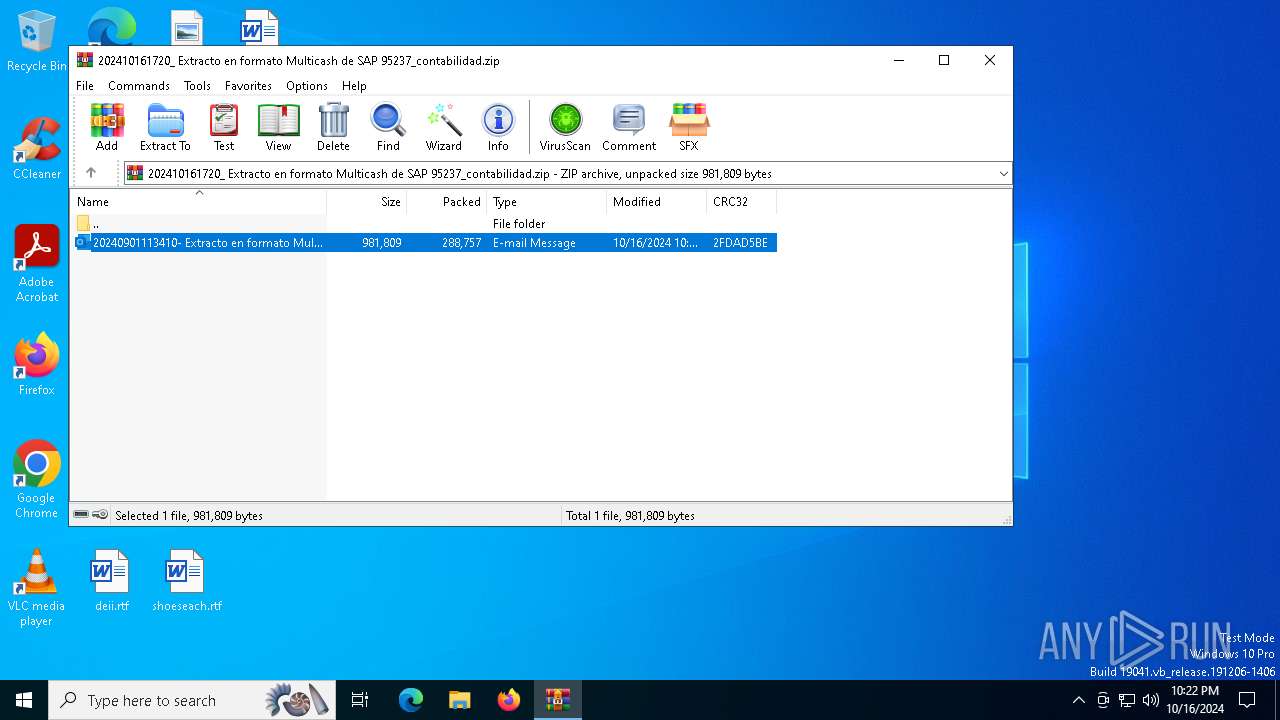
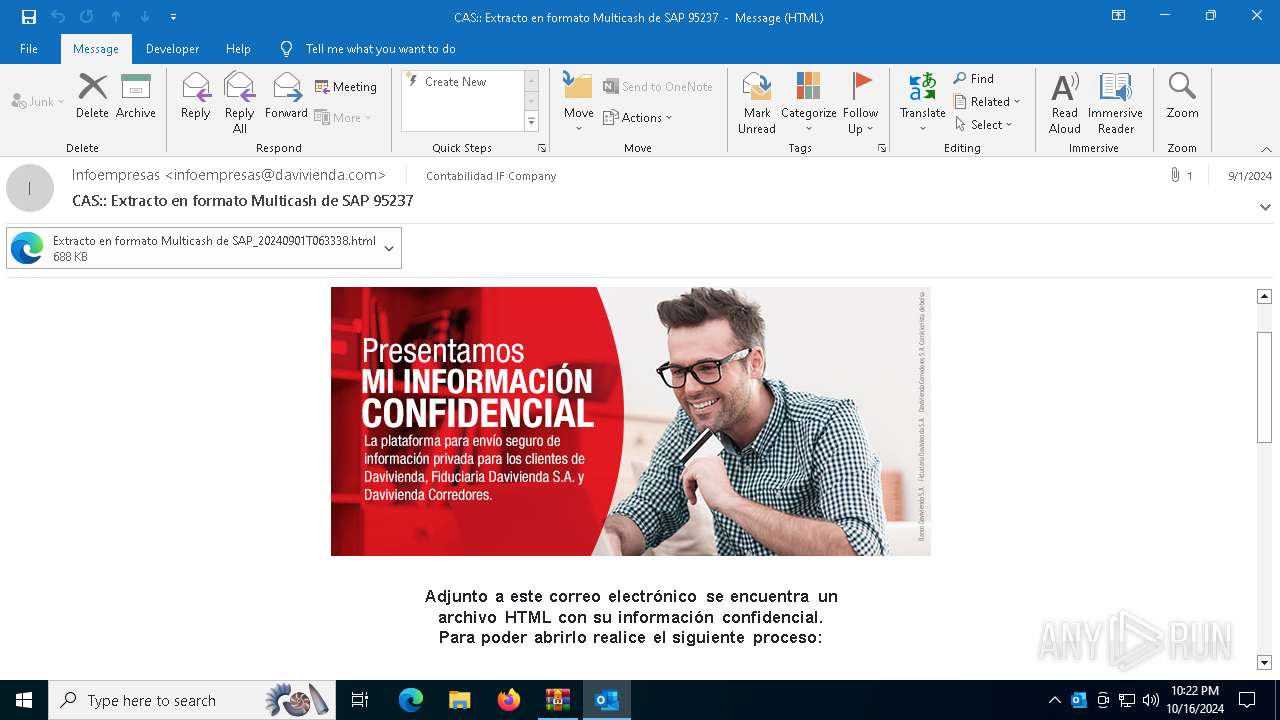
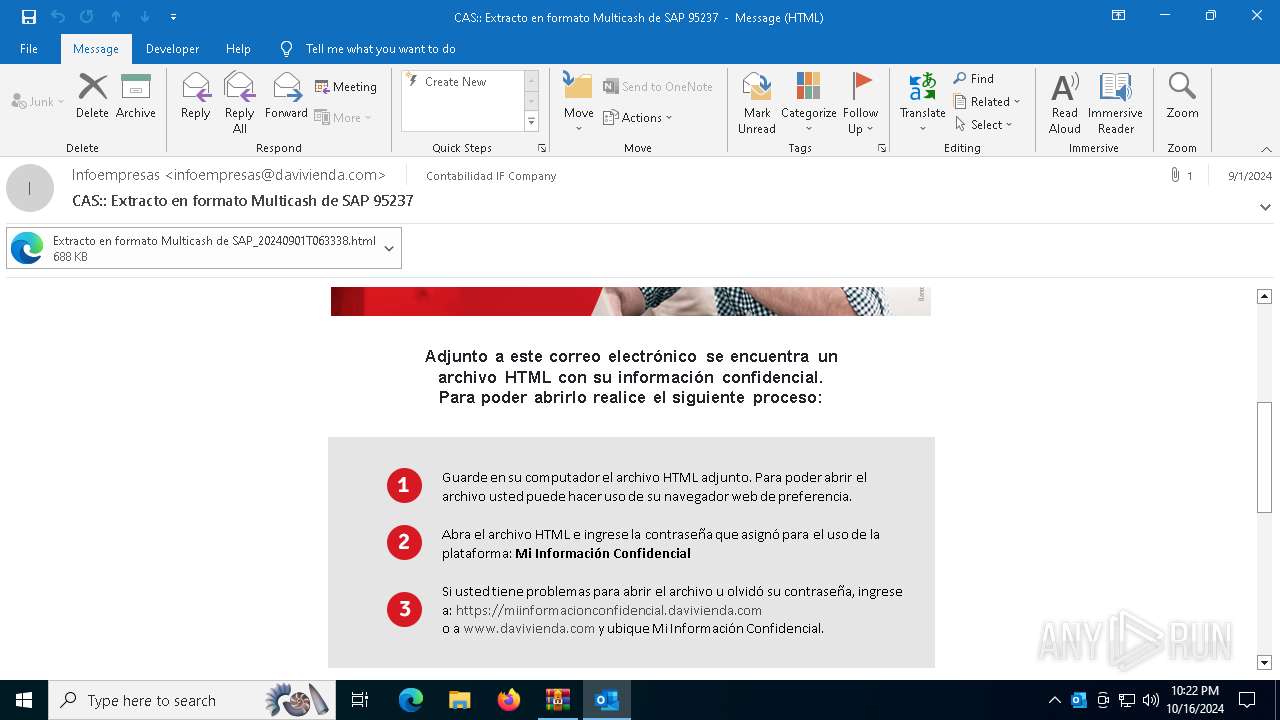
| File name: | 202410161720_ Extracto en formato Multicash de SAP 95237_contabilidad.zip |
| Full analysis: | https://app.any.run/tasks/254c4f46-d651-4316-a36c-78815dd7589e |
| Verdict: | Malicious activity |
| Analysis date: | October 16, 2024, 22:21:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D631168E383597DA25D72851EC41E81B |
| SHA1: | 542DC85B0FB5A3C9BCE216353EBDCE4321293CCB |
| SHA256: | D5668748C7C711C8C34E872DA414E04C58FBED1AD326714A3430CBA7873E7DC7 |
| SSDEEP: | 6144:/67+lf51HxzKywlUhLlzCokUTn18Q67Z6ZoOE86qOhGO6Ka23X2xLxlTlGNRaAyT:qm51Yhgz3pCtn86HU4pX2zlTlGNRarT |
MALICIOUS
Email came from third-party service (Amazon SES)
