| URL: | google.com |
| Full analysis: | https://app.any.run/tasks/58a6d081-508a-4ef2-aeea-b8924b1f9973 |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2024, 17:57:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1D5920F4B44B27A802BD77C4F0536F5A |
| SHA1: | BAEA954B95731C68AE6E45BD1E252EB4560CDC45 |
| SHA256: | D4C9D9027326271A89CE51FCAF328ED673F17BE33469FF979E8AB8DD501E664F |
| SSDEEP: | 3:duK:IK |
MALICIOUS
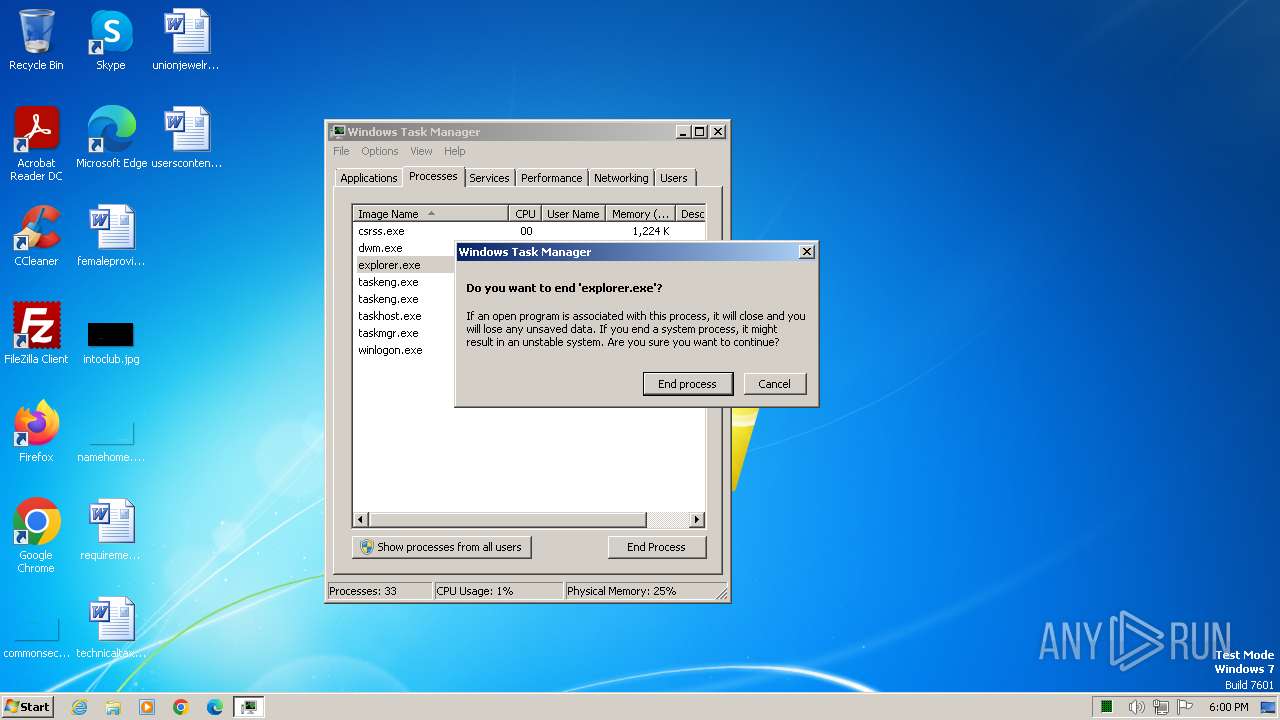
Changes the autorun value in the registry
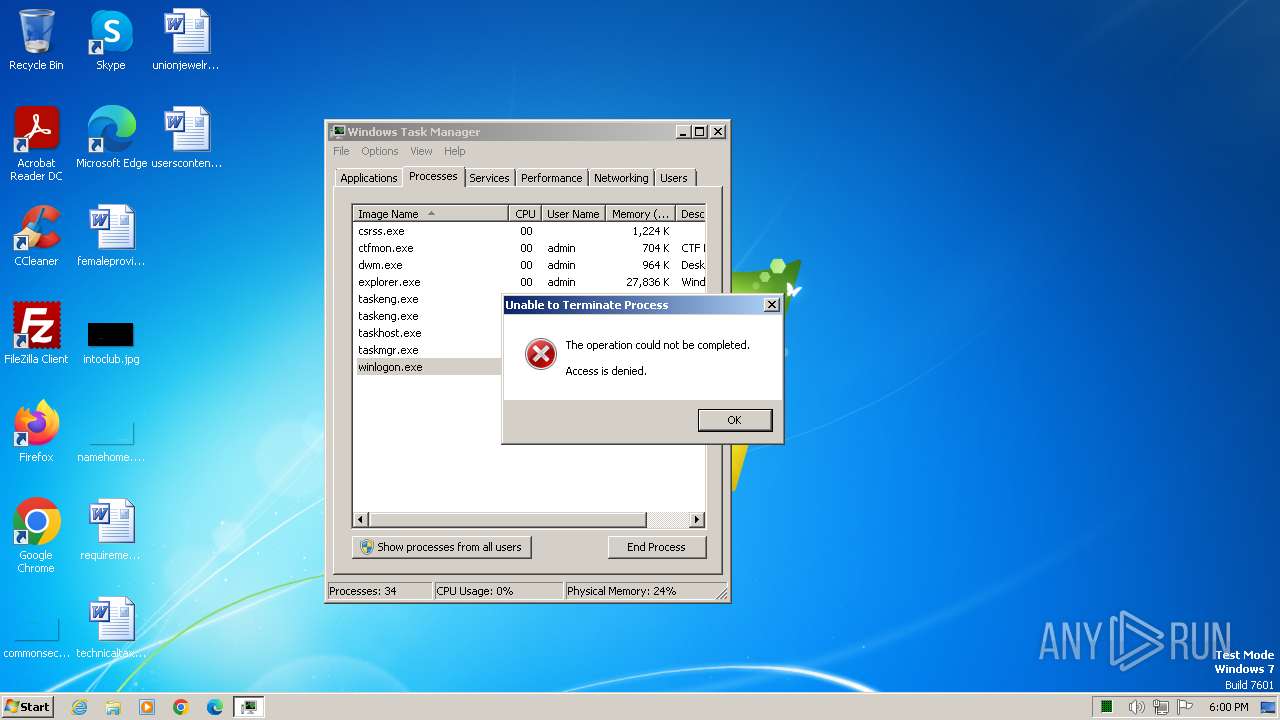
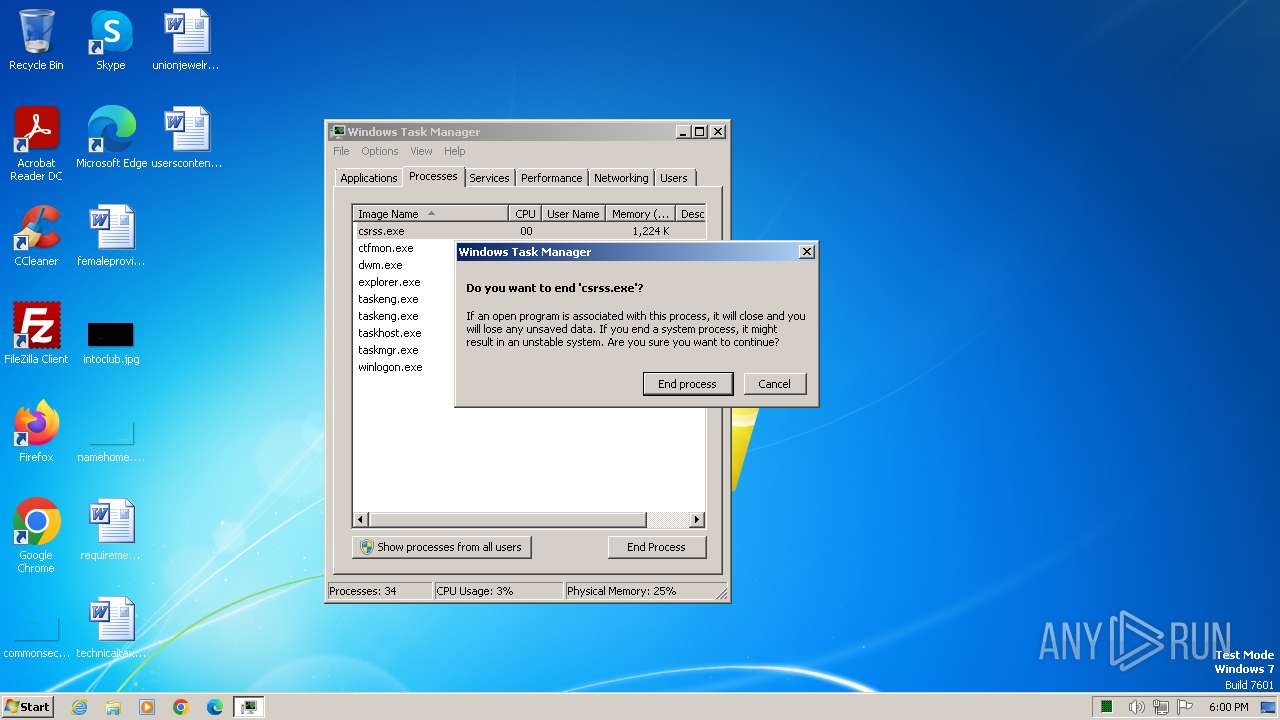
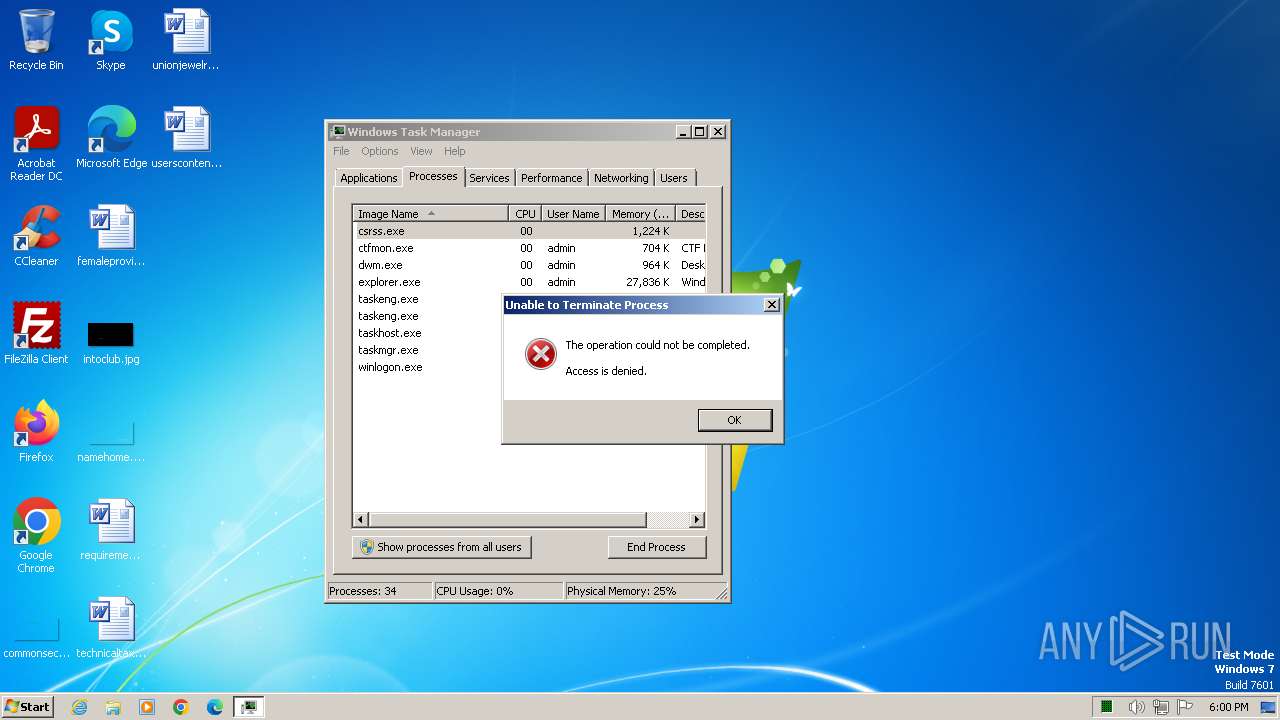
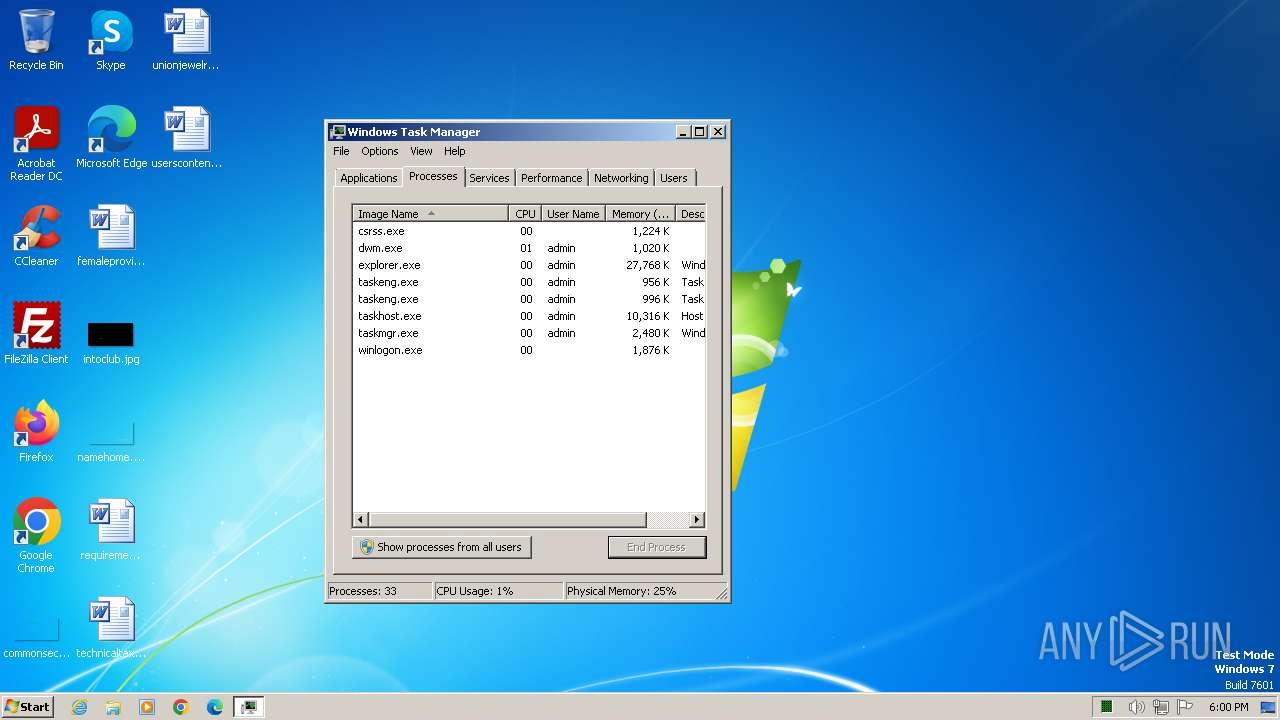
- taskmgr.exe (PID: 3452)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 3612)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3612)
Drops the executable file immediately after the start
- CCleaner.exe (PID: 3612)
SUSPICIOUS
The process executes via Task Scheduler
- CCleaner.exe (PID: 3612)
Executable content was dropped or overwritten
- CCleaner.exe (PID: 3612)
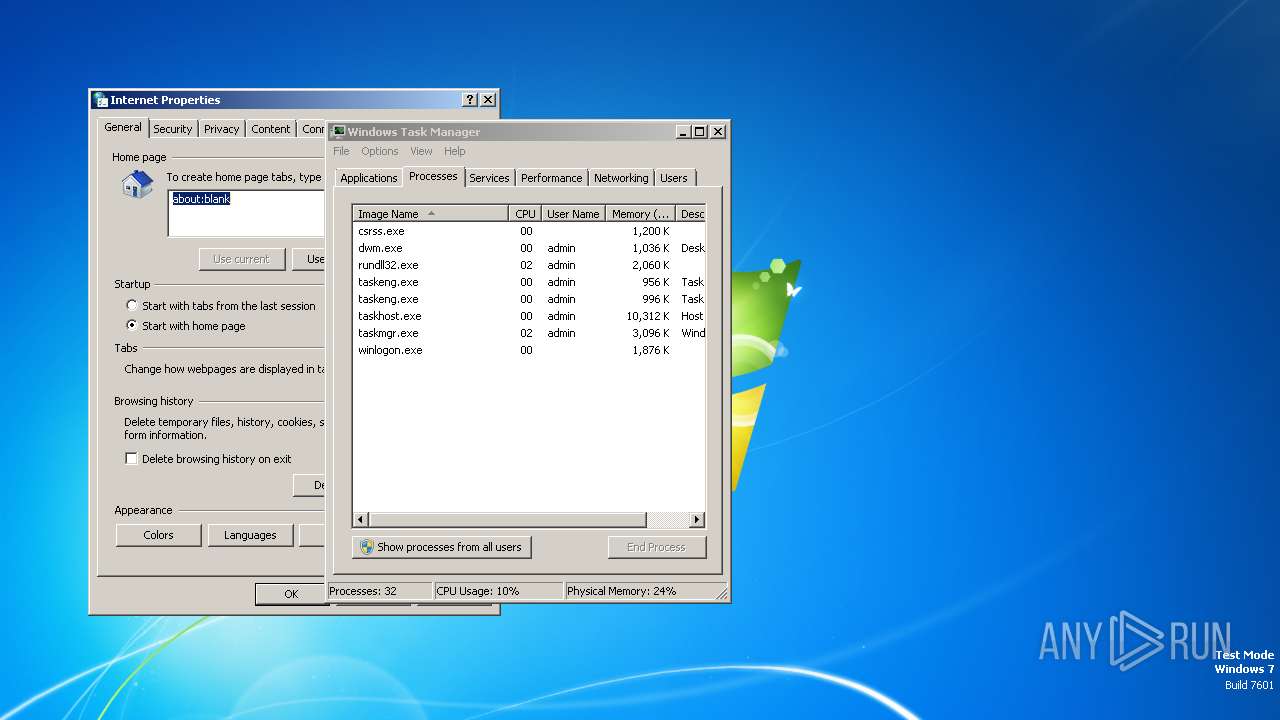
