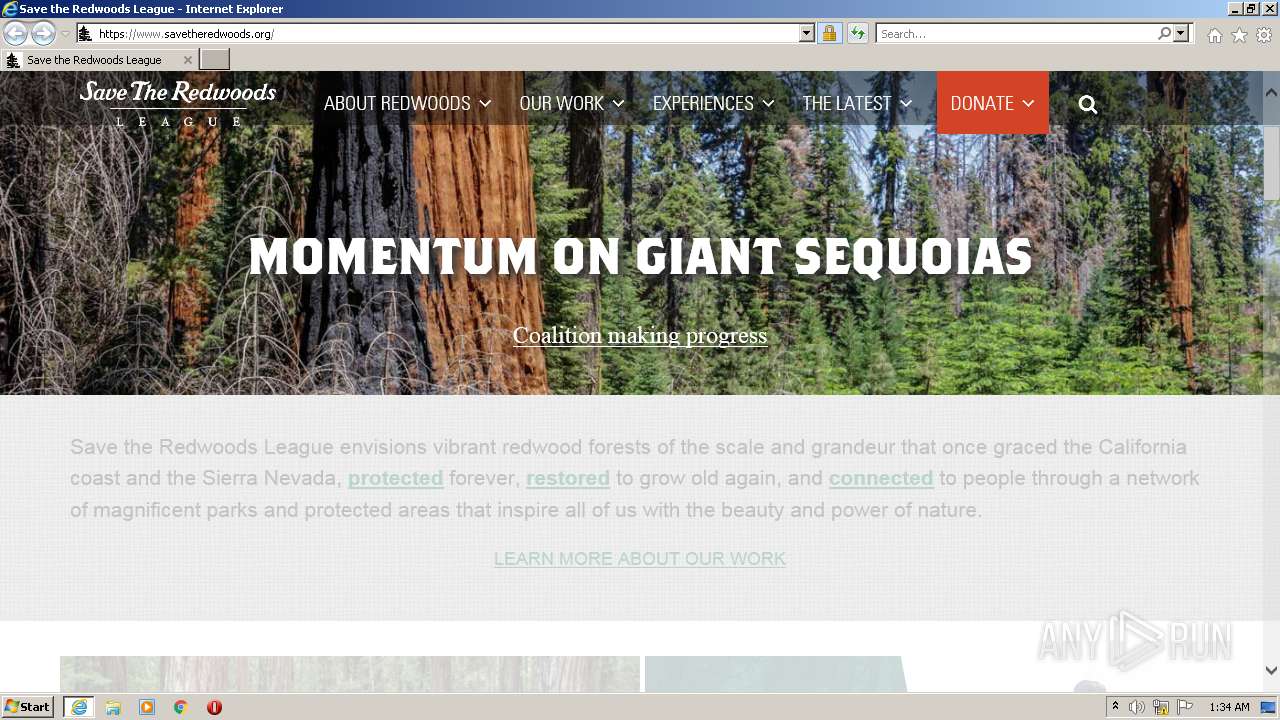
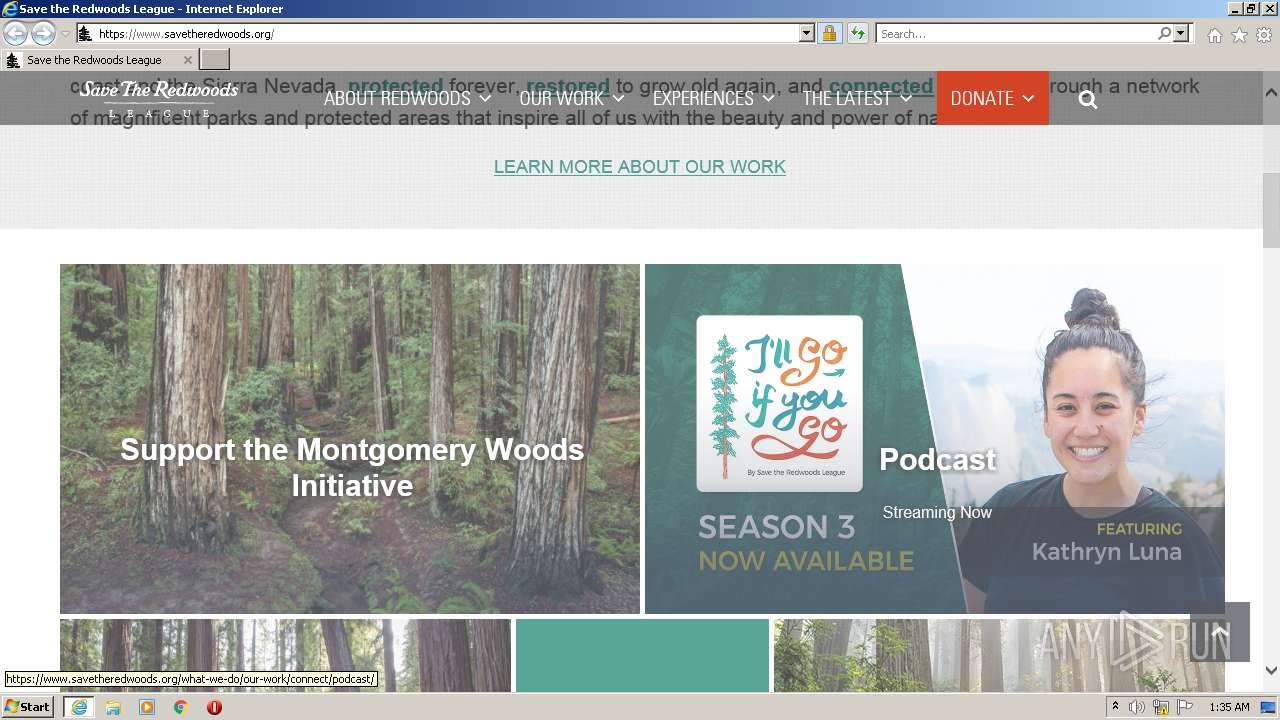
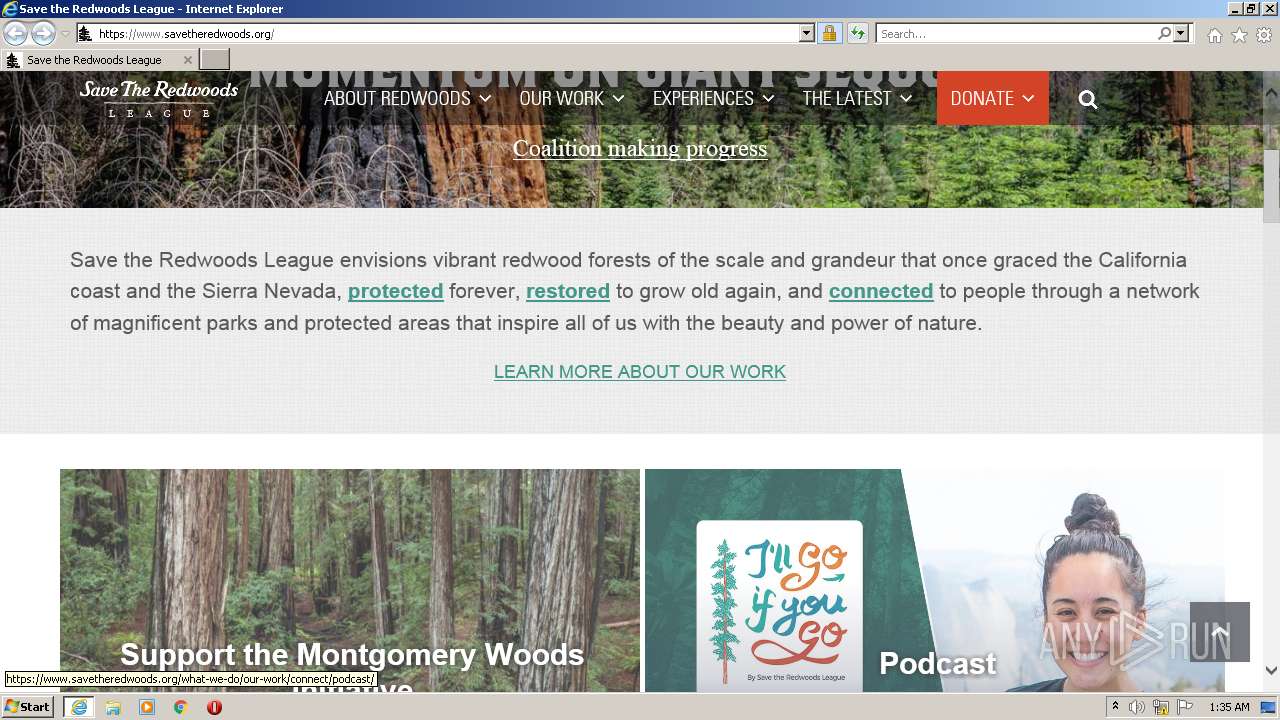
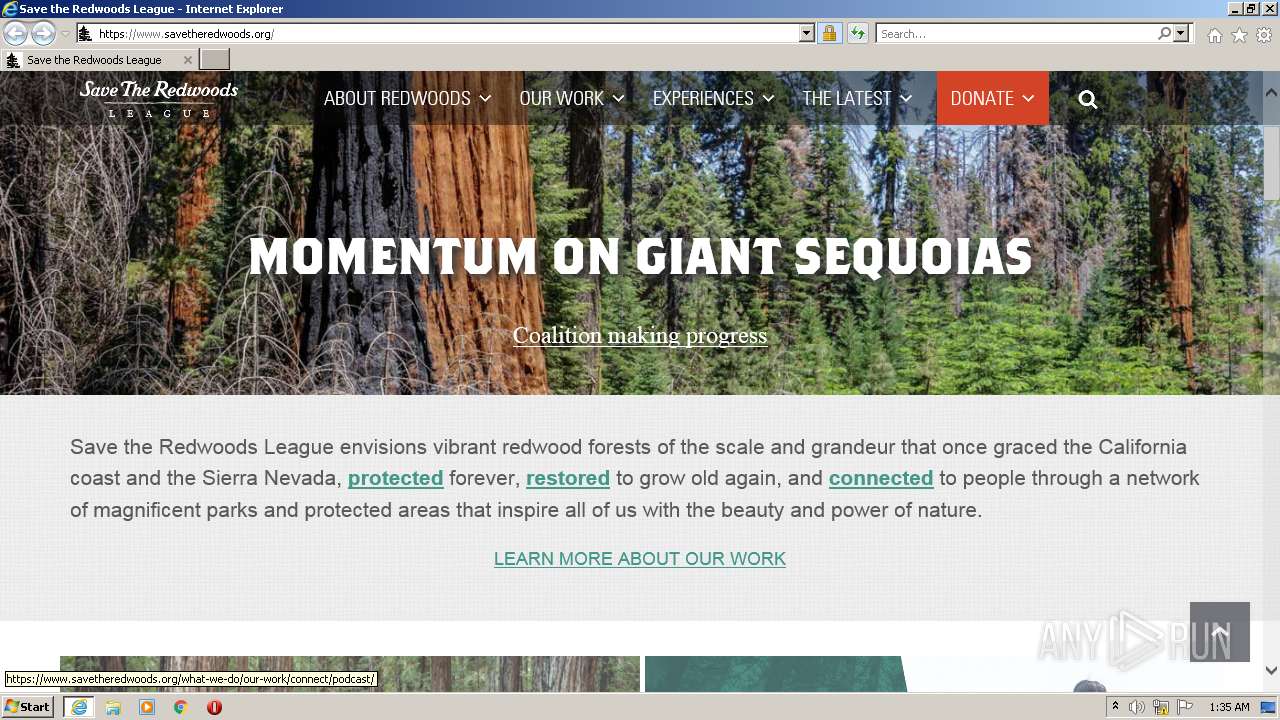
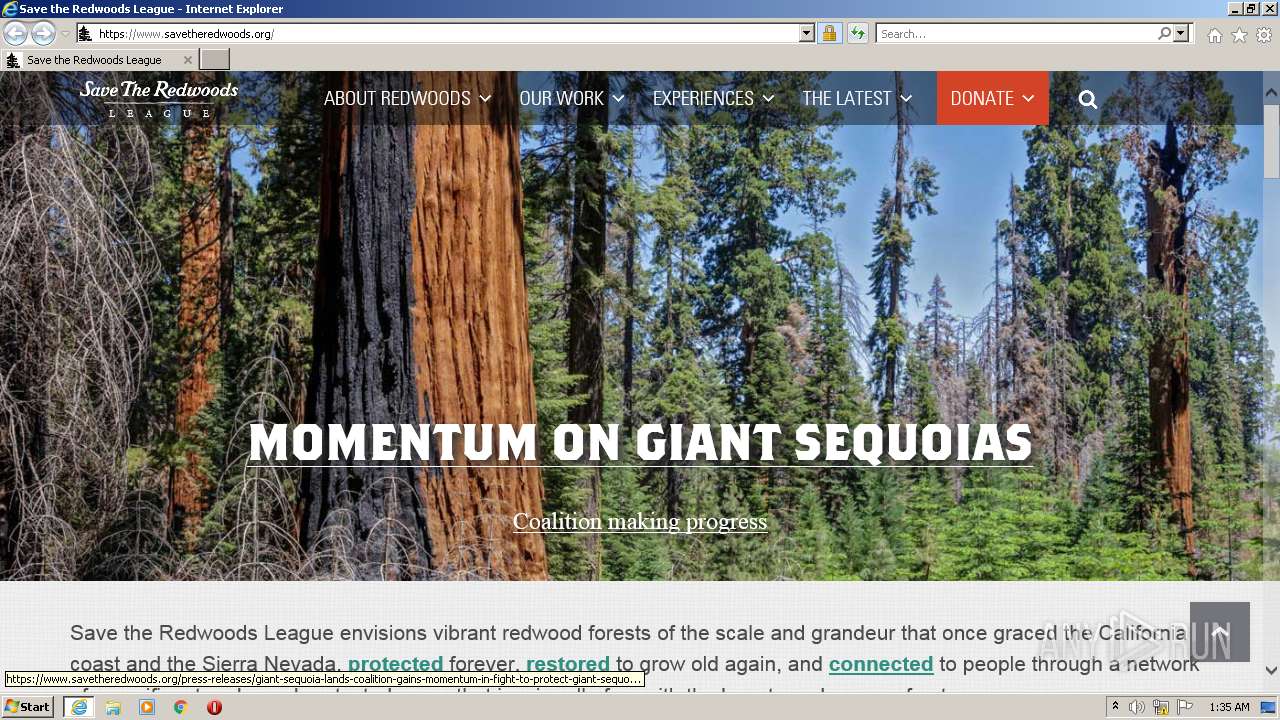
| URL: | http://savetheredwoods.org |
| Full analysis: | https://app.any.run/tasks/2e823e33-6107-4c37-99b0-762433fae945 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 00:34:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 693A1214D8F41346AD6CF1BF46F342E1 |
| SHA1: | 33B7867EE2F9B726D0378A2F5480CCFD31CB7EF9 |
| SHA256: | D4E23F94C7D583E5F471C1832BB227058E39816A05093D7F37DB494ACF0BC08E |
| SSDEEP: | 3:N1KNET0AKaLXCn:CWYAnjCn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Create files in a temporary directory
- iexplore.exe (PID: 616)
Application launched itself
- iexplore.exe (PID: 616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://savetheredwoods.org" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1656 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:616 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
29 814
Read events
29 606
Write events
208
Delete events
0
Modification events
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
52
Text files
148
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\VN2BGKLA.htm | html | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\QUC0EWML.htm | html | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\76QT2ZGJ | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
| 1656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
69
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
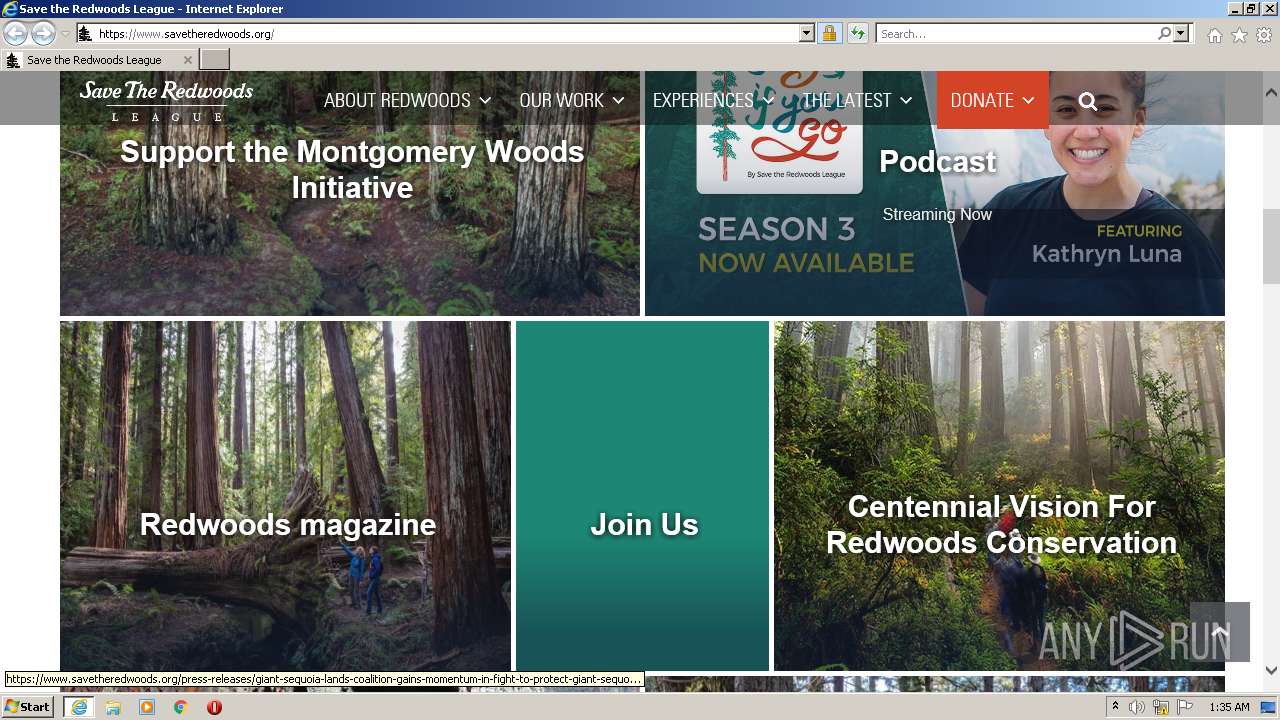
1656 | iexplore.exe | GET | 301 | 104.26.15.12:80 | http://savetheredwoods.org/ | US | — | — | suspicious |
1656 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
1656 | iexplore.exe | GET | 200 | 52.222.250.42:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | US | der | 1.39 Kb | shared |
1656 | iexplore.exe | GET | 200 | 2.16.187.26:80 | http://ocsp.vikingcloud.com//MFQwUjBQME4wTDAJBgUrDgMCGgUABBQ1mI4Ww4R5LZiQ295pj4OF%2F44yyAQUyk7dWyc1Kdn27sPlU%2B%2BkwBmWHa8CEwdrnIOiQP6Ksw2OiV0fRH0WmQ4%3D | unknown | der | 1.54 Kb | suspicious |
1656 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
616 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
1656 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD%2FB2zZ7cy1JAocIdUzcD8Q | US | der | 472 b | whitelisted |
1656 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCB%2B40Ok%2BQw3T | US | der | 1.74 Kb | whitelisted |
1656 | iexplore.exe | GET | 200 | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
1656 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA31XsESAKYiuBD9ZUgF0DE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1656 | iexplore.exe | 104.26.15.12:80 | www.savetheredwoods.org | CLOUDFLARENET | US | unknown |
616 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
616 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1656 | iexplore.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | suspicious |
1656 | iexplore.exe | 104.18.11.207:443 | maxcdn.bootstrapcdn.com | CLOUDFLARENET | — | suspicious |
1656 | iexplore.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
1656 | iexplore.exe | 52.222.250.185:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
1656 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1656 | iexplore.exe | 52.222.250.42:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
1656 | iexplore.exe | 192.124.249.24:80 | ocsp.godaddy.com | SUCURI-SEC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.savetheredwoods.org |
| unknown |
tags.wdsvc.net |
| unknown |
d3rse9xjbp8270.cloudfront.net |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |