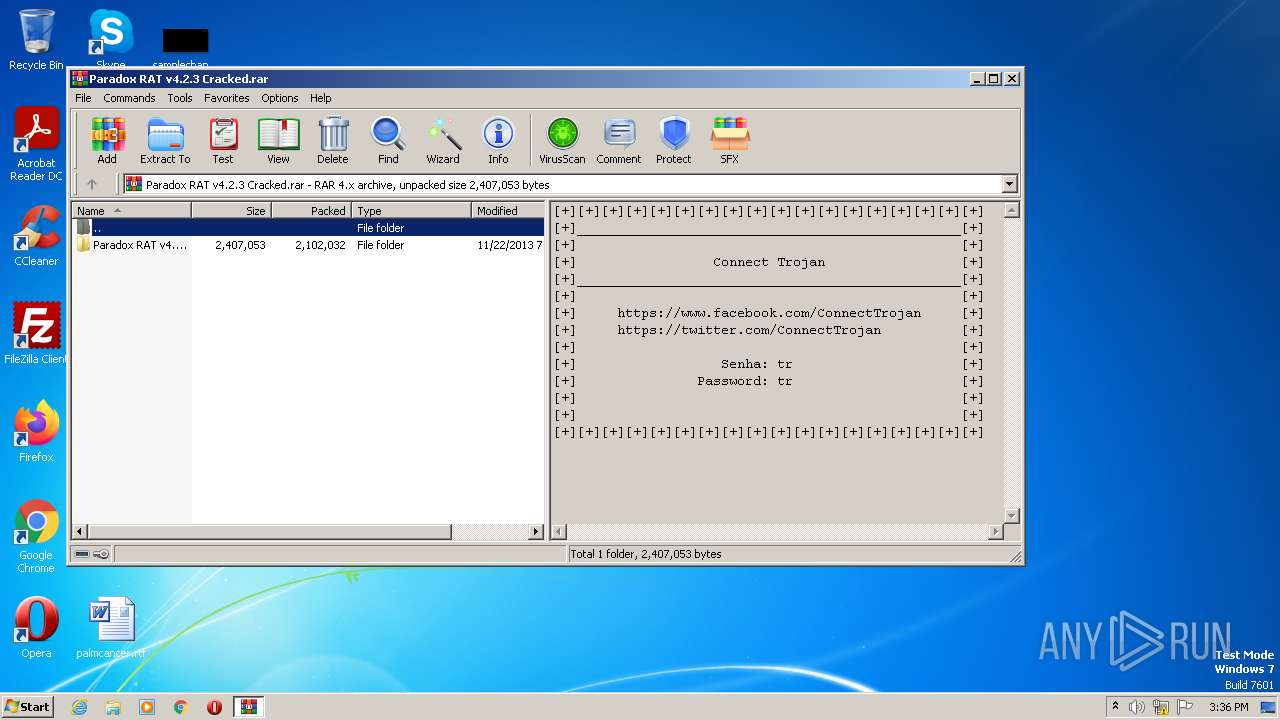
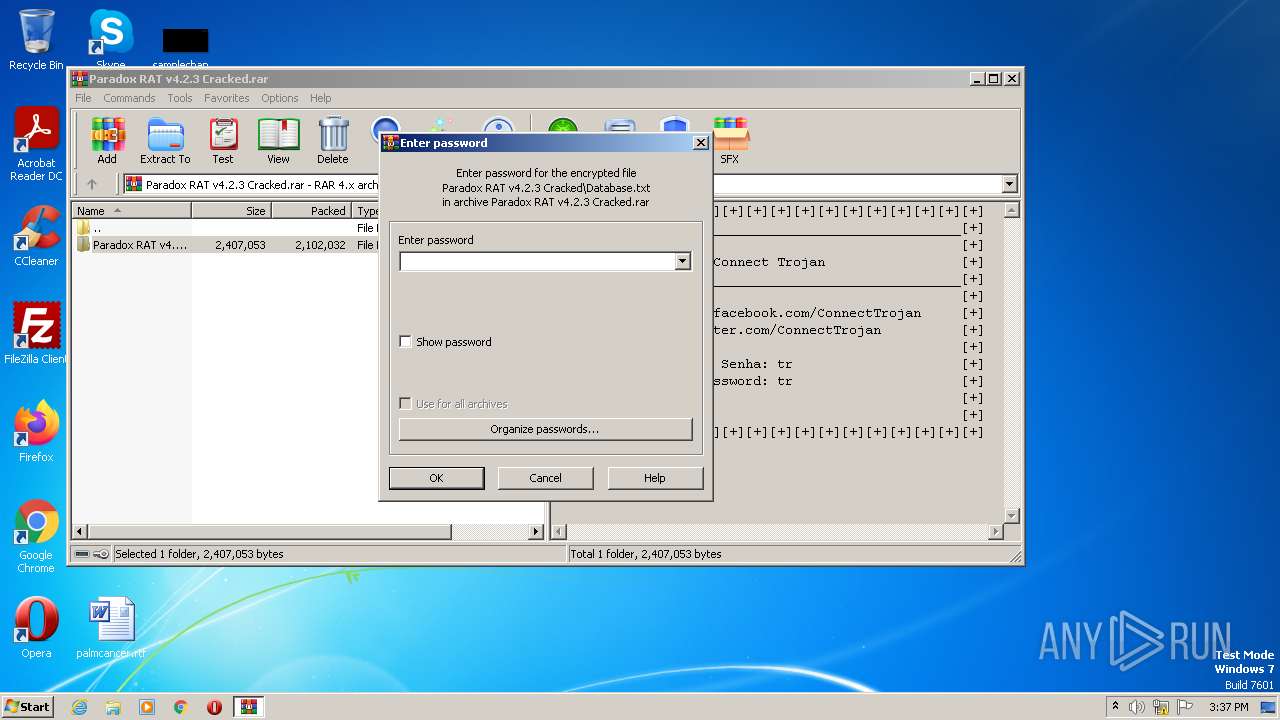
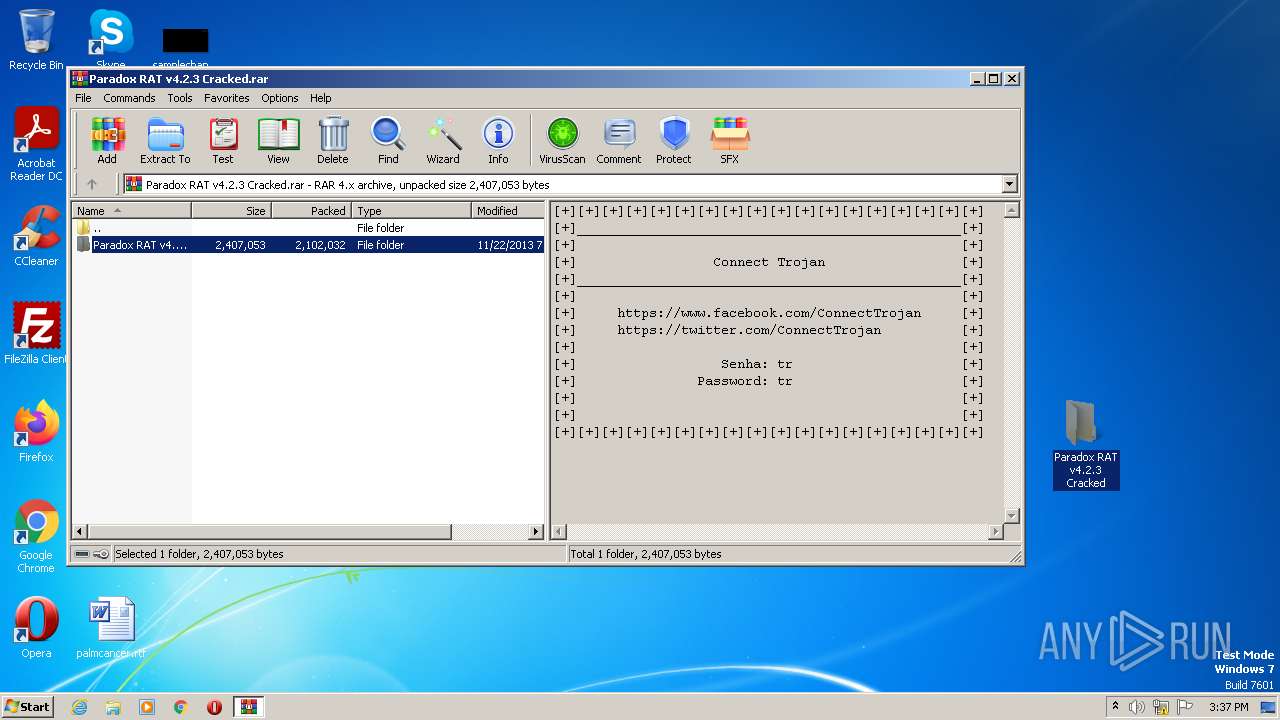
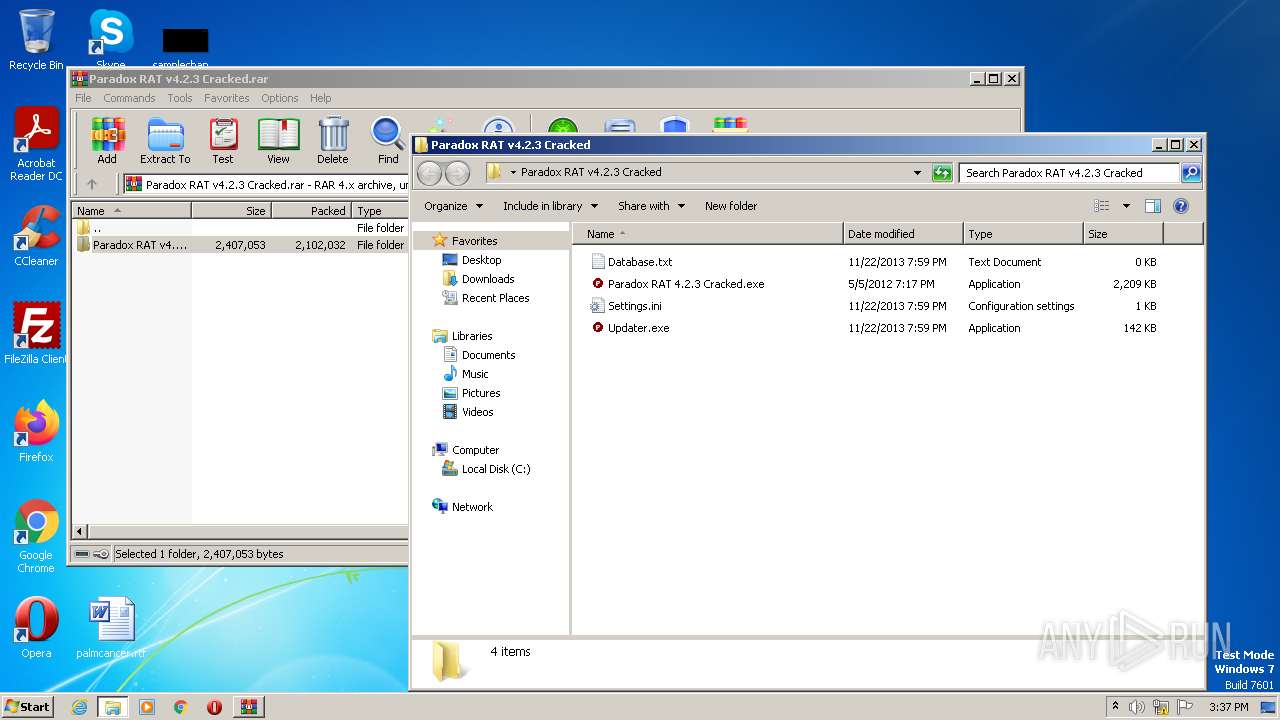
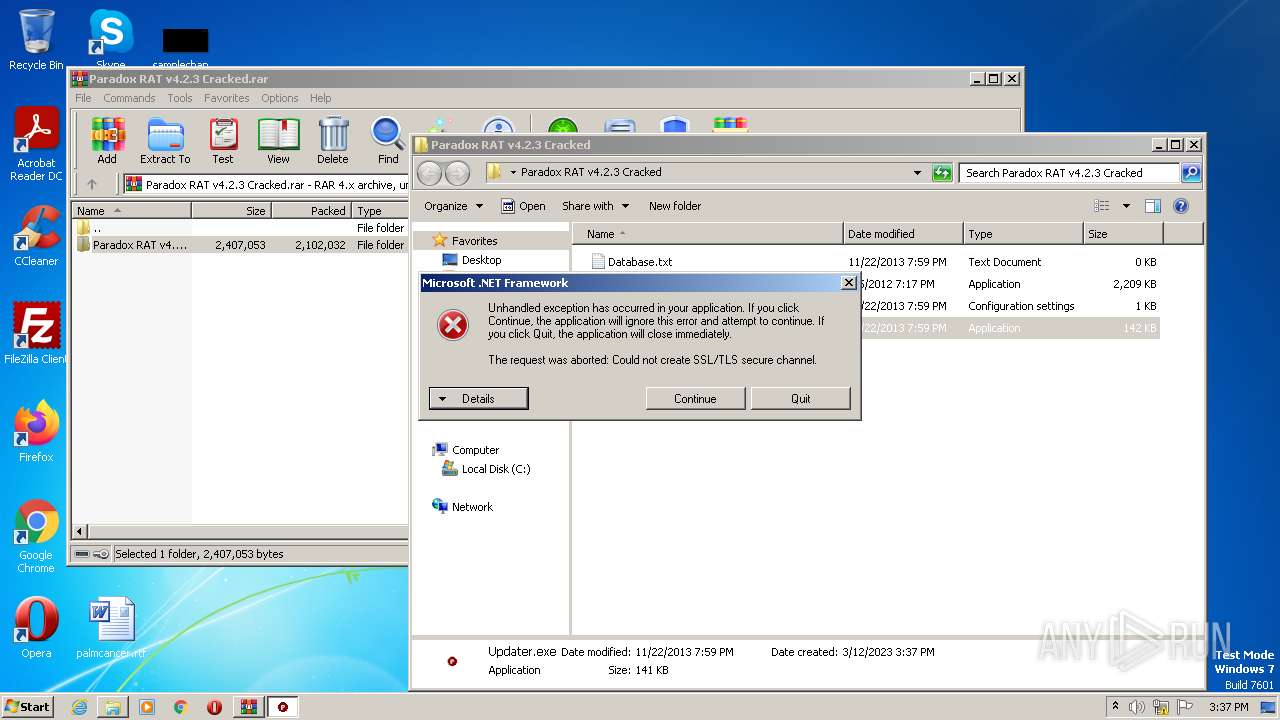
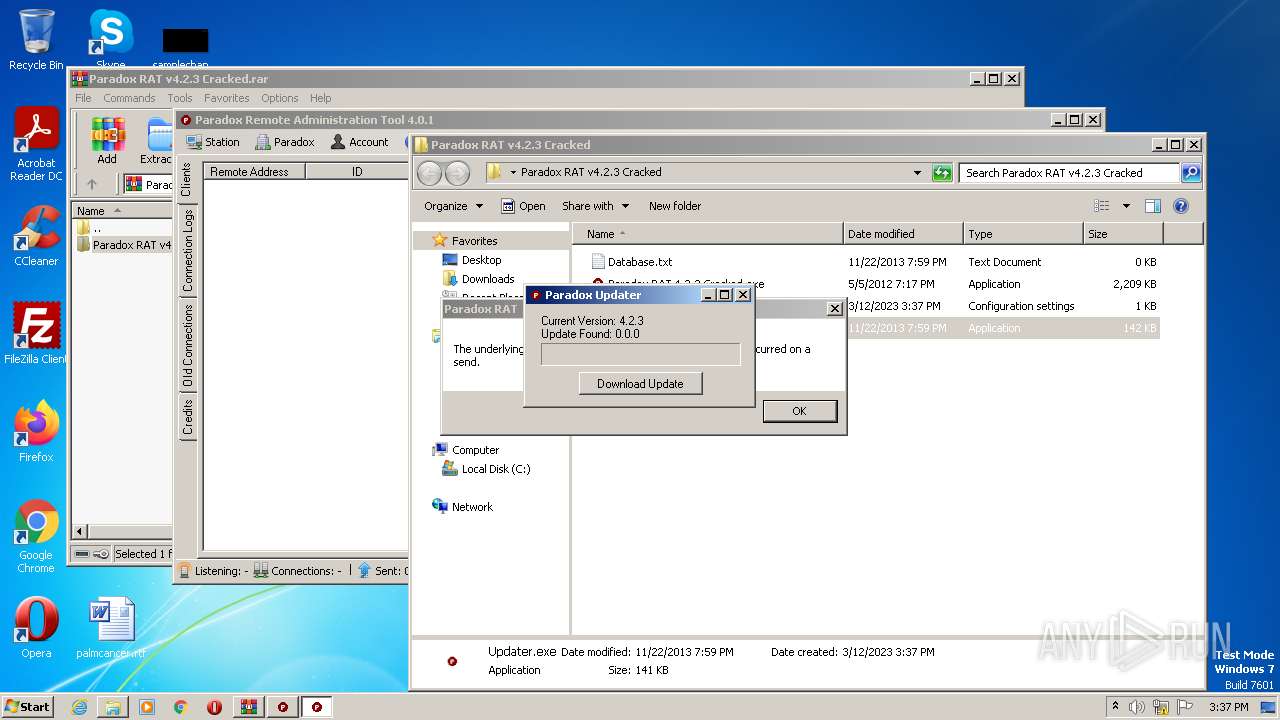
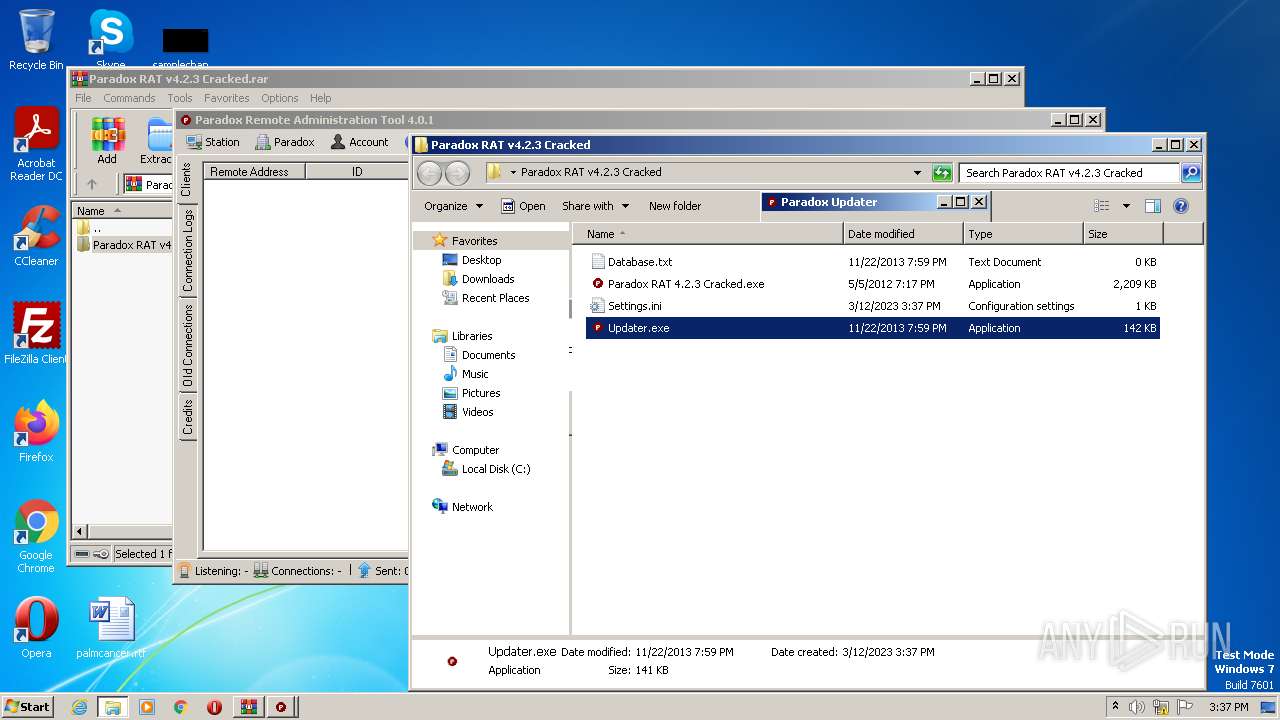
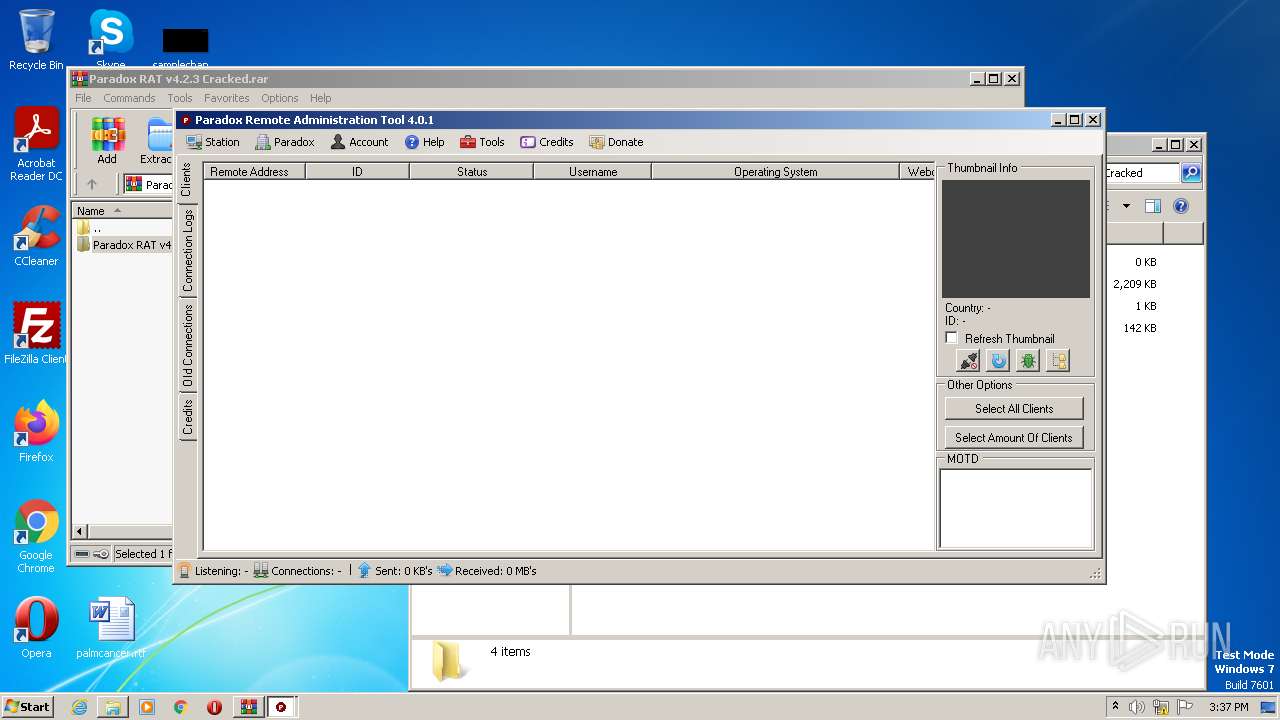
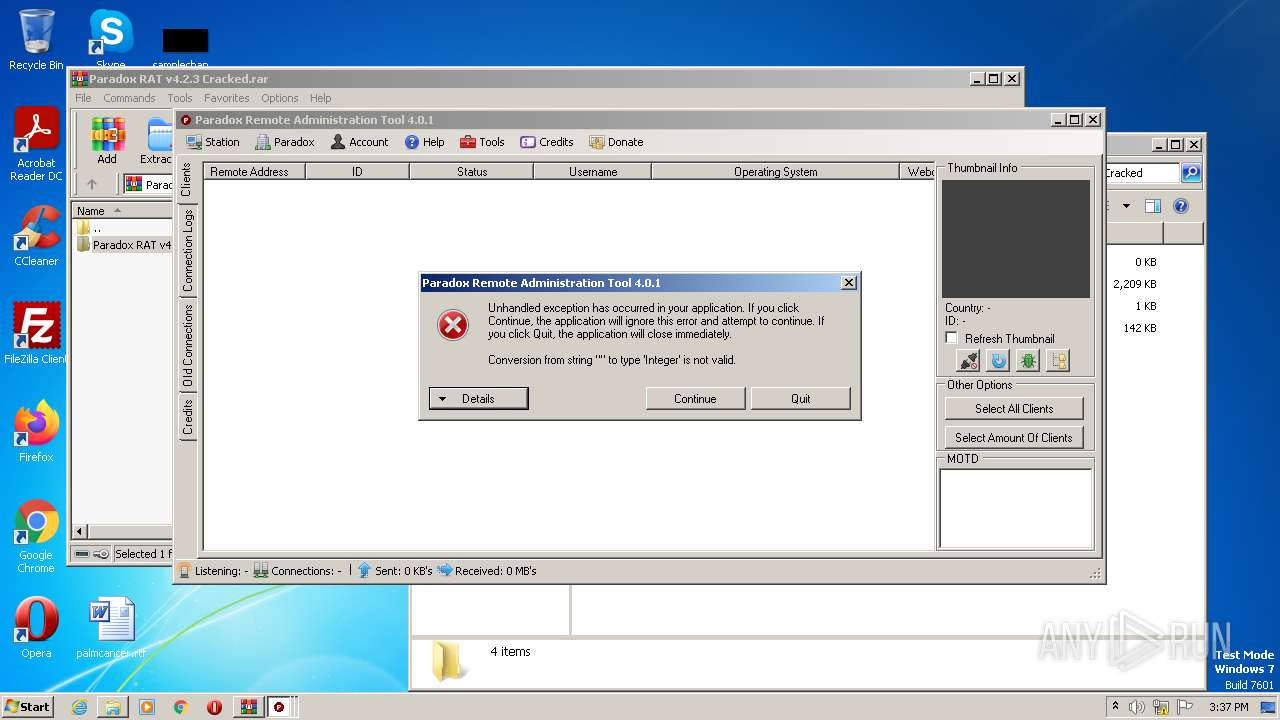
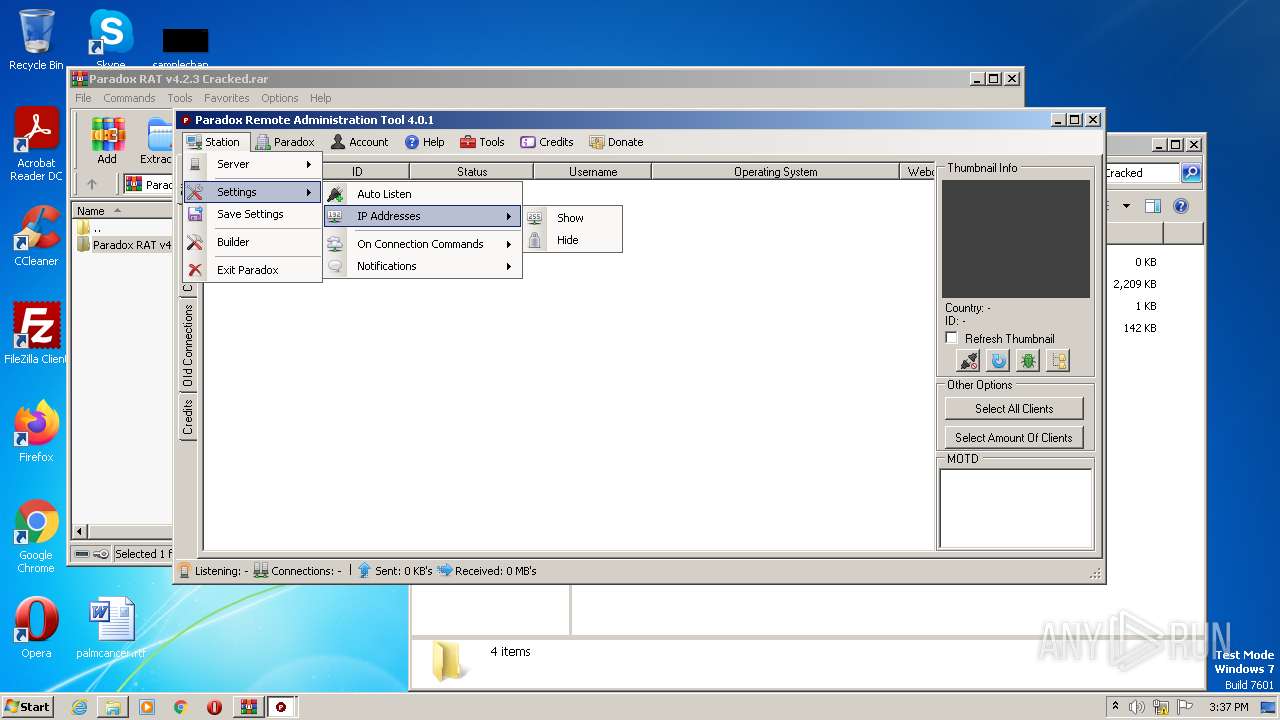
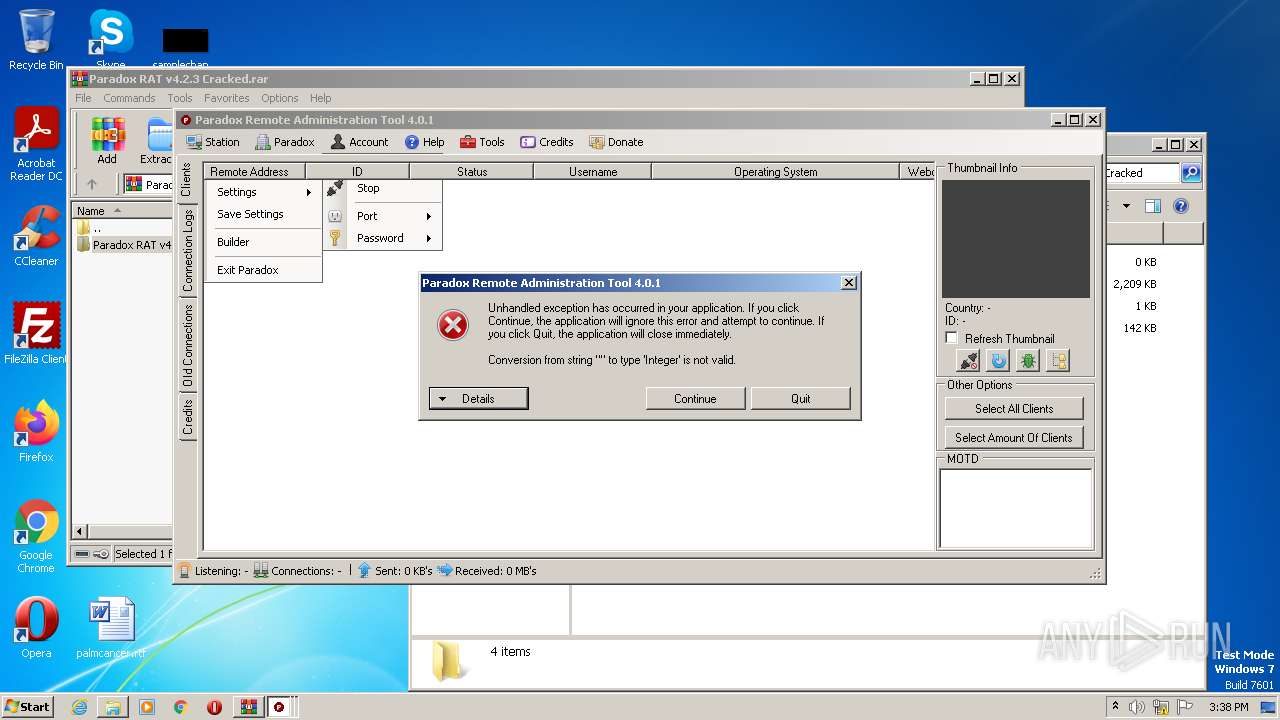
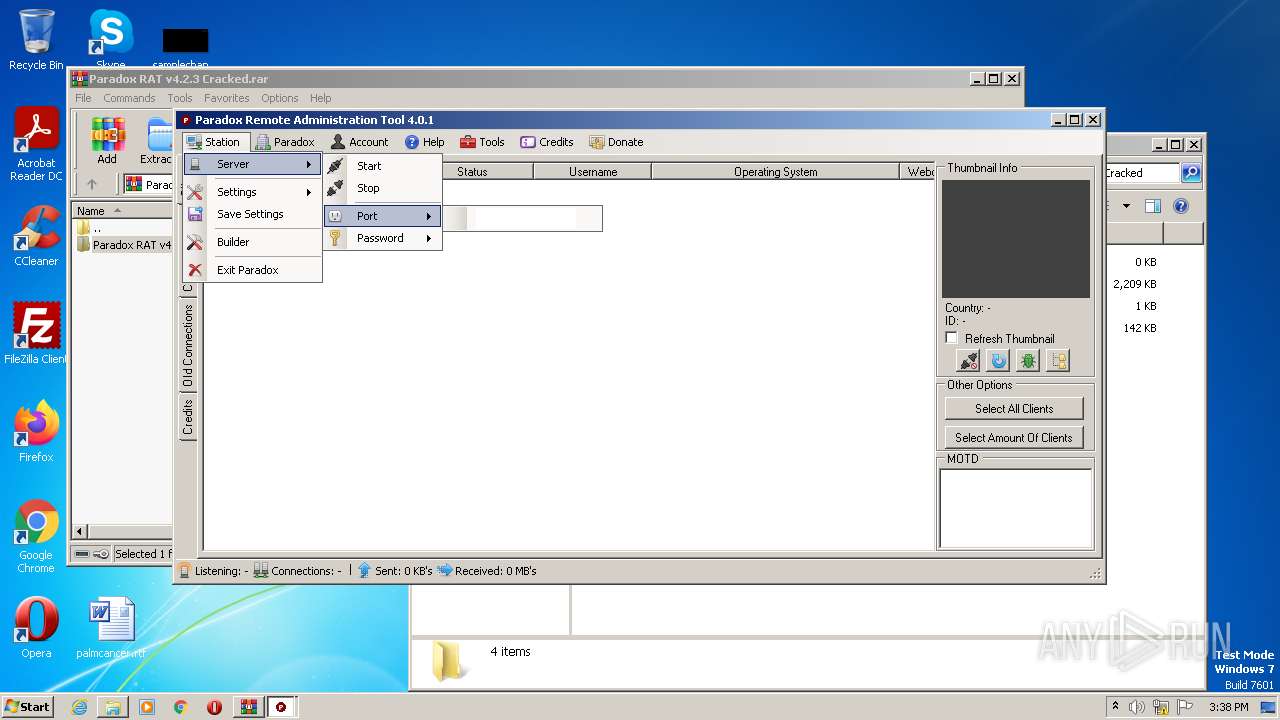
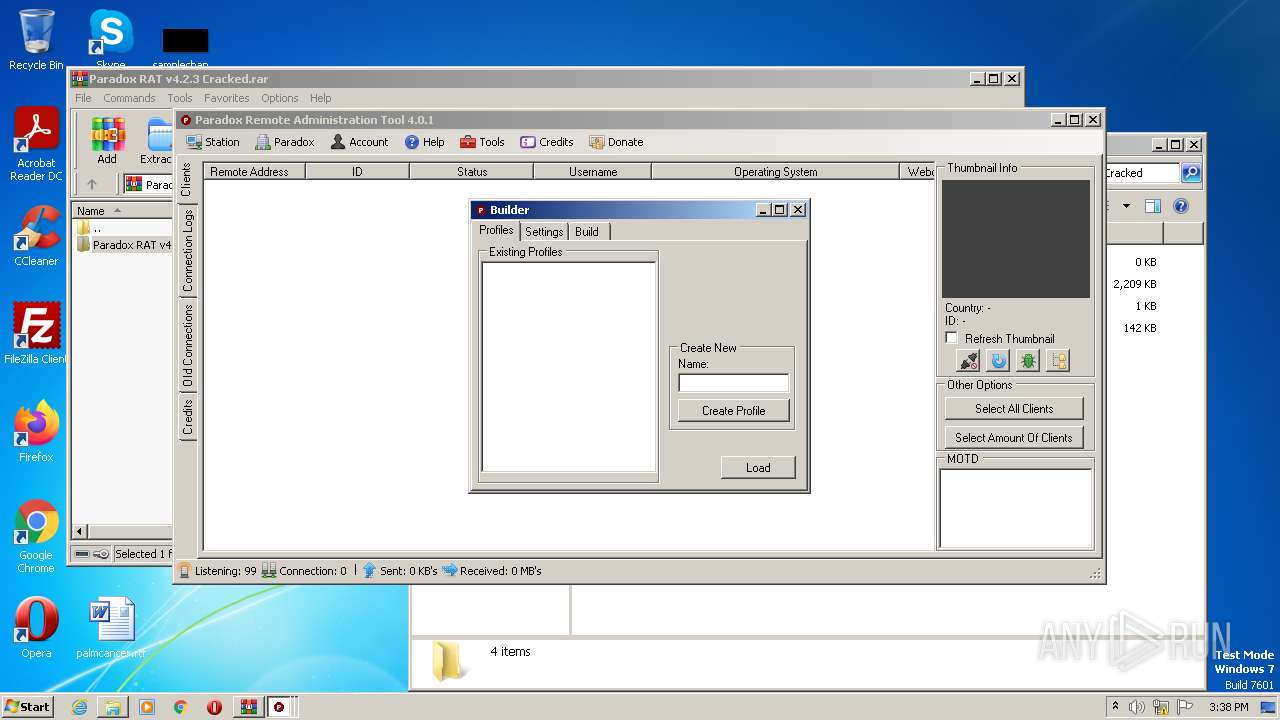
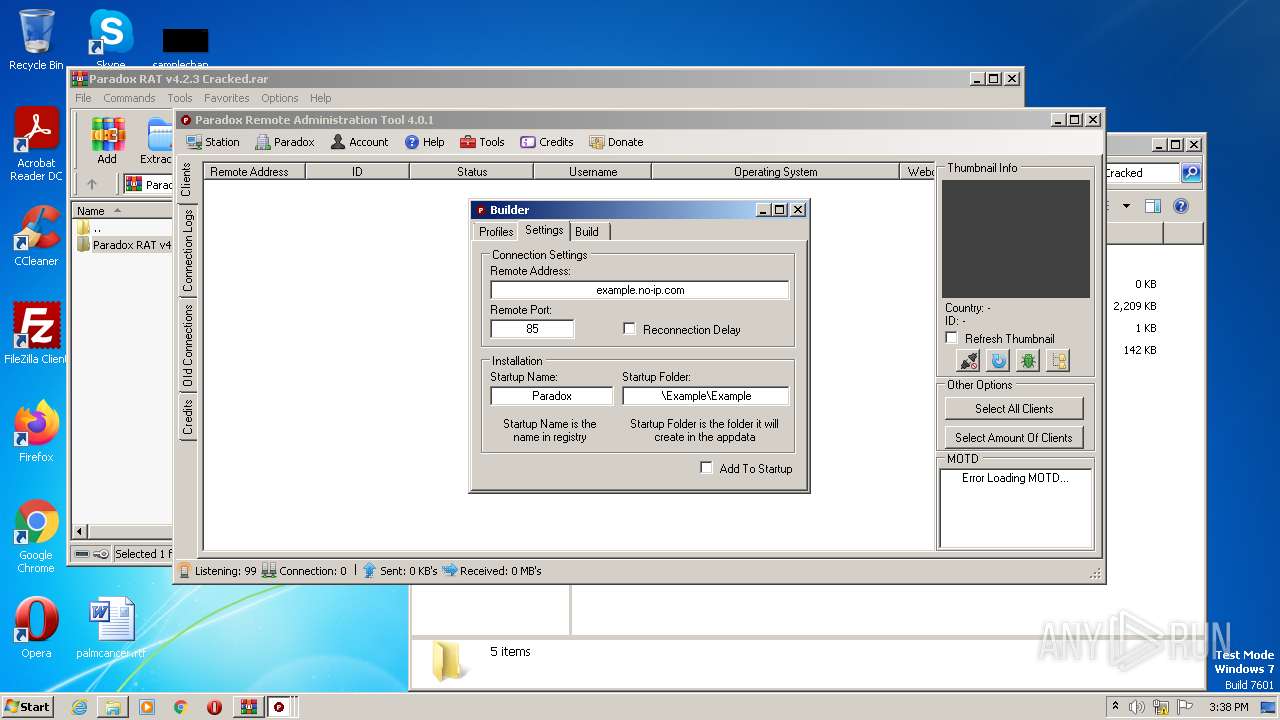
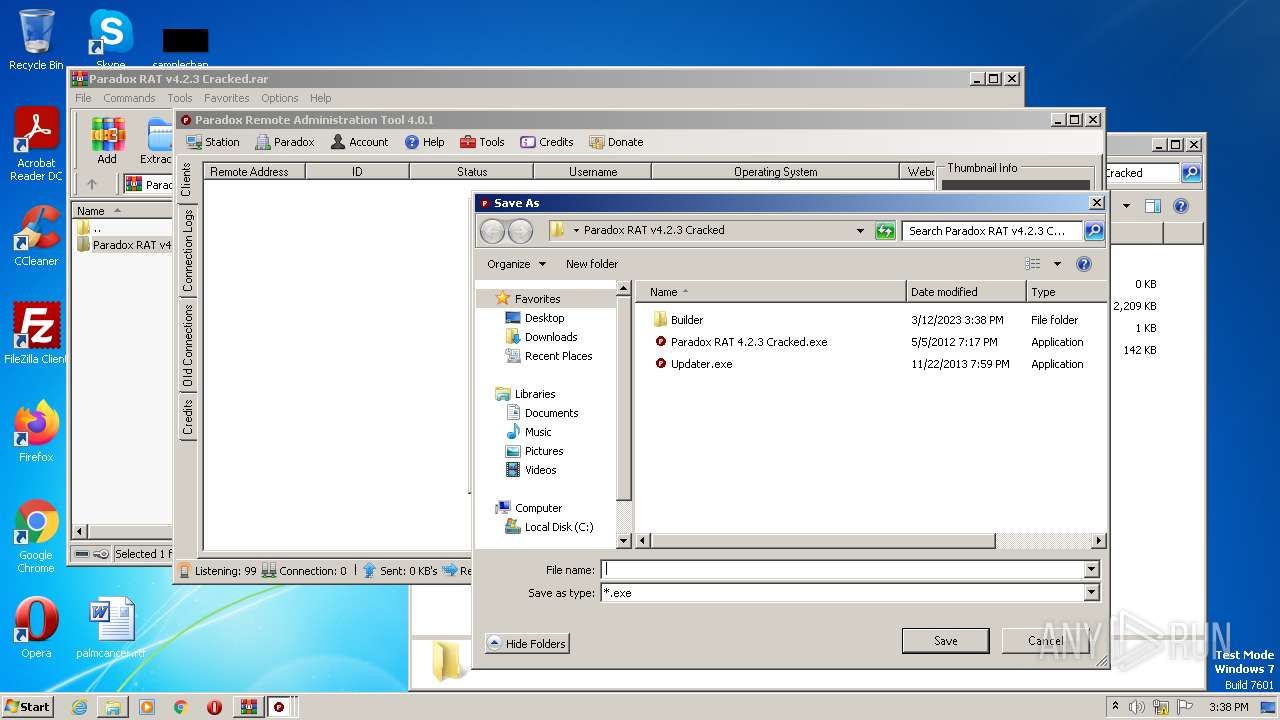
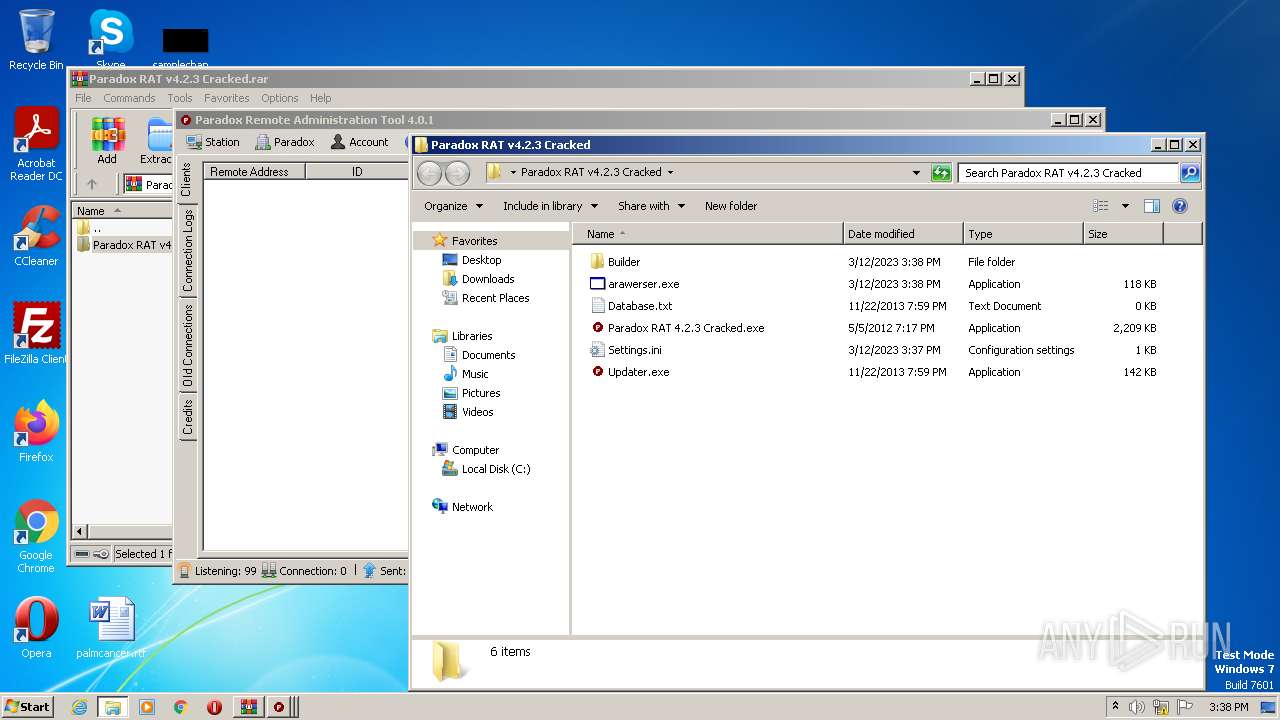
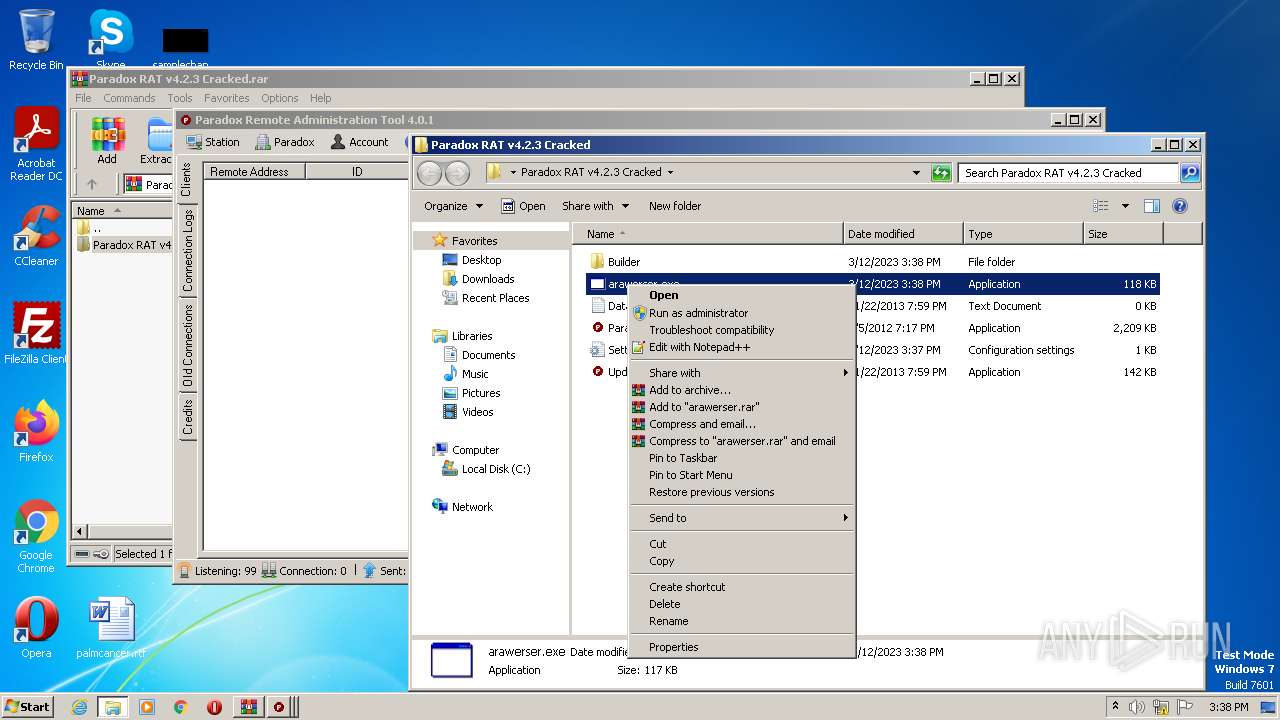
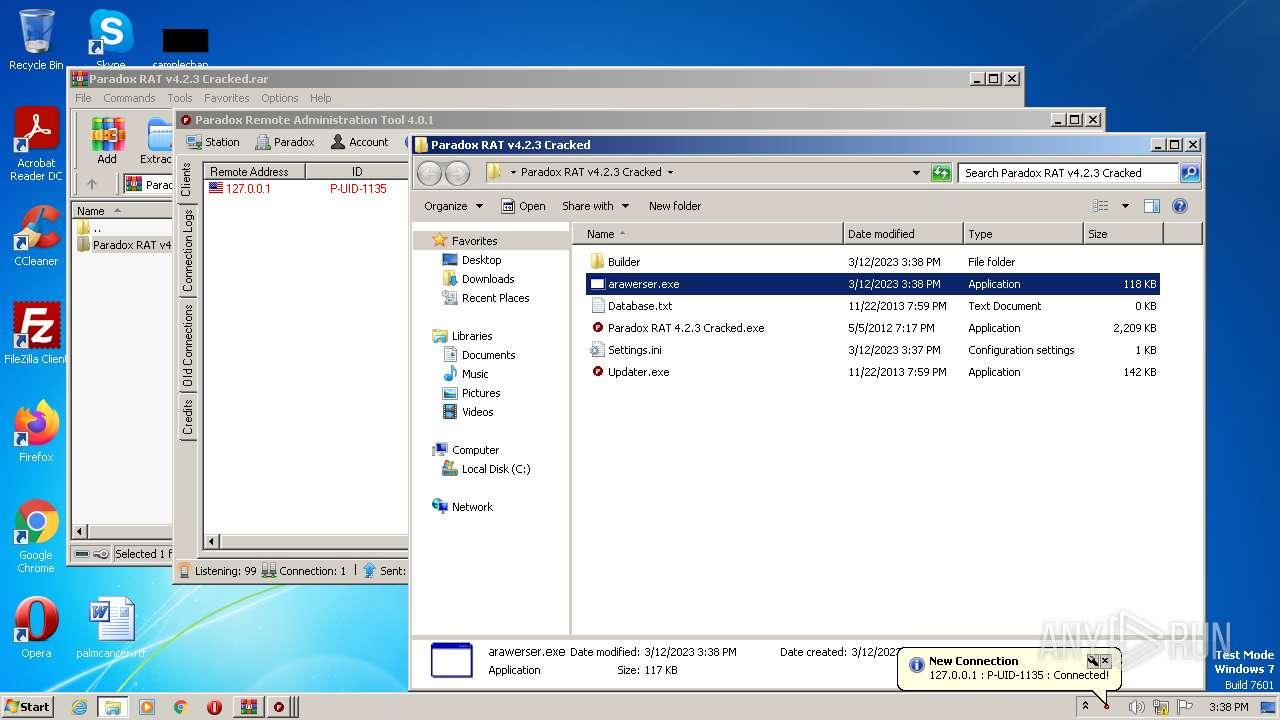
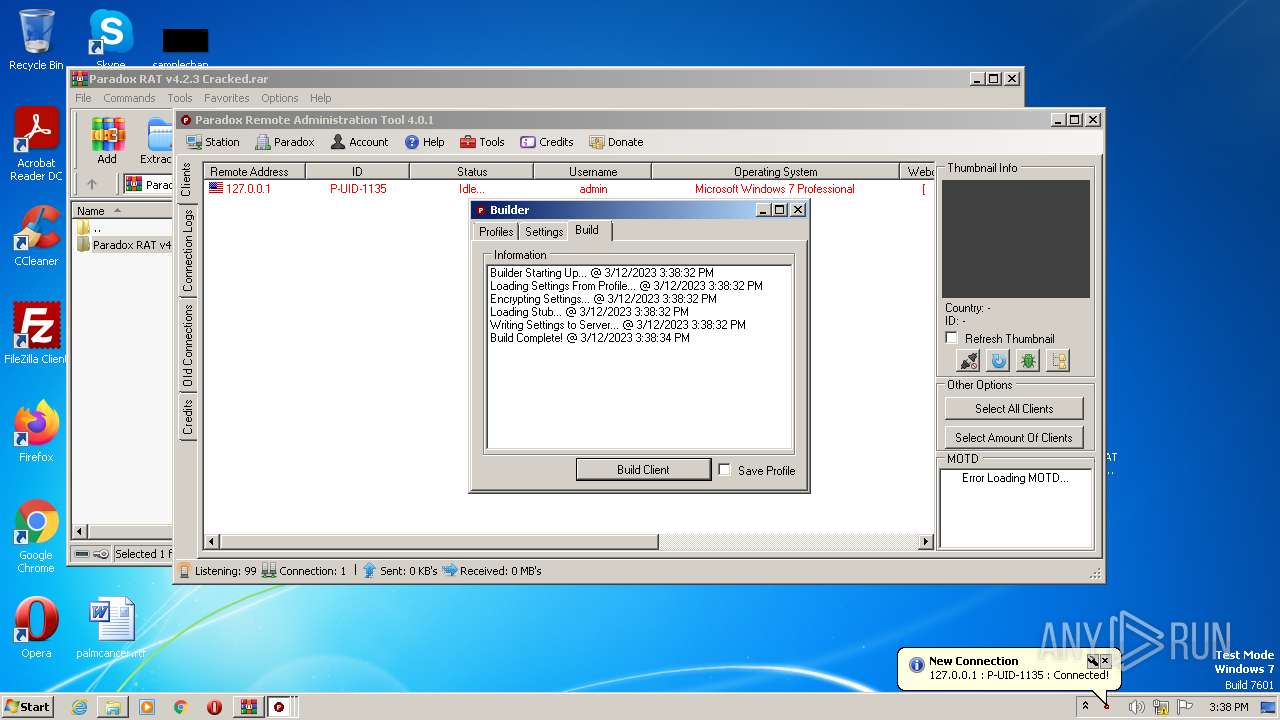
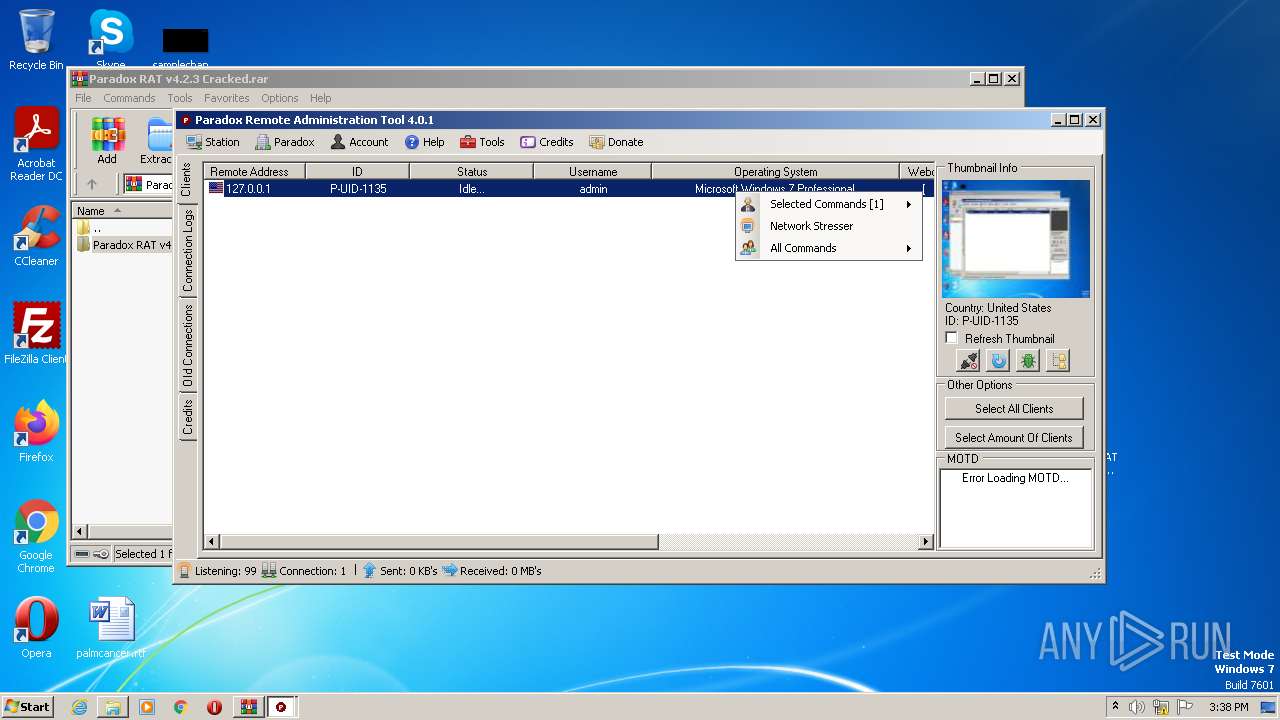
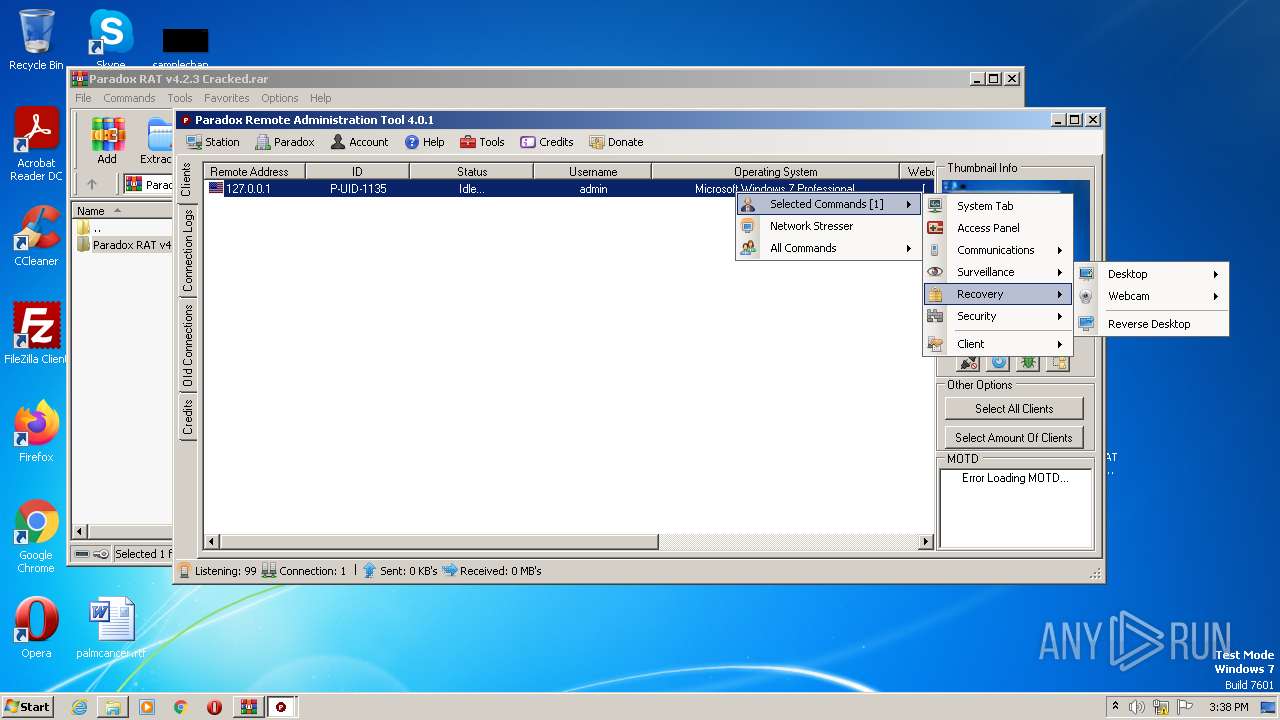
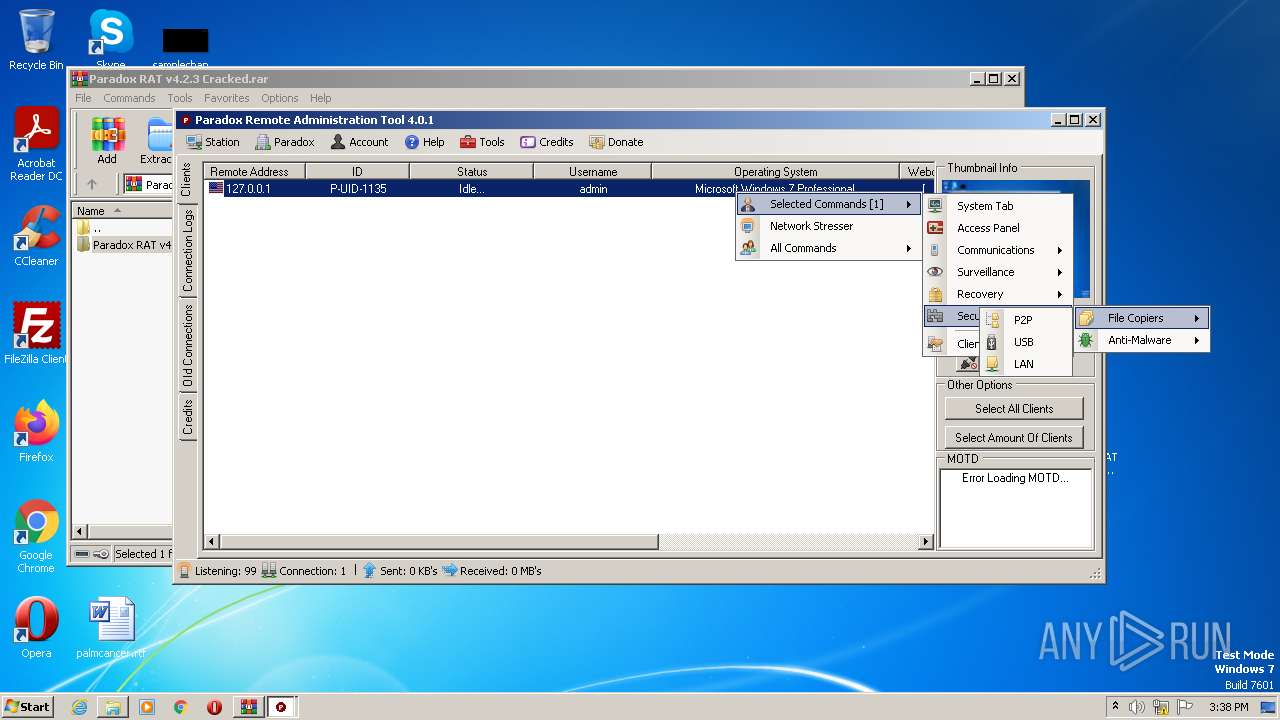
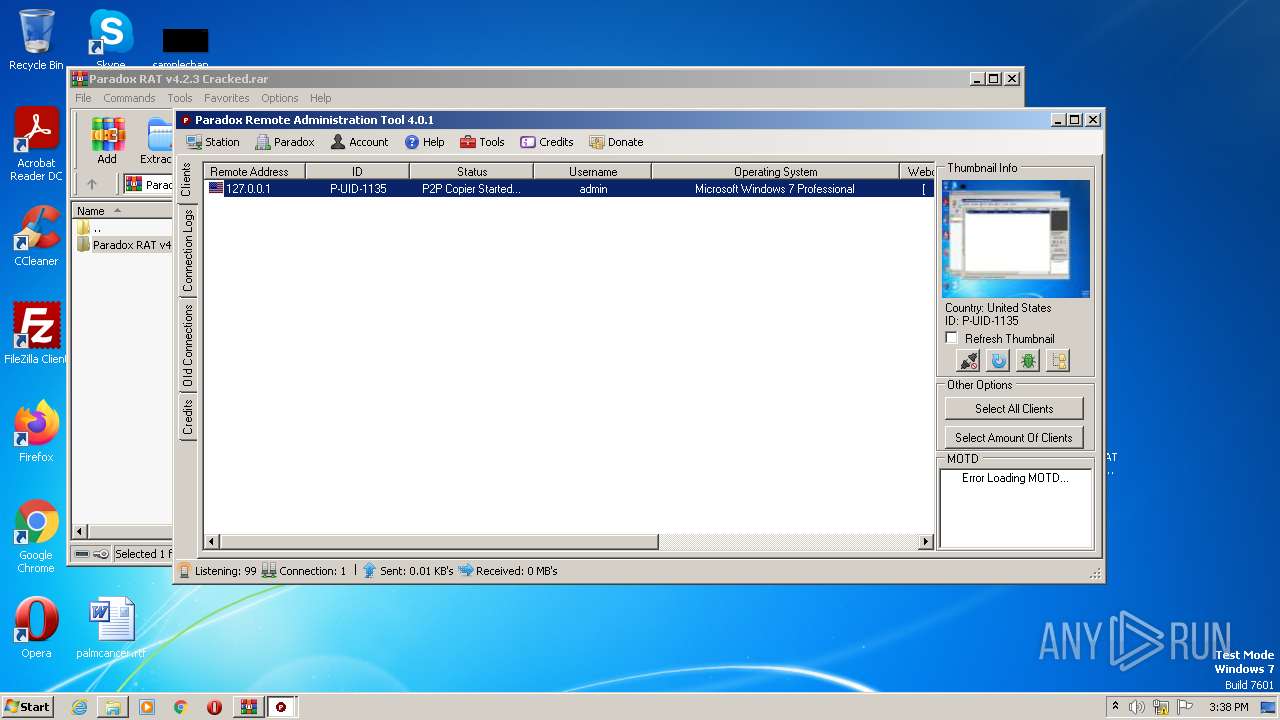
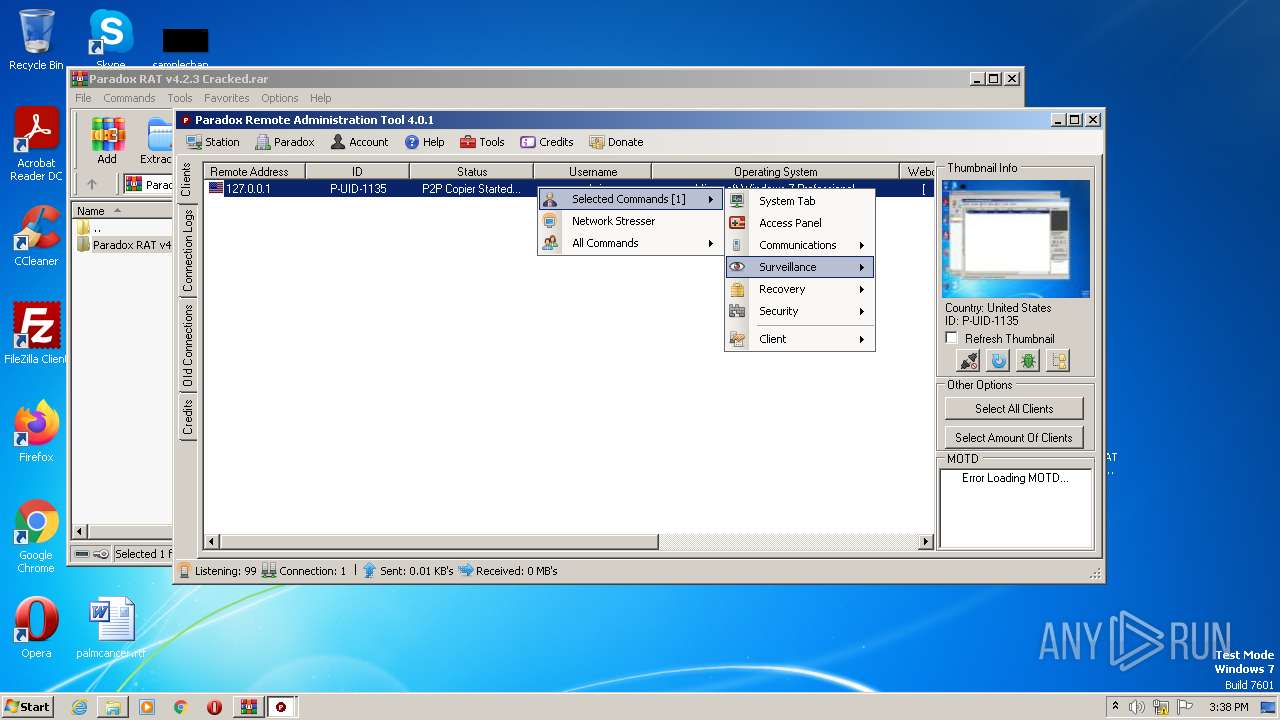
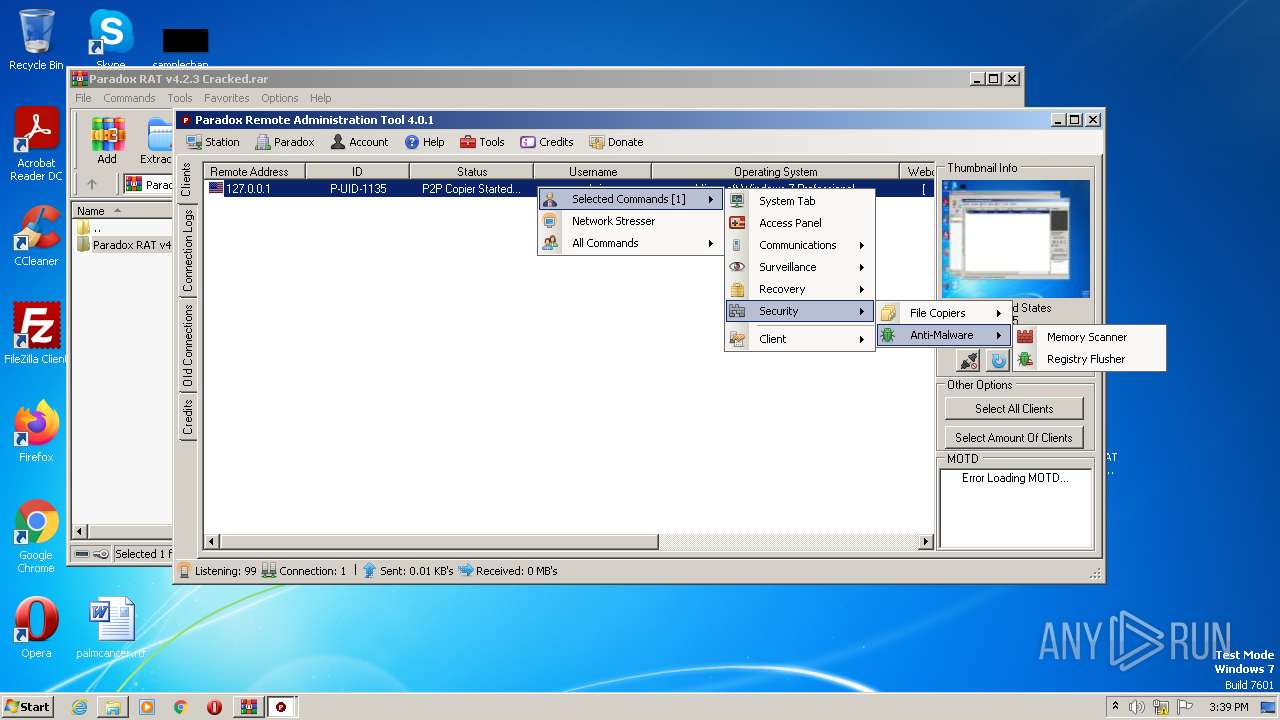
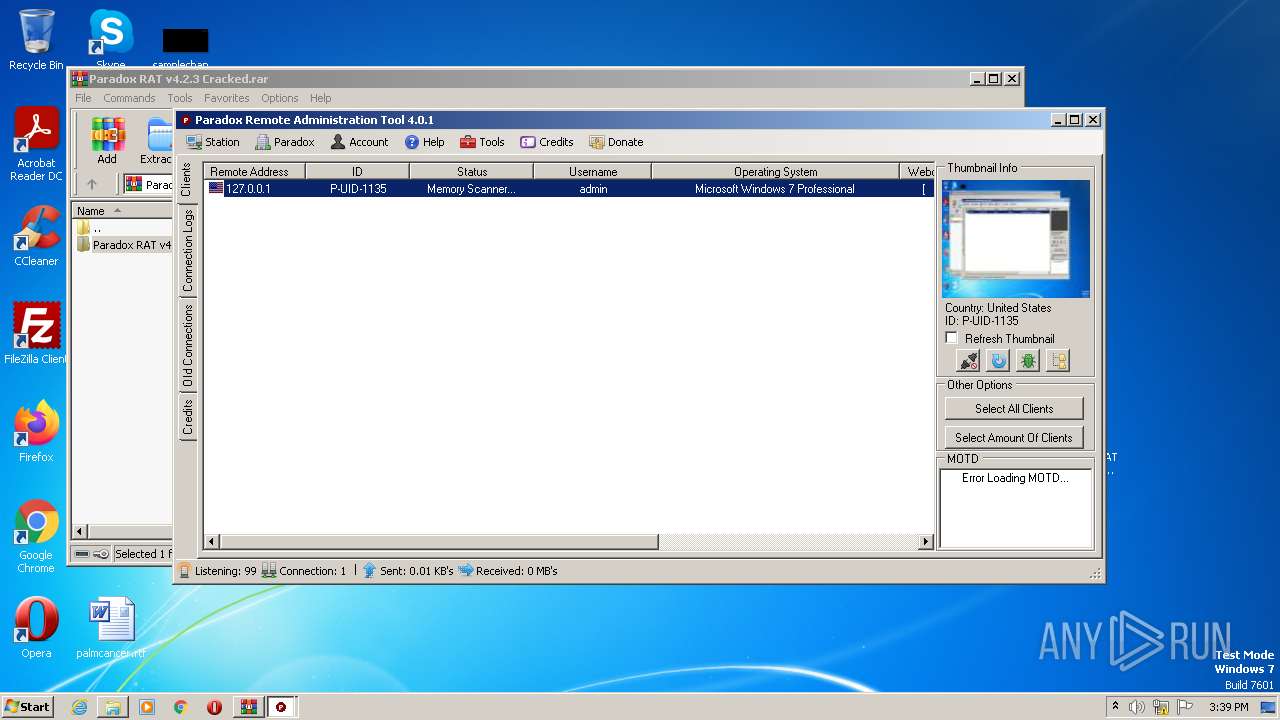
