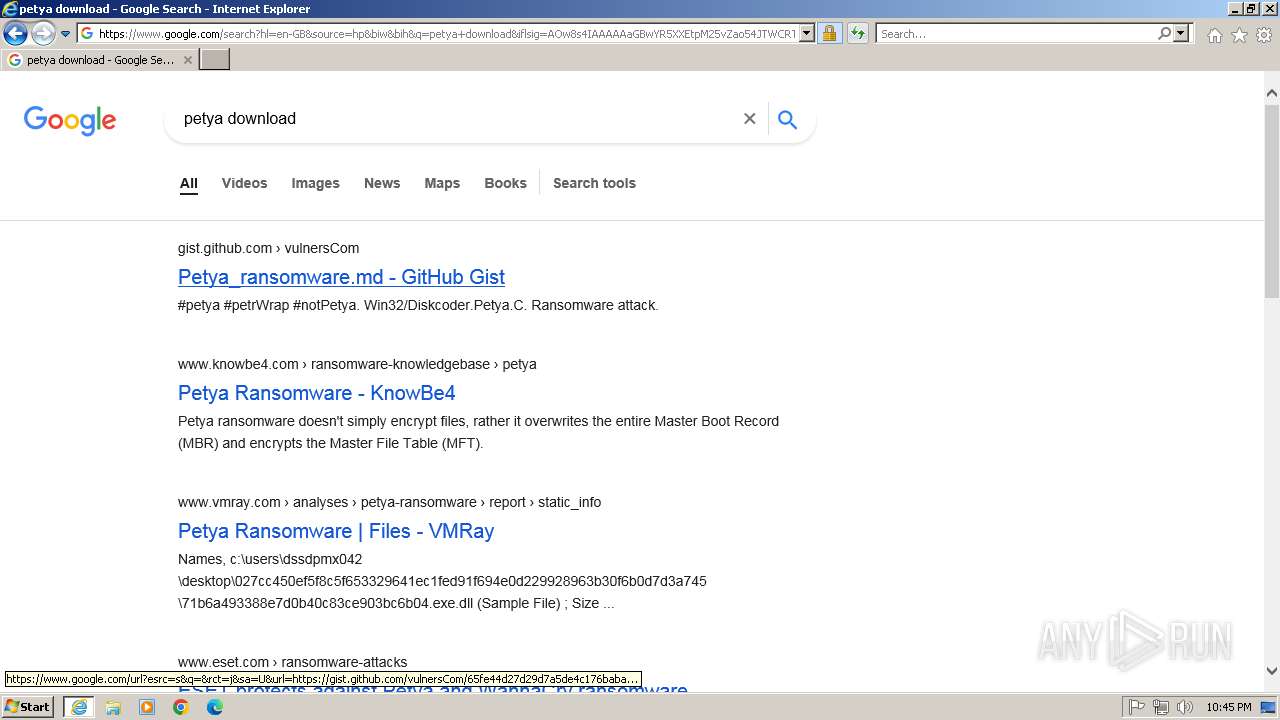
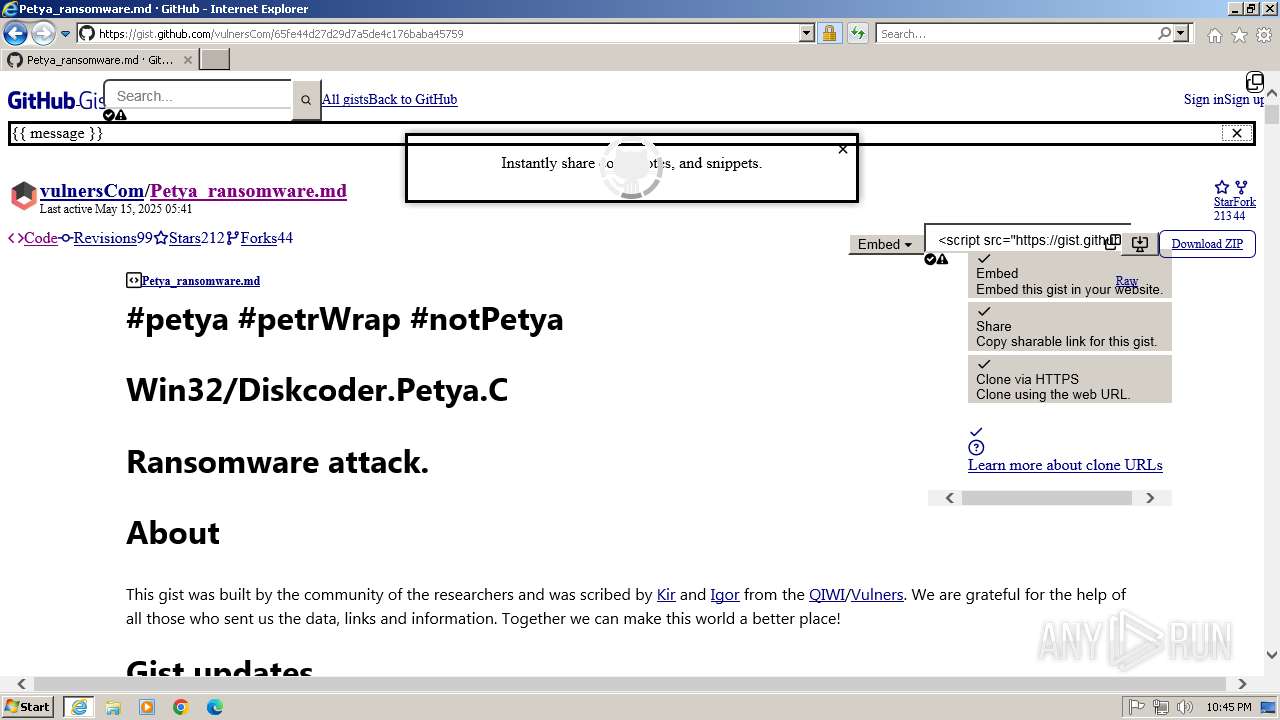
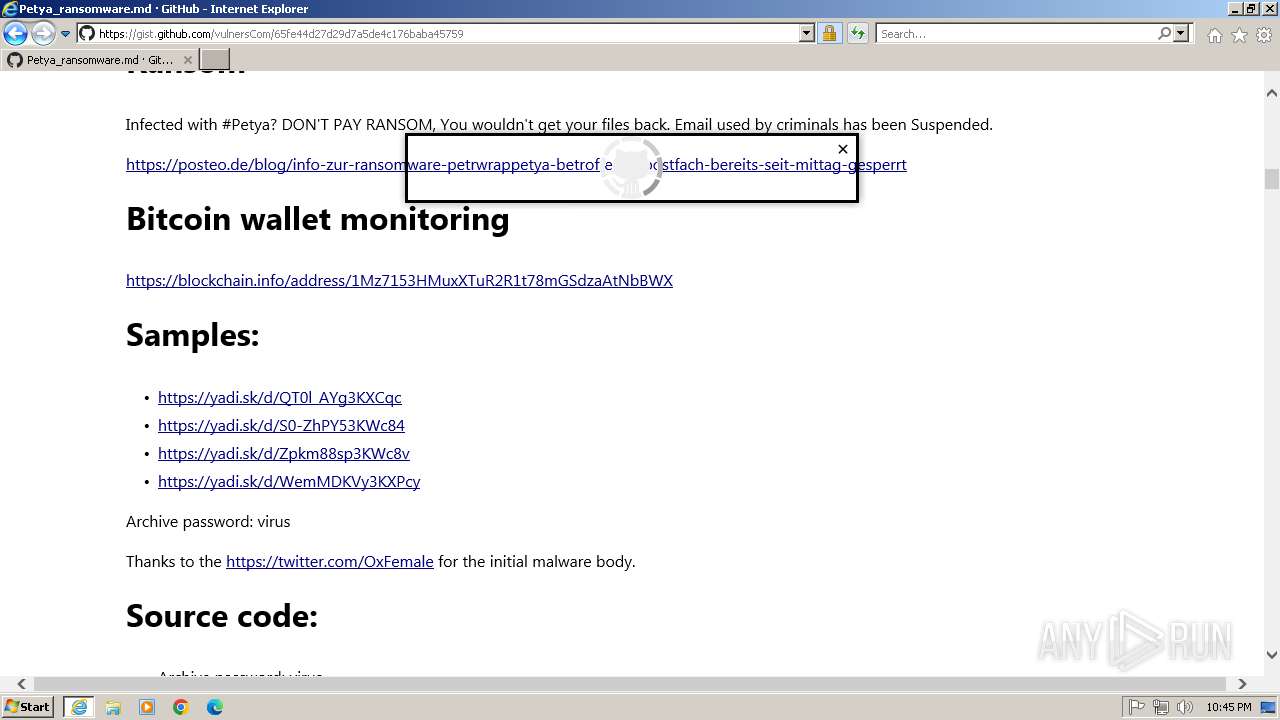
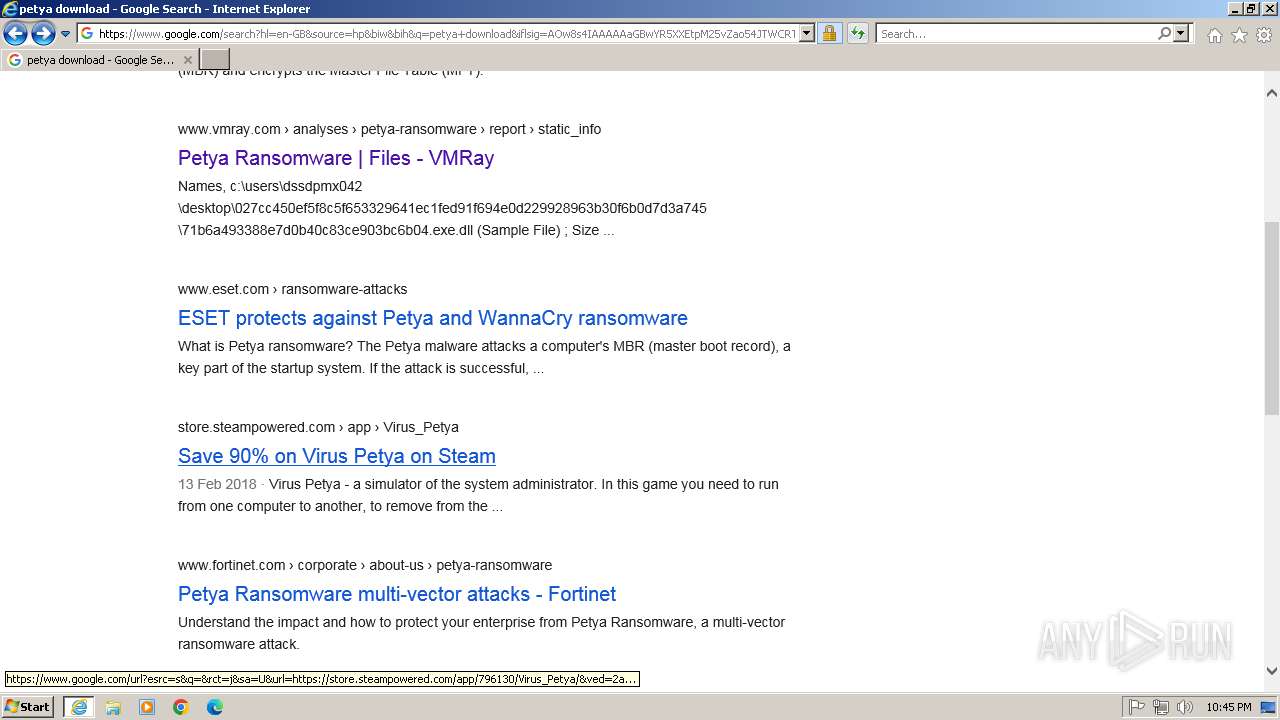
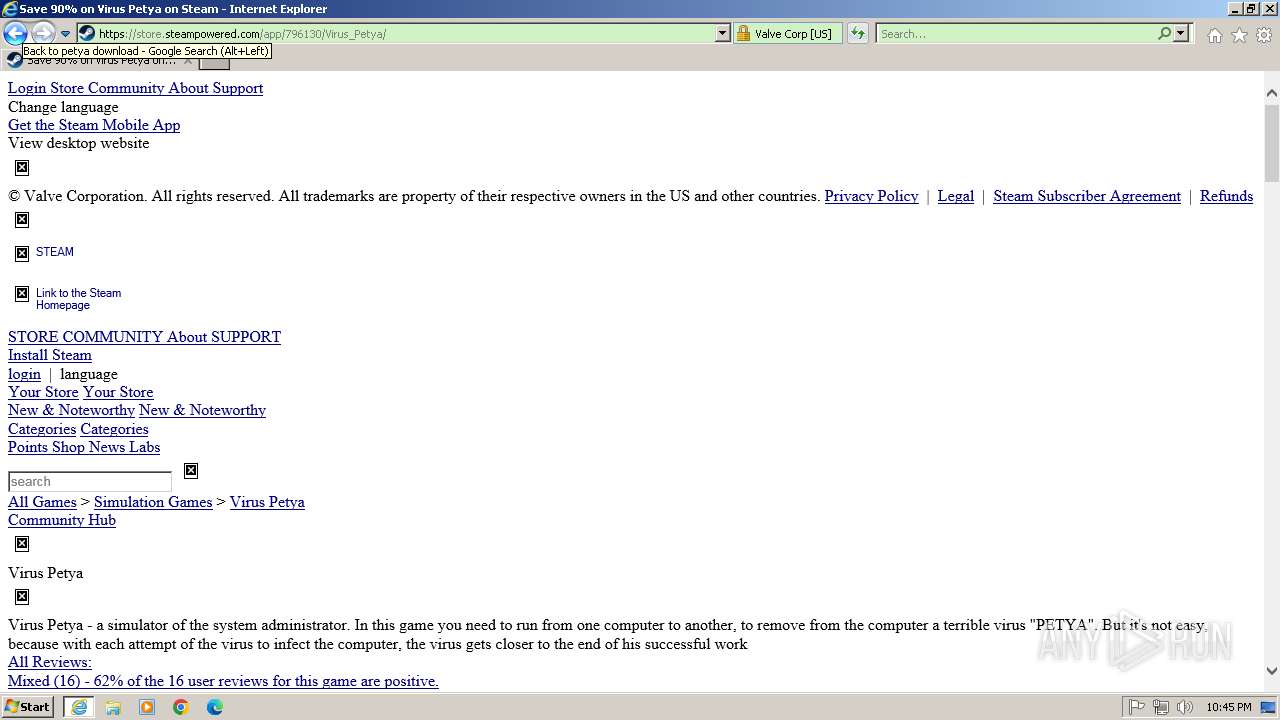
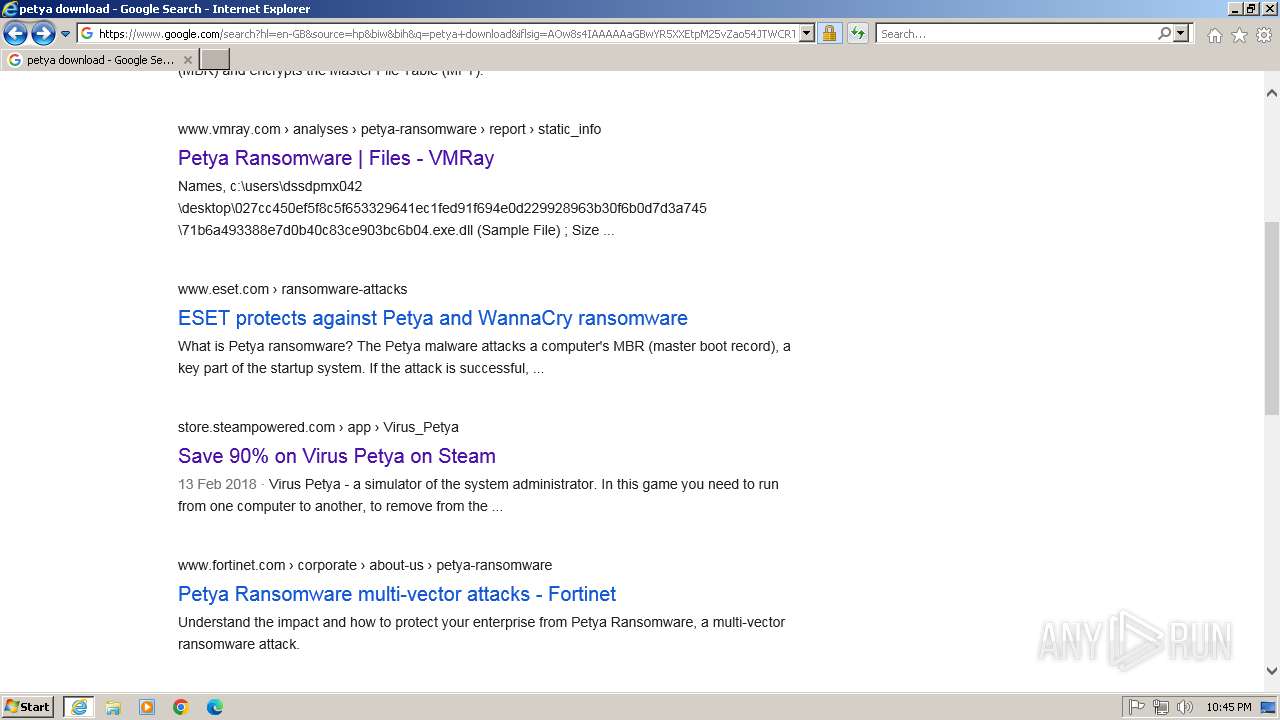
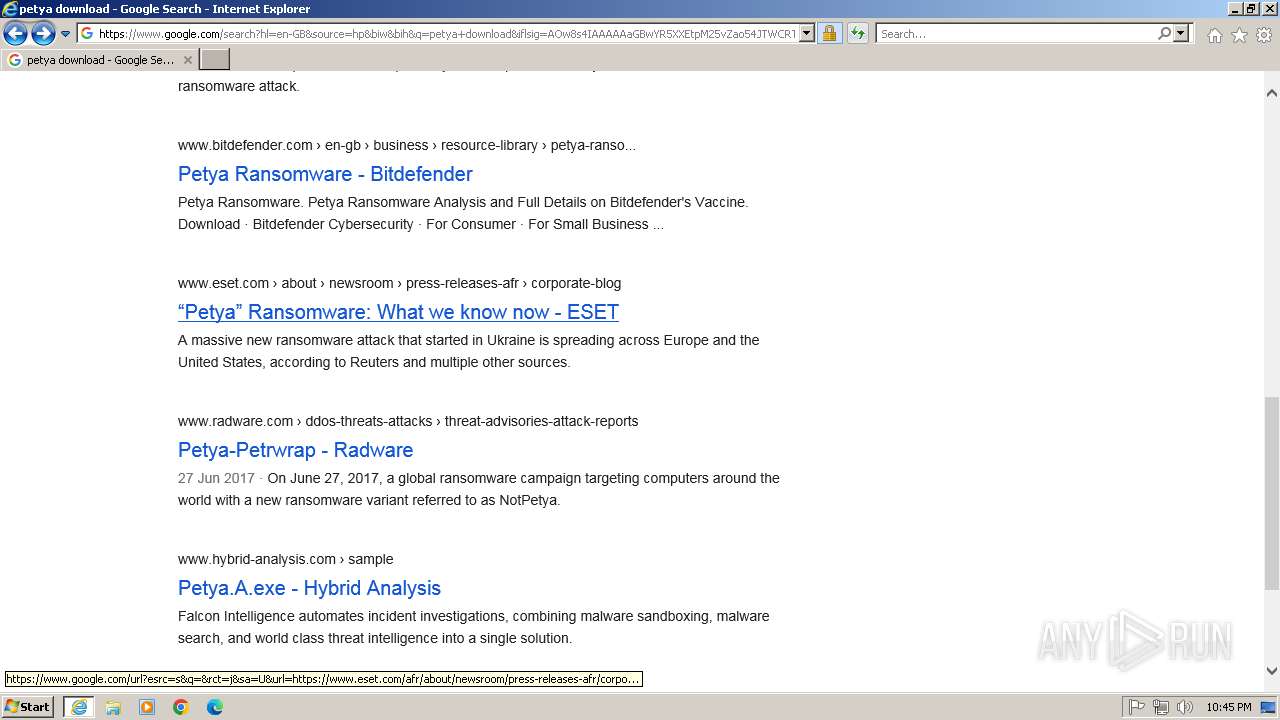
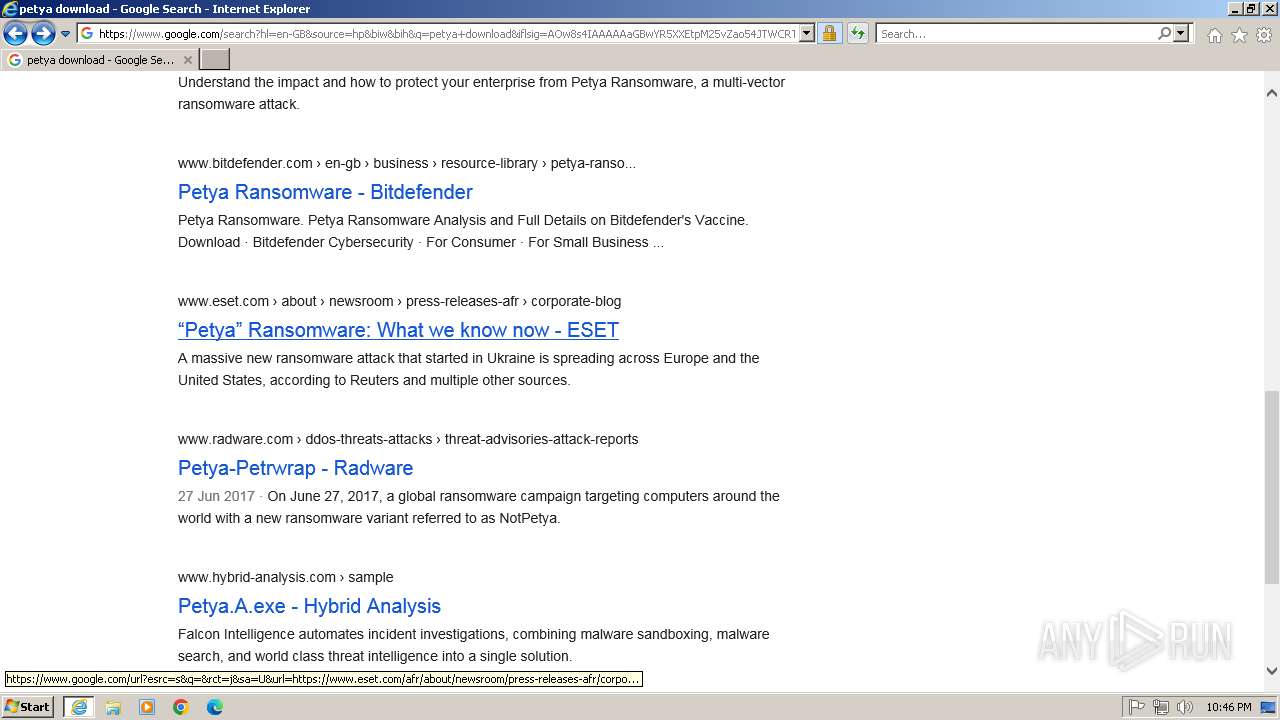
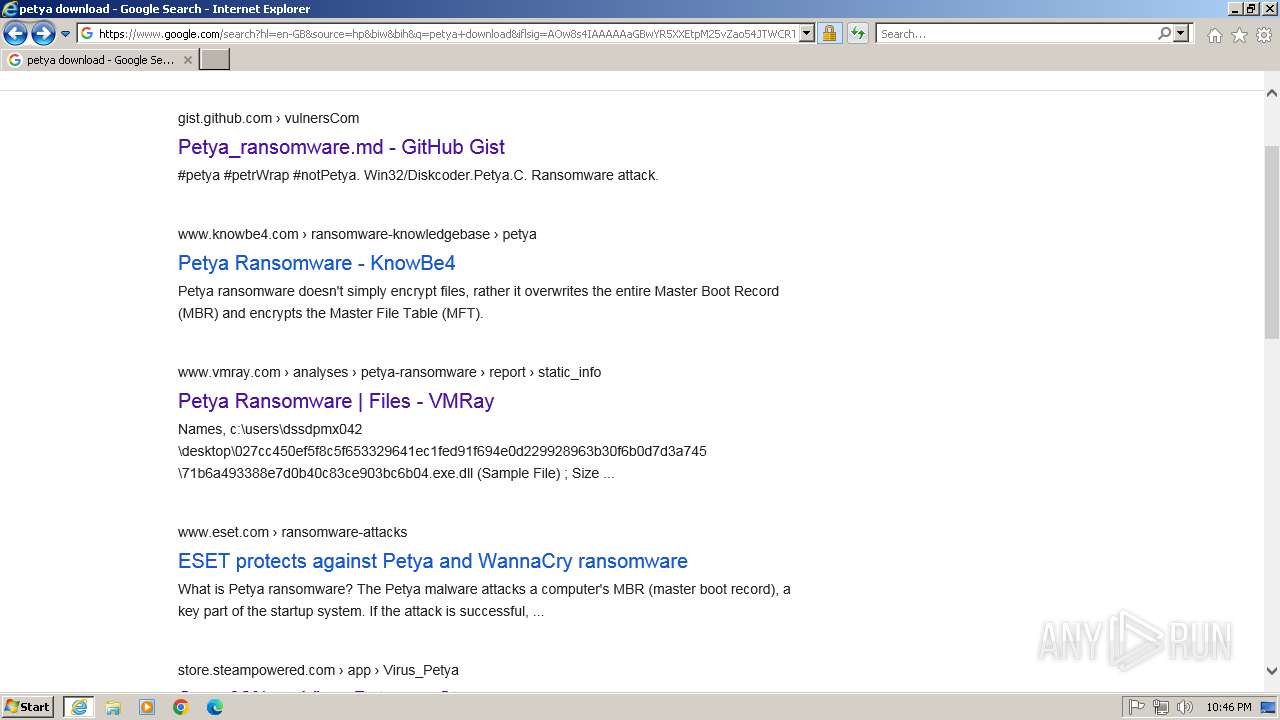
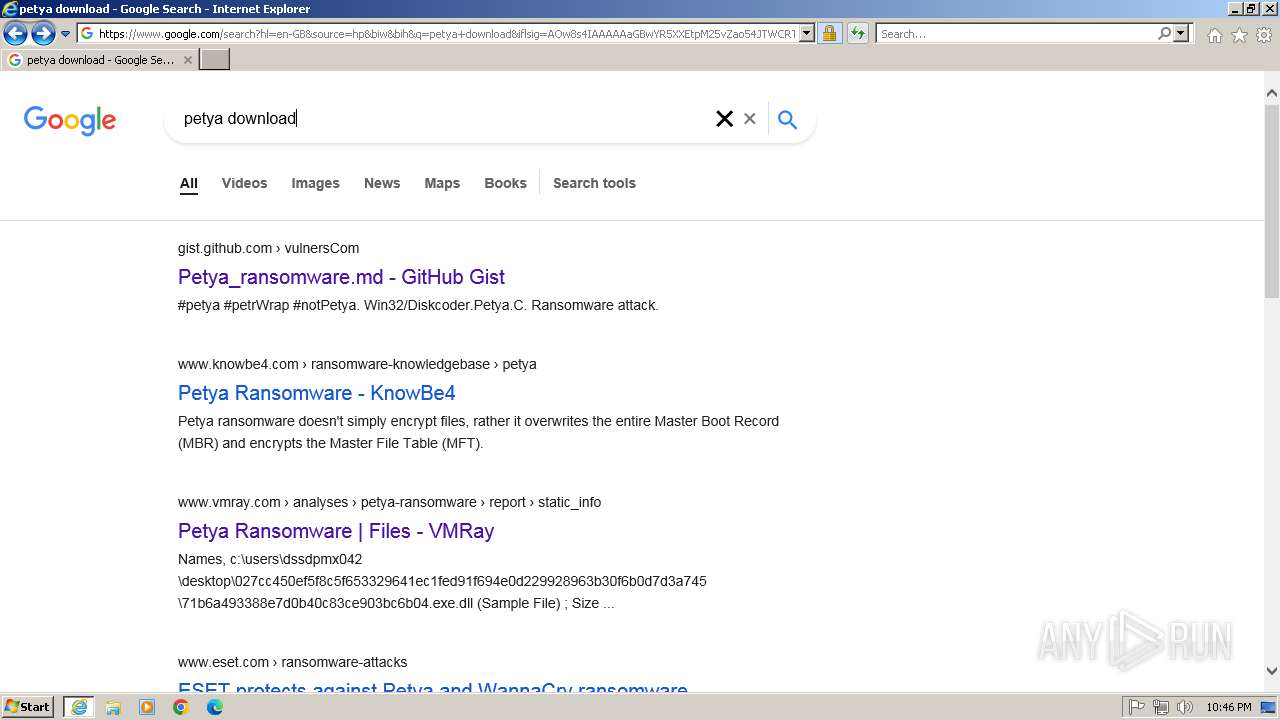
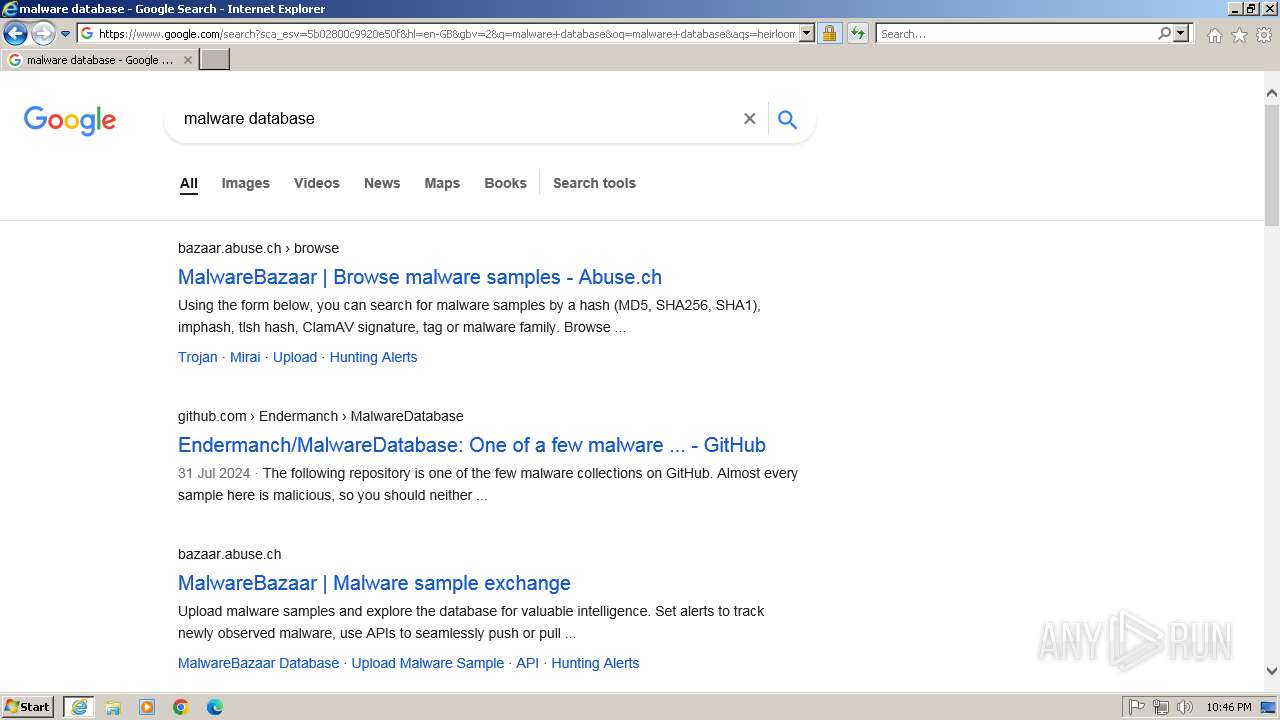
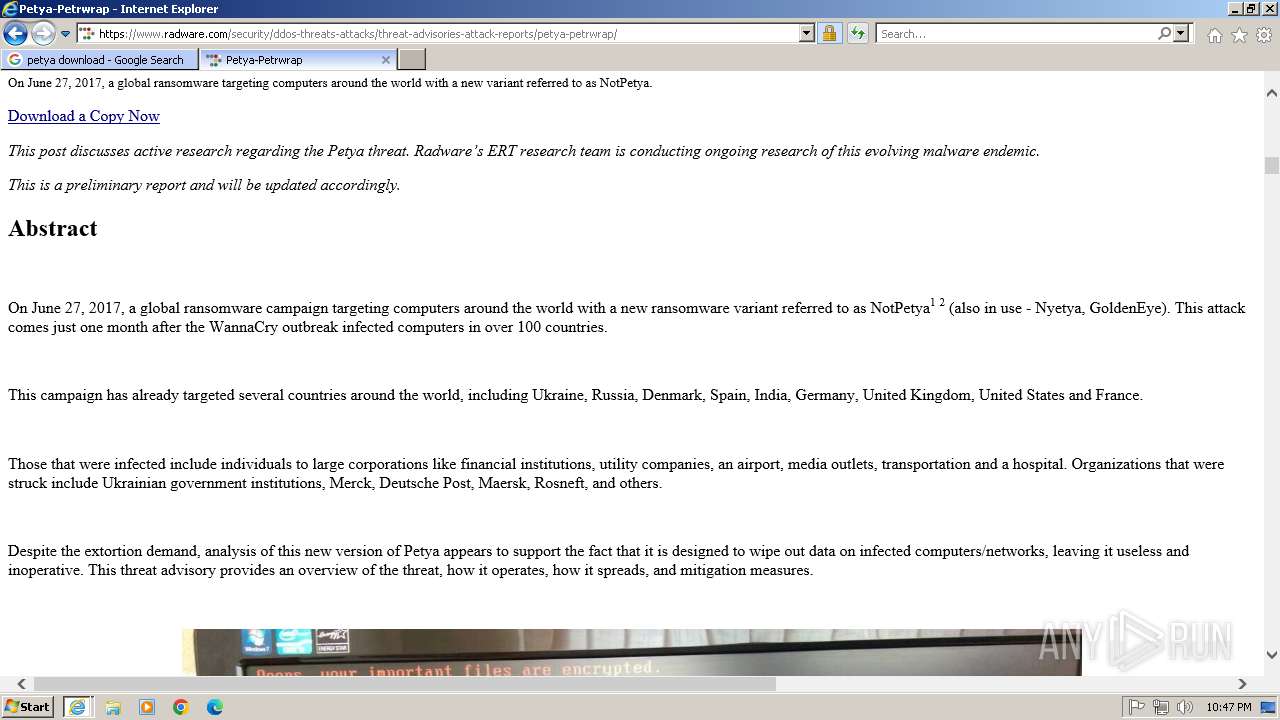
| URL: | google.com |
| Full analysis: | https://app.any.run/tasks/1438502d-6e72-46a9-ab78-c7c55c5b6997 |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2025, 21:44:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
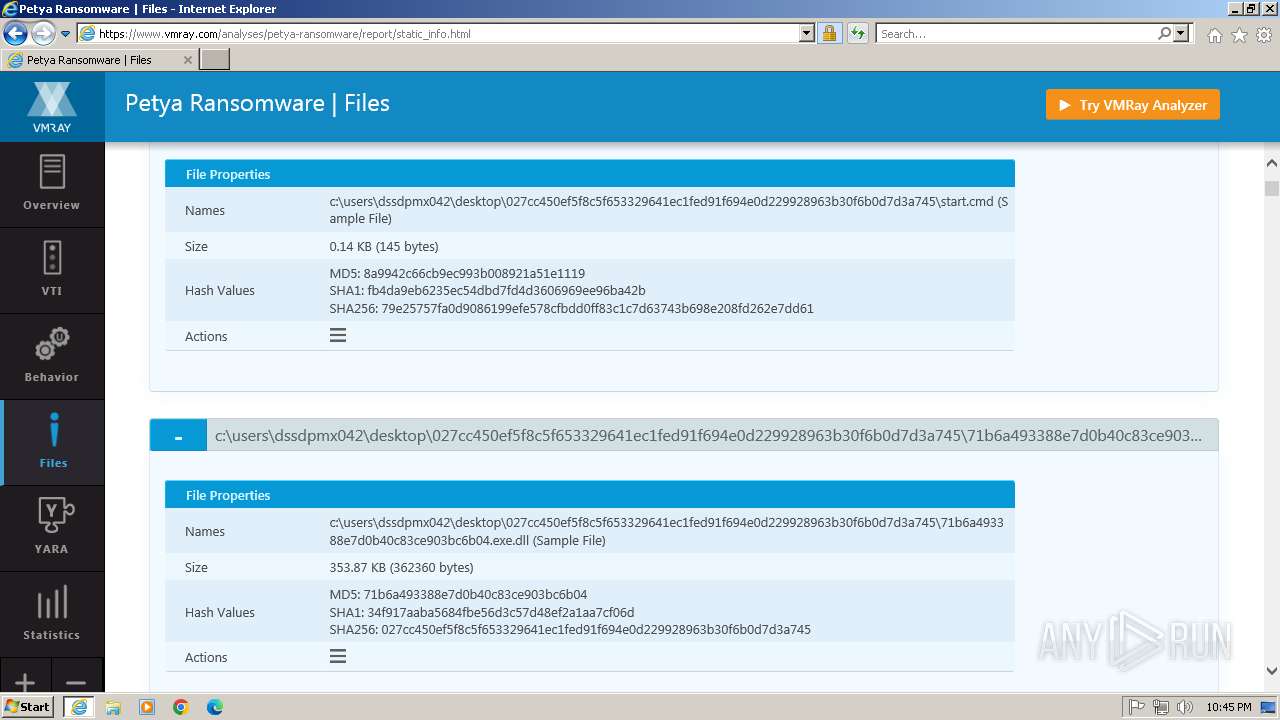
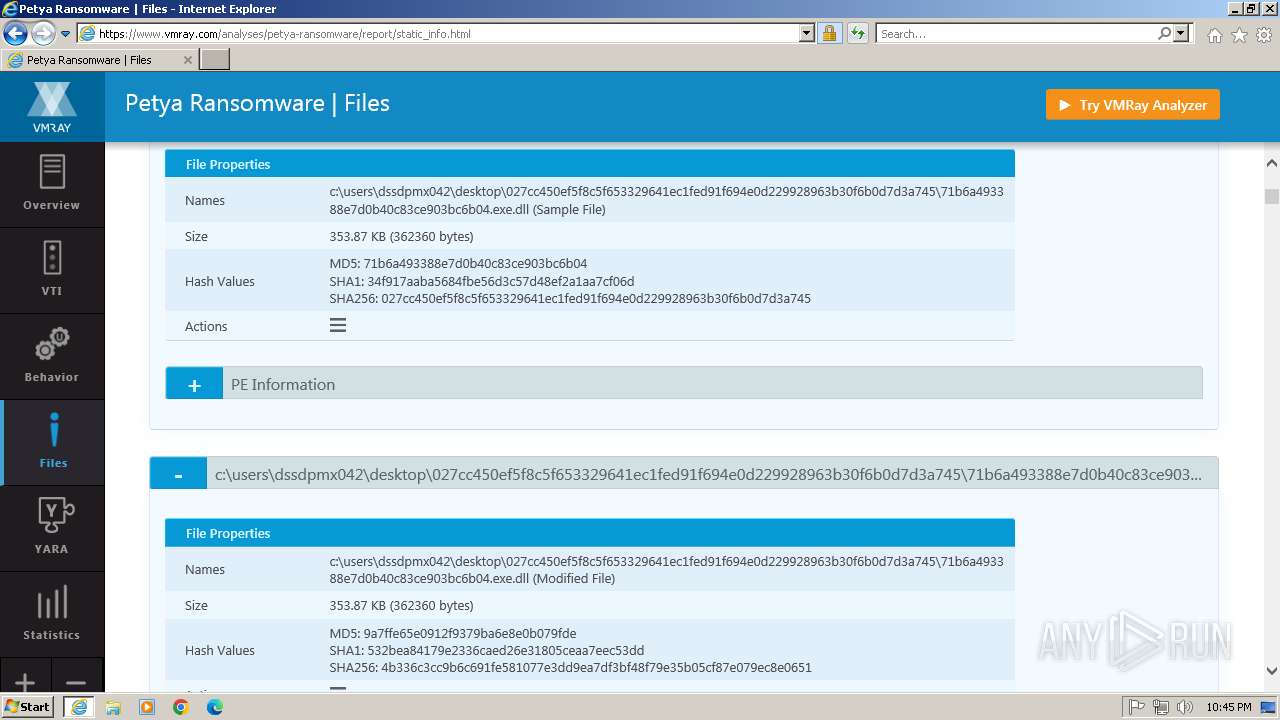
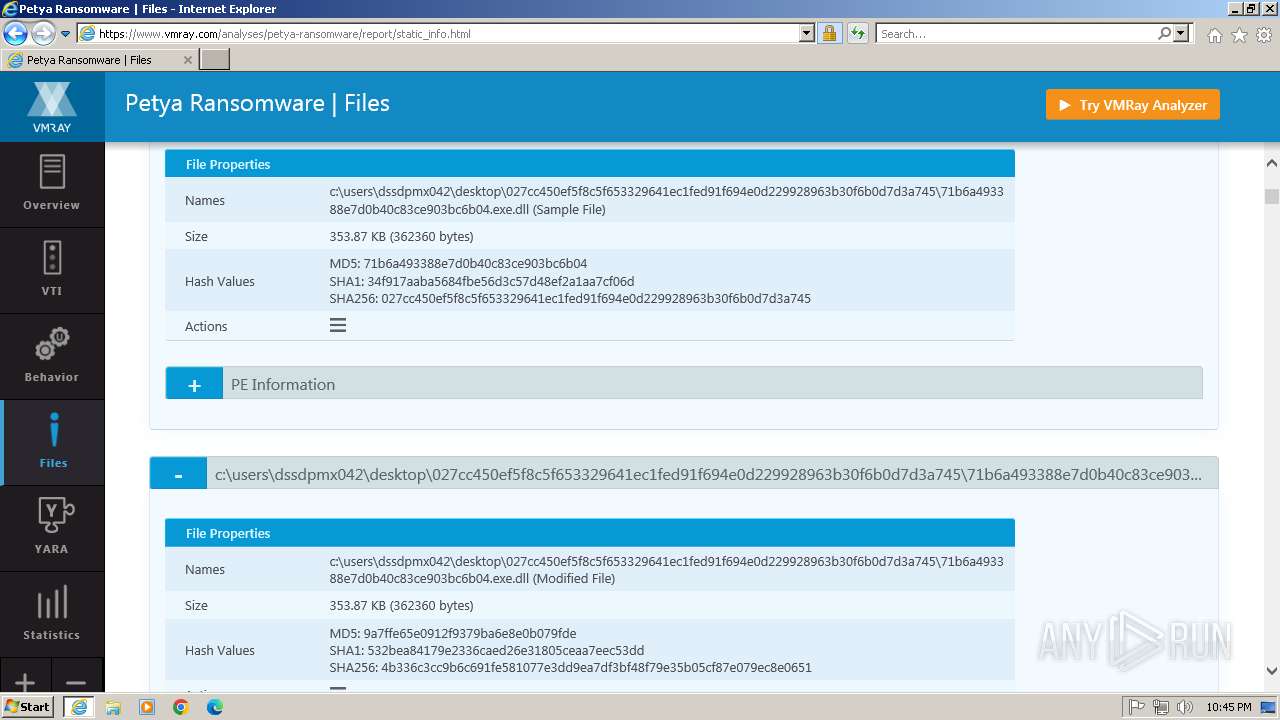
| MD5: | 1D5920F4B44B27A802BD77C4F0536F5A |
| SHA1: | BAEA954B95731C68AE6E45BD1E252EB4560CDC45 |
| SHA256: | D4C9D9027326271A89CE51FCAF328ED673F17BE33469FF979E8AB8DD501E664F |
| SSDEEP: | 3:duK:IK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- AcroRd32.exe (PID: 3172)
There is functionality for taking screenshot (YARA)
- AcroRd32.exe (PID: 3172)
INFO
Application launched itself
- AcroRd32.exe (PID: 2132)
- iexplore.exe (PID: 1396)
- RdrCEF.exe (PID: 1156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
14
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1156 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Internet Explorer\iexplore.exe" "google.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1064,9479980045839305220,1893250651418298578,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5848834478129355695 --renderer-client-id=6 --mojo-platform-channel-handle=1404 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 2400 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | iexplore.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1064,9479980045839305220,1893250651418298578,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=7855844030728935588 --mojo-platform-channel-handle=1204 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1064,9479980045839305220,1893250651418298578,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=13811400920101577830 --mojo-platform-channel-handle=1396 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2400 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1396 CREDAT:3413298 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 2400 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | iexplore.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3172 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /o /eo /l /b /id 2400 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1396 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
51 292
Read events
51 029
Write events
194
Delete events
69
Modification events
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31189109 | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31189109 | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1396) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
337
Text files
340
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9E62DD75009A293E0AF9565AE544F23E_BB07A5B9B2AB1D5B5BFC8DDE44F81FCD | binary | |
MD5:394FFFDF09E9109A33B6128561873173 | SHA256:9F37B687273F7174C8AEBDD3949D4C3141A3D97908A456E30541E1D76B74CE70 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\RP1I1AML.txt | text | |
MD5:8D87F4DB8E22F5F9E9166814F2429590 | SHA256:D1742381A9E713E6DBB0D83886ED5667292F9D7CDA3C7BCFCE94D20C3D6D6B53 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\W7QD6MRV.htm | html | |
MD5:7F8AB9E25F9290FE1BF4D565C23AF884 | SHA256:0B6315E2E1E1407BF0546E5FE561A496E061FD916C6ECFDB728657DFB7D88D95 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\0O3FMF3F.htm | html | |
