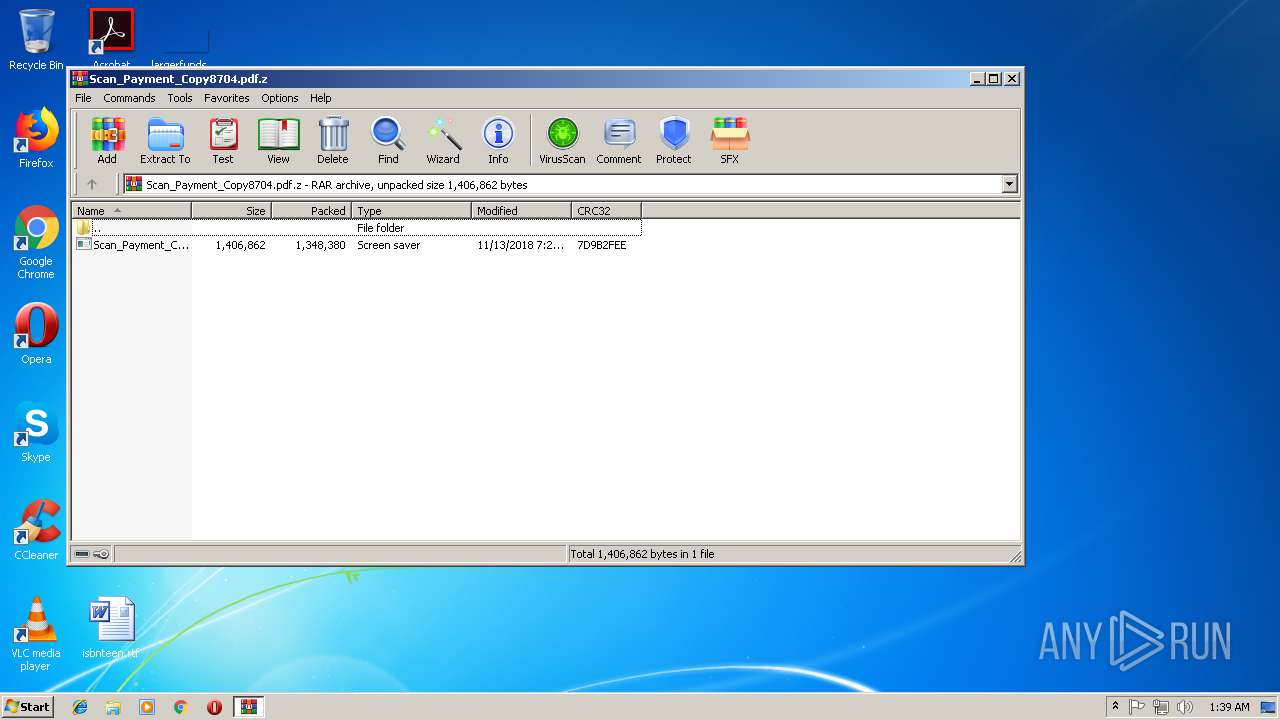
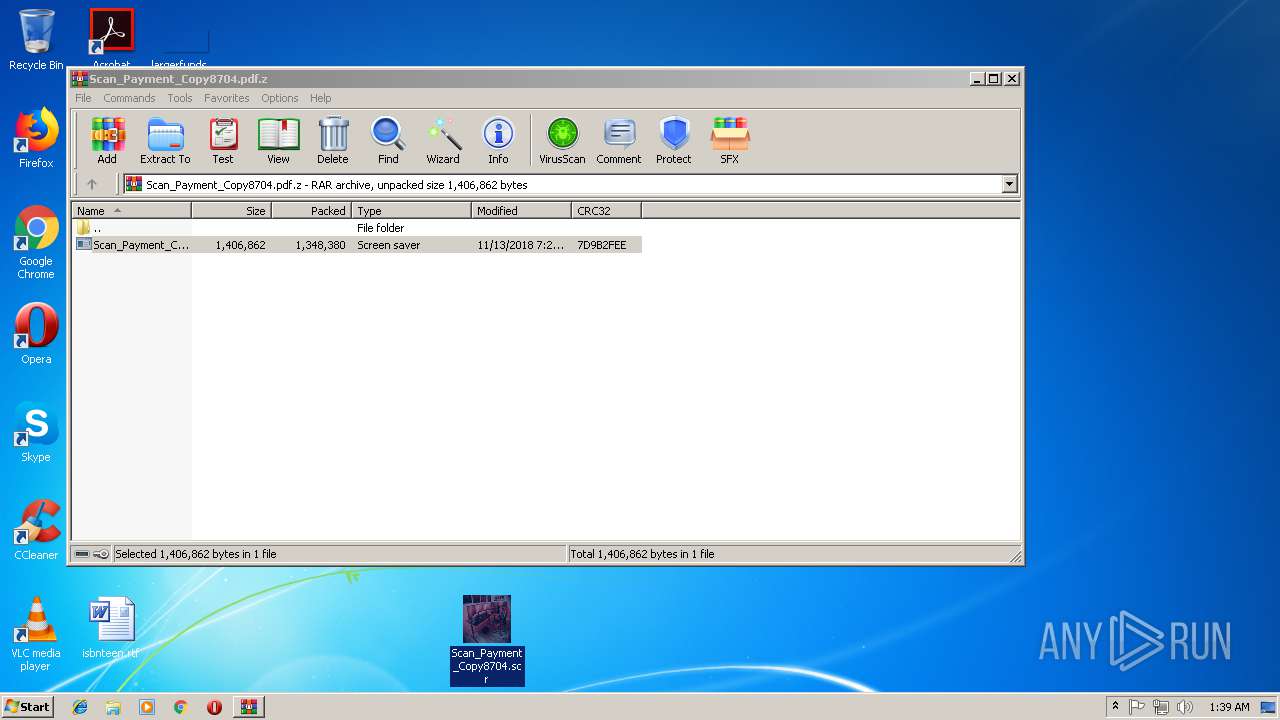
| File name: | Scan_Payment_Copy8704.pdf.z |
| Full analysis: | https://app.any.run/tasks/6615c80c-9566-4255-8f24-e24e852cc221 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 01:38:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 75A916608069CE9E740B74314045639E |
| SHA1: | 170EFD77F46BE82CA9EE66FE5C09841E192AF416 |
| SHA256: | D4A78BA5BA02A2C5A3B21DD2F56ADCE6AEFF1E682B02C57F8C933040B9EF191C |
| SSDEEP: | 24576:SMJ9TJ4saJMbKPuNGVw3BQc4I0btQYu0I+ZdXK1:XTJnaJI8uNMw3BQcGtQY1IKS |
MALICIOUS
Application was dropped or rewritten from another process
- Scan_Payment_Copy8704.scr (PID: 3216)
- che.exe (PID: 736)
- che.exe (PID: 312)
- IMDCSC.exe (PID: 2536)
- RegSvcs.exe (PID: 2144)
Changes the autorun value in the registry
- che.exe (PID: 312)
- RegSvcs.exe (PID: 2144)
SUSPICIOUS
Drop AutoIt3 executable file
- Scan_Payment_Copy8704.scr (PID: 3216)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2700)
- Scan_Payment_Copy8704.scr (PID: 3216)
- che.exe (PID: 312)
- RegSvcs.exe (PID: 2144)
Application launched itself
- che.exe (PID: 736)
Starts itself from another location
- RegSvcs.exe (PID: 2144)
INFO
Dropped object may contain Bitcoin addresses
- che.exe (PID: 736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
38
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | C:\Users\admin\AppData\Local\Temp\27018646\che.exe C:\Users\admin\AppData\Local\Temp\27018646\SYXOZ | C:\Users\admin\AppData\Local\Temp\27018646\che.exe | che.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 736 | "C:\Users\admin\AppData\Local\Temp\27018646\che.exe" itc=htc | C:\Users\admin\AppData\Local\Temp\27018646\che.exe | — | Scan_Payment_Copy8704.scr | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\AppData\Local\Temp\RegSvcs.exe" | C:\Users\admin\AppData\Local\Temp\RegSvcs.exe | che.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2536 | "C:\Users\admin\Documents\DCSCMIN\IMDCSC.exe" | C:\Users\admin\Documents\DCSCMIN\IMDCSC.exe | — | RegSvcs.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Scan_Payment_Copy8704.pdf.z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3216 | "C:\Users\admin\Desktop\Scan_Payment_Copy8704.scr" /S | C:\Users\admin\Desktop\Scan_Payment_Copy8704.scr | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 135
Read events
1 103
Write events
32
Delete events
0
Modification events
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Scan_Payment_Copy8704.pdf.z | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
| (PID) Process: | (3216) Scan_Payment_Copy8704.scr | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
5
Suspicious files
0
Text files
50
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\iux.icm | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\kwk.xl | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\vbh.mp3 | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\ikr.mp4 | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\tbc.mp3 | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\pjj.mp4 | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\see.ico | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\hkc.mp4 | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\hlw.txt | text | |
MD5:— | SHA256:— | |||
| 3216 | Scan_Payment_Copy8704.scr | C:\Users\admin\AppData\Local\Temp\27018646\vgs.jpg | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report