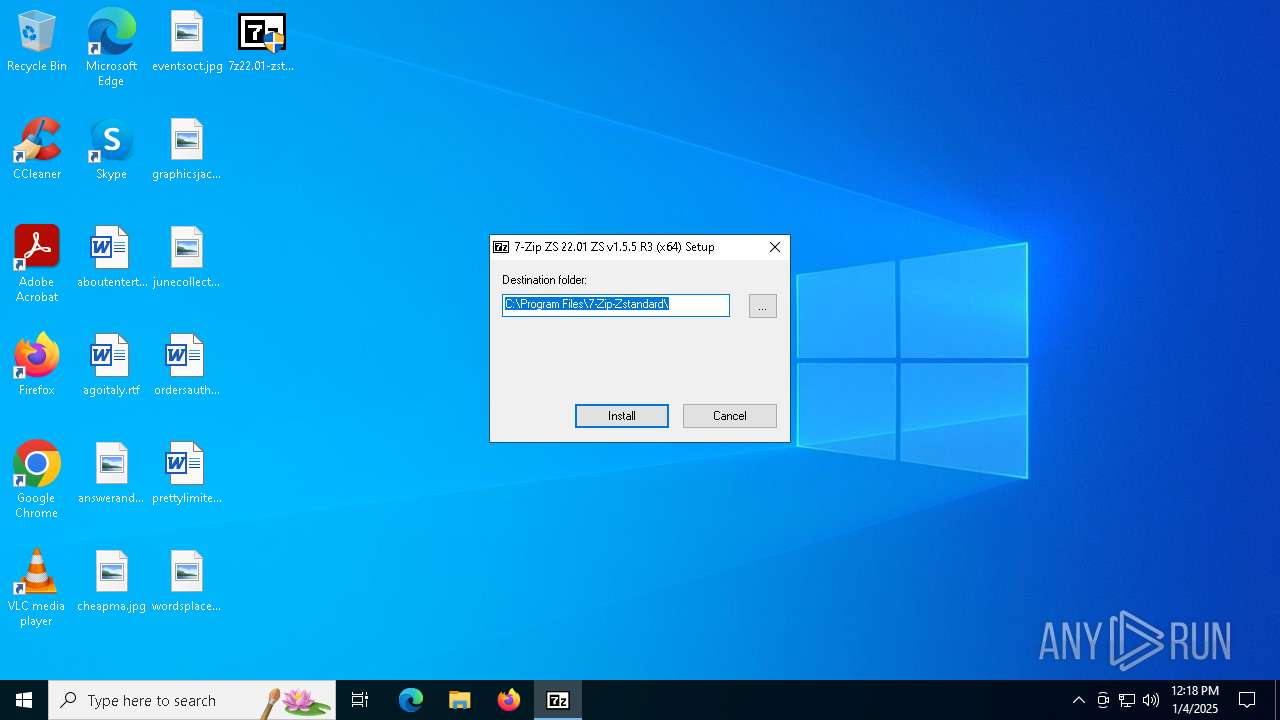
| File name: | 7z22.01-zstd-x64.exe |
| Full analysis: | https://app.any.run/tasks/660bd5d1-5ec2-40f0-9efa-c76d7f461e41 |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2025, 12:18:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 7D06C28595BD248B9F85FDBDC9B93D91 |
| SHA1: | 2A1E624836FAFC706C50325793F029E4FF7B0AC1 |
| SHA256: | D542D78397BBED8E77C221F36CAD461A0D83F1263B993A7048E81DF40F403FB8 |
| SSDEEP: | 98304:VOH/iyeqQaBcz7aeP0jU2nkg0xsxOmh+g1oyf8chgr4RrysfE+ipb5Cdz0BceHsN:mM3Q |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates a software uninstall entry
- 7z22.01-zstd-x64.exe (PID: 3840)
Executable content was dropped or overwritten
- 7z22.01-zstd-x64.exe (PID: 3840)
Creates/Modifies COM task schedule object
- 7z22.01-zstd-x64.exe (PID: 3840)
INFO
The sample compiled with english language support
- 7z22.01-zstd-x64.exe (PID: 3840)
Creates files in the program directory
- 7z22.01-zstd-x64.exe (PID: 3840)
The sample compiled with russian language support
- 7z22.01-zstd-x64.exe (PID: 3840)
Checks supported languages
- 7z22.01-zstd-x64.exe (PID: 3840)
Reads the computer name
- 7z22.01-zstd-x64.exe (PID: 3840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:06:18 13:18:53+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 86528 |
| InitializedDataSize: | 74240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8a54 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 22.1.6.0 |
| ProductVersionNumber: | 22.1.6.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov, Tino Reichardt |
| FileDescription: | 7-Zip Installer ZS |
| FileVersion: | 22.01 ZS v1.5.5 R3 |
| InternalName: | 7zipInstall |
| LegalCopyright: | Copyright (c) 1999-2022 Igor Pavlov, 2016-2023 Tino Reichardt |
| OriginalFileName: | 7zipInstall.exe |
| ProductName: | 7-Zip ZS |
| ProductVersion: | 22.01 ZS v1.5.5 R3 |
Total processes
121
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3032 | "C:\Users\admin\Desktop\7z22.01-zstd-x64.exe" | C:\Users\admin\Desktop\7z22.01-zstd-x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov, Tino Reichardt Integrity Level: MEDIUM Description: 7-Zip Installer ZS Exit code: 3221226540 Version: 22.01 ZS v1.5.5 R3 Modules
| |||||||||||||||
| 3840 | "C:\Users\admin\Desktop\7z22.01-zstd-x64.exe" | C:\Users\admin\Desktop\7z22.01-zstd-x64.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov, Tino Reichardt Integrity Level: HIGH Description: 7-Zip Installer ZS Exit code: 0 Version: 22.01 ZS v1.5.5 R3 Modules
| |||||||||||||||
Total events
188
Read events
167
