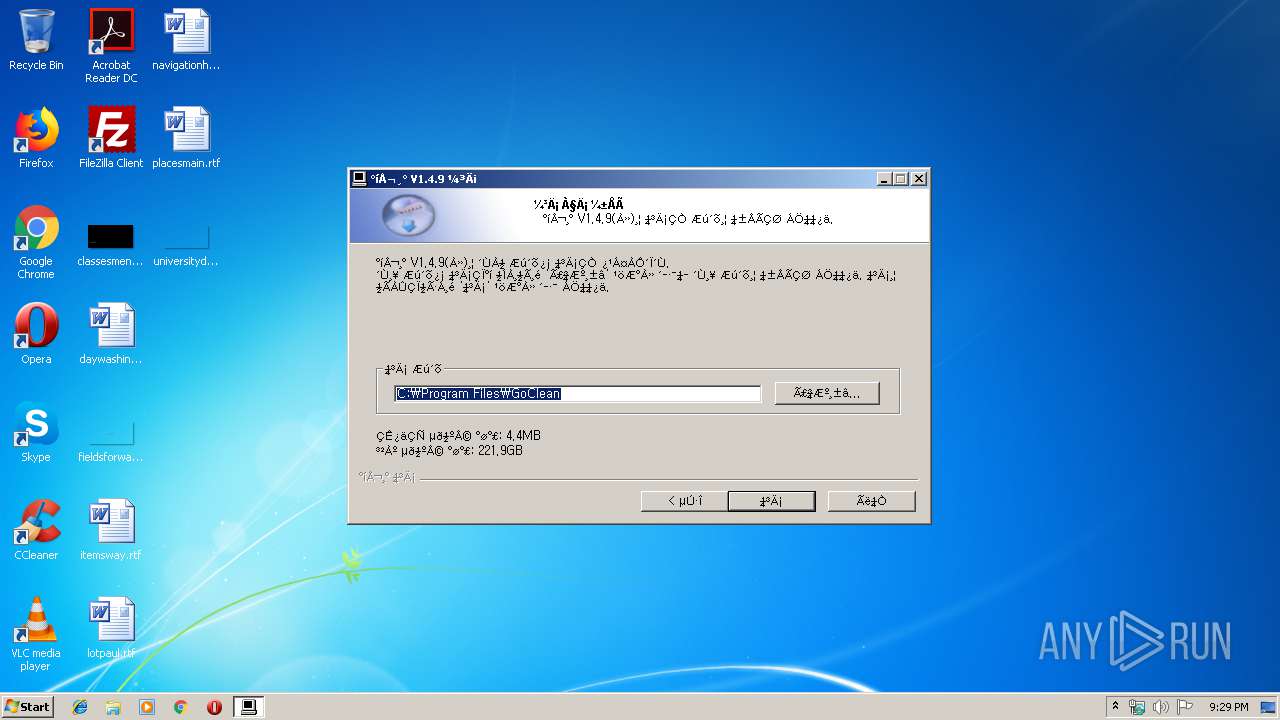
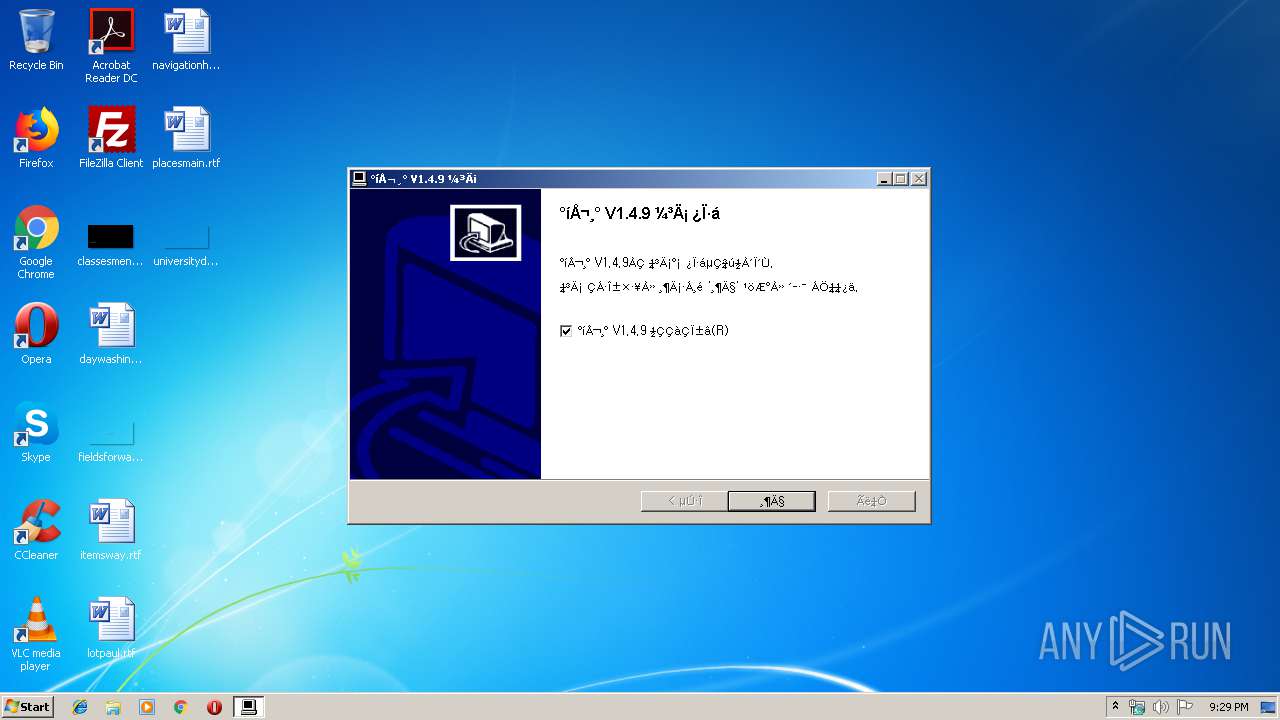
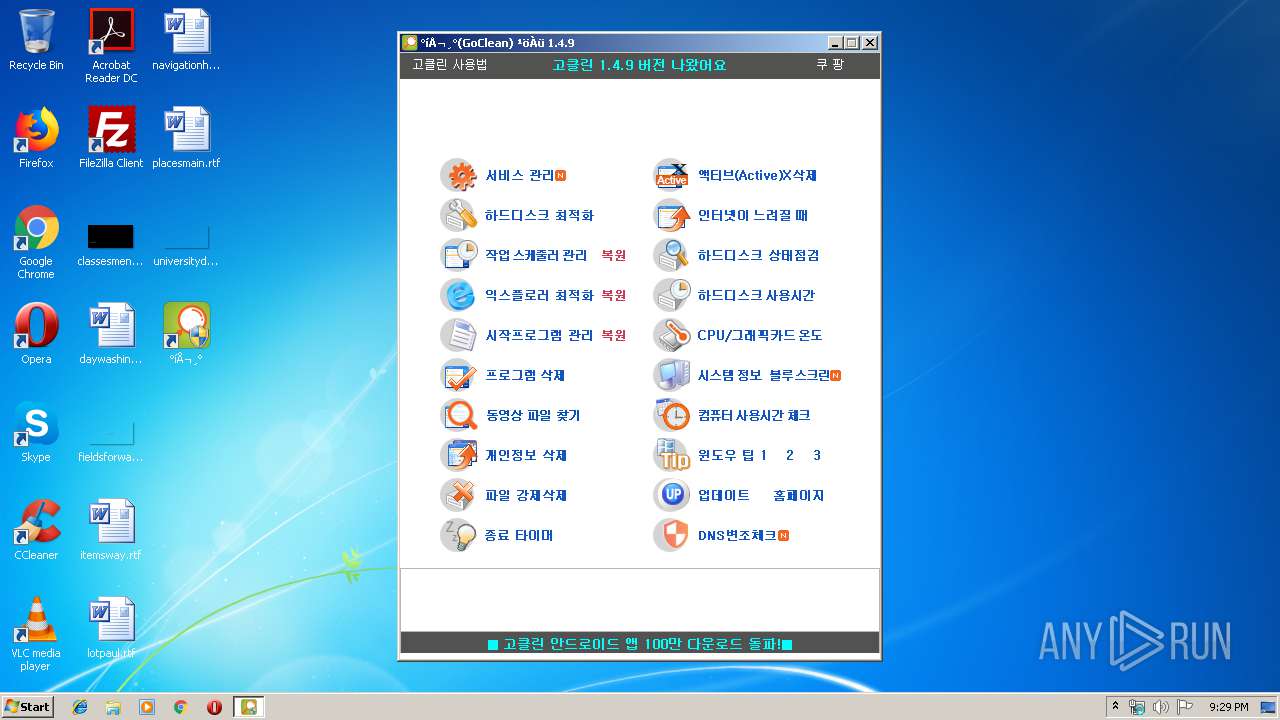
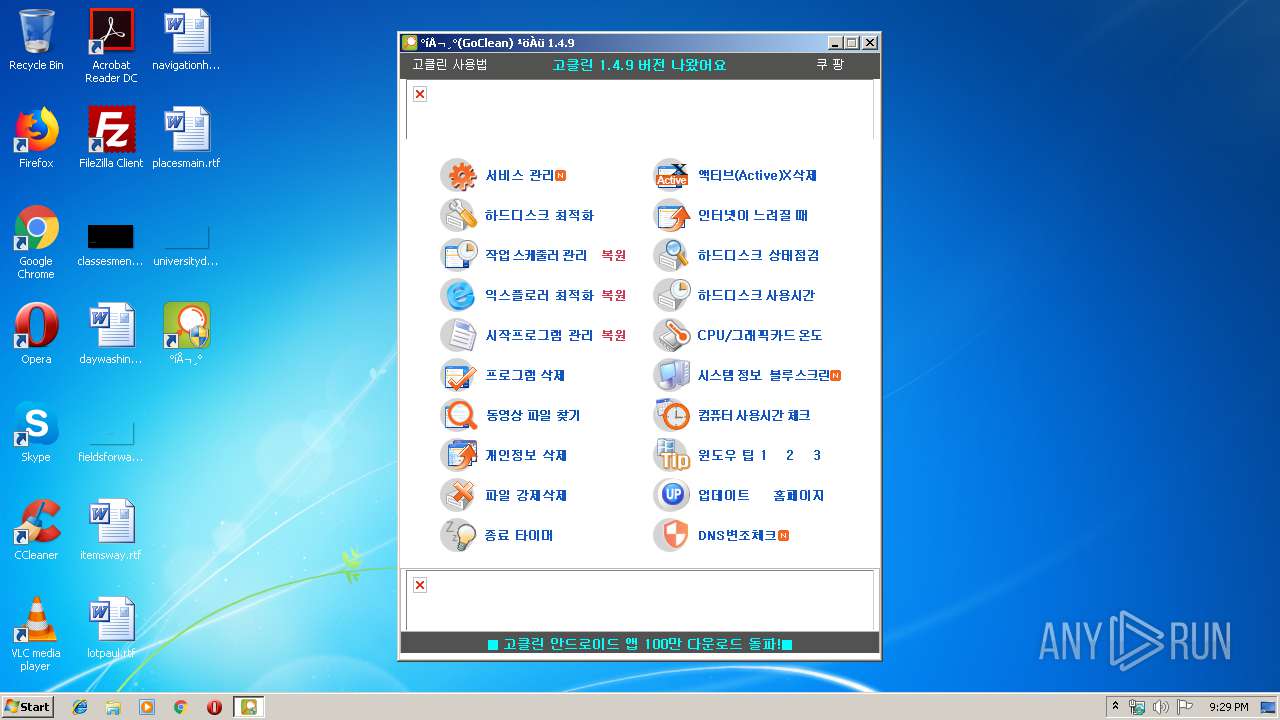
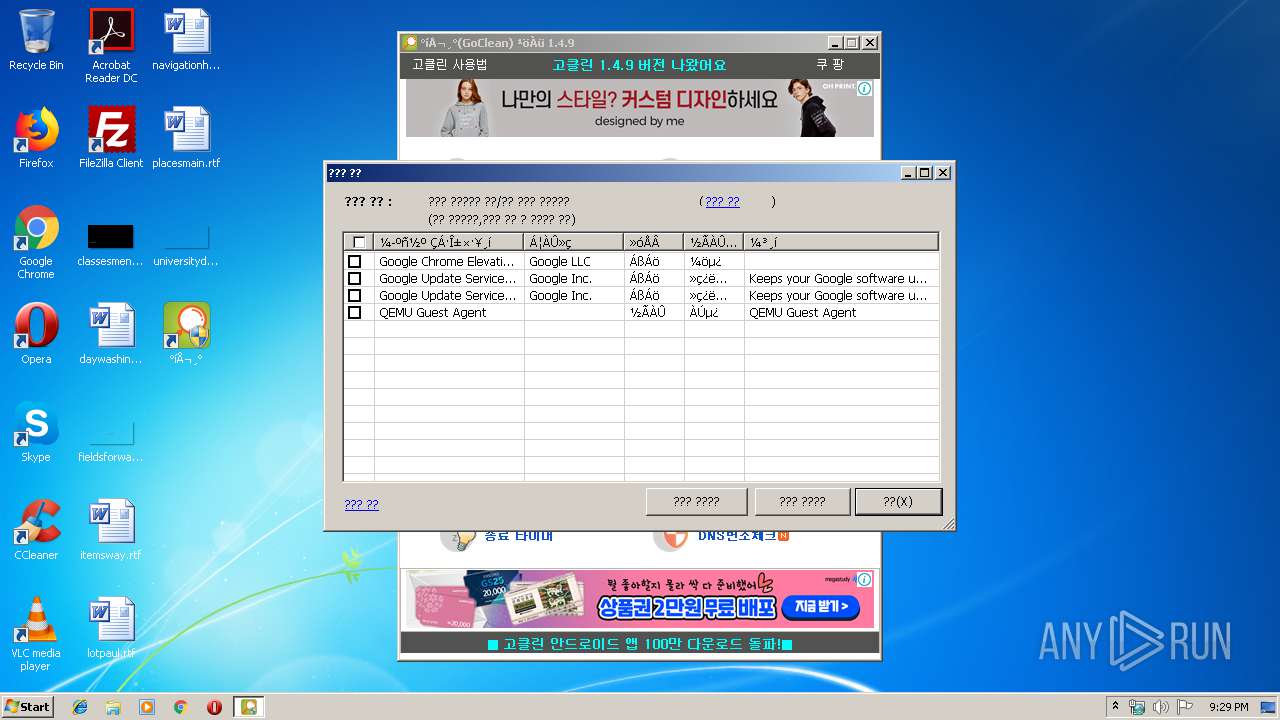
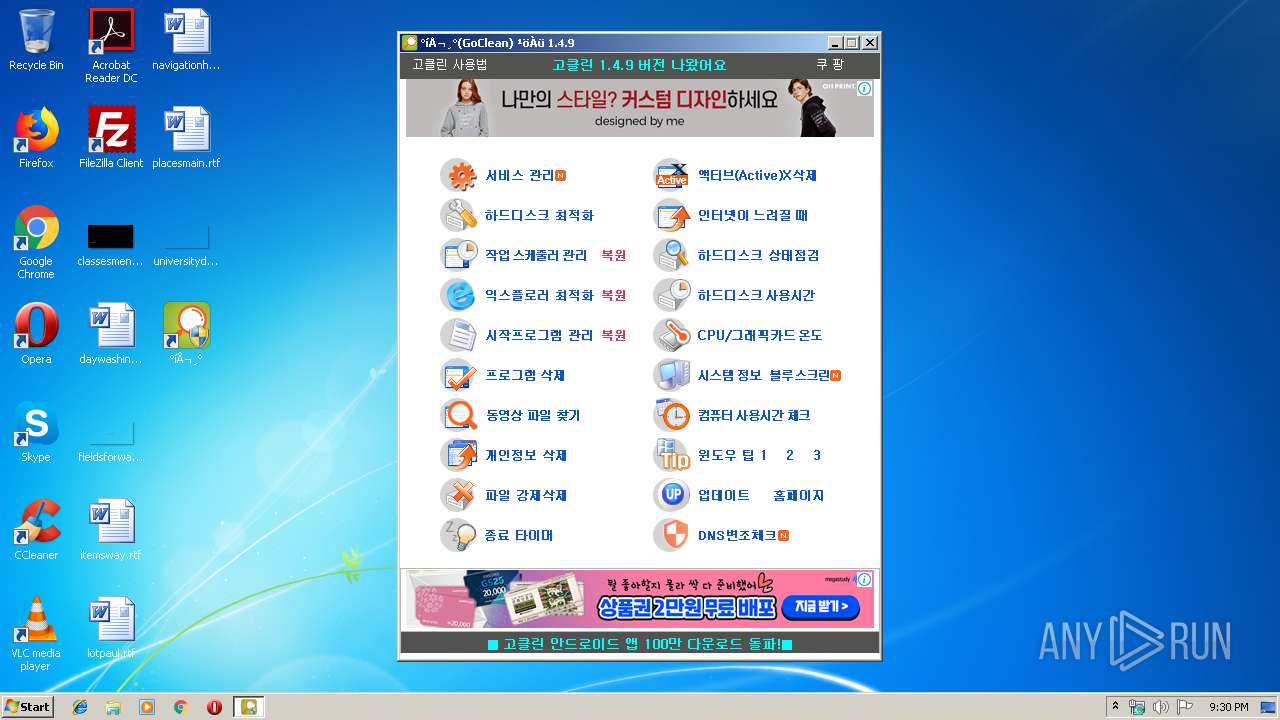
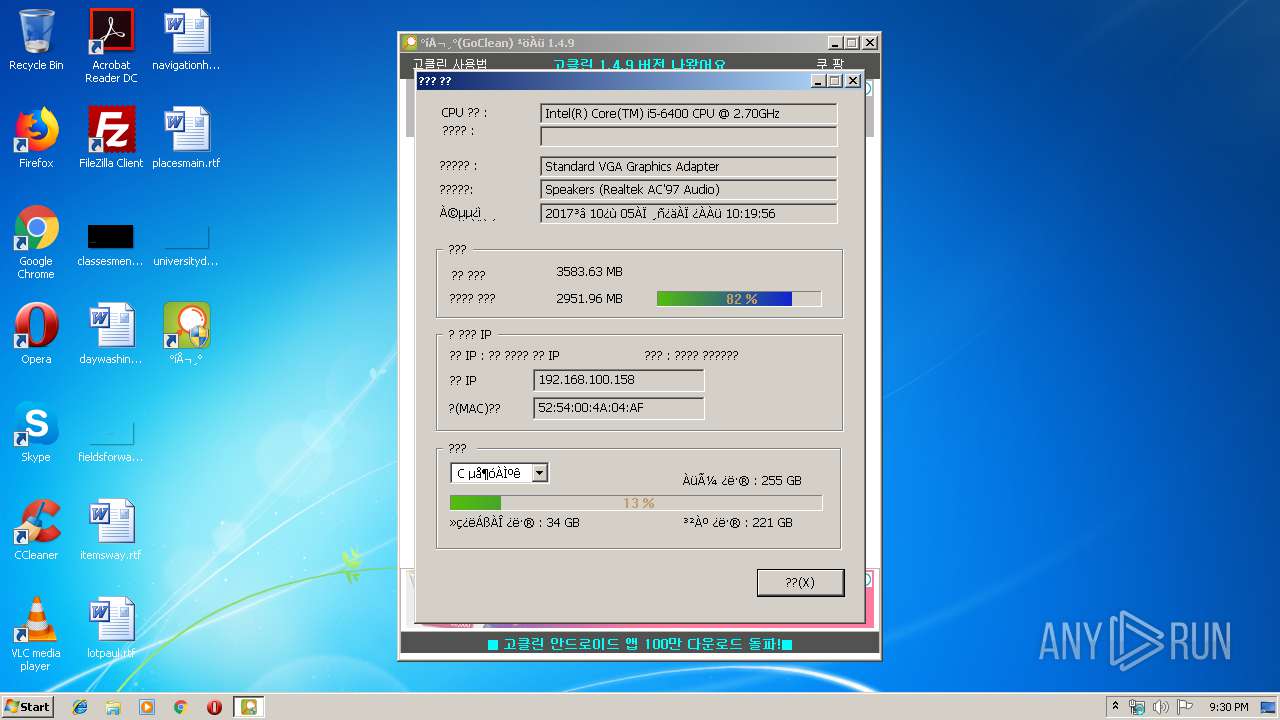
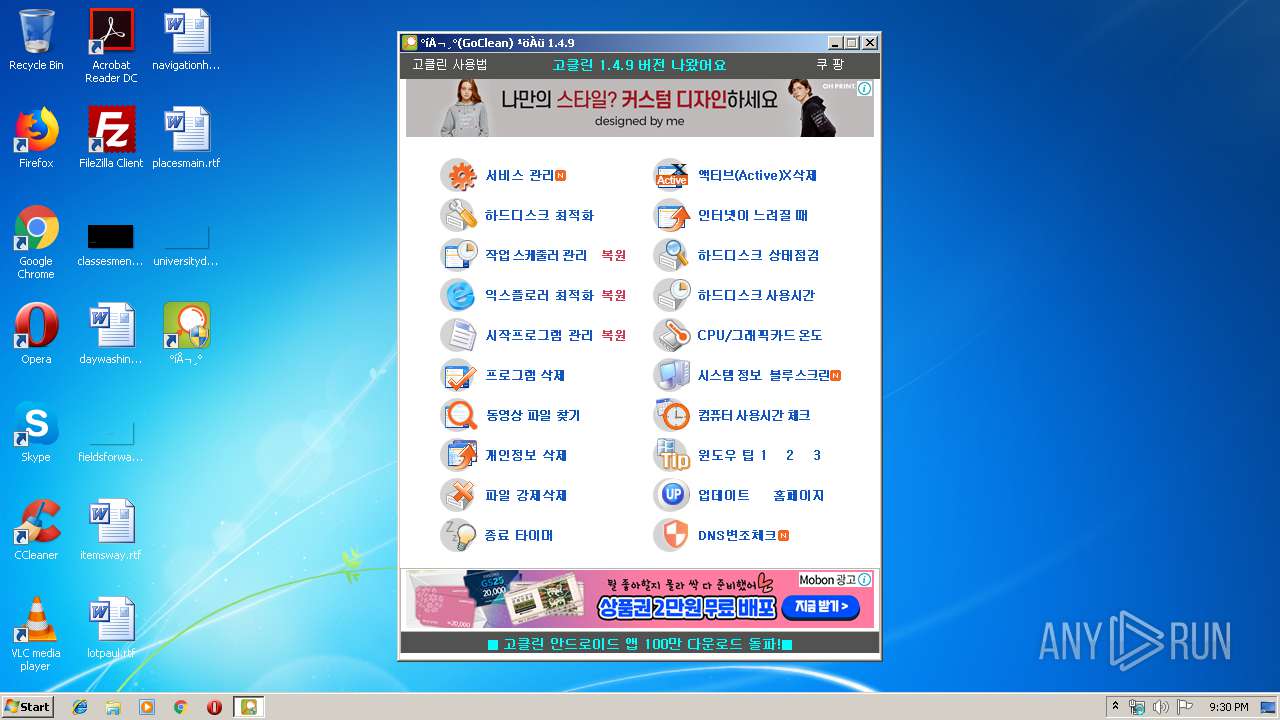
| File name: | gocleansetup149 (1).exe |
| Full analysis: | https://app.any.run/tasks/f53742c4-e04a-4ccd-99e0-cf542f4b4878 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 21:29:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 77B0DD7C7D3F67CA1EFD98AE8C19DA7A |
| SHA1: | D0F7D8227571E5FC9B9F63079245A526A25E3683 |
| SHA256: | D51676BFDFE801EB5900555F7C960437976A1181F2DA0E3C912605EF5E9180AA |
| SSDEEP: | 24576:8vd3Etzxrv+zECG5QG//uxFcgl+1amyXr+XeQwFMGGZ/kGo/rQ3c+dmfABJQWGAR:I0jv3L//33oKXMMG6kZsVmfAJJKf8 |
MALICIOUS
Loads dropped or rewritten executable
- gocleansetup149 (1).exe (PID: 3956)
- GoClean.EXE (PID: 332)
Application was dropped or rewritten from another process
- GoClean.EXE (PID: 332)
Loads the Task Scheduler COM API
- GoClean.EXE (PID: 332)
SUSPICIOUS
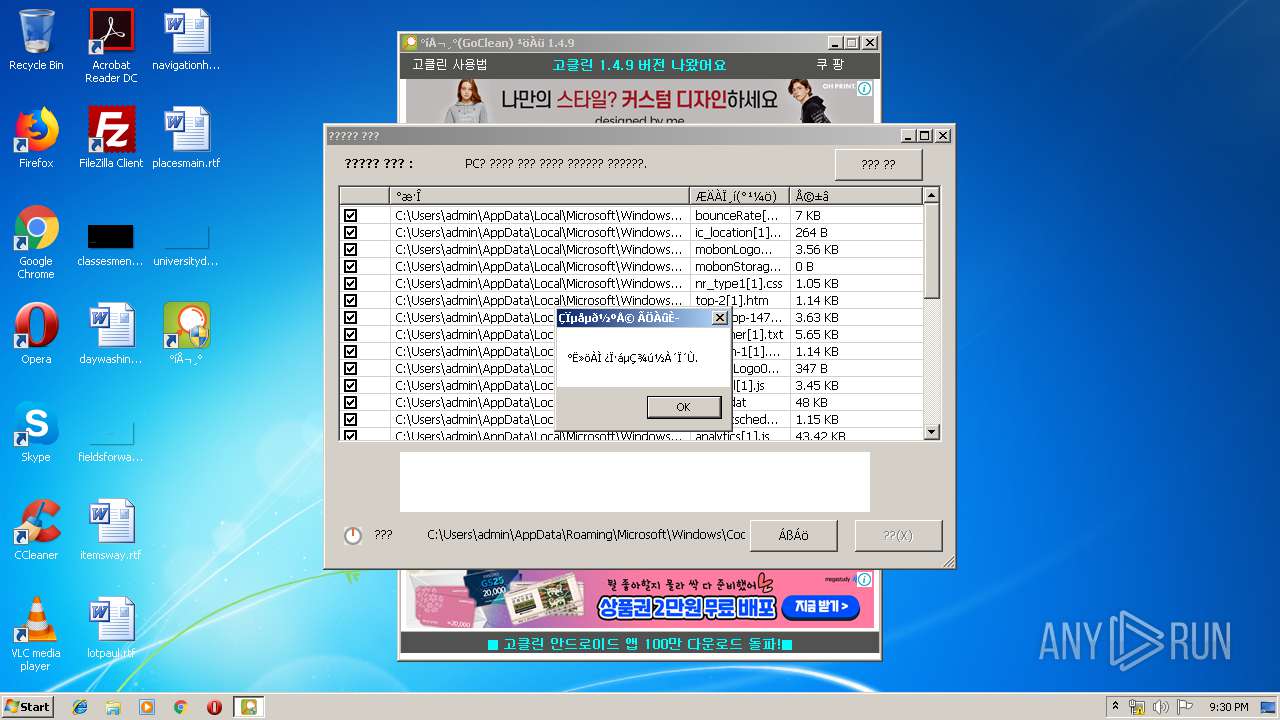
Creates files in the user directory
