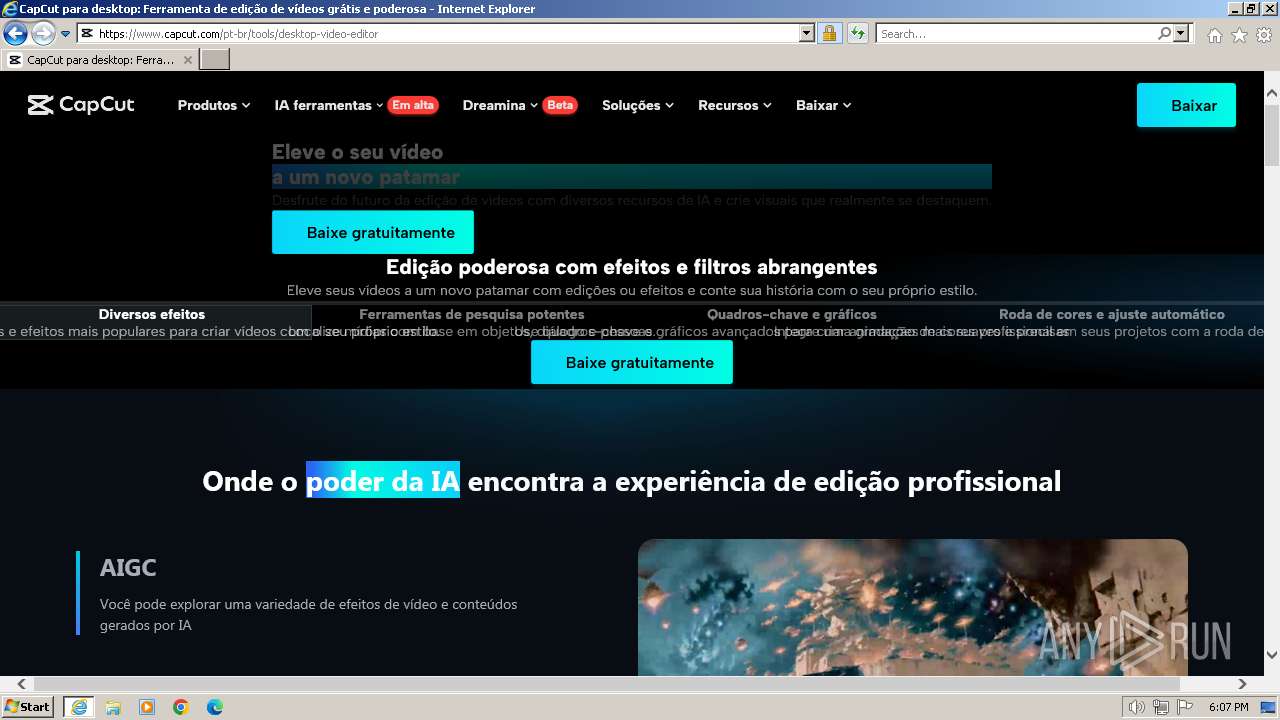
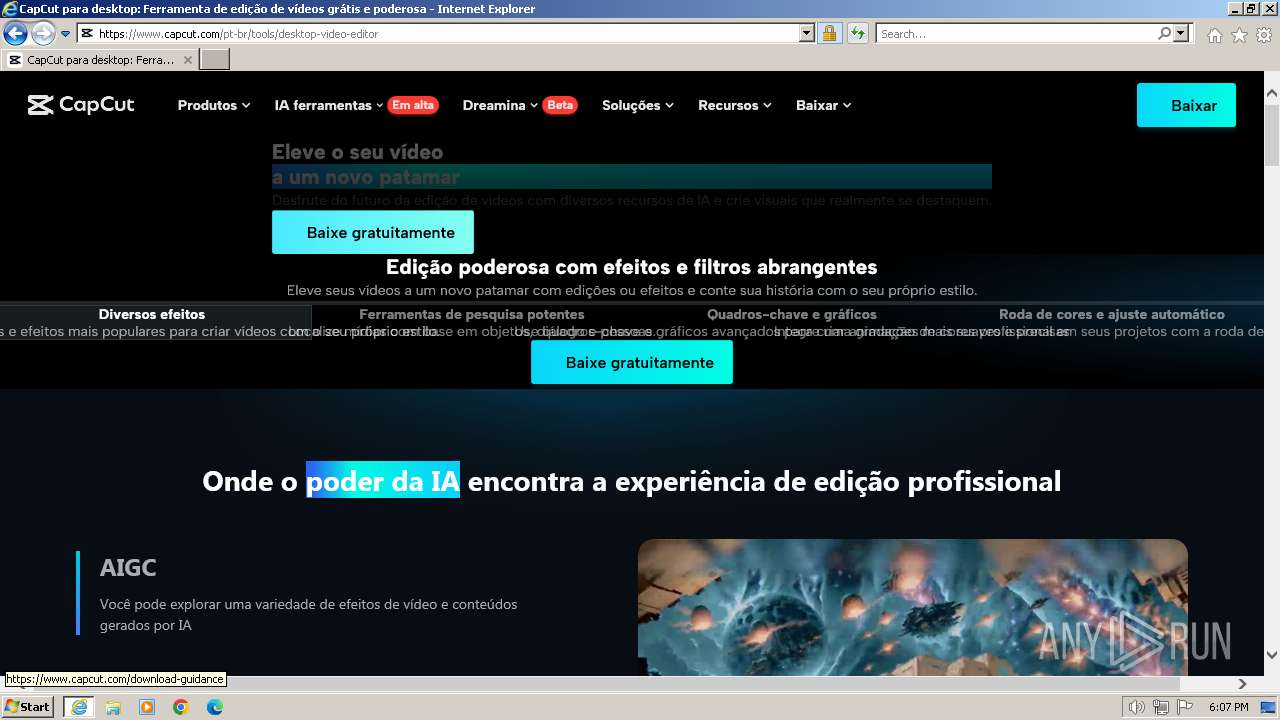
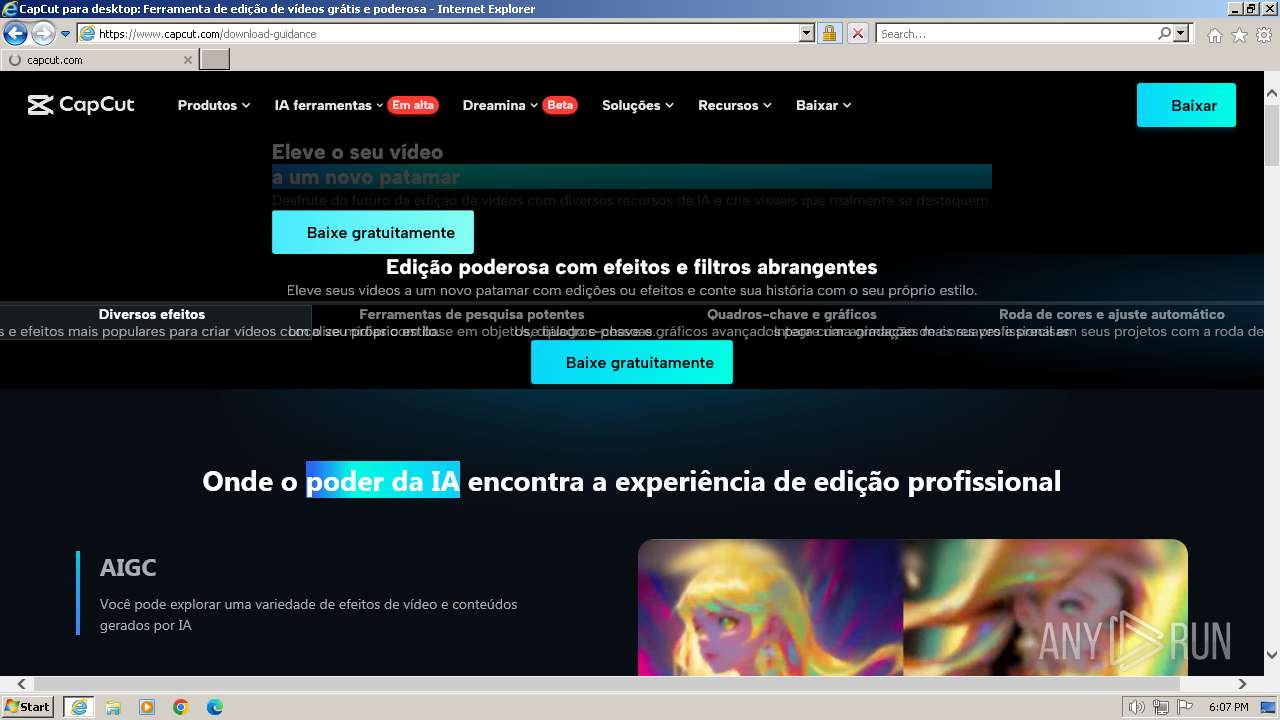
| URL: | google.com |
| Full analysis: | https://app.any.run/tasks/bf455561-b0a7-4c40-98f3-8d0ca2056d2f |
| Verdict: | Malicious activity |
| Analysis date: | June 26, 2024, 17:06:32 |
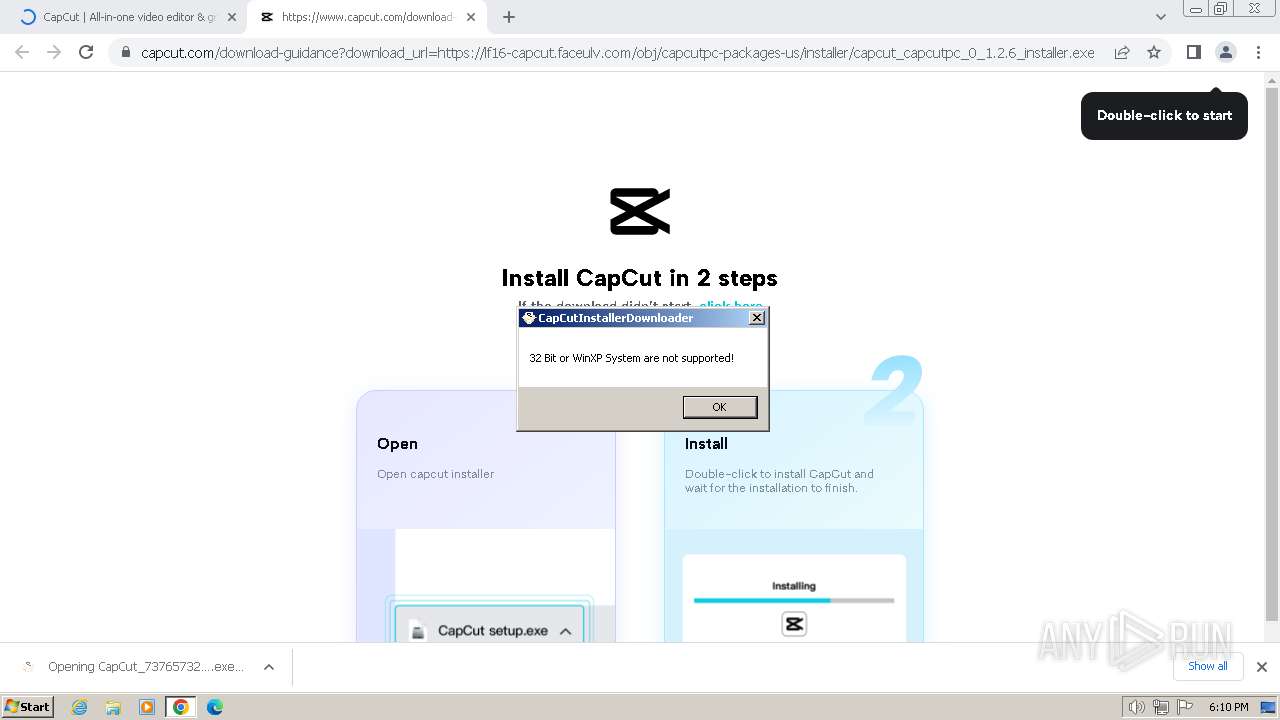
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1D5920F4B44B27A802BD77C4F0536F5A |
| SHA1: | BAEA954B95731C68AE6E45BD1E252EB4560CDC45 |
| SHA256: | D4C9D9027326271A89CE51FCAF328ED673F17BE33469FF979E8AB8DD501E664F |
| SSDEEP: | 3:duK:IK |
MALICIOUS
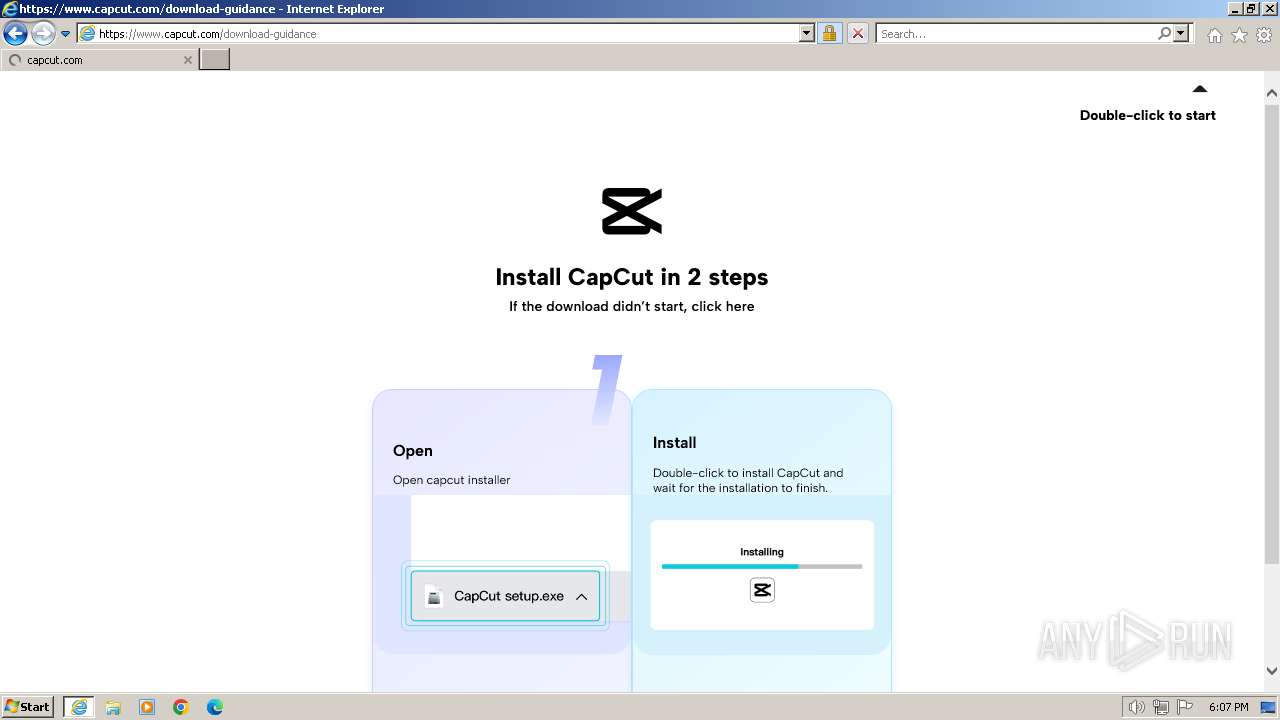
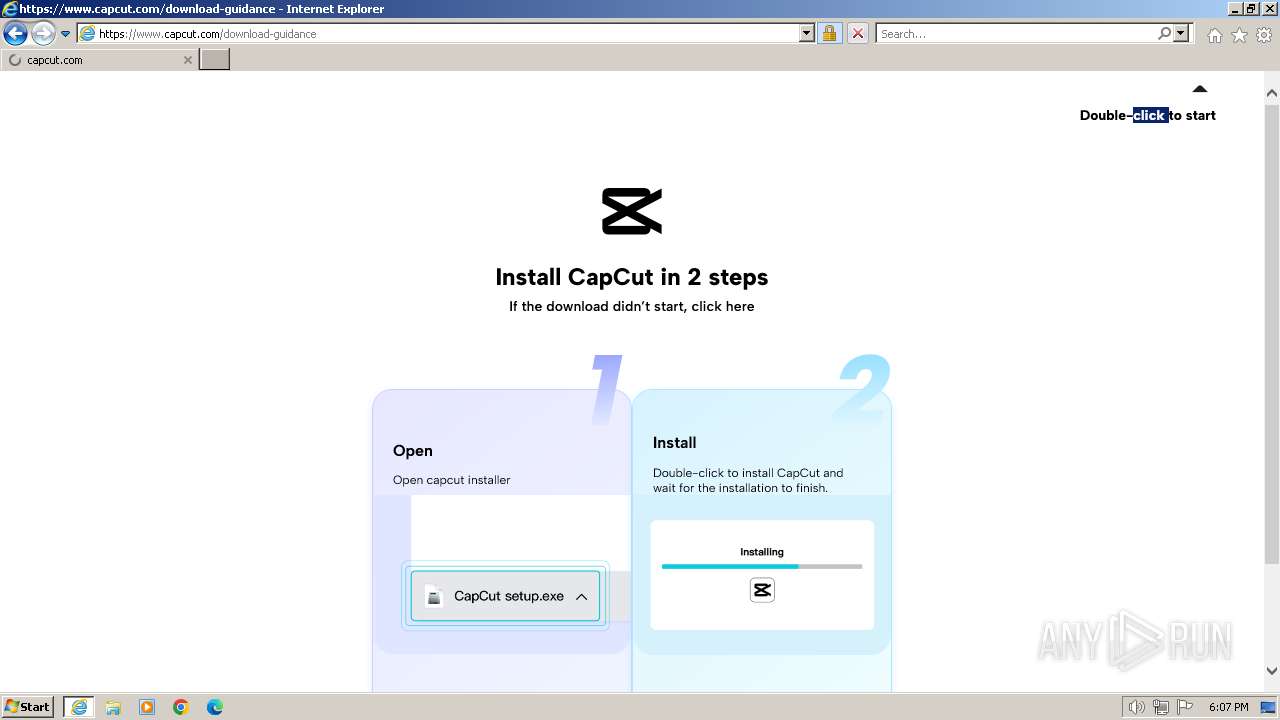
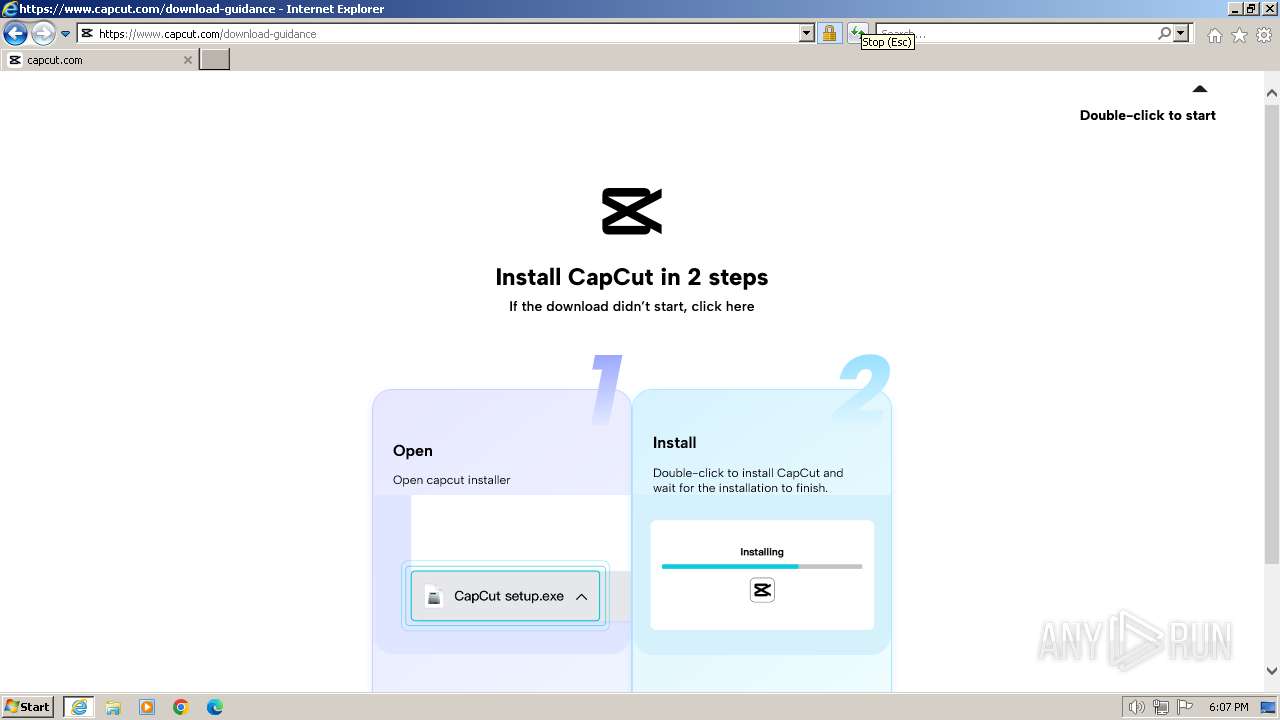
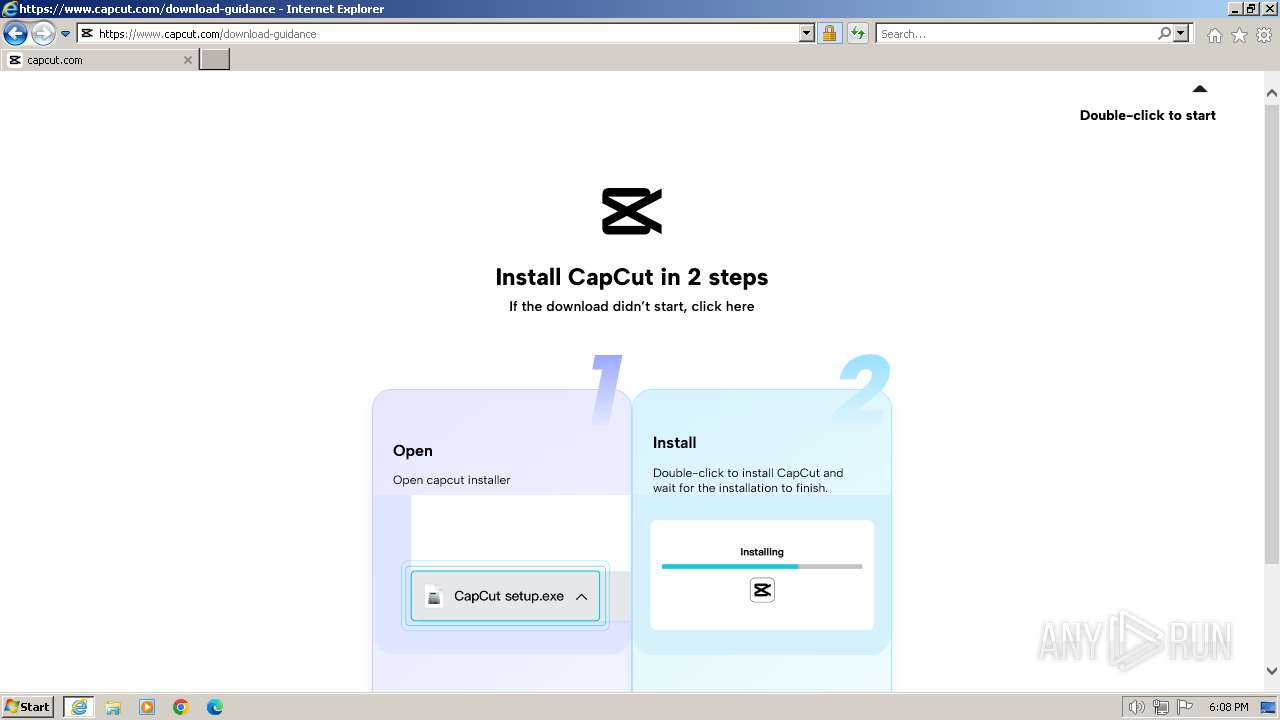
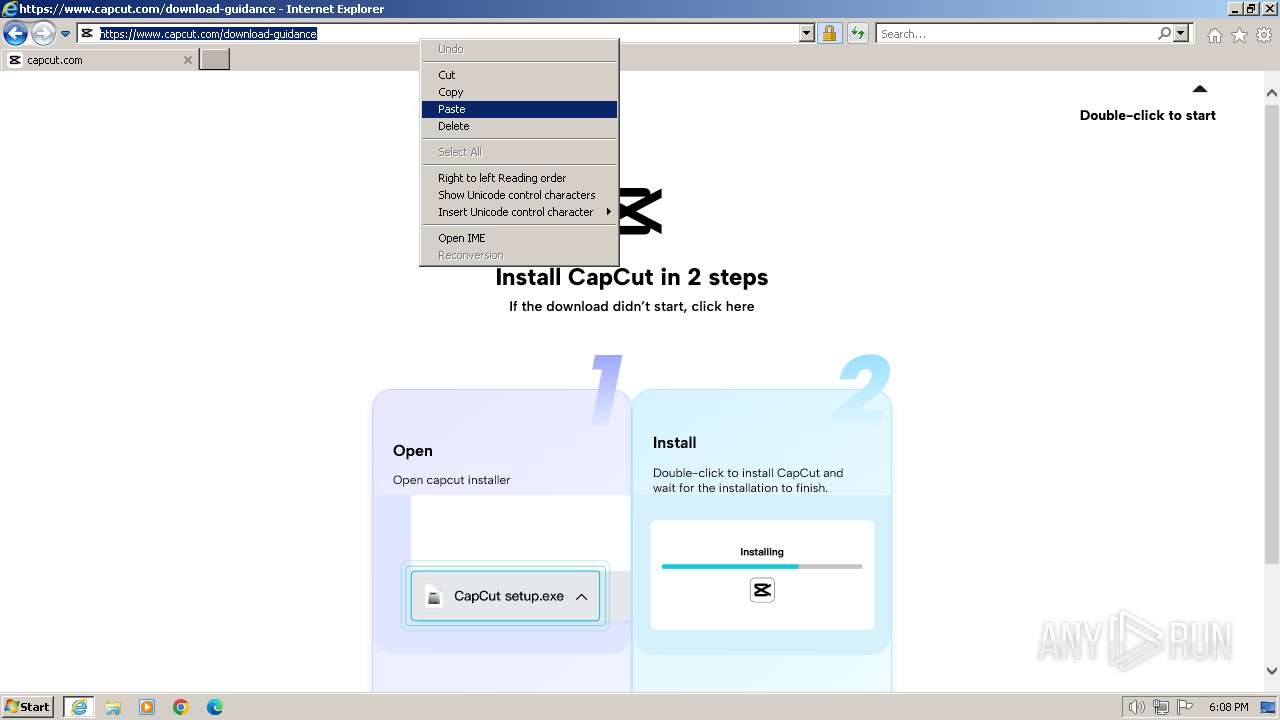
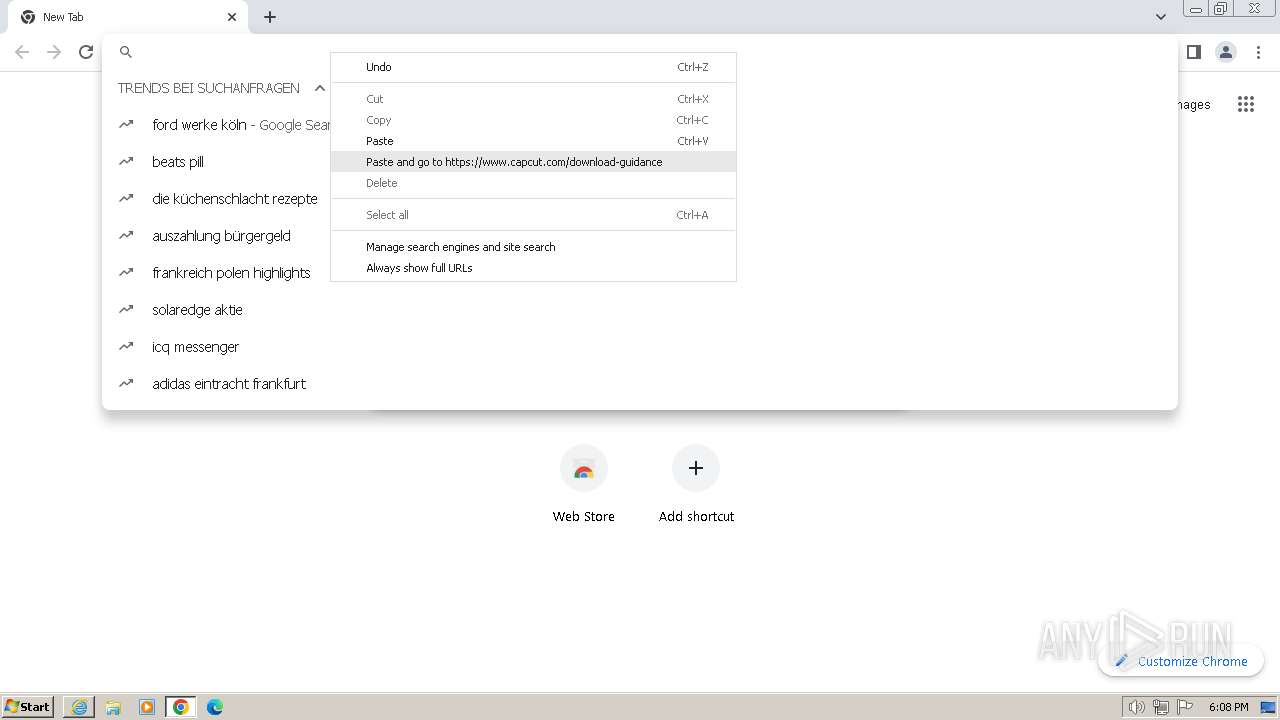
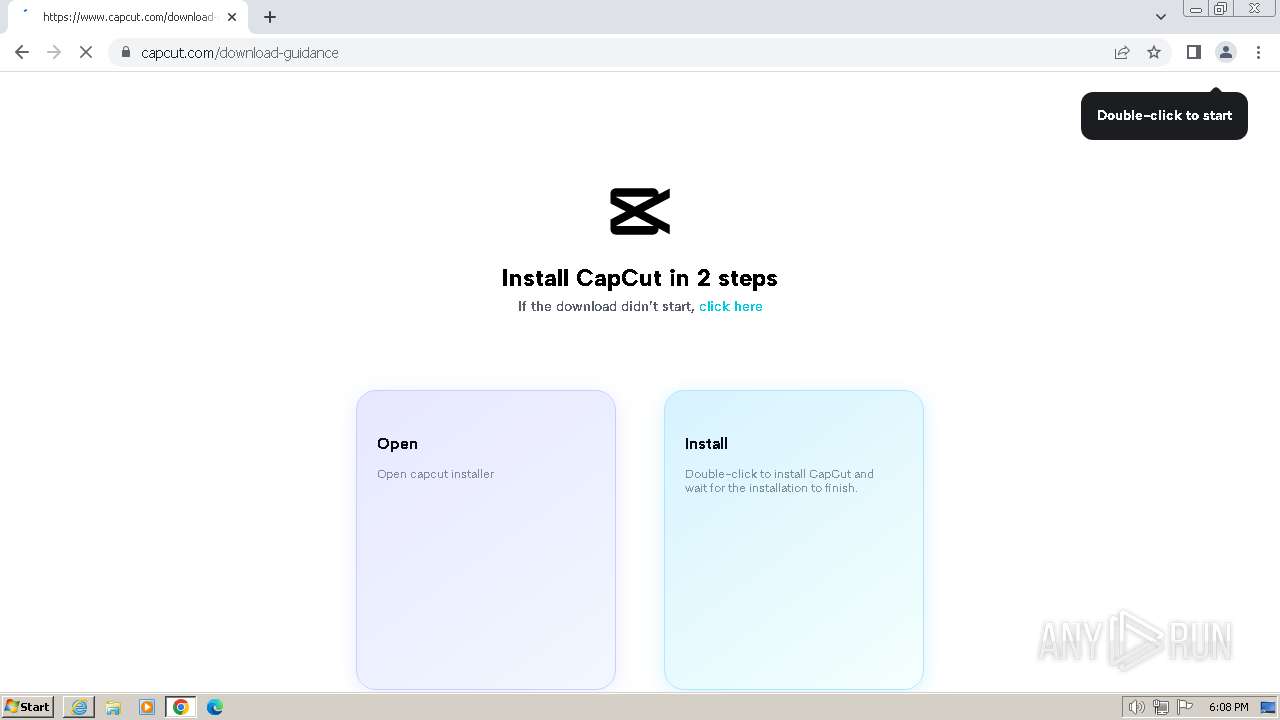
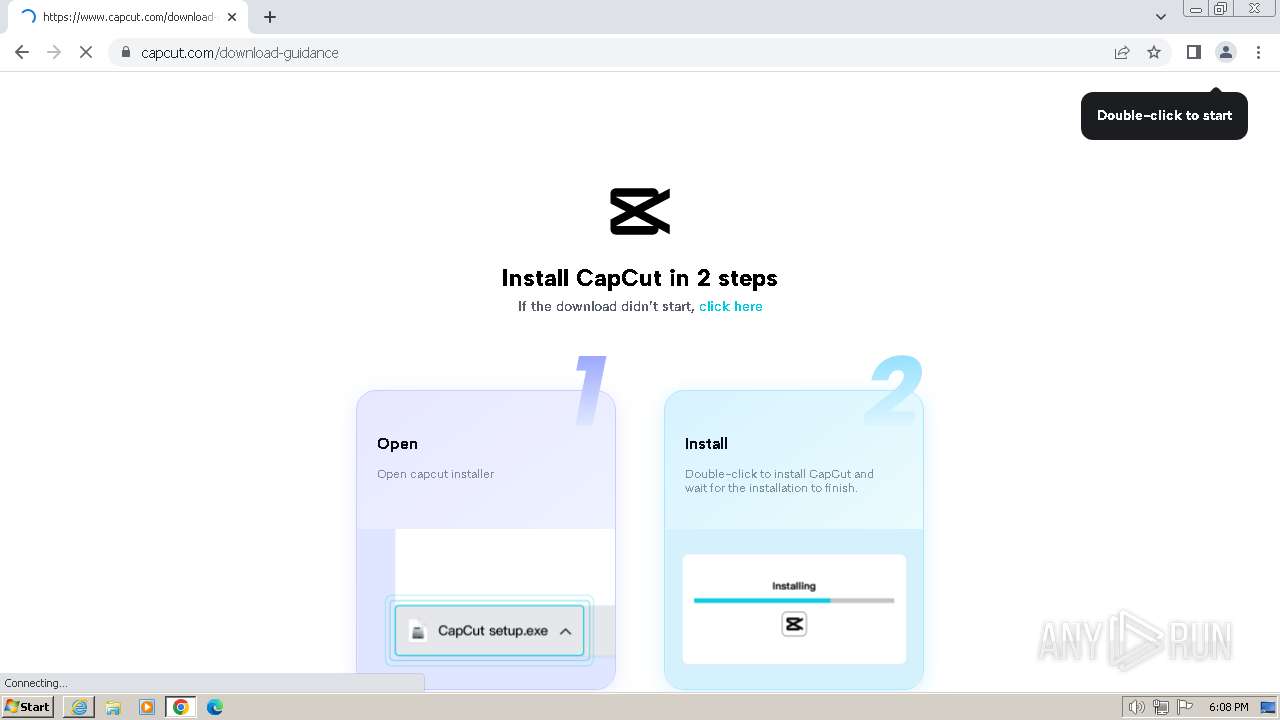
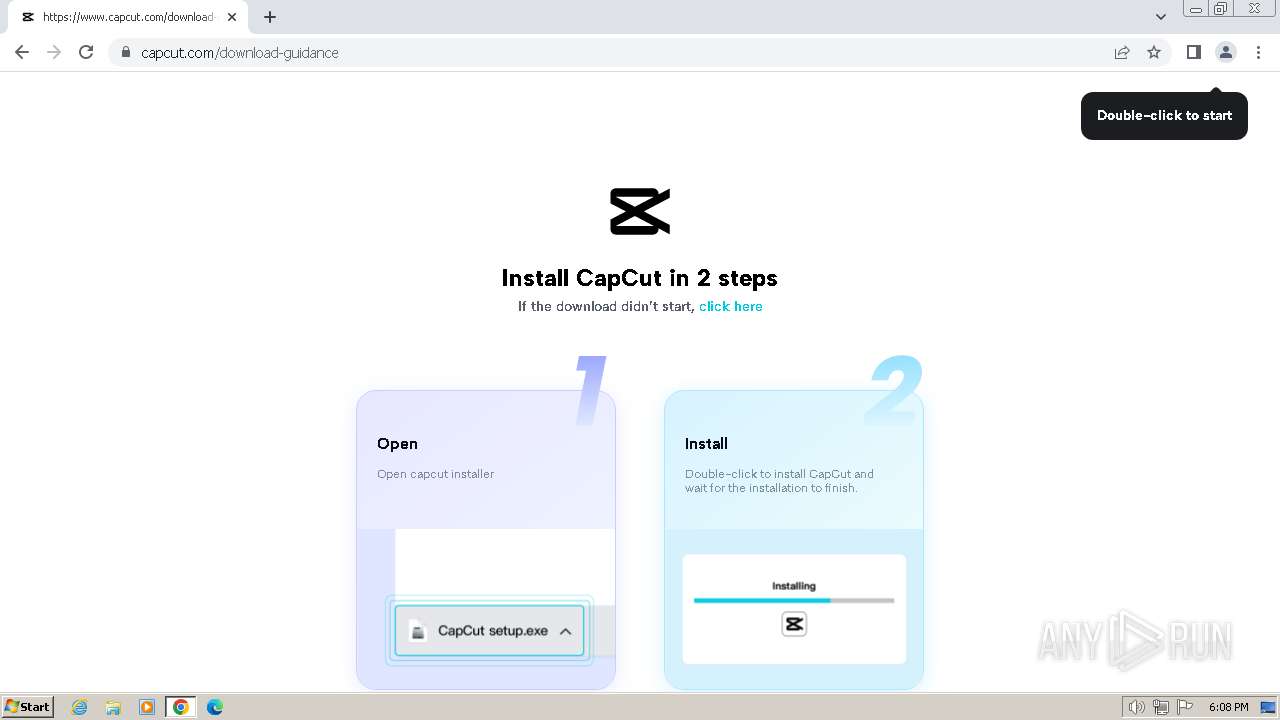
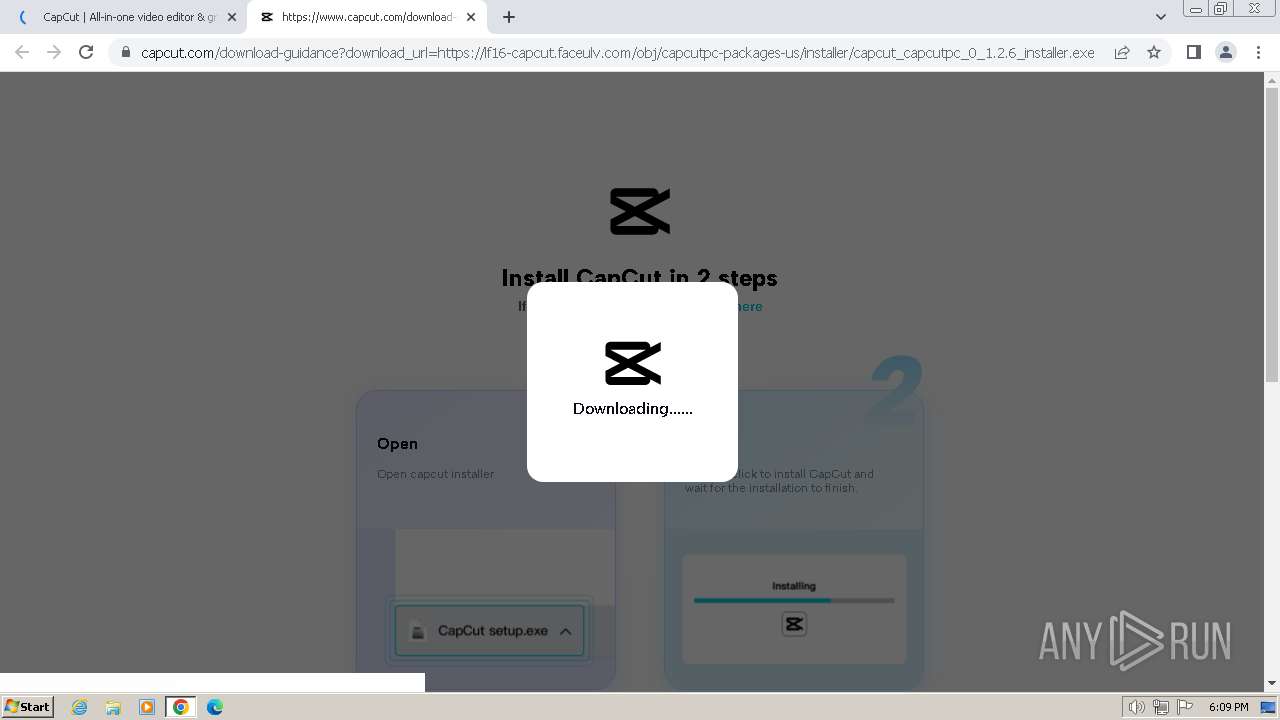
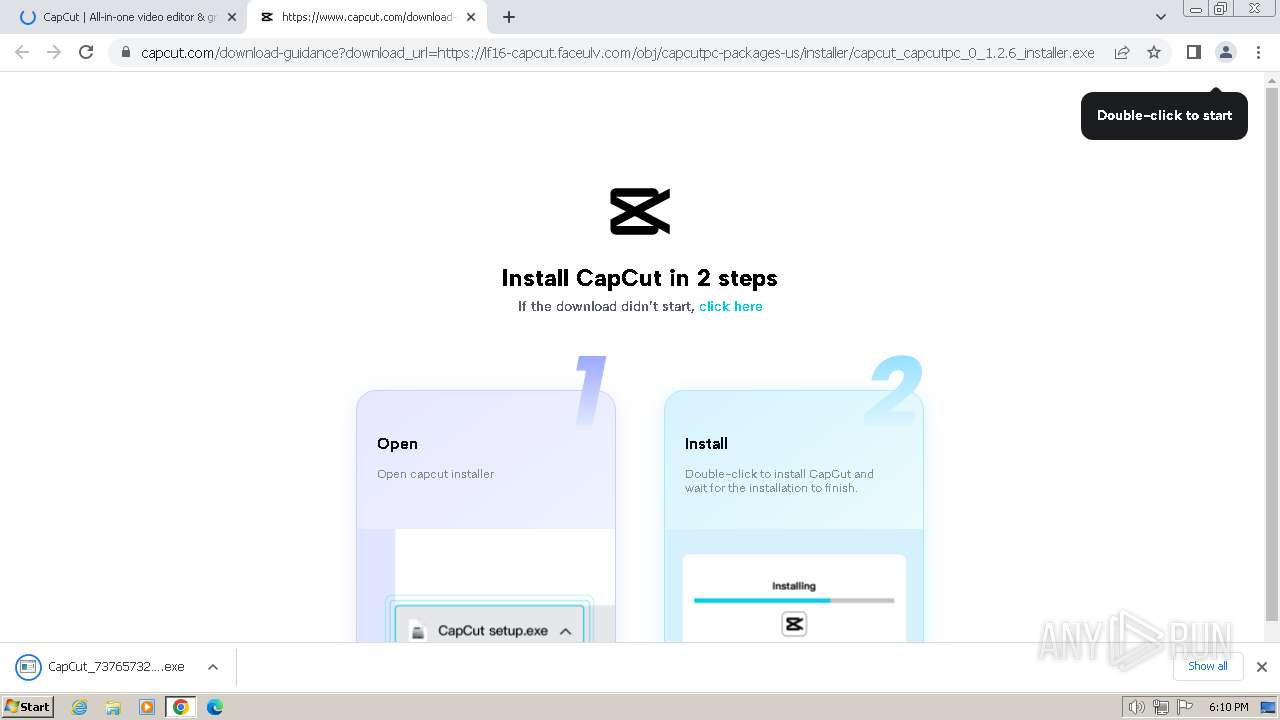
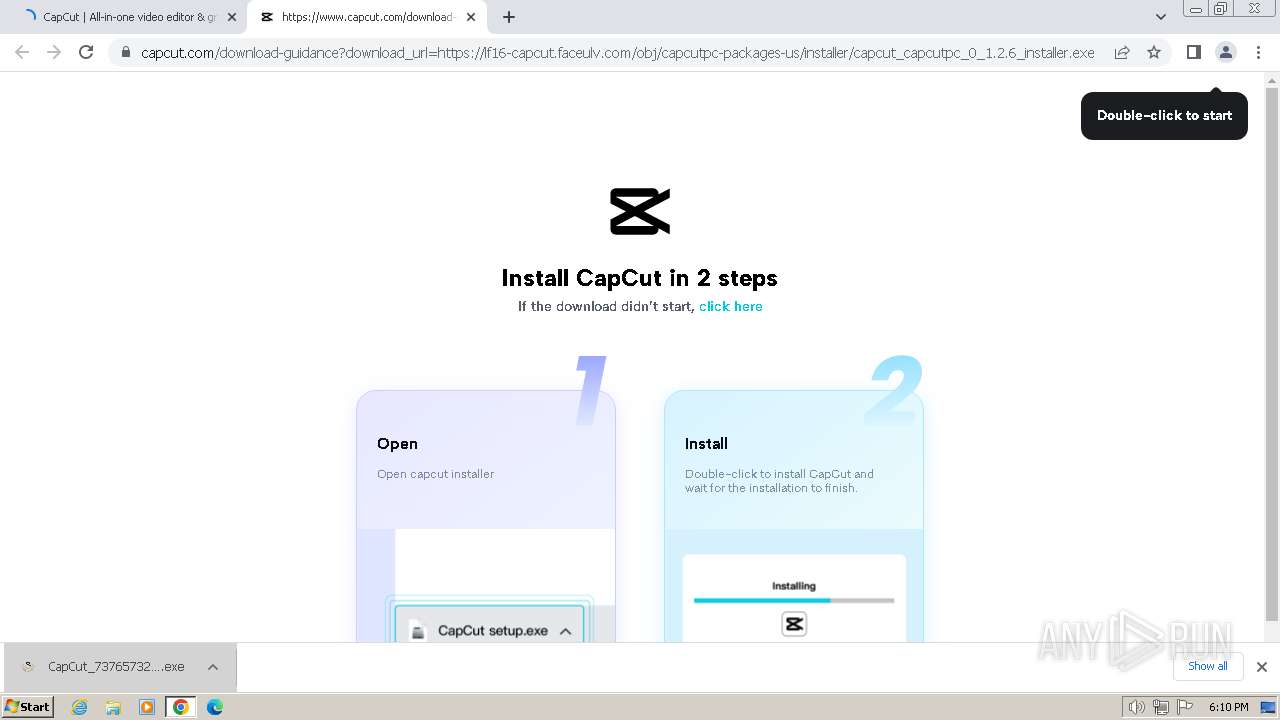
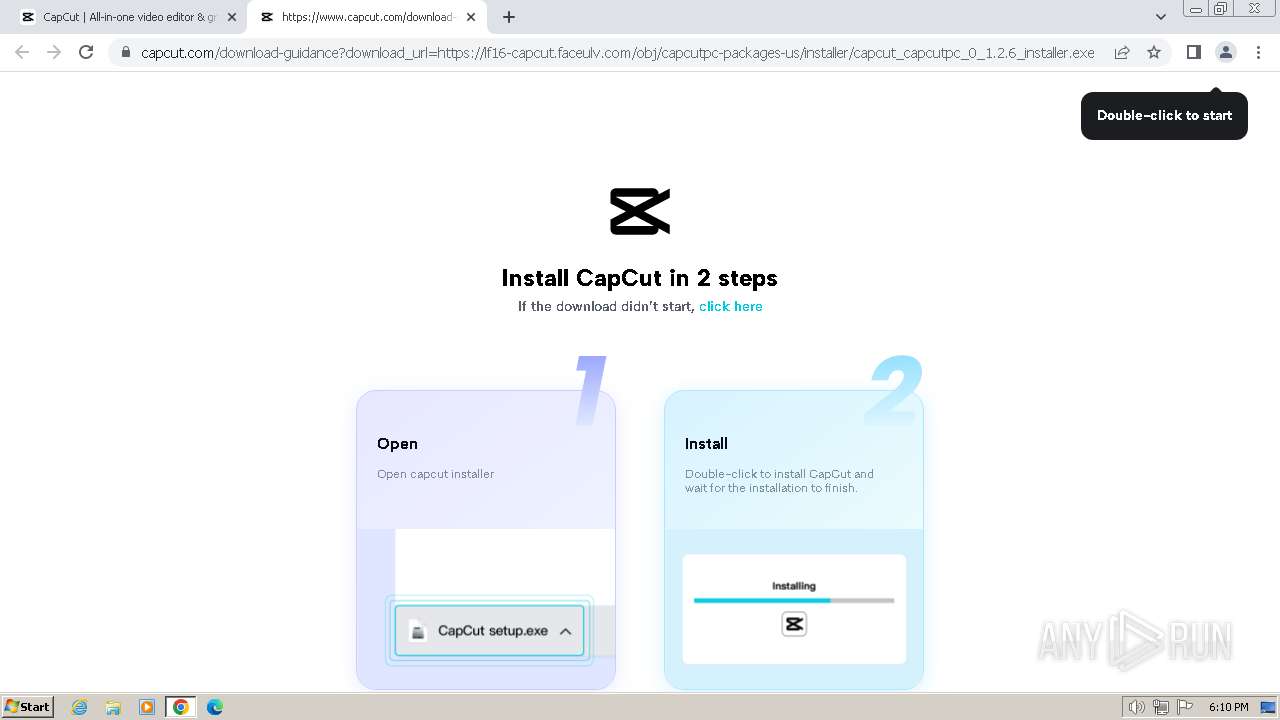
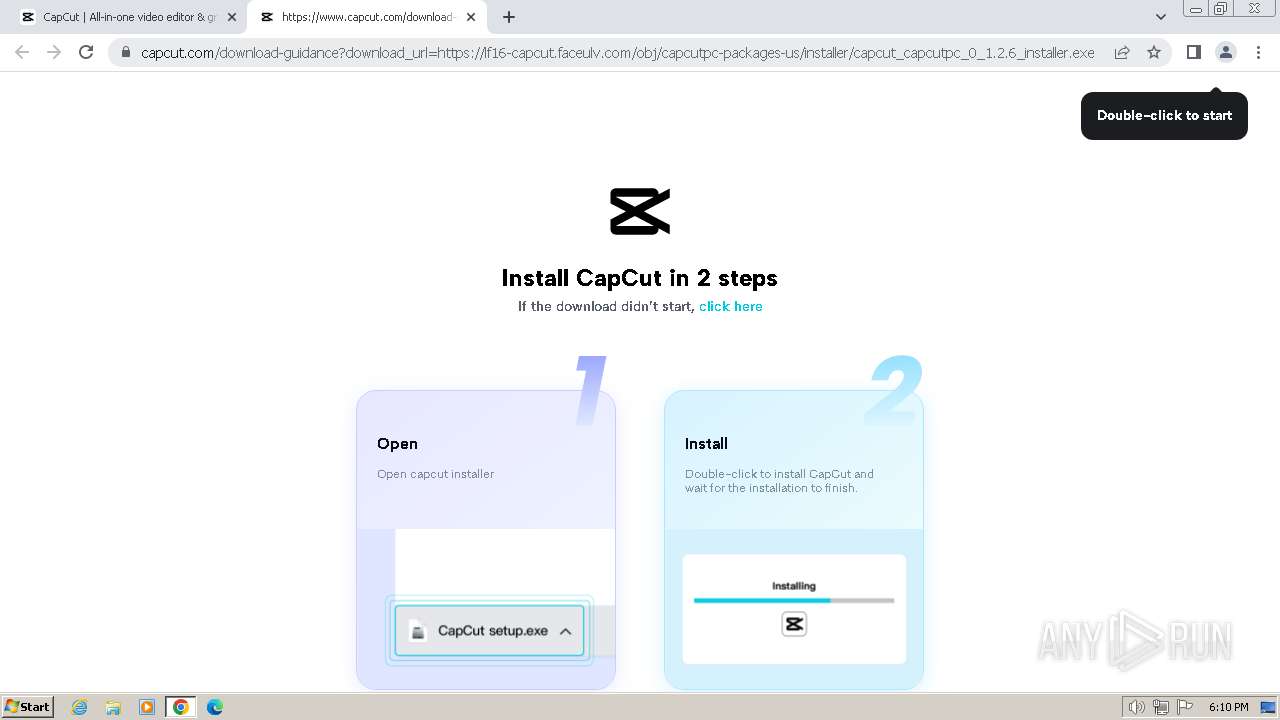
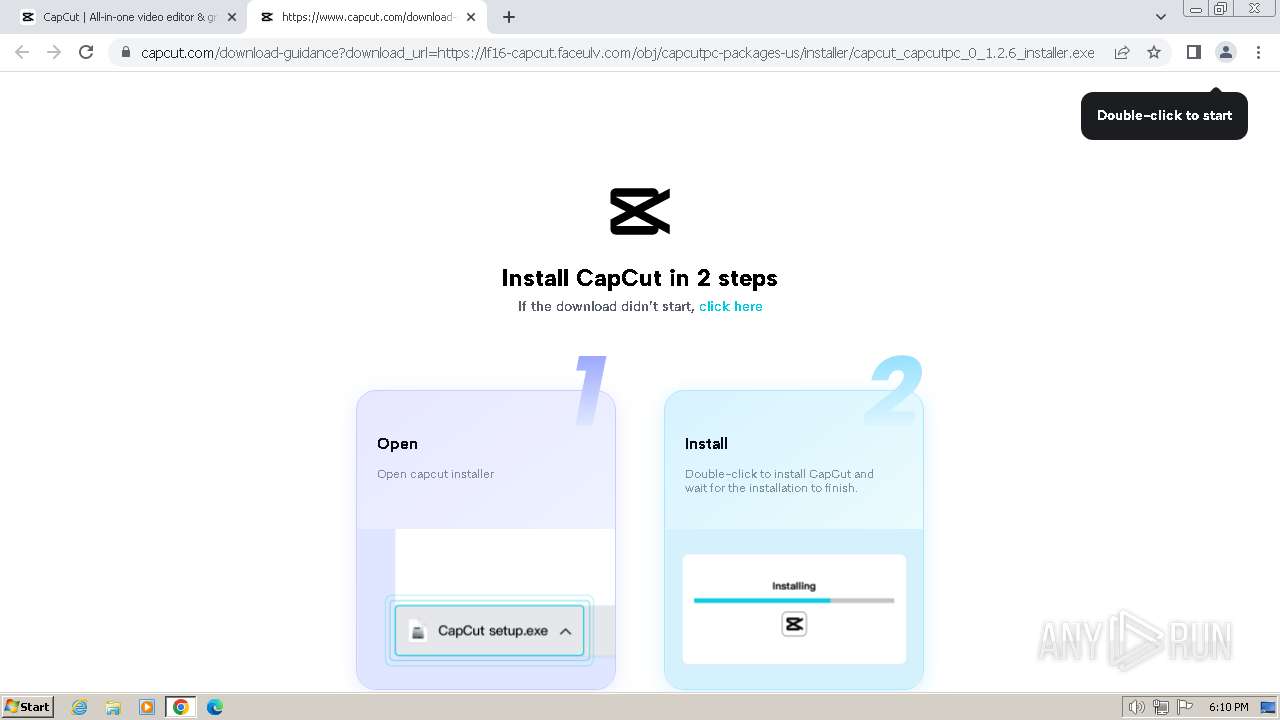
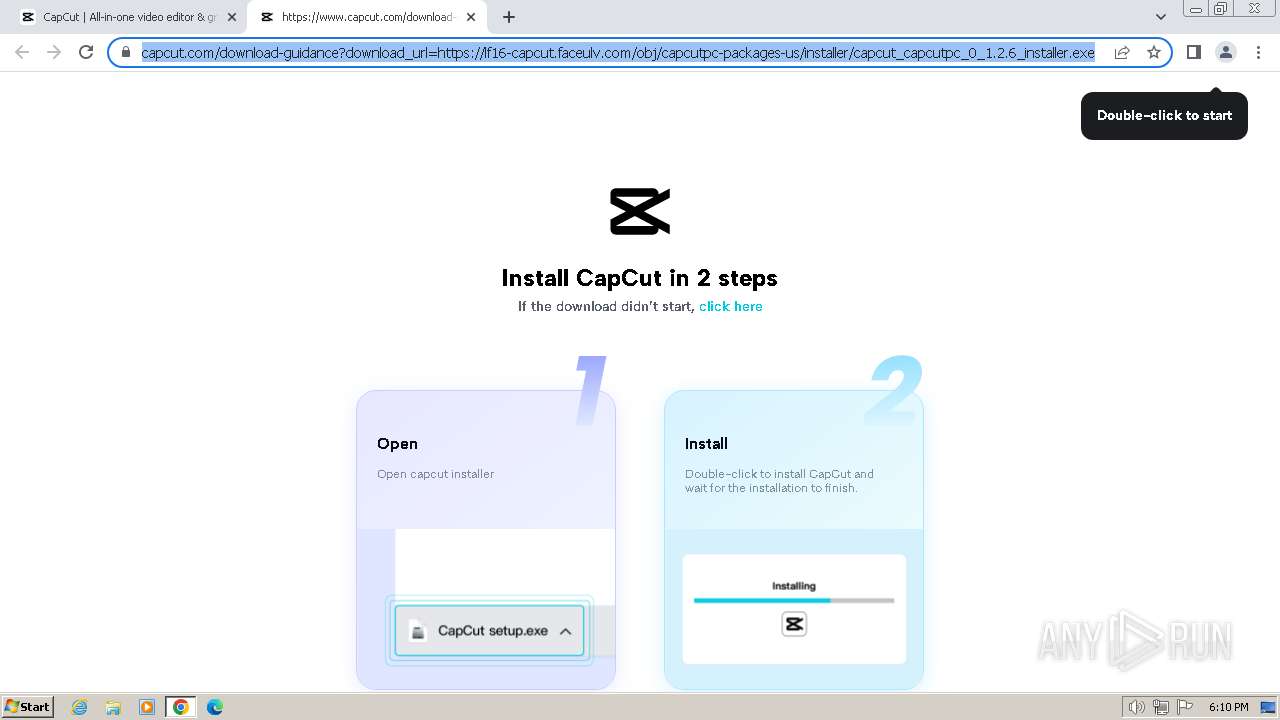
Drops the executable file immediately after the start
- CapCut_7376573271585718288_installer.exe (PID: 1392)
SUSPICIOUS
Potential Corporate Privacy Violation
- chrome.exe (PID: 2892)
Executable content was dropped or overwritten
- CapCut_7376573271585718288_installer.exe (PID: 1392)
Malware-specific behavior (creating "System.dll" in Temp)
- CapCut_7376573271585718288_installer.exe (PID: 1392)
INFO
Application launched itself
- iexplore.exe (PID: 3348)
- chrome.exe (PID: 880)
Executable content was dropped or overwritten
- chrome.exe (PID: 2892)
- chrome.exe (PID: 880)
Manual execution by a user
- chrome.exe (PID: 880)
Drops the executable file immediately after the start
- chrome.exe (PID: 2892)
- chrome.exe (PID: 880)
The process uses the downloaded file
- chrome.exe (PID: 2120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
69
Monitored processes
25
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3716 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2108 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x68988b38,0x68988b48,0x68988b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3356 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3856 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1392 | "C:\Users\admin\Downloads\CapCut_7376573271585718288_installer.exe" | C:\Users\admin\Downloads\CapCut_7376573271585718288_installer.exe | chrome.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 1516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3904 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1440 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3940 --field-trial-handle=1124,i,4089176664893766742,12929103228272743979,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
33 878
Read events
33 532
Write events
234
Delete events
112
Modification events
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 868527072 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31115243 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31115243 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
11
Suspicious files
367
Text files
207
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3532 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\DP119QMA.htm | html | |
MD5:D4B691CD9D99117B2EA34586D3E7EEB8 | SHA256:2178EEDD5723A6AC22E94EC59BDCD99229C87F3623753F5E199678242F0E90DE | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E397D59E65C61DA362A44DDE16FA0108 | SHA256:A002AA4C20AD46048545649AC97D70741AFE11D0942924699C34142AC8DE9CC9 | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4FA45AE1010E09657982D8D28B3BD38E_DDBD94486534E9D7296CF30055005EDC | der | |
MD5:5D1F2682BD9A3CFF7B2209D75D8E686A | SHA256:84E1100D1A56F5C39F3EB71995FA1B0AB1A799FEEF6F5DF680BFC4A7C18AB8D1 | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\WCZYMOF4.txt | text | |
MD5:0CE0B09F92F130FF756732911785BBAF | SHA256:89F87558C33A809C300CBE69DCC576D4369D4FE9B48562AB0B44C7734766AFEC | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:1CB06F1E183E4E348CE60EEB1E427C30 | SHA256:85514277B4B716F4E503A270445F06FF816C378C6B54917C2107B440AD5CEE93 | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4FA45AE1010E09657982D8D28B3BD38E_DDBD94486534E9D7296CF30055005EDC | binary | |
MD5:6E61C0FFBC3D8379655D233E1F2F2C5D | SHA256:1D4F76230DAE8FE64E3B90974234A1C72390F279BE4977B76A884552C124DD9B | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BAJPHMIB.txt | text | |
MD5:35A88D16E84362E21D0178019BB7E959 | SHA256:103C7D2428F62F895B057D9E011284B0E28F4EB3ED986BD8B3DB057144487DFB | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:8D1040B12A663CA4EC7277CFC1CE44F0 | SHA256:3086094D4198A5BBD12938B0D2D5F696C4DFC77E1EAE820ADDED346A59AA8727 | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DDE8B1B7E253A9758EC380BD648952AF_A3D4688236962EEA03574DE4F61B95D9 | der | |
MD5:0060DC981149DF3B94ED26CD961CCBFD | SHA256:8C1AF2B5F6479630BDACC9A7EA58D843FEC9BCE99536FCCF89CD4A21E60397BE | |||
| 3532 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DDE8B1B7E253A9758EC380BD648952AF_A3D4688236962EEA03574DE4F61B95D9 | binary | |
MD5:A3694DF1936D52B904F049DF12D15295 | SHA256:1520254077B4C3D2B05195C5F8C903B14A3F86CD6FB865D845D2A28D85D6B020 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
243
DNS requests
165
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3532 | iexplore.exe | GET | 304 | 2.16.10.176:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2eb9cb0aeb593466 | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 301 | 142.250.184.238:80 | http://google.com/ | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 302 | 216.58.206.68:80 | http://www.google.com/ | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCKrGgQlh%2BmUBCqAZP5%2Fey1 | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEDzB%2BrH%2BcR2lEC3VaK3WaPU%3D | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 304 | 2.16.10.176:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c5b25abc6f05efbc | unknown | — | — | unknown |
3532 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCRq%2FXldMamzQqGAD6YrjKf | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 304 | 2.16.10.176:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?75133f1458310141 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3532 | iexplore.exe | 142.250.184.238:80 | google.com | GOOGLE | US | whitelisted |
3532 | iexplore.exe | 216.58.206.68:80 | www.google.com | GOOGLE | US | whitelisted |
3532 | iexplore.exe | 216.58.206.68:443 | www.google.com | GOOGLE | US | whitelisted |
3532 | iexplore.exe | 2.16.10.176:80 | ctldl.windowsupdate.com | Akamai International B.V. | AT | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3532 | iexplore.exe | 142.250.186.99:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| unknown |
o.pki.goog |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
7 ETPRO signatures available at the full report