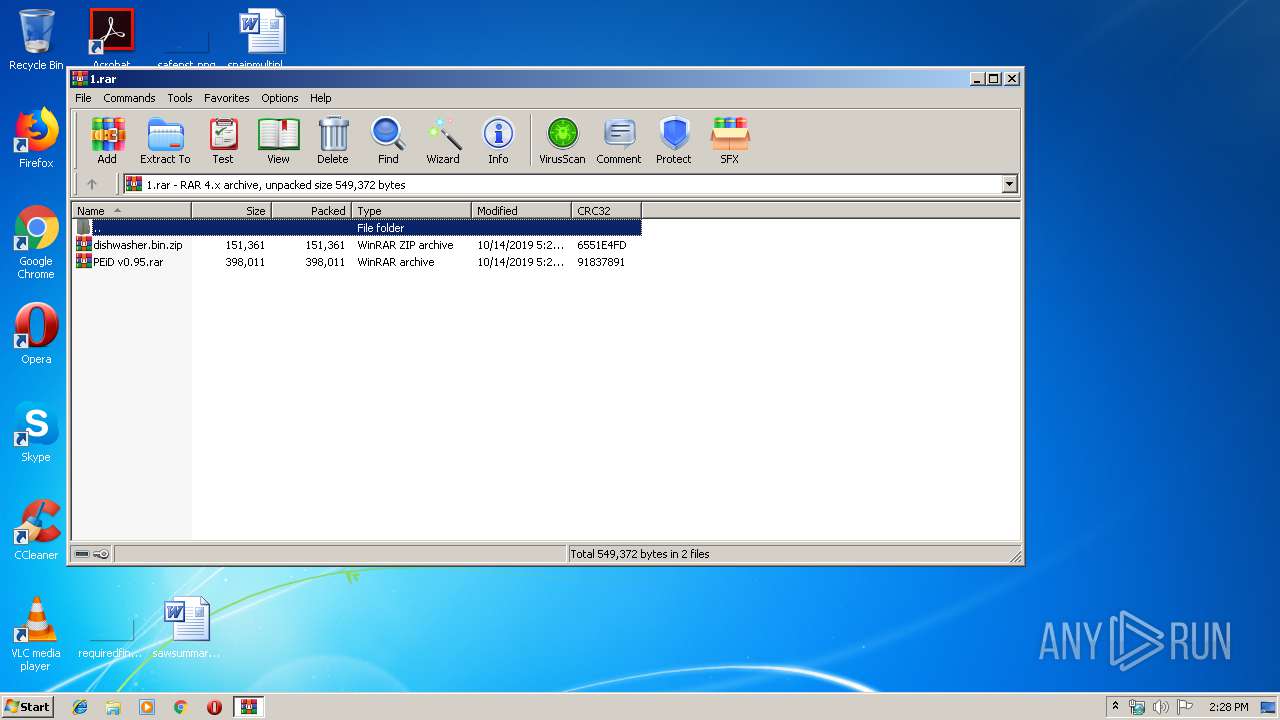
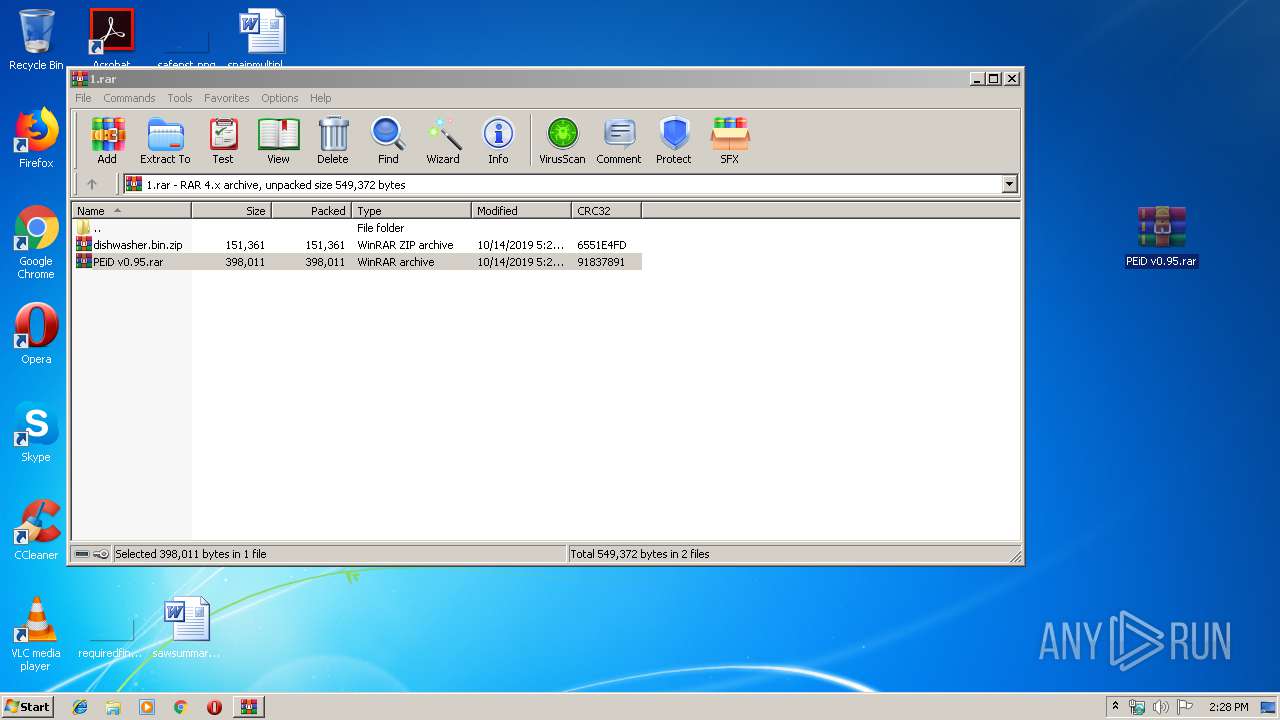
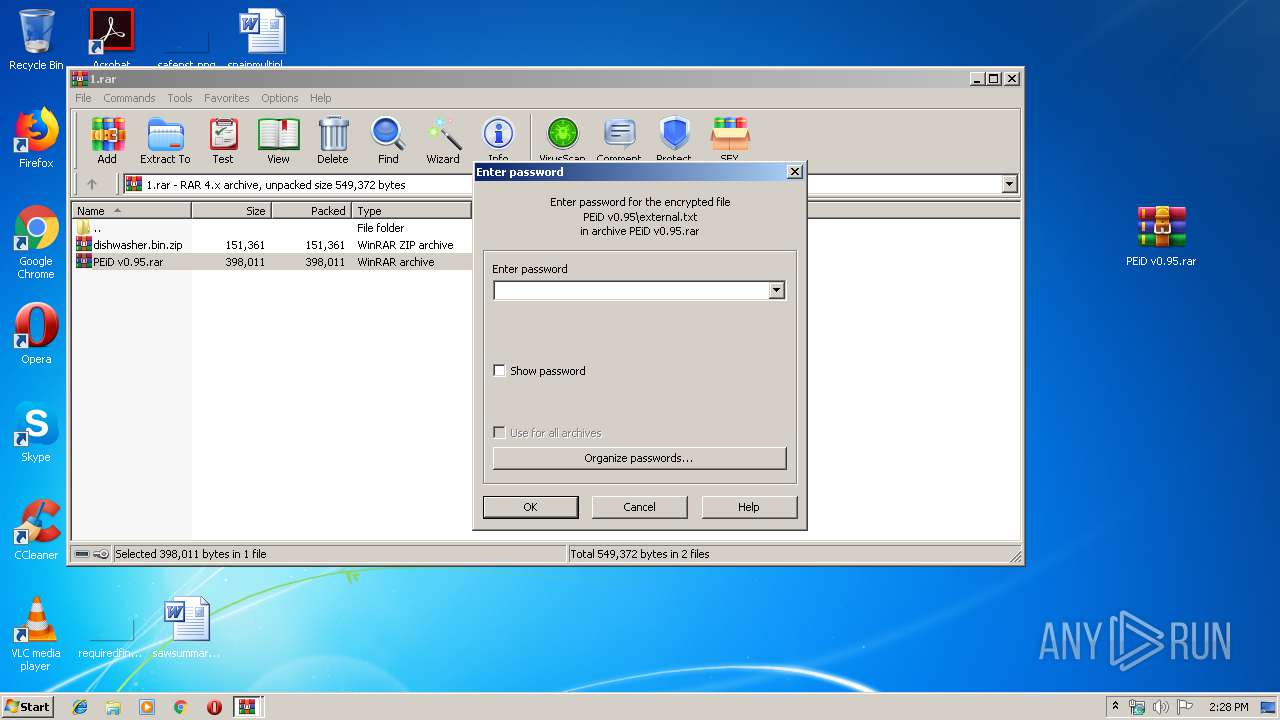
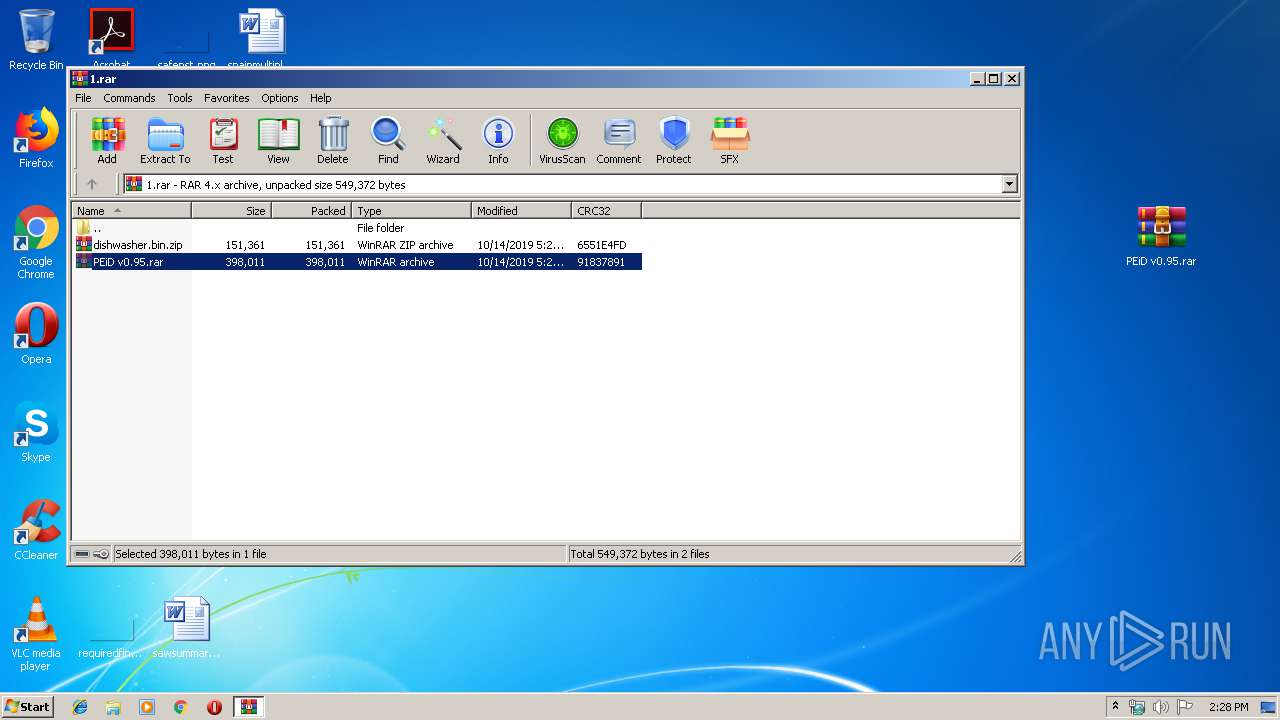
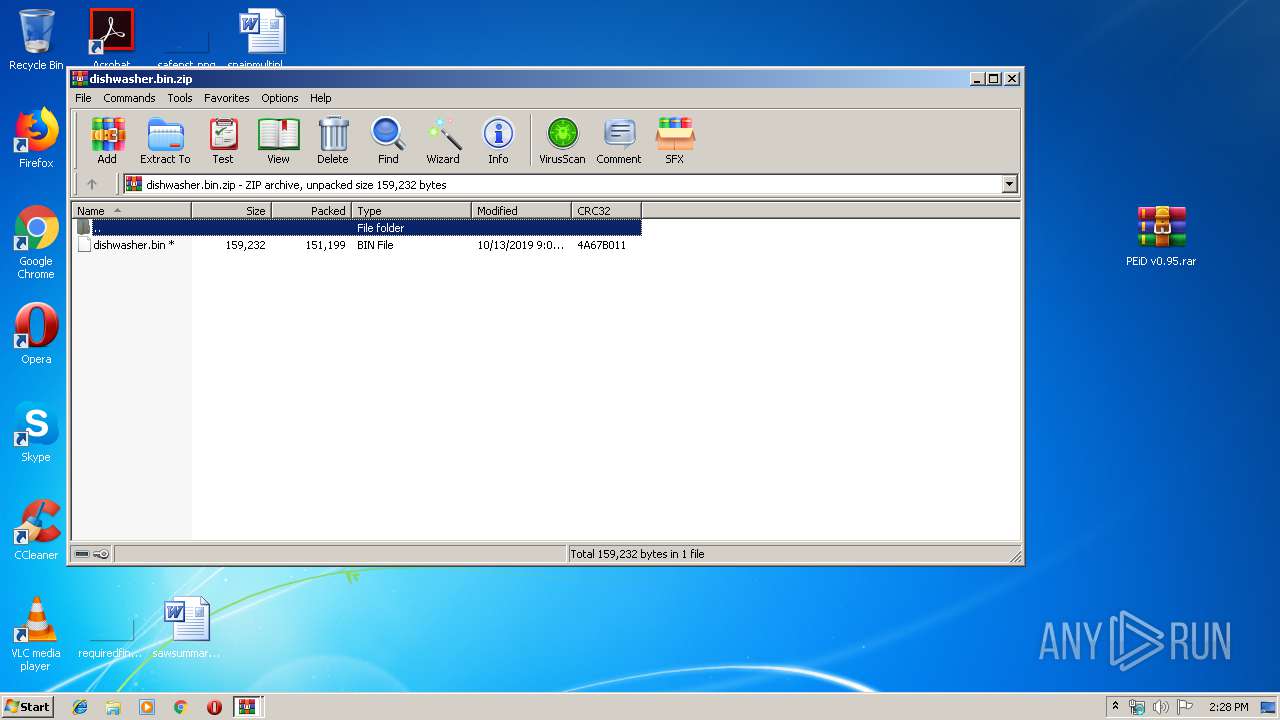
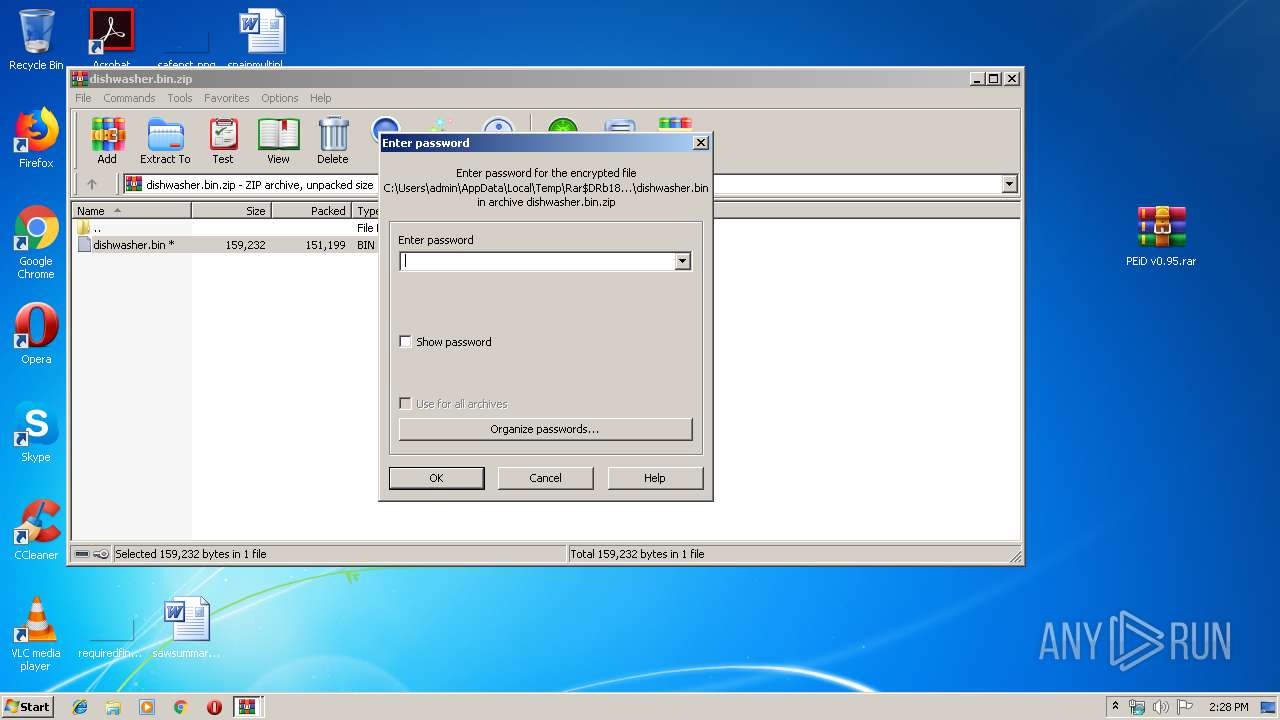
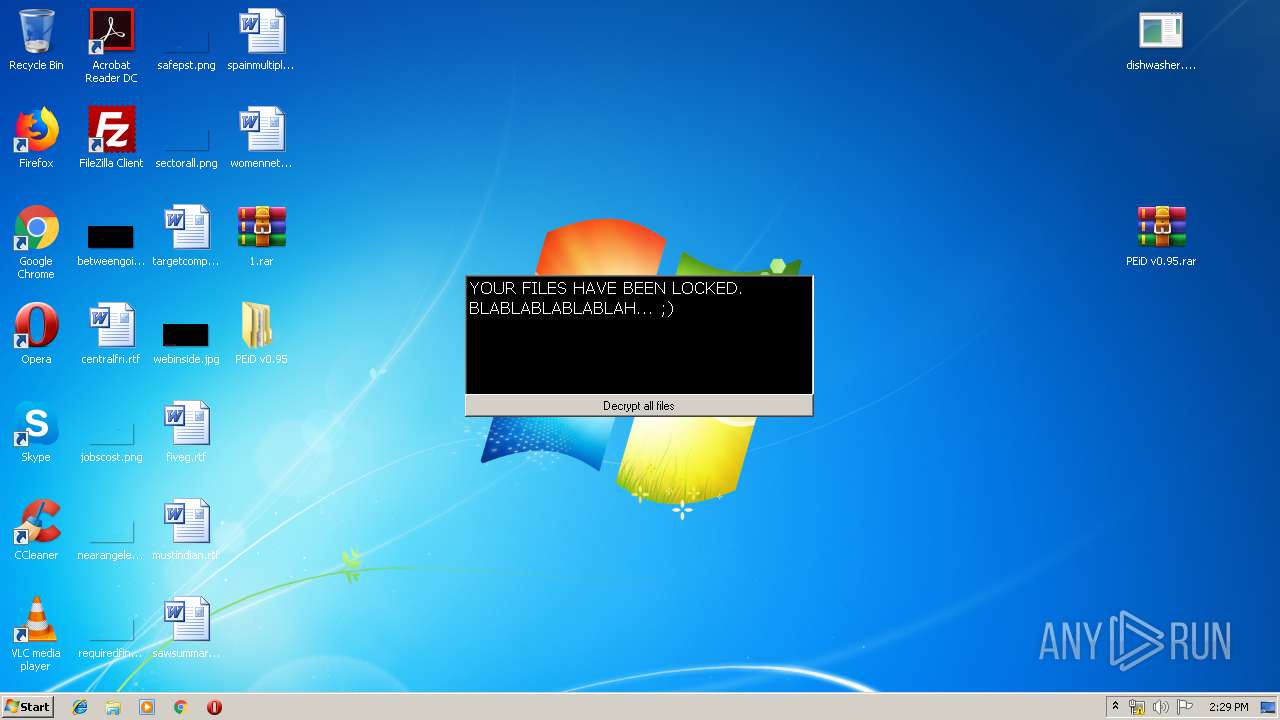
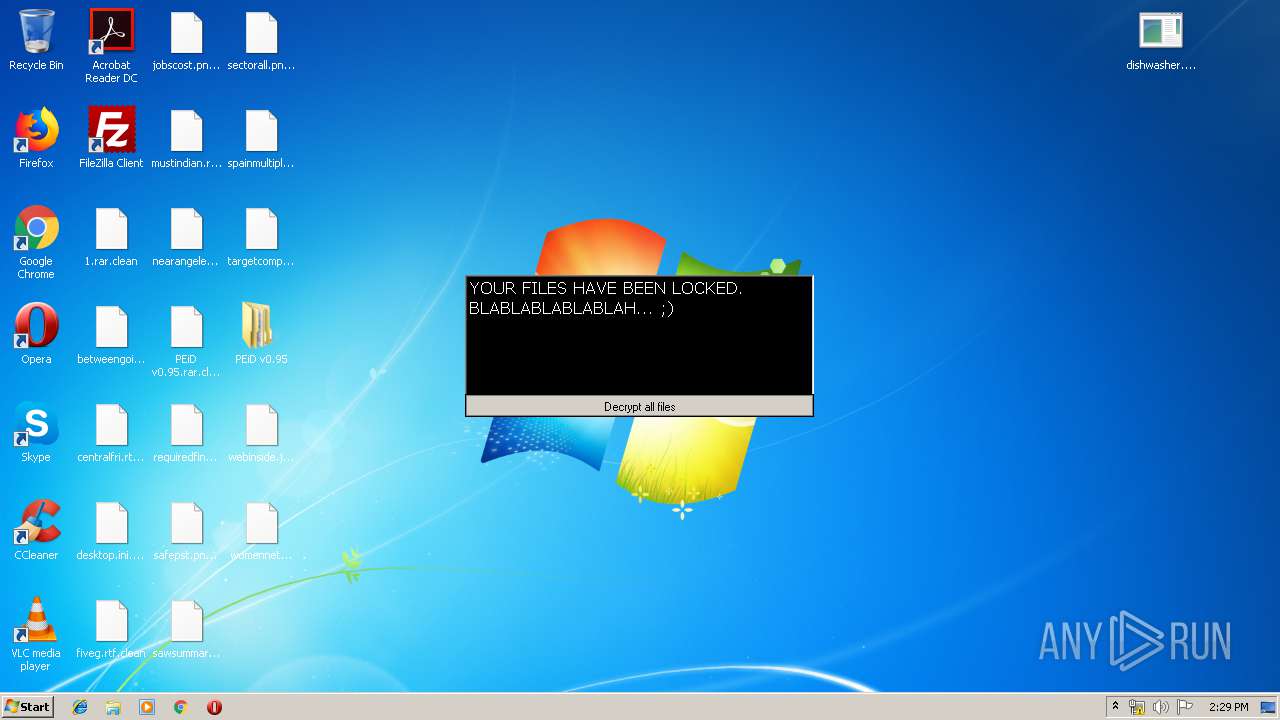
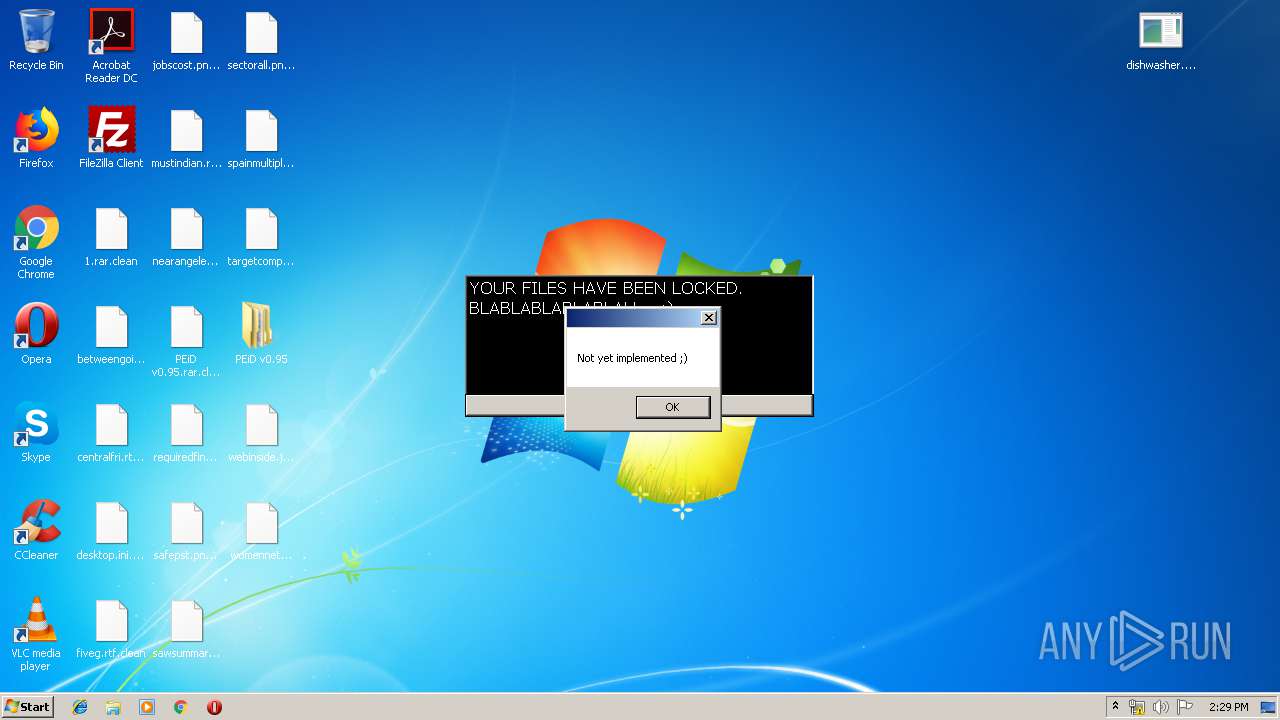
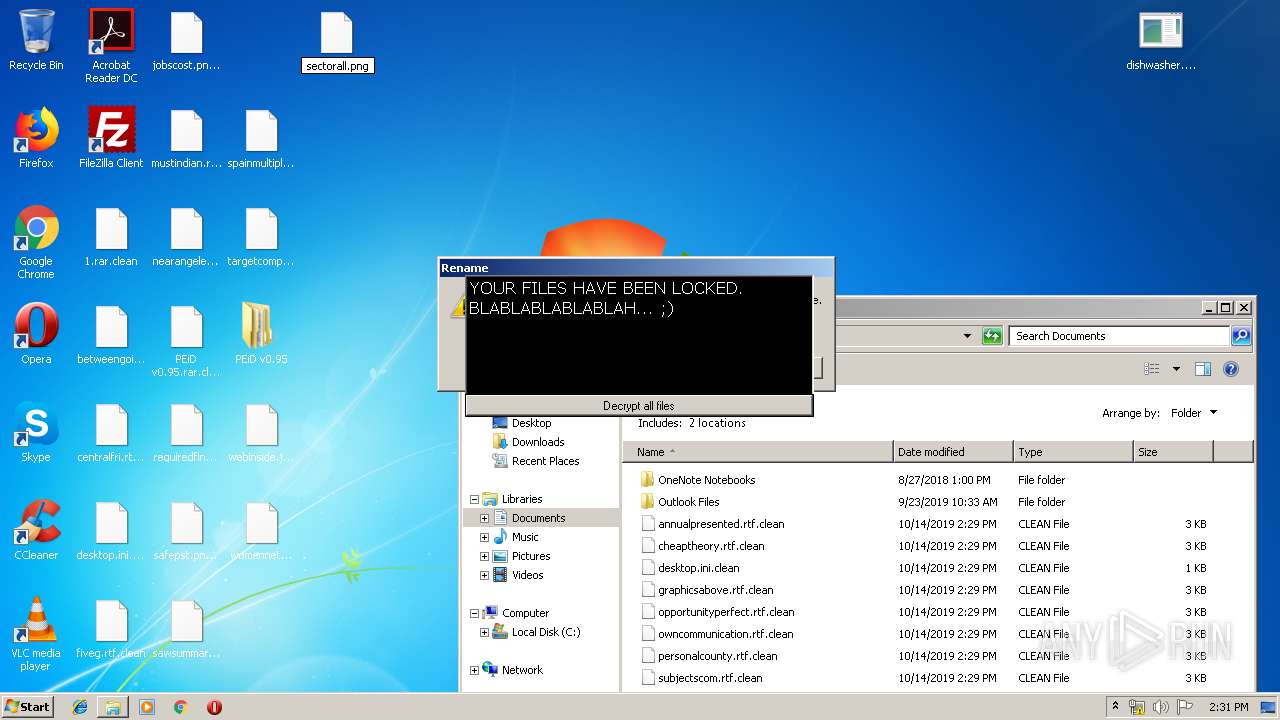
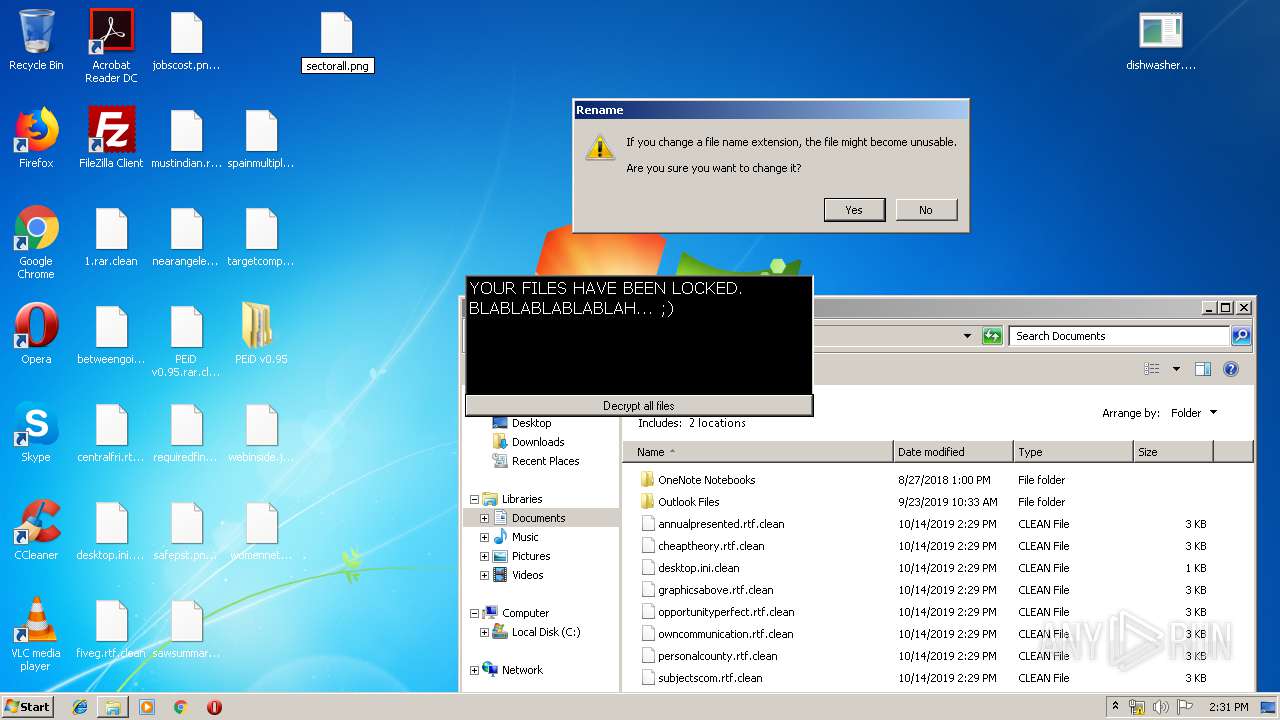
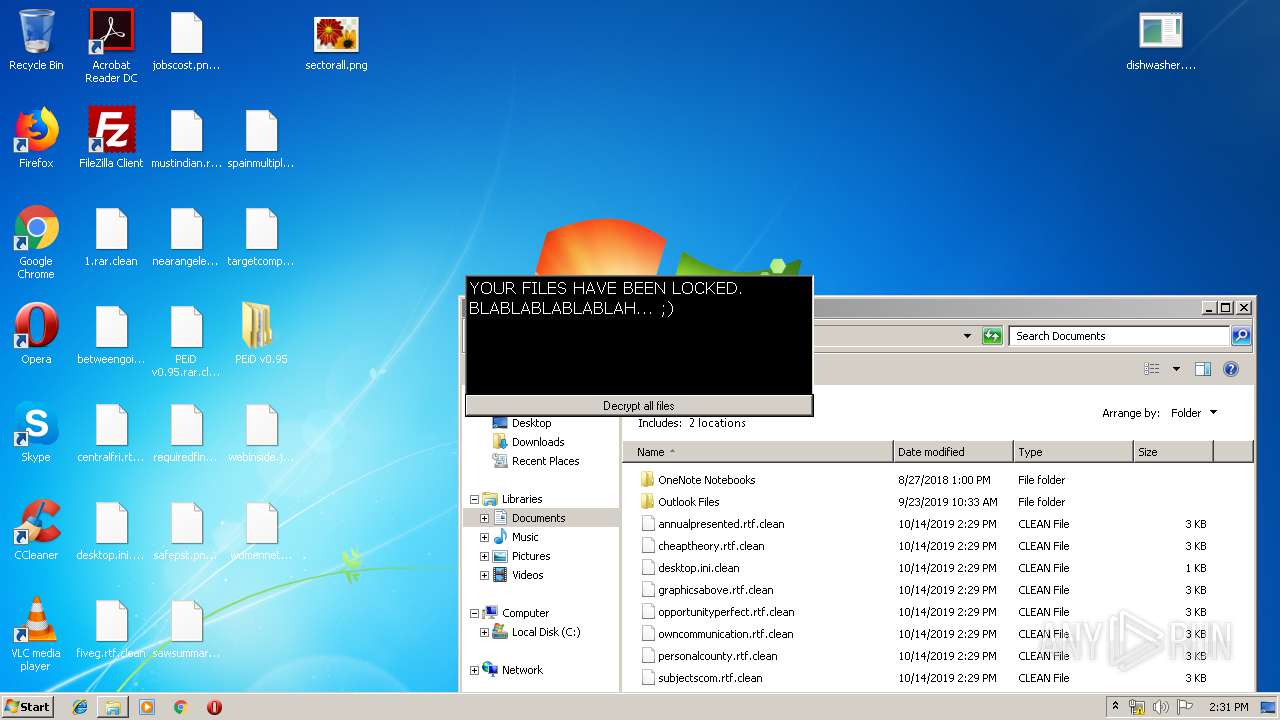
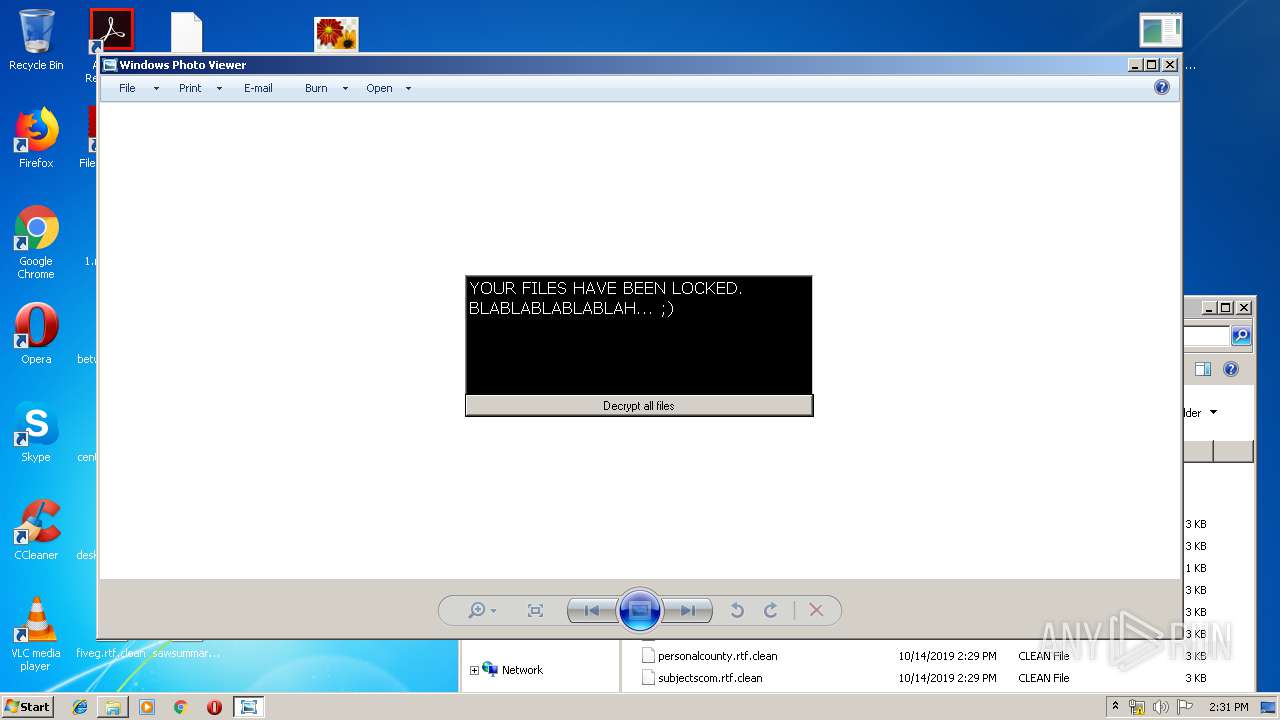
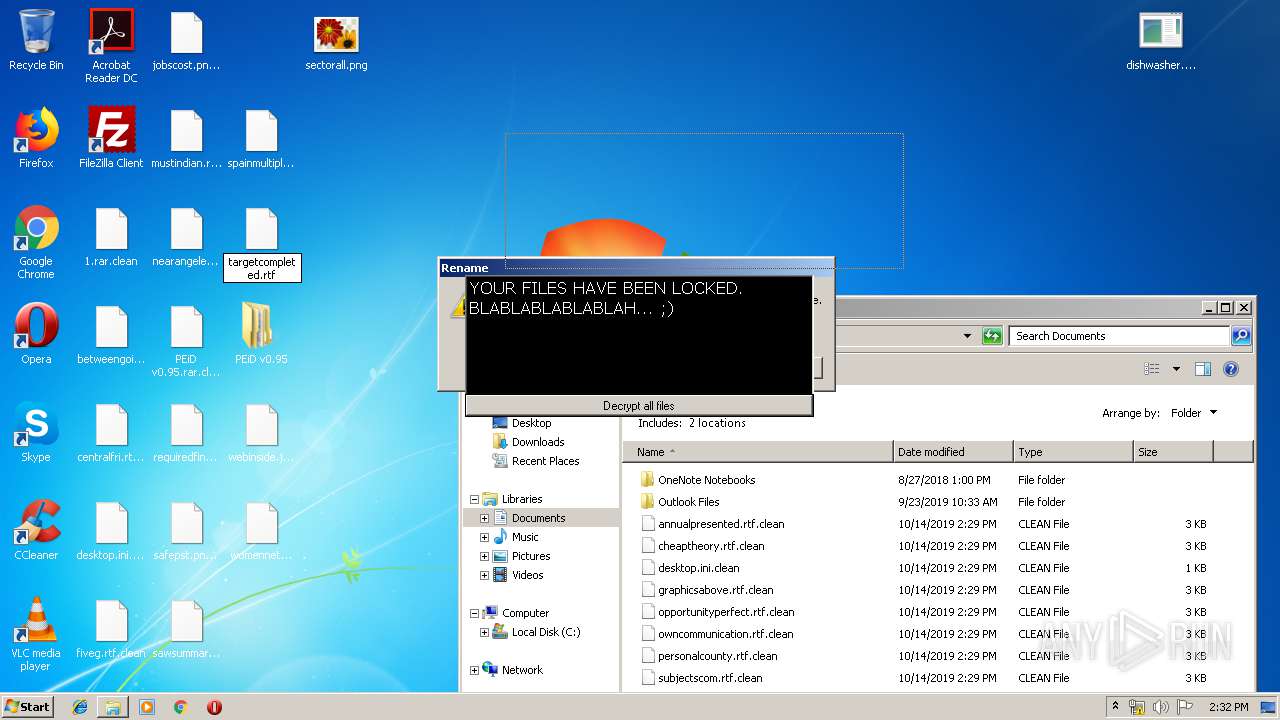
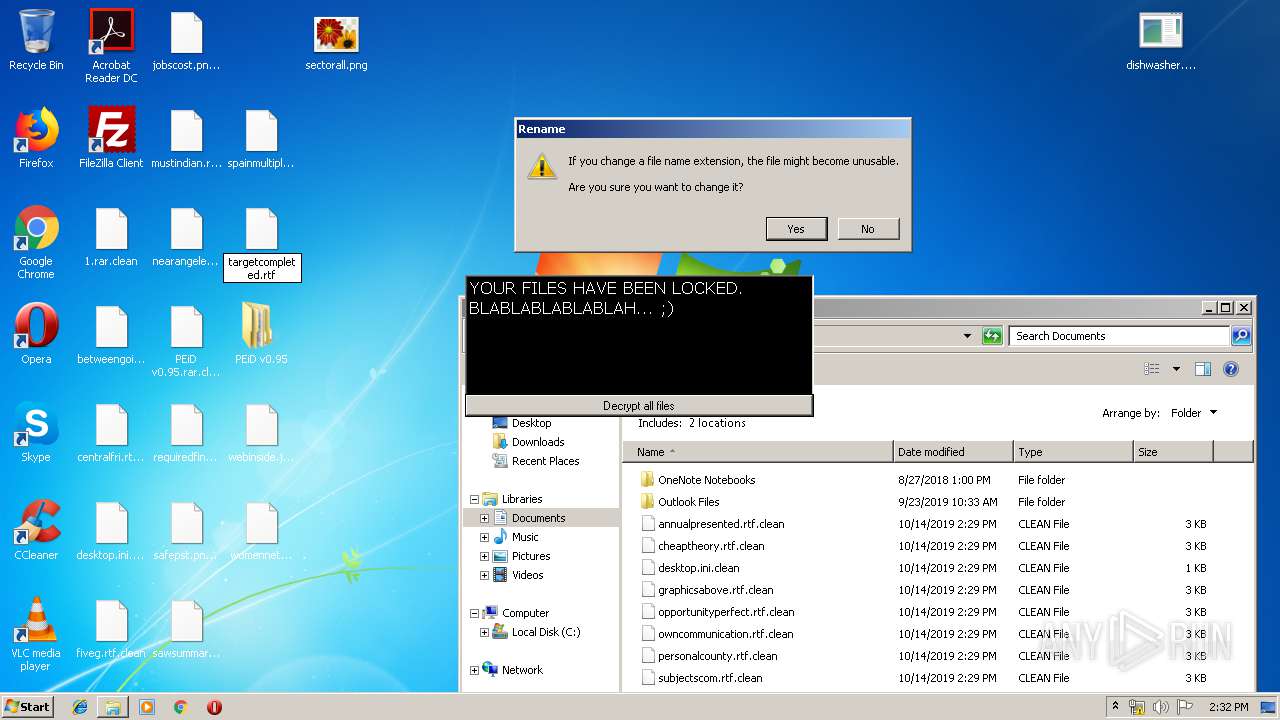
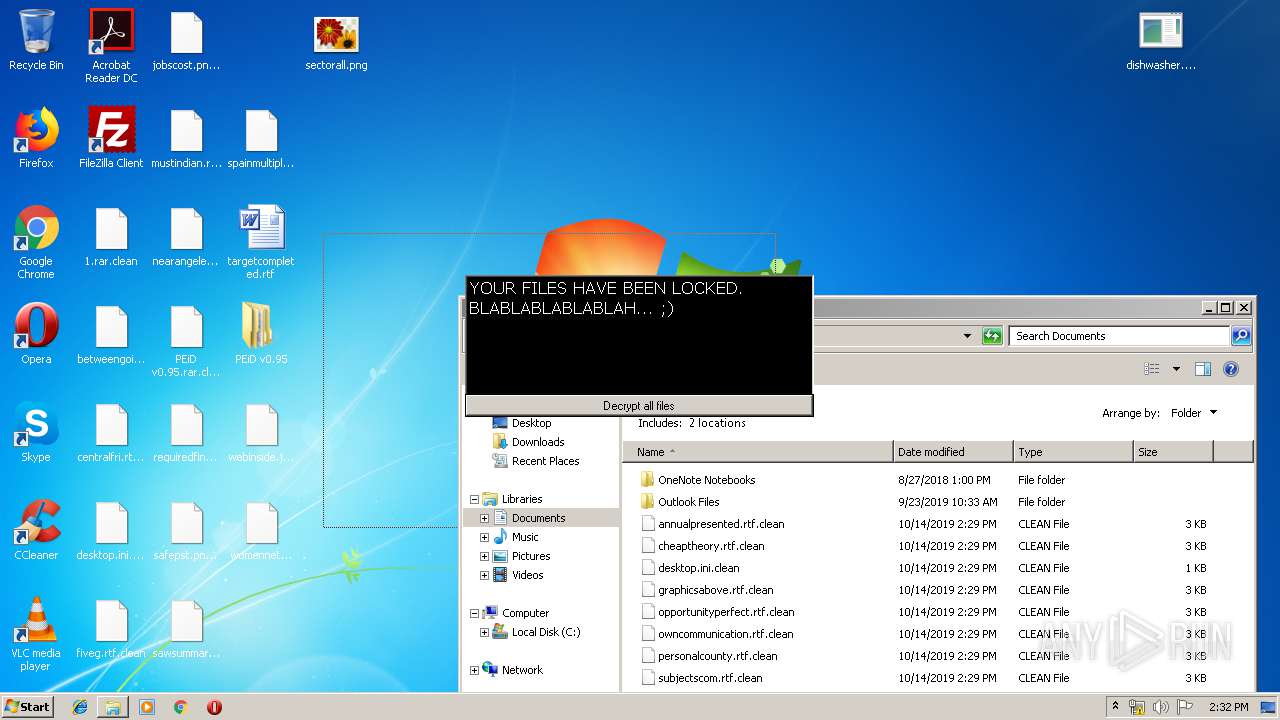
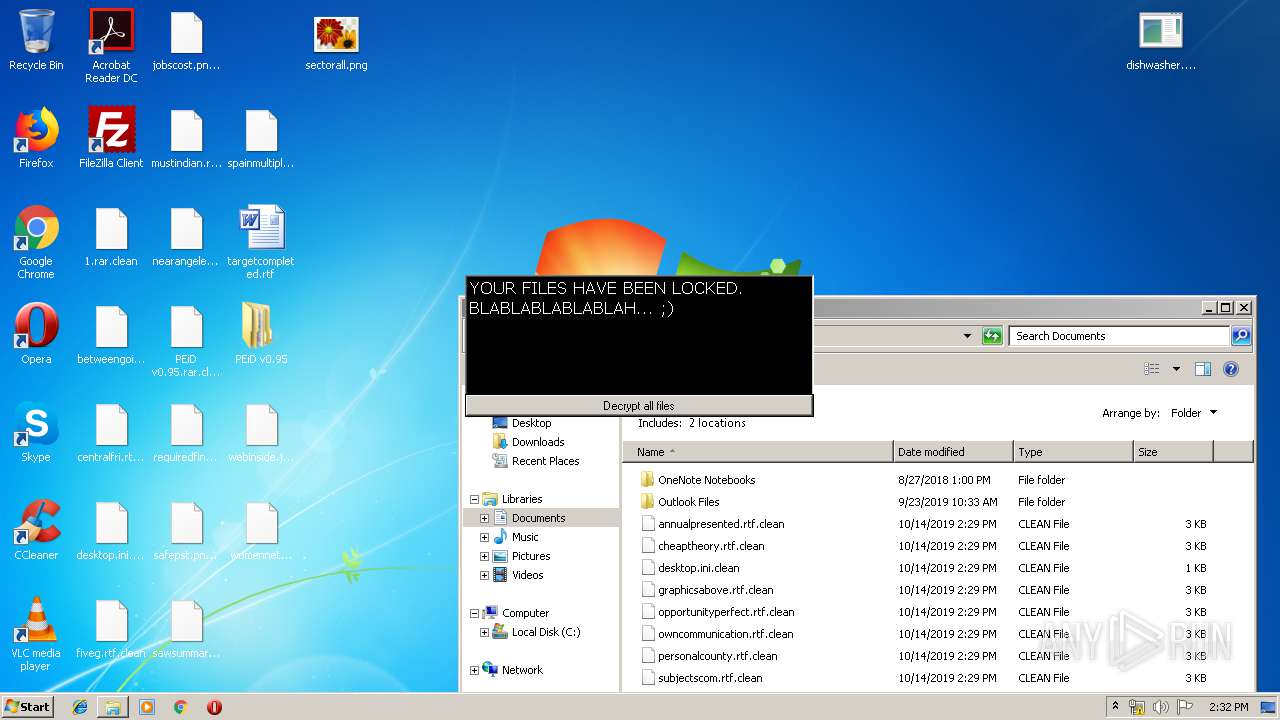
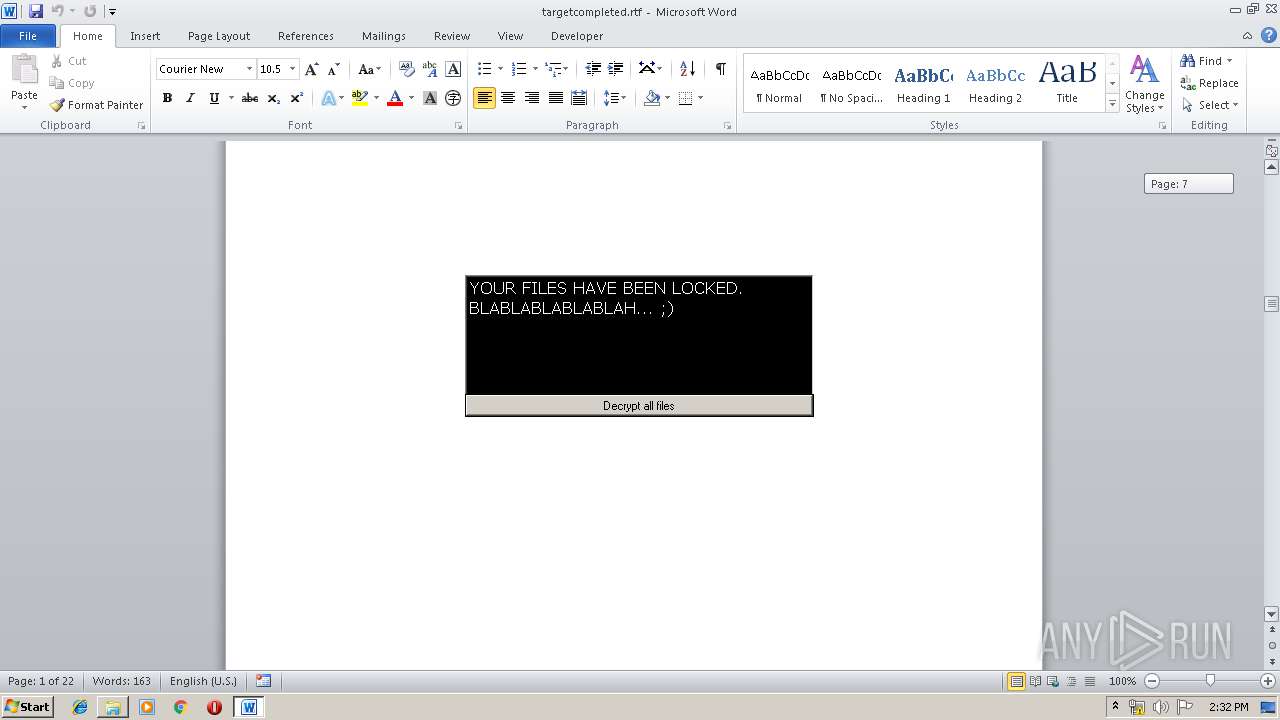
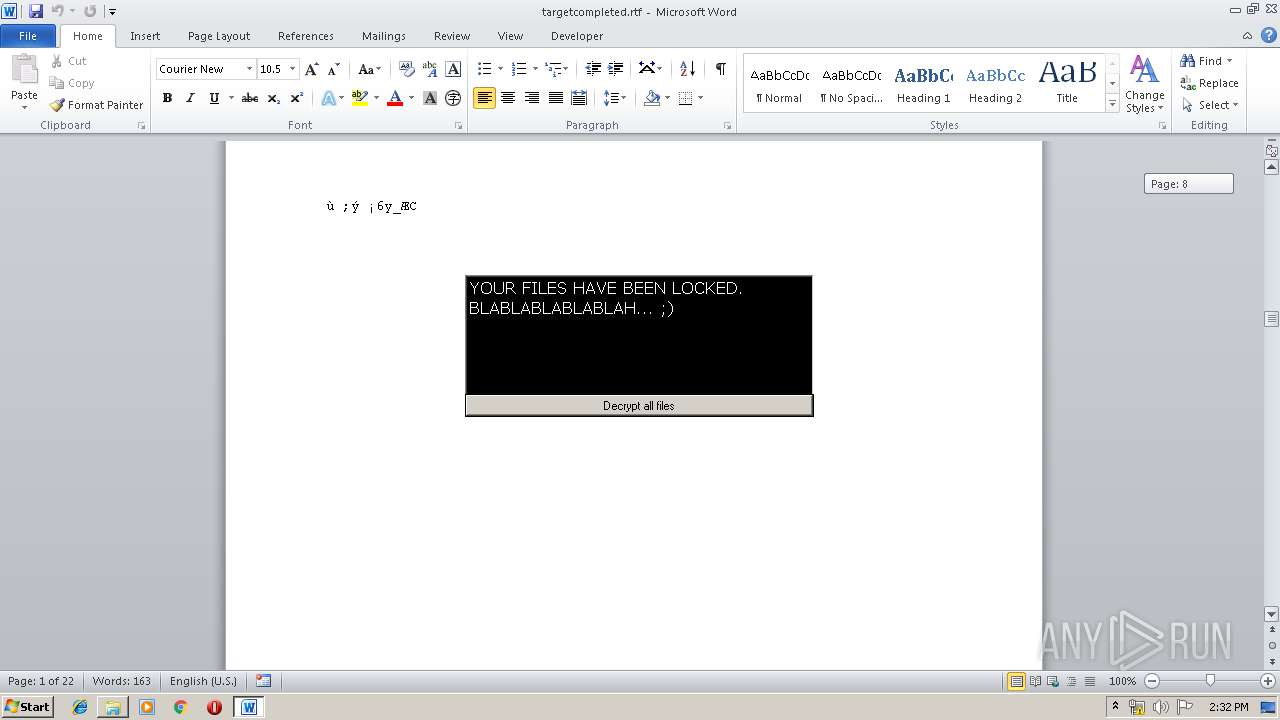