- WinRAR.exe (PID: 5624)
SUSPICIOUS
No suspicious indicators.INFO
Email with attachments
- WinRAR.exe (PID: 5624)
Email verification fail (SPF, DKIM or DMARC)
- WinRAR.exe (PID: 5624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:16 22:20:16 |
| ZipCRC: | 0x2fdad5be |
| ZipCompressedSize: | 288757 |
| ZipUncompressedSize: | 981809 |
| ZipFileName: | 20240901113410- Extracto en formato Multicash de SAP 95237-contabilidad.eml |
Total processes
137
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4548 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "57A100F0-B77F-41F4-A9B1-5EA8F5471386" "D5030F8C-DD35-4502-8053-983965BD36E0" "6240" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 5624 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\202410161720_ Extracto en formato Multicash de SAP 95237_contabilidad.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6240 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Rar$DIa5624.13713\20240901113410- Extracto en formato Multicash de SAP 95237-contabilidad.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6868 | C:\WINDOWS\system32\prevhost.exe {F8B8412B-DEA3-4130-B36C-5E8BE73106AC} -Embedding | C:\Windows\System32\prevhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Preview Handler Surrogate Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 264
Read events
14 146
Write events
998
Delete events
120
Modification events
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\202410161720_ Extracto en formato Multicash de SAP 95237_contabilidad.zip | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