Reads Internet Explorer settings
- CCleaner.exe (PID: 3612)
Reads the Internet Settings
- CCleaner.exe (PID: 3612)
- taskmgr.exe (PID: 3452)
- control.exe (PID: 2484)
- rundll32.exe (PID: 784)
The process verifies whether the antivirus software is installed
- CCleaner.exe (PID: 3612)
Searches for installed software
- CCleaner.exe (PID: 3612)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 3612)
- rundll32.exe (PID: 784)
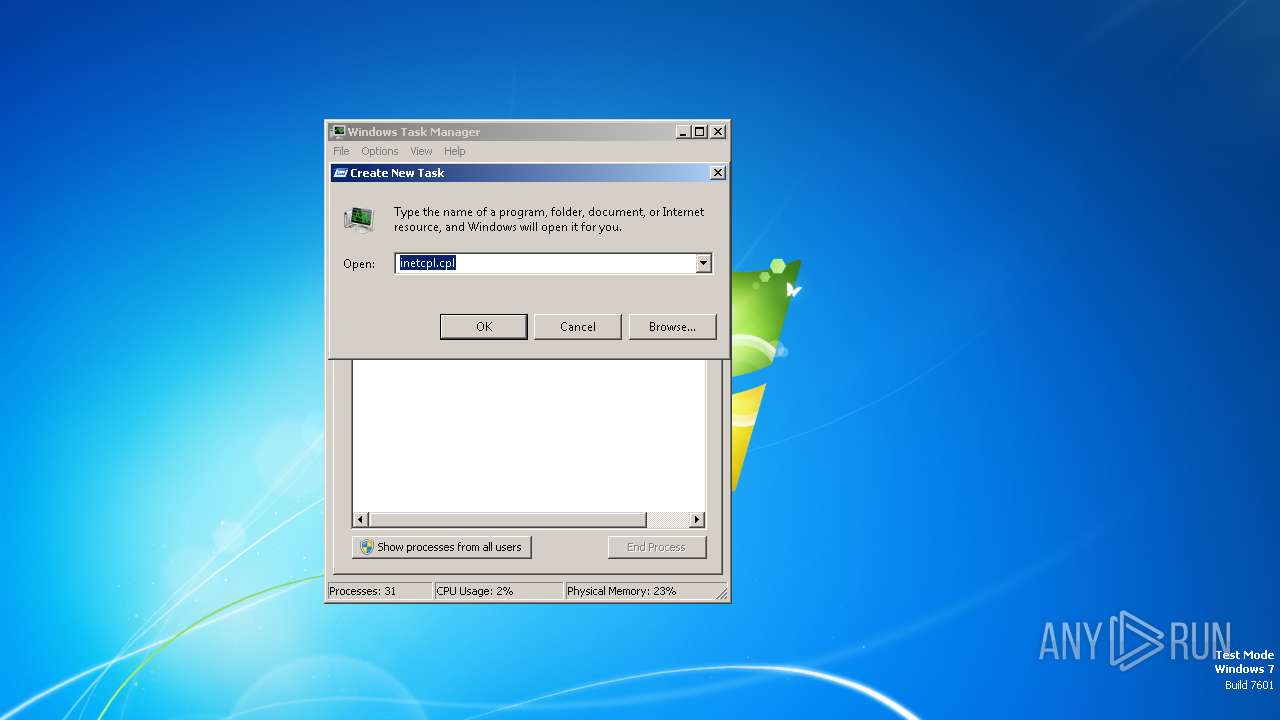
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2484)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 3612)
Reads settings of System Certificates
- CCleaner.exe (PID: 3612)
Checks Windows Trust Settings
- CCleaner.exe (PID: 3612)
INFO
Application launched itself
- iexplore.exe (PID: 1392)
- chrome.exe (PID: 3952)
- iexplore.exe (PID: 1840)
Checks supported languages
- CCleaner.exe (PID: 3576)
- CCleaner.exe (PID: 3612)
Reads the computer name
- CCleaner.exe (PID: 3576)
- CCleaner.exe (PID: 3612)
Reads Environment values
- CCleaner.exe (PID: 3576)
- CCleaner.exe (PID: 3612)
