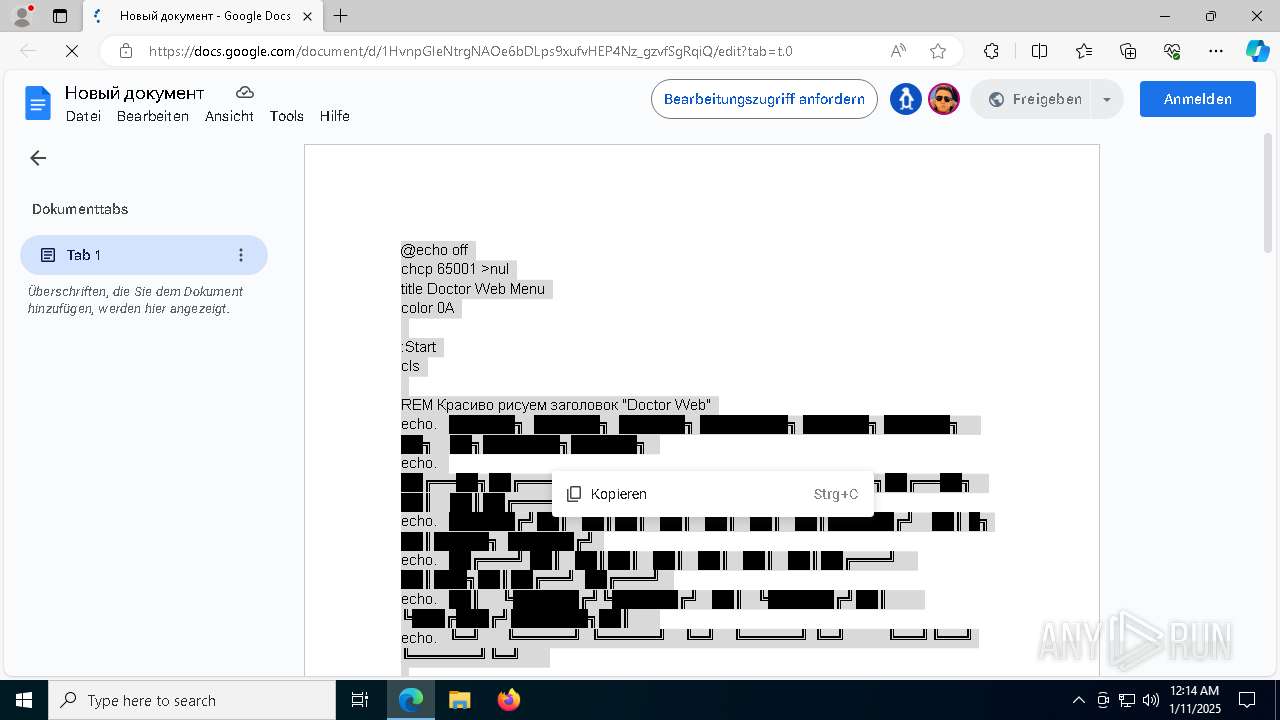
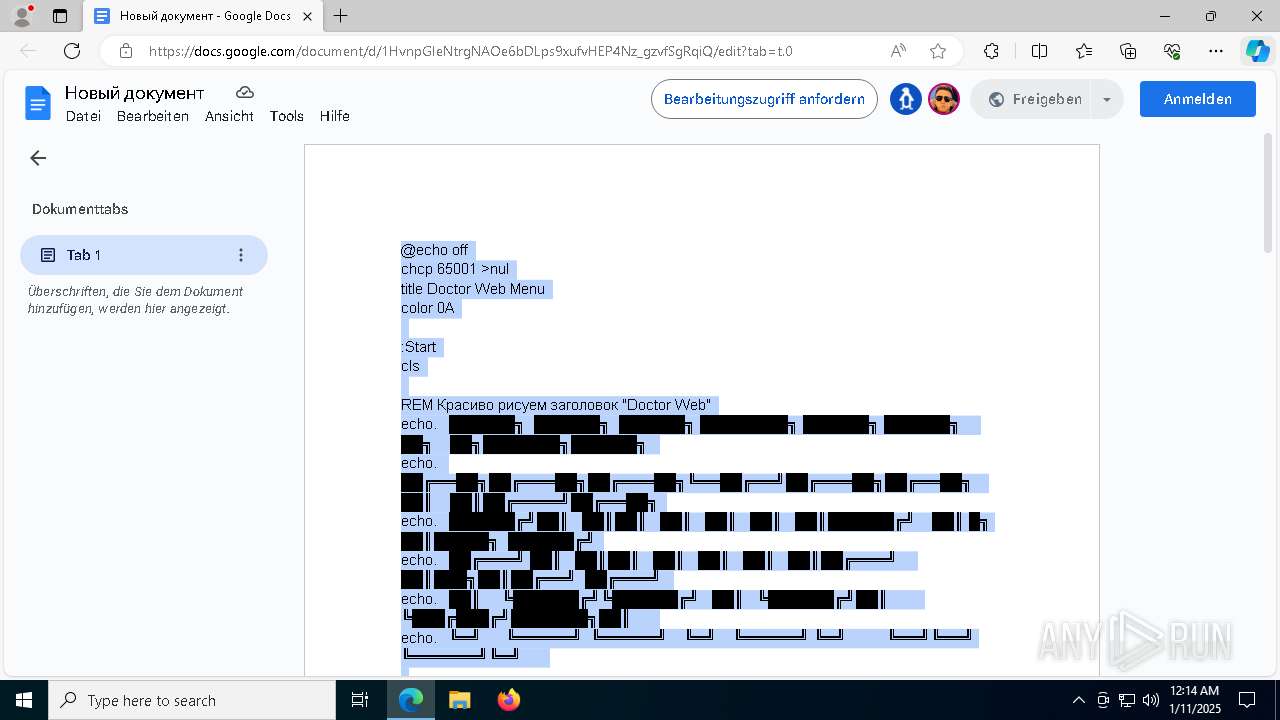
| URL: | https://docs.google.com/document/d/1HvnpGIeNtrgNAOe6bDLps9xufvHEP4Nz_gzvfSgRqiQ/edit?usp=drivesdk |
| Full analysis: | https://app.any.run/tasks/3a4dc493-5cb6-41b1-bd92-d88a881759a3 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 00:14:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6CA5B6AD6D5315C4E604358D2F5E63AE |
| SHA1: | EB112279E40AC6B315829B065BF176ACE2C906D3 |
| SHA256: | D531AE17F874B28F8C3152A9F1C595827C1E58FC03F7FC1CB983BF3524674E5A |
| SSDEEP: | 3:N8SP3unKJRBUt1g02HhpNwZnKrCMZ:2SmKJst1/2H/cWCo |
MALICIOUS
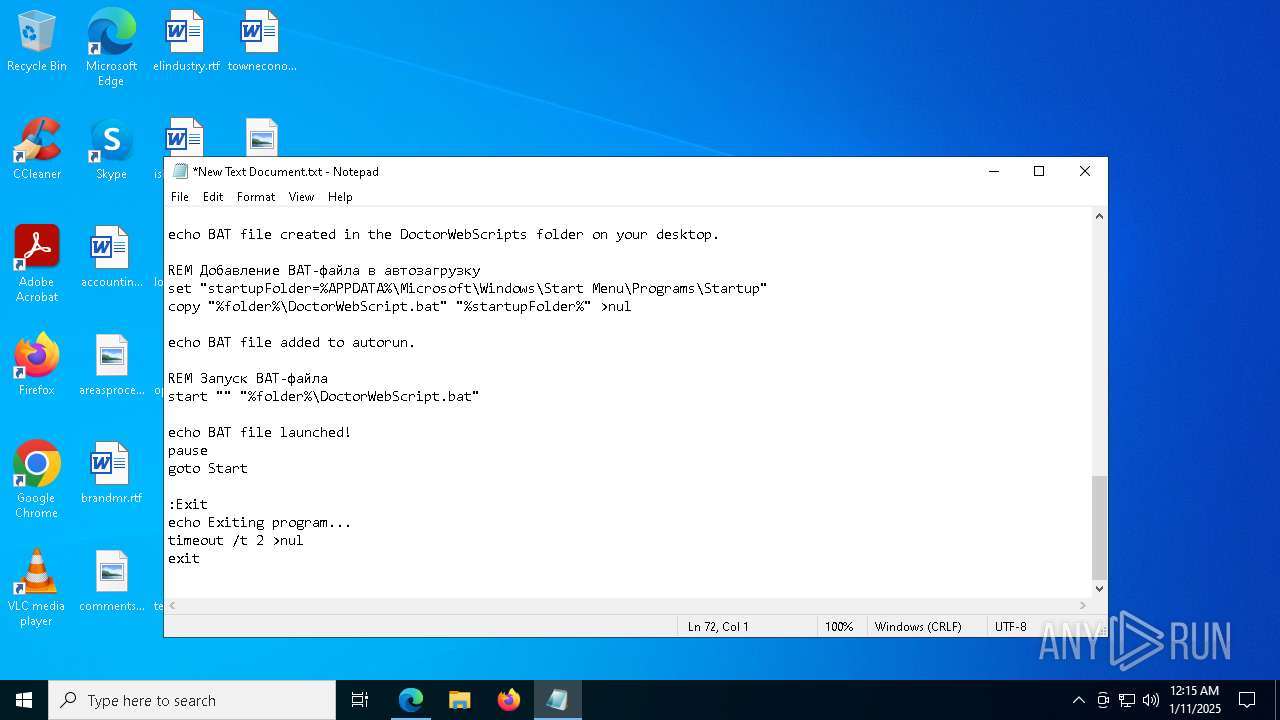
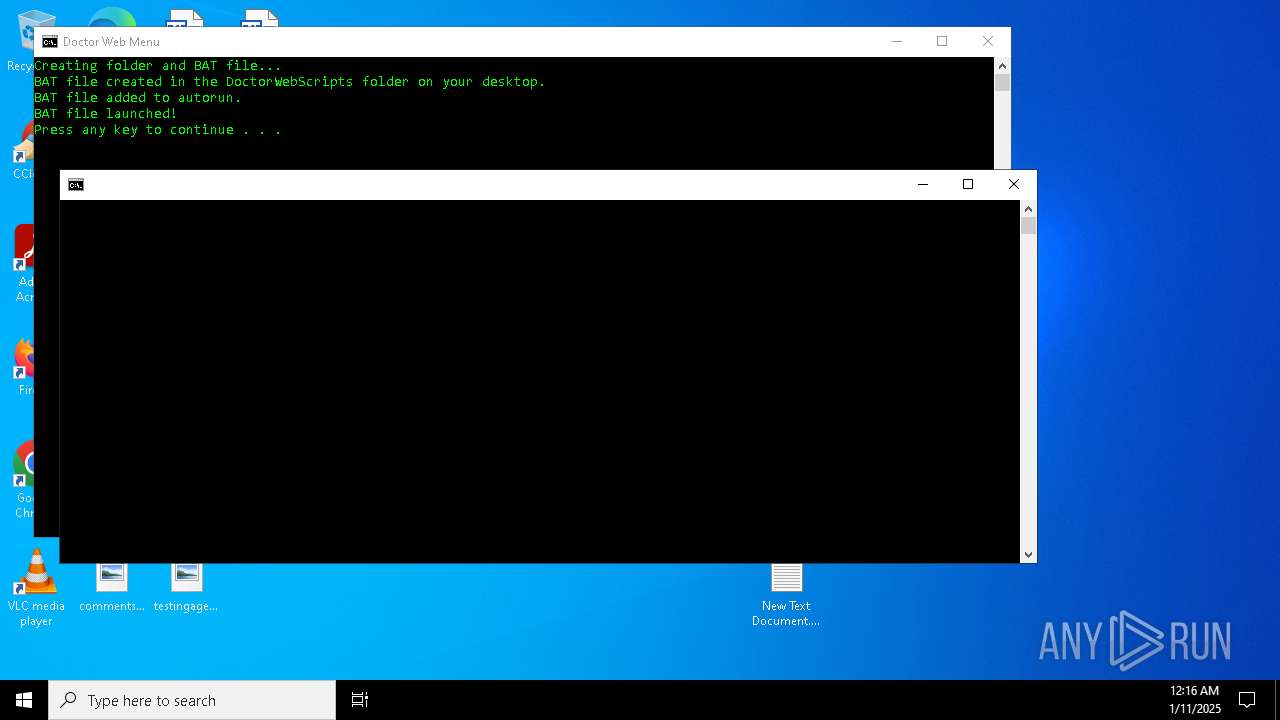
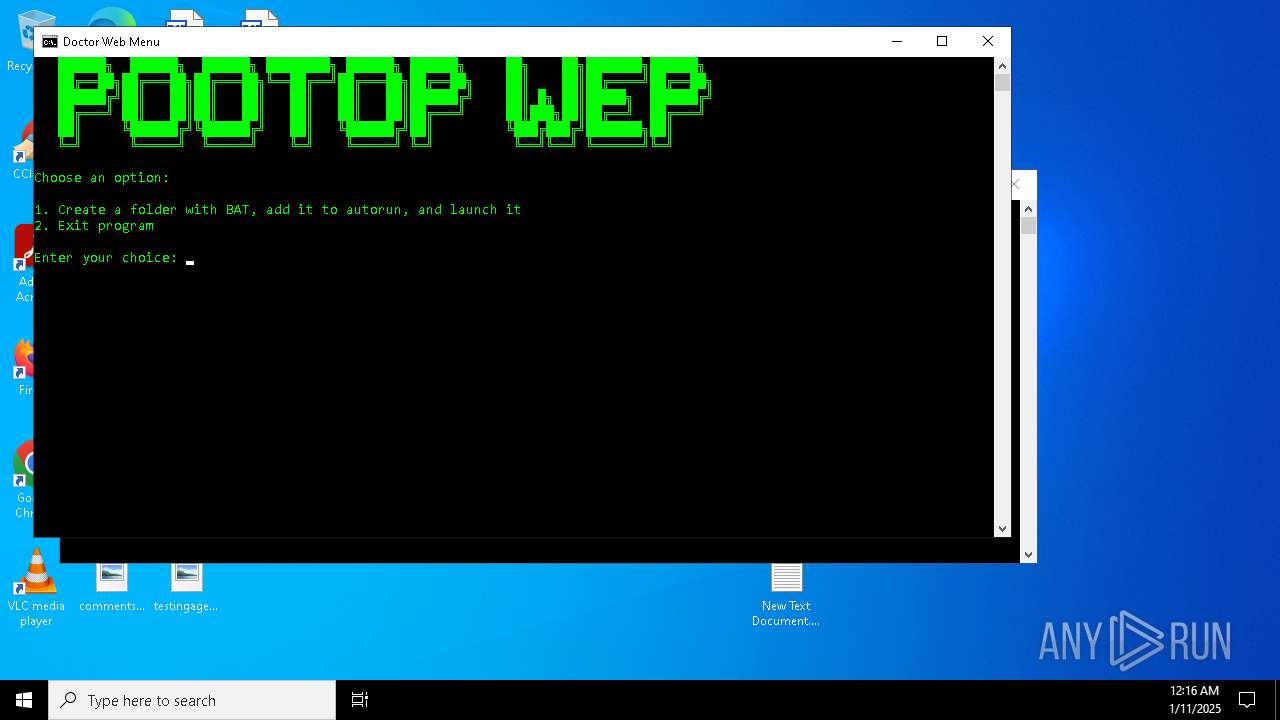
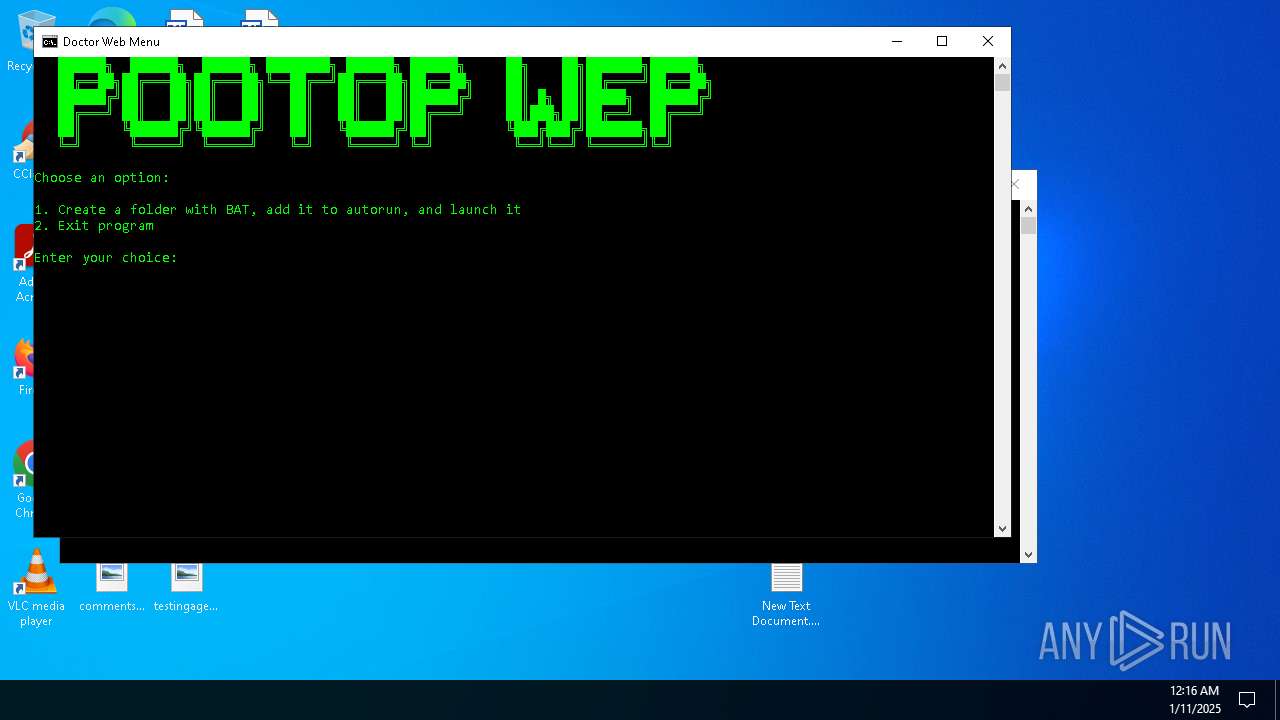
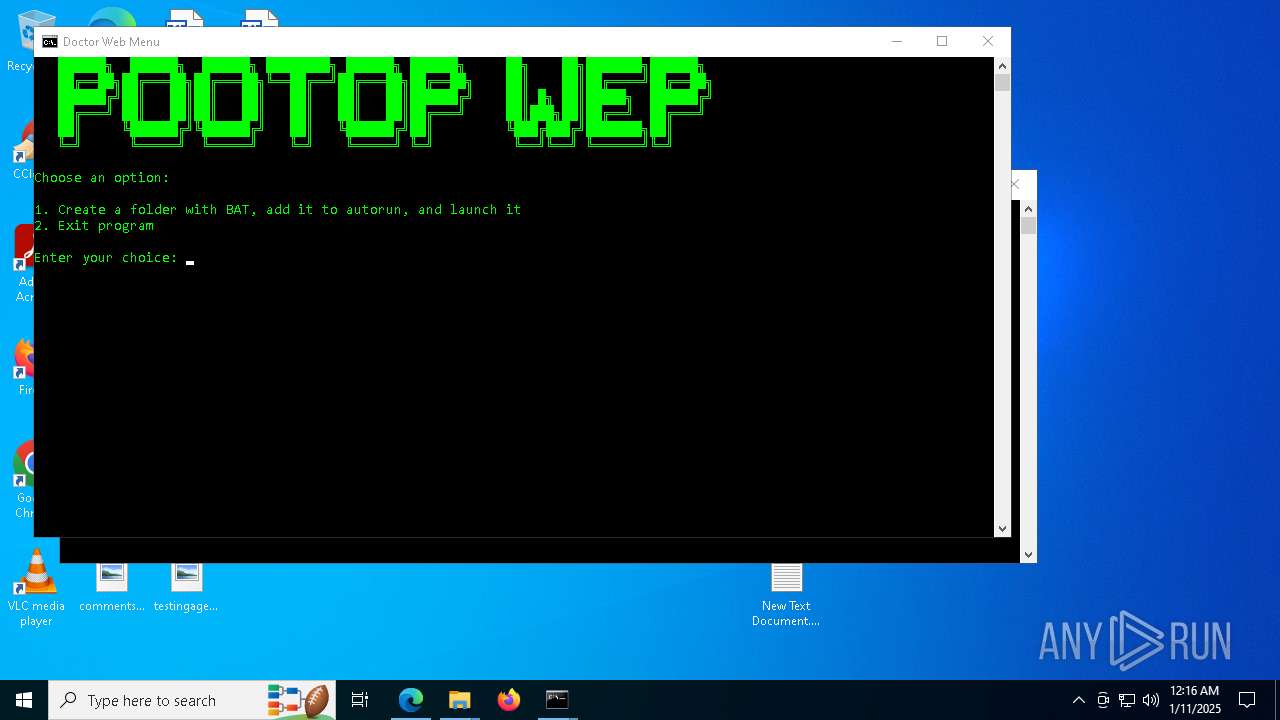
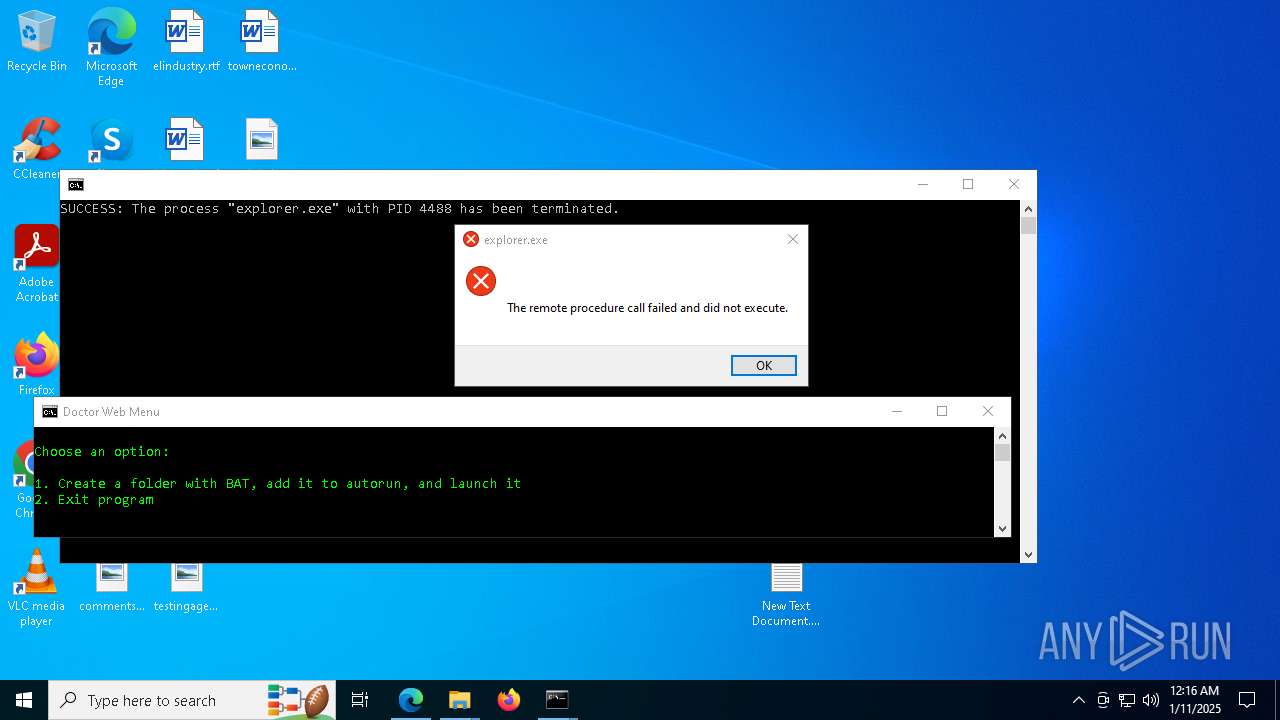
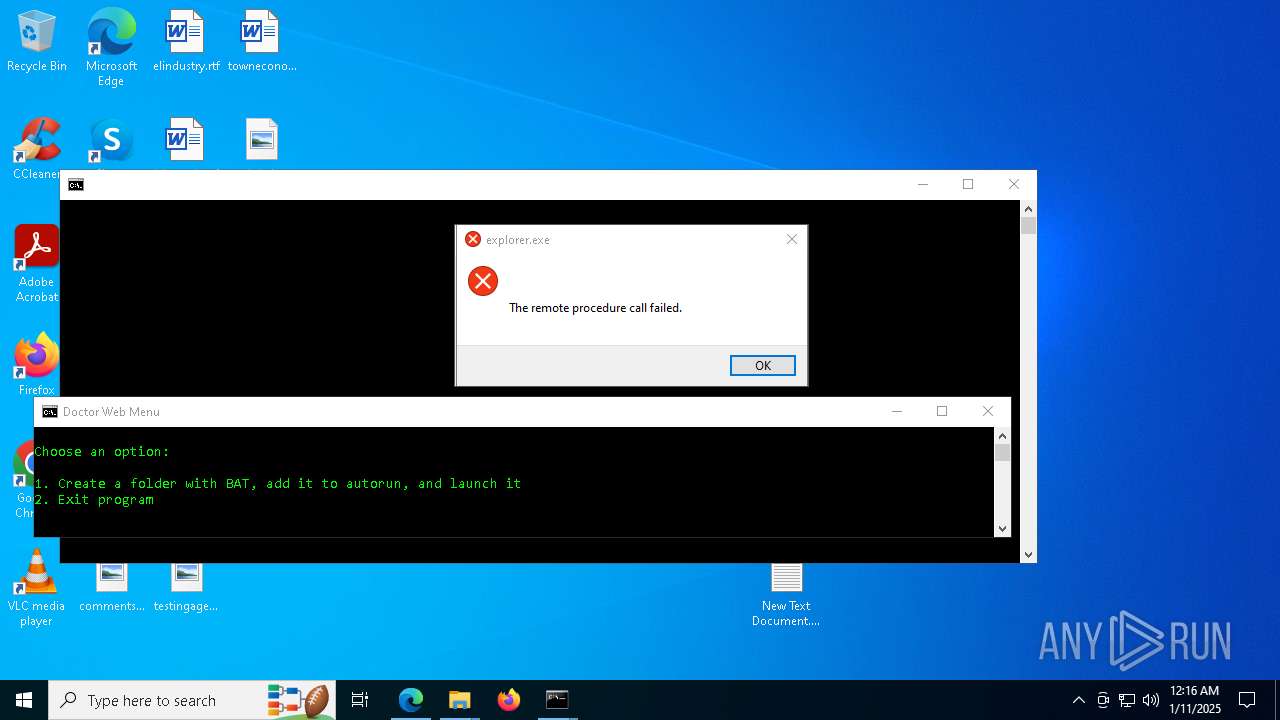
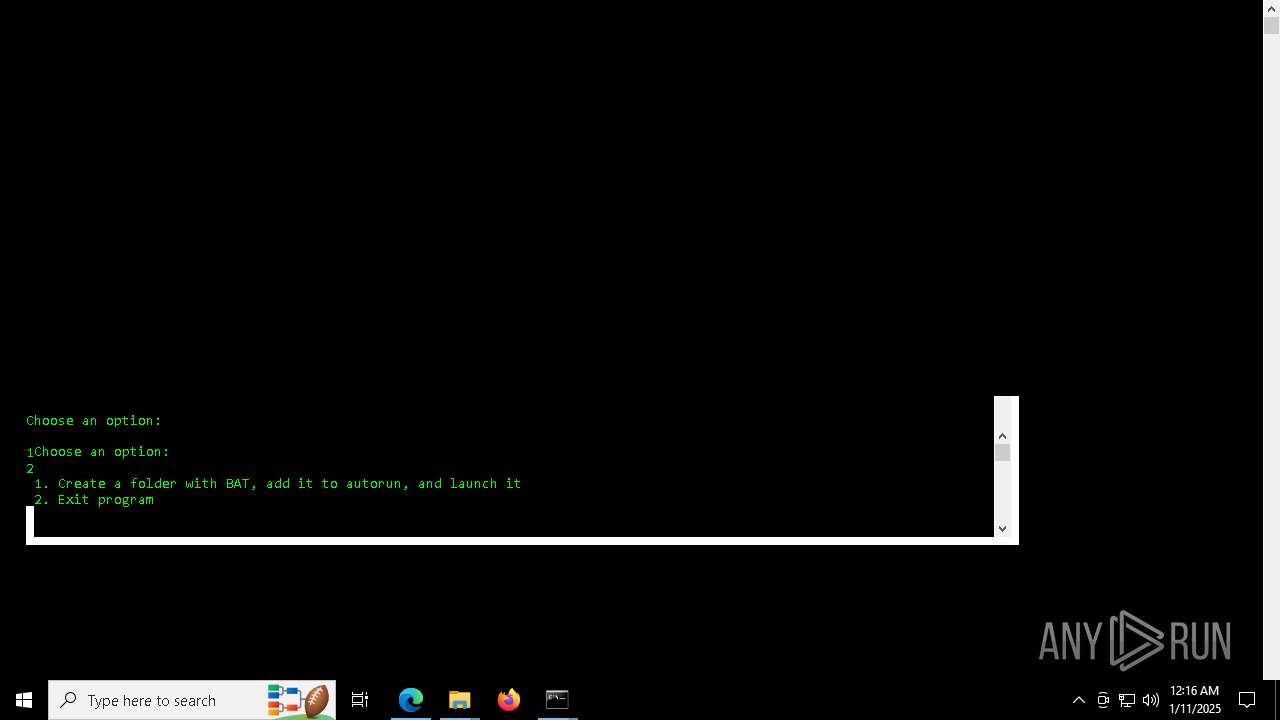
Create files in the Startup directory
- cmd.exe (PID: 7668)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 7668)
Application launched itself
- cmd.exe (PID: 7668)
Executing commands from a ".bat" file
- cmd.exe (PID: 7668)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7668)
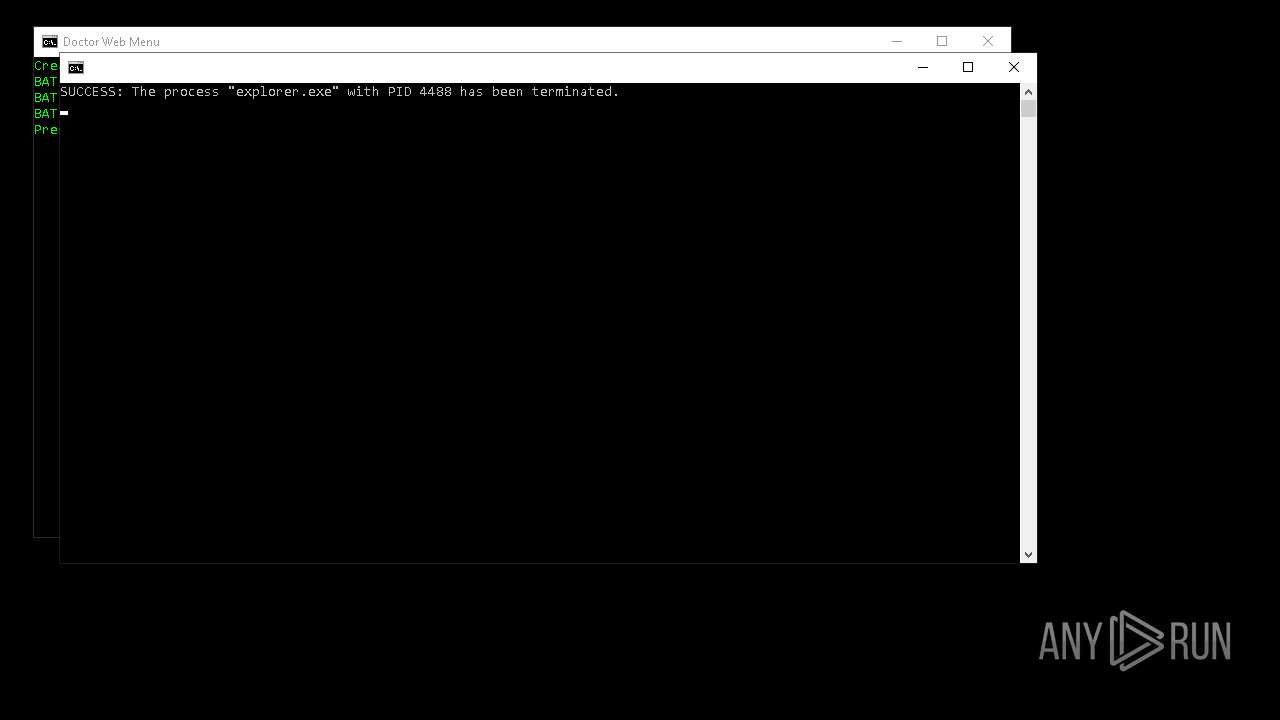
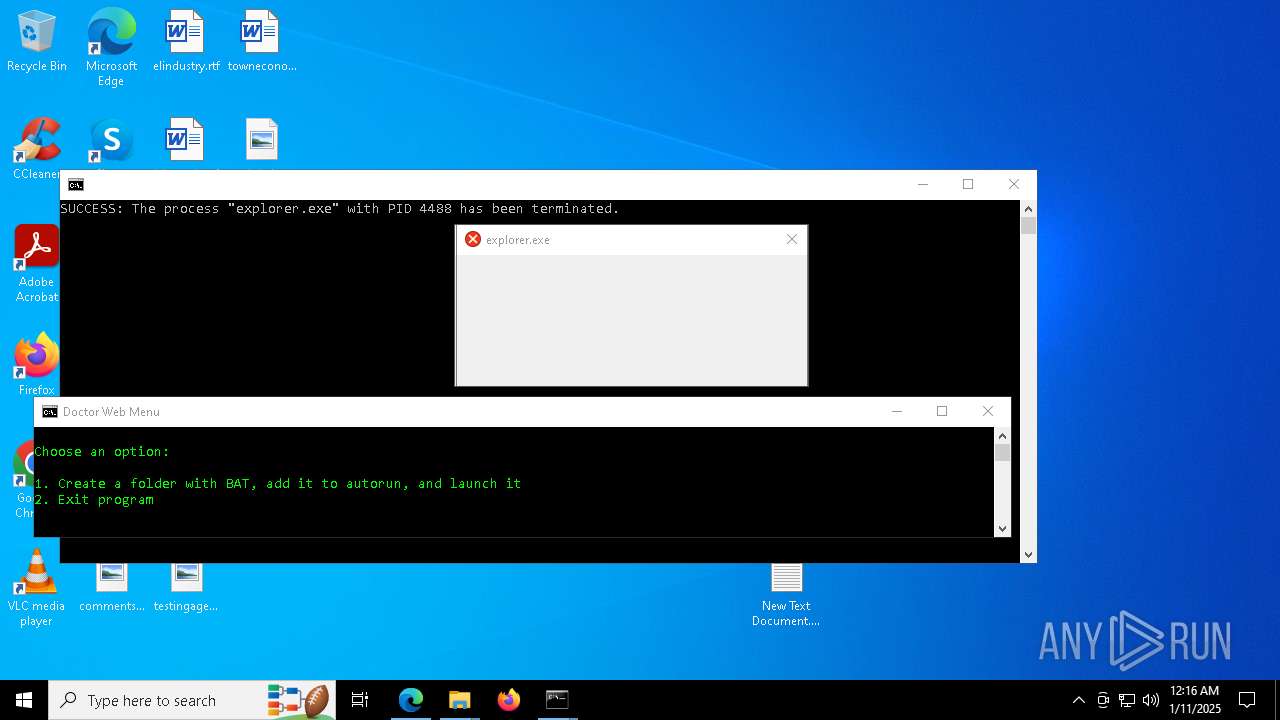
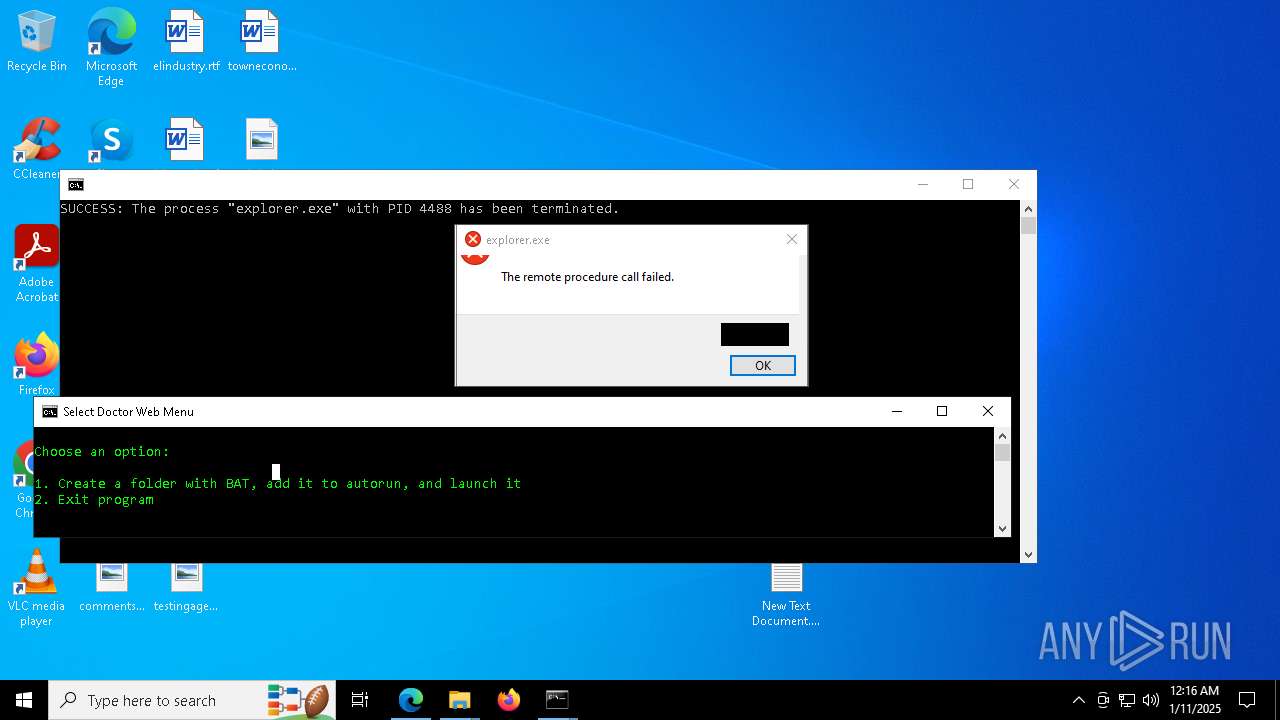
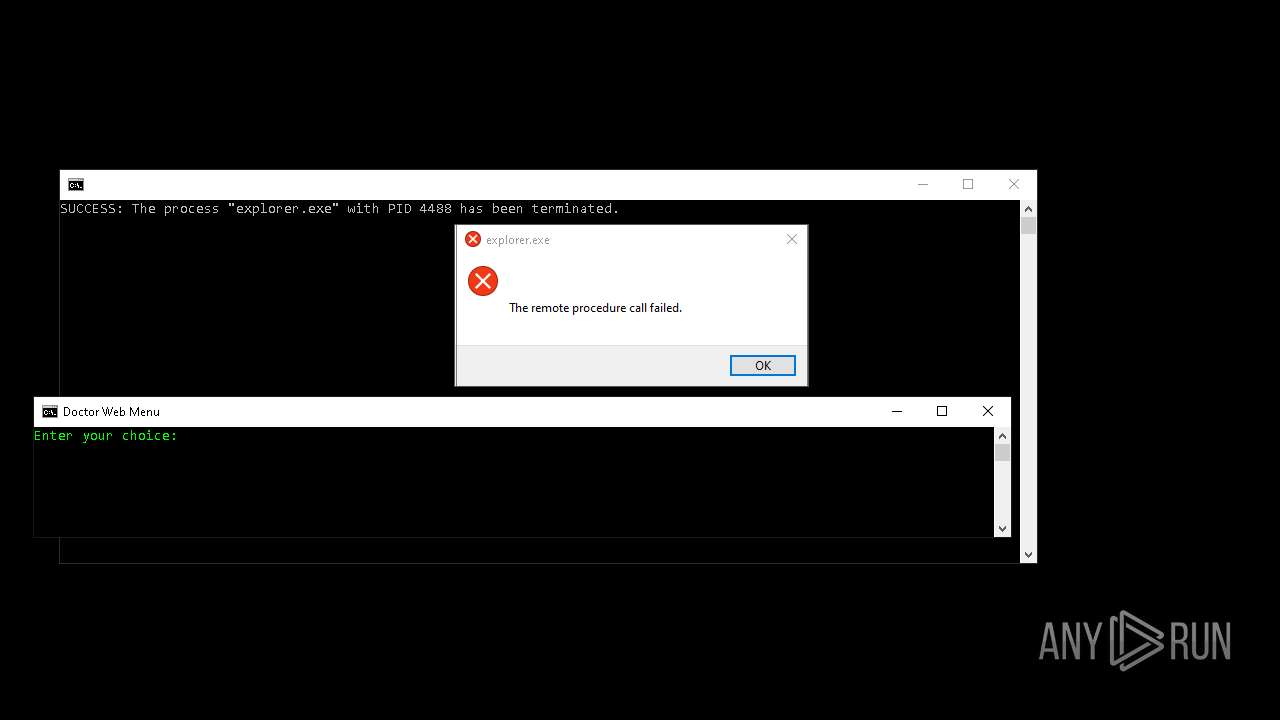
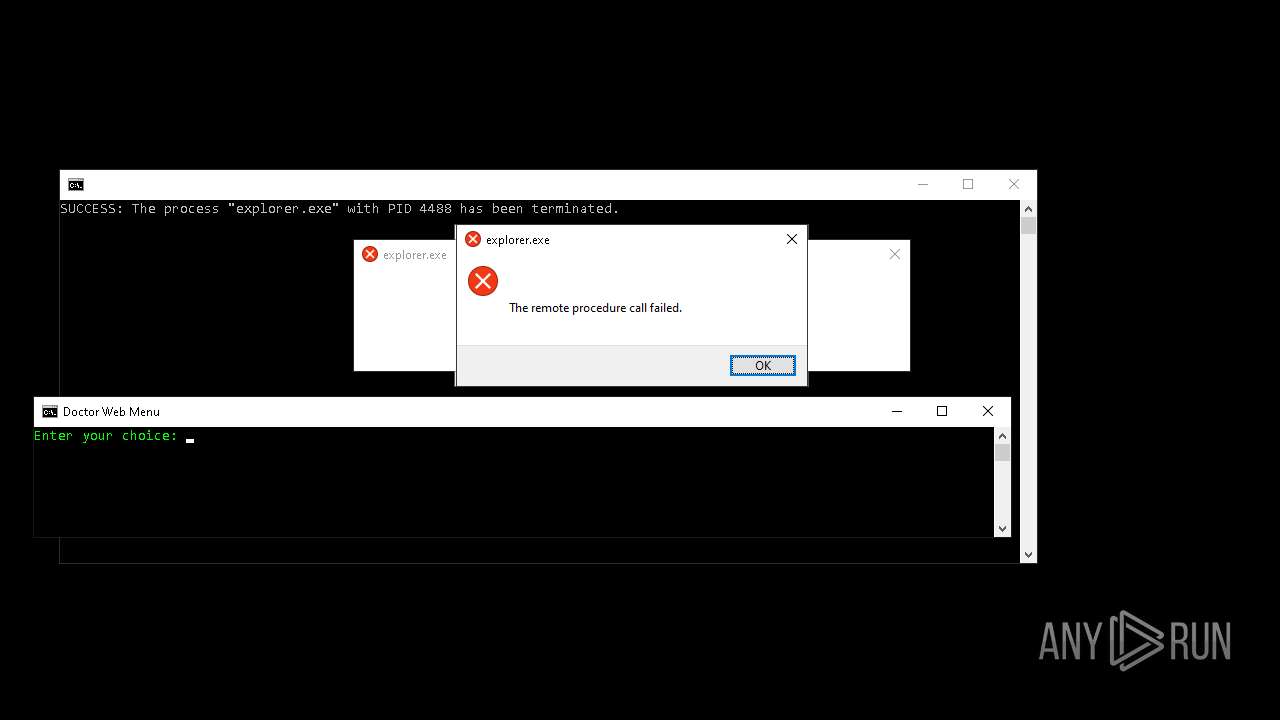
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7156)
The process creates files with name similar to system file names
- wermgr.exe (PID: 8656)
- wermgr.exe (PID: 8636)
- wermgr.exe (PID: 8864)
- WerFault.exe (PID: 5732)
- wermgr.exe (PID: 9520)
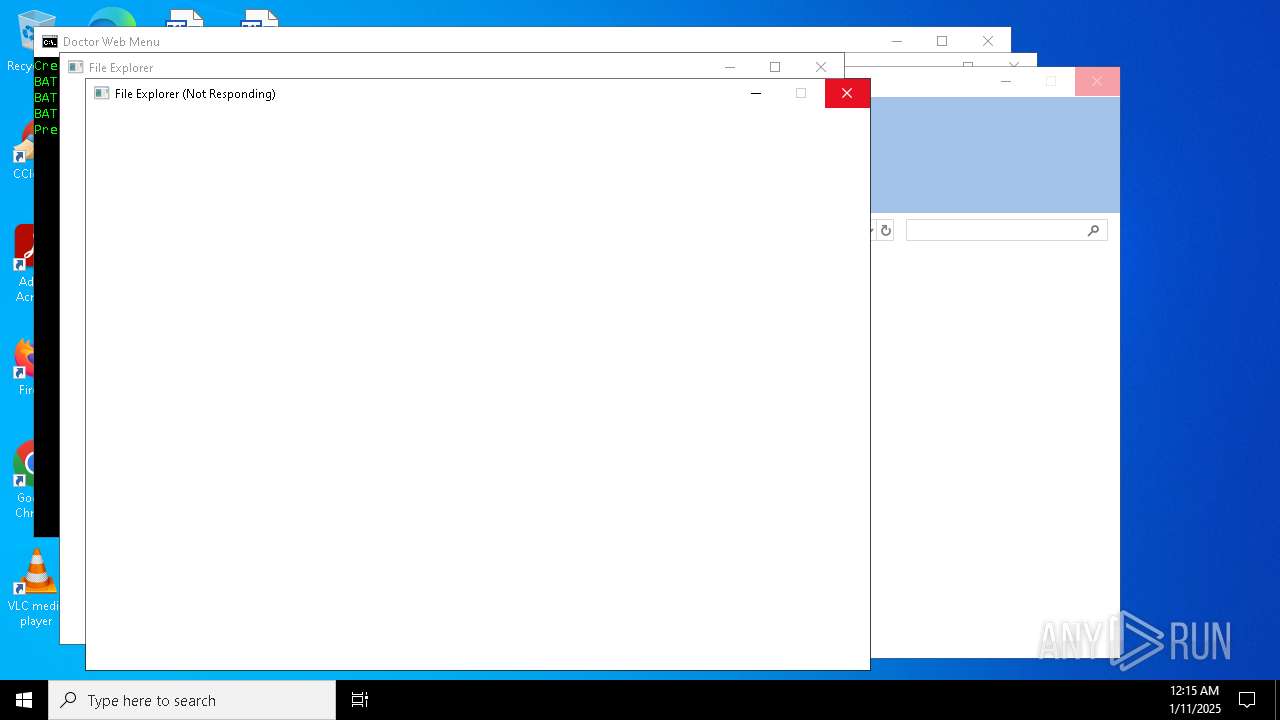
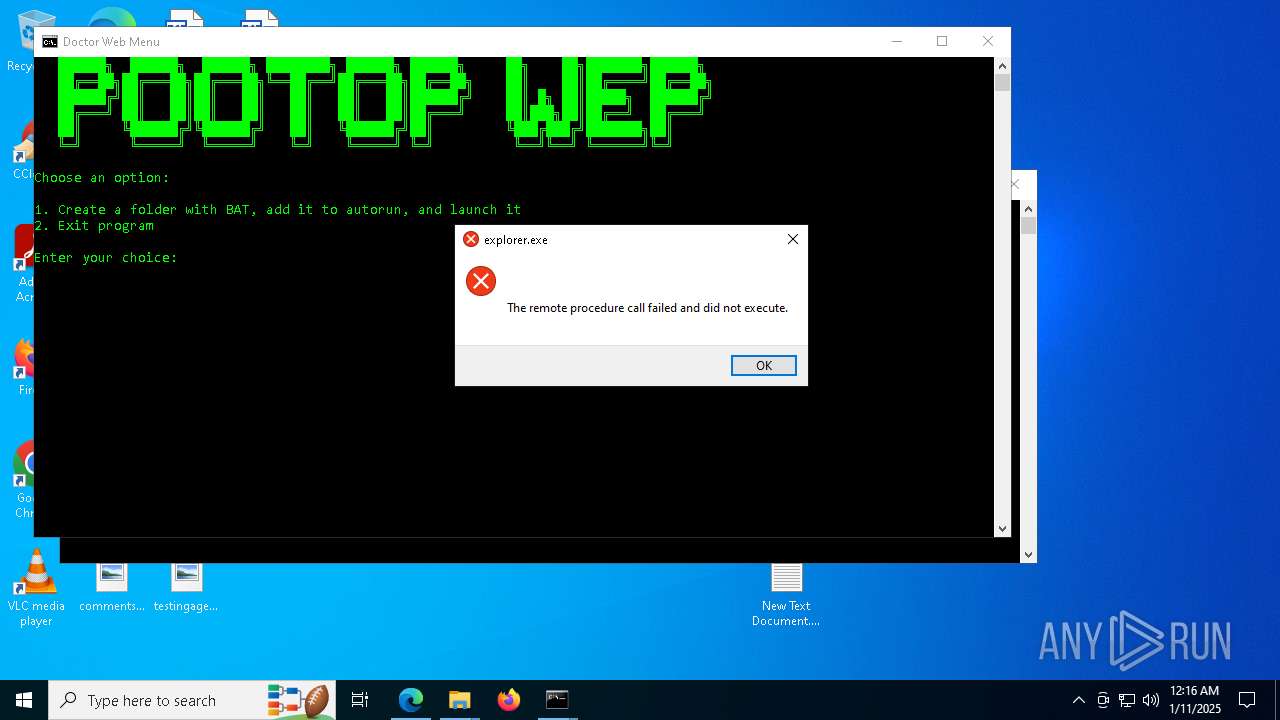
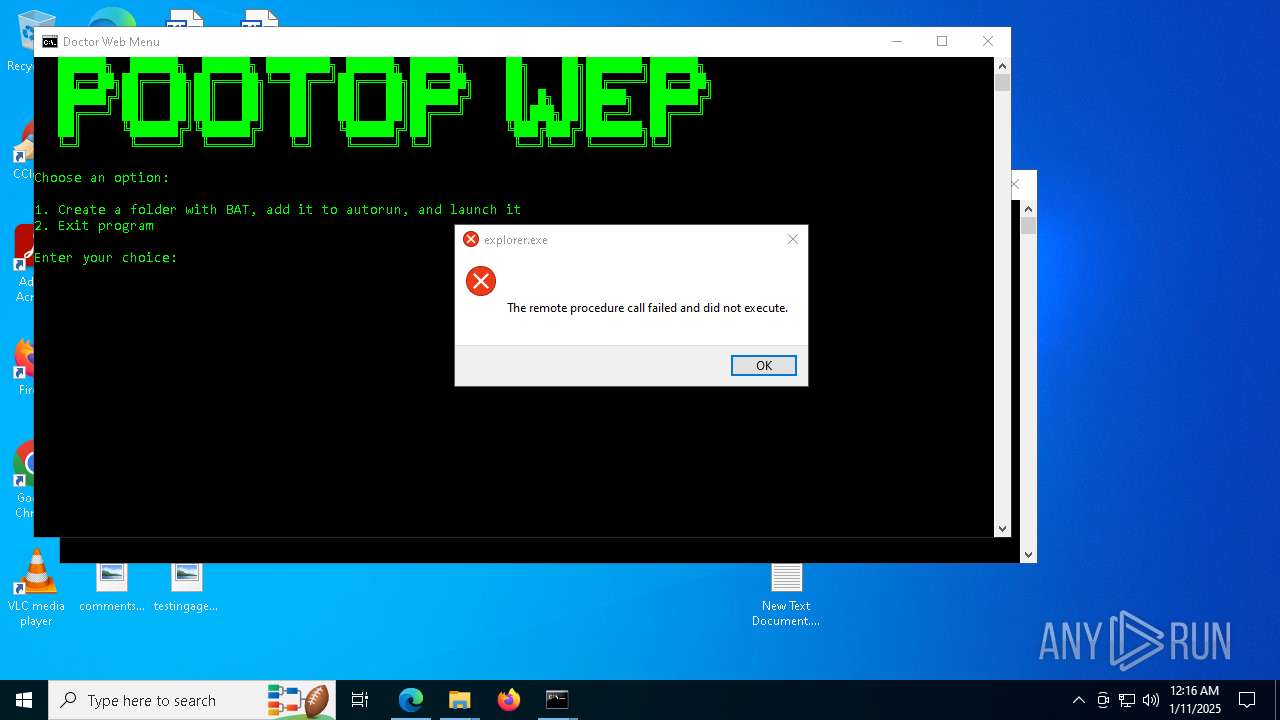
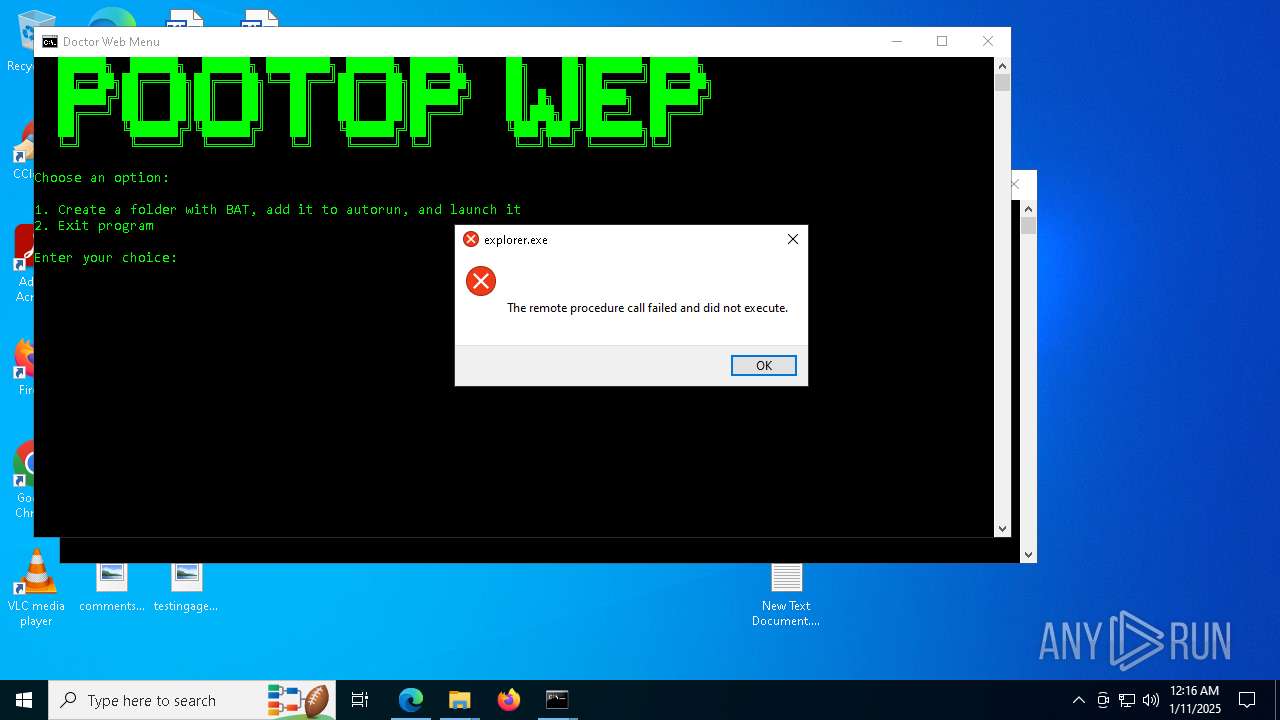
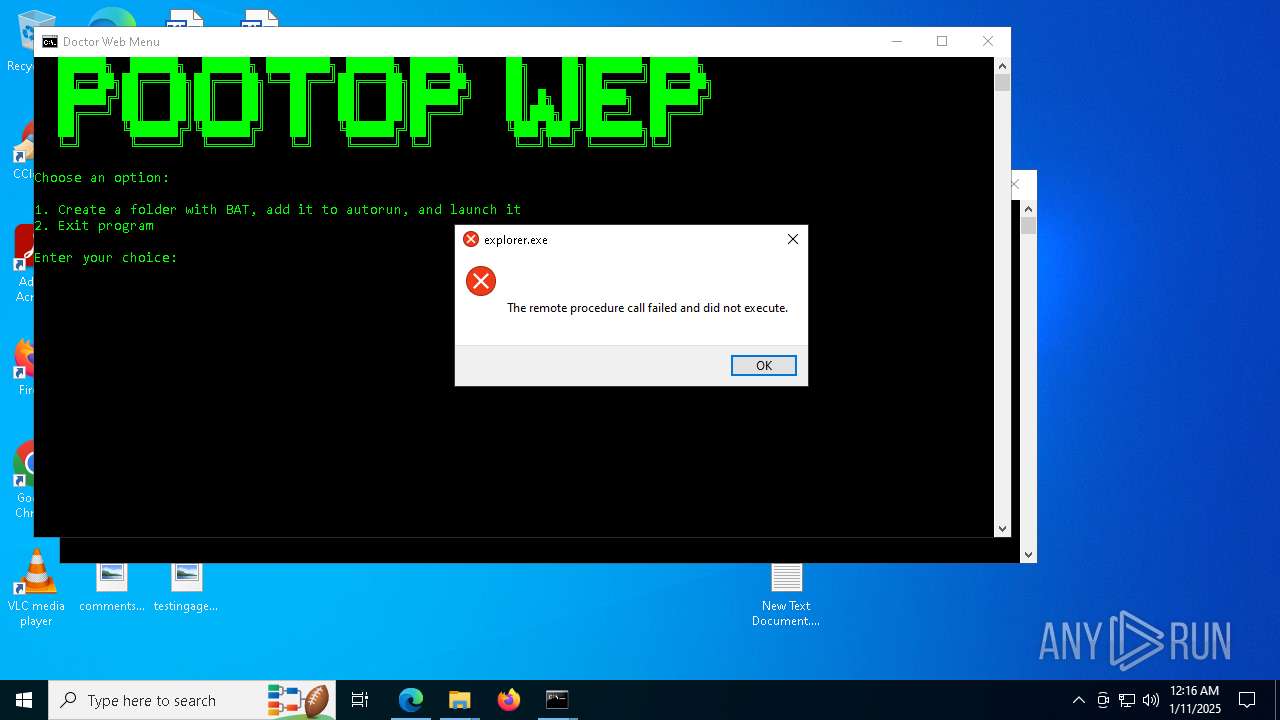
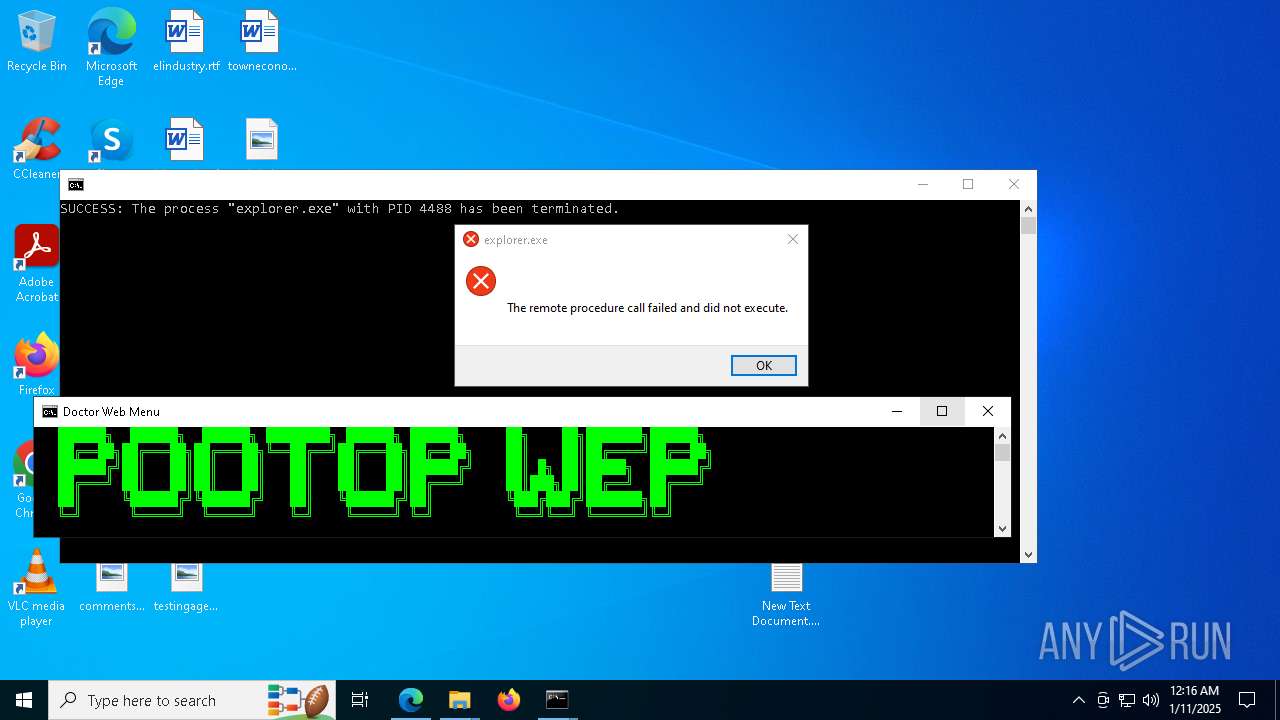
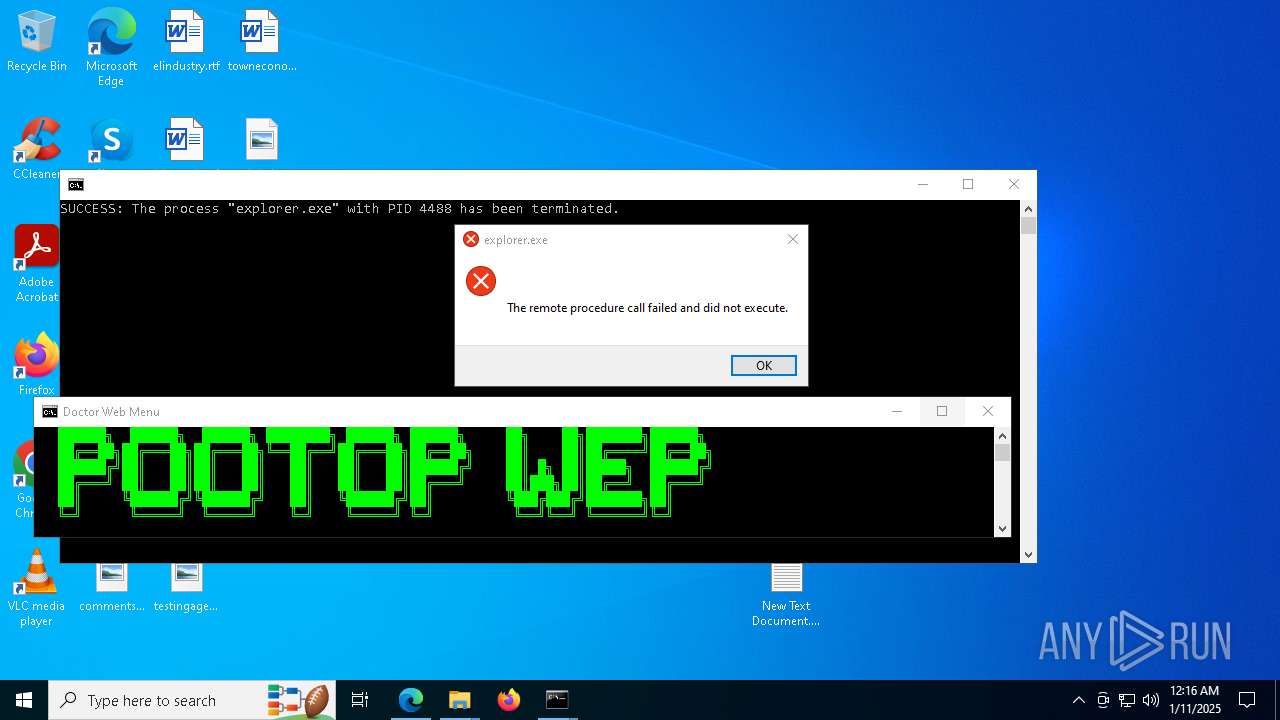
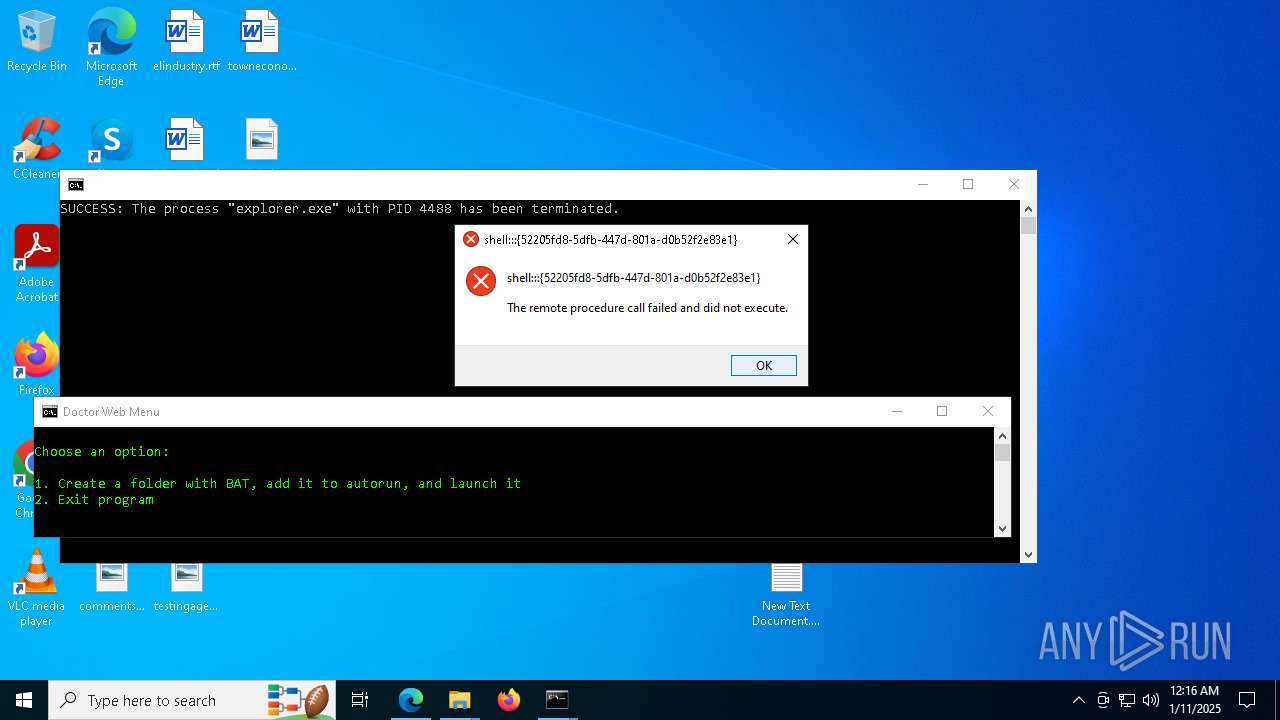
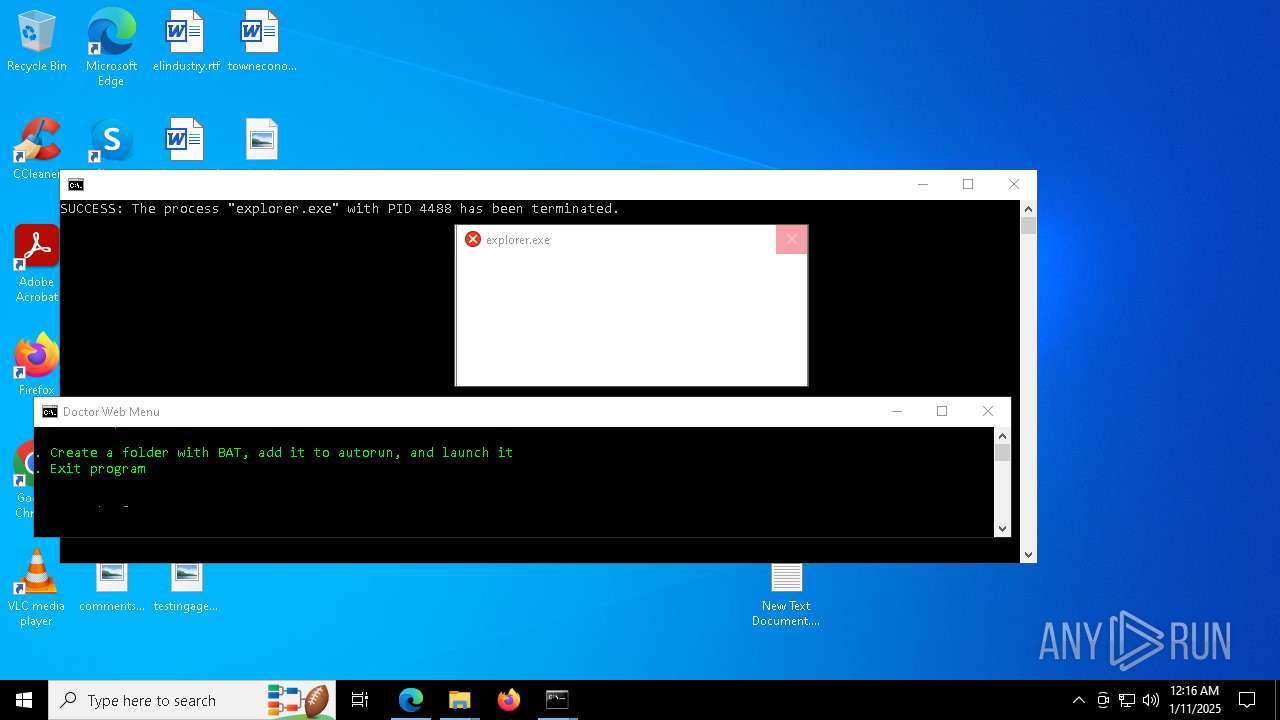
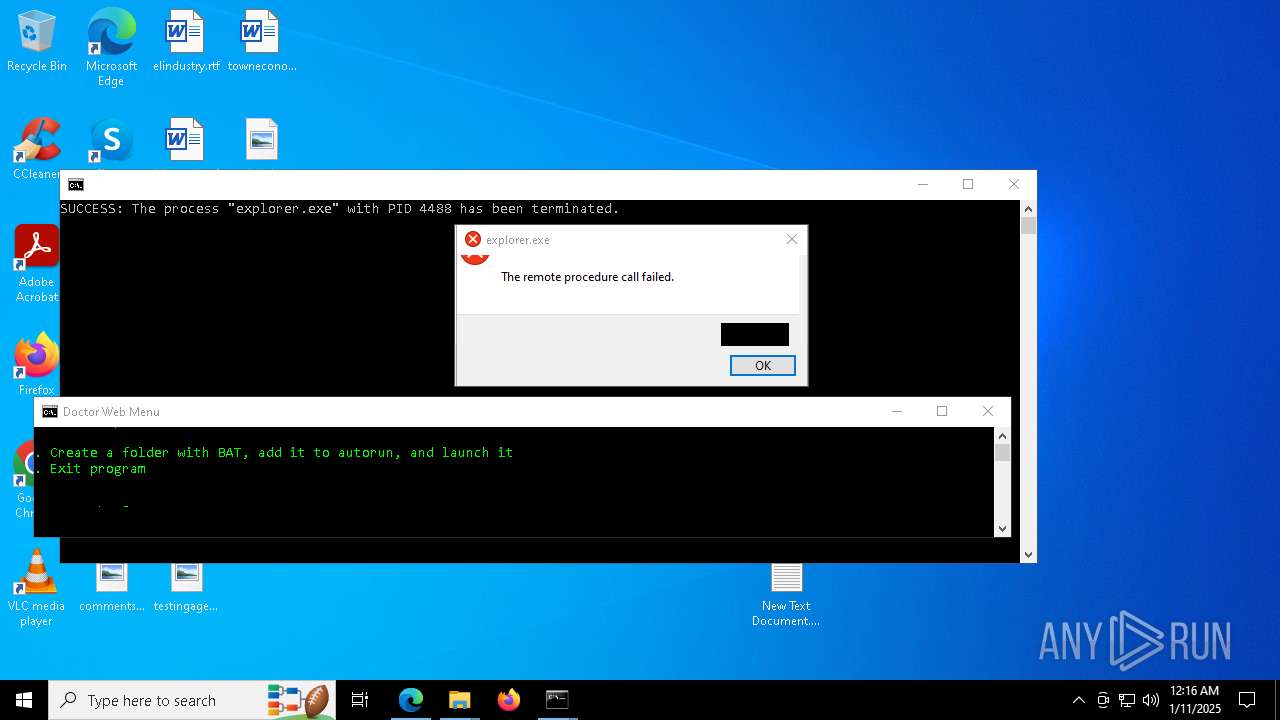
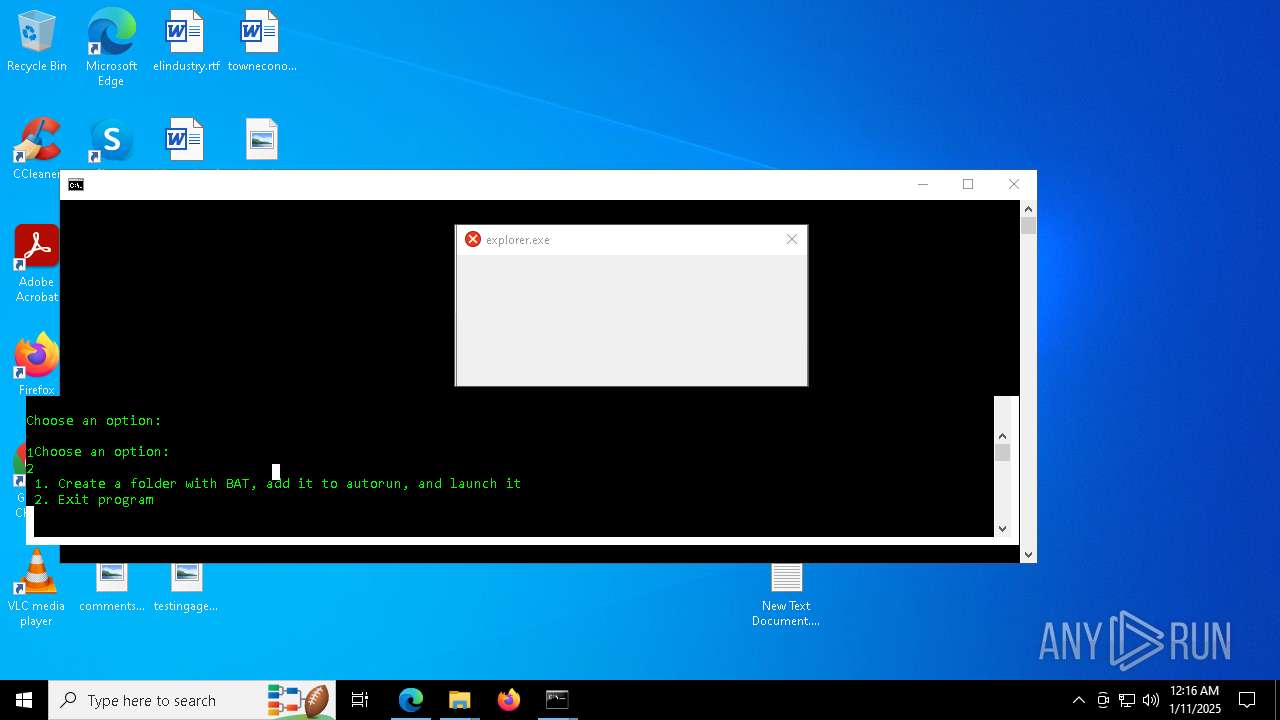
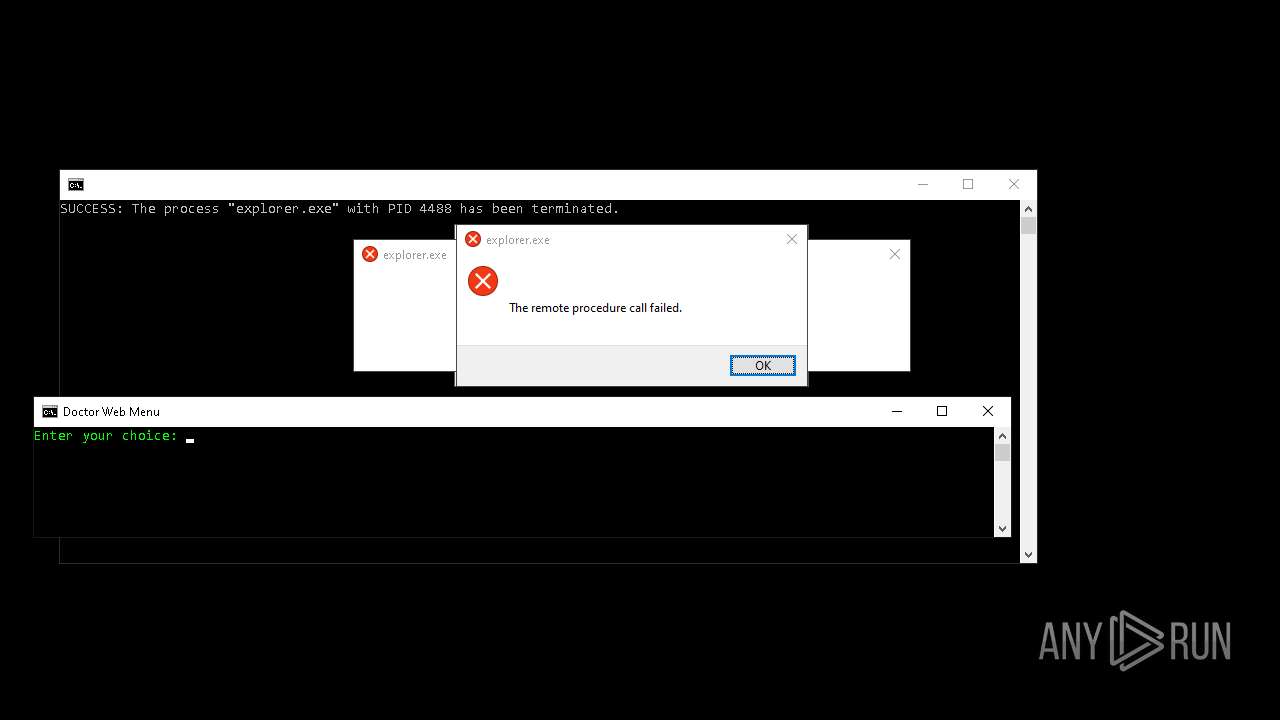
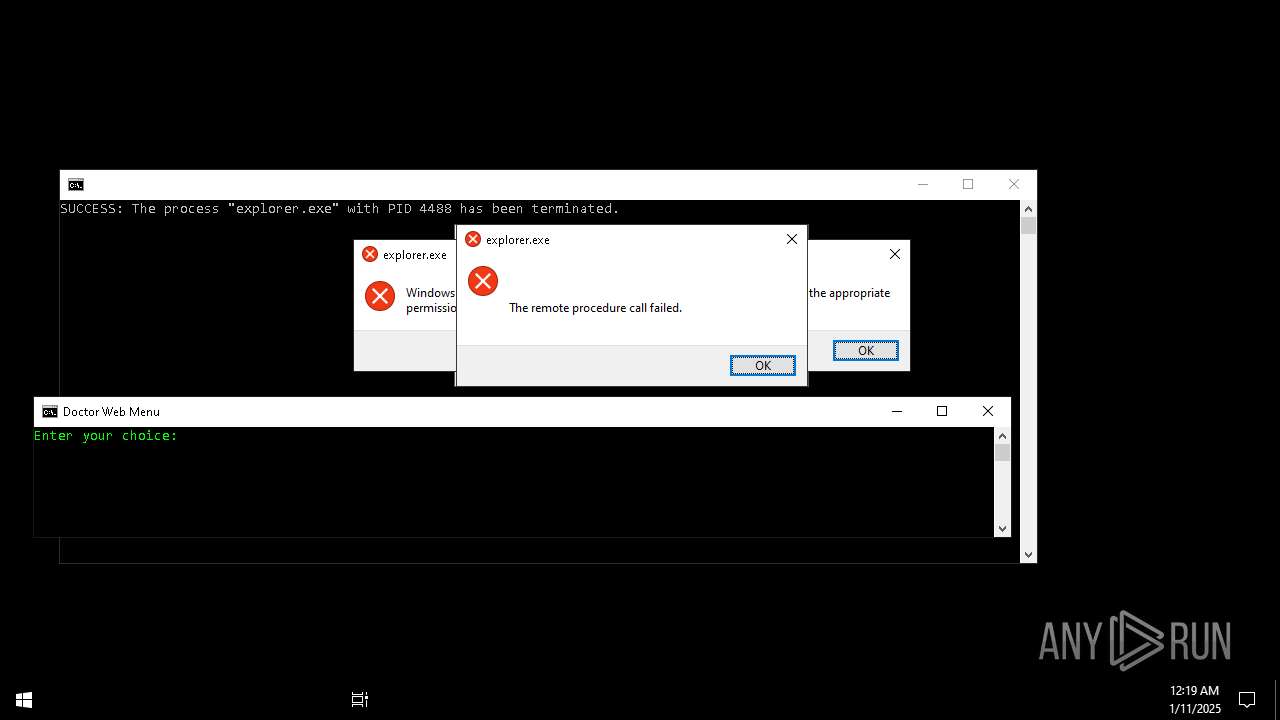
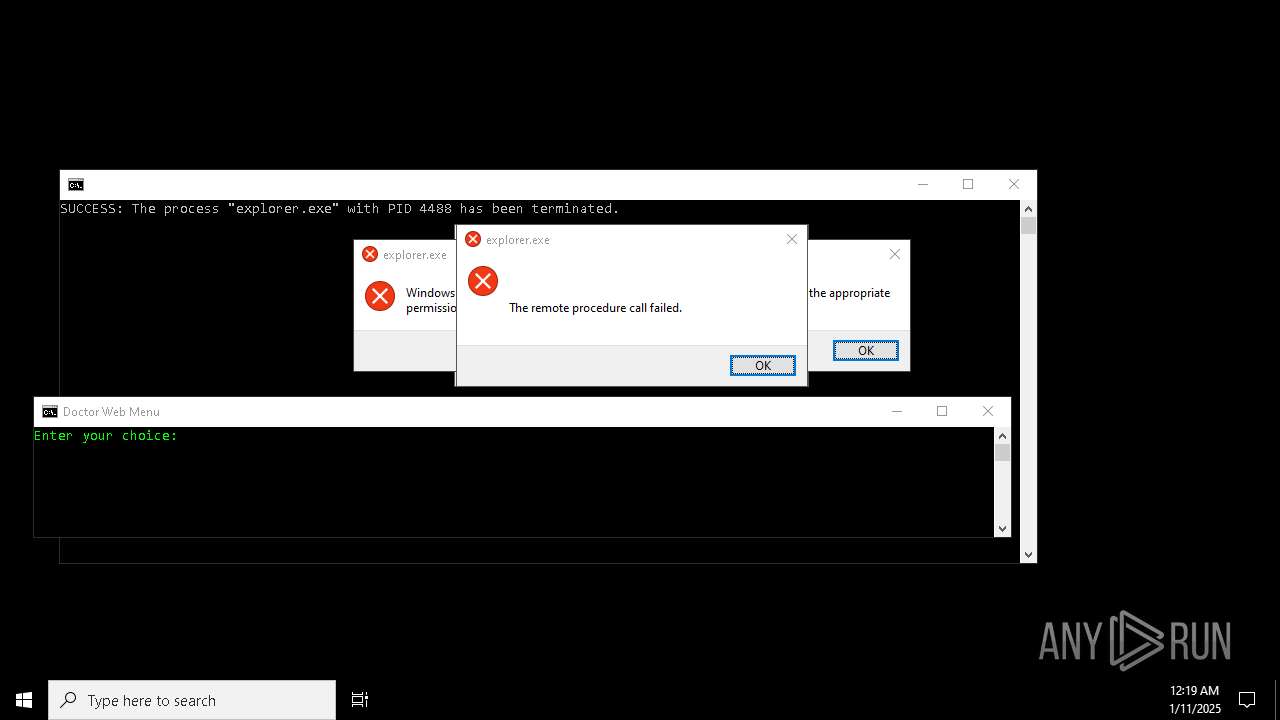
Executes application which crashes
- explorer.exe (PID: 7968)
- explorer.exe (PID: 20284)
- explorer.exe (PID: 19936)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 15912)
INFO
Reads the computer name
- identity_helper.exe (PID: 7908)
- StartMenuExperienceHost.exe (PID: 15912)
- TextInputHost.exe (PID: 19460)
Application launched itself
- msedge.exe (PID: 6428)
Reads Environment values
- identity_helper.exe (PID: 7908)
Checks supported languages
- identity_helper.exe (PID: 7908)
- chcp.com (PID: 7632)
- TextInputHost.exe (PID: 19460)
- SearchApp.exe (PID: 4156)
- StartMenuExperienceHost.exe (PID: 15912)
Reads security settings of Internet Explorer
- notepad.exe (PID: 624)
- explorer.exe (PID: 7968)
- explorer.exe (PID: 19936)
- explorer.exe (PID: 20284)
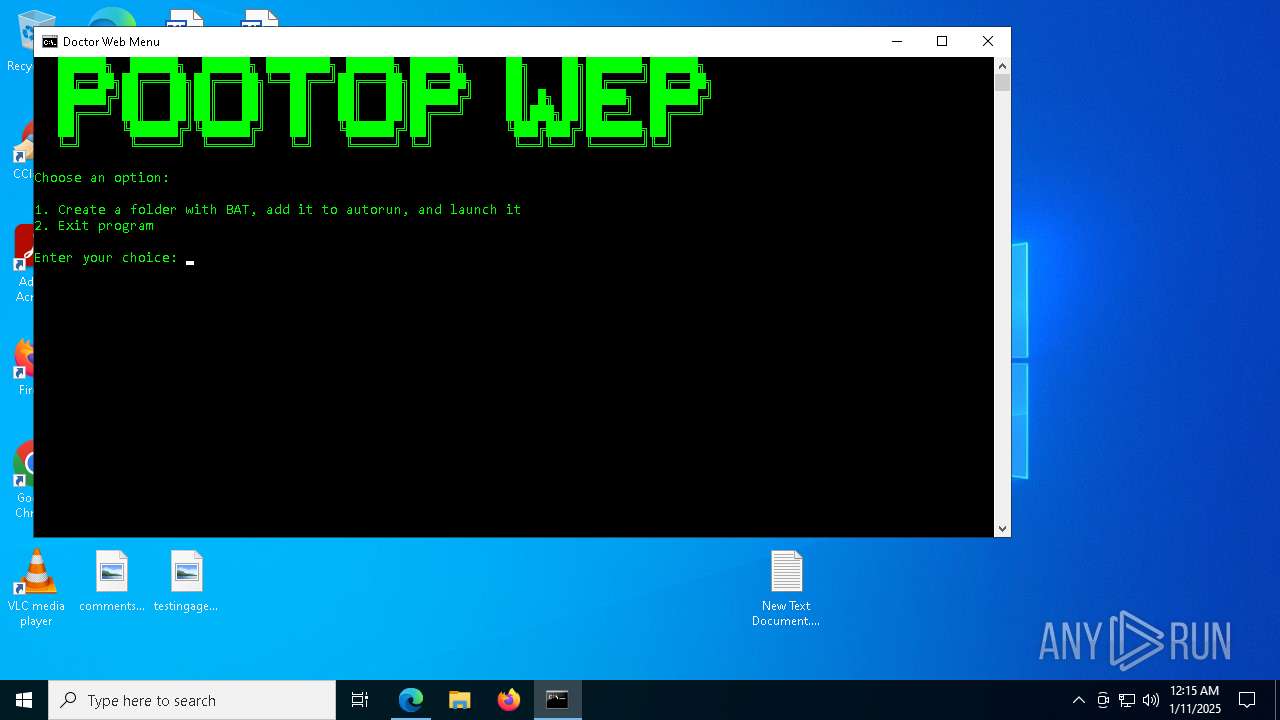
Manual execution by a user
- notepad.exe (PID: 624)
- cmd.exe (PID: 7668)
Changes the display of characters in the console
- cmd.exe (PID: 7668)
Creates files or folders in the user directory
- explorer.exe (PID: 7048)
- explorer.exe (PID: 2828)
- explorer.exe (PID: 7408)
- explorer.exe (PID: 8016)
- explorer.exe (PID: 2076)
- explorer.exe (PID: 7176)
- explorer.exe (PID: 5576)
- explorer.exe (PID: 1296)
- explorer.exe (PID: 5560)
- explorer.exe (PID: 4716)
- explorer.exe (PID: 2612)
- explorer.exe (PID: 8032)
- explorer.exe (PID: 1140)
- explorer.exe (PID: 8180)
- explorer.exe (PID: 904)
- explorer.exe (PID: 7564)
- explorer.exe (PID: 3984)
- explorer.exe (PID: 7720)
- explorer.exe (PID: 8148)
- explorer.exe (PID: 6392)
- explorer.exe (PID: 5604)
- explorer.exe (PID: 5096)
- explorer.exe (PID: 8012)
- explorer.exe (PID: 1572)
- explorer.exe (PID: 7712)
- explorer.exe (PID: 6732)
- explorer.exe (PID: 4592)
- explorer.exe (PID: 8960)
- explorer.exe (PID: 5392)
- explorer.exe (PID: 5388)
- explorer.exe (PID: 8872)
- explorer.exe (PID: 8892)
- explorer.exe (PID: 8468)
- explorer.exe (PID: 9020)
- explorer.exe (PID: 3832)
- explorer.exe (PID: 5076)
- explorer.exe (PID: 8048)
- explorer.exe (PID: 7968)
- explorer.exe (PID: 7308)
- explorer.exe (PID: 16012)
- explorer.exe (PID: 12440)
- explorer.exe (PID: 15556)
- explorer.exe (PID: 19936)
- explorer.exe (PID: 7280)
- explorer.exe (PID: 21720)
- explorer.exe (PID: 4640)
- explorer.exe (PID: 8684)
- explorer.exe (PID: 21652)
- explorer.exe (PID: 18880)
- explorer.exe (PID: 20004)
- explorer.exe (PID: 23600)
- explorer.exe (PID: 20588)
Attempting to use file storage service
- msedge.exe (PID: 6648)
Process checks computer location settings
- SearchApp.exe (PID: 4156)
Creates files in the program directory
- explorer.exe (PID: 7968)
- explorer.exe (PID: 20284)
Checks proxy server information
- explorer.exe (PID: 19936)
- WerFault.exe (PID: 12316)
Reads the software policy settings
- SearchApp.exe (PID: 4156)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 4156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
2 603
Monitored processes
2 459
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 580 815
Read events
1 577 017
Write events
3 764
Delete events
34
Modification events
| (PID) Process: | (3608) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3608) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3608) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3608) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3608) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3608) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
4
Suspicious files
356
Text files
194
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135883.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135883.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1358d1.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1358f1.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1358f1.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
126
DNS requests
106
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6300 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5236 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5236 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
20228 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1736912842&P2=404&P3=2&P4=W3EE4fM48I2fslJOceza5qr2OJHry5xYapZLDghSElbLWz4cOWzKCvgA5sRSM12Qq%2bZmBpJWr1PVbWyhNPJs2Q%3d%3d | unknown | — | — | whitelisted |
20228 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1736912842&P2=404&P3=2&P4=W3EE4fM48I2fslJOceza5qr2OJHry5xYapZLDghSElbLWz4cOWzKCvgA5sRSM12Qq%2bZmBpJWr1PVbWyhNPJs2Q%3d%3d | unknown | — | — | whitelisted |
12316 | WerFault.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2736 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6648 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
docs.google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6648 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a Documents sharing service is observed |
6648 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a Documents sharing service is observed |