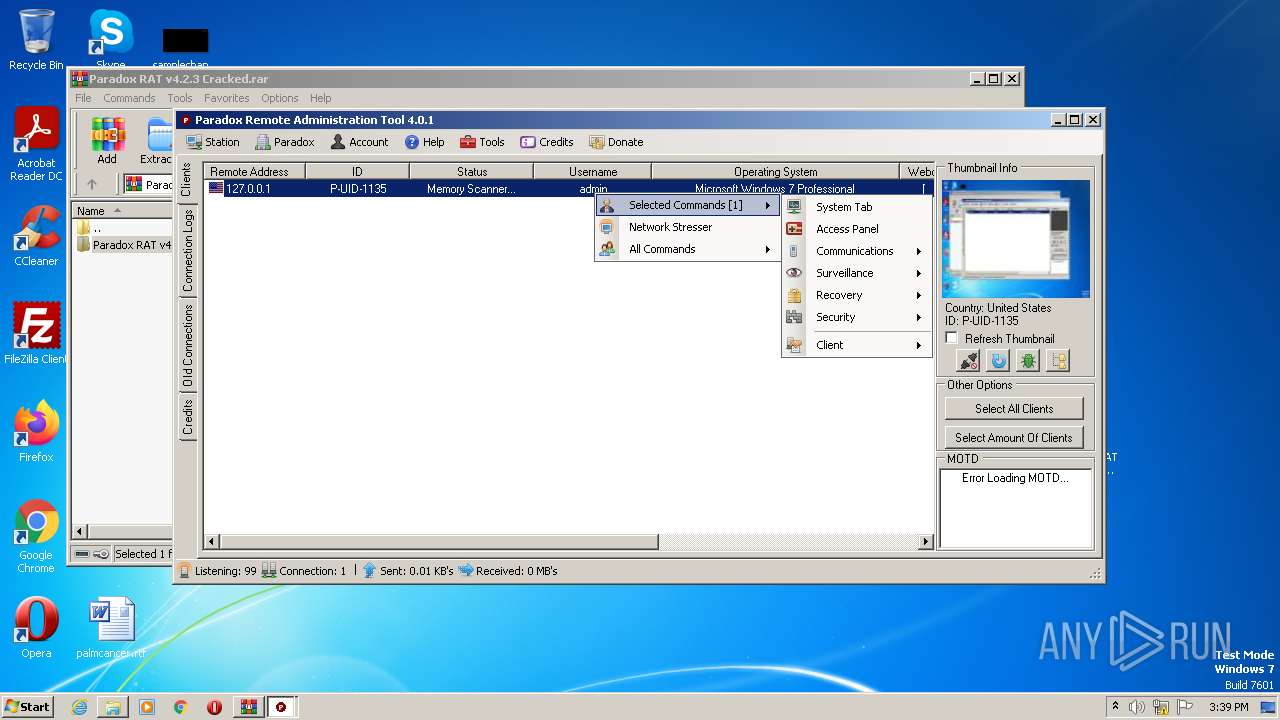
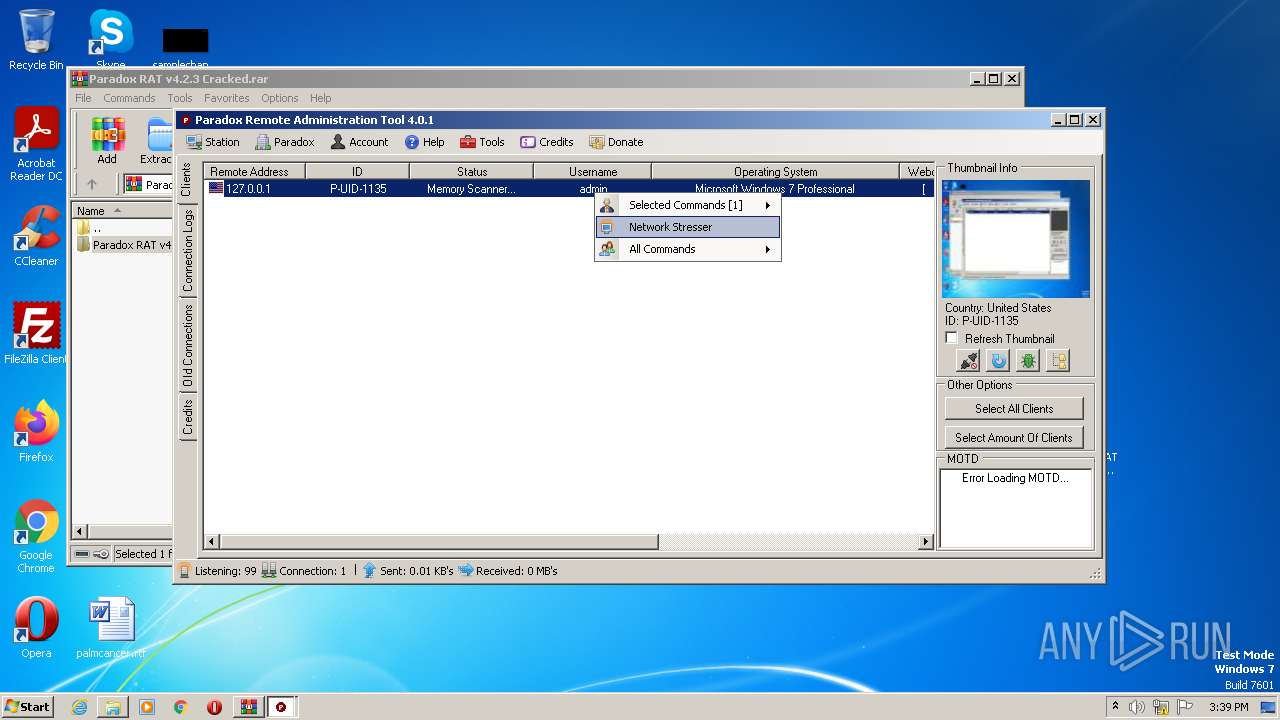
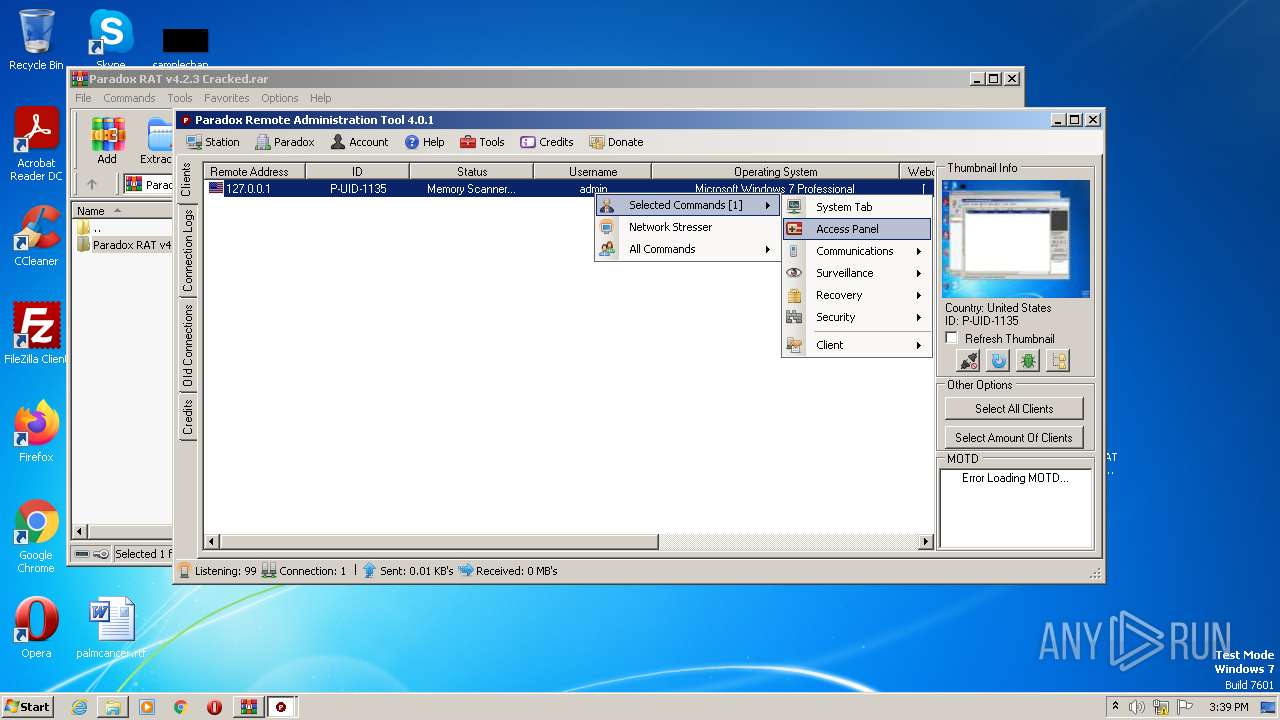
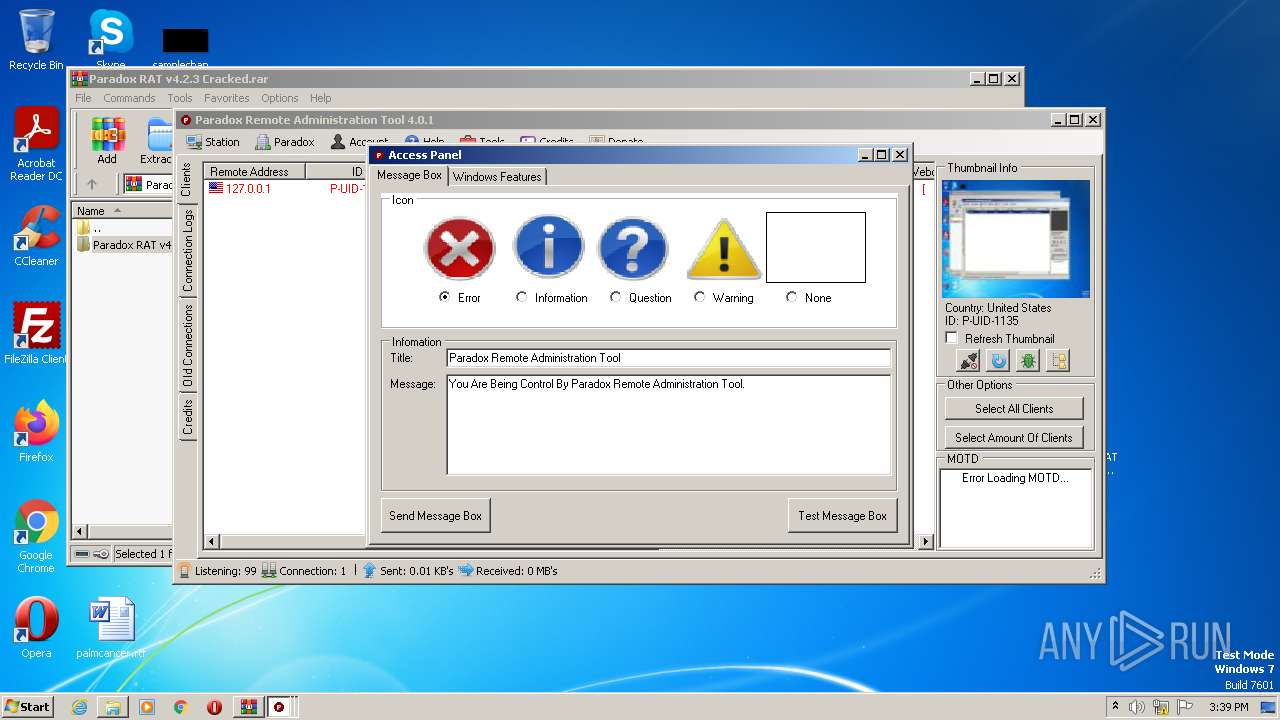
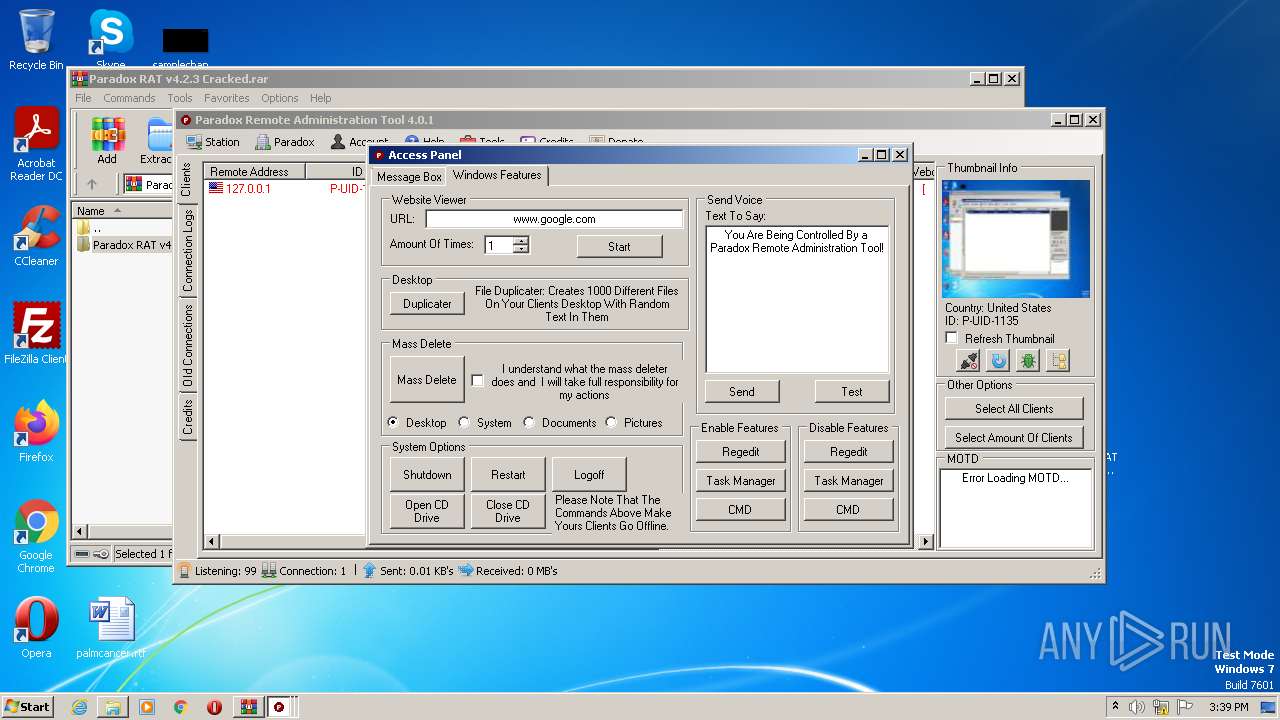
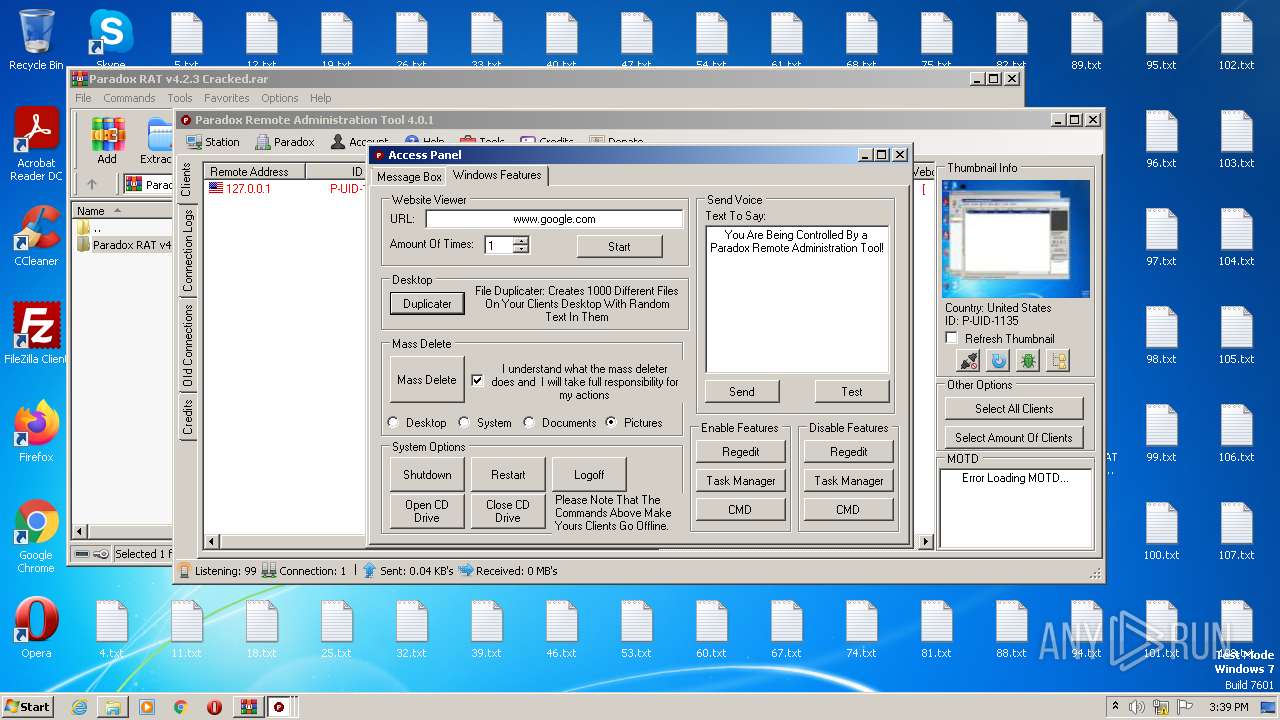
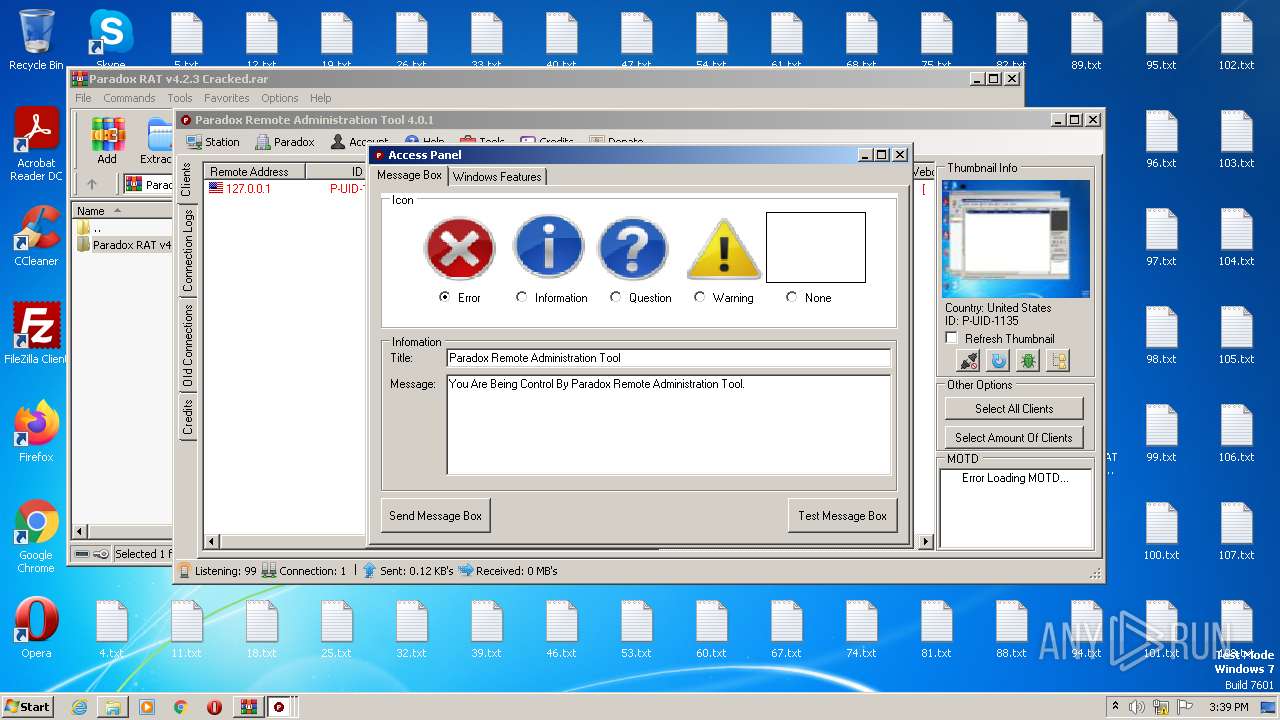
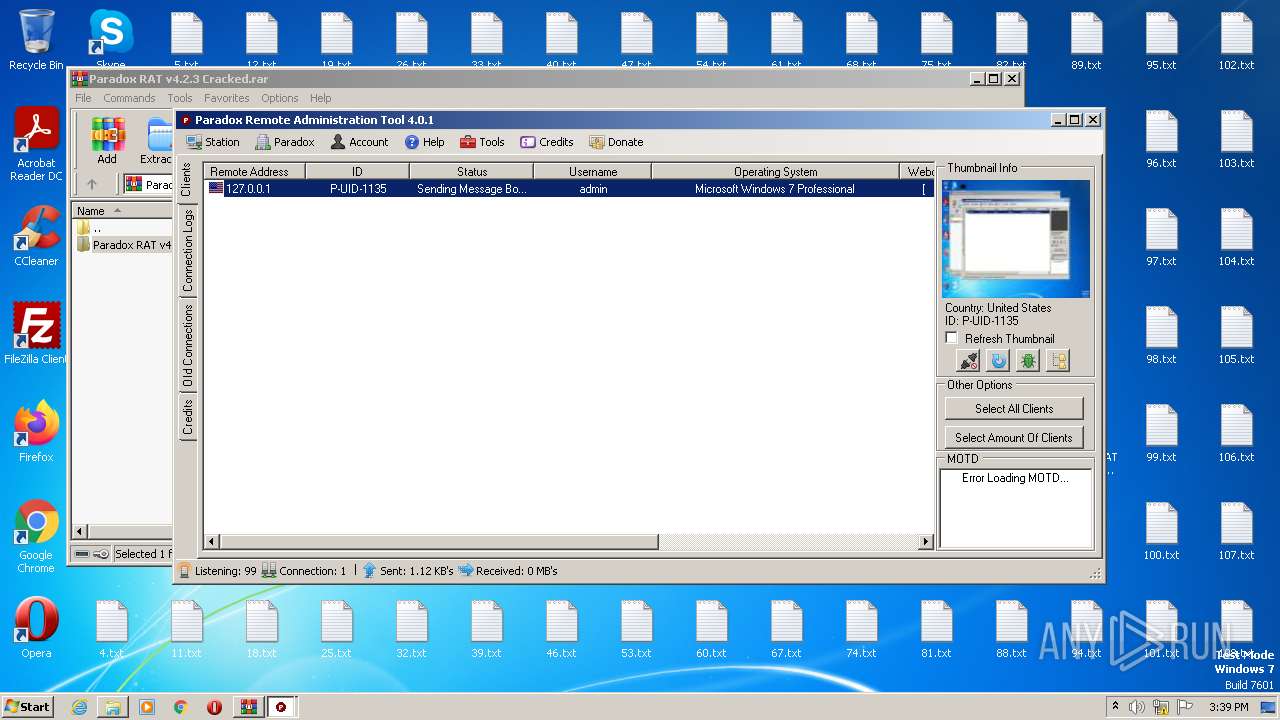
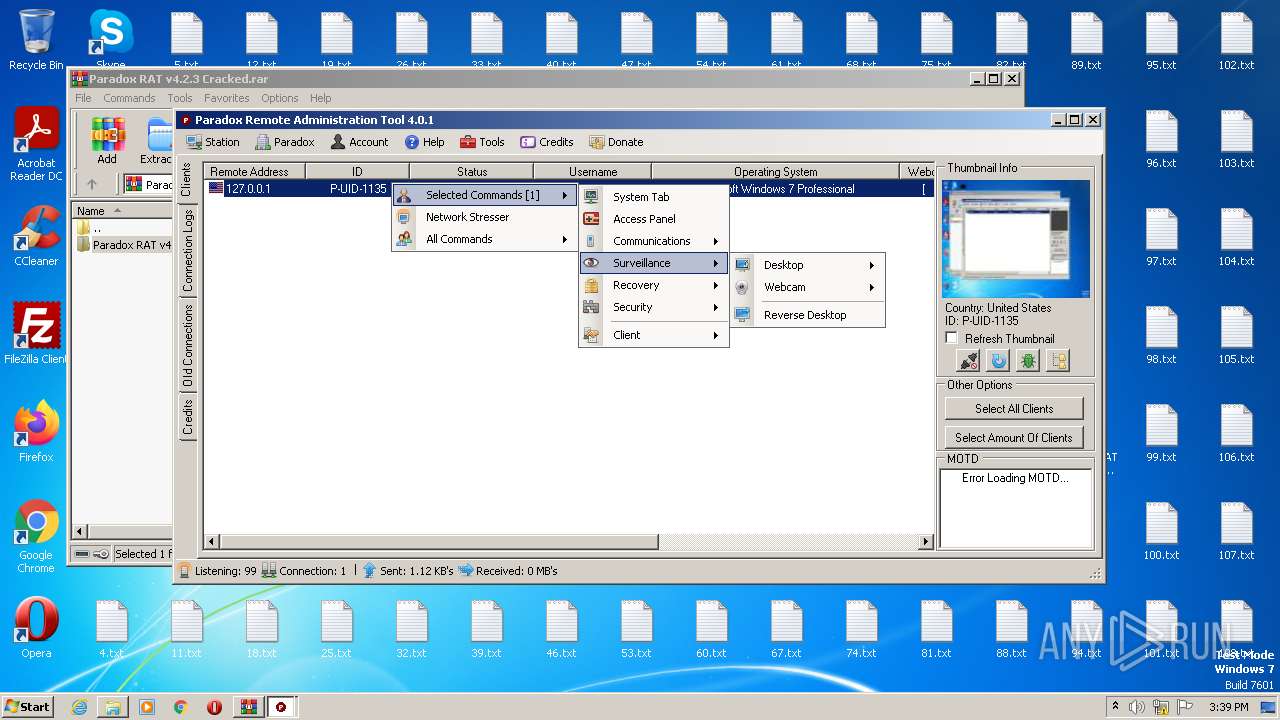
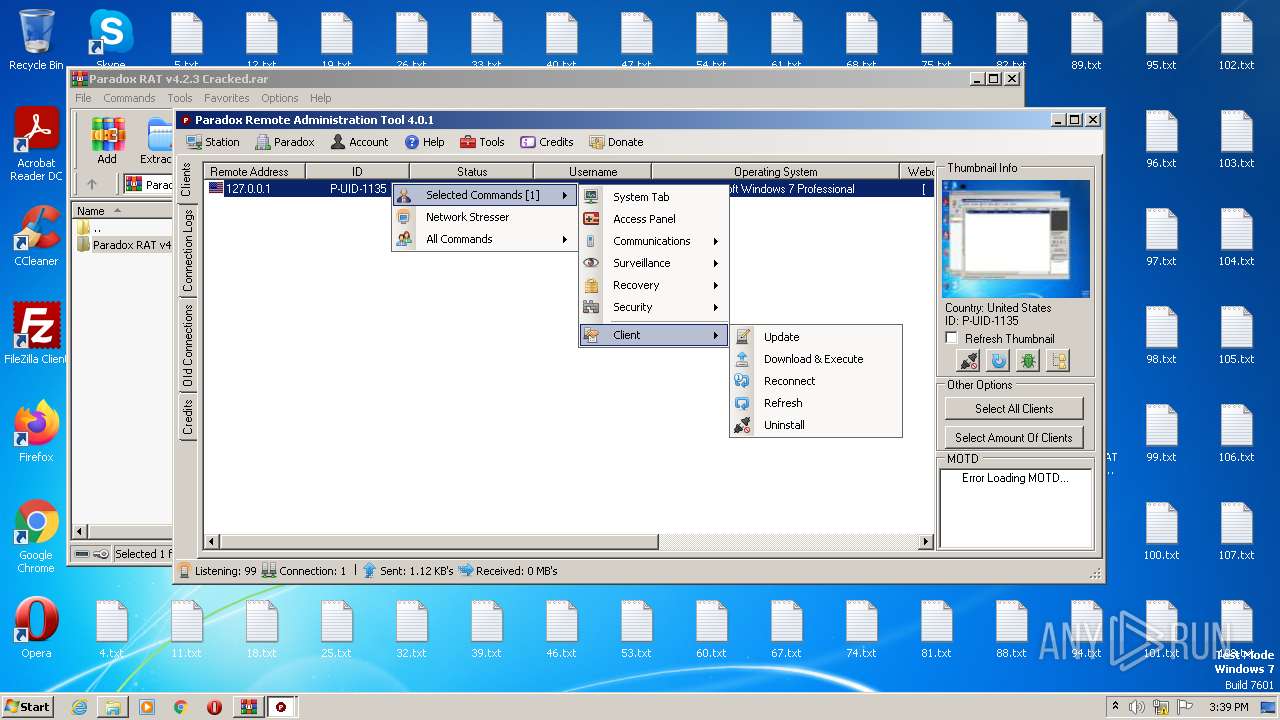
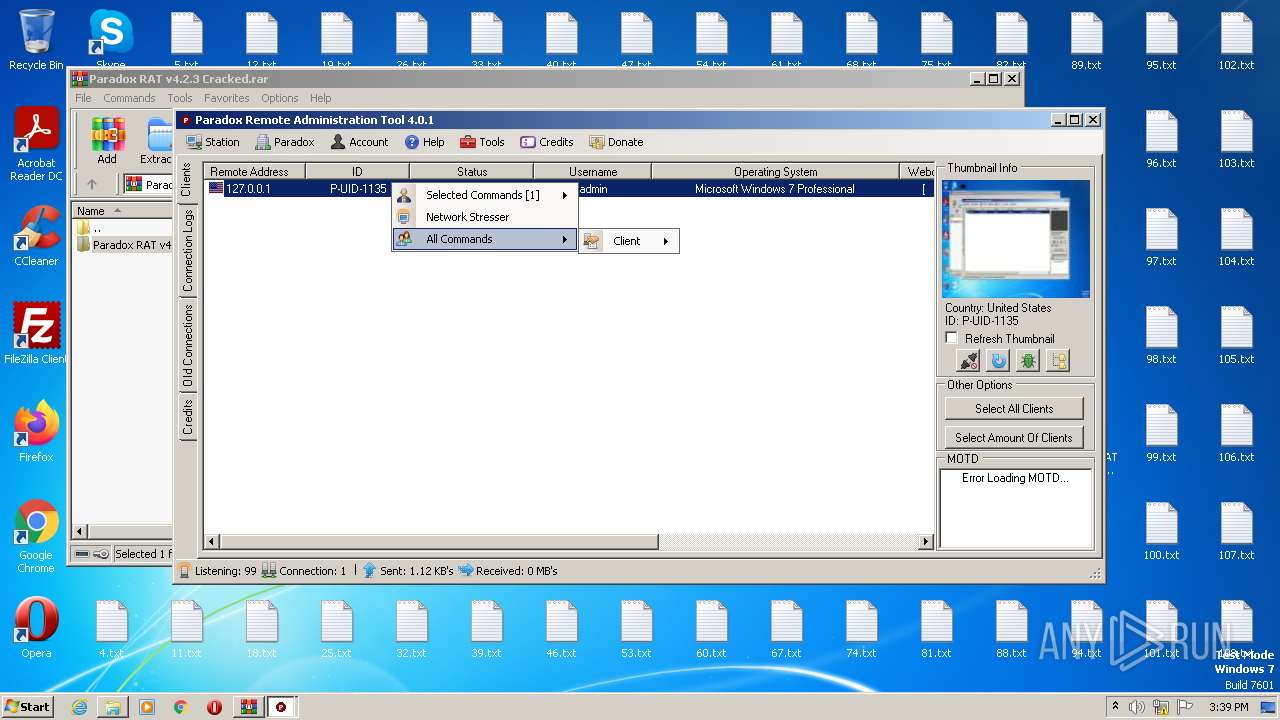
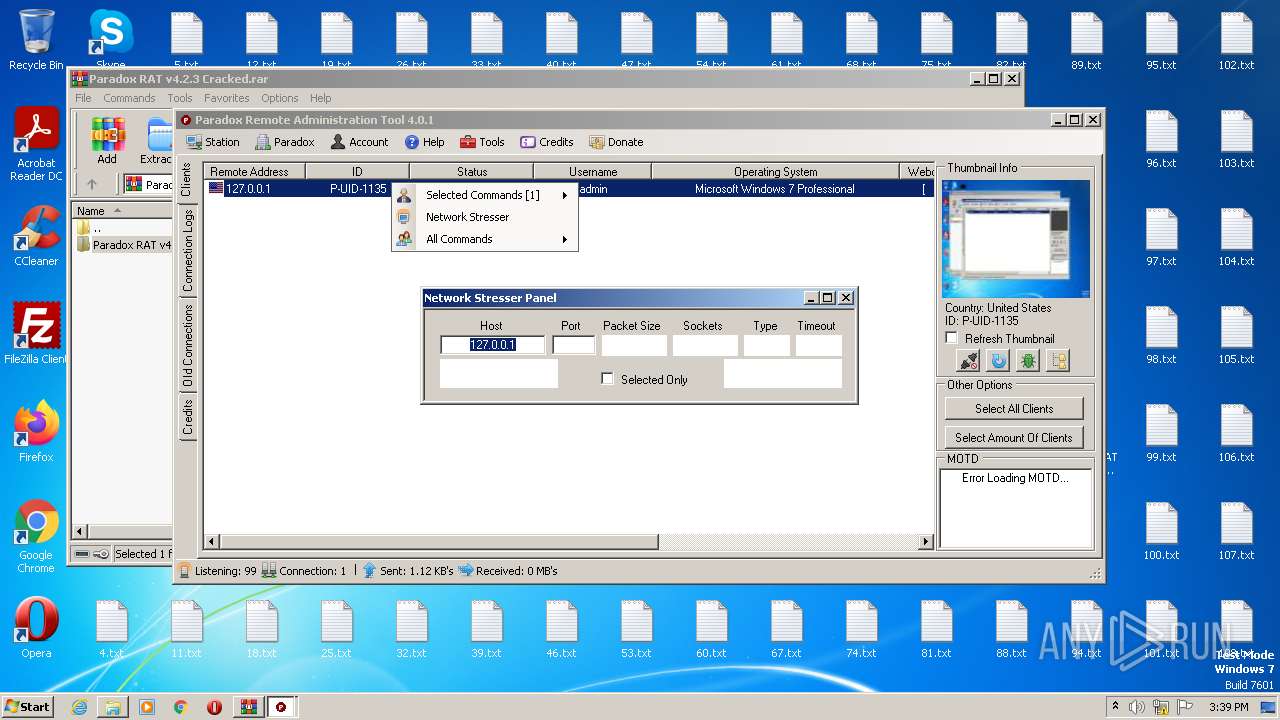
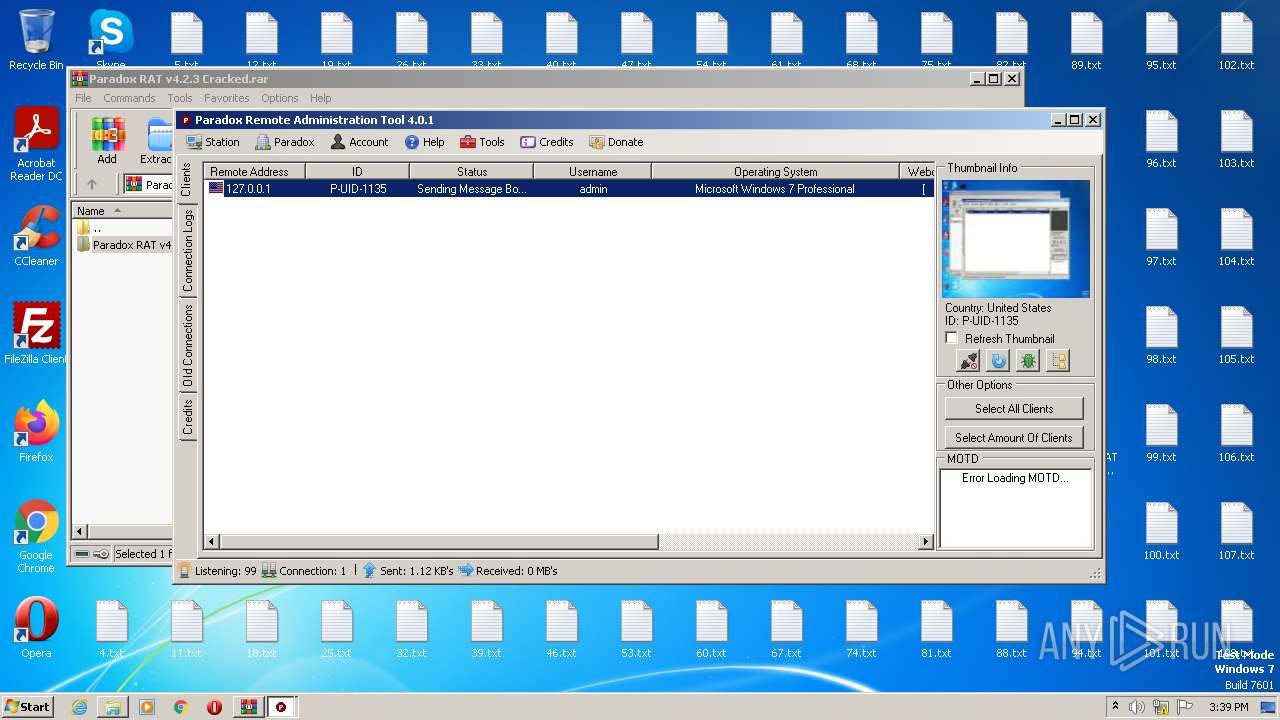
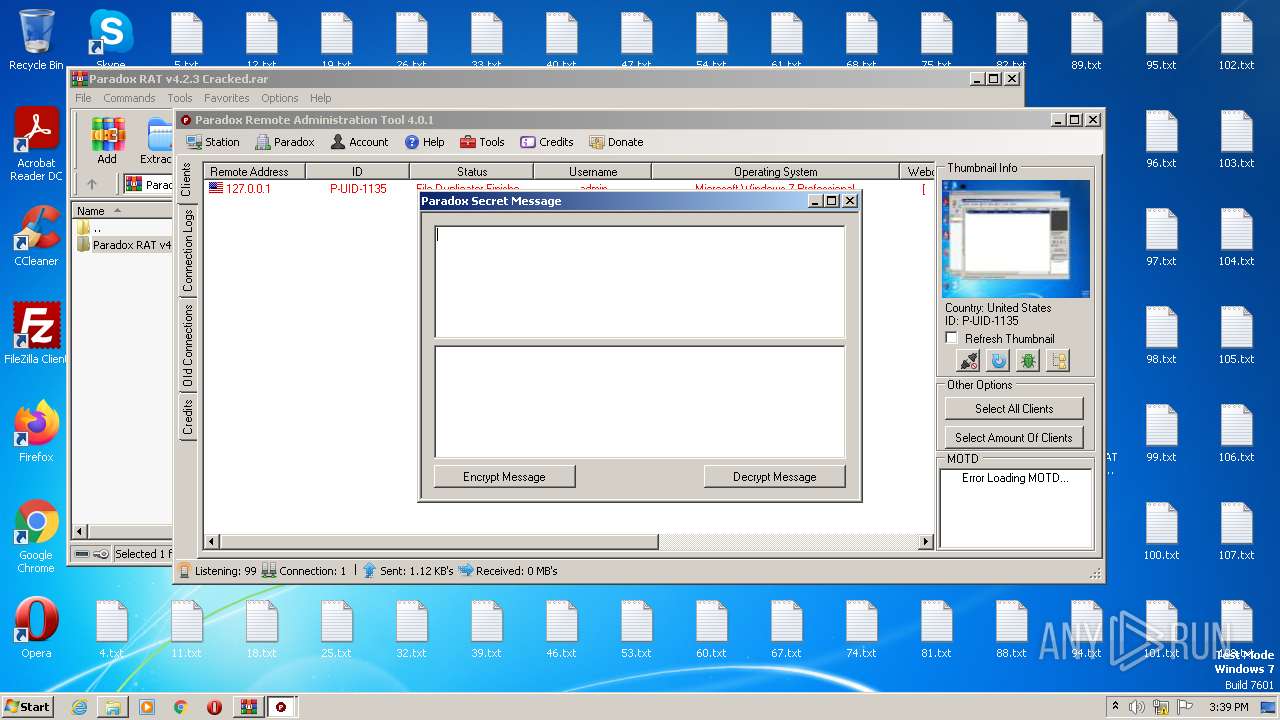
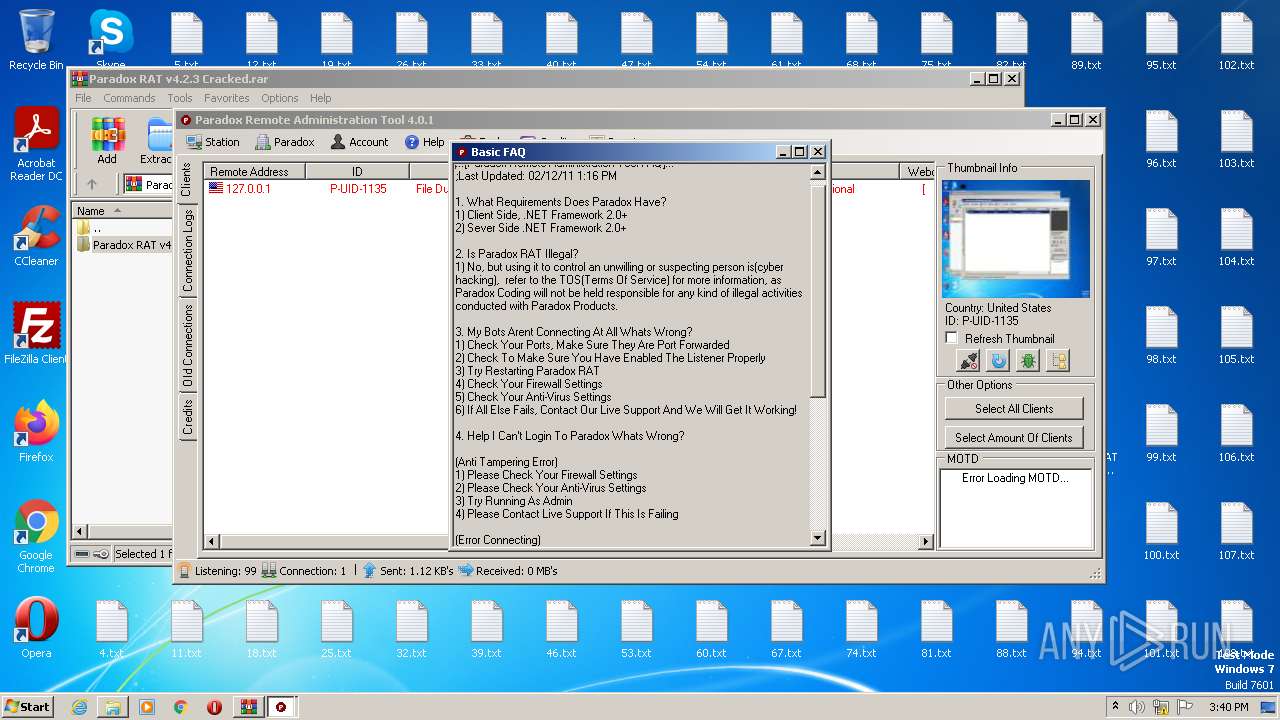
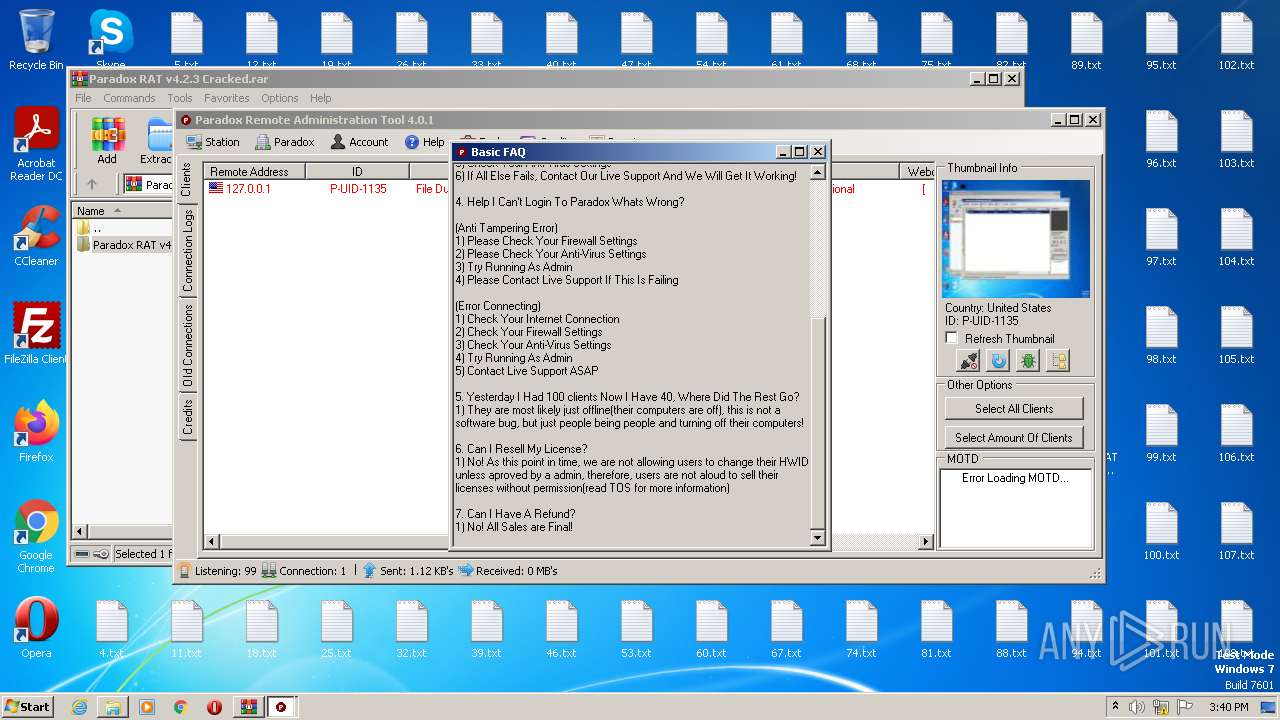
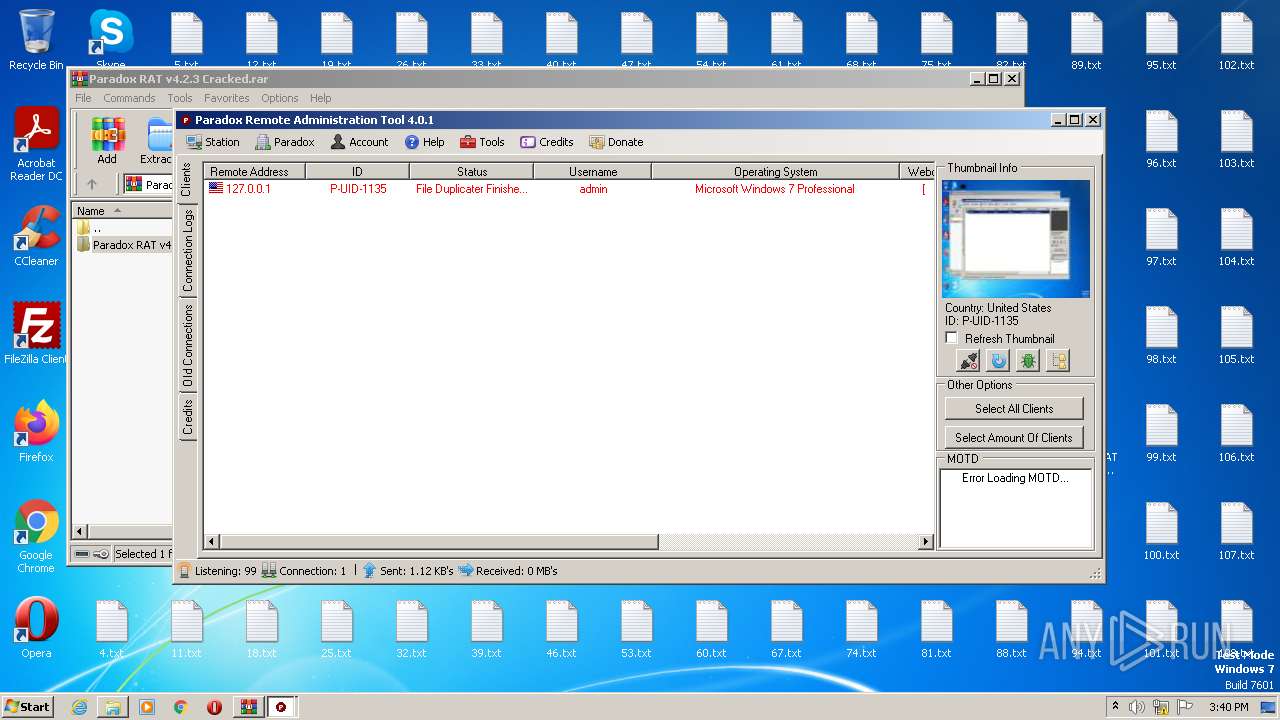
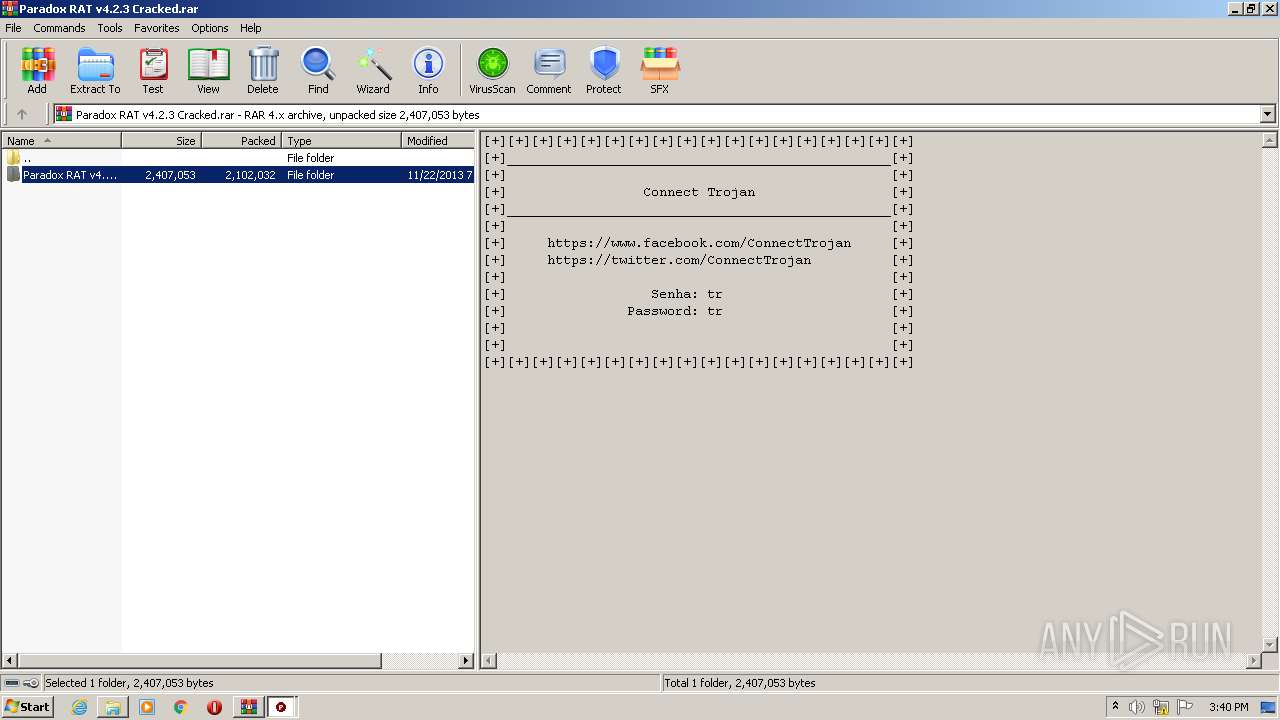
| File name: | Paradox RAT v4.2.3 Cracked.rar |
| Full analysis: | https://app.any.run/tasks/252ebe96-d32b-45b9-ad55-33bec9563ebd |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2023, 15:36:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | BDF1AB7F055F70776B2476332B2508A2 |
| SHA1: | B2F070AB9D8312BB6599D6030998AA6E451359A6 |