Manual execution by a user
- CCleaner.exe (PID: 3576)
- chrome.exe (PID: 3952)
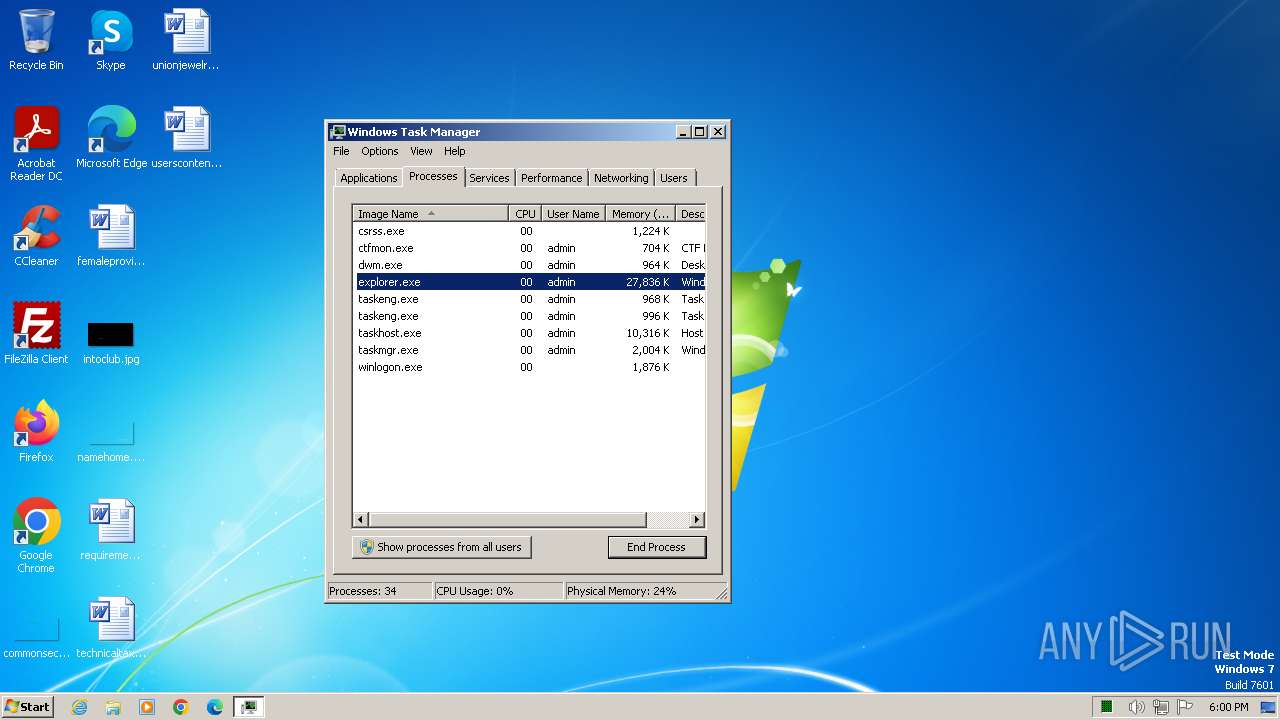
- taskmgr.exe (PID: 3452)
- explorer.exe (PID: 668)
Reads CPU info
- CCleaner.exe (PID: 3612)
Reads the machine GUID from the registry
- CCleaner.exe (PID: 3612)
Reads product name
- CCleaner.exe (PID: 3612)
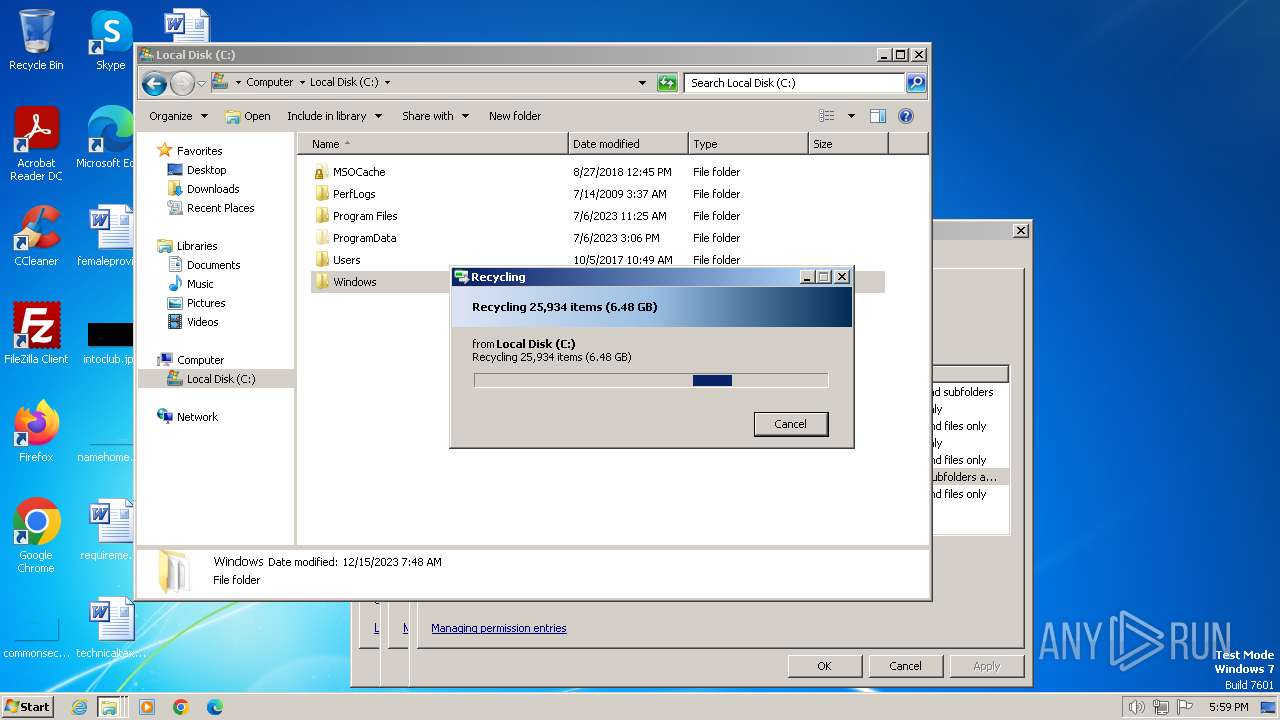
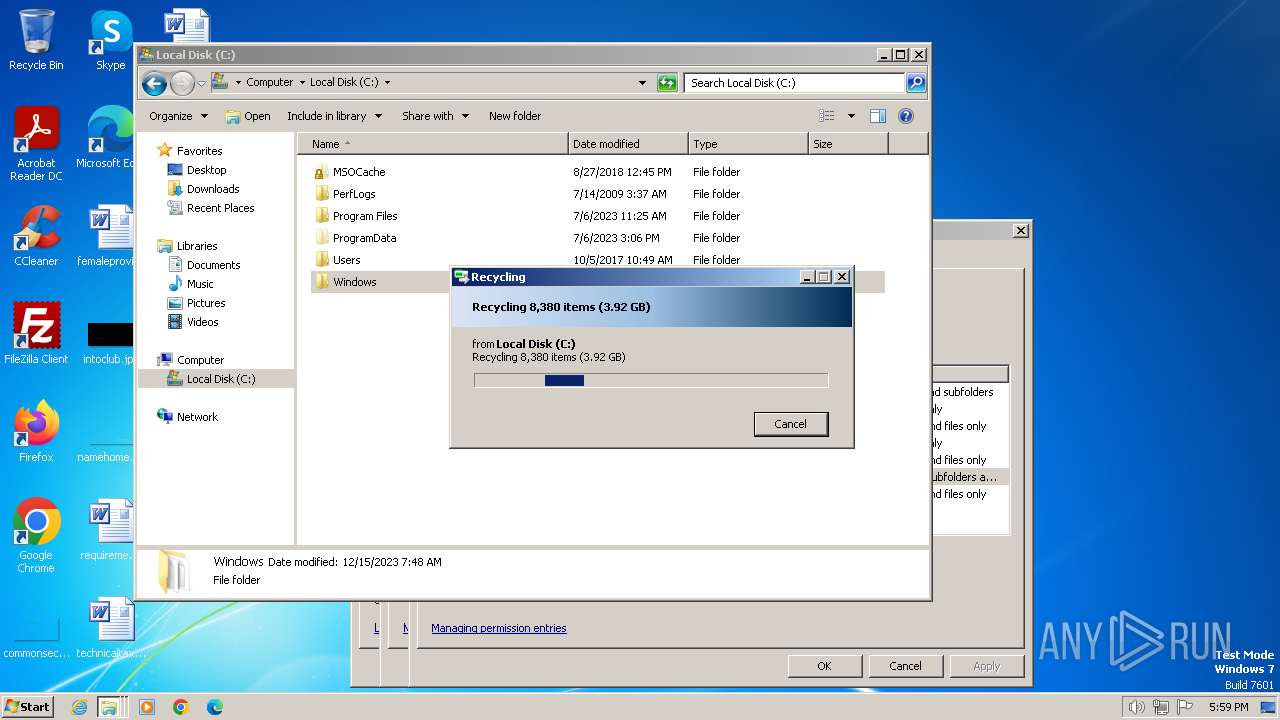
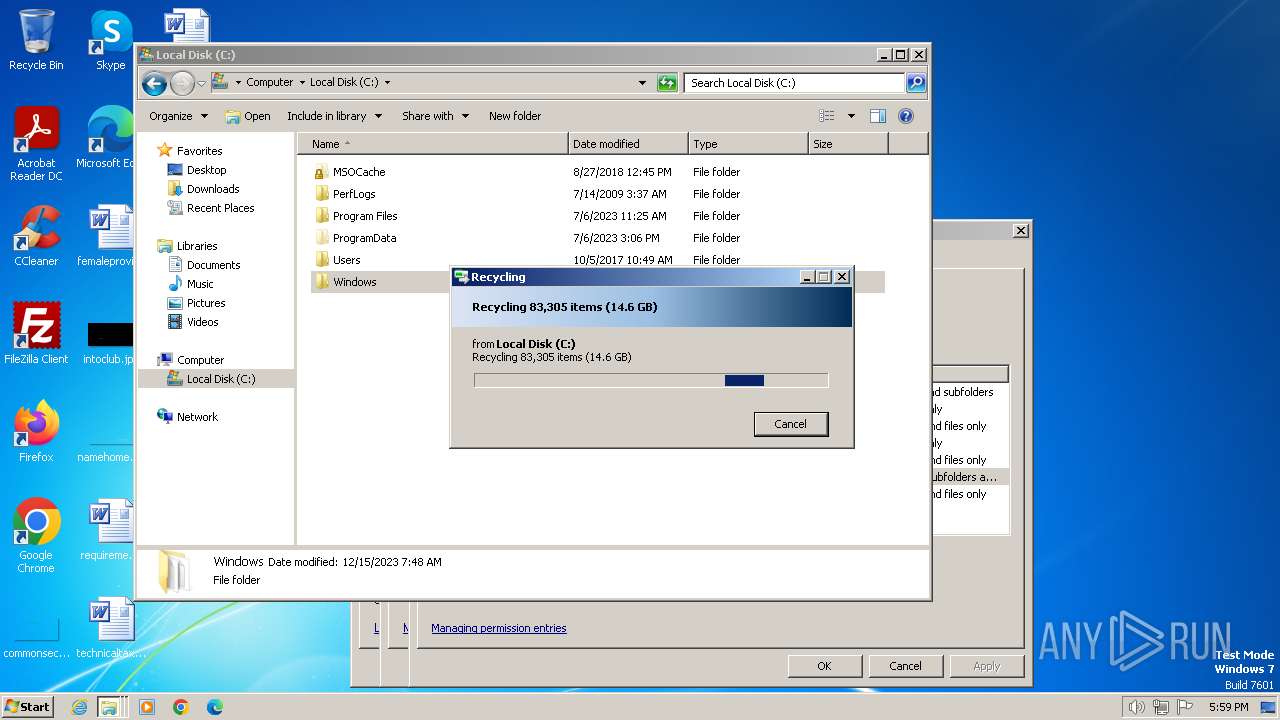
Creates files in the program directory
- CCleaner.exe (PID: 3612)
Checks proxy server information
- CCleaner.exe (PID: 3612)
Creates files or folders in the user directory
- CCleaner.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
75
Monitored processes
25
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3752 --field-trial-handle=1072,i,15995681186613170319,16587074007958917120,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3632 --field-trial-handle=1072,i,15995681186613170319,16587074007958917120,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 668 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\inetcpl.cpl", | C:\Windows\System32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Internet Explorer\iexplore.exe" "google.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3860 --field-trial-handle=1072,i,15995681186613170319,16587074007958917120,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1056 --field-trial-handle=1072,i,15995681186613170319,16587074007958917120,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1604 --field-trial-handle=1072,i,15995681186613170319,16587074007958917120,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2112 --field-trial-handle=1072,i,15995681186613170319,16587074007958917120,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
39 230
Read events
38 759
Write events
412
Delete events
59
Modification events
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1392) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
3
Suspicious files
116
Text files
238
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2736 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BHTJRBX5.txt | text | |
MD5:44792DB5532970861E3CD9E9852FF4D4 | SHA256:5BB74A8030C1FF419BEC949B154CFBD5149CD527A8A5E2010ACD40908C2CE888 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:0646E15AC17FD2F31CF8D2713984C7F6 | SHA256:0B30E2EAE722DCB1063523D75CD3F97513DDA85C41B7B4F5AFC68BAB5053D27B | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:D022364E647540F82682ADBC0BE0A7DD | SHA256:B9A18D9FD953A2F69B1E7D3F47B4A73E26B8A14A8C56BD9AC12712B331FE84F5 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:D49643E08BB2F555A62BF3D57ED64482 | SHA256:D2F5E0926A29872E8100DF816D3292124F6DCB676E95AAAEC418B39CA576B89B | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:C03544577D332D7136B79B734CECC011 | SHA256:E706F38F1225A905FDCC0C9A871A1347EB3CEEFE5226B640AF43E38BD800D85E | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_1C8038BAE9D4E52C4463A14FAB50BBA7 | binary | |
MD5:CC25056B39AB1E7C39BA9FF23C883906 | SHA256:DC98C7087B54260E2FD54BB014CF89B4D2C5BA4E382B5EDEF8972A9D91334EC6 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\api[1].js | text | |
MD5:DF08BFB855341C8529F5B9A8FCE9E5BC | SHA256:E5C4F205B08E4211E0EA0799D0A92462EE64690951CE8CB8DC61E7E984907051 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_DDCF8A1BB8132E191B1D87188F0E5FF4 | der | |
MD5:85ABA89C53BB7C2A4F540128473BC3B1 | SHA256:98E383259FD9F2D438B50930F12B97F0ECBFC10365E78CC24BB6154E2CA888F1 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_1C8038BAE9D4E52C4463A14FAB50BBA7 | binary | |
MD5:1767FB4BF4A586991E55818433DE8D20 | SHA256:6E454ED6E4D49D896E59D3712F5873BA950F95B4B2F58802BAC434DFC4CDCDD1 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\recaptcha__en[1].js | text | |
MD5:16CB1C02D3183E1026B4CA6B3EB3D509 | SHA256:689C72D7718868395EAF4BBE26E9F52E92F16DAAA1D5486B53AE3744A996F1E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
111
DNS requests
59
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2736 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2736 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?245ab6ffaf4de696 | unknown | — | — | unknown |
2736 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBNRO0CFNoMoCn81RqoChws%3D | unknown | binary | 471 b | unknown |
1392 | iexplore.exe | GET | 200 | 216.58.206.36:80 | http://www.google.com/favicon.ico | unknown | image | 1.46 Kb | unknown |
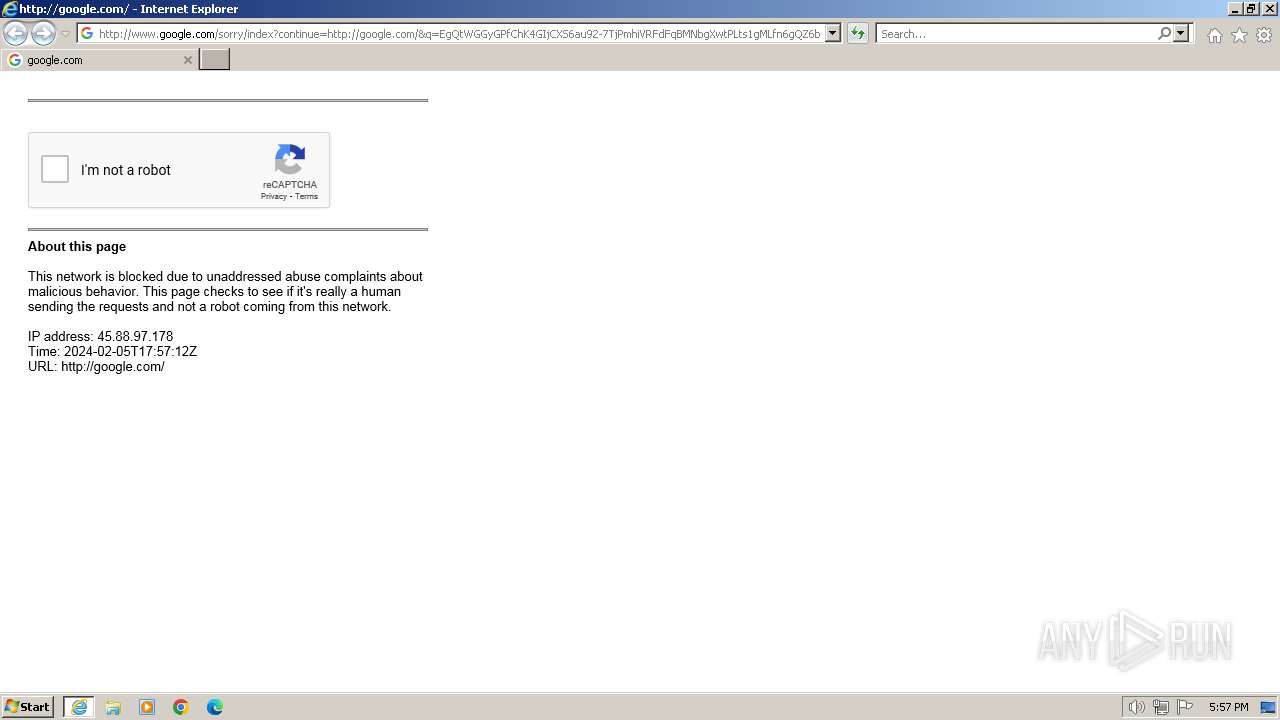
2736 | iexplore.exe | GET | 429 | 216.58.206.36:80 | http://www.google.com/sorry/index?continue=http://google.com/&q=EgQtWGGyGPfChK4GIjCXS6au92-7TjPmhiVRFdFqBMNbgXwtPLts1gMLfn6gQZ6bHoANcdsWnIKifCibk9syAXJKGVNPUlJZX0FCVVNJVkVfTkVUX01FU1NBR0VaAUM | unknown | html | 2.97 Kb | unknown |
2736 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1392 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?85e86cb0182c8369 | unknown | — | — | unknown |
2736 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDf%2FqechPhkiAm5teJWf%2BUv | unknown | binary | 472 b | unknown |
1392 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1392 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5565915fab5f2bac | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2736 | iexplore.exe | 142.250.185.174:80 | google.com | GOOGLE | US | whitelisted |
2736 | iexplore.exe | 216.58.206.36:80 | www.google.com | GOOGLE | US | whitelisted |
2736 | iexplore.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
2736 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2736 | iexplore.exe | 142.250.186.99:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2736 | iexplore.exe | 142.250.185.99:443 | www.gstatic.com | GOOGLE | US | whitelisted |
1392 | iexplore.exe | 216.58.206.36:80 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ncc.avast.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
3612 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner.exe | [2024-02-05 17:57:20.459] [error ] [settings ] [ 3612: 3624] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | [2024-02-05 17:57:21.146] [error ] [settings ] [ 3612: 3832] [9434E9: 359] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2024-02-05 17:57:21.162] [error ] [Burger ] [ 3612: 3832] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | [2024-02-05 17:57:21.162] [error ] [Burger ] [ 3612: 3832] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|