MD5:D4B691CD9D99117B2EA34586D3E7EEB8 | SHA256:2178EEDD5723A6AC22E94EC59BDCD99229C87F3623753F5E199678242F0E90DE | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\K2J44Z4K.txt | text | |
MD5:2E4550385B09E655F5DF64000232DAA6 | SHA256:67544023AA6744E15248CF6AED8B57EBDA01DE8954F54D7A5EEDE08A37DEFFFE | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:AB76ADCB330C17D0F741AC137085B678 | SHA256:EAEA41E20E5AED941C6C5B57F73A090E9E075932F319ABAC240B9086EEF41B99 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:865BA41DECC92B7B80D96D0E6929716F | SHA256:0B2F895ACE9FD14216B5C0FE1F2084CD9B791AED8C200F2F80876D9E66D8C4FB | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:45D93CAF903DC5257DD26B7ED2967B43 | SHA256:C83F9213BF727600136326628BA36E3A49A92AEFAF667AF8FE80CB449AD9AEF1 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C60C0C29522E01E6A22BD2717F20782E_927CD7694ABAB4DA64EA66E7743CA0D9 | binary | |
MD5:8294F83255226F27484270BC0AD79197 | SHA256:5ADA6BDECDA1D7E0769DDF9D3D9847E77AC50DBCAD552B39BD39A41D743948D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
379
DNS requests
69
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3488 | iexplore.exe | GET | 301 | 142.250.186.78:80 | http://google.com/ | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 302 | 172.217.18.4:80 | http://www.google.com/ | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ef5948cfb5b5b070 | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQCPz0Q6k3ZnYxK9AlR4cXYH | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEDXNWpWbUgWVEsVsLcqbQaY%3D | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQCebGtkb2cNegm%2FGwwoZmjS | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCECTjR6N8i3I8EBOwnacJjJA%3D | unknown | — | — | whitelisted |