| SHA256: | D5033F8715CE5BD5DB3FF90B383770AFF79136DB5DC14D74CBB99BAD59095E68 |
| SSDEEP: | 49152:lYDO0rza7ydsctw1wZ2xL8fCET+VfzHVRY:a6CMyKct8wZ2OfCikfY |
MALICIOUS
Application was dropped or rewritten from another process
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
Drops the executable file immediately after the start
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
Connects to unusual port
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
Reads the Internet Settings
- Updater.exe (PID: 3008)
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
Executable content was dropped or overwritten
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
INFO
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2672)
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2672)
Manual execution by a user
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2672)
Checks supported languages
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
Creates files in the program directory
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
Creates files or folders in the user directory
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- arawerser.exe (PID: 3112)
Reads the computer name
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
Reads Environment values
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
Reads the machine GUID from the registry
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
The process checks LSA protection
- Paradox RAT 4.2.3 Cracked.exe (PID: 188)
- Updater.exe (PID: 3008)
- arawerser.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | Paradox RAT v4.2.3 Cracked\Database.txt |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2013:11:22 19:59:54 |
| OperatingSystem: | Win32 |
| UncompressedSize: | - |
| CompressedSize: | 89 |
Total processes
52
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\Paradox RAT 4.2.3 Cracked.exe" | C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\Paradox RAT 4.2.3 Cracked.exe | explorer.exe | ||||||||||||
User: admin Company: Paradox Coding Integrity Level: MEDIUM Description: Paradox RAT 4.0 Exit code: 0 Version: 4.0.8.0 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\Updater.exe" | C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\Updater.exe | explorer.exe | ||||||||||||
User: admin Company: Paradox Coding Inc Integrity Level: MEDIUM Description: Paradox Update Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3112 | "C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\arawerser.exe" | C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\arawerser.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
12 974
Read events
12 882
Write events
86
Delete events
6
Modification events
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (188) Paradox RAT 4.2.3 Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (188) Paradox RAT 4.2.3 Cracked.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E0000000C000000000000000B00000001000000020000000D00000007000000060000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
Executable files
6
Suspicious files
32
Text files
1 998
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2672.41227\Paradox RAT v4.2.3 Cracked\Settings.ini | ini | |
MD5:— | SHA256:— | |||
| 188 | Paradox RAT 4.2.3 Cracked.exe | C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\arawerser.exe | executable | |
MD5:— | SHA256:— | |||
| 188 | Paradox RAT 4.2.3 Cracked.exe | C:\ProgramData\DYA_CABFHNOWBPPHTAFRR\1.0.0\Data\app.dat | binary | |
MD5:4C4DDA39E883DAAB216E73A069FCD2EF | SHA256:05B16F5A1B15033F0F5EDB0BE29D8C6867F81CB501AAF42C3AE35059CEC6A61B | |||
| 188 | Paradox RAT 4.2.3 Cracked.exe | C:\Users\admin\AppData\Roaming\DYA_CABFHNOWBPPHTAFRR\1.0.0\Data\dya.dat | binary | |
MD5:4C74BAF7B3F144027E8E72F09037A1AD | SHA256:2A8232561DCC2C0E555145D9DD5273A1B058C29498BD874EFB297C2F9075D1BE | |||
| 188 | Paradox RAT 4.2.3 Cracked.exe | C:\ProgramData\DYA_CABFHNOWBPPHTAFRR\1.0.0:$SS_DESCRIPTOR_SBXNV9VVGV1BFLVHNF1HJ2B3MFLBJTV1KBXV36JFSPF7VB4VP4GV | binary | |
MD5:D84987E02C6BCB22A99923A9036BAA82 | SHA256:1B366175BF7779558F9BE9F75392704523955292E1A9212BBC62ECA000783622 | |||
| 2672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2672.41227\Paradox RAT v4.2.3 Cracked\Paradox RAT 4.2.3 Cracked.exe | executable | |
MD5:4674151265EE5F4C33AB71FCA3662031 | SHA256:FC53DEDFA564864E96EBF7839232E0C3B998070479E5C25CB5351F4613E5DBEF | |||
| 188 | Paradox RAT 4.2.3 Cracked.exe | C:\ProgramData:$SS_DESCRIPTOR_SBXNV9VVGV1BFLVHNF1HJ2B3MFLBJTV1KBXV36JFSPF7VB4VP4GV | binary | |
MD5:8D45B315B1BBFBA59A613575FACB3044 | SHA256:A00C54685419AE5BA1B509B37CA8C2FB420CA4FB9EE16519BB5DD4A96110D355 | |||
| 188 | Paradox RAT 4.2.3 Cracked.exe | C:\ProgramData\DYA_CABFHNOWBPPHTAFRR\1.0.0\Data\updates.dat | binary | |
MD5:C4DD250A4FFFBA7F74CE24CB3A17520B | SHA256:5FA173893BDB515B6A18ECBA2DE838EE7F4DDBF4EB2FD50E9B46353736612296 | |||
| 3112 | arawerser.exe | C:\Users\admin\Desktop\Paradox RAT v4.2.3 Cracked\Logs.txt | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 3112 | arawerser.exe | C:\Users\admin\Desktop\2.txt | binary | |
MD5:C81E728D9D4C2F636F067F89CC14862C | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
4
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3008 | Updater.exe | GET | 301 | 162.125.66.15:80 | http://dl.dropbox.com/u/23639317/Paradox/Version.txt | DE | — | — | shared |
188 | Paradox RAT 4.2.3 Cracked.exe | GET | 301 | 162.125.66.15:80 | http://dl.dropbox.com/u/23639317/Paradox/Version.txt | DE | — | — | shared |
188 | Paradox RAT 4.2.3 Cracked.exe | GET | 301 | 162.125.66.15:80 | http://dl.dropbox.com/u/23639317/Paradox/MOTD.txt | DE | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
188 | Paradox RAT 4.2.3 Cracked.exe | 162.125.66.15:80 | dl.dropbox.com | DROPBOX | DE | malicious |
188 | Paradox RAT 4.2.3 Cracked.exe | 162.125.66.15:443 | dl.dropbox.com | DROPBOX | DE | malicious |
188 | Paradox RAT 4.2.3 Cracked.exe | 94.73.33.36:81 | vpslogin1.no-ip.info | Xtra Telecom S.A. | ES | malicious |
3008 | Updater.exe | 162.125.66.15:80 | dl.dropbox.com | DROPBOX | DE | malicious |
3008 | Updater.exe | 162.125.66.15:443 | dl.dropbox.com | DROPBOX | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vpslogin1.no-ip.info |
| malicious |
dl.dropbox.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
5 ETPRO signatures available at the full report