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip-Zstandard |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip-Zstandard\ | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip-Zstandard |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip-Zstandard\ | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip-Zstandard |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip-Zstandard\ | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip-Zstandard |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip-Zstandard\ | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{23170F69-20BB-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{23170F69-20BB-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-20BB-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-20BB-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\7zFM.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip-Zstandard\ | |||
| (PID) Process: | (3840) 7z22.01-zstd-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip-Zstandard |
| Operation: | write | Name: | DisplayName |
Value: 7-Zip ZS 22.01 ZS v1.5.5 R3 (x64) | |||
Executable files
12
Suspicious files
2
Text files
97
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\7za.exe | executable | |
MD5:77A93B9CAC617C06A3394A9364D35694 | SHA256:EC085C6245A98A234DBF750202C34CDDBC633FAA945B2E915C4E29A909B1A7B0 | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\7-zip32.dll | executable | |
MD5:02C326E385FB8BD5A0F024E5E76DE255 | SHA256:E2A86745E36113106B9A981E48E30292770833D84AE9AA03F2247DA4C3FACB7A | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\Lang\ar.txt | text | |
MD5:1C45E6A6ECB3B71A7316C466B6A77C1C | SHA256:972261B53289DE2BD8A65E787A6E7CD6DEFC2B5F7E344128F2FE0492ED30CCF1 | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\7-zip.dll | executable | |
MD5:8D783680585680BF17FFD4B5B4EEF375 | SHA256:86C055F0D90C71A595D806F8EB8BA57538E29370F52D476A72018D6B1C4E200D | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\7zxa.dll | executable | |
MD5:DF57EA81450588647A47E8DBD8AC325D | SHA256:227DDD5115EE8277B7010DFFA4558C5B606103DECC6FE74B2D9CAE8CC82CFE43 | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\7zFM.exe | executable | |
MD5:FEA2166E75330AA45D9CF1BCDB1C6D78 | SHA256:010415F21A405C9BA85223527AF2D147190819E8CD2CEFC1E8BD3ECACAC550FE | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\Lang\an.txt | text | |
MD5:BF8564B2DAD5D2506887F87AEE169A0A | SHA256:0E8DD119DFA6C6C1B3ACA993715092CDF1560947871092876D309DBC1940A14A | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\Lang\af.txt | text | |
MD5:FBBE51ACB879B525CC6B19D386697924 | SHA256:3793FB69EE9FD958CF15A272B1ED54E4B3D75592836EBCD085DC0E7B1400D1CB | |||
| 3840 | 7z22.01-zstd-x64.exe | C:\Program Files\7-Zip-Zstandard\Lang\ba.txt | text | |
MD5:D83B65AC086DA0C94D6EB57BEE669C2B | SHA256:2901B54F7621C95429658CB4EDB28ABD0CB5B6E257C7D9A364FC468A8B86BAAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 2.19.80.27:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
188 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.80.75:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
188 | svchost.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
188 | svchost.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |