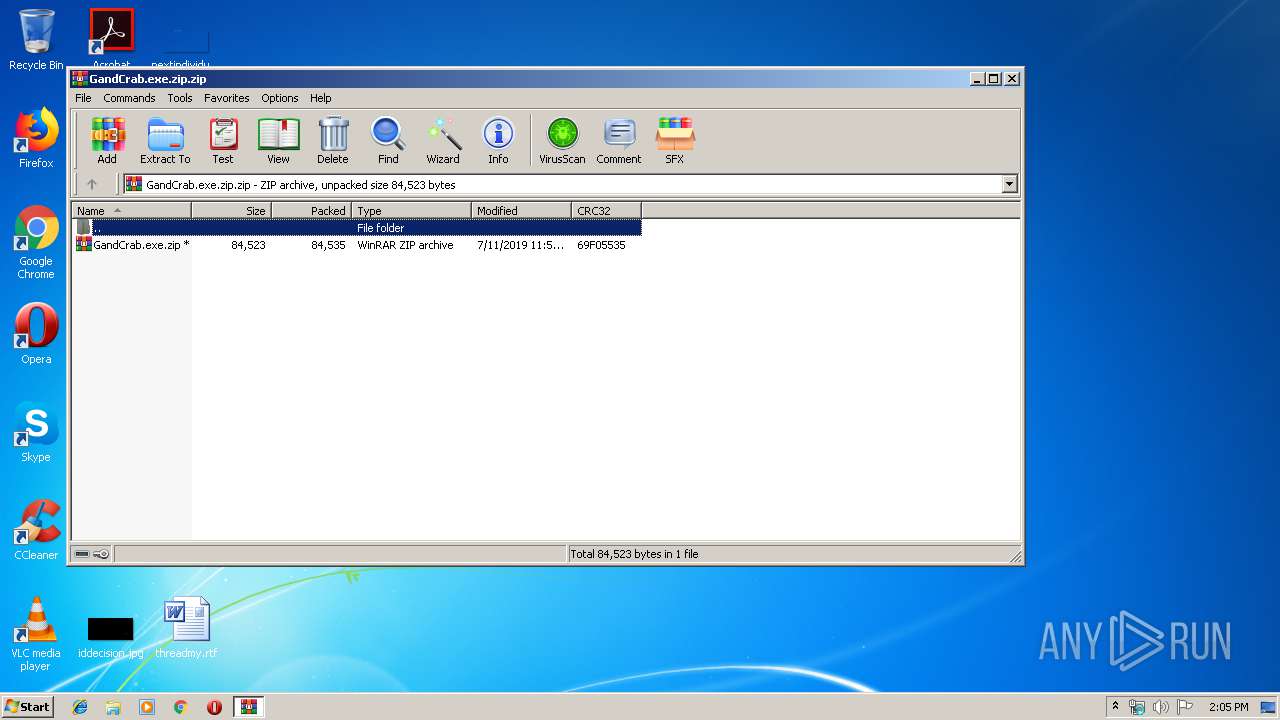
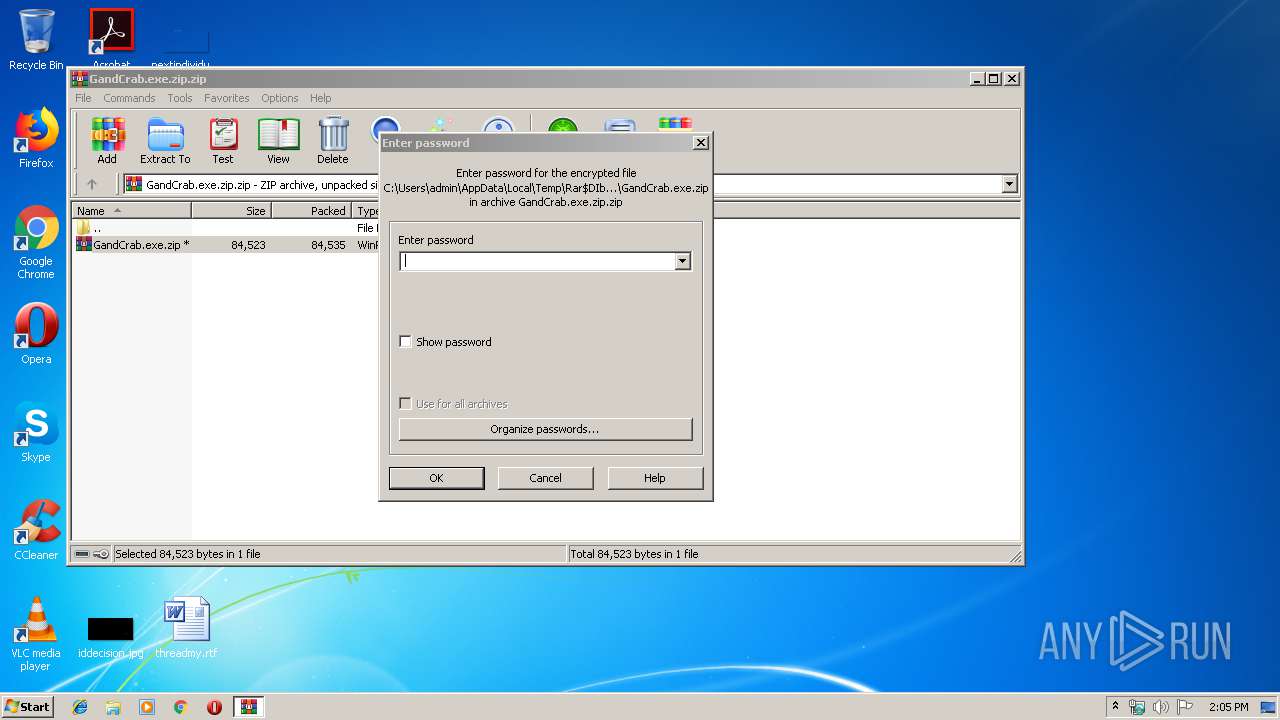
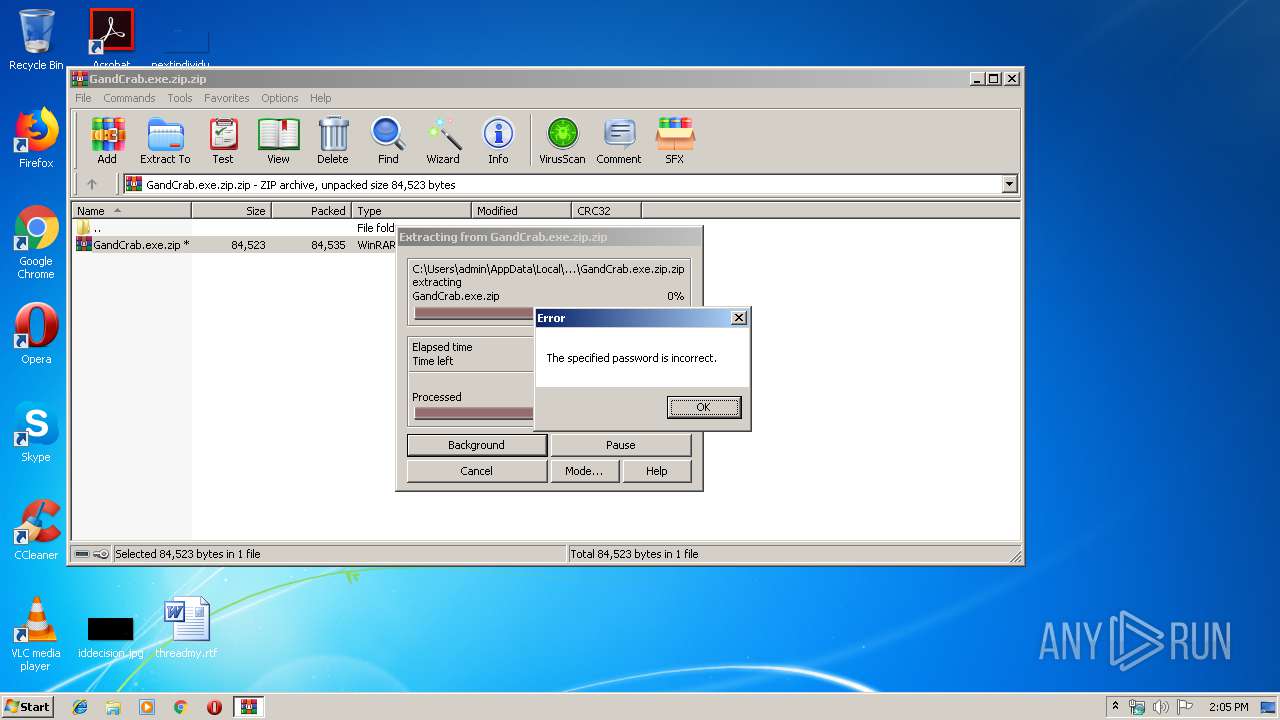
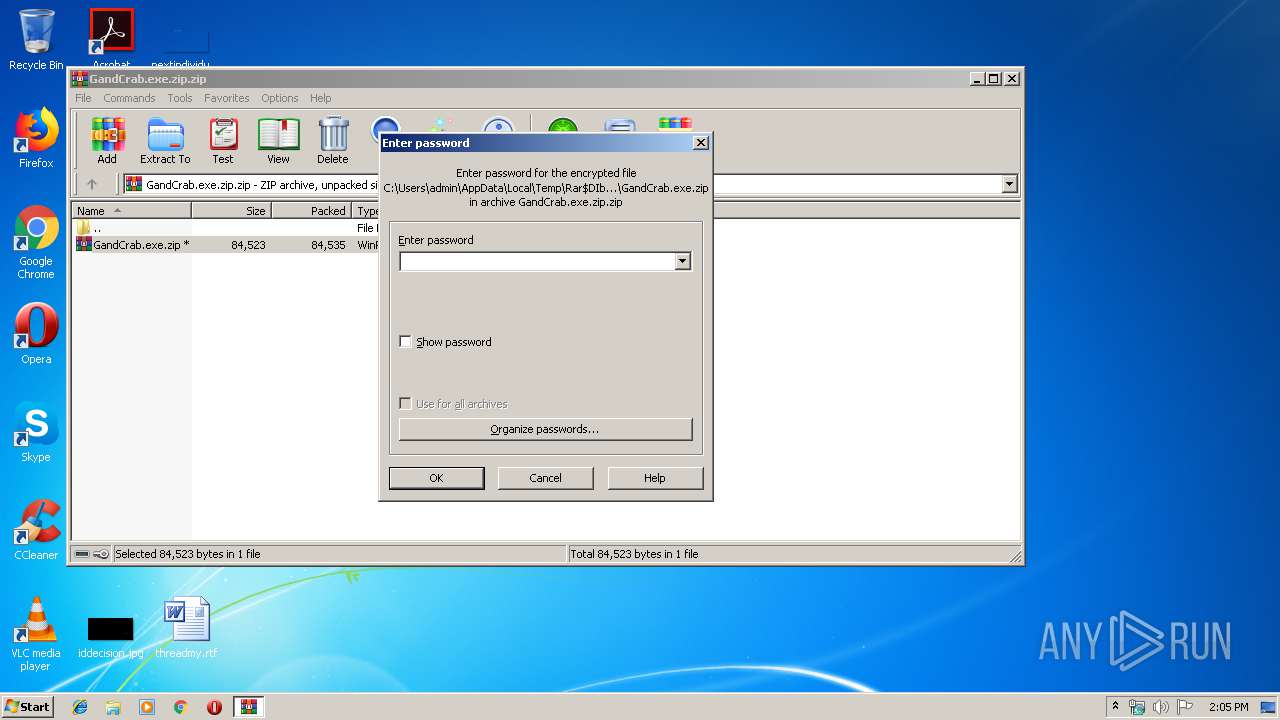
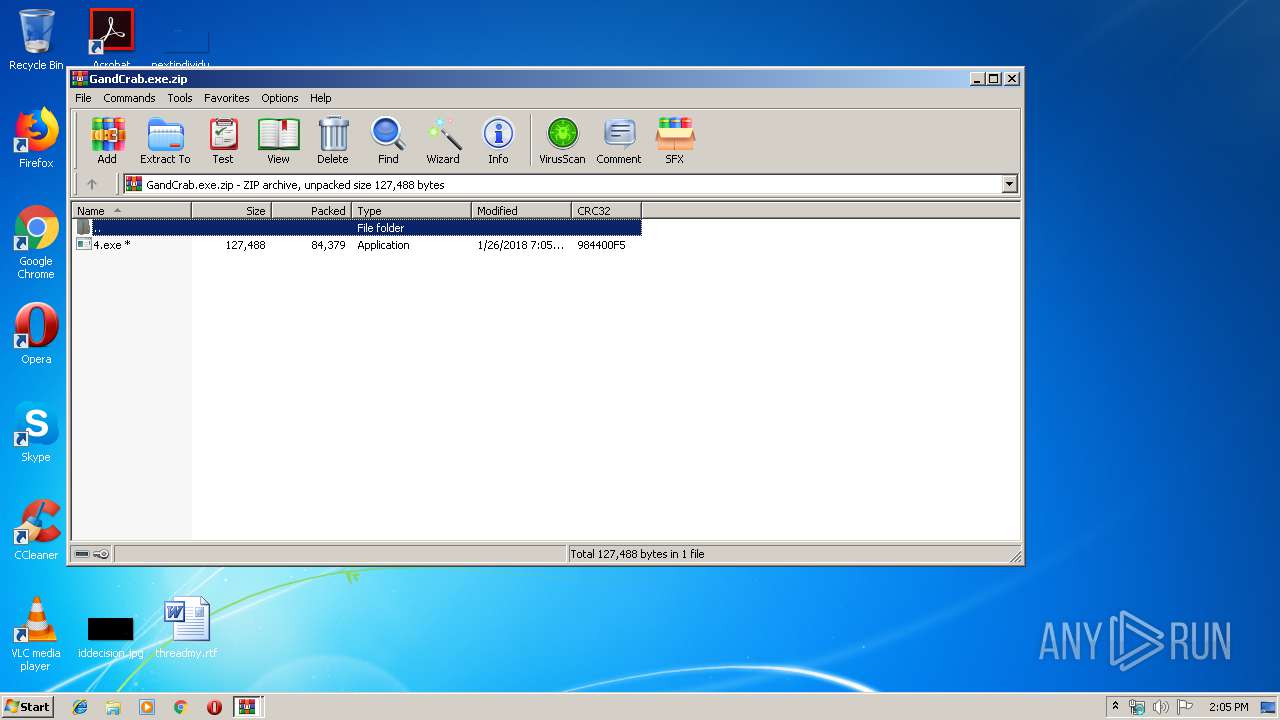
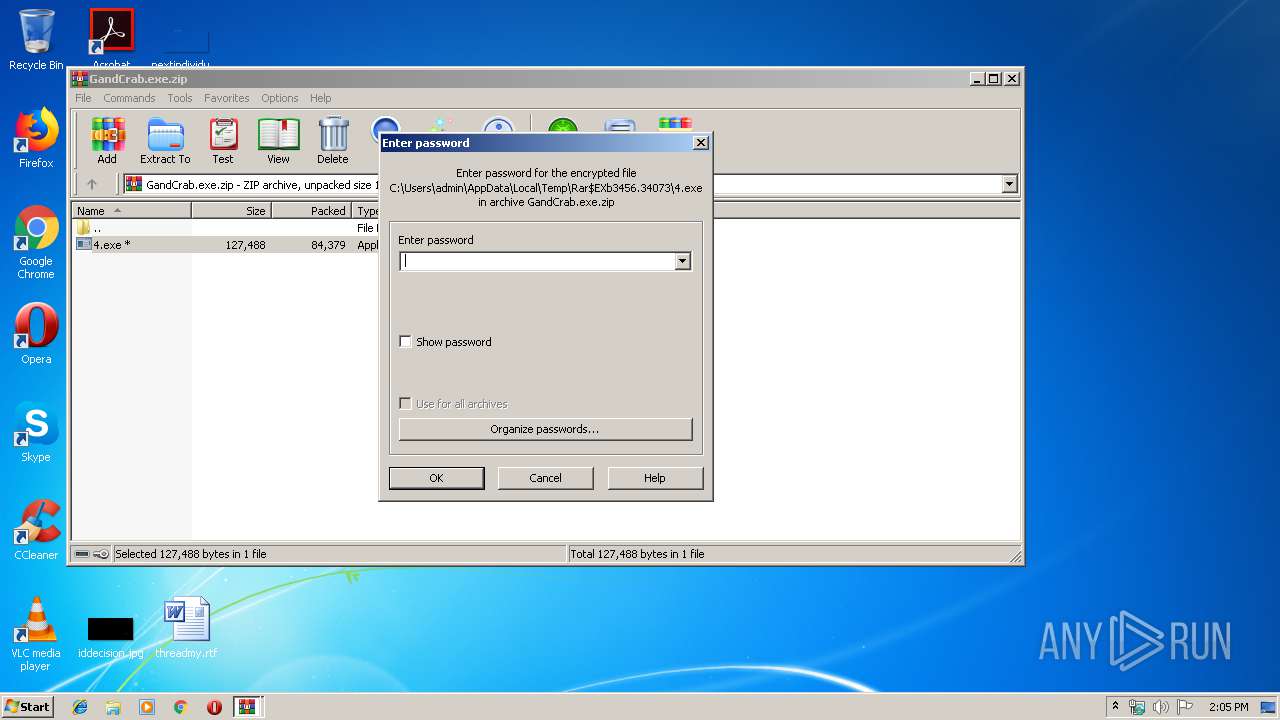
| File name: | GandCrab.exe.zip.zip |
| Full analysis: | https://app.any.run/tasks/d14c217e-6907-4637-81bd-fd4dfb3a808a |
| Verdict: | Malicious activity |
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | July 11, 2019, 13:05:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D72A8E2C2B73056F22106DD041C1B618 |
| SHA1: | A8701545357B546AD838DF8FA9841957F1739B92 |
| SHA256: | D4DC112E3632645BF575B8DF99CF4D84D63DB15D0091677F4067DDD365E01081 |
| SSDEEP: | 1536:ht0J7OqCkRDRD3aKf9cwAVmNrBAYZHQtgOi1rTl570yA/mBazMuRRcbCmm:HqCkvGKf/A0NrPVQtgv57YmwzMuR8m |
MALICIOUS
Application was dropped or rewritten from another process
- 4.exe (PID: 2968)
Changes the autorun value in the registry
- 4.exe (PID: 2968)
GANDCRAB was detected
- nslookup.exe (PID: 2268)
- nslookup.exe (PID: 3760)
- nslookup.exe (PID: 3316)
- nslookup.exe (PID: 1768)
- nslookup.exe (PID: 3324)
- nslookup.exe (PID: 3212)
- nslookup.exe (PID: 3920)
- nslookup.exe (PID: 1740)
- nslookup.exe (PID: 2840)
- nslookup.exe (PID: 3448)
- nslookup.exe (PID: 3108)
- nslookup.exe (PID: 2408)
GandCrab detected
- 4.exe (PID: 2968)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3048)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3456)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | None |
| ZipModifyDate: | 2019:07:11 12:58:15 |
| ZipCRC: | 0x69f05535 |
| ZipCompressedSize: | 84535 |
| ZipUncompressedSize: | 84535 |
| ZipFileName: | GandCrab.exe.zip |
Total processes
60
Monitored processes
15
Malicious processes
15
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1740 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2268 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2408 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2840 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2968 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3456.34073\4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3456.34073\4.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 11.0.0.1 Modules
| |||||||||||||||
| 3048 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\GandCrab.exe.zip.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3108 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3316 | nslookup gandcrab.bit a.dnspod.com | C:\Windows\system32\nslookup.exe | 4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
982
Read events
935
Write events
47
Delete events
0
Modification events
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GandCrab.exe.zip.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
1
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | 4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\ipv4bot_whatismyipaddress_com[1].htm | — | |
MD5:— | SHA256:— | |||
| 2968 | 4.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\0f5007522459c86e95ffcc62f32308f1_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:— | SHA256:— | |||
| 3048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3048.33102\GandCrab.exe.zip | compressed | |
MD5:35CEEDC16B0E266D2FABAFCC6C760D91 | SHA256:042BF39F7D33613EB5DD085CBE871A1F1E5C3B9DEE64A4CA9D6D1E5D3B6B3F61 | |||
| 3456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3456.34073\4.exe | executable | |
MD5:A635D6A35C2FC054042B6868EF52A0C3 | SHA256:643F8043C0B0F89CEDBFC3177AB7CFE99A8E2C7FE16691F3D54FB18BC14B8F45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
61
DNS requests
62
Threats
98
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2968 | 4.exe | GET | 200 | 66.171.248.178:80 | http://ipv4bot.whatismyipaddress.com/ | US | text | 15 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3324 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
3108 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
3920 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
2408 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
2840 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
2968 | 4.exe | 66.171.248.178:80 | ipv4bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
3448 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
3316 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
3212 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
2268 | nslookup.exe | 58.251.121.110:53 | a.dnspod.com | China Unicom Shenzen network | CN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipv4bot.whatismyipaddress.com |
| shared |
a.dnspod.com |
| shared |
110.121.251.58.in-addr.arpa |
| unknown |
gandcrab.bit |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2968 | 4.exe | Misc activity | SUSPICIOUS [PTsecurity] IP Check (whatismyipaddress) |
2840 | nslookup.exe | A Network Trojan was detected | ET TROJAN Observed GandCrab Domain (gandcrab .bit) |
2840 | nslookup.exe | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
2840 | nslookup.exe | A Network Trojan was detected | ET TROJAN Observed GandCrab Domain (gandcrab .bit) |
2840 | nslookup.exe | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
2840 | nslookup.exe | A Network Trojan was detected | ET TROJAN Observed GandCrab Domain (gandcrab .bit) |
2840 | nslookup.exe | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
2840 | nslookup.exe | A Network Trojan was detected | ET TROJAN Observed GandCrab Domain (gandcrab .bit) |
2840 | nslookup.exe | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
3448 | nslookup.exe | A Network Trojan was detected | ET TROJAN Observed GandCrab Domain (gandcrab .bit) |
1 ETPRO signatures available at the full report