| File name: | 1.rar |
| Full analysis: | https://app.any.run/tasks/a134e971-b5a7-4ef9-9e53-70424d5d5ae1 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2019, 13:28:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | DF3138DFBB2BCBA4319D3A21B023864B |
| SHA1: | 056EA6B2C17AEEBB3020124A267E9C6322F0F867 |
| SHA256: | D531FE3E814CFBBC836B72B8AB7F23A0546DA9C5008E8E0CDFD1DFFE99AD4EF8 |
| SSDEEP: | 12288:sQPmSwLzwkqSJTskT+Xtgi2gjIDSiSa1GvLPeC48UBMprJ+Eo:sgmSMwkqSGi+Xtr2TDwa12PeC48UGV+t |
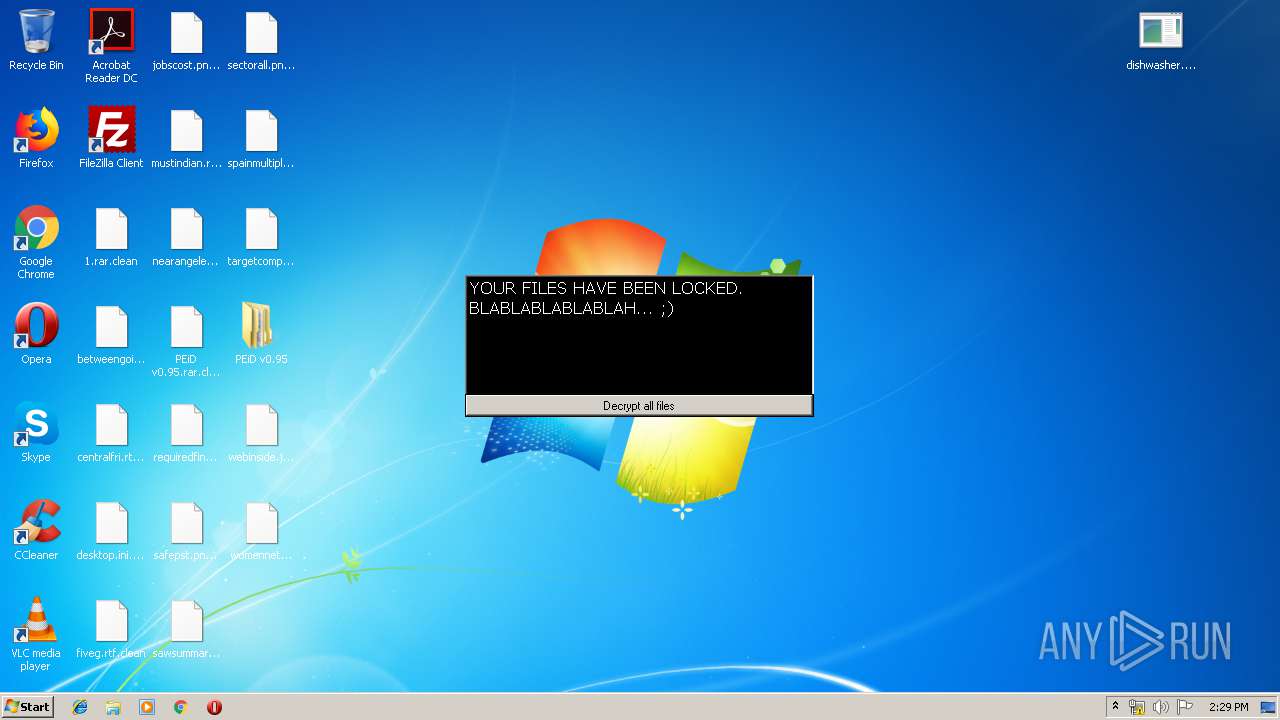
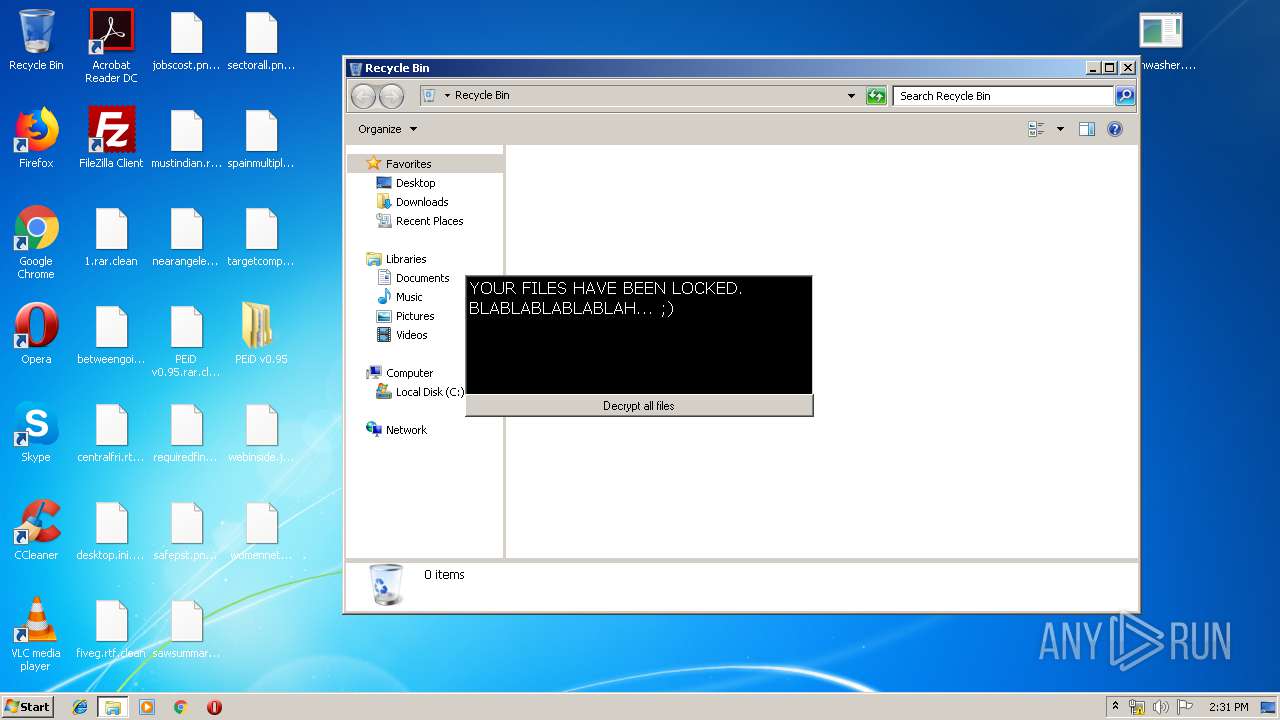
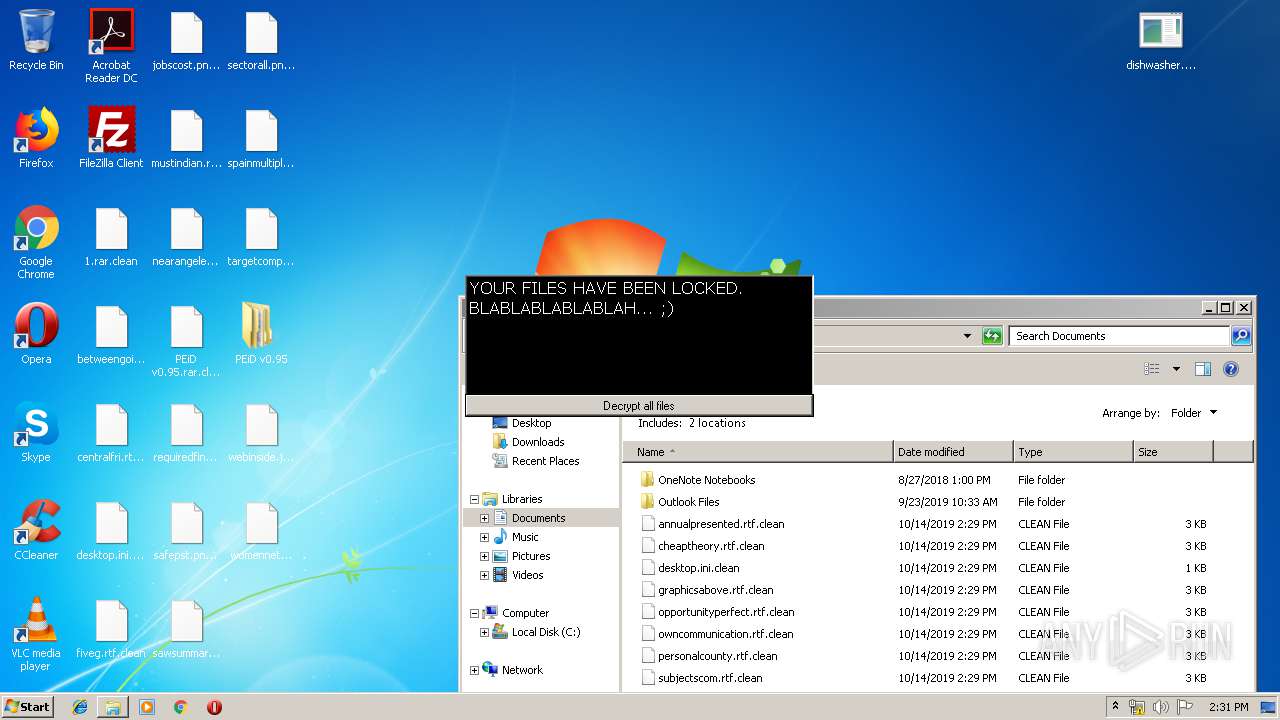
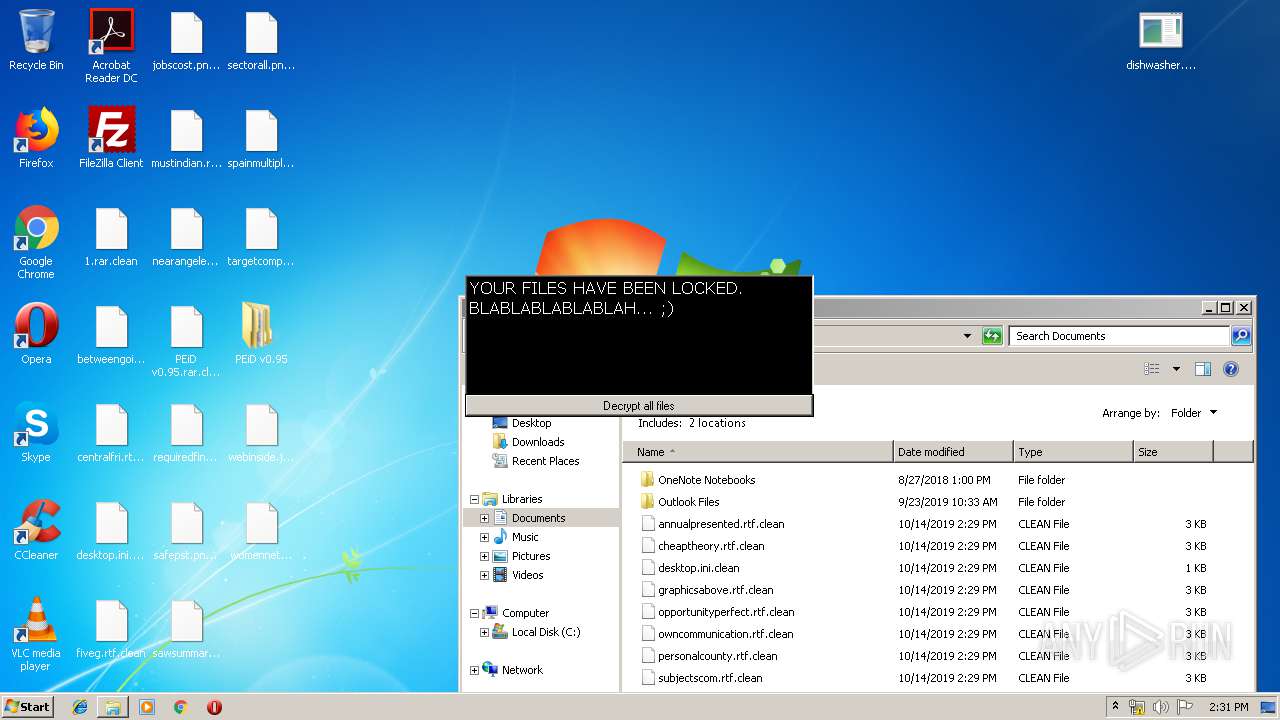
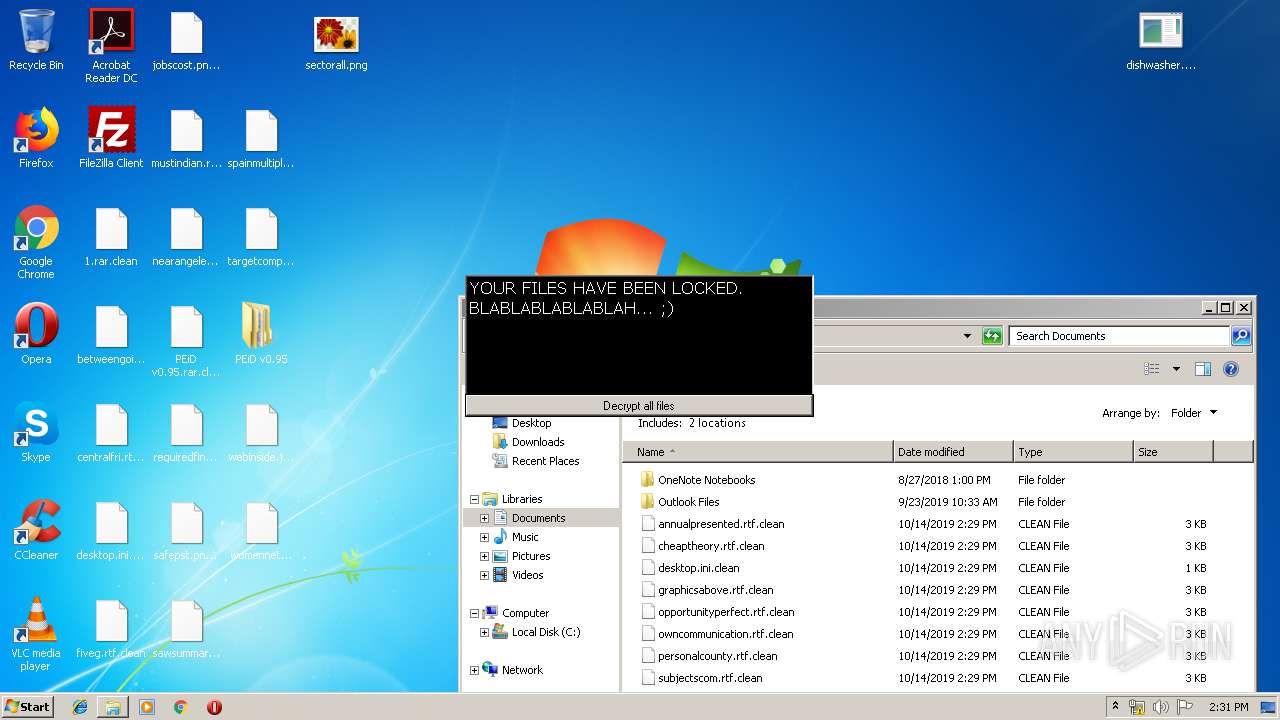
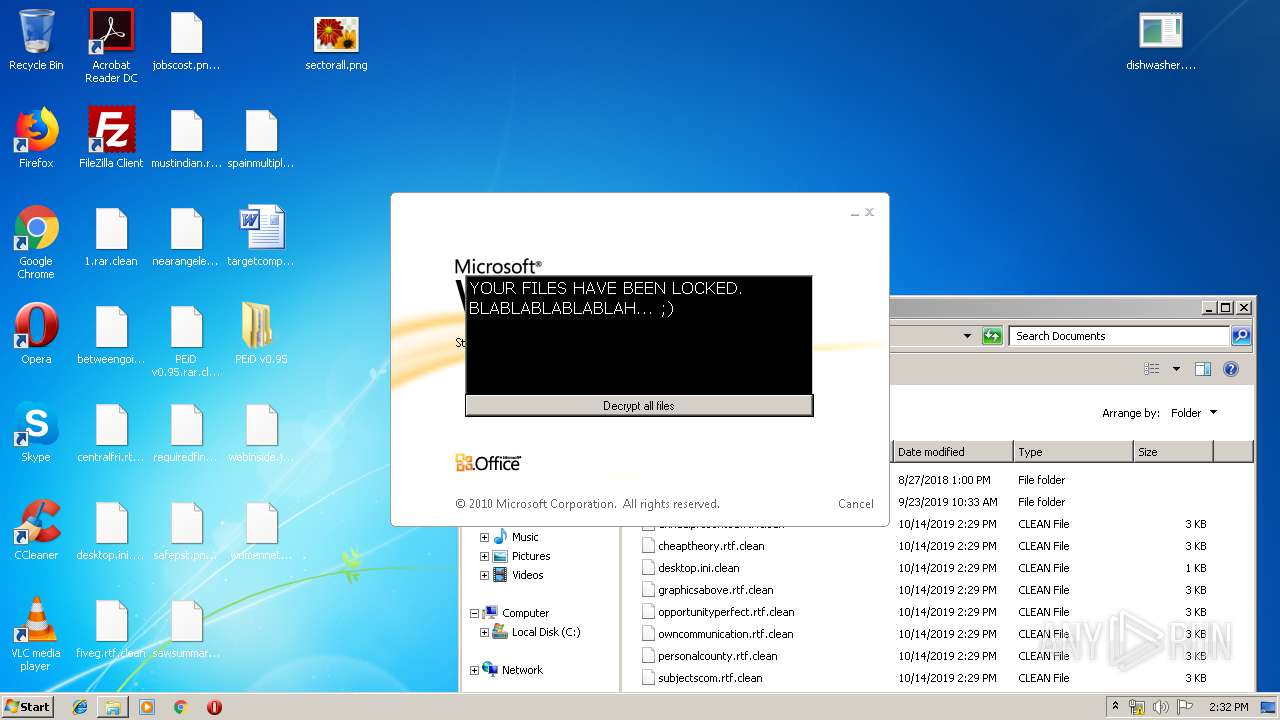
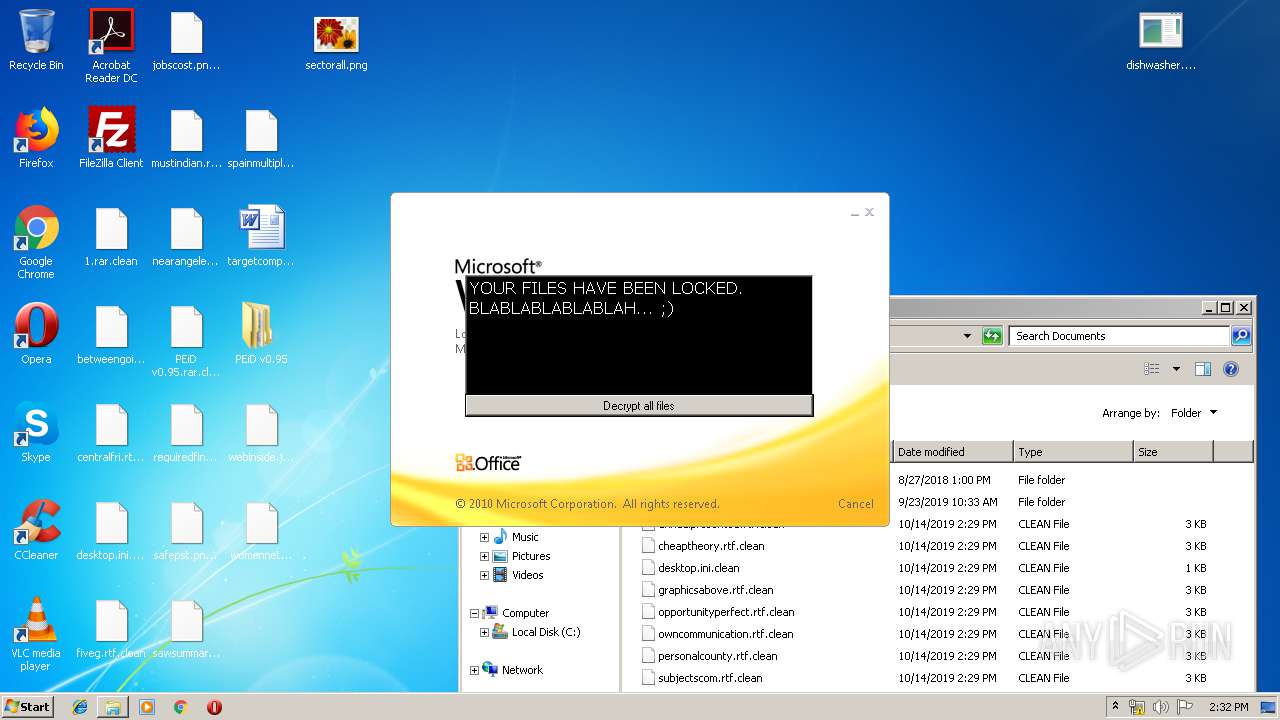
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3440)
- PEiD.exe (PID: 3600)
Application was dropped or rewritten from another process
- PEiD.exe (PID: 3600)
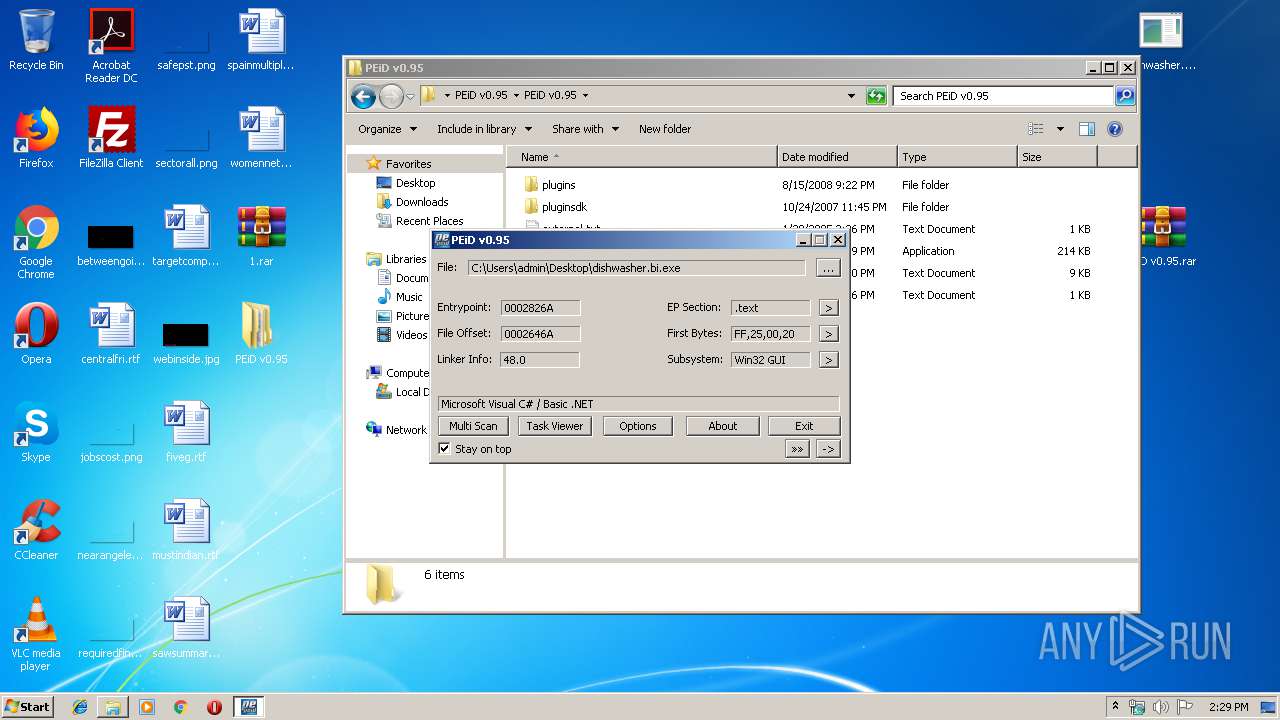
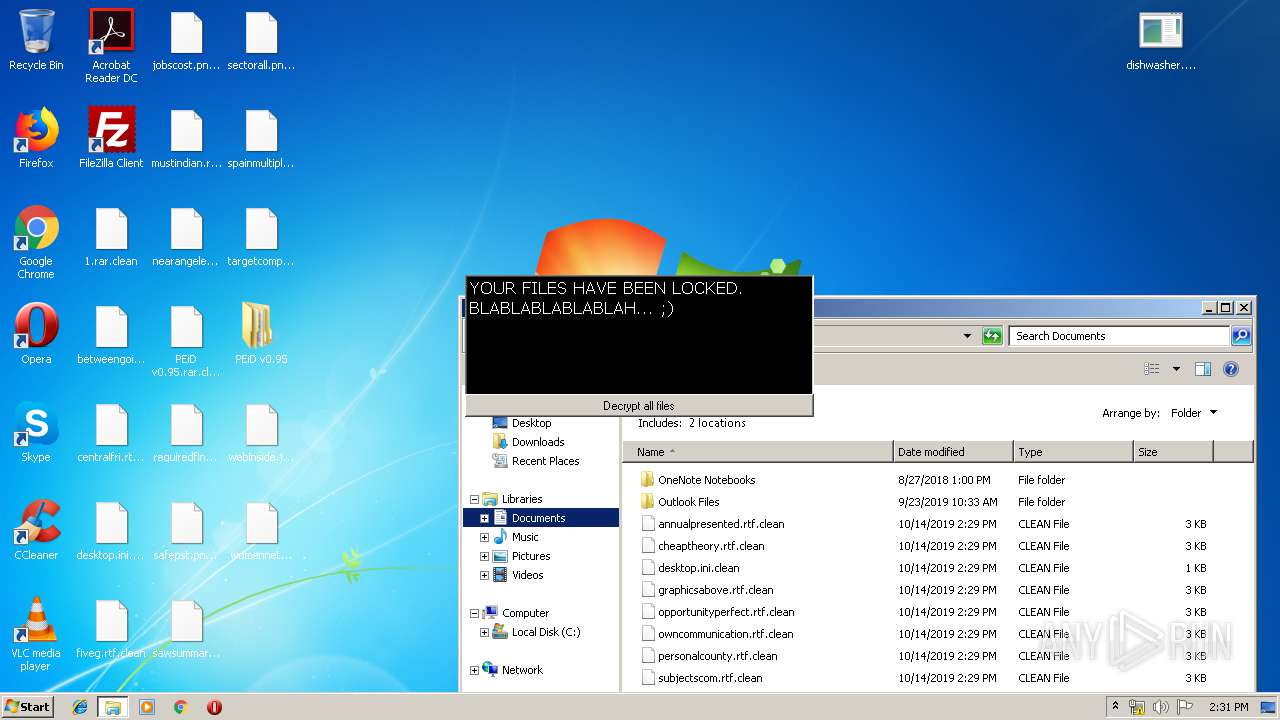
- dishwasher.bi.exe (PID: 2776)
- dishwasher.bi.exe (PID: 1560)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3172)
- dishwasher.bi.exe (PID: 2776)
Application launched itself
- WinRAR.exe (PID: 1904)
Starts itself from another location
- dishwasher.bi.exe (PID: 2776)
Executed via COM
- DllHost.exe (PID: 1908)
INFO
Manual execution by user
- WinRAR.exe (PID: 3172)
- dishwasher.bi.exe (PID: 2776)
- PEiD.exe (PID: 3600)
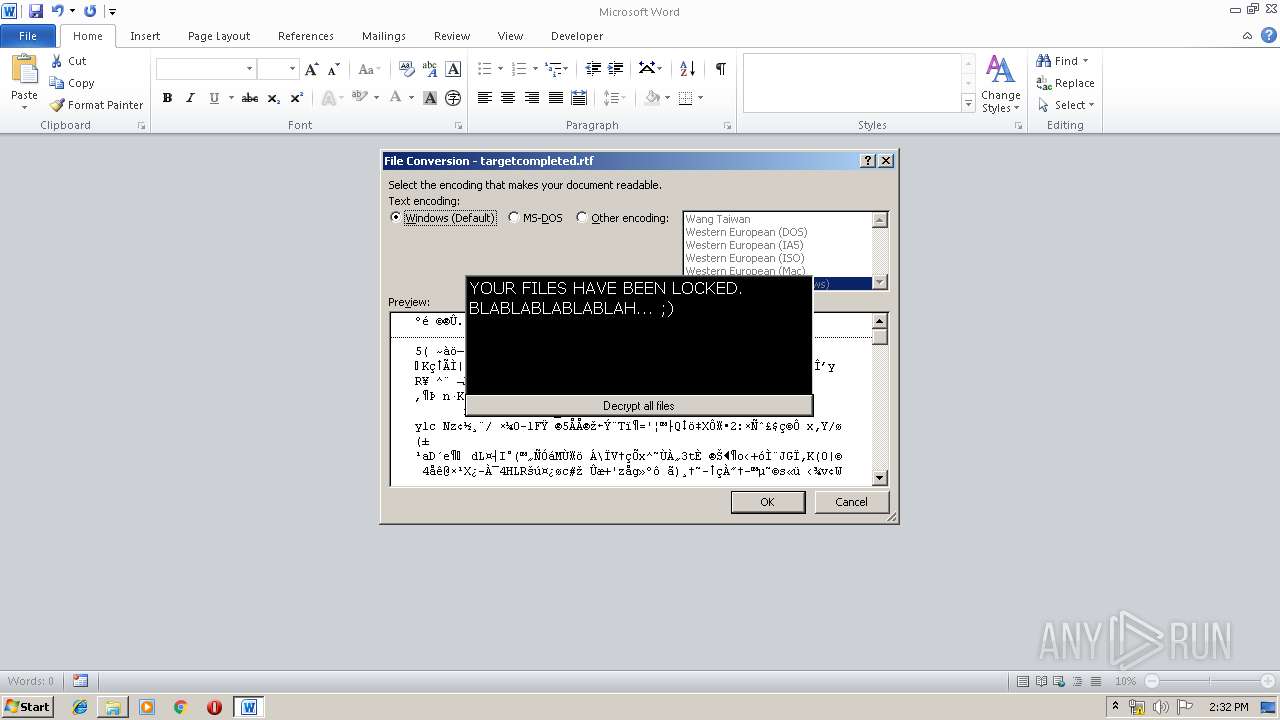
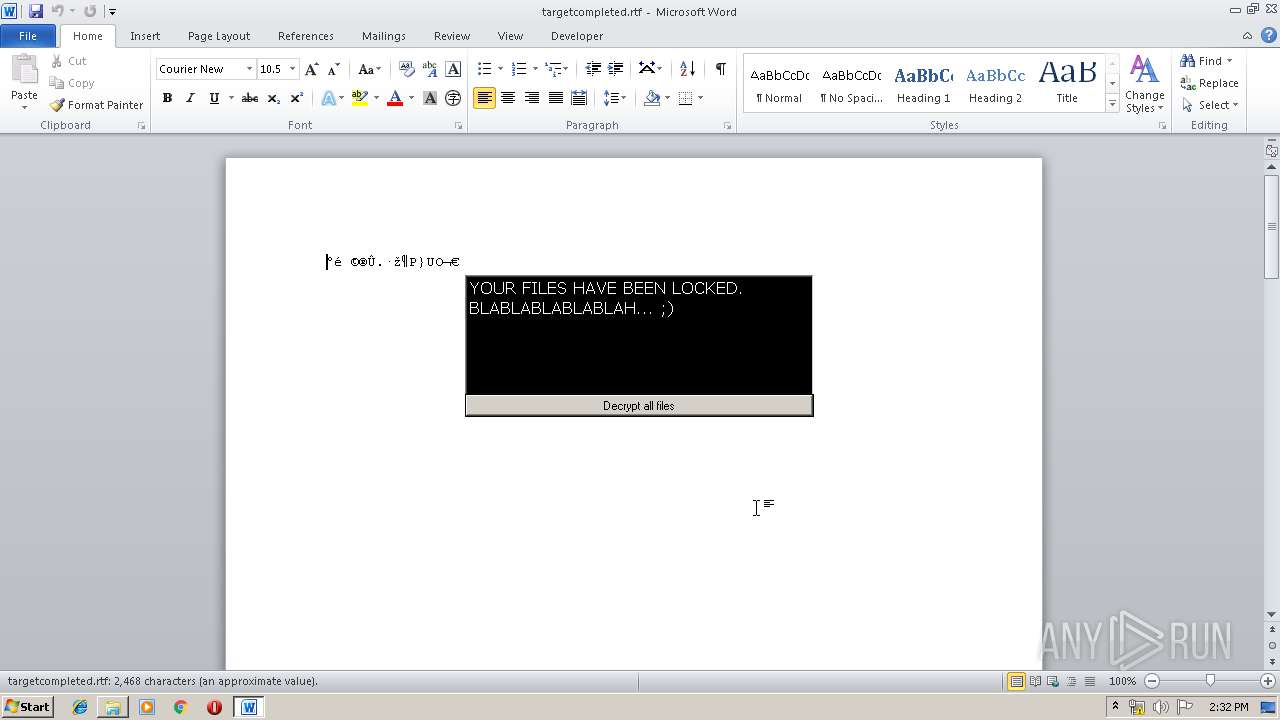
