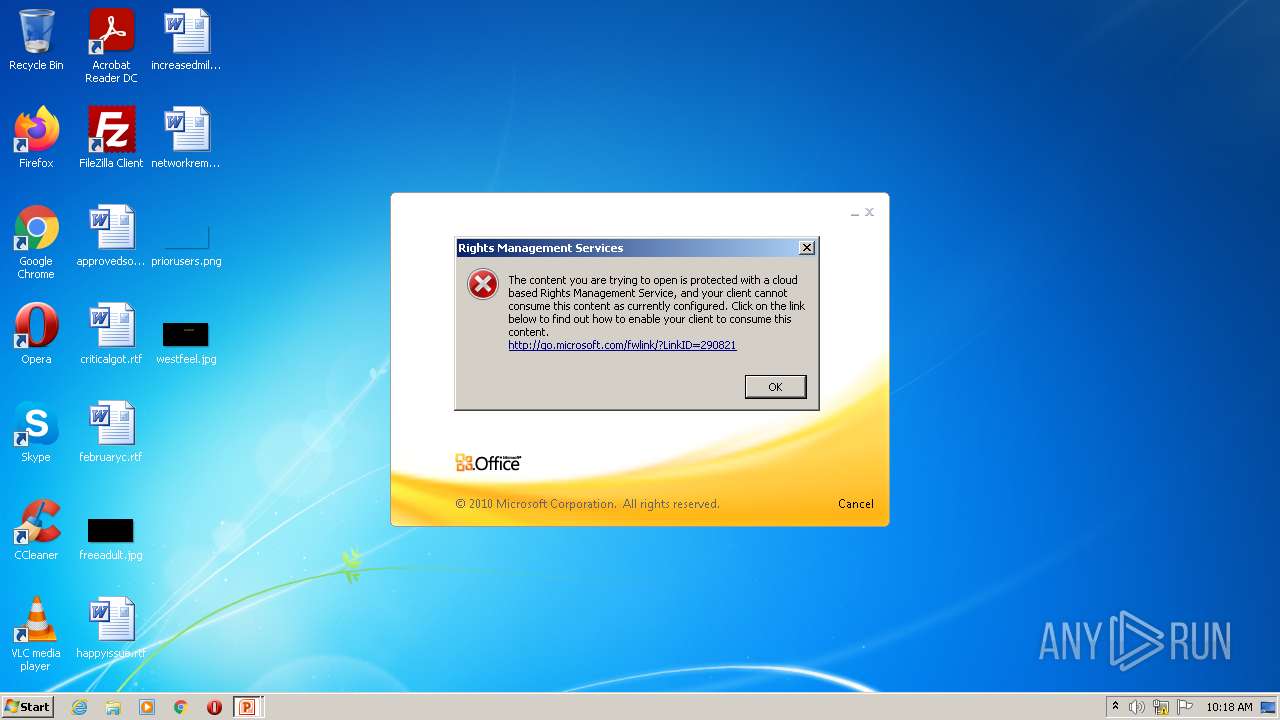
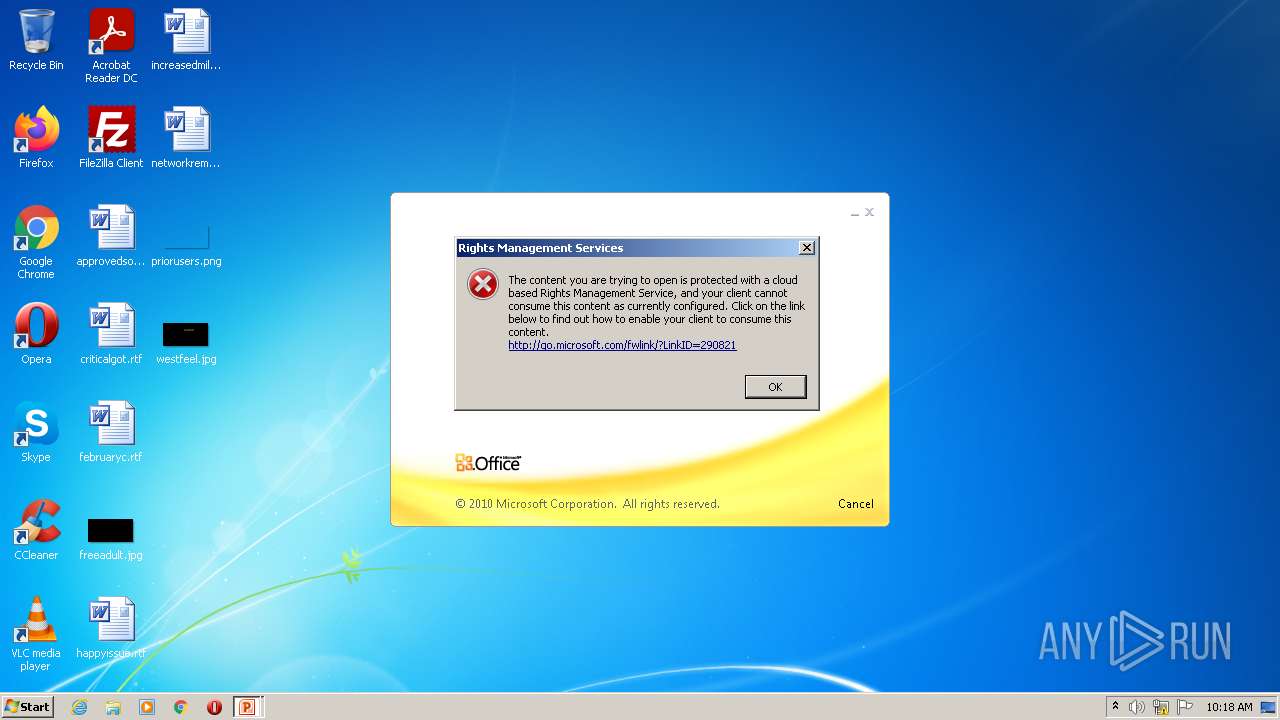
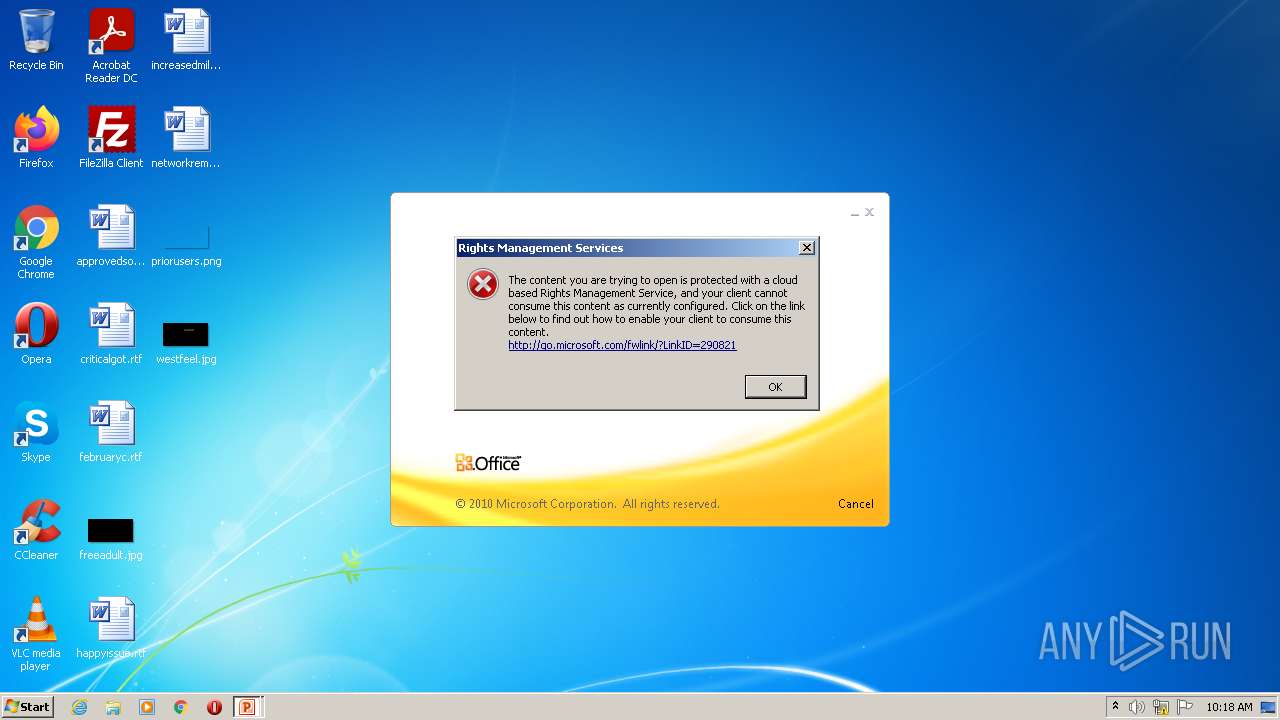
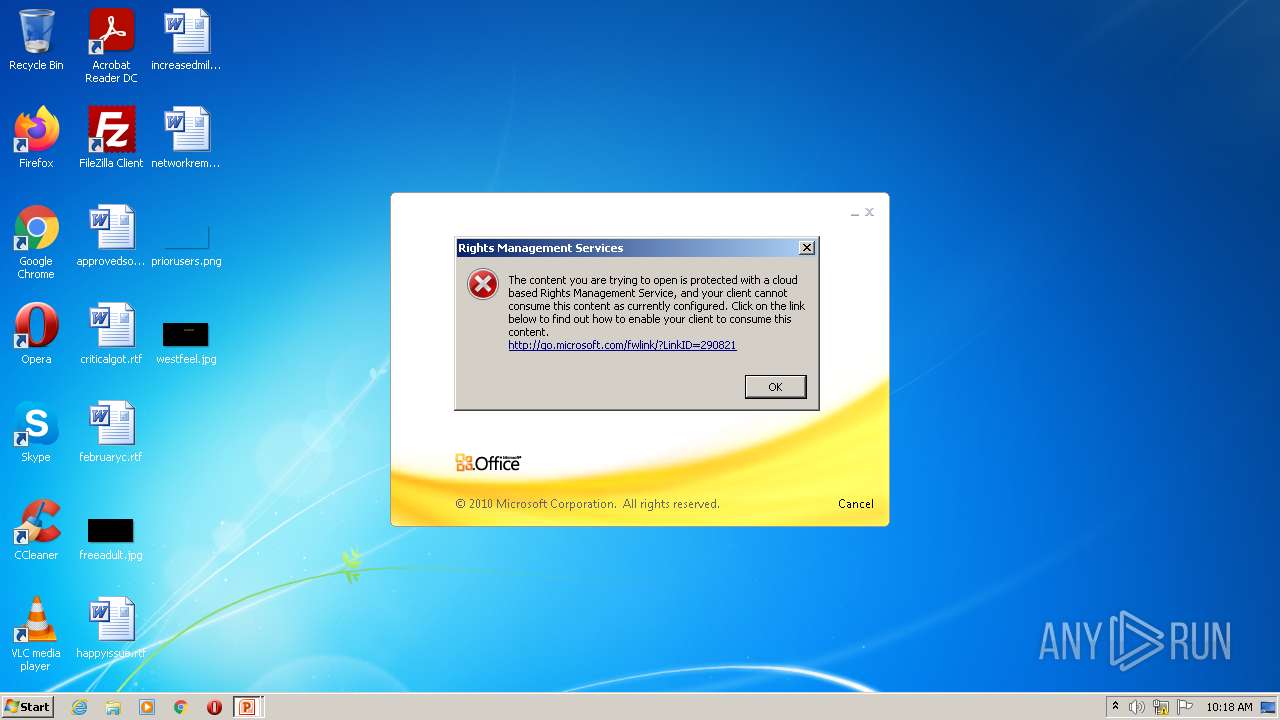
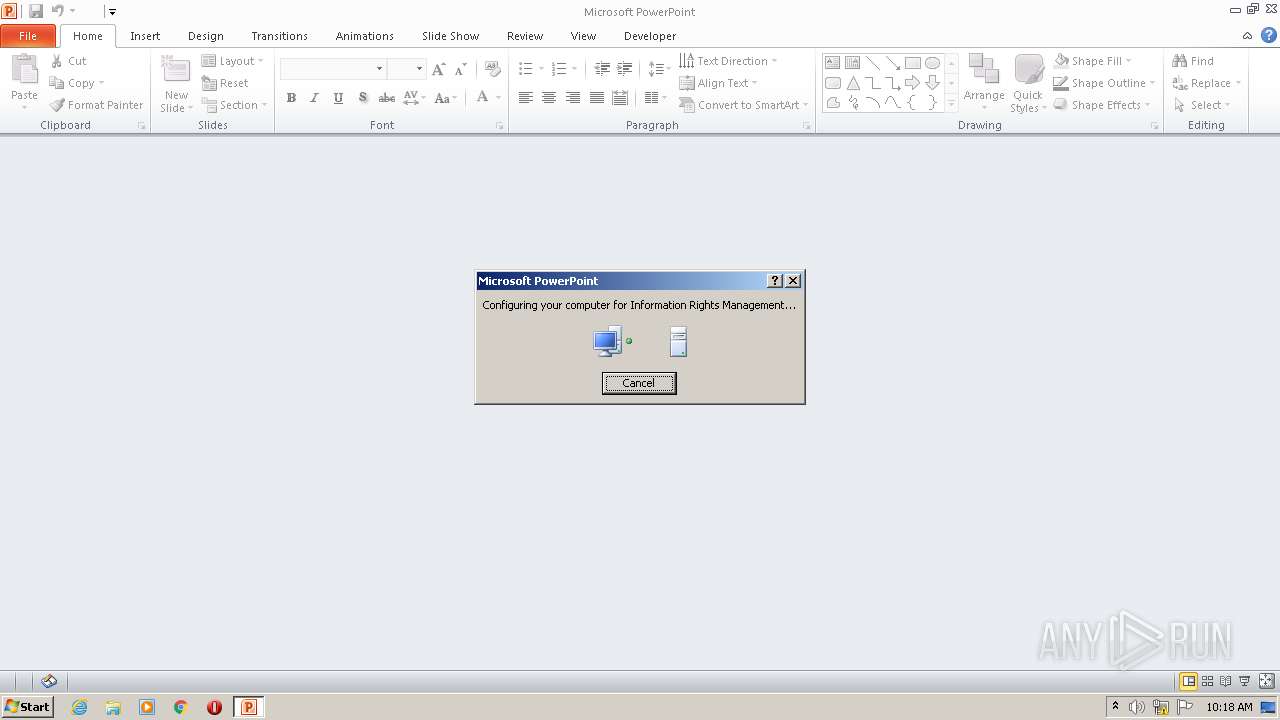
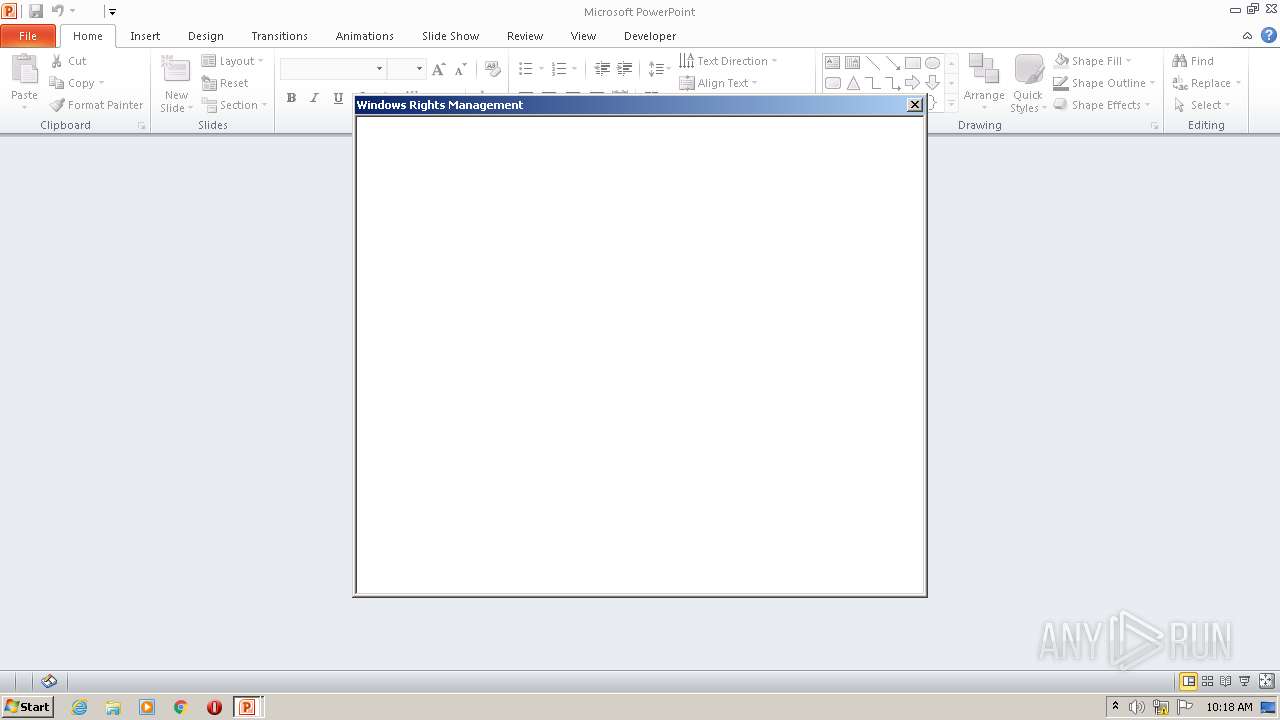
| File name: | EC BU Jun'22 Contract Rev_FC_V2.pptx |
| Full analysis: | https://app.any.run/tasks/0038e92a-041f-4b29-a2d6-6a2b7b699546 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 09:18:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
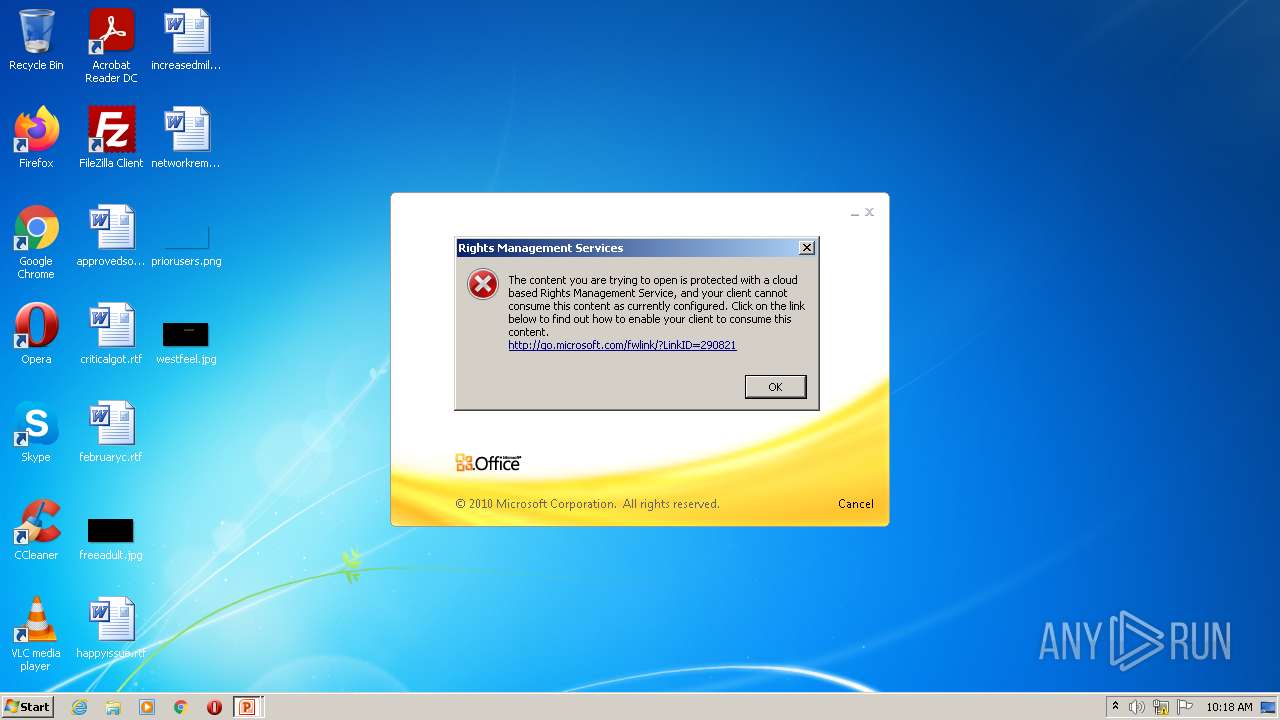
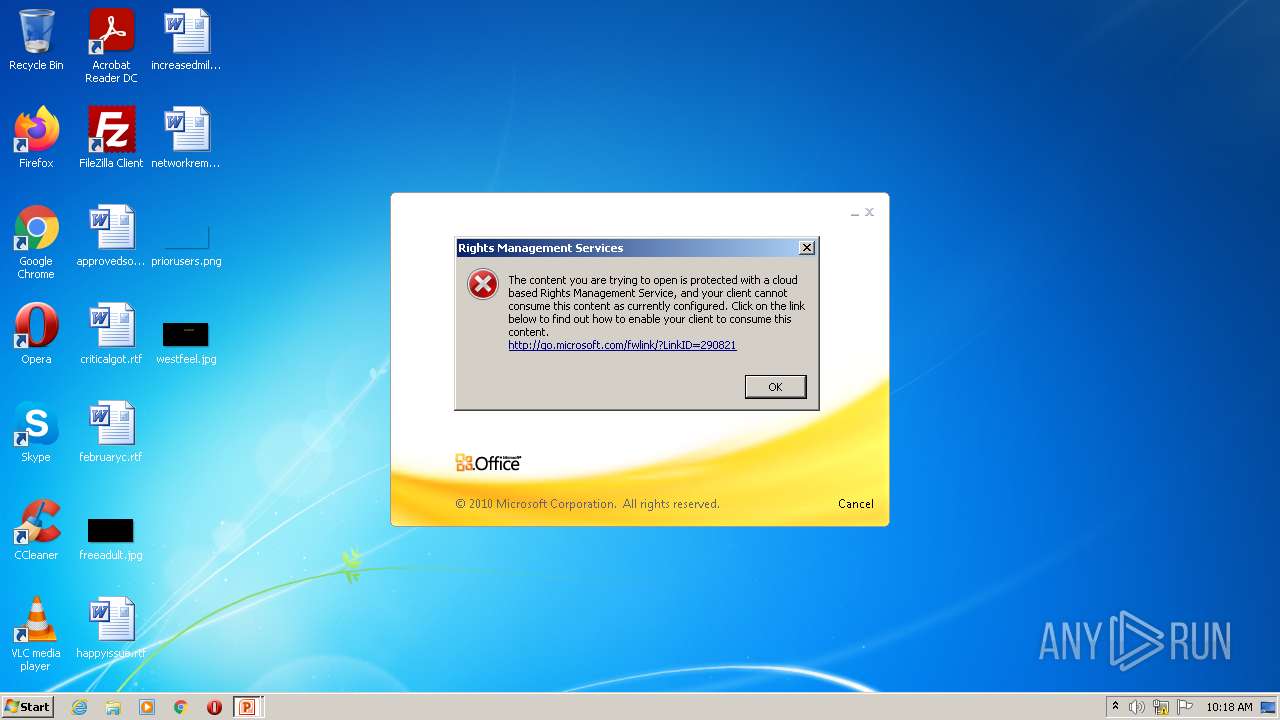
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | 0A105F8BB9D20EE945D358699461390F |
| SHA1: | C6AF5235DC97B078EA154E33B1C1B9B4145F41E0 |
| SHA256: | D53B7B870ECA49D8C3B9346EAD5680EBDEBBF503824C757C2A44CA4E3DD00465 |
| SSDEEP: | 49152:BbkXdEsrwLBUid/B81gfQ1TtQV2zPDedcz/NsnG:Bbkt36Ui8H1G2mwsn |
MALICIOUS
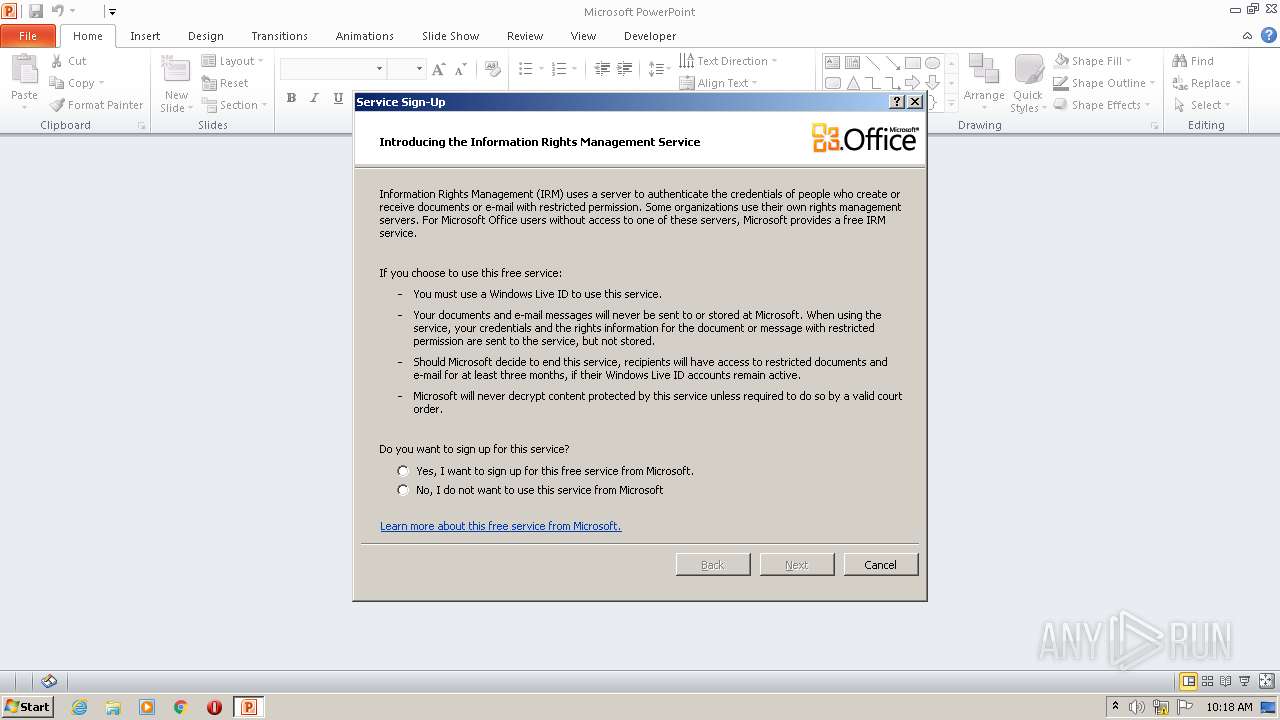
Unusual execution from Microsoft Office
- POWERPNT.EXE (PID: 2848)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- POWERPNT.EXE (PID: 2848)
- rmactivate.exe (PID: 1384)
Checks supported languages
- POWERPNT.EXE (PID: 2848)
- rmactivate.exe (PID: 1384)
Reads settings of System Certificates
- rmactivate.exe (PID: 1384)
Checks Windows Trust Settings
- rmactivate.exe (PID: 1384)
Reads Microsoft Outlook installation path
- POWERPNT.EXE (PID: 2848)
Reads Microsoft Office registry keys
- POWERPNT.EXE (PID: 2848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1384 | "C:\Windows\system32\rmactivate.exe" | C:\Windows\system32\rmactivate.exe | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Rights Management Services Activation for Desktop Security Processor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\EC BU Jun'22 Contract Rev_FC_V2.pptx" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
6 396
Read events
6 319
Write events
77
Delete events
0
Modification events
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Resiliency\StartupItems |
| Operation: | write | Name: | $#; |
Value: 24233B00200B0000010000000000000000000000 | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2848) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
10
Text files
0
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR5390.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C7F163ED126D5C3CB9457F68EC64E9E | der | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B8CC409ACDBF2A2FE04C56F2875B1FD6 | binary | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2CD1F910DD5DC23C234E99A91DE345C0 | der | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1384 | rmactivate.exe | C:\Users\admin\AppData\Local\Microsoft\DRM\CERT-Machine-2048.drm | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1384 | rmactivate.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | US | der | 564 b | whitelisted |
1384 | rmactivate.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | US | der | 824 b | whitelisted |
1384 | rmactivate.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | US | der | 555 b | whitelisted |
2848 | POWERPNT.EXE | GET | 302 | 104.89.38.104:80 | http://go.microsoft.com/fwlink/?LinkId=5998&LANGID=1033 | NL | — | — | whitelisted |
1384 | rmactivate.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | US | der | 519 b | whitelisted |
1384 | rmactivate.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | US | der | 767 b | whitelisted |
1384 | rmactivate.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | US | der | 530 b | whitelisted |
1384 | rmactivate.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?deb7c9b9cac21aae | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1384 | rmactivate.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
1384 | rmactivate.exe | 23.35.229.160:80 | www.microsoft.com | Zayo Bandwidth Inc | US | whitelisted |
1384 | rmactivate.exe | 23.216.77.28:80 | crl.microsoft.com | NTT DOCOMO, INC. | US | suspicious |
— | — | 65.55.61.29:443 | certification.drm.microsoft.com | Microsoft Corporation | US | whitelisted |
2848 | POWERPNT.EXE | 65.55.61.29:443 | certification.drm.microsoft.com | Microsoft Corporation | US | whitelisted |
— | — | 104.89.38.104:80 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
certification.drm.microsoft.com |
| whitelisted |