| (PID) Process: | (5624) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {5FA29220-36A1-40F9-89C6-F4B384B7642E} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 0100000000000000C97C47D61920DB01 | |||
| (PID) Process: | (6240) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6240) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6240 |
| Operation: | write | Name: | 0 |
Value: 0B0E107D16601D414EC24F82212EEA5EA02663230046ADD9AAD09D83C8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511E030D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
0
Suspicious files
15
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6240 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6240 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\529835D7-C954-4082-9186-AFC185EFE8F7 | xml | |
MD5:01C836BF43BA1A8F8E3E85C46211AD90 | SHA256:2054BDA97EC58B36557DA7256F72DCF70C3453D59BBA25E19E55249A8403928E | |||
| 6240 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkEEED.tmp | text | |
MD5:6A38A821BC4E14A0D32E88C7541482A4 | SHA256:353FDCC338184526C1ACAFC2EB24362103996A4C48A737A21D61E4E3EC493B5B | |||
| 5624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5624.13713\20240901113410- Extracto en formato Multicash de SAP 95237-contabilidad.eml | binary | |
MD5:14571153B00C2B2D8B94DE0665A502B5 | SHA256:41DEB9493574A5D122967E115EDD64D9ABC44DEFEAF640AB31650D554063EB21 | |||
| 5624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5624.13713\20240901113410- Extracto en formato Multicash de SAP 95237-contabilidad.eml:OECustomProperty | binary | |