- WINWORD.EXE (PID: 184)
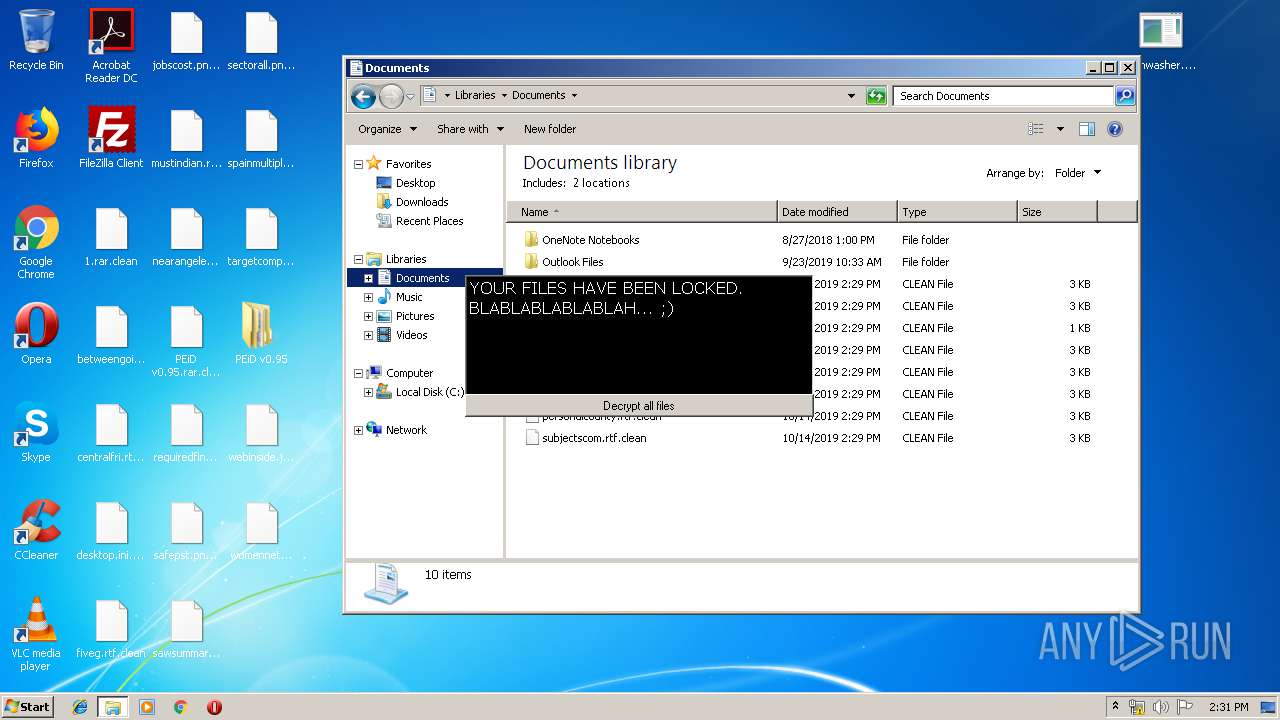
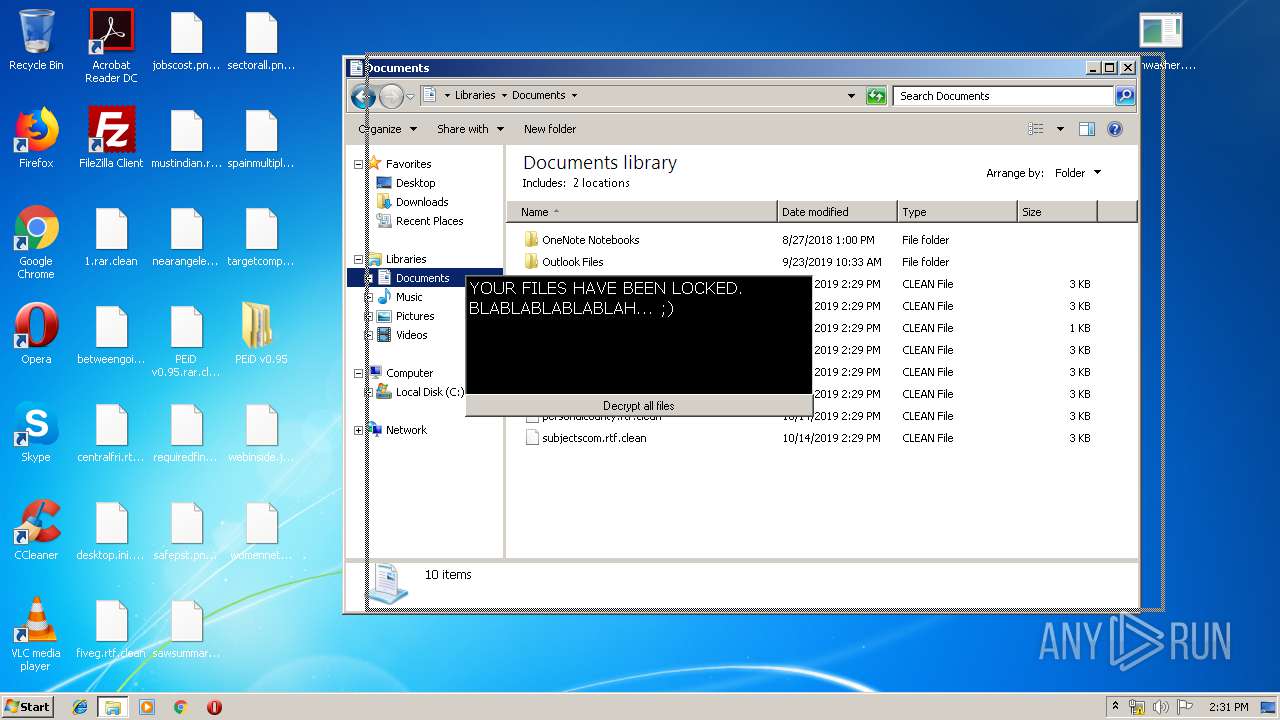
Creates files in the user directory
- WINWORD.EXE (PID: 184)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 151405 |
|---|---|
| UncompressedSize: | 151361 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2019:10:14 17:20:18 |
| PackingMethod: | Stored |
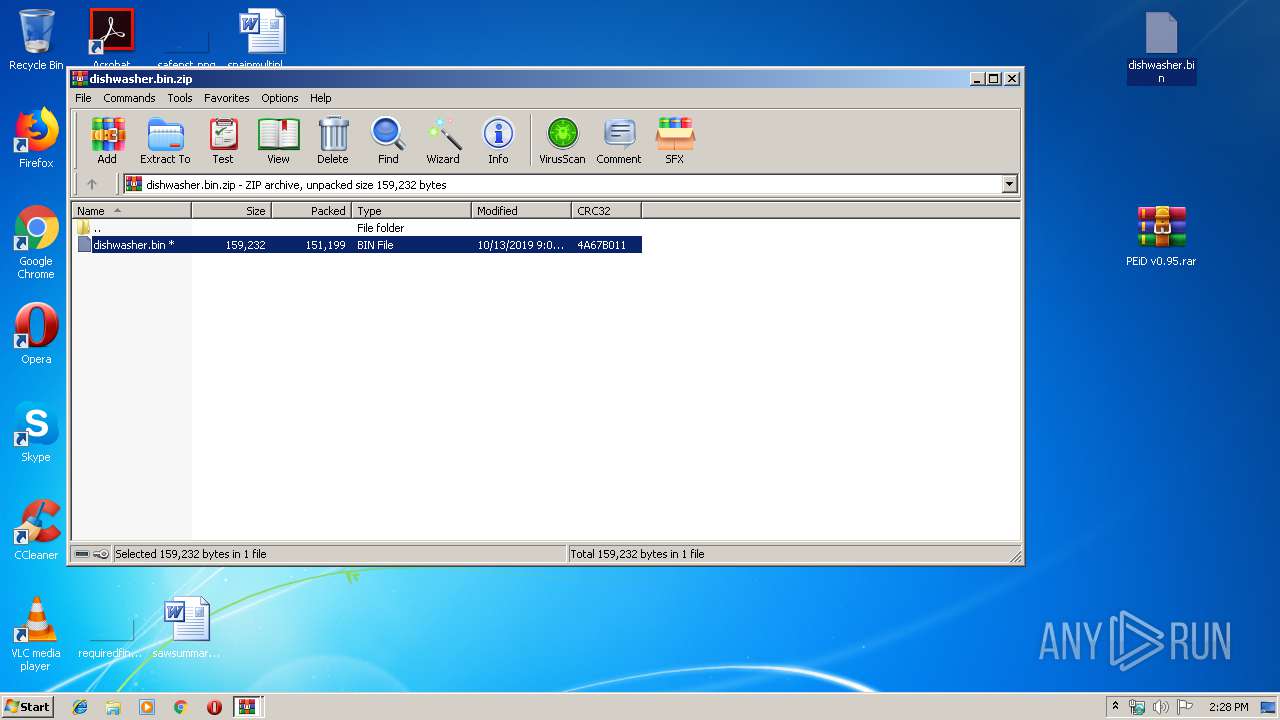
| ArchivedFileName: | dishwasher.bin.zip |
Total processes
52
Monitored processes
9
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\targetcompleted.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\AppData\Local\Temp\dishwasher.bi.exe" | C:\Users\admin\AppData\Local\Temp\dishwasher.bi.exe | — | dishwasher.bi.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1820 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1904.22631\dishwasher.bin.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\1.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1908 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\Desktop\dishwasher.bi.exe" | C:\Users\admin\Desktop\dishwasher.bi.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
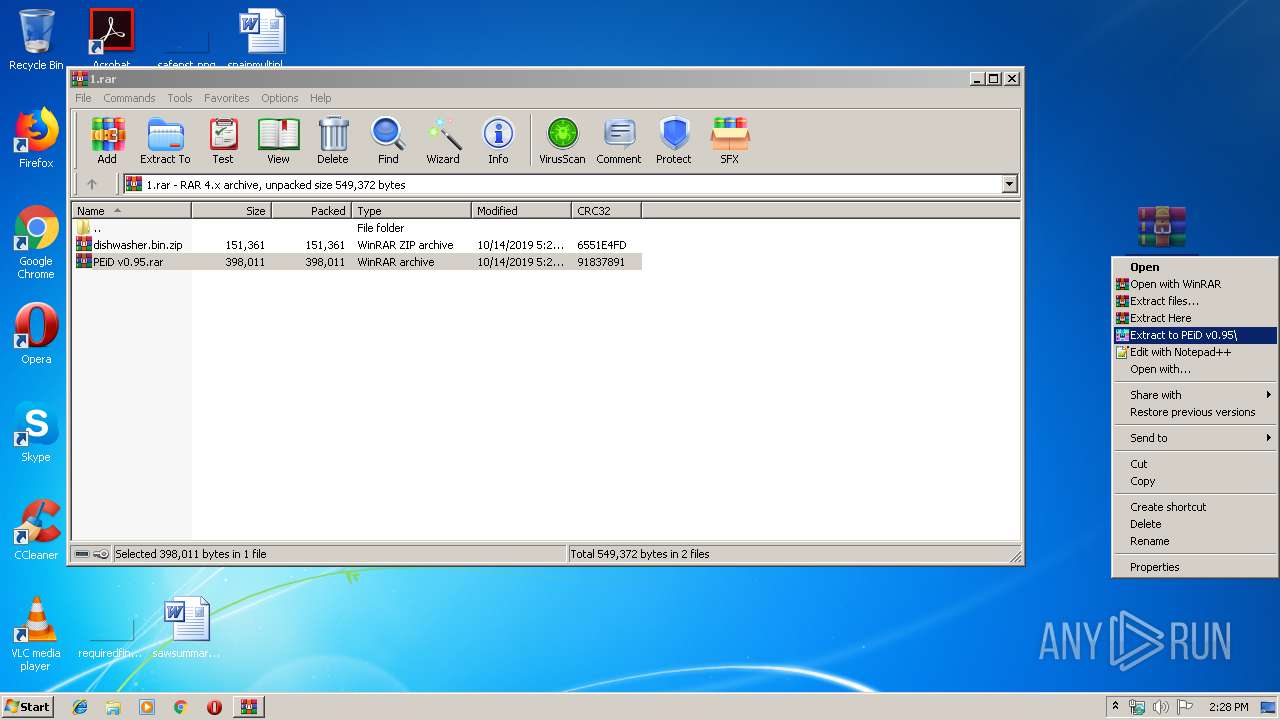
| 3172 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\PEiD v0.95.rar" "C:\Users\admin\Desktop\PEiD v0.95\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3440 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3600 | "C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\PEiD.exe" C:\Users\admin\Desktop\dishwasher.bi.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\PEiD.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
2 709
Read events
2 316
Write events
247
Delete events
146
Modification events
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\1.rar | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
6
Suspicious files
61
Text files
48
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1820 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1820.23279\dishwasher.bin | — | |
MD5:— | SHA256:— | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1904.21843\PEiD v0.95.rar | compressed | |
MD5:— | SHA256:— | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\PEiD.exe | executable | |
MD5:4B5289D1DBD727C5DD0E247A7D7DB03E | SHA256:E13171D50F45A79BC09B9E4B9FFA38EB02301ACA94A1867A9BF8ACCCC3759030 | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\external.txt | text | |
MD5:AFD443CC0C5D9B3DF146294D89EA45C6 | SHA256:91F4499A4395F76B0D408D702663BD471F7158D9B5D2044576759BC7FC8784A9 | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\pluginsdk\C++\null.c | text | |
MD5:34E7B31CD8E5FD191D5EC5DDEEE63188 | SHA256:A607448FF316316D2A39A34A8E12362398086CFFB3DD261D4D83EC8E36602ABD | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\plugins\ImpREC.dll | executable | |
MD5:8B623ADE9D85E81F754BA49C72CF6789 | SHA256:1455C5790AFDFD9B1AFDC84F2D1F2A0CC3E7162BD2127033E22DF9A123066EF4 | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\plugins\GenOEP.dll | executable | |
MD5:5F70E720B000B649FC3ADB34304424A6 | SHA256:6625F4D4D93D5FB3C6C91152E3B9E4F4FECD824DAB6DBFCABCA22B97B98072A1 | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\plugins\kanal.dll | executable | |
MD5:30C1B6D7ED23997E380BE509E5849CF5 | SHA256:37765A23911158BE8351781771758D0B7AF3E8B6943EA97E32612DDB5E4E0272 | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\pluginsdk\MASM\compile.bat | text | |
MD5:C08FE1558E092E9D6A601E8F455454CA | SHA256:31D198367B1CF69ADAAD5AE06CE436AE00782982DB97AA2098C375FB565623FA | |||
| 3172 | WinRAR.exe | C:\Users\admin\Desktop\PEiD v0.95\PEiD v0.95\plugins\ZDRx.dll | executable | |
MD5:E0B6CD76991F335AF003D22CA5F44FB2 | SHA256:D89FA0E7DFAA5937ABE1FD112902EB5EAC52DC97E974DA37BA5610A75B1F4519 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report