- GoClean.EXE (PID: 332)
Reads internet explorer settings
- GoClean.EXE (PID: 332)
Creates files in the program directory
- gocleansetup149 (1).exe (PID: 3956)
Executable content was dropped or overwritten
- gocleansetup149 (1).exe (PID: 3956)
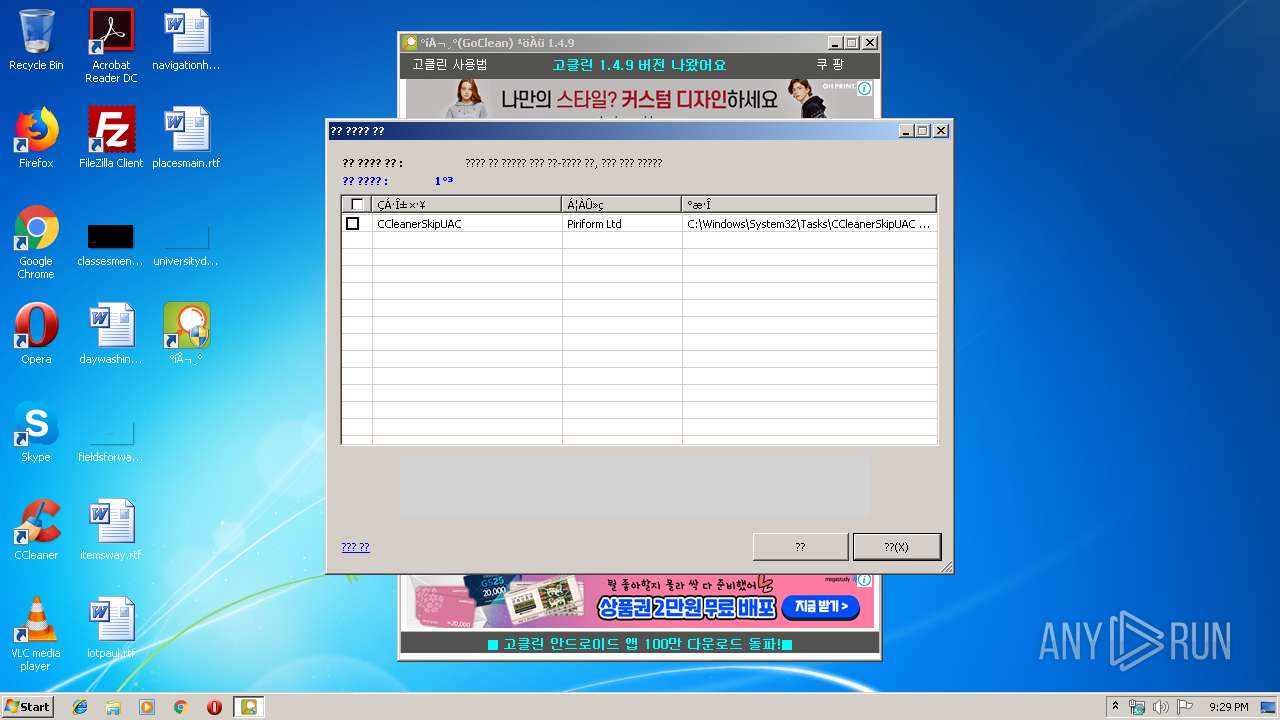
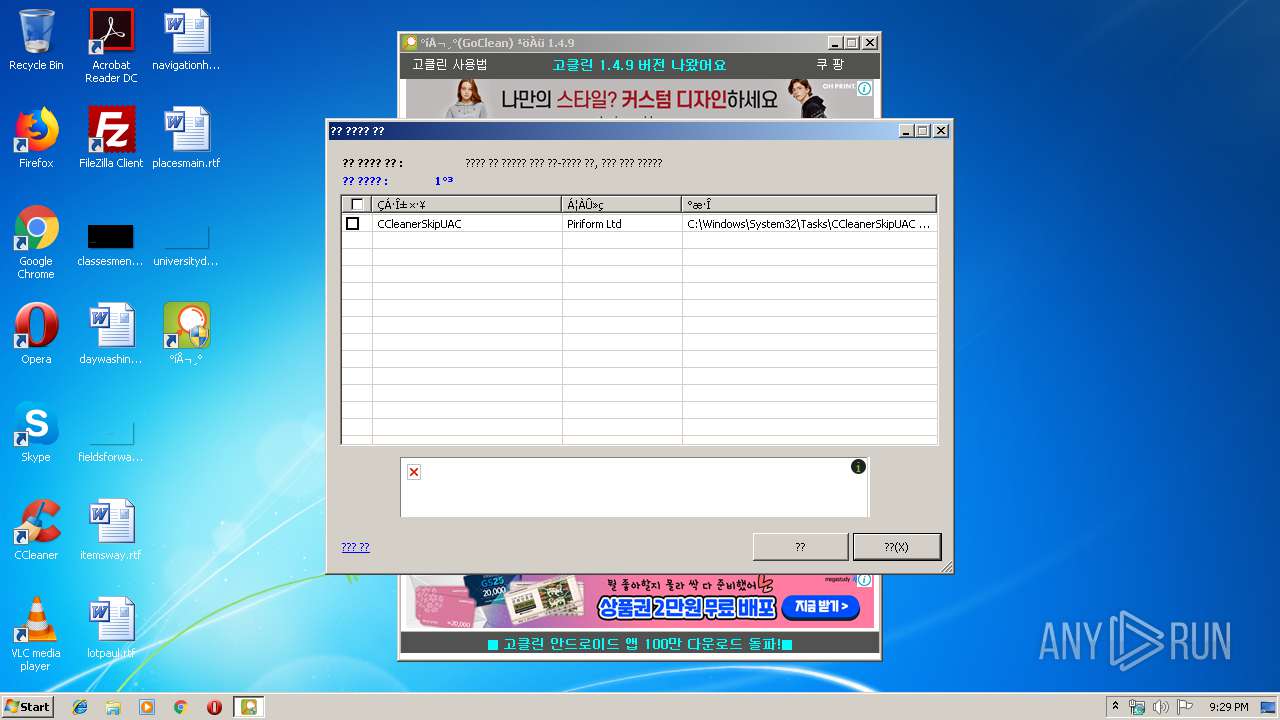
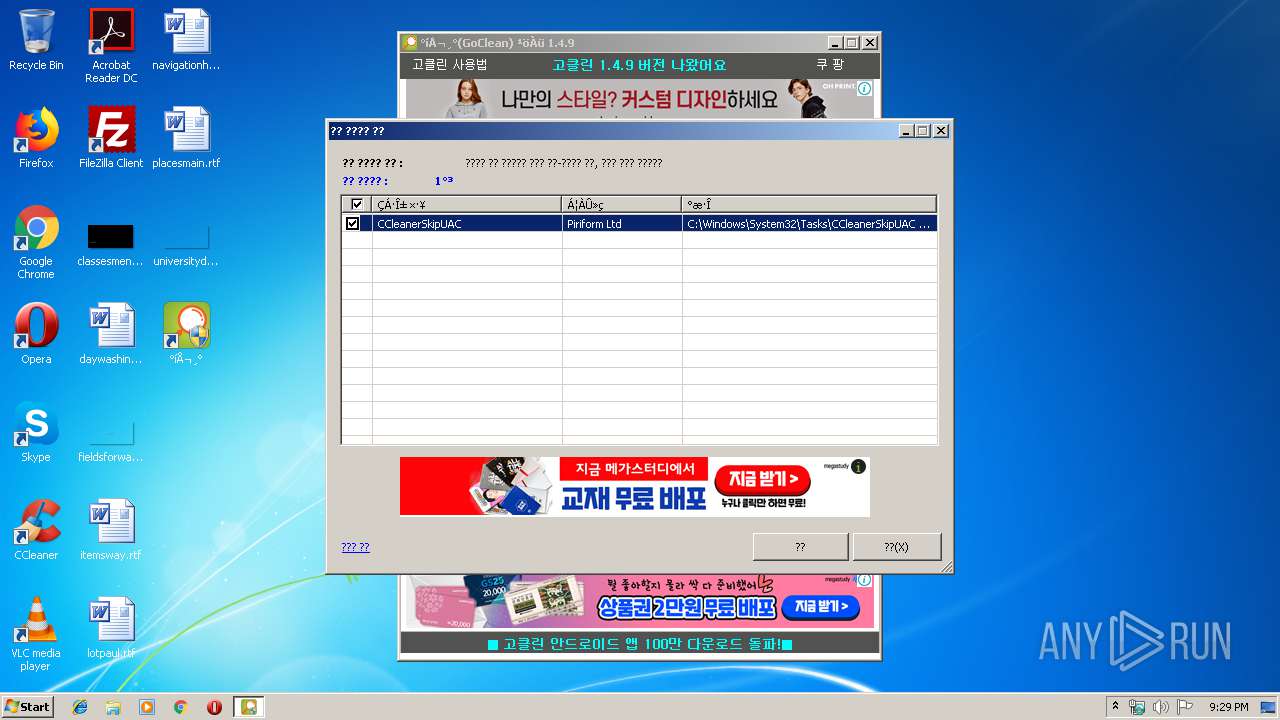
Creates a software uninstall entry
- gocleansetup149 (1).exe (PID: 3956)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:12:11 22:50:23+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24576 |
| InitializedDataSize: | 3782656 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3180 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Korean |
| CharacterSet: | Windows, Korea (Shift - KSC 5601) |
| Comments: | 고클린 설치 파일 (2019-03-07 오후 5:49:25) |
| CompanyName: | 고클린 |
| FileDescription: | 고클린 설치 파일 |
| FileVersion: | V1.4.9 |
| LegalCopyright: | 저작권(C) 2007 고클린 |
| ProductName: | 고클린 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Dec-2016 21:50:23 |
| Detected languages: |
|
| Comments: | 고클린 설치 파일 (2019-03-07 오후 5:49:25) |
| CompanyName: | 고클린 |
| FileDescription: | 고클린 설치 파일 |
| FileVersion: | V1.4.9 |