MD5:EAF19F8D16296B762B4FAF11A8ED3DEA | SHA256:1C22A2AAB8B8585BAB3249A47C612CEAF9841F155E98225EE829296EBB4100E5 | |||
| 6240 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:D818C49C3DE29B2112CB52F1F951F1A9 | SHA256:C409ACCDD1E449958BE77A6A57450FEBF595072B6FD46AE9E34511C48D28B257 | |||
| 5624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\202410161720_ Extracto en formato Multicash de SAP 95237_contabilidad.zip | compressed | |
MD5:269A86324316E4B84644AF22AA3FEBFE | SHA256:659DB288A088002170968E8C05EB3B36005C58E946E9DA7F4C46C141F0FDD771 | |||
| 6240 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:43BE1FC3EF9D60D21CC7B73727F7F106 | SHA256:47DD59EE09A10DD7AE590BCB63ACF8EF8668BF3FEEBC87C15057D7F322906989 | |||
| 5624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_5624.14512 | compressed | |
MD5:269A86324316E4B84644AF22AA3FEBFE | SHA256:659DB288A088002170968E8C05EB3B36005C58E946E9DA7F4C46C141F0FDD771 | |||
| 6240 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:2C106E9F90F40434BF71AEDA3E012FB7 | SHA256:11C42FFA3280F9369ED1BA7C5B701DBAD188E7348F7398353ABD73F814688C6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
71
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6240 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3860 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6240 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
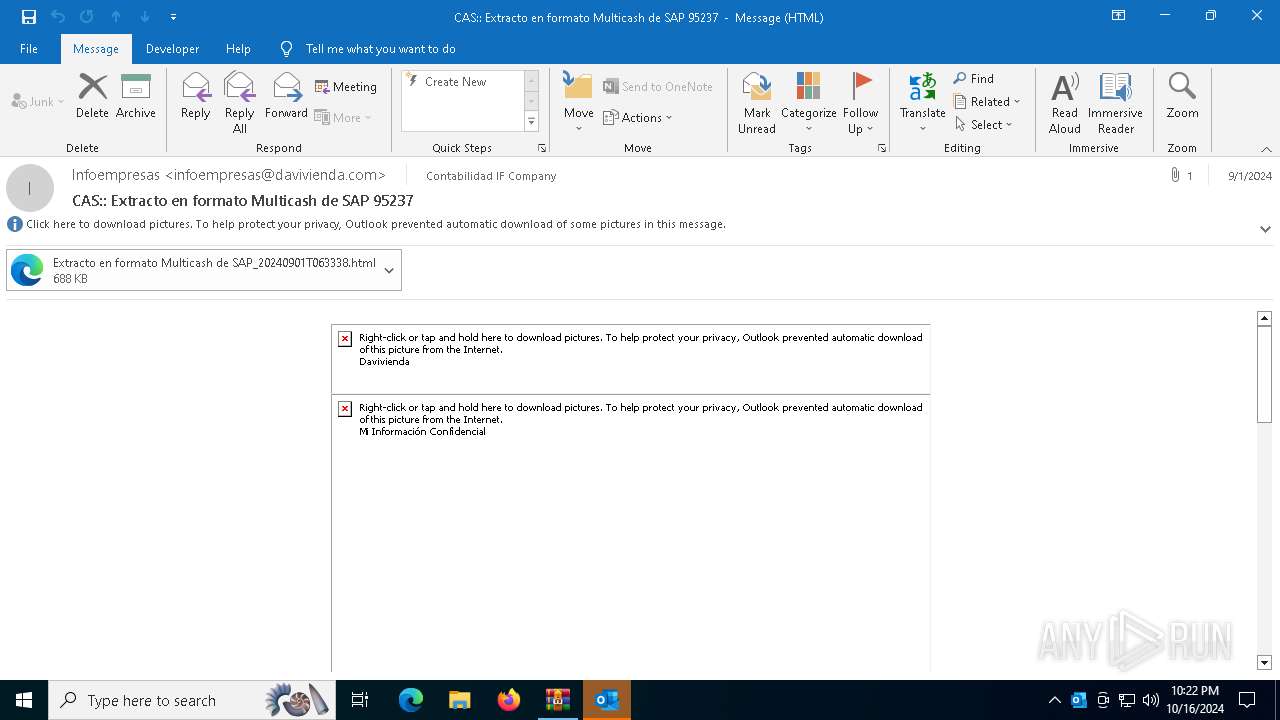
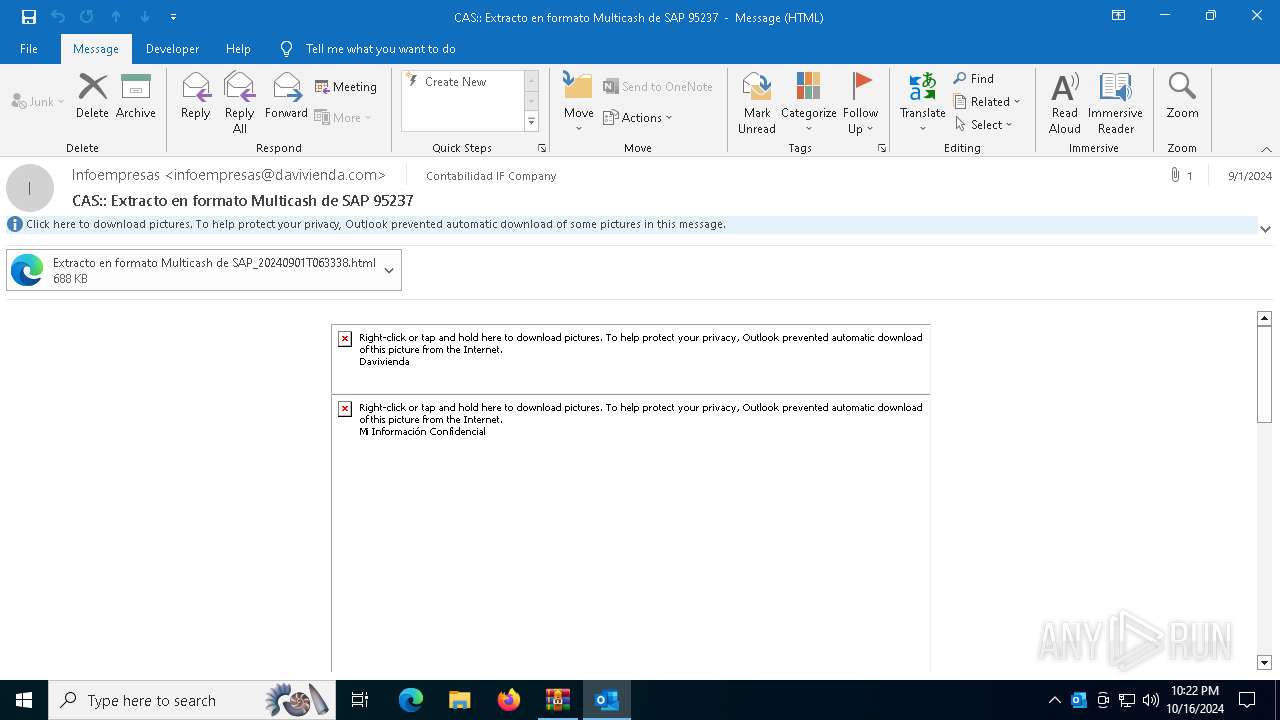
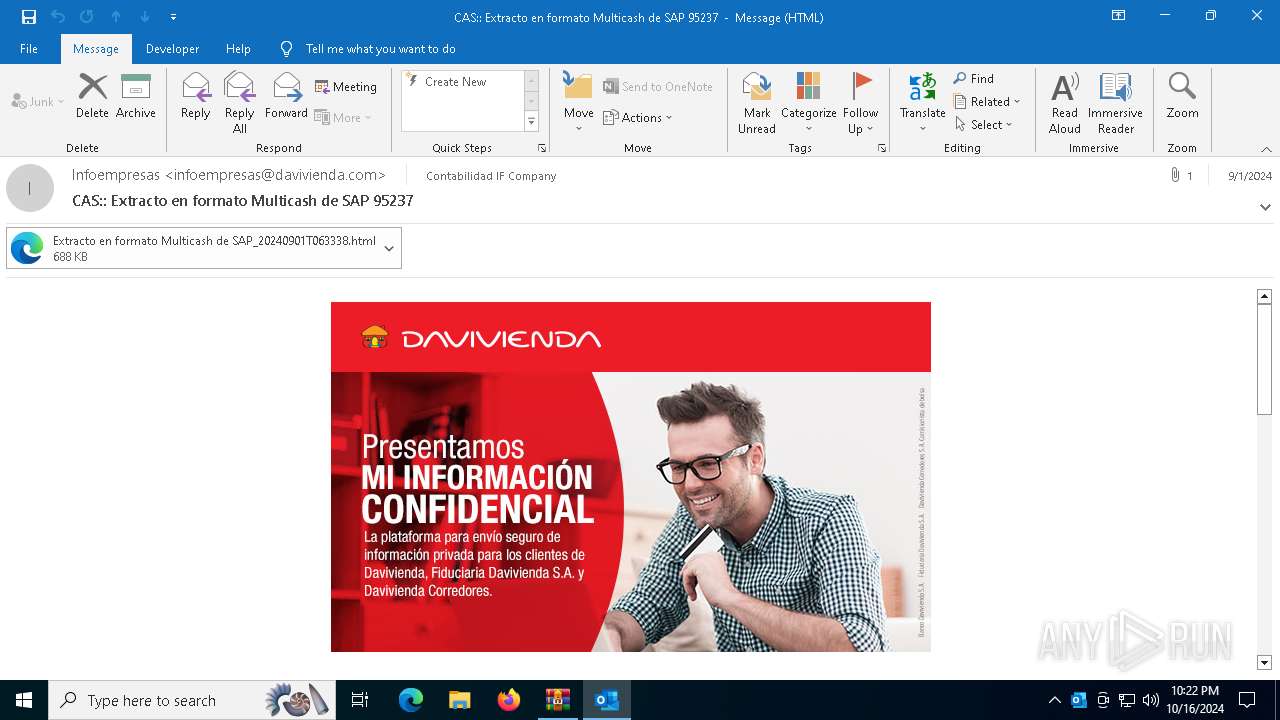