3488 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQCjL0CNZkjo7hCxrY6qmdi%2F | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
3488 | iexplore.exe | 142.250.186.78:80 | google.com | GOOGLE | US | whitelisted |
3488 | iexplore.exe | 172.217.18.4:80 | www.google.com | GOOGLE | US | whitelisted |
3488 | iexplore.exe | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
3488 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3488 | iexplore.exe | 172.217.18.3:80 | c.pki.goog | GOOGLE | US | whitelisted |
3488 | iexplore.exe | 142.250.186.67:80 | o.pki.goog | GOOGLE | US | whitelisted |
3488 | iexplore.exe | 216.58.206.35:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogads-pa.clients6.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
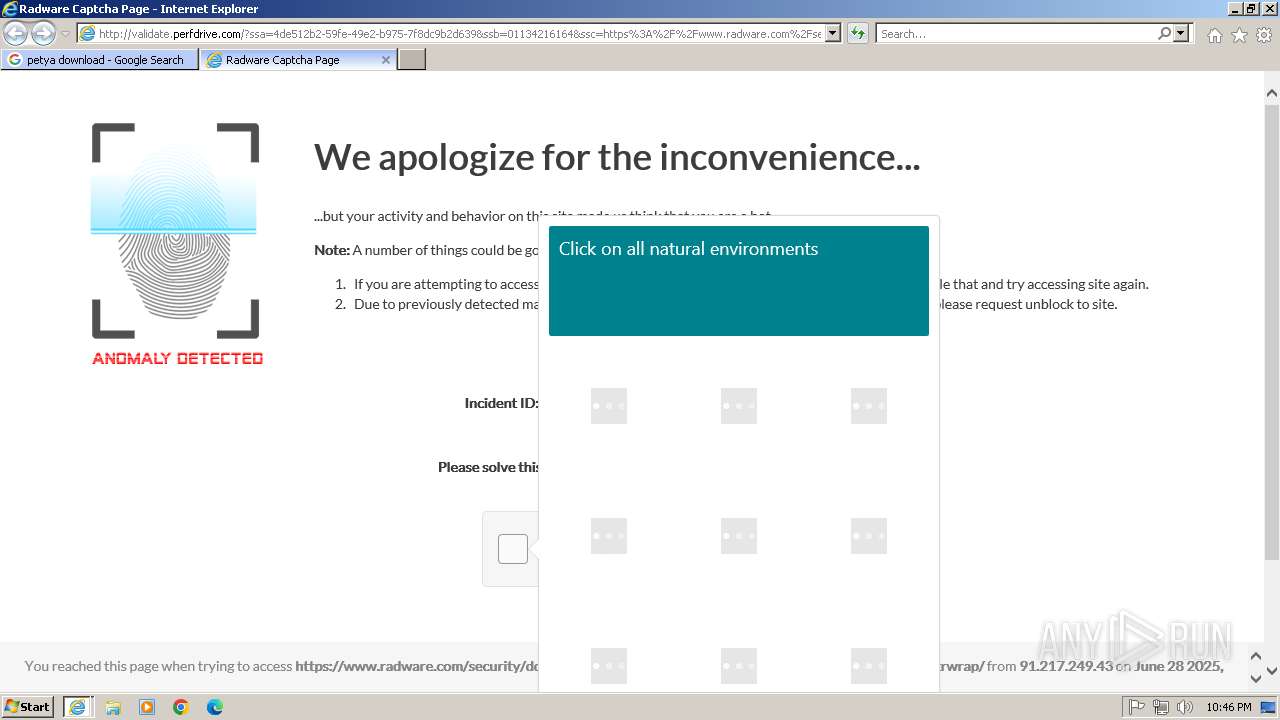
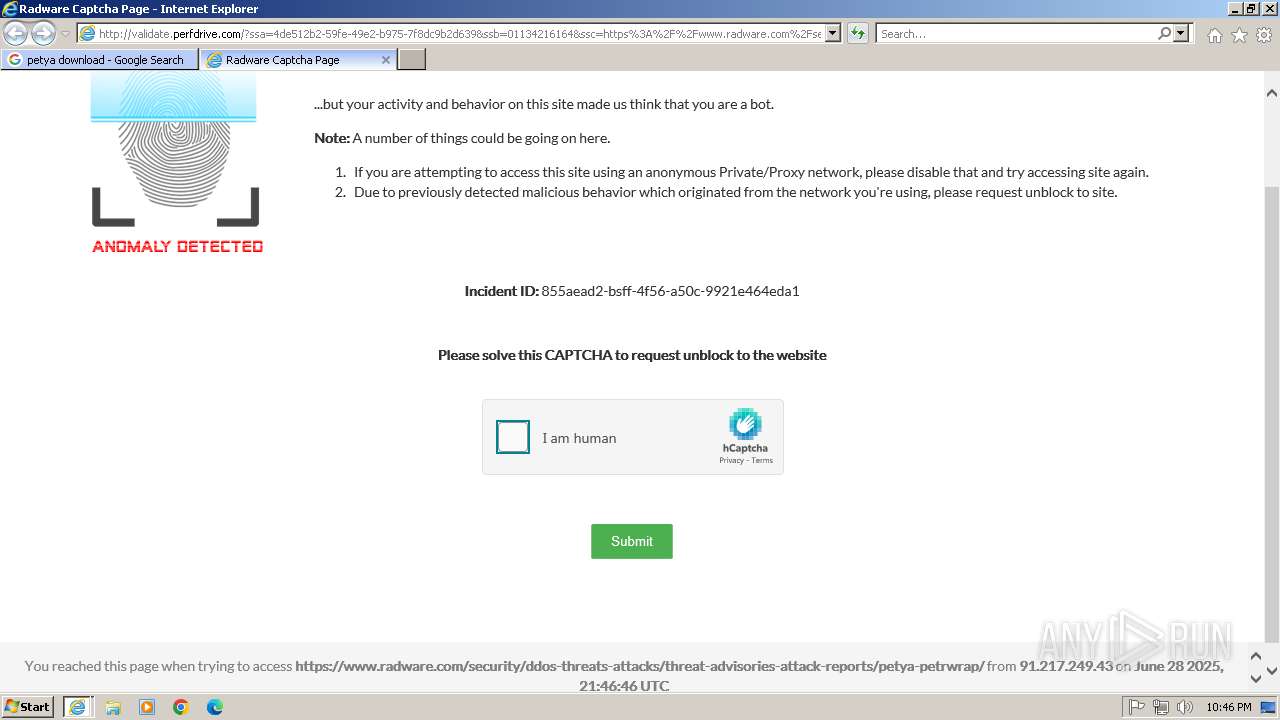
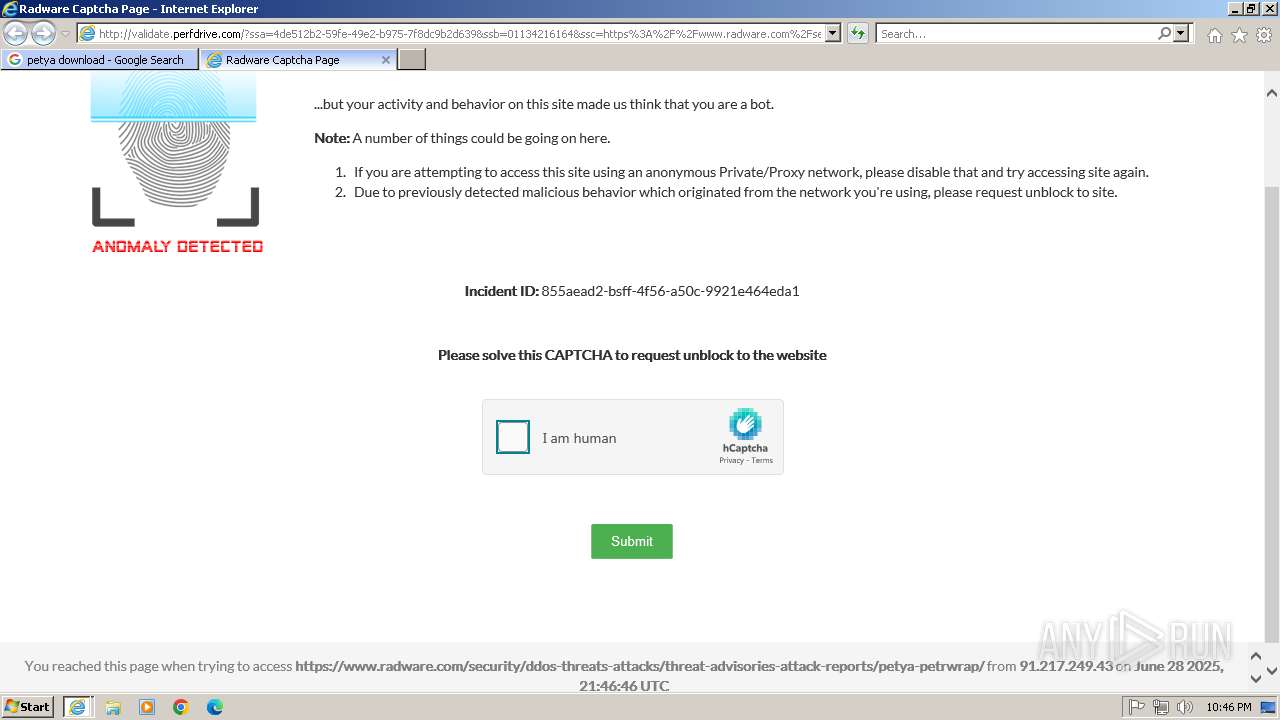
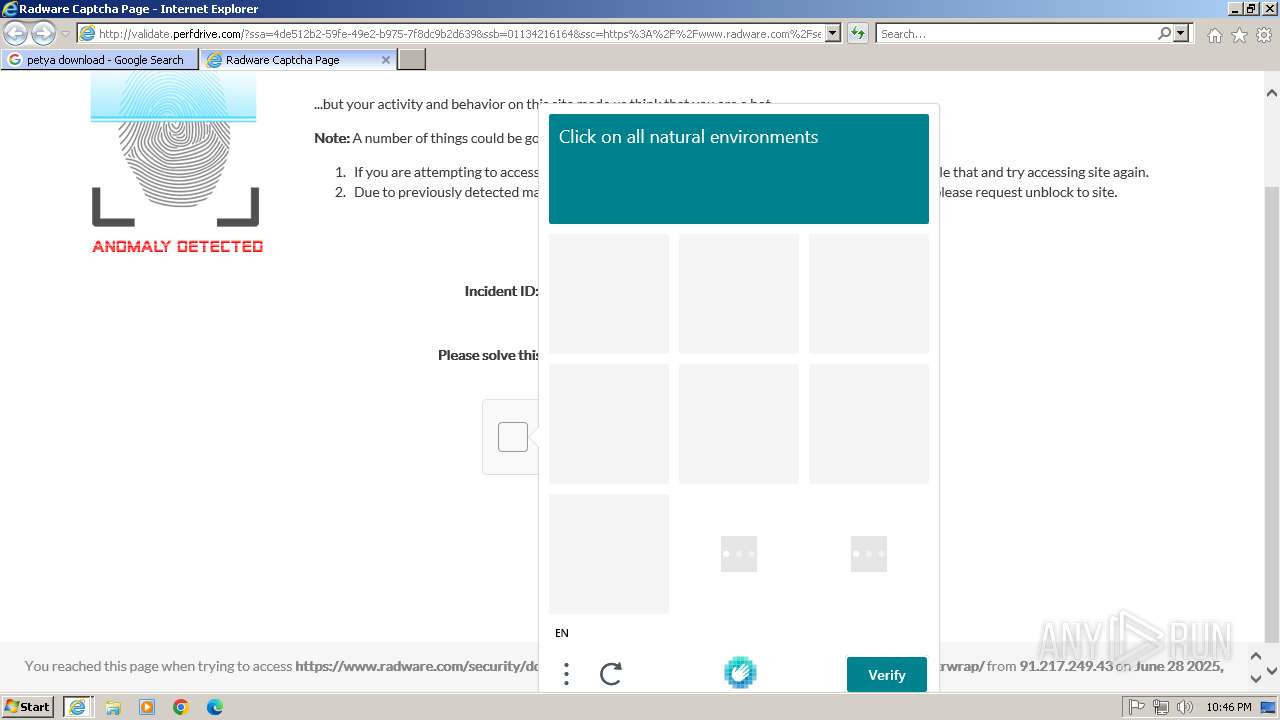
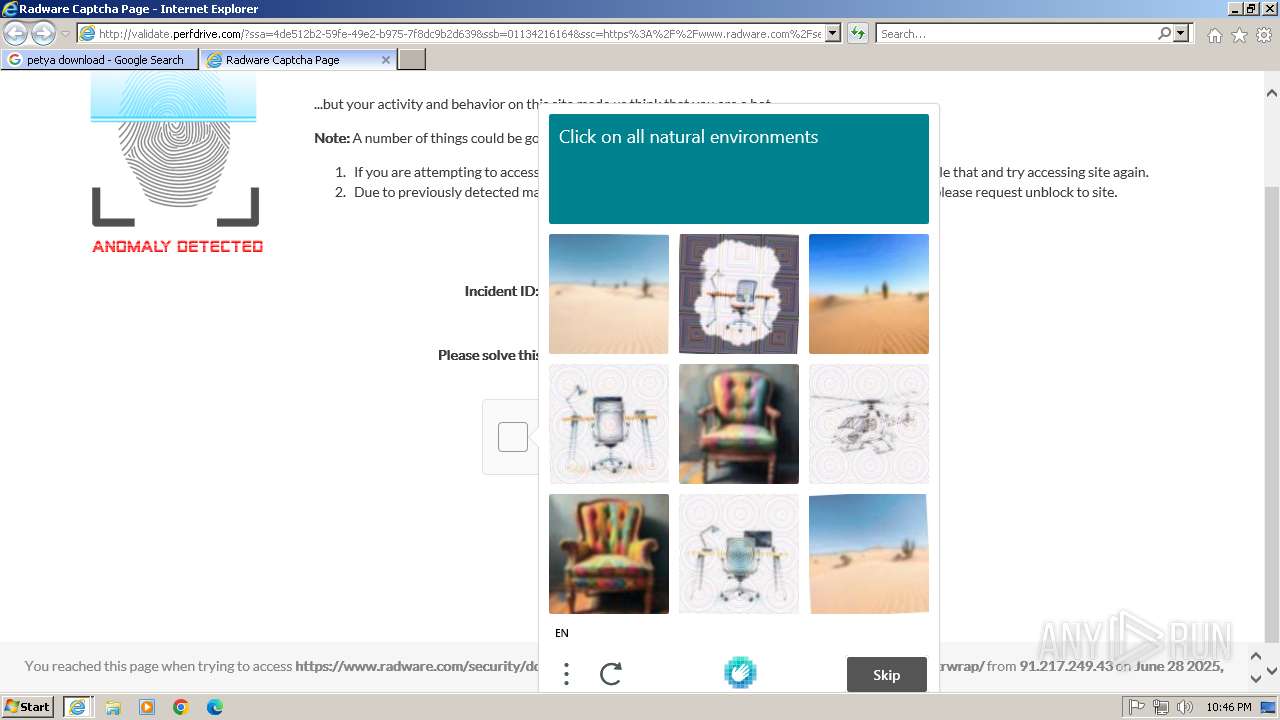
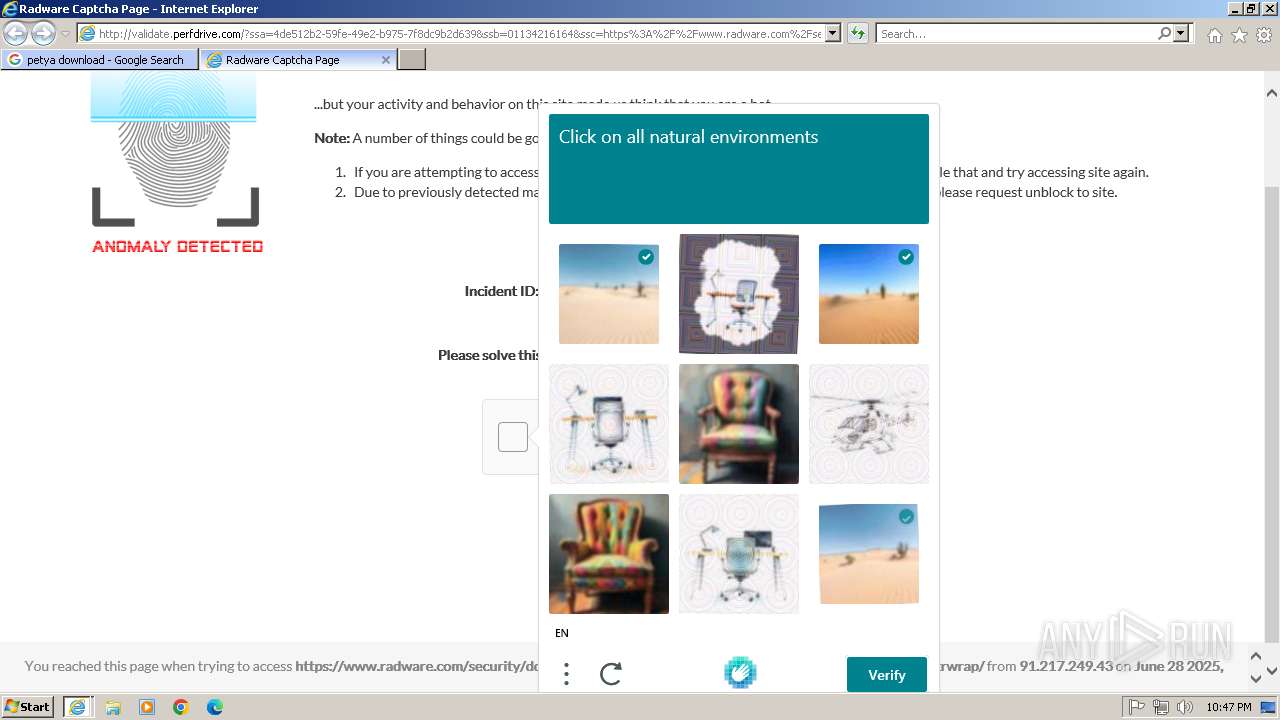
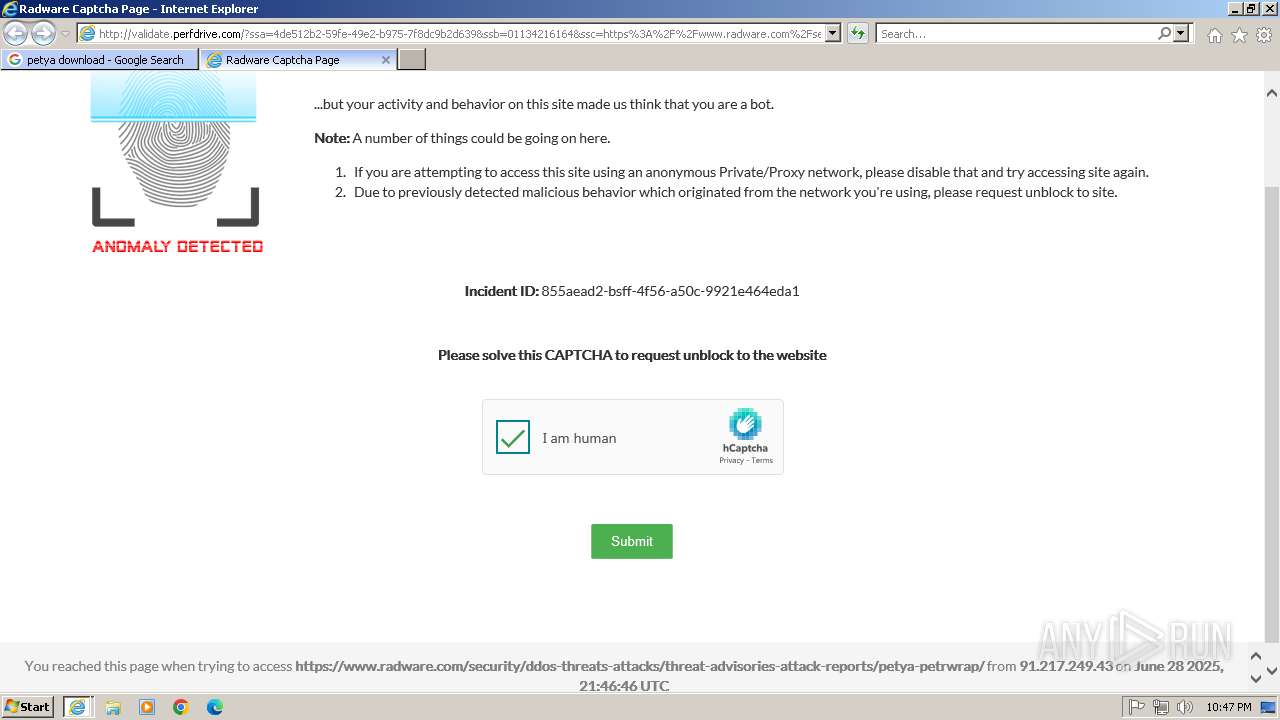
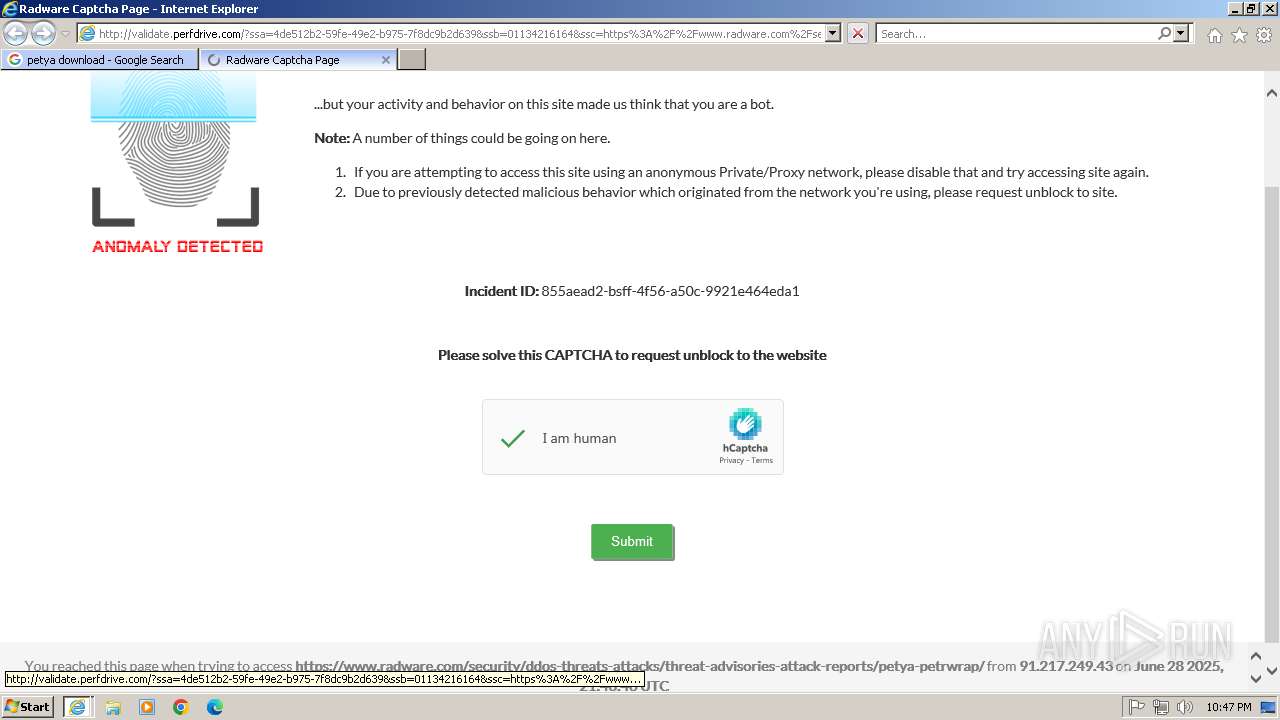
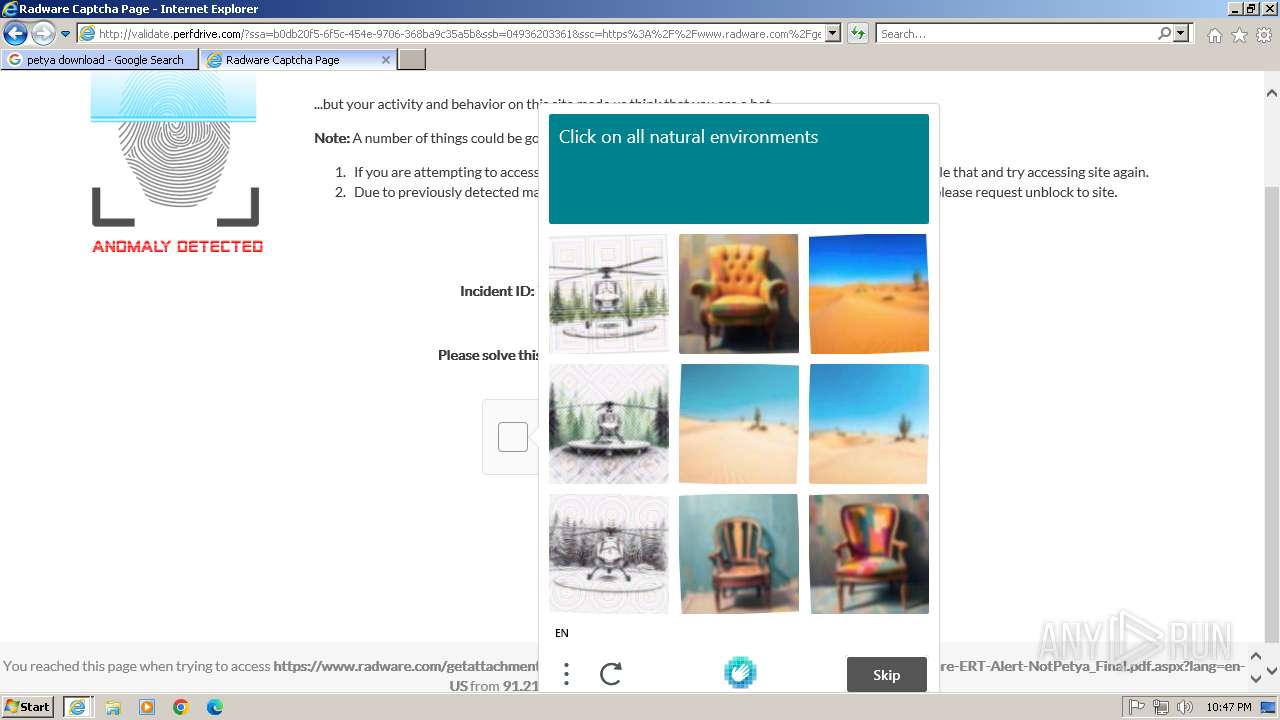
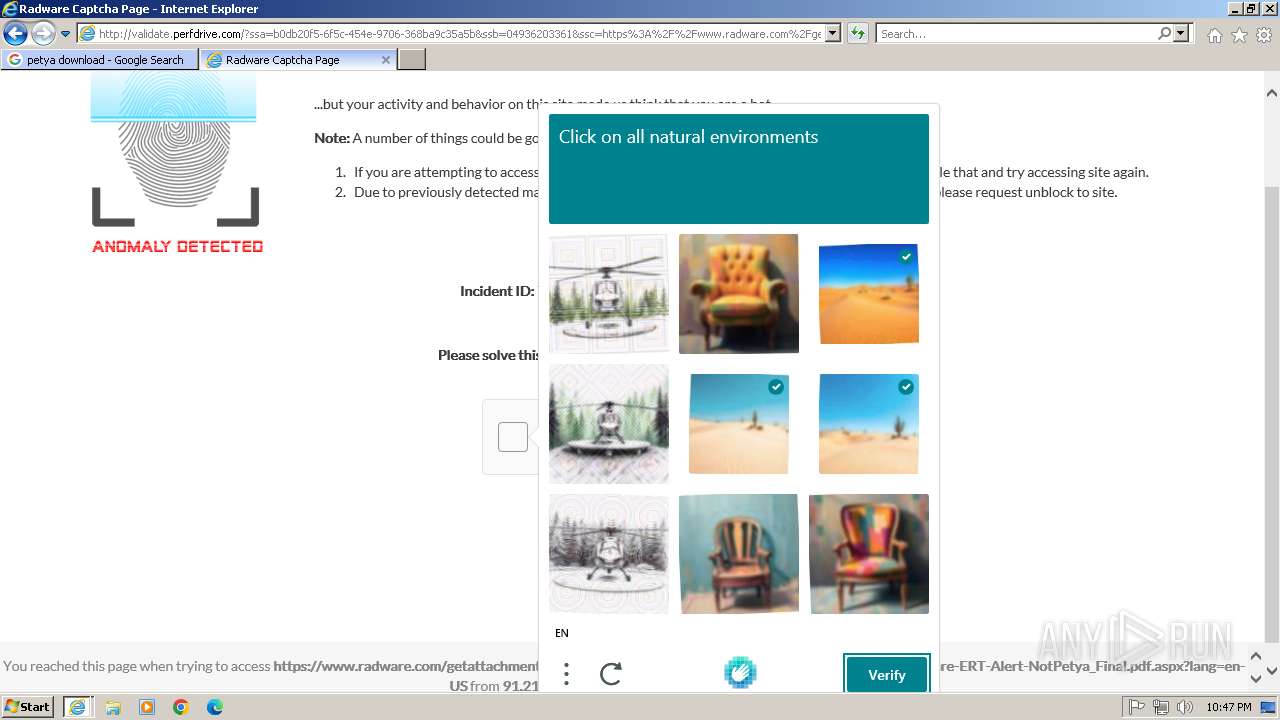
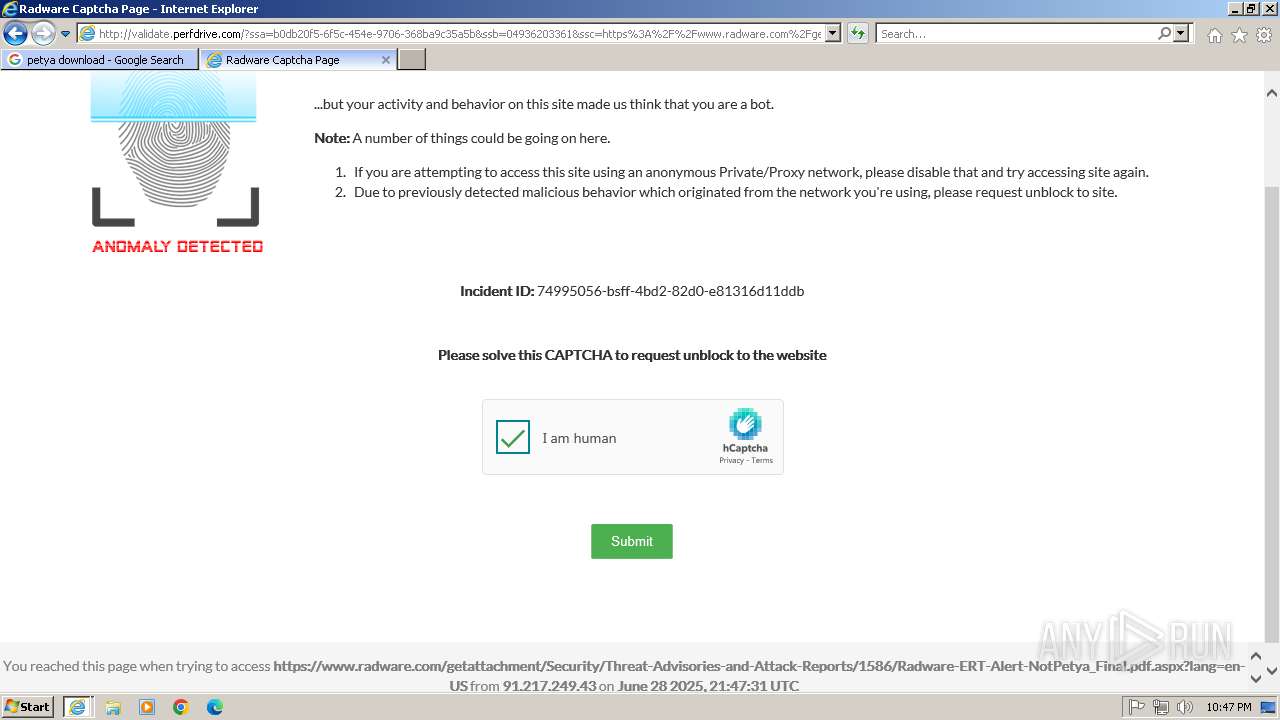
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2400 | iexplore.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M1 |
2400 | iexplore.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M2 |
2400 | iexplore.exe | Misc activity | SUSPICIOUS [ANY.RUN] JavaScript Obfuscation (ParseInt) |
2400 | iexplore.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M3 |
2400 | iexplore.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M1 |
2400 | iexplore.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M2 |
2400 | iexplore.exe | Misc activity | SUSPICIOUS [ANY.RUN] JavaScript Obfuscation (ParseInt) |
2400 | iexplore.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M3 |