| LegalCopyright: | 저작권(C) 2007 고클린 |
| ProductName: | 고클린 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-Dec-2016 21:50:23 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005E4A | 0x00006000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.46167 |
.rdata | 0x00007000 | 0x00001246 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.00503 |
.data | 0x00009000 | 0x00399038 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.11743 |
.ndata | 0x003A3000 | 0x00009000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x003AC000 | 0x00001B38 | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.1682 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28813 | 1070 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.76386 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 1.97134 | 34 | UNKNOWN | English - United States | RT_GROUP_ICON |
104 | 2.60821 | 260 | UNKNOWN | English - United States | RT_DIALOG |
105 | 2.61 | 492 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.86295 | 228 | UNKNOWN | English - United States | RT_DIALOG |
107 | 2.4032 | 140 | UNKNOWN | English - United States | RT_DIALOG |
109 | 2.6232 | 192 | UNKNOWN | English - United States | RT_DIALOG |
110 | 2.82633 | 1638 | UNKNOWN | English - United States | RT_BITMAP |
111 | 2.92694 | 218 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
40
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "C:\Program Files\GoClean\GoClean.EXE" | C:\Program Files\GoClean\GoClean.EXE | gocleansetup149 (1).exe | ||||||||||||
User: admin Company: 고클린 Integrity Level: HIGH Description: 고클린 Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1912 | "C:\Users\admin\AppData\Local\Temp\gocleansetup149 (1).exe" | C:\Users\admin\AppData\Local\Temp\gocleansetup149 (1).exe | — | explorer.exe | |||||||||||
User: admin Company: 고클린 Integrity Level: MEDIUM Description: 고클린 설치 파일 Exit code: 3221226540 Version: V1.4.9 Modules
| |||||||||||||||
| 3956 | "C:\Users\admin\AppData\Local\Temp\gocleansetup149 (1).exe" | C:\Users\admin\AppData\Local\Temp\gocleansetup149 (1).exe | explorer.exe | ||||||||||||
User: admin Company: 고클린 Integrity Level: HIGH Description: 고클린 설치 파일 Exit code: 0 Version: V1.4.9 Modules
| |||||||||||||||
Total events
574
Read events
512
Write events
62
Delete events
0
Modification events
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_CURRENT_USER\Software\GoClean\GoClean |
| Operation: | write | Name: | ProgramFolder |
Value: C:\Program Files\GoClean | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_CURRENT_USER\Software\GoClean\GoClean |
| Operation: | write | Name: | ProgramPath |
Value: C:\Program Files\GoClean\GoClean.EXE | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GoClean\GoClean |
| Operation: | write | Name: | ProgramFolder |
Value: C:\Program Files\GoClean | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GoClean\GoClean |
| Operation: | write | Name: | ProgramPath |
Value: C:\Program Files\GoClean\GoClean.EXE | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\GoClean.EXE |
| Operation: | write | Name: | |
Value: "C:\Program Files\GoClean\GoClean.EXE" | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\GoClean.EXE |
| Operation: | write | Name: | Path |
Value: "C:\Program Files\GoClean\GoClean.EXE" | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GoClean |
| Operation: | write | Name: | DisplayName |
Value: °íŬ¸° | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GoClean |
| Operation: | write | Name: | DisplayVersion |
Value: 1.4.9 | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GoClean |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\GoClean\uninstall.exe" | |||
| (PID) Process: | (3956) gocleansetup149 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GoClean |
| Operation: | write | Name: | DisplayIcon |
Value: "C:\Program Files\GoClean\GoClean.EXE" | |||
Executable files
9
Suspicious files
0
Text files
84
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | gocleansetup149 (1).exe | C:\Users\admin\AppData\Local\Temp\nsaA043.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 332 | GoClean.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\115[1] | — | |
MD5:— | SHA256:— | |||
| 3956 | gocleansetup149 (1).exe | C:\Program Files\GoClean\GoCleanUp.exe | executable | |
MD5:— | SHA256:— | |||
| 3956 | gocleansetup149 (1).exe | C:\Program Files\GoClean\GoClean.exe | executable | |
MD5:— | SHA256:— | |||
| 3956 | gocleansetup149 (1).exe | C:\Program Files\GoClean\uninstall.exe | executable | |
MD5:— | SHA256:— | |||
| 3956 | gocleansetup149 (1).exe | C:\Program Files\GoClean\cpuidsdk.dll | executable | |
MD5:— | SHA256:— | |||
| 3956 | gocleansetup149 (1).exe | C:\Users\admin\AppData\Local\Temp\nsaA043.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 3956 | gocleansetup149 (1).exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\°íŬ¸°\°íŬ¸°.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3956 | gocleansetup149 (1).exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\°íŬ¸°\ÇÁ·Î±×·¥ Á¦°Å.lnk | lnk | |
MD5:— | SHA256:— | |||
| 332 | GoClean.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@gobest[2].txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
11
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
332 | GoClean.EXE | GET | 200 | 13.225.84.219:80 | http://www.gobest.kr/goclean/upversion2.dat | US | text | 438 b | whitelisted |
332 | GoClean.EXE | GET | — | 14.0.113.209:80 | http://img.mobon.net/newAd/img/logoImg/mobonLogo01.png | KR | — | — | suspicious |
332 | GoClean.EXE | GET | 200 | 13.225.84.219:80 | http://www.gobest.kr/adfile/top-2.htm | US | html | 1.15 Kb | whitelisted |
332 | GoClean.EXE | GET | 200 | 13.225.84.219:80 | http://www.gobest.kr/adfile/bottom-1.htm | US | html | 1.15 Kb | whitelisted |
332 | GoClean.EXE | GET | 200 | 14.0.113.209:80 | http://img.mobon.net/Frtb/common/css/mobon_reset.css?201706292 | KR | text | 9.72 Kb | suspicious |
332 | GoClean.EXE | GET | 200 | 13.225.84.219:80 | http://www.gobest.kr/adfile/ad-m-bottom-147.htm | US | html | 2.67 Kb | whitelisted |
332 | GoClean.EXE | GET | 200 | 13.225.84.219:80 | http://www.gobest.kr/adfile/ad-m-top-147.htm | US | html | 3.63 Kb | whitelisted |
332 | GoClean.EXE | GET | 200 | 14.0.113.209:80 | http://img.mobon.net/Frtb/js/frame_default_script_S.js | KR | text | 45.0 Kb | suspicious |
332 | GoClean.EXE | GET | 200 | 14.0.113.209:80 | http://img.mobon.net/js/bounceRate.js | KR | text | 7.01 Kb | suspicious |
332 | GoClean.EXE | GET | 200 | 14.0.113.209:80 | http://img.mobon.net/newAd/img/logoImg/mobonLogoiW01.png | KR | image | 2.23 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
332 | GoClean.EXE | 13.225.84.219:80 | www.gobest.kr | — | US | suspicious |
332 | GoClean.EXE | 172.217.18.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
332 | GoClean.EXE | 119.205.238.29:80 | www.mediacategory.com | Korea Telecom | KR | suspicious |
332 | GoClean.EXE | 14.0.113.209:80 | img.mobon.net | — | KR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gobest.kr |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.mediacategory.com |
| suspicious |
img.mobon.net |
| suspicious |