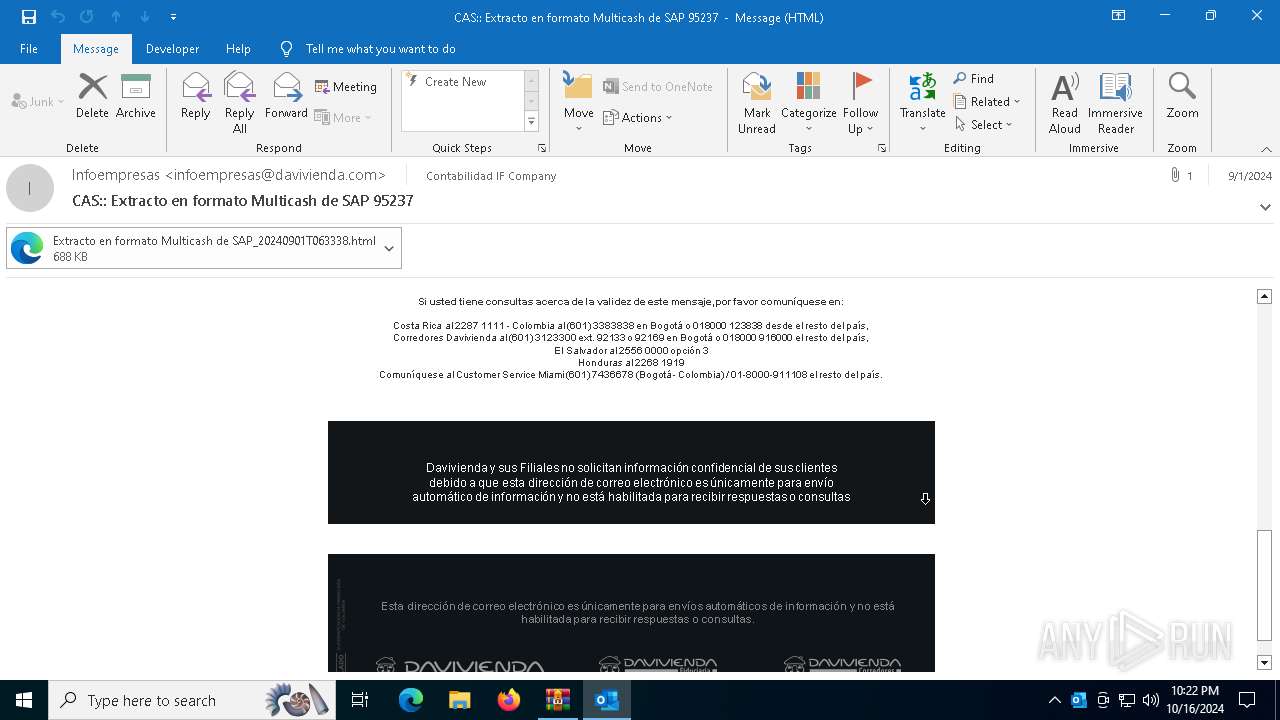
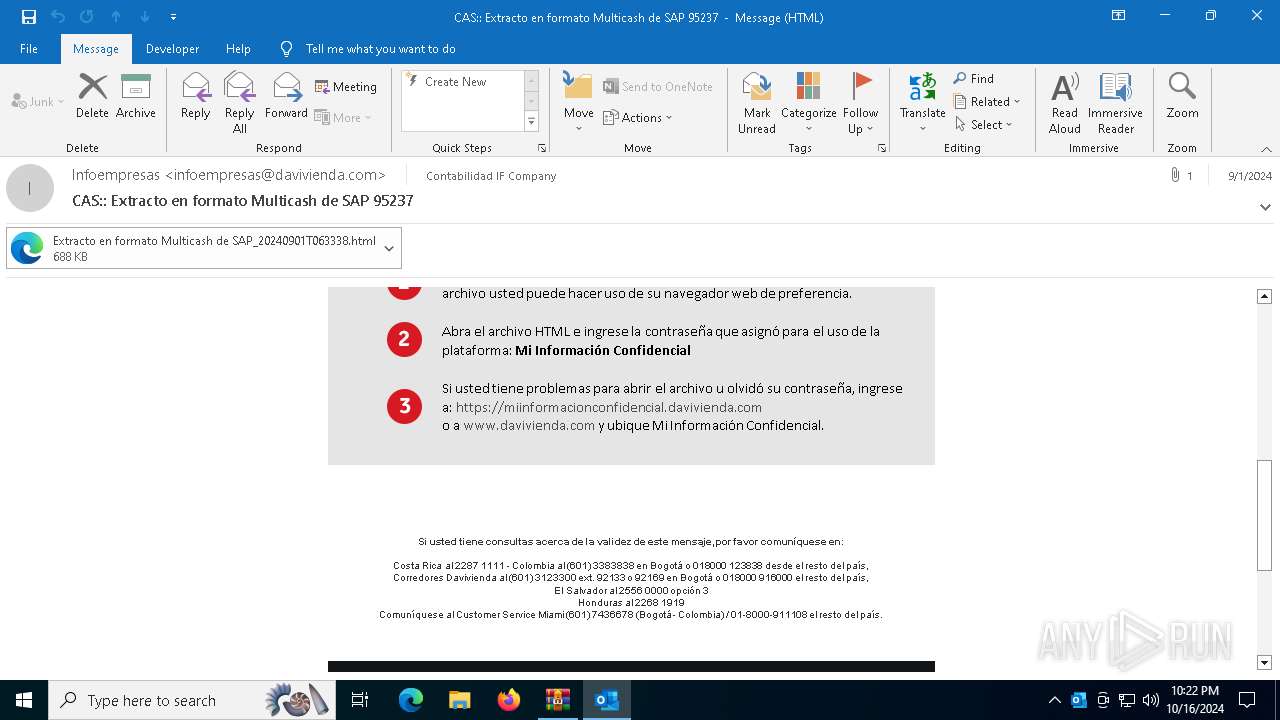
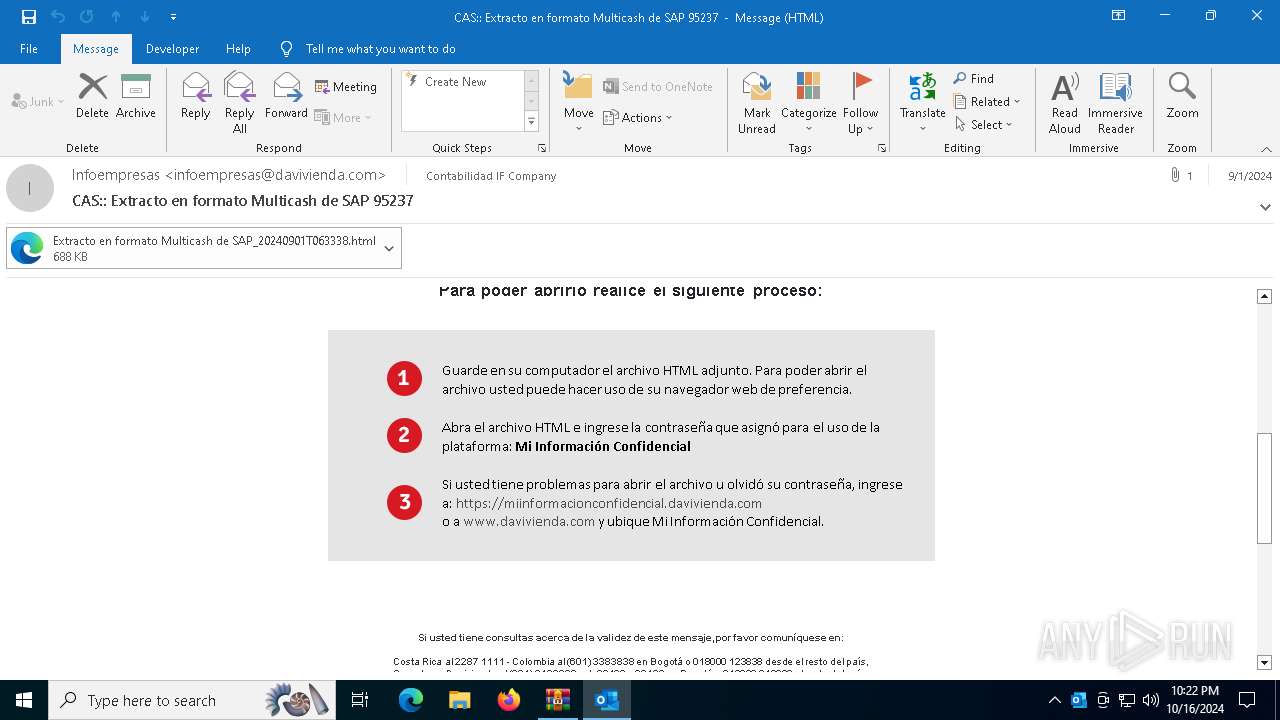
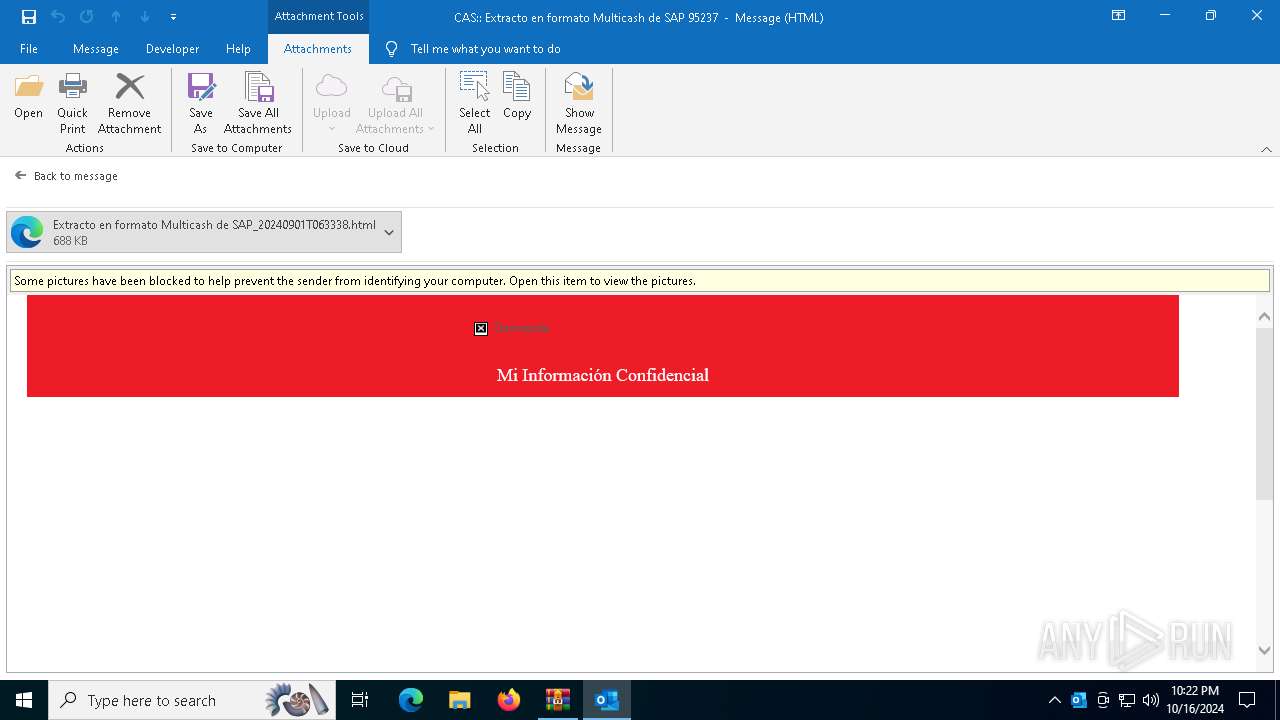
6240 | OUTLOOK.EXE | GET | 200 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/1.png | unknown | — | — | whitelisted |
6240 | OUTLOOK.EXE | GET | 200 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/banner.jpg | unknown | — | — | whitelisted |
6240 | OUTLOOK.EXE | GET | 200 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/header.jpg | unknown | — | — | whitelisted |
6240 | OUTLOOK.EXE | GET | 200 | 45.60.197.231:80 | http://miinformacionconfidencial.davivienda.com/email/3.png | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1748 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |